Comparative Analysis of Cipher Encryption Techniques: ECB, CBC, OFB
VerifiedAdded on 2022/11/17
|14
|2343
|240
Report
AI Summary
This report provides a detailed analysis of three cipher encryption techniques: Electronic Codebook (ECB), Cipher Block Chaining (CBC), and Output Feedback (OFB). It explains the fundamental principles behind each method, including how plaintext is encrypted into ciphertext using keys and initialization vectors. The report compares the encryption results of ECB with CBC and OFB, highlighting the security vulnerabilities of ECB, particularly the risk of data leakage due to repetitive patterns in the encrypted image. It emphasizes the importance of CBC and OFB in enhancing data confidentiality and security through the introduction of randomness and the use of initialization vectors. The conclusion underscores the suitability of CBC and OFB for secure encryption, especially where data integrity and confidentiality are critical, offering a comprehensive understanding of these cipher techniques and their practical implications.

Running head: ANALYSIS OF CIPHERS TECHNIQUES
ANALYSIS OF CIPHERS TECHNIQUES
Name of the Student
Name of the University
Author Note
ANALYSIS OF CIPHERS TECHNIQUES
Name of the Student
Name of the University
Author Note
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

1ANALYSIS OF CIPHERS TECHNIQUES
Executive summary
This report has analysed various chipper encryption method. Three important cipher
encryption methods is analysed in this report, which includes ECB, CBC and OFB. Here in
this report an analysis has been done on the performance of this three different mode of
encryption an image has been considered and on this image, this three different encryption
mode has applied the result obtained in this process is analyzed to identify how is method
actually work. Electronic codebook chipper cryptography is a powerful tool to encrypt plain
text. This is the simplest form of encrypting a plain text with chipper cryptography. CBC and
OFB offers better encryption than ECB, which has some security issues as well as it, offers
basic level of encryption.
Executive summary
This report has analysed various chipper encryption method. Three important cipher
encryption methods is analysed in this report, which includes ECB, CBC and OFB. Here in
this report an analysis has been done on the performance of this three different mode of
encryption an image has been considered and on this image, this three different encryption
mode has applied the result obtained in this process is analyzed to identify how is method
actually work. Electronic codebook chipper cryptography is a powerful tool to encrypt plain
text. This is the simplest form of encrypting a plain text with chipper cryptography. CBC and
OFB offers better encryption than ECB, which has some security issues as well as it, offers
basic level of encryption.

2ANALYSIS OF CIPHERS TECHNIQUES
Table of Contents
Introduction:...............................................................................................................................3
Discussion:.................................................................................................................................3
ECB (Electronic CodeBook)..................................................................................................3
CBC (Cipher Block Chaining)...............................................................................................4
OFB (Output Feedback).........................................................................................................7
Comparison of encryption result between ECB, CFC and OFB:...........................................9
Reason not to consider ECB for encryption and chose CBC or OFB:.................................10
Conclusion:..............................................................................................................................11
References:...............................................................................................................................12
Table of Contents
Introduction:...............................................................................................................................3
Discussion:.................................................................................................................................3
ECB (Electronic CodeBook)..................................................................................................3
CBC (Cipher Block Chaining)...............................................................................................4
OFB (Output Feedback).........................................................................................................7
Comparison of encryption result between ECB, CFC and OFB:...........................................9
Reason not to consider ECB for encryption and chose CBC or OFB:.................................10
Conclusion:..............................................................................................................................11
References:...............................................................................................................................12
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

3ANALYSIS OF CIPHERS TECHNIQUES
Introduction:
In cryptography, cipher is best described as an algorithm that performs encryption and
decryption. It provides a detailed systematic procedure, which is required for encrypting and
decrypting information (Das & De, 2018). In this method of cryptography, original message
has information that is known as plain text. Now based on different cipher cryptography
mode, various techniques are applied for converting a plain text into encrypted text known as
cipher text. In order to encrypt the plain text, a secret key is considered which is known as
cipher key and encrypted message is known as cipher text.
Discussion:
ECB (Electronic CodeBook)
In this mode, a plain text is divided into blocks and these blocks are considered one at a time.
Only one key is considered for encrypting all of the blocks derived from the plaintext.
