Comprehensive Analysis of Nessus and Nmap for Network Security
VerifiedAdded on 2024/05/29
|17
|1294
|337
Report
AI Summary
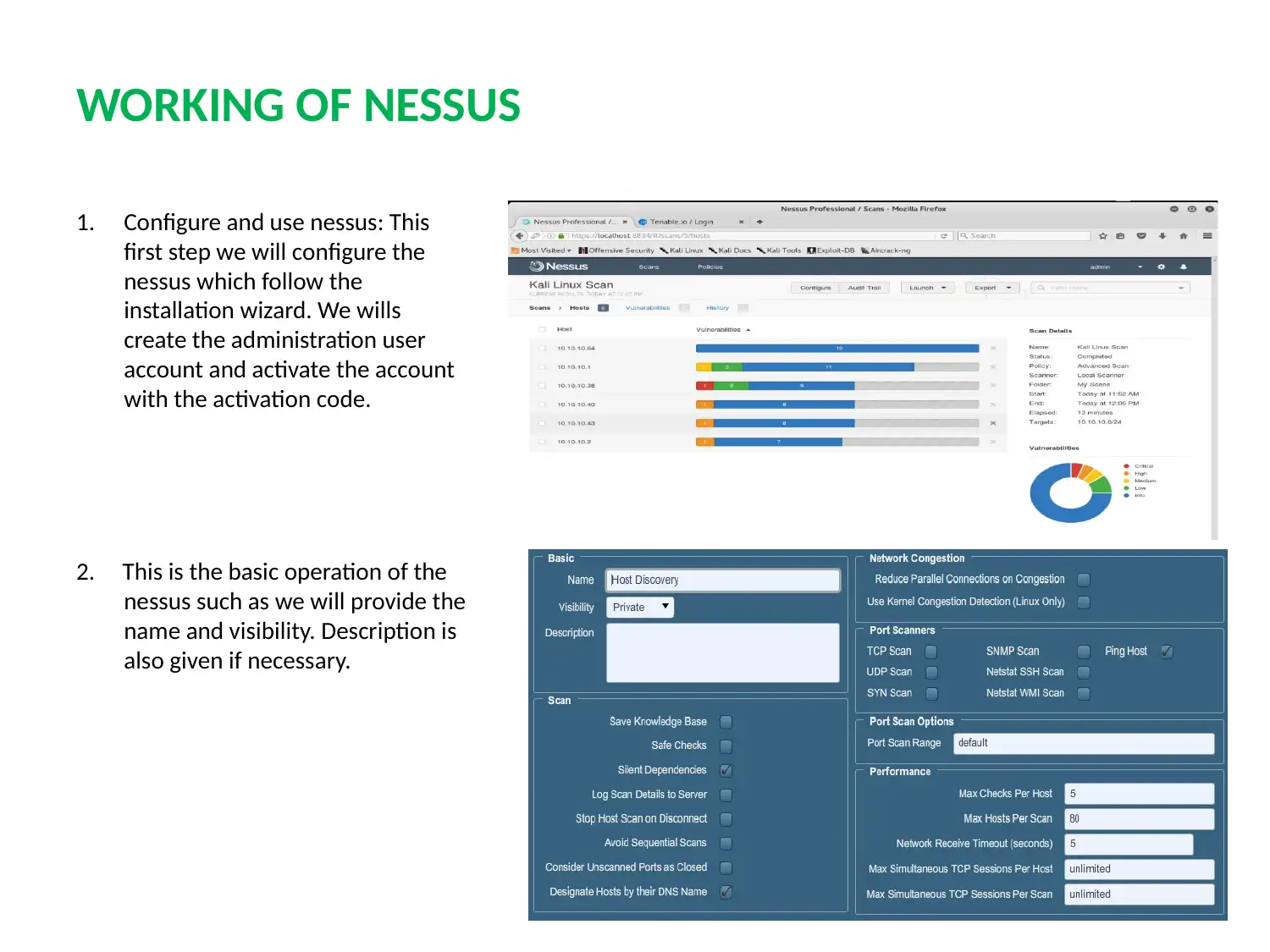
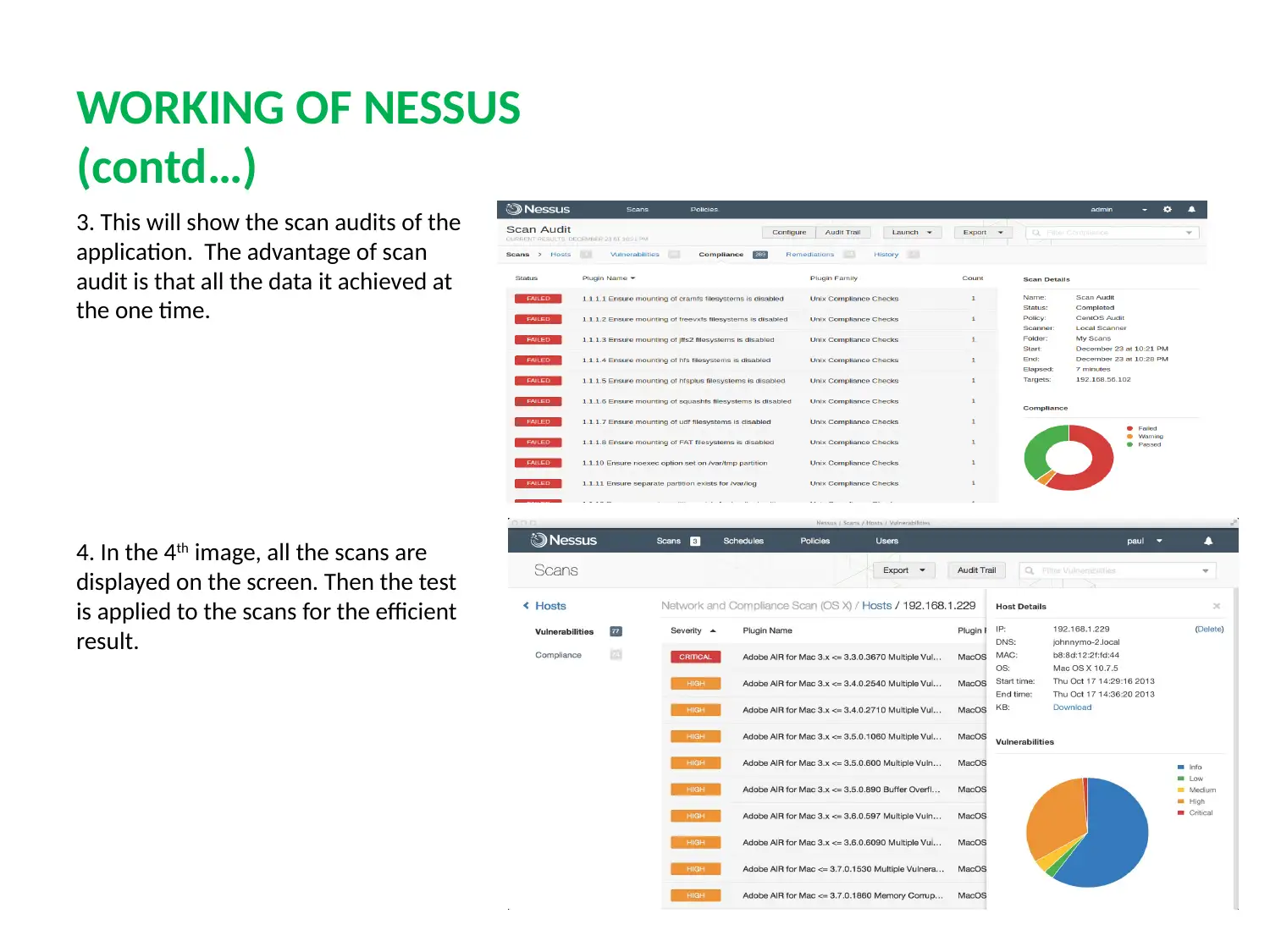
