Forensic Analysis of Android and iOS Devices: Techniques and Tools
VerifiedAdded on 2019/09/23
|15
|2125
|438
Homework Assignment
AI Summary
This assignment delves into mobile forensics, covering techniques for acquiring and analyzing data from Android and iOS devices. It begins with a discussion of screen lock bypass techniques on Android, including the use of Safe Mode and factory reset, and explores scenarios where these techniques might be useful for data gathering. The assignment then examines rooting Android devices and jailbreaking iOS devices, detailing the data available before and after these procedures, along with associated legal issues. It includes practical exercises using ADB commands, such as pulling application data from an un-rooted Android device and interpreting the results. The assignment further explains manual, logical, and physical extraction methods, detailing the circumstances in which each technique is applicable. Finally, it addresses the best acquisition techniques for iOS devices, including normal, DFU, and recovery modes, and discusses the limitations of these methods. The assignment concludes with the use of ADB commands like dumpsys and batterystats to gather system information and analyze battery usage data.

1. Please discuss the screen lock by passing techniques in Android devices. Our discussion should
include a scenario where these techniques might be useful to gather data out of the mobile device.
Explanation:
Using Safe Mode to Unlock Android phone pattern lock:
It’s a simple and effective solution to know how to unlock pattern on Android device. This solution will
only work with the third-party lock screen apps. If we are using our phone’s built in lock feature, then it
might not work. Restarting our phone in Safe Mode, we can easily move-past is pattern lock without any
trouble.
Below are the steps:-
1. Long press the Power button to get the Power menu on screen.
2. Tap and hold the “Power off” option.
3. One pop-up message will be displayed as shown in following image. Agree and reboot phone in Safe
Mode.
include a scenario where these techniques might be useful to gather data out of the mobile device.
Explanation:
Using Safe Mode to Unlock Android phone pattern lock:
It’s a simple and effective solution to know how to unlock pattern on Android device. This solution will
only work with the third-party lock screen apps. If we are using our phone’s built in lock feature, then it
might not work. Restarting our phone in Safe Mode, we can easily move-past is pattern lock without any
trouble.
Below are the steps:-
1. Long press the Power button to get the Power menu on screen.
2. Tap and hold the “Power off” option.
3. One pop-up message will be displayed as shown in following image. Agree and reboot phone in Safe
Mode.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

4. When device is rebooted in Safe Mode then the third-party lock screen will automatically be disabled.
Afterwards also we can go to device’s Settings -> Apps, and there remove the third-party application.
Unlocking pattern lock with factory reset
Consider this as our last option as it will wipe all the data and saved settings on our device permanently.
As the name suggests, our device would be restored to its original settings..
Let us now learn how to unlock pattern by performing a factory reset. For that we need to perform these
steps:
1. Enter the Recovery Mode on device. For this Press the Home key + Power button + Volume Up key at
a time.
2. The above key combination may be different for different android device.
3. Use the Volume Up and Down key to traverse and the Power/Home button to pick and choose.
Afterwards also we can go to device’s Settings -> Apps, and there remove the third-party application.
Unlocking pattern lock with factory reset
Consider this as our last option as it will wipe all the data and saved settings on our device permanently.
As the name suggests, our device would be restored to its original settings..
Let us now learn how to unlock pattern by performing a factory reset. For that we need to perform these
steps:
1. Enter the Recovery Mode on device. For this Press the Home key + Power button + Volume Up key at
a time.
2. The above key combination may be different for different android device.
3. Use the Volume Up and Down key to traverse and the Power/Home button to pick and choose.

4. Choose the wipe data/factory reset option to implement pattern unlock.
5. Confirm your choice so as to factory reset your device.
6. Wait for a while as your phone will execute the needed operations.
7. Now you can choose to reboot your phone and access it without any lock screen.
5. Confirm your choice so as to factory reset your device.
6. Wait for a while as your phone will execute the needed operations.
7. Now you can choose to reboot your phone and access it without any lock screen.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

Q-2:- Please discuss rooting an Android device and jail broken an iOS device with respect to what
data is available before and after these procedures. In our discussion please also briefly discuss the
legal issues performing those procedures.
Ans :- Rooting is a method which allows all smartphone users to run the Android operating system to
achieve all restricted access (Also called as Root Access).
