Report on Face ID: Technology, Security Features, and Future Trends
VerifiedAdded on 2024/05/17
|13
|2354
|89
Report
AI Summary
This report provides an in-depth analysis of Apple's Face ID technology, a biometric authentication system that uses facial recognition. It discusses the technology behind Face ID, including the TrueDepth camera system and A11 Bionic chip, and how it works to capture and authenticate a user's face. The report also examines the security safeguards, privacy measures, and limitations of Face ID, such as its performance in varying lighting conditions and its inability to distinguish between identical twins. Furthermore, it explores the potential future developments of Face ID, including support for multiple users and wider integration across devices, and evaluates market responses to the technology, highlighting both its positive and negative aspects. The report concludes that Face ID has a promising future in biometric authentication, with the potential to replace other methods like Touch ID, despite its current limitations. Desklib provides a platform for students to access this and other solved assignments.

FACE ID
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

TABLE OF CONTENT
INTRODUCTION...........................................................................................................................5
MAIN BODY..................................................................................................................................5
CONCLUSION..............................................................................................................................12
INTRODUCTION...........................................................................................................................5
MAIN BODY..................................................................................................................................5
CONCLUSION..............................................................................................................................12
List of tables
Table 1: specifications.....................................................................................................................8
Table 1: specifications.....................................................................................................................8
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

LIST OF FIGURES
Figure 1: Face Recognition by mapping..........................................................................................4
Figure 2: Capturing an image..........................................................................................................5
Figure 3: Face recognition...............................................................................................................6
Figure 1: Face Recognition by mapping..........................................................................................4
Figure 2: Capturing an image..........................................................................................................5
Figure 3: Face recognition...............................................................................................................6
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

INTRODUCTION
Face ID is a new concept that has been developed and designed by Apple Inc for its new mobile
launched. These technologies according to its name denote it to be face recognition system
through biometric authentication technology. Face ID is a revolutionary authentication that is
meant for succeeding Touch ID method that helps in identification using finger print. With the
help of this technique the mobile phone can get unlock with just a single glance. TrueDepth
camera together with other advance technology is used in Face ID providing secure and
spontaneous verification.
MAIN BODYTechnology used:
Face ID is one of the latest and a rarely used technology which is build using mainly by
advanced software and hardware system. The camera has sensor having two modules, one of the
module of TrueDepth camera incarcerate precise data of a person’s face by analyzing projecting
more than 30,000 dots created invisible for accurate mapping of face and also holds the face’s
infrared image. While the other module works for reading the pattern either for confirming or for
denying access. In next step in Face ID, the depth map and infrared image taken is then
represented mathematically using A11 Bionic chip's neural engines that compare the former with
already registered facial data (Swanlund, 2017).
Face ID is a new concept that has been developed and designed by Apple Inc for its new mobile
launched. These technologies according to its name denote it to be face recognition system
through biometric authentication technology. Face ID is a revolutionary authentication that is
meant for succeeding Touch ID method that helps in identification using finger print. With the
help of this technique the mobile phone can get unlock with just a single glance. TrueDepth
camera together with other advance technology is used in Face ID providing secure and
spontaneous verification.
MAIN BODYTechnology used:
Face ID is one of the latest and a rarely used technology which is build using mainly by
advanced software and hardware system. The camera has sensor having two modules, one of the
module of TrueDepth camera incarcerate precise data of a person’s face by analyzing projecting
more than 30,000 dots created invisible for accurate mapping of face and also holds the face’s
infrared image. While the other module works for reading the pattern either for confirming or for
denying access. In next step in Face ID, the depth map and infrared image taken is then
represented mathematically using A11 Bionic chip's neural engines that compare the former with
already registered facial data (Swanlund, 2017).

Figure 1: Face Recognition by mapping
The system is designed in such a way that it is capable of leaning gradual human changes in face
with age, light, make up or accessories. Hence, a device enabled with Face ID can recognise the
face of the own even if the person is wearing a hat, glasses or sunglasses
Working of Face ID:
Face ID compares two images by enrolling the faces just like in Touch ID.