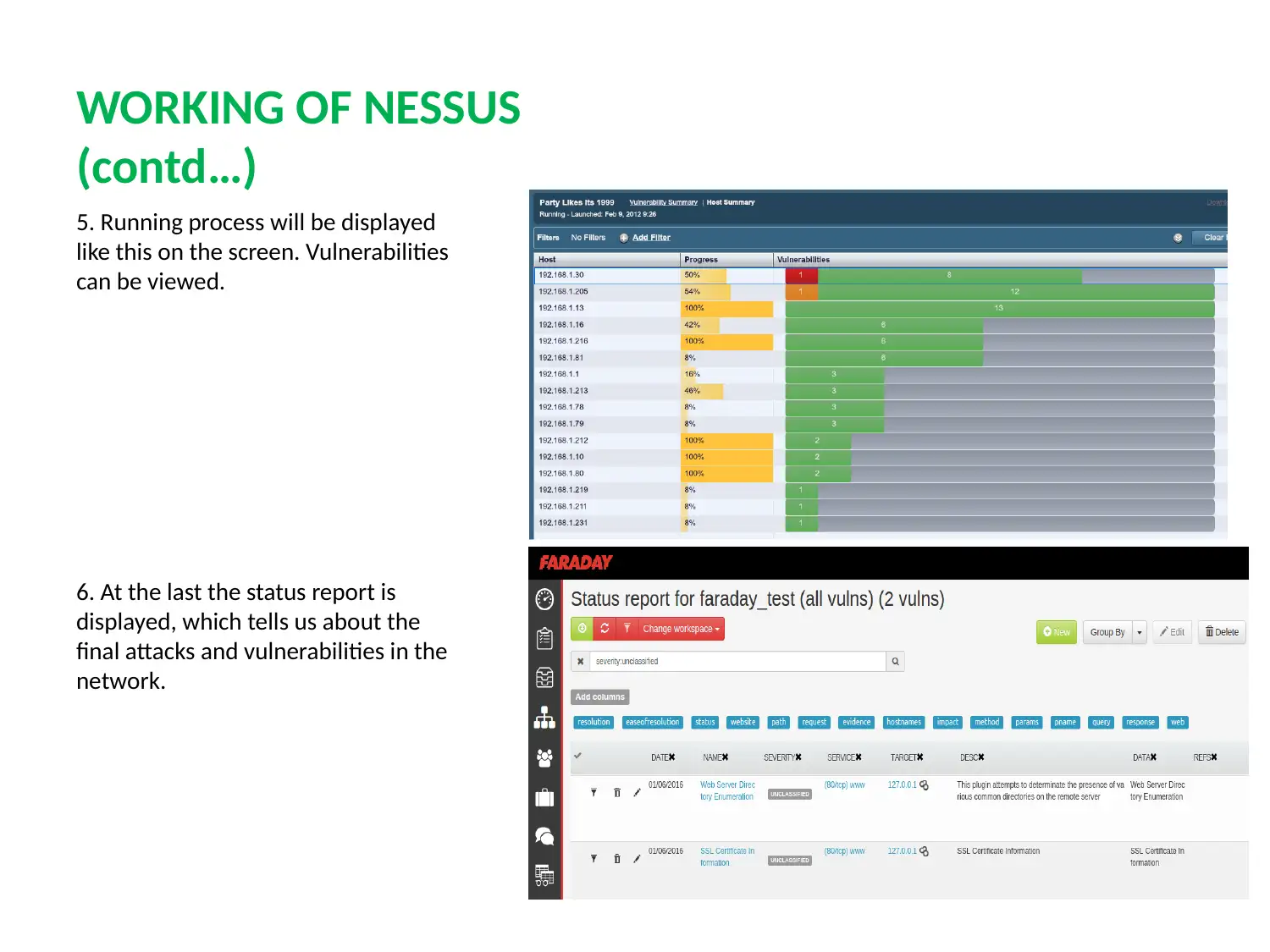
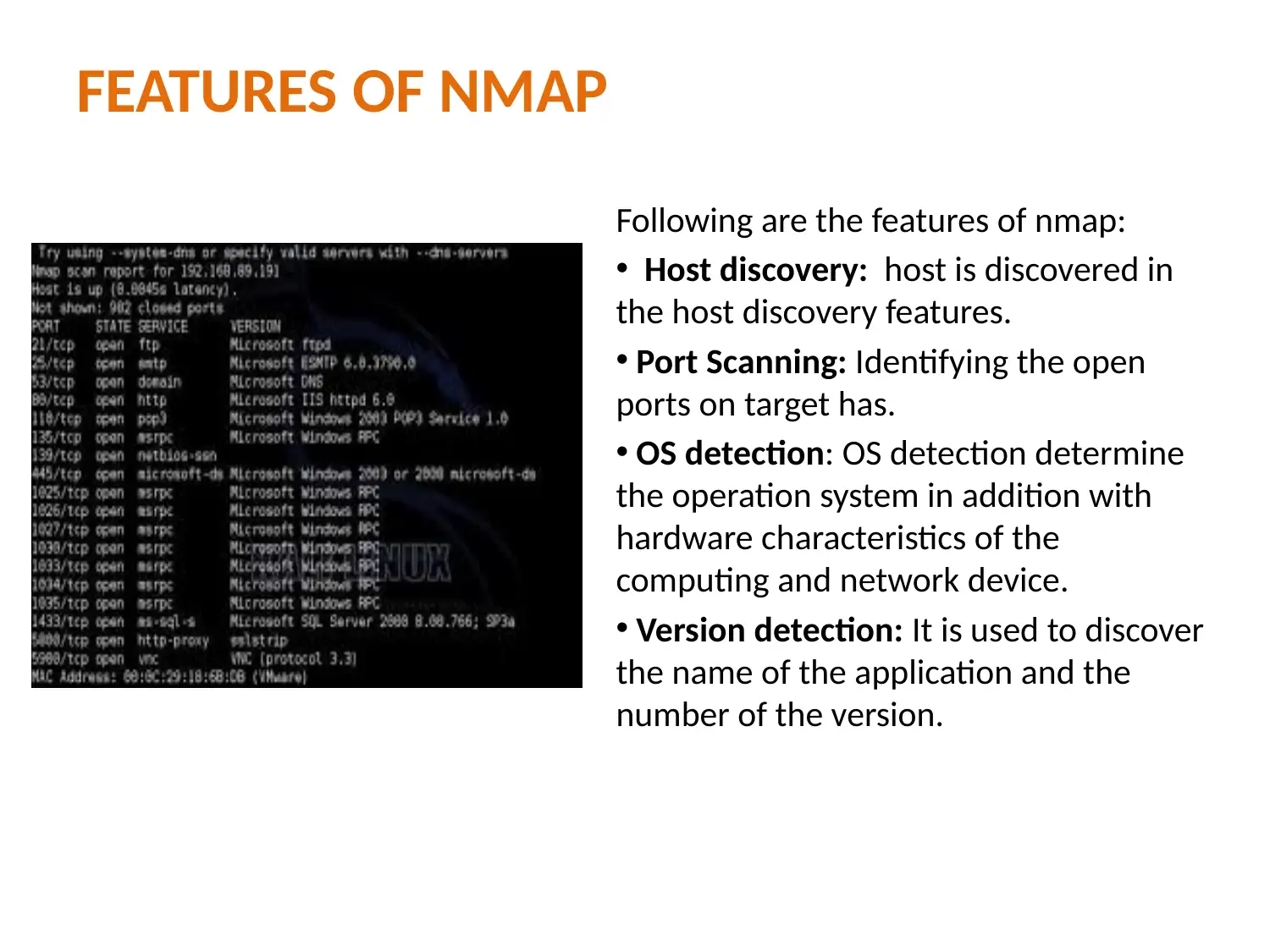
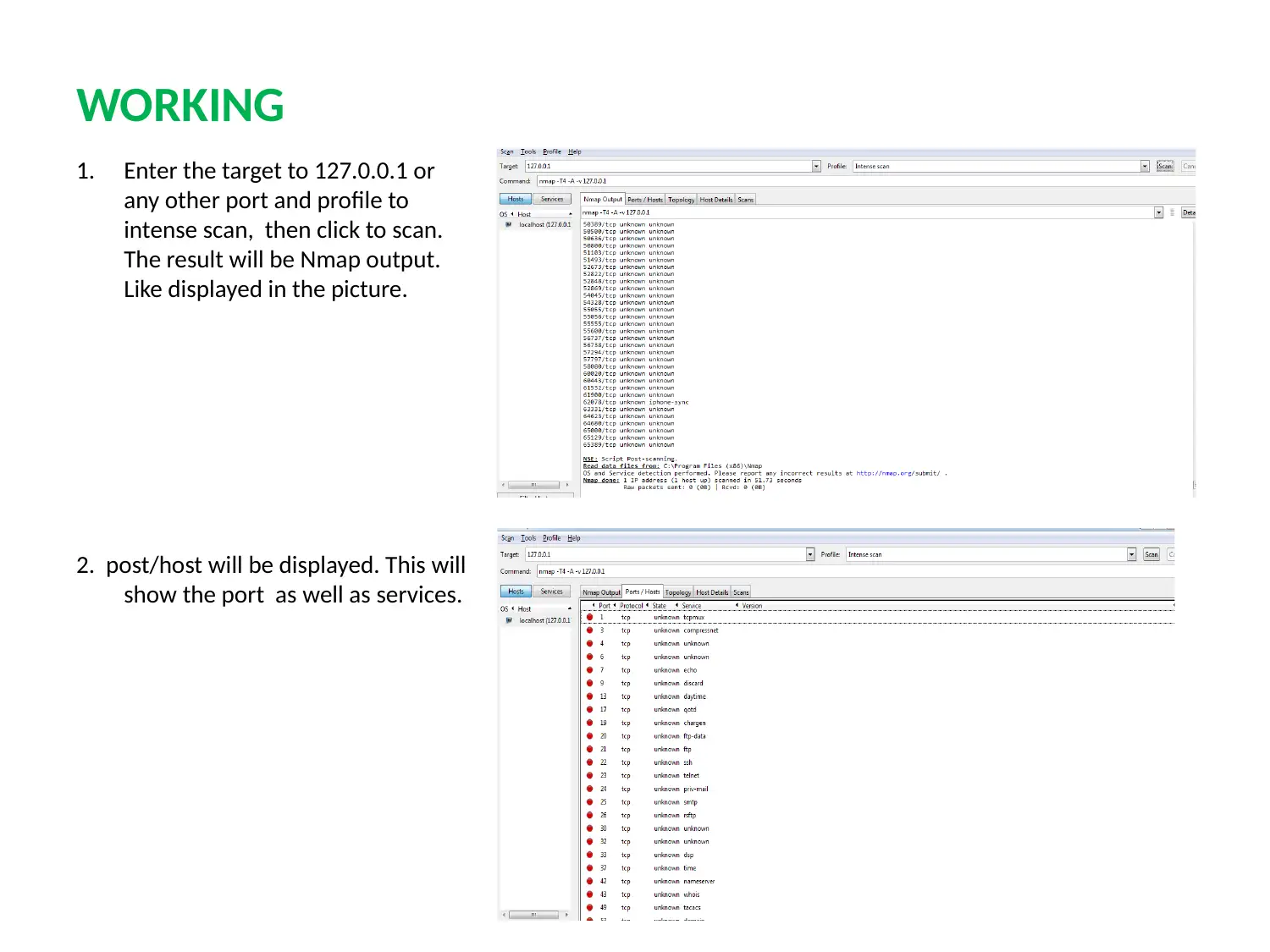
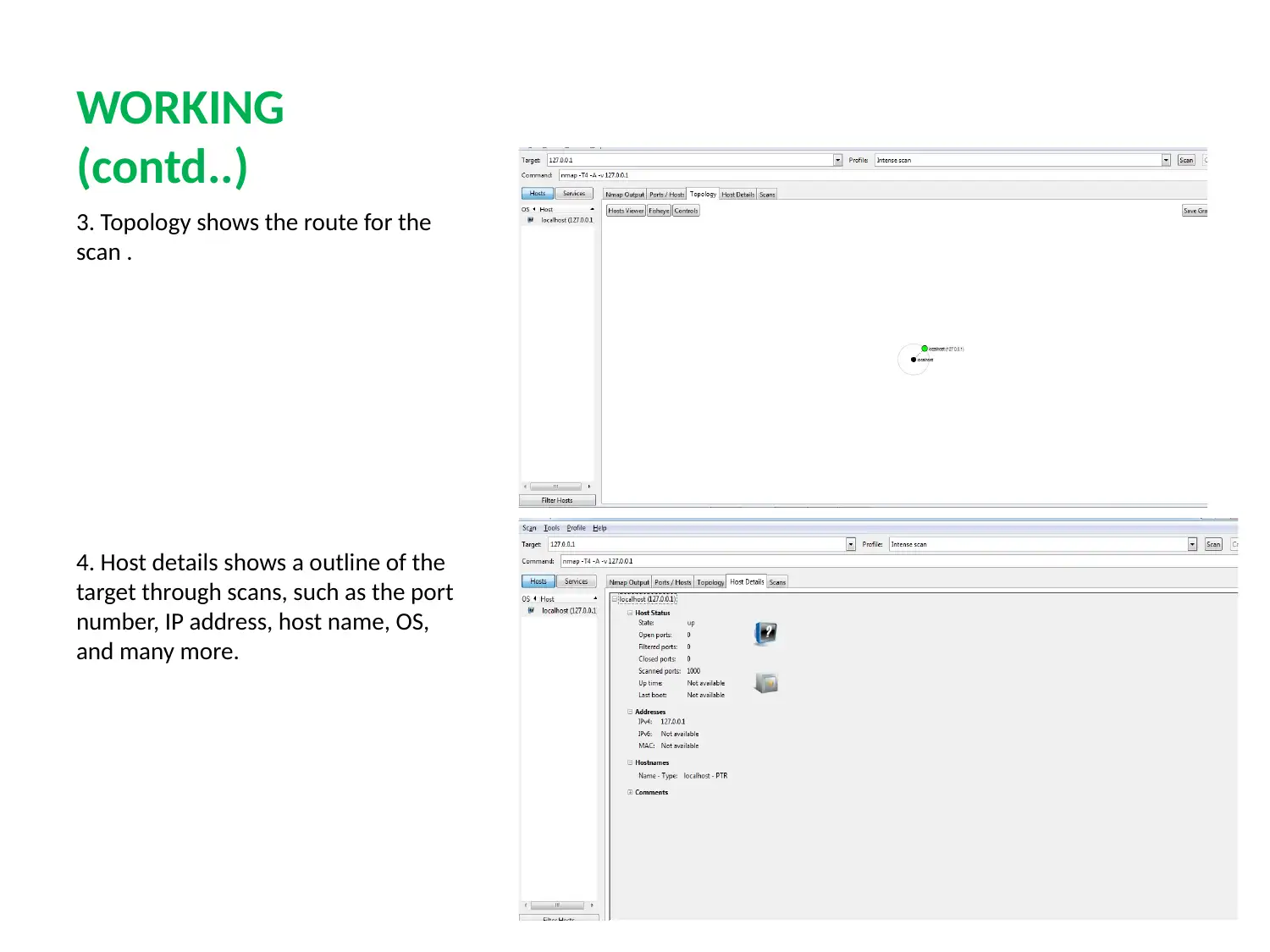
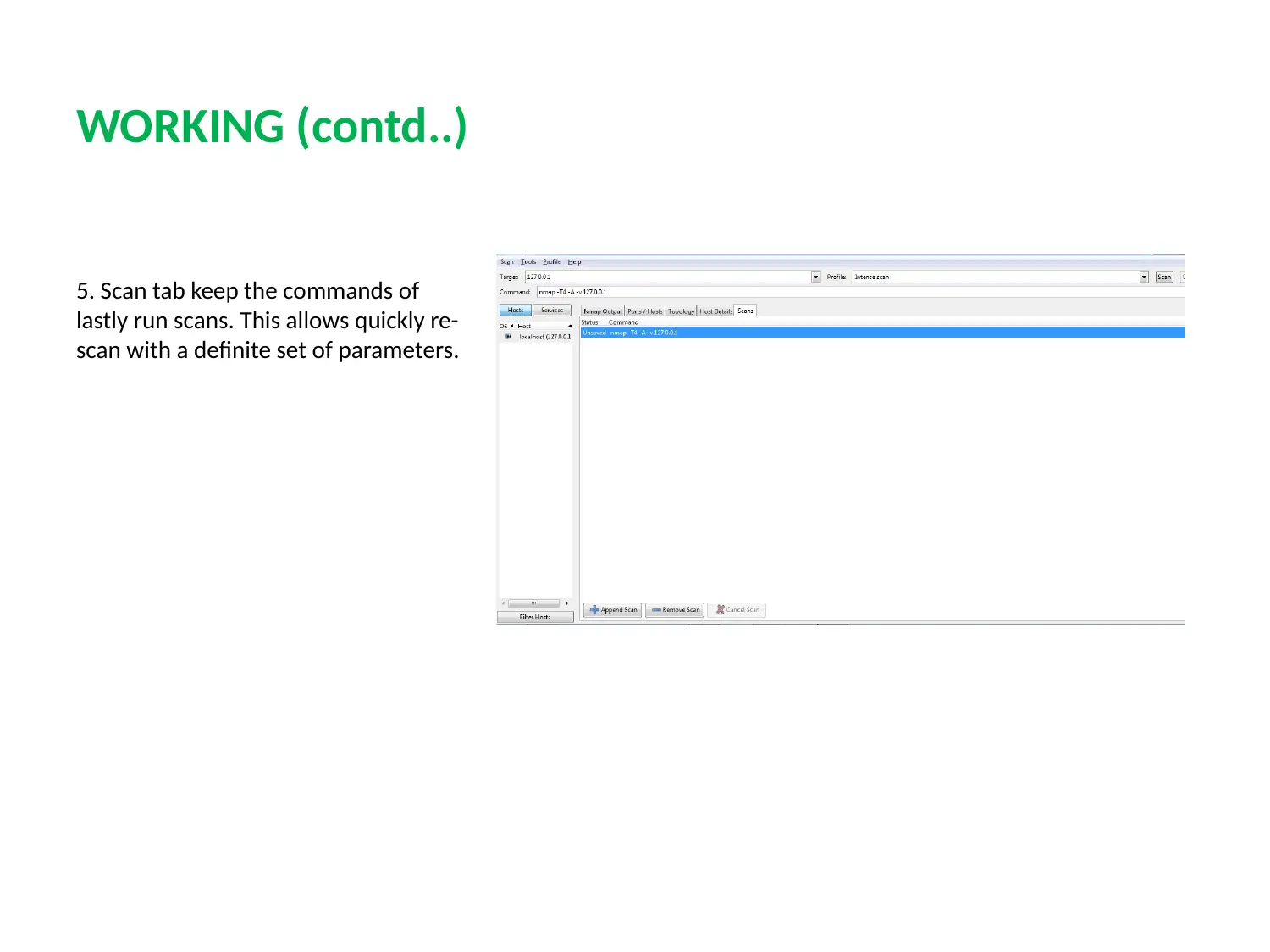