Linux is used in Android operating systems. Rooting gives the access to executive permissions as on
Linux or Unix-based operating system such as Mac Operating System
Device is rooted to overcome the limitations which are placed by manufacturers. Thus rooting allows
switching system apps and their settings, running certain apps that need an administrative permissions etc.
Rooting a device can also provide the entire new version of operating system, generally to downgrade or
upgrade the version of software.
Pros:-
Rooting device include the possibility for complete control over the look and feel of the device. It gives
access to all system files.
Full application control, including backup, restore, or edit applications, or to remove bloat ware that
usually is pre-installed by manufacturers.
Custom programmed system-level processes through the use of third-party applications.
Full control of the kernel, like CPU, GPU etc.
Installation of Custom ROM for better control over device and access full potential of it.
How to easily root an Android device
The KingoRoot application is not available on playstore. That is why we need to download KingoRoot
APK and install it by allowing third-party app access.
data is available before and after these procedures. In our discussion please also briefly discuss the
legal issues performing those procedures.
Ans :- Rooting is a method which allows all smartphone users to run the Android operating system to
achieve all restricted access (Also called as Root Access).
Linux is used in Android operating systems. Rooting gives the access to executive permissions as on
Linux or Unix-based operating system such as Mac Operating System
Device is rooted to overcome the limitations which are placed by manufacturers. Thus rooting allows
switching system apps and their settings, running certain apps that need an administrative permissions etc.
Rooting a device can also provide the entire new version of operating system, generally to downgrade or
upgrade the version of software.
Pros:-
Rooting device include the possibility for complete control over the look and feel of the device. It gives
access to all system files.
Full application control, including backup, restore, or edit applications, or to remove bloat ware that
usually is pre-installed by manufacturers.
Custom programmed system-level processes through the use of third-party applications.
Full control of the kernel, like CPU, GPU etc.