Therefore, for a specific cipher key, there is a cheaper text that is unique in nature and this is
applicable for each of the block of the plain text that is in a bit in size (Zhdanov, & Sokolov,
2016). So this system like a codebook where for every possible n-bit plain text there will be
an associated keypad text to which plaintext in identified due to similarity in encryption
approach. Hence, this encryption mode is known as electronic codebook. However some time
plaintext might be longer than b-bit and in this scenario, strategy is straight forward, just the
message have to be divided in b-bit Block and if required the last block is padded (Anand et
al., 2016). it's not only about encryption, but decryption also follow the simplicity just like
encryption process here also the same key is considered for decryption of the plaintext.
Introduction:
In cryptography, cipher is best described as an algorithm that performs encryption and
decryption. It provides a detailed systematic procedure, which is required for encrypting and
decrypting information (Das & De, 2018). In this method of cryptography, original message
has information that is known as plain text. Now based on different cipher cryptography
mode, various techniques are applied for converting a plain text into encrypted text known as
cipher text. In order to encrypt the plain text, a secret key is considered which is known as
cipher key and encrypted message is known as cipher text.
Discussion:
ECB (Electronic CodeBook)
In this mode, a plain text is divided into blocks and these blocks are considered one at a time.
Only one key is considered for encrypting all of the blocks derived from the plaintext.
Therefore, for a specific cipher key, there is a cheaper text that is unique in nature and this is
applicable for each of the block of the plain text that is in a bit in size (Zhdanov, & Sokolov,
2016). So this system like a codebook where for every possible n-bit plain text there will be
an associated keypad text to which plaintext in identified due to similarity in encryption
approach. Hence, this encryption mode is known as electronic codebook. However some time
plaintext might be longer than b-bit and in this scenario, strategy is straight forward, just the
message have to be divided in b-bit Block and if required the last block is padded (Anand et
al., 2016). it's not only about encryption, but decryption also follow the simplicity just like
encryption process here also the same key is considered for decryption of the plaintext.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

4ANALYSIS OF CIPHERS TECHNIQUES
Encryption in the ECB mode
Decryption in the ECB mode
CBC (Cipher Block Chaining)
Cipher block chaining is another popular mode of encryption however there is a significant
difference in terms of execution when compared to Electronic codebook that has been
discussed in this context. In electronic codebook repetitive plain text in the message resulted
in repeated cheaper text. However, in cheaper block chaining fast plaintext is converted into
ciphertext, which is then XORed with next block of plaintext (Li et al., 2018). Therefore, at
any given instance the process of driving a cheaper text for plaintext depends on the
processing of the previous plaintext till that plaintext in consideration (Hemamalini et al.,
2016). The same key is considered for repeated in the text it does not provide the same output
as this was the case with electronic codebook. Therefore it is not possible to differentiate
repetitive plaintext from actual message due to the high level of encryption.
Encryption in the ECB mode
Decryption in the ECB mode
CBC (Cipher Block Chaining)
Cipher block chaining is another popular mode of encryption however there is a significant
difference in terms of execution when compared to Electronic codebook that has been
discussed in this context. In electronic codebook repetitive plain text in the message resulted
in repeated cheaper text. However, in cheaper block chaining fast plaintext is converted into
ciphertext, which is then XORed with next block of plaintext (Li et al., 2018). Therefore, at
any given instance the process of driving a cheaper text for plaintext depends on the
processing of the previous plaintext till that plaintext in consideration (Hemamalini et al.,
2016). The same key is considered for repeated in the text it does not provide the same output
as this was the case with electronic codebook. Therefore it is not possible to differentiate
repetitive plaintext from actual message due to the high level of encryption.

5ANALYSIS OF CIPHERS TECHNIQUES
In order to produce the first block of text initialisation vector integrated with a plain text and
operation is performed between encryption key and n bit plain text. Ciphertext produced in
this way is then fed to next plain text in sequence this process is repeated. Decryption in this
process is bit complicated output produced through the decryption algorithm is exhausted
with initialisation vector this is done to recover fast plaintext initialisation vector has the
same sizes the block.
