Developing a Risk Management Plan for ANZ Bank's Cyber Defence
VerifiedAdded on 2023/06/04
|7
|1157
|71
Project
AI Summary
This project solution provides a comprehensive overview of a risk management plan for a cyber defence project within ANZ Bank. It includes a detailed scope statement outlining the project's description, business benefits, deliverables, acceptance criteria, and out-of-scope items. The solution identifies key constraints, assumptions, and risks associated with the project, such as costs, vulnerability assessments, and compliance issues. It also discusses various risk response strategies, including risk buffering, avoidance, sharing, and transference, with specific examples related to the project. The document emphasizes the importance of stakeholder engagement and provides insights into managing potential risks to ensure the successful implementation of the cyber defence project. It is contributed by a student and available on Desklib, a platform offering a variety of study tools and resources.

Running head: RISK MANAGEMENT
Risk Management
University Name
Student Name
Authors’ Note
Risk Management
University Name
Student Name
Authors’ Note
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

2
RISK MANAGEMENT
Table of Contents
Part 1:.........................................................................................................................................2
Part 2:.........................................................................................................................................5
Part 3:.........................................................................................................................................5
References..................................................................................................................................7
RISK MANAGEMENT
Table of Contents
Part 1:.........................................................................................................................................2
Part 2:.........................................................................................................................................5
Part 3:.........................................................................................................................................5
References..................................................................................................................................7
3
RISK MANAGEMENT
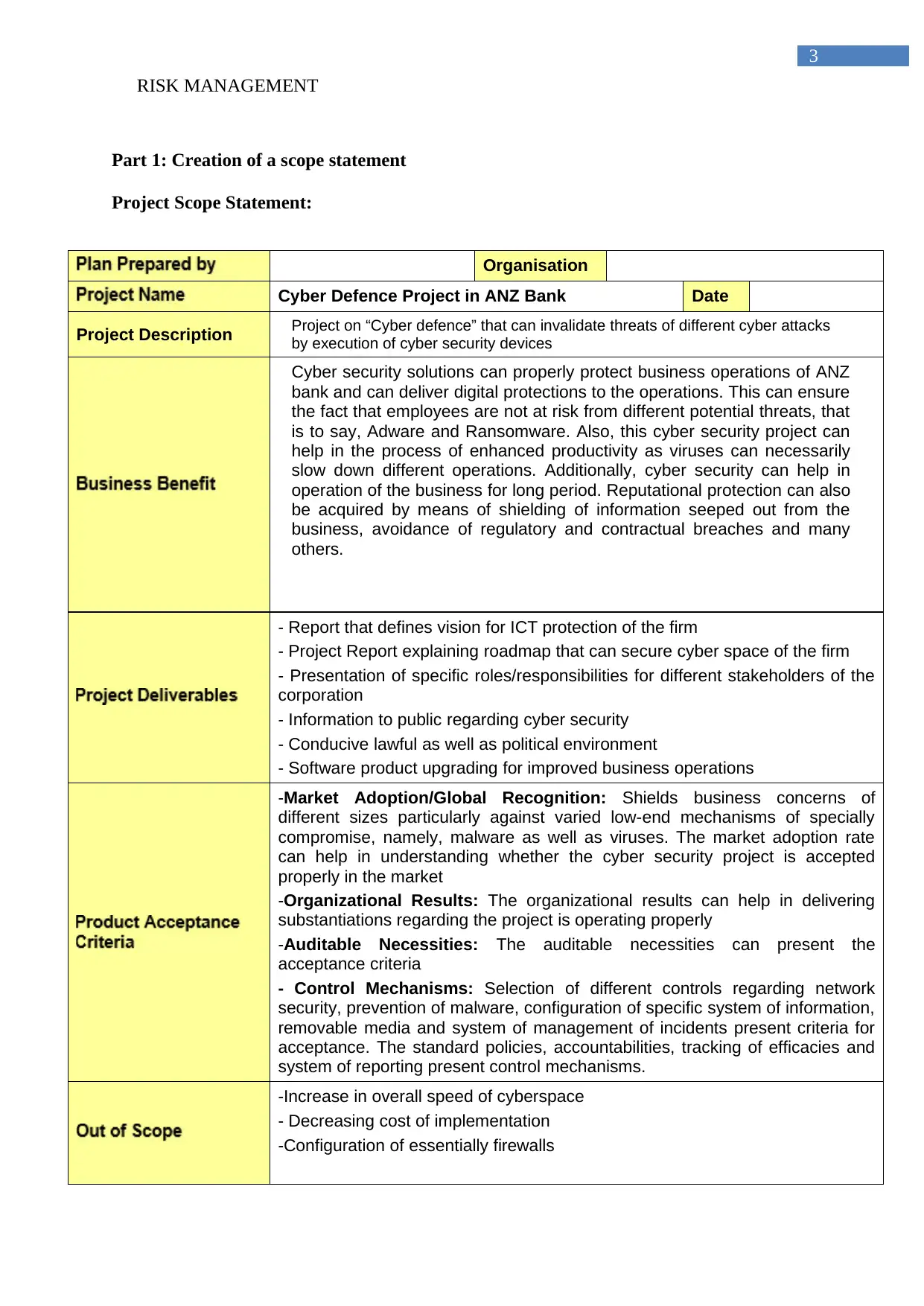
Part 1: Creation of a scope statement
Project Scope Statement:
Organisation
Cyber Defence Project in ANZ Bank Date
Project Description Project on “Cyber defence” that can invalidate threats of different cyber attacks
by execution of cyber security devices
Cyber security solutions can properly protect business operations of ANZ
bank and can deliver digital protections to the operations. This can ensure
