Operating System and Application Security: A Comprehensive Report
VerifiedAdded on 2021/01/02
|12
|3214
|467
Report
AI Summary
This report provides a comprehensive overview of operating system (OS) and application security, focusing on security hardening requirements and cybersecurity frameworks. It explores the importance of securing systems by reducing complexities and eliminating risks, especially in the context of email services. The report details security requirements for protocols like IMAP and EAS, emphasizing the need for dedicated servers, restricted submissions, digital signatures, and front-end servers. It also discusses controls and measures, including the NIST framework and CSF, for protecting against cyber threats. The report highlights the significance of core email server applications, server auditing, and the use of tools like Postfix and Dovecot. Overall, the assignment emphasizes the importance of implementing robust security measures to safeguard data and ensure secure communication within organizations.

Operating system and Application
Security
Security
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Contents
INTRODUCTION...........................................................................................................................1
SECTION 1......................................................................................................................................1
Security hardening Requirements...............................................................................................1
Controls and measures of security hardening requirements.......................................................5
CONCLUSION ...............................................................................................................................7
REFERENCES ...............................................................................................................................8
INTRODUCTION...........................................................................................................................1
SECTION 1......................................................................................................................................1
Security hardening Requirements...............................................................................................1
Controls and measures of security hardening requirements.......................................................5
CONCLUSION ...............................................................................................................................7
REFERENCES ...............................................................................................................................8

INTRODUCTION
Operating system (OS) can be considered as the comprehensive process which controls
integrated components such as hardware, software, security, confidentiality and availability.
Application security canj be reffered as those measures which companies adopt to protect the
data and information. Application hardening of OS determines configuration of security features
and it also consists of rules and policies which helps in governing the system in more secured
manner. This also helps in excluding unnecessary services and application. This study will
contain information on security hardening requirements. The report will also focuss on
cybersecurity frameworks which protect the confidential data of the company. Furthermoer, it
will explain about the security requirements of IMAP or EAS. This report will also provide brief
view about security measures which control these security operating system and Application
security.
SECTION 1
Security hardening Requirements
Security hardening requirements is basically a process of securing operating system by
reducing the complexities of functions. this can be resolved by adopting single function system
which is more secured than multi-purpose system. These hardening requirements helps in
eliminating lot of risks. In present time, there are number of issues and problems which are
occurring in systems (Shaghaghi and et.al., 2018. ). This has resulted in data loss and leakage.
Hence, it leads to change in connection of network. There are many security hardening tools
available which can be installed.
In addition to this, installation of additional software and systems is used to provide
security to systems and it also helps in reducing vulnerabilities in different functions of the
device. They help in encryption of data packets and delivering them to destination. Also, it
providing more security to systems ensure that vulnerabilities are removed. Furthermore, there
are many other things due to which security is provided to systems. This report will show
different types of security hardening tools which will be installed in system. Also, it will describe
policies while implementation of devices and tools.
Applications: Application provides lot of services including Mail transfer services and mailbox
server (Roesner, Kohno and Molnar, 2014). Email can be considered as a main source of
communication in this technology based world. Therefore, Email services are great point of
1
Operating system (OS) can be considered as the comprehensive process which controls
integrated components such as hardware, software, security, confidentiality and availability.
Application security canj be reffered as those measures which companies adopt to protect the
data and information. Application hardening of OS determines configuration of security features
and it also consists of rules and policies which helps in governing the system in more secured
manner. This also helps in excluding unnecessary services and application. This study will
contain information on security hardening requirements. The report will also focuss on
cybersecurity frameworks which protect the confidential data of the company. Furthermoer, it
will explain about the security requirements of IMAP or EAS. This report will also provide brief
view about security measures which control these security operating system and Application
security.
SECTION 1
Security hardening Requirements
Security hardening requirements is basically a process of securing operating system by
reducing the complexities of functions. this can be resolved by adopting single function system
which is more secured than multi-purpose system. These hardening requirements helps in
eliminating lot of risks. In present time, there are number of issues and problems which are
occurring in systems (Shaghaghi and et.al., 2018. ). This has resulted in data loss and leakage.
Hence, it leads to change in connection of network. There are many security hardening tools
available which can be installed.
In addition to this, installation of additional software and systems is used to provide
security to systems and it also helps in reducing vulnerabilities in different functions of the
device. They help in encryption of data packets and delivering them to destination. Also, it
providing more security to systems ensure that vulnerabilities are removed. Furthermore, there
are many other things due to which security is provided to systems. This report will show
different types of security hardening tools which will be installed in system. Also, it will describe
policies while implementation of devices and tools.
Applications: Application provides lot of services including Mail transfer services and mailbox
server (Roesner, Kohno and Molnar, 2014). Email can be considered as a main source of
communication in this technology based world. Therefore, Email services are great point of
1
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