When initialisation factor is considered in this process, it is important to notice that the
initialisation vector has to be known to both sender and receiver. if the sender doesn't have
that initialisation vector it is not possible to decrypt the encrypted messages produced through
CBC. However, it is also important to note that the initialisation vector has to be kept a secret
from any third party. Otherwise, the security of the system will be compromised. If the third
party knows the initialization vector, they will be able to decrypt the message and derive
important information that is assumed to be secret (Kumar et al., 2016). Due to this,
confidentiality and valuation of data initialisation vector in its first place should be made
secured enough so that others do not know it before the key is generated. In order to to ensure
maximum security, it is suggested that initialisation vector is protected from illegal access
and it should be difficult to modify the initialisation vector without proper authorisation this
is possible to implement if initialisation vector is sent through ECB encryption.
Which CBC it is possible to encrypt a message that is not the same size as the size of
ciphertext. Therefore CBC might be considered for increasing confidentiality and authenticity
of data on the message that is being encrypted with this process.
In order to produce the first block of text initialisation vector integrated with a plain text and
operation is performed between encryption key and n bit plain text. Ciphertext produced in
this way is then fed to next plain text in sequence this process is repeated. Decryption in this
process is bit complicated output produced through the decryption algorithm is exhausted
with initialisation vector this is done to recover fast plaintext initialisation vector has the
same sizes the block.
When initialisation factor is considered in this process, it is important to notice that the
initialisation vector has to be known to both sender and receiver. if the sender doesn't have
that initialisation vector it is not possible to decrypt the encrypted messages produced through
CBC. However, it is also important to note that the initialisation vector has to be kept a secret
from any third party. Otherwise, the security of the system will be compromised. If the third
party knows the initialization vector, they will be able to decrypt the message and derive
important information that is assumed to be secret (Kumar et al., 2016). Due to this,
confidentiality and valuation of data initialisation vector in its first place should be made
secured enough so that others do not know it before the key is generated. In order to to ensure
maximum security, it is suggested that initialisation vector is protected from illegal access
and it should be difficult to modify the initialisation vector without proper authorisation this
is possible to implement if initialisation vector is sent through ECB encryption.
Which CBC it is possible to encrypt a message that is not the same size as the size of