Installation of Custom ROM for better control over device and access full potential of it.
How to easily root an Android device
The KingoRoot application is not available on playstore. That is why we need to download KingoRoot
APK and install it by allowing third-party app access.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
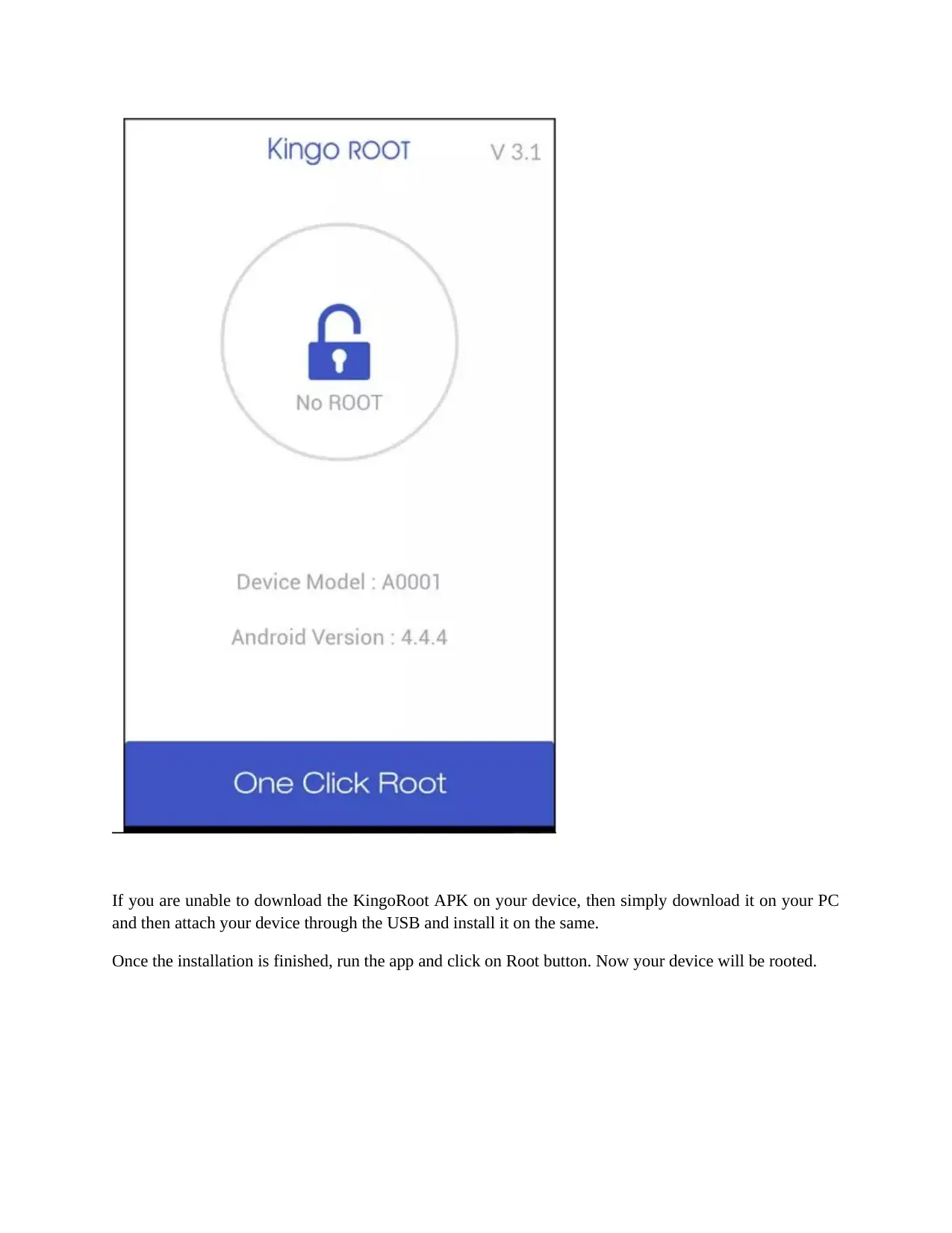
If you are unable to download the KingoRoot APK on your device, then simply download it on your PC
and then attach your device through the USB and install it on the same.
Once the installation is finished, run the app and click on Root button. Now your device will be rooted.
and then attach your device through the USB and install it on the same.
Once the installation is finished, run the app and click on Root button. Now your device will be rooted.
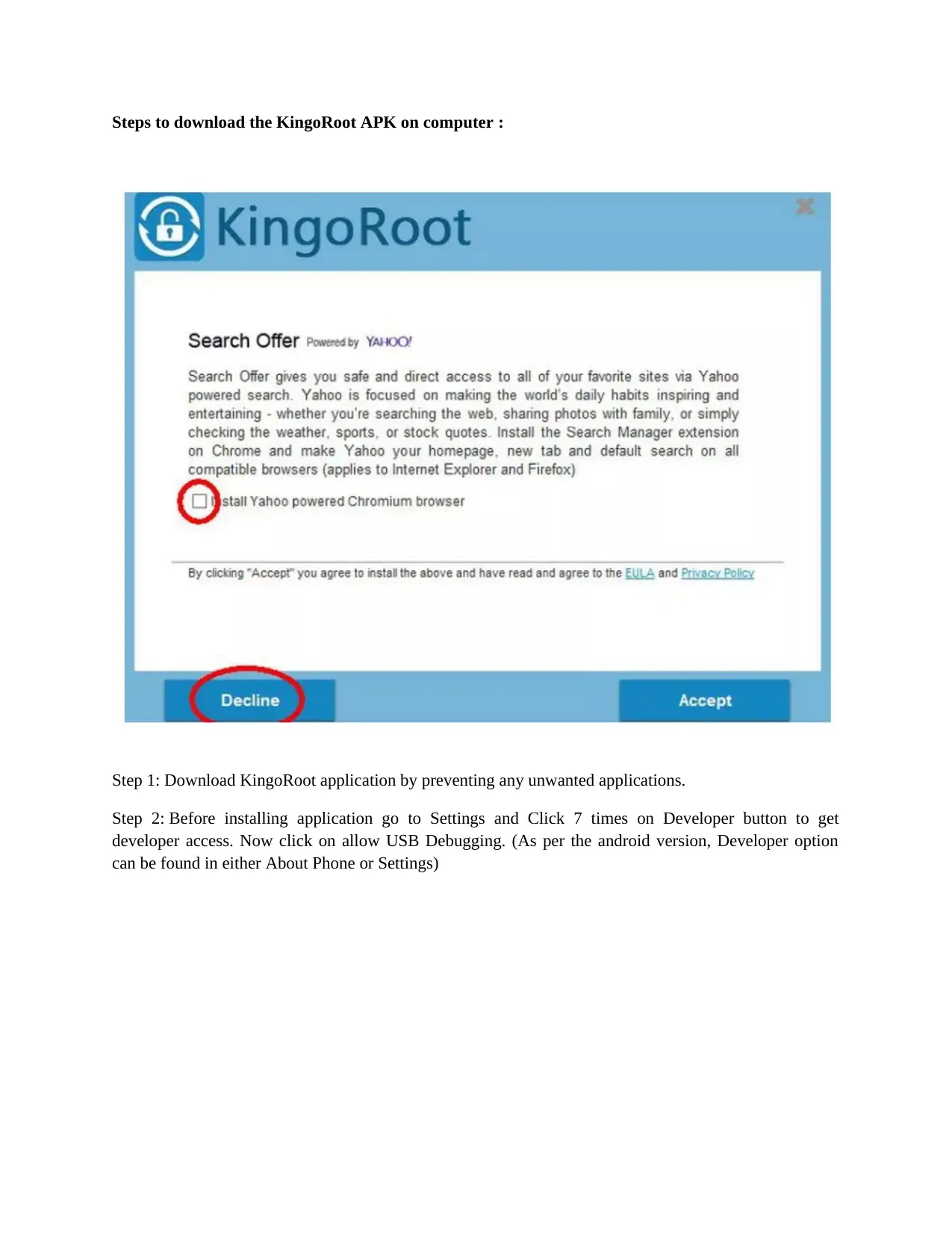
Steps to download the KingoRoot APK on computer :
Step 1: Download KingoRoot application by preventing any unwanted applications.
Step 2: Before installing application go to Settings and Click 7 times on Developer button to get
developer access. Now click on allow USB Debugging. (As per the android version, Developer option
can be found in either About Phone or Settings)
Step 1: Download KingoRoot application by preventing any unwanted applications.
Step 2: Before installing application go to Settings and Click 7 times on Developer button to get
developer access. Now click on allow USB Debugging. (As per the android version, Developer option
can be found in either About Phone or Settings)
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

Step 3: If you are downloading application on desktop, then connect your device by USB cable. Allow
USB Debugging permissions from device.
USB Debugging permissions from device.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Step 4: Now we are set for Rooting device, Just Click on ROOT button and wait while the application
performs necessary steps. We will receive success message as Your Phone is rooted.
We may reverse rooting process by simply clicking on Remove Root
performs necessary steps. We will receive success message as Your Phone is rooted.
We may reverse rooting process by simply clicking on Remove Root

Jailbreaking an iOS device
Jailbreaking generally is the process of removing the restrictions device manufacturer set. It generally
performed on Apple devices which removes the restrictions set by company. Also it allows us to change
