Aliceo Inc. Breach Scenario: Cybersecurity Risk Mitigation Report
VerifiedAdded on 2022/08/15
|6
|1100
|15
Report
AI Summary
This report analyzes a cybersecurity breach scenario at Aliceo Inc., a consumer credit ratings agency. The scenario involves communication breakdowns and the discovery of fake credentials and unencrypted data. The report focuses on mitigating cyber security risks through the implementation of firewalls, investment in updated security software, and the incorporation of machine learning into security protocols. The report discusses the effectiveness of firewalls in controlling network traffic, the importance of updated software in protecting against viruses and malware, and the advantages of machine learning in enhancing security protocols. The student's analysis provides insights into protecting systems and networks from digital attacks and ensuring the safety of organizational operations. The report emphasizes the importance of proactive measures in addressing cybersecurity threats.

Running head: BREACH SCENARIO
Chapter 6 Breach Scenario
Name of the Student
Name of the University
Author’s Note:
Chapter 6 Breach Scenario
Name of the Student
Name of the University
Author’s Note:
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

1
BREACH SCENARIO
Cyber Risk Issues for the Charitable Operation
The organization of Aliceo Inc. has faced a major breakdown in communications
within one of the corporate lines of business and the cyber security team. Cyber security
could be referred to as the core practice to secure networks, programs and systems from
different digital attacks. Such distinct attacks are majorly aimed at accessing, destroying or
changing the sensitive information for coercion of money from distinct users and interrupting
usual business processes (Buczak & Guven, 2015). A proper deloyment of an effective
measure of cyber security is quite challenging, since there exists no devices than individual
and the attacks are turning extremely innovative.
Konovsky have checked the credentials of Bob Fake and discovers that the credentials
are false and he is not a real individual, but a computer generated ID, which was being
created by a specific website designing organization. Moreover, after quick scanning of the
website, several unencrypted usernames and passwords were found out for the Buenos Aires
based Aliceo Inc. employees, who have taken participation within the charitable initiative.
This came into account, when Konovsky searched about the scope of the breach and it
was found out that there was a new alert from the exfiltration from the respective Compliant
Resolution Group (Ben-Asher & Gonzalez, 2015). There are some of the most important and
significant techniques that can easily diminish the issues related to cyber security and these
techniques are provided in the following paragraphs:
i) Implementation of Firewalls: The first and the foremost effective measure for
mitigation of the cyber security risk within the charitable operations for Aliceo Inc. would be
successful implementation of firewalls. It is referred to as the most significant and
noteworthy protection of systems and networks from any type of unauthorized accessibility.
It is the specific system of network security, which monitors as well as controls the incoming
BREACH SCENARIO
Cyber Risk Issues for the Charitable Operation
The organization of Aliceo Inc. has faced a major breakdown in communications
within one of the corporate lines of business and the cyber security team. Cyber security
could be referred to as the core practice to secure networks, programs and systems from
different digital attacks. Such distinct attacks are majorly aimed at accessing, destroying or
changing the sensitive information for coercion of money from distinct users and interrupting
usual business processes (Buczak & Guven, 2015). A proper deloyment of an effective
measure of cyber security is quite challenging, since there exists no devices than individual
and the attacks are turning extremely innovative.
Konovsky have checked the credentials of Bob Fake and discovers that the credentials
are false and he is not a real individual, but a computer generated ID, which was being
created by a specific website designing organization. Moreover, after quick scanning of the
website, several unencrypted usernames and passwords were found out for the Buenos Aires
based Aliceo Inc. employees, who have taken participation within the charitable initiative.
This came into account, when Konovsky searched about the scope of the breach and it
was found out that there was a new alert from the exfiltration from the respective Compliant
Resolution Group (Ben-Asher & Gonzalez, 2015). There are some of the most important and
significant techniques that can easily diminish the issues related to cyber security and these
techniques are provided in the following paragraphs:
i) Implementation of Firewalls: The first and the foremost effective measure for
mitigation of the cyber security risk within the charitable operations for Aliceo Inc. would be
successful implementation of firewalls. It is referred to as the most significant and
noteworthy protection of systems and networks from any type of unauthorized accessibility.
It is the specific system of network security, which monitors as well as controls the incoming
2
BREACH SCENARIO
and outgoing traffic on the basis of different previously determined security rules (Gupta,
Agrawal & Yamaguchi, 2016).