the fact that employees are not at risk from different potential threats, that
is to say, Adware and Ransomware. Also, this cyber security project can
help in the process of enhanced productivity as viruses can necessarily
slow down different operations. Additionally, cyber security can help in
operation of the business for long period. Reputational protection can also
be acquired by means of shielding of information seeped out from the
business, avoidance of regulatory and contractual breaches and many
others.
- Report that defines vision for ICT protection of the firm
- Project Report explaining roadmap that can secure cyber space of the firm
- Presentation of specific roles/responsibilities for different stakeholders of the
corporation
- Information to public regarding cyber security
- Conducive lawful as well as political environment
- Software product upgrading for improved business operations
-Market Adoption/Global Recognition: Shields business concerns of
different sizes particularly against varied low-end mechanisms of specially
compromise, namely, malware as well as viruses. The market adoption rate
can help in understanding whether the cyber security project is accepted
properly in the market
-Organizational Results: The organizational results can help in delivering
substantiations regarding the project is operating properly
-Auditable Necessities: The auditable necessities can present the
acceptance criteria
- Control Mechanisms: Selection of different controls regarding network
security, prevention of malware, configuration of specific system of information,
removable media and system of management of incidents present criteria for
acceptance. The standard policies, accountabilities, tracking of efficacies and
system of reporting present control mechanisms.
-Increase in overall speed of cyberspace
- Decreasing cost of implementation
-Configuration of essentially firewalls
RISK MANAGEMENT
Part 1: Creation of a scope statement
Project Scope Statement:
Organisation
Cyber Defence Project in ANZ Bank Date
Project Description Project on “Cyber defence” that can invalidate threats of different cyber attacks
by execution of cyber security devices
Cyber security solutions can properly protect business operations of ANZ
bank and can deliver digital protections to the operations. This can ensure
the fact that employees are not at risk from different potential threats, that
is to say, Adware and Ransomware. Also, this cyber security project can
help in the process of enhanced productivity as viruses can necessarily
slow down different operations. Additionally, cyber security can help in
operation of the business for long period. Reputational protection can also
be acquired by means of shielding of information seeped out from the
business, avoidance of regulatory and contractual breaches and many
others.