ciphertext. Therefore CBC might be considered for increasing confidentiality and authenticity
of data on the message that is being encrypted with this process.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
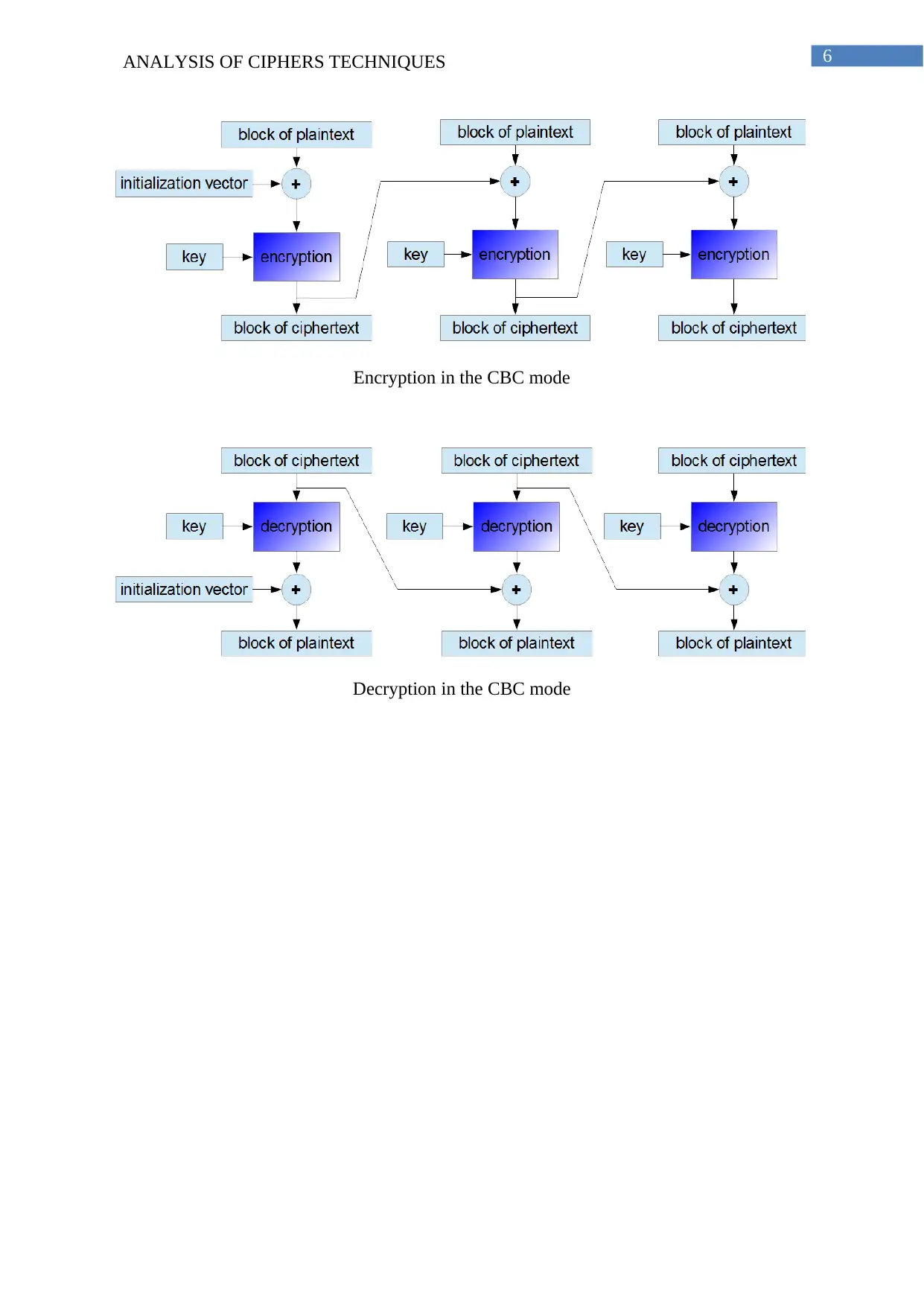
6ANALYSIS OF CIPHERS TECHNIQUES
Encryption in the CBC mode
Decryption in the CBC mode
Encryption in the CBC mode
Decryption in the CBC mode
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
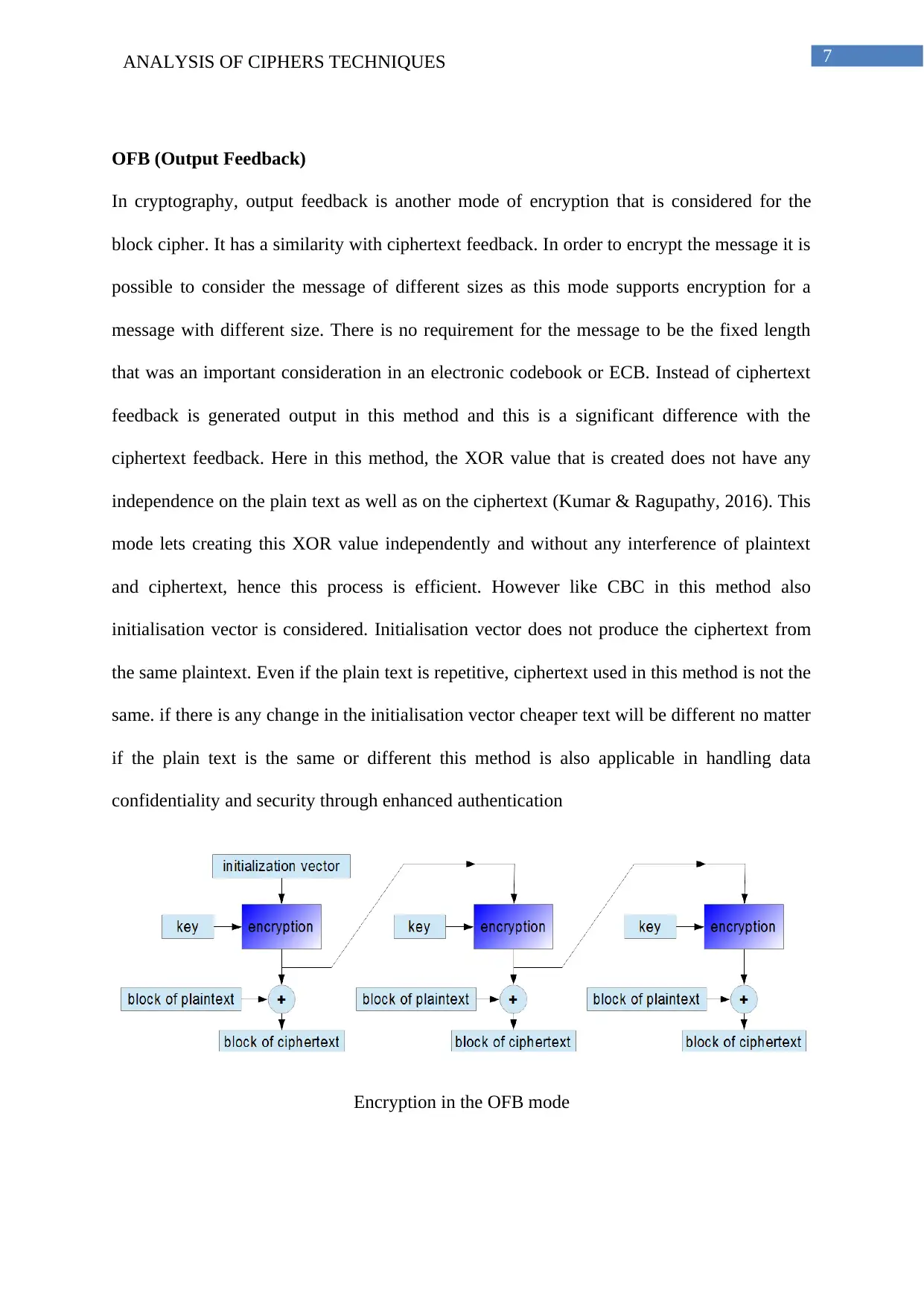
7ANALYSIS OF CIPHERS TECHNIQUES
OFB (Output Feedback)
In cryptography, output feedback is another mode of encryption that is considered for the
block cipher. It has a similarity with ciphertext feedback. In order to encrypt the message it is
possible to consider the message of different sizes as this mode supports encryption for a
message with different size. There is no requirement for the message to be the fixed length
that was an important consideration in an electronic codebook or ECB. Instead of ciphertext
feedback is generated output in this method and this is a significant difference with the
ciphertext feedback. Here in this method, the XOR value that is created does not have any
independence on the plain text as well as on the ciphertext (Kumar & Ragupathy, 2016). This
mode lets creating this XOR value independently and without any interference of plaintext
and ciphertext, hence this process is efficient. However like CBC in this method also