Capture Image- with the help of sensor and light projector Face ID takes and capture various
images of the users face and features. These system is together is known as TrueDepth camera
system. Face can be recognised quickly along with mapping of a detailed depth of the user’s
face. Instructions are provided in the screen of the devices for taking multiple shots of the image
for creating a 3D mapping (Bud, 2018).
Along with this Infrared light is used for image capturing that can effectively work both in day
and night it means intensity of light does not matter.
The system is designed in such a way that it is capable of leaning gradual human changes in face
with age, light, make up or accessories. Hence, a device enabled with Face ID can recognise the
face of the own even if the person is wearing a hat, glasses or sunglasses
Working of Face ID:
Face ID compares two images by enrolling the faces just like in Touch ID.
Capture Image- with the help of sensor and light projector Face ID takes and capture various
images of the users face and features. These system is together is known as TrueDepth camera
system. Face can be recognised quickly along with mapping of a detailed depth of the user’s
face. Instructions are provided in the screen of the devices for taking multiple shots of the image
for creating a 3D mapping (Bud, 2018).
Along with this Infrared light is used for image capturing that can effectively work both in day
and night it means intensity of light does not matter.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

Figure 2: Capturing an image
Face recognition- Face comes under biometric it means it can be measured through biological
characteristics. In biometric authentication, the system usually compares two images according
to their complexity pattern and similarity is calculated. The comparison is done with the present
image taken along with the image that is already store for reference for verification. For
verification a threshold is calculated and comparison is done accordingly. Face ID used by Apple
uses a processor Neural Engine that is capable of performing billions of operation per second and
is efficient to do face recognition in Real time. After completion of recognition phase
authentication process begins.
Face recognition- Face comes under biometric it means it can be measured through biological
characteristics. In biometric authentication, the system usually compares two images according
to their complexity pattern and similarity is calculated. The comparison is done with the present
image taken along with the image that is already store for reference for verification. For
verification a threshold is calculated and comparison is done accordingly. Face ID used by Apple
uses a processor Neural Engine that is capable of performing billions of operation per second and
is efficient to do face recognition in Real time. After completion of recognition phase
authentication process begins.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Figure 3: Face recognition
Authentication – Accuracy in face recognition depends on various factors including expression,
illumination and pose. It is often know as PIE. Under favourable condition like if the user is too
much cooperative in providing frontal pose, uniform illumination and neutral expression even
then the accuracy rate is 99.99%. Last but not the least factor that influence the accuracy of face
recognition is facial occlusion.
Face ID has claim to be out of odd that it can efficiently recognise a user face irrespective of
physical changes like hat, beard, scarf etc (Furnell and Clarke, 2014). Neural technology applied
in Face ID has capability of recognising face along with the use of specific machine learning
algorithm. Artificial Neural technology works like a human neural system that has an
interconnected structure that provide fast processing for adaptation and learning similar to human
brain. Machine learning algorithm is instruction sets that allows machine to adapt according to
the provided instruction. Face ID updates it algorithm very frequently with time so that face ID
can recognise the user face irrespective of chances in appearances.
Security safeguard:
Information in our device needs to be protected by maintaining proper security. The Face ID
system uses TrueDepth camera along with machine learning for providing solution for secure
Authentication – Accuracy in face recognition depends on various factors including expression,
illumination and pose. It is often know as PIE. Under favourable condition like if the user is too
much cooperative in providing frontal pose, uniform illumination and neutral expression even
then the accuracy rate is 99.99%. Last but not the least factor that influence the accuracy of face
recognition is facial occlusion.