- Report that defines vision for ICT protection of the firm
- Project Report explaining roadmap that can secure cyber space of the firm
- Presentation of specific roles/responsibilities for different stakeholders of the
corporation
- Information to public regarding cyber security
- Conducive lawful as well as political environment
- Software product upgrading for improved business operations
-Market Adoption/Global Recognition: Shields business concerns of
different sizes particularly against varied low-end mechanisms of specially
compromise, namely, malware as well as viruses. The market adoption rate
can help in understanding whether the cyber security project is accepted
properly in the market
-Organizational Results: The organizational results can help in delivering
substantiations regarding the project is operating properly
-Auditable Necessities: The auditable necessities can present the
acceptance criteria
- Control Mechanisms: Selection of different controls regarding network
security, prevention of malware, configuration of specific system of information,
removable media and system of management of incidents present criteria for
acceptance. The standard policies, accountabilities, tracking of efficacies and
system of reporting present control mechanisms.
-Increase in overall speed of cyberspace
- Decreasing cost of implementation
-Configuration of essentially firewalls
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
4
RISK MANAGEMENT
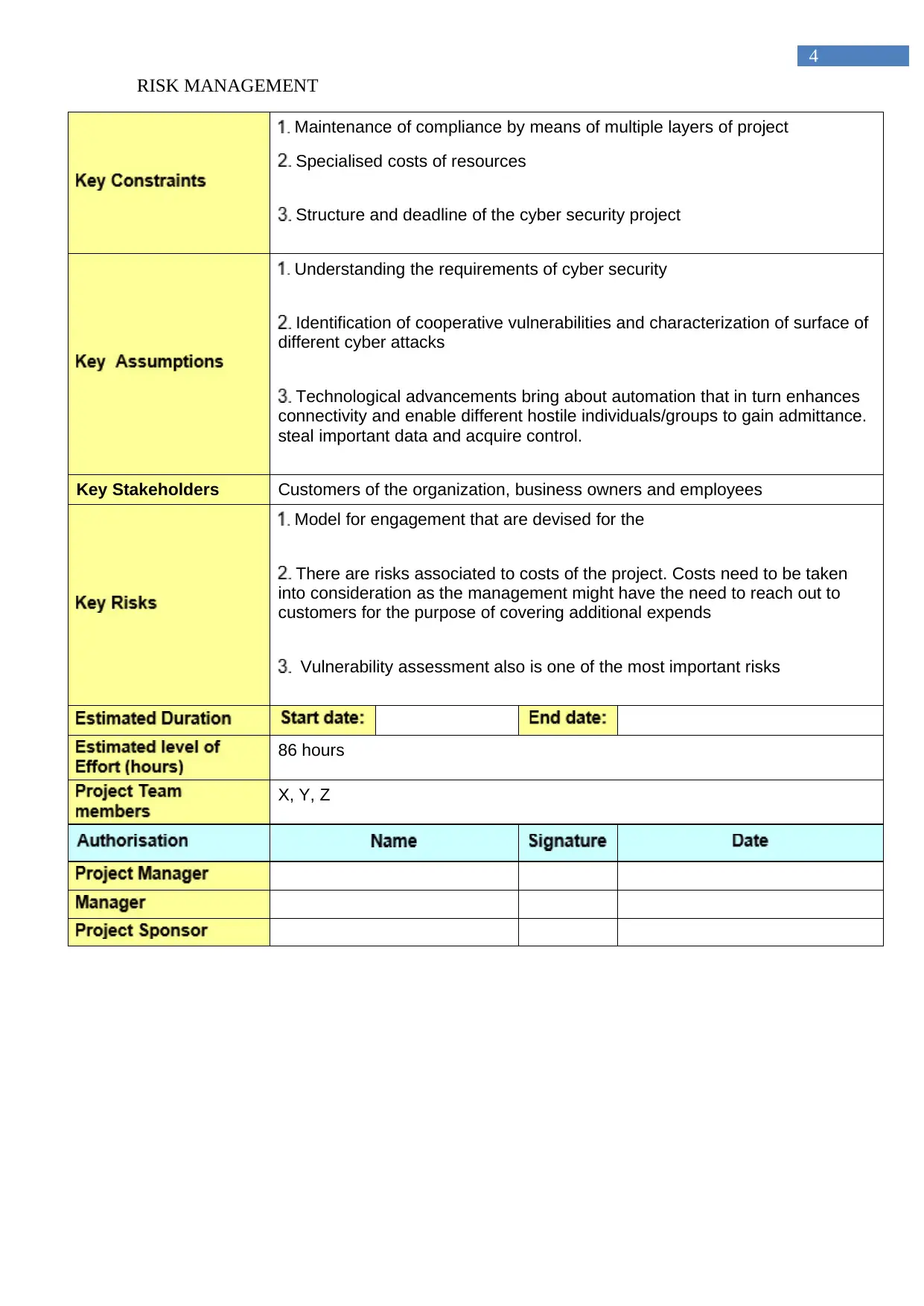
Maintenance of compliance by means of multiple layers of project
Specialised costs of resources
Structure and deadline of the cyber security project
Understanding the requirements of cyber security
Identification of cooperative vulnerabilities and characterization of surface of
different cyber attacks
Technological advancements bring about automation that in turn enhances
connectivity and enable different hostile individuals/groups to gain admittance.
