CYB-690: Cybersecurity Program Development - All Health Corporation
VerifiedAdded on 2022/08/27
|5
|977
|19
Project
AI Summary
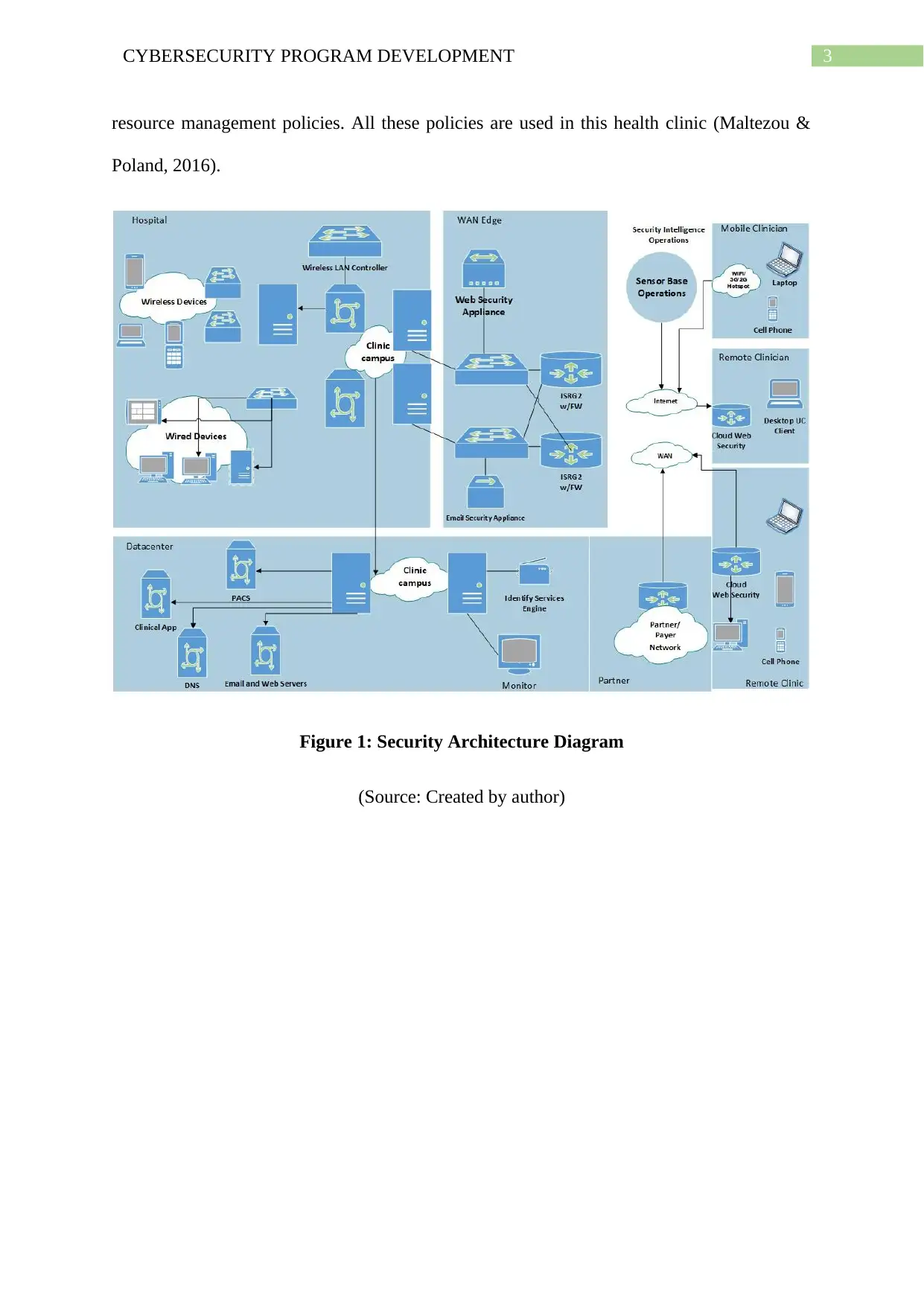
This project focuses on developing a cybersecurity program for All Health Corporation, a healthcare clinic. It identifies six types of sensitive data stored, including electronic health records and claims data, and details where this information is stored within a Clinical Data Repository (CDR) or Clinical Data Warehouse (CDW). The assignment outlines the hardware and software infrastructure, including routers, firewalls, and EMR systems, and presents a security architecture diagram. It also addresses potential cybersecurity threats such as ransomware and data breaches, and specifies security controls like patient identification and access restrictions. The project concludes with a discussion of relevant policies, including administrative, information management, and human resource policies, to ensure comprehensive data protection within the clinic. References are provided for further research and understanding of cybersecurity in healthcare.
1 out of 5











![[object Object]](/_next/static/media/star-bottom.7253800d.svg)