Face ID has claim to be out of odd that it can efficiently recognise a user face irrespective of
physical changes like hat, beard, scarf etc (Furnell and Clarke, 2014). Neural technology applied
in Face ID has capability of recognising face along with the use of specific machine learning
algorithm. Artificial Neural technology works like a human neural system that has an
interconnected structure that provide fast processing for adaptation and learning similar to human
brain. Machine learning algorithm is instruction sets that allows machine to adapt according to
the provided instruction. Face ID updates it algorithm very frequently with time so that face ID
can recognise the user face irrespective of chances in appearances.
Security safeguard:
Information in our device needs to be protected by maintaining proper security. The Face ID
system uses TrueDepth camera along with machine learning for providing solution for secure

authentication. Unlike Touch ID, it has been seen that probability that random user looks and
unlocks the screen using Face Id is 1 out of 10 million while in case of touch ID it is 1 in every
50 thousand.
Additional feature with Face ID is pass code that allows five matches that can be unsuccessful
before locking the system for 48 hrs. No 2D photographs can be used for face verification in
Face ID as depth information to match cannot be seen. Hence, the device cannot be open or
unlocked using some kind of picture or mask. Face ID support anti-spoofing system by the use
of complicated anti-spoofing neural networks that cannot be tracked easily. Additionally Face ID
is attention aware it means it recognises a face only if the eyes are opened.
Maintaining Privacy:
Data used in Face ID for recognition of face are mathematical representations of a face which
with the help of Secure Enclave are encrypted and protected. Face id successive updates data
whenever a close match is found by verifying it with a pass code from the user. Data in face ID
is saved locally it doesn’t leave the device and is not stored in cloud or somewhere else
(Hopkins, 2015). And the feature of the technique can be disabled as per user requirement. An
app in the device having Face ID can be access only with successful authentication.
Safety:
The device and the camera (TrueDepth) are checked and tested efficiently for meeting the
standard of international safety. Under normal condition it is effective to use Truedepth camera
system for capturing image of the user for authentication purpose. The camera system has
features like tamper detection.
Night detection:
Even if the user is in low light or dark, Face ID is capable of recognising the user face though the
use of Flood Illuminator that uses infrared camera using infrared light for face detection and
recognising.
Table 1: specifications
Price $112
unlocks the screen using Face Id is 1 out of 10 million while in case of touch ID it is 1 in every
50 thousand.
Additional feature with Face ID is pass code that allows five matches that can be unsuccessful
before locking the system for 48 hrs. No 2D photographs can be used for face verification in
Face ID as depth information to match cannot be seen. Hence, the device cannot be open or
unlocked using some kind of picture or mask. Face ID support anti-spoofing system by the use
of complicated anti-spoofing neural networks that cannot be tracked easily. Additionally Face ID
is attention aware it means it recognises a face only if the eyes are opened.
Maintaining Privacy:
Data used in Face ID for recognition of face are mathematical representations of a face which
with the help of Secure Enclave are encrypted and protected. Face id successive updates data
whenever a close match is found by verifying it with a pass code from the user. Data in face ID
is saved locally it doesn’t leave the device and is not stored in cloud or somewhere else
(Hopkins, 2015). And the feature of the technique can be disabled as per user requirement. An
app in the device having Face ID can be access only with successful authentication.
Safety:
The device and the camera (TrueDepth) are checked and tested efficiently for meeting the
standard of international safety. Under normal condition it is effective to use Truedepth camera
system for capturing image of the user for authentication purpose. The camera system has
features like tamper detection.
Night detection:
Even if the user is in low light or dark, Face ID is capable of recognising the user face though the
use of Flood Illuminator that uses infrared camera using infrared light for face detection and
recognising.