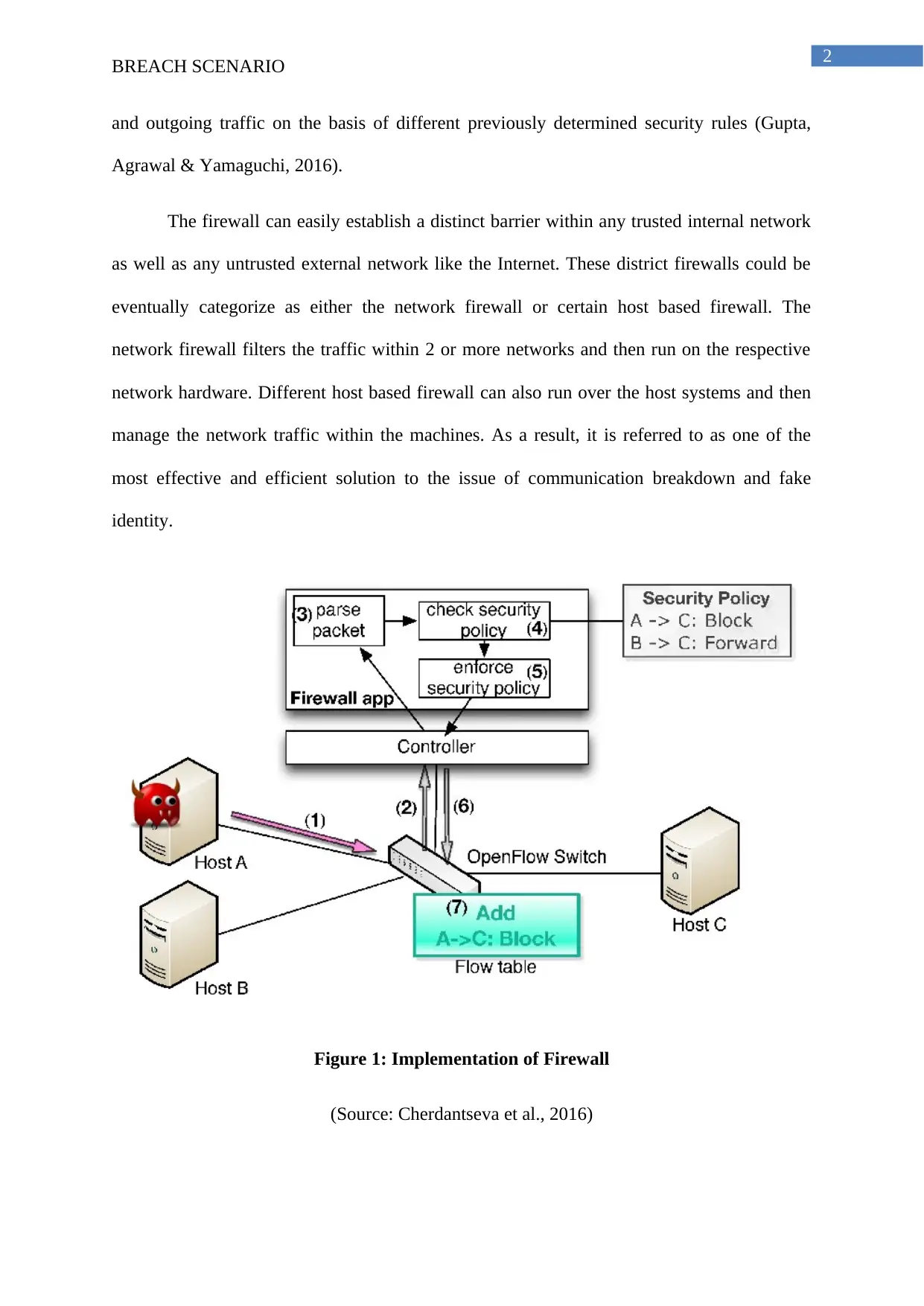
The firewall can easily establish a distinct barrier within any trusted internal network
as well as any untrusted external network like the Internet. These district firewalls could be
eventually categorize as either the network firewall or certain host based firewall. The
network firewall filters the traffic within 2 or more networks and then run on the respective
network hardware. Different host based firewall can also run over the host systems and then
manage the network traffic within the machines. As a result, it is referred to as one of the
most effective and efficient solution to the issue of communication breakdown and fake
identity.
Figure 1: Implementation of Firewall
(Source: Cherdantseva et al., 2016)
BREACH SCENARIO
and outgoing traffic on the basis of different previously determined security rules (Gupta,
Agrawal & Yamaguchi, 2016).
The firewall can easily establish a distinct barrier within any trusted internal network
as well as any untrusted external network like the Internet. These district firewalls could be
eventually categorize as either the network firewall or certain host based firewall. The
network firewall filters the traffic within 2 or more networks and then run on the respective
network hardware. Different host based firewall can also run over the host systems and then
manage the network traffic within the machines. As a result, it is referred to as one of the
most effective and efficient solution to the issue of communication breakdown and fake
identity.
Figure 1: Implementation of Firewall
(Source: Cherdantseva et al., 2016)
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

3
BREACH SCENARIO
ii) Investment in the Updated Security Software: The second suitable and effective
measure for mitigation of the cyber security risk within the charitable operations for Aliceo
Inc. would be investing in the up graded security software. It is quite important and
significant to make investments in the security software, since it can secure as well as protect
a computer, computing enabled device or network.