steal important data and acquire control.
Key Stakeholders Customers of the organization, business owners and employees
Model for engagement that are devised for the
There are risks associated to costs of the project. Costs need to be taken
into consideration as the management might have the need to reach out to
customers for the purpose of covering additional expends
Vulnerability assessment also is one of the most important risks
86 hours
X, Y, Z
RISK MANAGEMENT
Maintenance of compliance by means of multiple layers of project
Specialised costs of resources
Structure and deadline of the cyber security project
Understanding the requirements of cyber security
Identification of cooperative vulnerabilities and characterization of surface of
different cyber attacks
Technological advancements bring about automation that in turn enhances
connectivity and enable different hostile individuals/groups to gain admittance.
steal important data and acquire control.
Key Stakeholders Customers of the organization, business owners and employees
Model for engagement that are devised for the
There are risks associated to costs of the project. Costs need to be taken
into consideration as the management might have the need to reach out to
customers for the purpose of covering additional expends
Vulnerability assessment also is one of the most important risks
86 hours
X, Y, Z
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
5
RISK MANAGEMENT
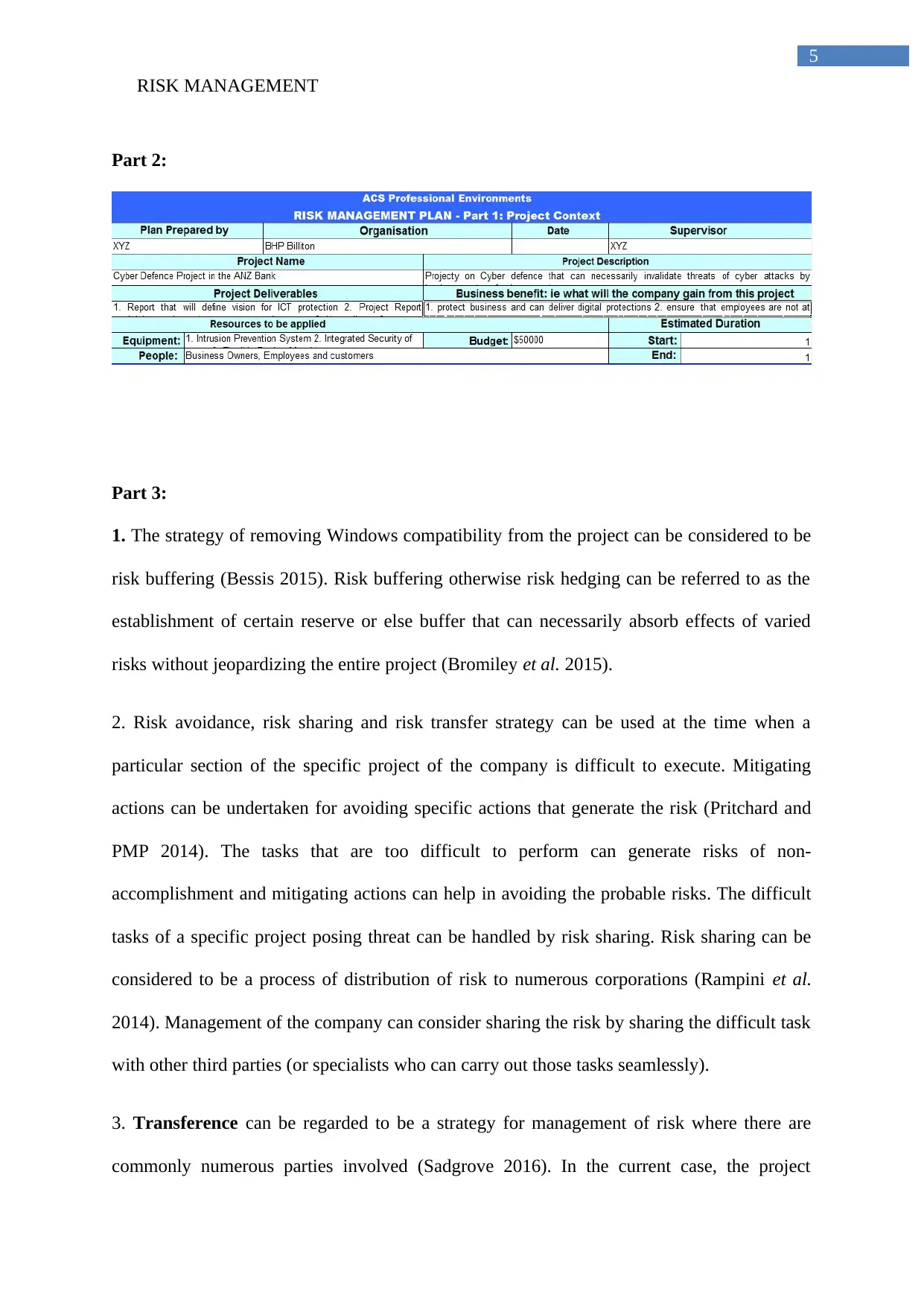
Part 2:
Part 3:
1. The strategy of removing Windows compatibility from the project can be considered to be
risk buffering (Bessis 2015). Risk buffering otherwise risk hedging can be referred to as the
establishment of certain reserve or else buffer that can necessarily absorb effects of varied
risks without jeopardizing the entire project (Bromiley et al. 2015).
2. Risk avoidance, risk sharing and risk transfer strategy can be used at the time when a