initialisation vector is considered. Initialisation vector does not produce the ciphertext from
the same plaintext. Even if the plain text is repetitive, ciphertext used in this method is not the
same. if there is any change in the initialisation vector cheaper text will be different no matter
if the plain text is the same or different this method is also applicable in handling data
confidentiality and security through enhanced authentication
Encryption in the OFB mode
OFB (Output Feedback)
In cryptography, output feedback is another mode of encryption that is considered for the
block cipher. It has a similarity with ciphertext feedback. In order to encrypt the message it is
possible to consider the message of different sizes as this mode supports encryption for a
message with different size. There is no requirement for the message to be the fixed length
that was an important consideration in an electronic codebook or ECB. Instead of ciphertext
feedback is generated output in this method and this is a significant difference with the
ciphertext feedback. Here in this method, the XOR value that is created does not have any
independence on the plain text as well as on the ciphertext (Kumar & Ragupathy, 2016). This
mode lets creating this XOR value independently and without any interference of plaintext
and ciphertext, hence this process is efficient. However like CBC in this method also
initialisation vector is considered. Initialisation vector does not produce the ciphertext from
the same plaintext. Even if the plain text is repetitive, ciphertext used in this method is not the
same. if there is any change in the initialisation vector cheaper text will be different no matter
if the plain text is the same or different this method is also applicable in handling data
confidentiality and security through enhanced authentication
Encryption in the OFB mode
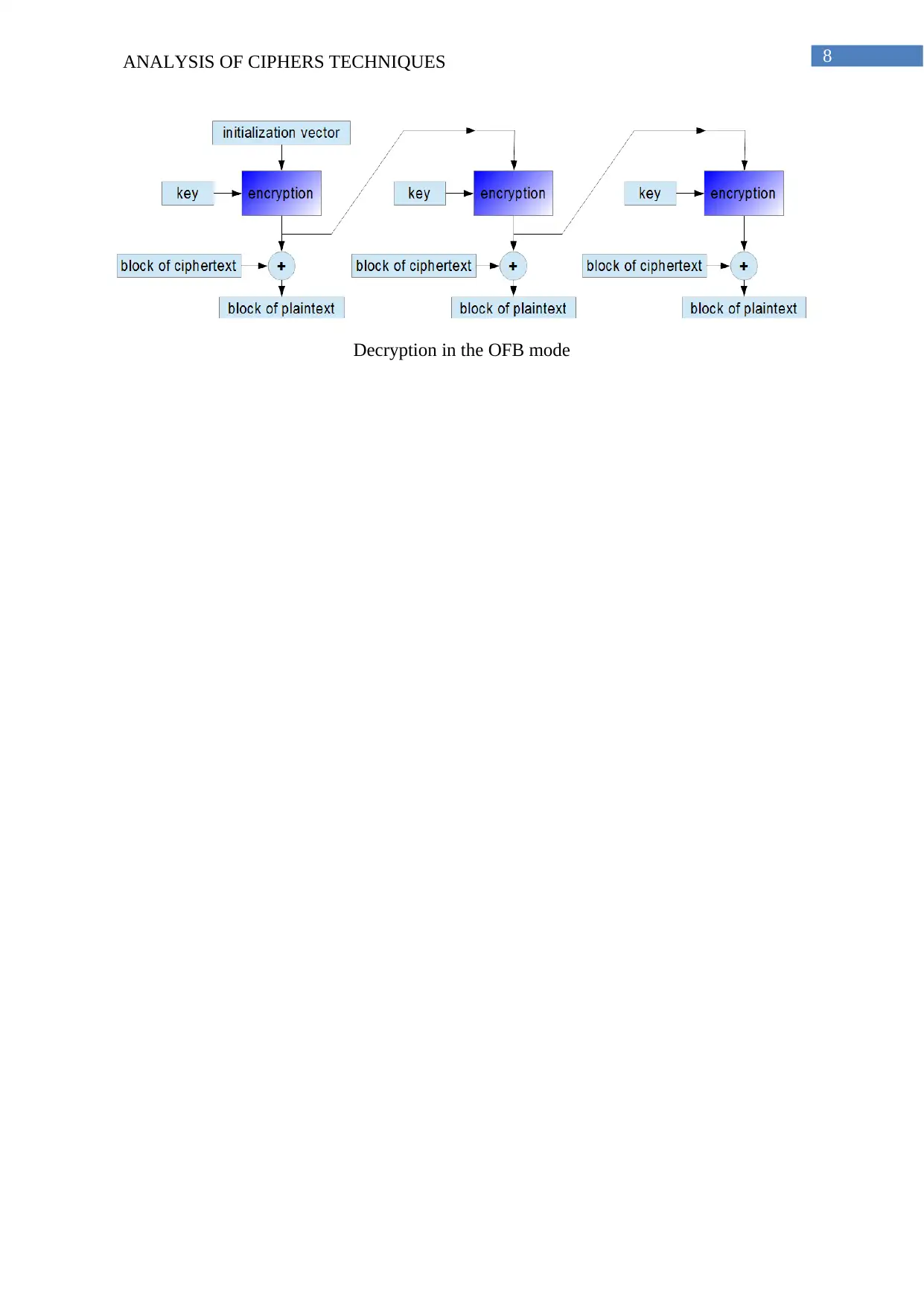
8ANALYSIS OF CIPHERS TECHNIQUES
Decryption in the OFB mode
Decryption in the OFB mode
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
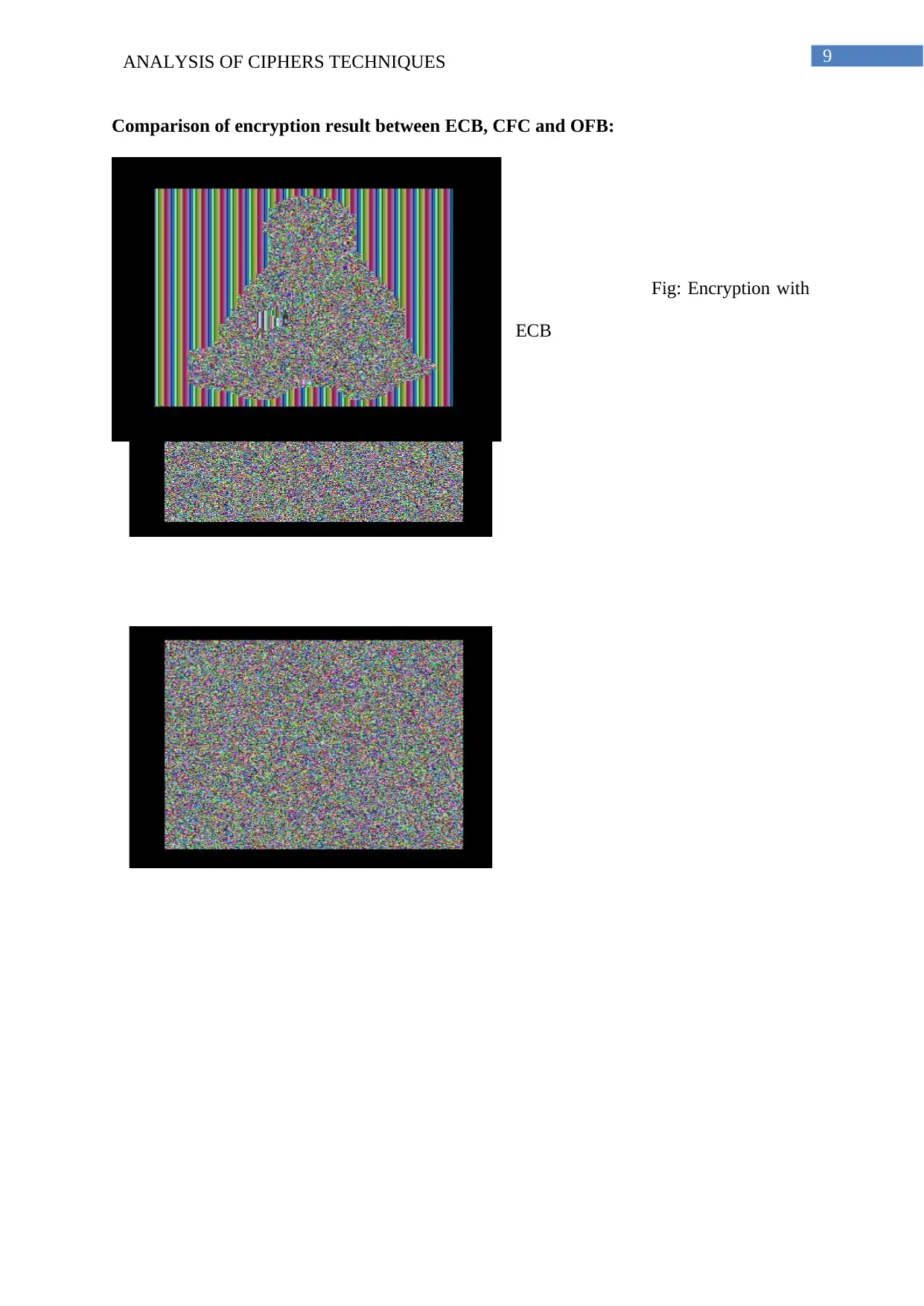
9ANALYSIS OF CIPHERS TECHNIQUES
Comparison of encryption result between ECB, CFC and OFB:
Fig: Encryption with
ECB
Comparison of encryption result between ECB, CFC and OFB:
Fig: Encryption with
ECB
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

10ANALYSIS OF CIPHERS TECHNIQUES
When ECB is applied to the image, it is seen that although some important details like colour,
shape has modified a little bit especially the colour information is not visible from the image.
however if analyzed in detail, it has seen that section of the image which has repetitive
structures has same set of characteristics in the encrypted image which make prediction for
the original image easier and this is what needs to be avoided in encryption. However when
the other two encryption mode such as CBC and OFB It is seen that introduction of
initialization vector along with mechanism considered in ECB for converting plain text into
encrypted text or ciphertext.