Table 1: specifications
Price $112
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
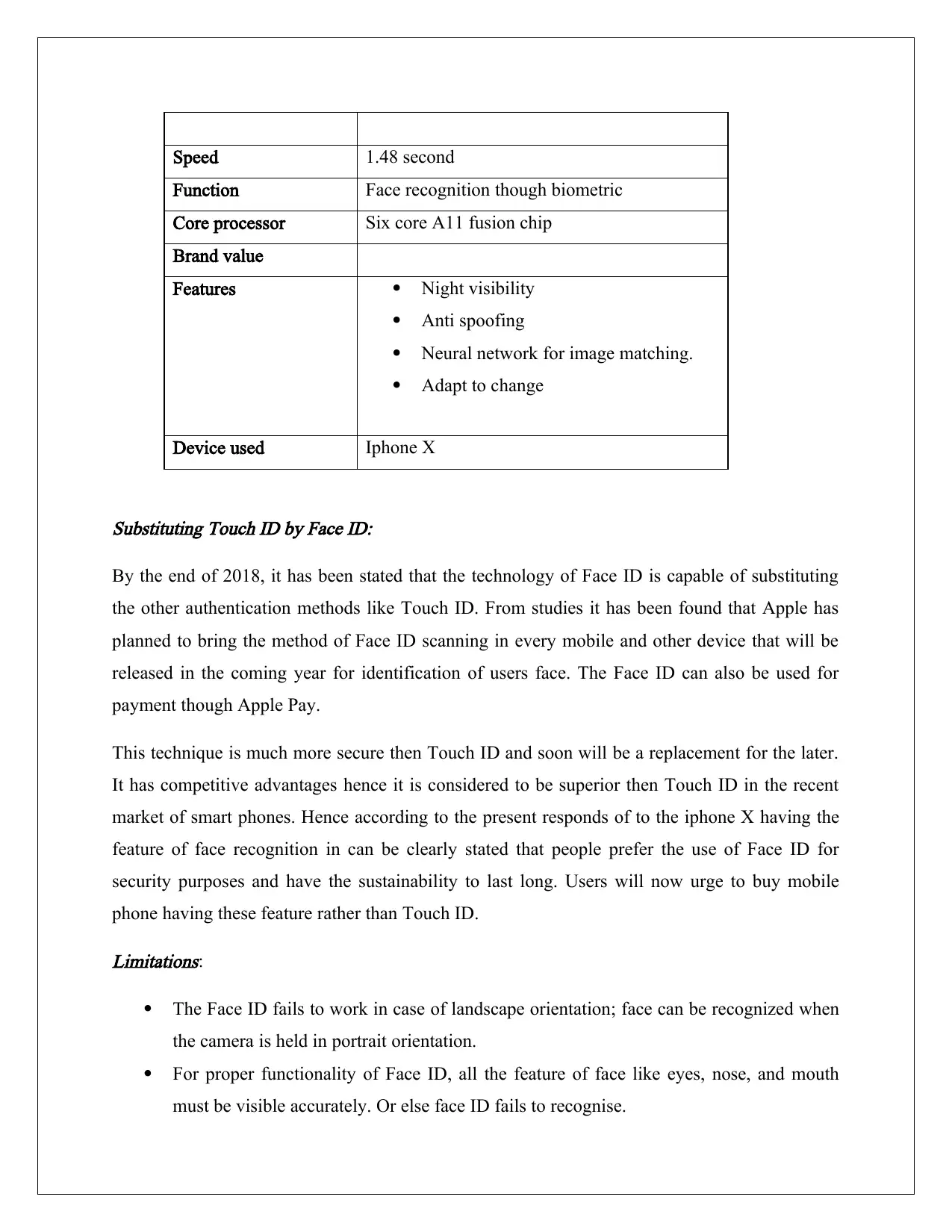
Speed 1.48 second
Function Face recognition though biometric
Core processor Six core A11 fusion chip
Brand value
Features Night visibility
Anti spoofing
Neural network for image matching.
Adapt to change
Device used Iphone X
Substituting Touch ID by Face ID:
By the end of 2018, it has been stated that the technology of Face ID is capable of substituting
the other authentication methods like Touch ID. From studies it has been found that Apple has
planned to bring the method of Face ID scanning in every mobile and other device that will be
released in the coming year for identification of users face. The Face ID can also be used for
payment though Apple Pay.