or modify softwares completely.
For Obvious reasons these manufacturers of devices don’t want us to Jailbreak which allows us to even
change default progams on iOS. Hence we need to find soft spots to target. Whereas Android devices do
permit us to install Third party applications manually and don’t need to Jailbreak.
Jailbreaking generally is the process of removing the restrictions device manufacturer set. It generally
performed on Apple devices which removes the restrictions set by company. Also it allows us to change
or modify softwares completely.
For Obvious reasons these manufacturers of devices don’t want us to Jailbreak which allows us to even
change default progams on iOS. Hence we need to find soft spots to target. Whereas Android devices do
permit us to install Third party applications manually and don’t need to Jailbreak.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

Q-3: Please use adb pull command on an un-rooted Android device to try extracting any
application data from the device. Please share our screenshots and explain our observations.
Ans:- (How to Push and Pull files on /android using ADB Commands)
Connect your device to computer using USB cable.
Now perform below steps in ABD
1 Download and Install ADB on your PC.
2 Open Command Prompt in ADB folder
3 Now to pull any file from your device, path should be known to you. Using that path enter the pull
command as follows:
For example lets pull settings.apk file which location is /system/app/ on your device. (or you can first
check the path and then use it)
abd pull / system / app/Settings.apk
Now after this the settings.spk file will be pulled and saved inside ADB folder only. You can see the
command prompt as follows:
Here in above image we can also see the transfer rate of the Settings.apk file.
.
Q-4: Please briefly explain what manual, logical and physical extractions on Android devices are
and explain in what circumstances we would we each techniques.
Ans:- Acquisition (Evidence Acquisition in Mobile Forensics):
This is the second step in the forensic process.
When the device’s power is down, it is not easily possible to acquire data from device due to the nature of
it. One needs to perform device acquisition live only. To initiate the memory manager for writing
purpose, device needs to recognize the no network phase.
Almost all acquisition tools designed for mobile devices are automated and are viable. They are
comprised of hardware and software components both.