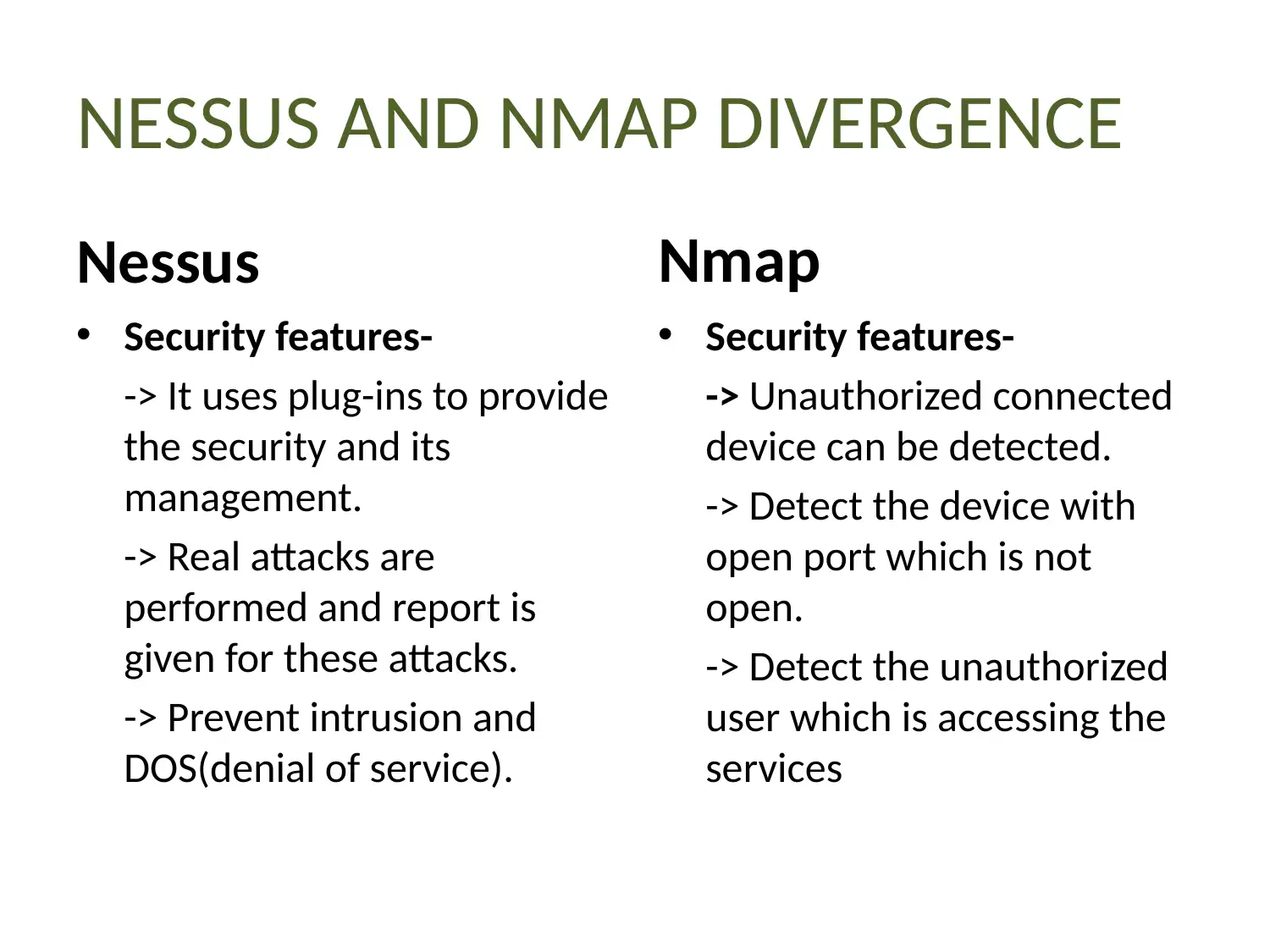
This report provides a detailed analysis of two prominent network security tools, Nessus and Nmap. Nessus, a proprietary vulnerability scanner, is explored in terms of its features, working mechanism, and application in identifying misconfigurations, common passwords, and potential denial-of-service vulnerabilities. Nmap, a free security scanner used for host and service discovery, is examined for its host discovery, port scanning, OS detection, and version detection capabilities. The report contrasts the security features, detection times, and ease of use of both tools. A case scenario involving an educational institute (UVW) highlights the selection of Nessus based on its ability to provide multiple services, efficient attack management through plugins, and periodic auditing. The conclusion emphasizes the essential role of vulnerability scanners in network security and the ongoing competition between Nessus and Nmap in providing robust security solutions. Finally, the report mentions that these tools help to protect weak components from known attacks.
1 out of 17










![[object Object]](/_next/static/media/star-bottom.7253800d.svg)