This technique is much more secure then Touch ID and soon will be a replacement for the later.
It has competitive advantages hence it is considered to be superior then Touch ID in the recent
market of smart phones. Hence according to the present responds of to the iphone X having the
feature of face recognition in can be clearly stated that people prefer the use of Face ID for
security purposes and have the sustainability to last long. Users will now urge to buy mobile
phone having these feature rather than Touch ID.
Limitations:
The Face ID fails to work in case of landscape orientation; face can be recognized when
the camera is held in portrait orientation.
For proper functionality of Face ID, all the feature of face like eyes, nose, and mouth
must be visible accurately. Or else face ID fails to recognise.
Function Face recognition though biometric
Core processor Six core A11 fusion chip
Brand value
Features Night visibility
Anti spoofing
Neural network for image matching.
Adapt to change
Device used Iphone X
Substituting Touch ID by Face ID:
By the end of 2018, it has been stated that the technology of Face ID is capable of substituting
the other authentication methods like Touch ID. From studies it has been found that Apple has
planned to bring the method of Face ID scanning in every mobile and other device that will be
released in the coming year for identification of users face. The Face ID can also be used for
payment though Apple Pay.
This technique is much more secure then Touch ID and soon will be a replacement for the later.
It has competitive advantages hence it is considered to be superior then Touch ID in the recent
market of smart phones. Hence according to the present responds of to the iphone X having the
feature of face recognition in can be clearly stated that people prefer the use of Face ID for
security purposes and have the sustainability to last long. Users will now urge to buy mobile
phone having these feature rather than Touch ID.
Limitations:
The Face ID fails to work in case of landscape orientation; face can be recognized when
the camera is held in portrait orientation.
For proper functionality of Face ID, all the feature of face like eyes, nose, and mouth
must be visible accurately. Or else face ID fails to recognise.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Direct or intense sunlight make the Face ID camera blind and affect it working.
Illumination causes problem while recognising a user in high sunlight or darkness
(Kummer, 2017).
Face ID fails to detect user below 13, for proper working of the application distant facial
feature. It is a reason to worry as youngster are the frequent customer of any new product
buying phone with Face ID and growing with time accordingly can be reason to not
being able to get recognised by the device.
Face ID is not effective to identify identical twins. It leads to privacy issues in some case
as all the store information can be opened and executed by the other sibling.
The Face ID can recognise only one face in a system. It is a problem with many people
practically quite impossible as a device tends to get operated by various users even the
family member uses a device of one another. Creating a issue to buy a thing and to make
payment using Apple pay or apple store.
Security always conflicts with convenience. Moreover, biometrics like Touch ID and Face ID,
are new technique of verification and authentication mainly with expedient along with
maintenance of high security level. Even with limitation Face ID is very demanding and
impressive.
Future recommendation:
After launching iPhone in market by Apple with additional and new feature like Face ID, it has
been seen that Face ID is very different from other facial recognition system. It is becoming an
integral part of daily life. Face ID has various mentioned limitations, hence it is seen that the
future of the system include:
Currently Face ID is capable of recognising a signal user face. Although Apple states
that Iphone is a single user phone but that is practically impossible and sharing password
is risky. Accordingly, recent technology is to support Face ID’s purview to be handled
and give access to different user by recognising them (Wojewidka, 2017).
More devices should support Face ID.
Faster the face ID will help in faster authentication.
Two side of Face ID:
Illumination causes problem while recognising a user in high sunlight or darkness
(Kummer, 2017).
Face ID fails to detect user below 13, for proper working of the application distant facial
feature. It is a reason to worry as youngster are the frequent customer of any new product
buying phone with Face ID and growing with time accordingly can be reason to not
being able to get recognised by the device.
Face ID is not effective to identify identical twins. It leads to privacy issues in some case
as all the store information can be opened and executed by the other sibling.