Reason not to consider ECB for encryption and chose CBC or OFB:
In the encrypted image, a similar portion of the image has resulted in similar encryption and
has similar details. The reason behind this is that in ECB same encryption key is considered
for all the blocks of the plaintext that is derived from the main message. Therefore,
application on the same plaintext has resulted in the same ciphertext therefore in ECB there is
a chance of data leak as even after encryption prediction for original data is not so difficult. It
requires a trial and error method for successfully identifying the original data pattern from
encrypted data (Liu et al., 2015). Hackers try to identify similarities in data patterns as similar
ciphertext belongs to the same plaintext, which means prediction for one ciphertext will help
in successful identification of plaintext, which will help in interpreting the original message
(Kumar & Ragupathy, 2016). This is why ECB is not considered for encryption especially
where data security, Data integrity and data confidentiality plays a significant role and this
requires an effective encryption technology to ensure that data is not interpreted easily so that
its confidentiality and authenticity is maintained which ensures data security.
However, application of initialization vector has added an extra layer of randomness with the
encrypted image hence from the encrypted image in CBC and OFB. It is not easy to predict
the actual image and this is what encryption is all about, to hide specific details that are
When ECB is applied to the image, it is seen that although some important details like colour,
shape has modified a little bit especially the colour information is not visible from the image.
however if analyzed in detail, it has seen that section of the image which has repetitive
structures has same set of characteristics in the encrypted image which make prediction for
the original image easier and this is what needs to be avoided in encryption. However when
the other two encryption mode such as CBC and OFB It is seen that introduction of
initialization vector along with mechanism considered in ECB for converting plain text into
encrypted text or ciphertext.
Reason not to consider ECB for encryption and chose CBC or OFB:
In the encrypted image, a similar portion of the image has resulted in similar encryption and
has similar details. The reason behind this is that in ECB same encryption key is considered
for all the blocks of the plaintext that is derived from the main message. Therefore,
application on the same plaintext has resulted in the same ciphertext therefore in ECB there is
a chance of data leak as even after encryption prediction for original data is not so difficult. It
requires a trial and error method for successfully identifying the original data pattern from
encrypted data (Liu et al., 2015). Hackers try to identify similarities in data patterns as similar
ciphertext belongs to the same plaintext, which means prediction for one ciphertext will help
in successful identification of plaintext, which will help in interpreting the original message
(Kumar & Ragupathy, 2016). This is why ECB is not considered for encryption especially
where data security, Data integrity and data confidentiality plays a significant role and this
requires an effective encryption technology to ensure that data is not interpreted easily so that
its confidentiality and authenticity is maintained which ensures data security.
However, application of initialization vector has added an extra layer of randomness with the
encrypted image hence from the encrypted image in CBC and OFB. It is not easy to predict
the actual image and this is what encryption is all about, to hide specific details that are

11ANALYSIS OF CIPHERS TECHNIQUES
important so that it is not easy to access the information without proper authorization needed
for that (Buchanan, 2017). Hence, this mode of encryption is preferred over ECB, which is
very simple and less reliable for encryption.
Conclusion:
While discussing characteristics of ECB, it is identified that it is suitable for a small amount
of data, which might include an encryption key. one important attractive that define this
method is that if the given message has repetitive plaintext that is n-bit of size, then that n-bit
plain text to appear as many times as it appears in the message. Hence, the ciphertext that is
derived from the plaintext is somehow identical in terms of ciphertext. Therefore
sophisticated encryption mode is required and hence CBC and OFB is an important choice in
this context, which increases complexity of encryption with introduction of randomness
through the application of initialization vector, and it increases security of the encryption
techniques.
important so that it is not easy to access the information without proper authorization needed
for that (Buchanan, 2017). Hence, this mode of encryption is preferred over ECB, which is
very simple and less reliable for encryption.
Conclusion:
While discussing characteristics of ECB, it is identified that it is suitable for a small amount
of data, which might include an encryption key. one important attractive that define this
method is that if the given message has repetitive plaintext that is n-bit of size, then that n-bit
plain text to appear as many times as it appears in the message. Hence, the ciphertext that is
derived from the plaintext is somehow identical in terms of ciphertext. Therefore
sophisticated encryption mode is required and hence CBC and OFB is an important choice in
this context, which increases complexity of encryption with introduction of randomness
through the application of initialization vector, and it increases security of the encryption
techniques.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 14
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