particular section of the specific project of the company is difficult to execute. Mitigating
actions can be undertaken for avoiding specific actions that generate the risk (Pritchard and
PMP 2014). The tasks that are too difficult to perform can generate risks of non-
accomplishment and mitigating actions can help in avoiding the probable risks. The difficult
tasks of a specific project posing threat can be handled by risk sharing. Risk sharing can be
considered to be a process of distribution of risk to numerous corporations (Rampini et al.
2014). Management of the company can consider sharing the risk by sharing the difficult task
with other third parties (or specialists who can carry out those tasks seamlessly).
3. Transference can be regarded to be a strategy for management of risk where there are
commonly numerous parties involved (Sadgrove 2016). In the current case, the project
RISK MANAGEMENT
Part 2:
Part 3:
1. The strategy of removing Windows compatibility from the project can be considered to be
risk buffering (Bessis 2015). Risk buffering otherwise risk hedging can be referred to as the
establishment of certain reserve or else buffer that can necessarily absorb effects of varied
risks without jeopardizing the entire project (Bromiley et al. 2015).
2. Risk avoidance, risk sharing and risk transfer strategy can be used at the time when a
particular section of the specific project of the company is difficult to execute. Mitigating
actions can be undertaken for avoiding specific actions that generate the risk (Pritchard and
PMP 2014). The tasks that are too difficult to perform can generate risks of non-
accomplishment and mitigating actions can help in avoiding the probable risks. The difficult
tasks of a specific project posing threat can be handled by risk sharing. Risk sharing can be
considered to be a process of distribution of risk to numerous corporations (Rampini et al.