This type of software would manage the access control and then provide data
protection for ensuring that the system is absolutely safe and secured from the viruses or any
type of network based intrusion, so that they are able to defend against the system level
security threats (Abomhara, 2015). Moreover, such distinct software up gradation would be
encompassing a suite of various software, which could deliver data as well as network or
cyber security in different formations. The updated security software could easily protect the
system from virus, unauthenticated usage, security exploitation and malware that originate
from the Internet.
iii) Incorporation of Machine Learning into Security Protocols: The third effective
and suitable measure for mitigation of the cyber security risk within the charitable operations
for Aliceo Inc. is proper incorporation of machine learning into security protocols. Since, the
organization is dealing with different issues related to communication breakdown, it would
be extremely advantageous for them to include machine learning within security protocols
(Dua & Du, 2016). Machine learning is the significant application of AI, which provides the
system with the core ability to mechanically learn and then improvise from experiences
without being explicitly programmed.
As a result, this machine learning would focus on the overall development of the
computerized programmed, which could easily access the data and then utilize it for
themselves. Involvement of machine learning within security protocols would ensure that the
BREACH SCENARIO
ii) Investment in the Updated Security Software: The second suitable and effective
measure for mitigation of the cyber security risk within the charitable operations for Aliceo
Inc. would be investing in the up graded security software. It is quite important and
significant to make investments in the security software, since it can secure as well as protect
a computer, computing enabled device or network.
This type of software would manage the access control and then provide data
protection for ensuring that the system is absolutely safe and secured from the viruses or any
type of network based intrusion, so that they are able to defend against the system level
security threats (Abomhara, 2015). Moreover, such distinct software up gradation would be
encompassing a suite of various software, which could deliver data as well as network or
cyber security in different formations. The updated security software could easily protect the
system from virus, unauthenticated usage, security exploitation and malware that originate
from the Internet.
iii) Incorporation of Machine Learning into Security Protocols: The third effective
and suitable measure for mitigation of the cyber security risk within the charitable operations
for Aliceo Inc. is proper incorporation of machine learning into security protocols. Since, the
organization is dealing with different issues related to communication breakdown, it would
be extremely advantageous for them to include machine learning within security protocols
(Dua & Du, 2016). Machine learning is the significant application of AI, which provides the
system with the core ability to mechanically learn and then improvise from experiences
without being explicitly programmed.
As a result, this machine learning would focus on the overall development of the
computerized programmed, which could easily access the data and then utilize it for
themselves. Involvement of machine learning within security protocols would ensure that the
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
4
BREACH SCENARIO
respective systems and processes are safe and secured and would not bring out any type of
vulnerability under any circumstance. Hence, the organizational charitable operations in
Aliceo Inc. would be free from cyber risks.
BREACH SCENARIO
respective systems and processes are safe and secured and would not bring out any type of
vulnerability under any circumstance. Hence, the organizational charitable operations in
Aliceo Inc. would be free from cyber risks.

5
BREACH SCENARIO
References
Abomhara, M. (2015). Cyber security and the internet of things: vulnerabilities, threats,
intruders and attacks. Journal of Cyber Security and Mobility, 4(1), 65-88.
Ben-Asher, N., & Gonzalez, C. (2015). Effects of cyber security knowledge on attack
detection. Computers in Human Behavior, 48, 51-61.
Buczak, A. L., & Guven, E. (2015). A survey of data mining and machine learning methods
for cyber security intrusion detection. IEEE Communications surveys &
tutorials, 18(2), 1153-1176.
Cherdantseva, Y., Burnap, P., Blyth, A., Eden, P., Jones, K., Soulsby, H., & Stoddart, K.
(2016). A review of cyber security risk assessment methods for SCADA
systems. Computers & security, 56, 1-27.
Dua, S., & Du, X. (2016). Data mining and machine learning in cybersecurity. Auerbach
Publications.
Gupta, B., Agrawal, D. P., & Yamaguchi, S. (Eds.). (2016). Handbook of research on
modern cryptographic solutions for computer and cyber security. IGI global.
BREACH SCENARIO
References
Abomhara, M. (2015). Cyber security and the internet of things: vulnerabilities, threats,
intruders and attacks. Journal of Cyber Security and Mobility, 4(1), 65-88.
Ben-Asher, N., & Gonzalez, C. (2015). Effects of cyber security knowledge on attack
detection. Computers in Human Behavior, 48, 51-61.
Buczak, A. L., & Guven, E. (2015). A survey of data mining and machine learning methods
for cyber security intrusion detection. IEEE Communications surveys &
tutorials, 18(2), 1153-1176.
Cherdantseva, Y., Burnap, P., Blyth, A., Eden, P., Jones, K., Soulsby, H., & Stoddart, K.
(2016). A review of cyber security risk assessment methods for SCADA
systems. Computers & security, 56, 1-27.
Dua, S., & Du, X. (2016). Data mining and machine learning in cybersecurity. Auerbach
Publications.
Gupta, B., Agrawal, D. P., & Yamaguchi, S. (Eds.). (2016). Handbook of research on
modern cryptographic solutions for computer and cyber security. IGI global.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 6
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