Most acquisition tools for mobile devices are automated and are commercial in nature and consist of both
hardware and software component.
application data from the device. Please share our screenshots and explain our observations.
Ans:- (How to Push and Pull files on /android using ADB Commands)
Connect your device to computer using USB cable.
Now perform below steps in ABD
1 Download and Install ADB on your PC.
2 Open Command Prompt in ADB folder
3 Now to pull any file from your device, path should be known to you. Using that path enter the pull
command as follows:
For example lets pull settings.apk file which location is /system/app/ on your device. (or you can first
check the path and then use it)
abd pull / system / app/Settings.apk
Now after this the settings.spk file will be pulled and saved inside ADB folder only. You can see the
command prompt as follows:
Here in above image we can also see the transfer rate of the Settings.apk file.
.
Q-4: Please briefly explain what manual, logical and physical extractions on Android devices are
and explain in what circumstances we would we each techniques.
Ans:- Acquisition (Evidence Acquisition in Mobile Forensics):
This is the second step in the forensic process.
When the device’s power is down, it is not easily possible to acquire data from device due to the nature of
it. One needs to perform device acquisition live only. To initiate the memory manager for writing
purpose, device needs to recognize the no network phase.
Almost all acquisition tools designed for mobile devices are automated and are viable. They are
comprised of hardware and software components both.
Most acquisition tools for mobile devices are automated and are commercial in nature and consist of both
hardware and software component.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Data acquisition types
Manual acquisition
To scrutinize the contents from device’s memory, the investigator uses the user interface of device. The
device is used normally and the investigator captures screenshots or photos of each screen’s contents. So
in this way you don’t need any specially designed tool to convert raw information into layman’s
language. This method is commonly used for mobile phones, GPS systems etc.
The negative is, this process is time consuming, and data which is available to operating system is
through pictures only.
Logical acquisition
Logical acquisition extracts every single bit of logical storage like directories and files.
Advantage is, comparatively it is easy for a device to mine and organize system data structures, to
synchronize contents of device using PC. As logical acquisition does not create any large binary data is
generally easier to work with. Imperative to say skilled forensic examiner will be far better option.
File system acquisition
Logical acquisition do not provide access to any erased evidence, as it is removed from phone’s file
system. Particularly with platforms built on SQLite, phone may keep a database simply as it does not
delete keeps for overwriting for later.
Physical acquisition
Physical extraction suggests the copy of whole physical storage.
Physical extraction suggests copy of an entire physical store (e.g. flash memory); that’s like of a personal
computer. We can examine deleted files and data remnants which is the advantage. Physical extraction
acquires information by accessing directly to the flash memories.
Logically it is difficult to attain because the manufacturer has to safeguard the random memory
reading.Digital forensics tool providers often create their own boot loaders which enables to access the
memory.
Manual acquisition
To scrutinize the contents from device’s memory, the investigator uses the user interface of device. The
device is used normally and the investigator captures screenshots or photos of each screen’s contents. So
in this way you don’t need any specially designed tool to convert raw information into layman’s
language. This method is commonly used for mobile phones, GPS systems etc.
The negative is, this process is time consuming, and data which is available to operating system is
through pictures only.
Logical acquisition
Logical acquisition extracts every single bit of logical storage like directories and files.
Advantage is, comparatively it is easy for a device to mine and organize system data structures, to
synchronize contents of device using PC. As logical acquisition does not create any large binary data is
generally easier to work with. Imperative to say skilled forensic examiner will be far better option.
File system acquisition
Logical acquisition do not provide access to any erased evidence, as it is removed from phone’s file
system. Particularly with platforms built on SQLite, phone may keep a database simply as it does not
delete keeps for overwriting for later.
Physical acquisition
Physical extraction suggests the copy of whole physical storage.
Physical extraction suggests copy of an entire physical store (e.g. flash memory); that’s like of a personal
computer. We can examine deleted files and data remnants which is the advantage. Physical extraction
acquires information by accessing directly to the flash memories.
Logically it is difficult to attain because the manufacturer has to safeguard the random memory
reading.Digital forensics tool providers often create their own boot loaders which enables to access the
memory.

There are two phases of physical extraction
A. Dumping phase
B. Decoding phase.
Difference between the mobile extraction methods are
A. Dumping phase
B. Decoding phase.
Difference between the mobile extraction methods are
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 15
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.