2014). Management of the company can consider sharing the risk by sharing the difficult task
with other third parties (or specialists who can carry out those tasks seamlessly).
3. Transference can be regarded to be a strategy for management of risk where there are
commonly numerous parties involved (Sadgrove 2016). In the current case, the project

6
RISK MANAGEMENT
managers acknowledge that there can be contravention of law accidentally. It is for this
reason, they intend to hire a specialist to deal with the compliance issue and in this way the
liability is transferred to another party (Wiengarten et al. 2016). Thus, it can be considered to
be an example of transference strategy.
4. Avoidance can be considered to be a conscious decision not to carry out a specific project
or else an activity (Wolke 2017). In this regard, it is ascertained that the probable risk
surpasses the probable benefits. On the other hand, acceptance can be considered Acceptance
can be regarded as conscious decision to take part in a specific project or else activity since
the payback can be considered to be greater than transferring cost (Aven 2016).
RISK MANAGEMENT
managers acknowledge that there can be contravention of law accidentally. It is for this
reason, they intend to hire a specialist to deal with the compliance issue and in this way the
liability is transferred to another party (Wiengarten et al. 2016). Thus, it can be considered to
be an example of transference strategy.
4. Avoidance can be considered to be a conscious decision not to carry out a specific project
or else an activity (Wolke 2017). In this regard, it is ascertained that the probable risk
surpasses the probable benefits. On the other hand, acceptance can be considered Acceptance
can be regarded as conscious decision to take part in a specific project or else activity since
the payback can be considered to be greater than transferring cost (Aven 2016).
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

7
RISK MANAGEMENT
References
Aven, T., 2016. Risk assessment and risk management: Review of recent advances on their
foundation. European Journal of Operational Research, 253(1), pp.1-13.
Bessis, J., 2015. Risk management in banking. John Wiley & Sons.
Bromiley, P., McShane, M., Nair, A. and Rustambekov, E., 2015. Enterprise risk
management: Review, critique, and research directions. Long range planning, 48(4), pp.265-
276.
Pritchard, C.L. and PMP, P.R., 2014. Risk management: concepts and guidance. Auerbach
Publications.
Rampini, A.A., Sufi, A. and Viswanathan, S., 2014. Dynamic risk management. Journal of
Financial Economics, 111(2), pp.271-296.
Sadgrove, K., 2016. The complete guide to business risk management. Routledge.
Wiengarten, F., Humphreys, P., Gimenez, C. and McIvor, R., 2016. Risk, risk management
practices, and the success of supply chain integration. International Journal of Production
Economics, 171, pp.361-370.
Wolke, T., 2017. Risk Management. Walter de Gruyter GmbH & Co KG.
RISK MANAGEMENT
References
Aven, T., 2016. Risk assessment and risk management: Review of recent advances on their
foundation. European Journal of Operational Research, 253(1), pp.1-13.
Bessis, J., 2015. Risk management in banking. John Wiley & Sons.
Bromiley, P., McShane, M., Nair, A. and Rustambekov, E., 2015. Enterprise risk
management: Review, critique, and research directions. Long range planning, 48(4), pp.265-
276.
Pritchard, C.L. and PMP, P.R., 2014. Risk management: concepts and guidance. Auerbach
Publications.
Rampini, A.A., Sufi, A. and Viswanathan, S., 2014. Dynamic risk management. Journal of
Financial Economics, 111(2), pp.271-296.
Sadgrove, K., 2016. The complete guide to business risk management. Routledge.
Wiengarten, F., Humphreys, P., Gimenez, C. and McIvor, R., 2016. Risk, risk management
practices, and the success of supply chain integration. International Journal of Production
Economics, 171, pp.361-370.
Wolke, T., 2017. Risk Management. Walter de Gruyter GmbH & Co KG.
1 out of 7
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.