The Face ID can recognise only one face in a system. It is a problem with many people
practically quite impossible as a device tends to get operated by various users even the
family member uses a device of one another. Creating a issue to buy a thing and to make
payment using Apple pay or apple store.
Security always conflicts with convenience. Moreover, biometrics like Touch ID and Face ID,
are new technique of verification and authentication mainly with expedient along with
maintenance of high security level. Even with limitation Face ID is very demanding and
impressive.
Future recommendation:
After launching iPhone in market by Apple with additional and new feature like Face ID, it has
been seen that Face ID is very different from other facial recognition system. It is becoming an
integral part of daily life. Face ID has various mentioned limitations, hence it is seen that the
future of the system include:
Currently Face ID is capable of recognising a signal user face. Although Apple states
that Iphone is a single user phone but that is practically impossible and sharing password
is risky. Accordingly, recent technology is to support Face ID’s purview to be handled
and give access to different user by recognising them (Wojewidka, 2017).
More devices should support Face ID.
Faster the face ID will help in faster authentication.
Two side of Face ID:

Positive side: Face ID is a technology used mainly for device security. Face ID uses True Depth
which is huge by nature although the notch is smaller than the area needed for finger print. Face
ID will lead to an integrated, revolutionary and secure system supporting online payment through
face recognition. Face ID is more secure than any other system in the present world as possibility
of match is very less.
Negative side:
New technology bring new thing to worry about. Data can secretly be kept by the company that
is an issue related to privacy. Unlike finger printing, human face tend to differ with time
although apple having feature of Face ID claims to support changing hair colour, beard or hat but
has no guarantee regarding a teen buying the device and growing different with time.
Market responses:
To rival the Face ID technique used by Apple, a China base Smartphone making organisation is
developing a new technique of face recognition. The organisation instead of using laser sensor
uses simple HD camera having 280 x 800 pixels and capable of identifying 300,000 projection
points in less than 10 sec along with depression and elevation in the user proving to be a tough
competition to Apple’s Face ID that takes about only 0.4 seconds to unlock mobile phones
through face recognition and with minimum cost of the device.
CONCLUSION
In these above report it has been seen that Face ID technology used by Apple for face
recognition has future objective and great market. It is the most recent technology that is used for
authentication purpose in mobile phones. Face ID in the recent year can very easily suppress the
other technologies like Touch ID used for the same purpose of biometric authentication in
devices like computer and mobile phones. In these report, various expects of Face ID has been
studied including technology used, working, limitation, scope and future requirement, market
responses.
which is huge by nature although the notch is smaller than the area needed for finger print. Face
ID will lead to an integrated, revolutionary and secure system supporting online payment through
face recognition. Face ID is more secure than any other system in the present world as possibility
of match is very less.
Negative side:
New technology bring new thing to worry about. Data can secretly be kept by the company that
is an issue related to privacy. Unlike finger printing, human face tend to differ with time
although apple having feature of Face ID claims to support changing hair colour, beard or hat but
has no guarantee regarding a teen buying the device and growing different with time.
Market responses:
To rival the Face ID technique used by Apple, a China base Smartphone making organisation is
developing a new technique of face recognition. The organisation instead of using laser sensor
uses simple HD camera having 280 x 800 pixels and capable of identifying 300,000 projection
points in less than 10 sec along with depression and elevation in the user proving to be a tough
competition to Apple’s Face ID that takes about only 0.4 seconds to unlock mobile phones
through face recognition and with minimum cost of the device.
CONCLUSION
In these above report it has been seen that Face ID technology used by Apple for face
recognition has future objective and great market. It is the most recent technology that is used for
authentication purpose in mobile phones. Face ID in the recent year can very easily suppress the
other technologies like Touch ID used for the same purpose of biometric authentication in
devices like computer and mobile phones. In these report, various expects of Face ID has been
studied including technology used, working, limitation, scope and future requirement, market
responses.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 13
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