concern for many business operators. So lot of security requirements are arrived in transferring
mails via server. These requirements are as follows: Dedicated simple mail transfer protocols (SMTP) virtual servers for IMAP and POP
clients: It will ensure the use of emails within a closed messaging environment. These are
the two most widely used mailbox access protocols which are generally used by
commercial software manufacturers (Jing and et.al., 2014.). So, it will reduce the
possibilities arriving anonymous emails. Mailbox is considered as the simplest method
which allow users to access the mailbox and retrieve the messages. POP3 is the latest
version which reduces the security risks but although it also had to face limitations as pop
server deletes those messages or email files which ones retrieve to user. So users find it
difficult to access those documents another time. So there is great need to configure POP
messages so that it cannot be deleted from server. Internet message access protocol was
introduced to address all the limitations of POP. IMAP provides a centrally located server
which respond to multiple clients who wants to access the mails of a particular user. It
had fulfilled the security requirement of Email services which works on the principle of
CRAM (challenge-Response Authentication Mechanism). So IMAP dedicated servers
have proved the way to communicate with different users within an enclosed area. Restricting submissions to distribution lists and users: This security hardening
requirement is needed to prevent formulation of non-trusted senders. It restricts
unauthorised users to communicate with internal -only distribution list. This method
protects the organisation from the anonymous emails and it does not allow spam
messages to enter into the internal environment. This Security requirement will ensure
submission of messages to those people who are involved in the distribution lists. Formulate the use of Digitally sign and encrypted form of email documents:This
requirement methodology will protect the flow of data and information from
unauthorised users. Digital signature and Encryption of emails provide the highest
security to Application system (Sajid, Abbas and Saleem, 2016). This is a major
requirement of organisations to secure their commercial messages or confidential data
from the external users. This security hardening requirement prevents the data from other
interruptions like cybercrimes who aim at stealing the confidential information of the
firm.
2
mails via server. These requirements are as follows: Dedicated simple mail transfer protocols (SMTP) virtual servers for IMAP and POP
clients: It will ensure the use of emails within a closed messaging environment. These are
the two most widely used mailbox access protocols which are generally used by
commercial software manufacturers (Jing and et.al., 2014.). So, it will reduce the
possibilities arriving anonymous emails. Mailbox is considered as the simplest method
which allow users to access the mailbox and retrieve the messages. POP3 is the latest
version which reduces the security risks but although it also had to face limitations as pop
server deletes those messages or email files which ones retrieve to user. So users find it
difficult to access those documents another time. So there is great need to configure POP
messages so that it cannot be deleted from server. Internet message access protocol was
introduced to address all the limitations of POP. IMAP provides a centrally located server
which respond to multiple clients who wants to access the mails of a particular user. It
had fulfilled the security requirement of Email services which works on the principle of
CRAM (challenge-Response Authentication Mechanism). So IMAP dedicated servers
have proved the way to communicate with different users within an enclosed area. Restricting submissions to distribution lists and users: This security hardening
requirement is needed to prevent formulation of non-trusted senders. It restricts
unauthorised users to communicate with internal -only distribution list. This method
protects the organisation from the anonymous emails and it does not allow spam
messages to enter into the internal environment. This Security requirement will ensure
submission of messages to those people who are involved in the distribution lists. Formulate the use of Digitally sign and encrypted form of email documents:This
requirement methodology will protect the flow of data and information from
unauthorised users. Digital signature and Encryption of emails provide the highest
security to Application system (Sajid, Abbas and Saleem, 2016). This is a major
requirement of organisations to secure their commercial messages or confidential data
from the external users. This security hardening requirement prevents the data from other
interruptions like cybercrimes who aim at stealing the confidential information of the
firm.
2
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Establishing front end serves: These servers can be helpful in providing security to mail
server and operating system. It is used to disable the unnecessary information or services
from operating system. The purpose of operating system is to manage and control all the
activities of the system so keeping the large source of data into the system reduces
potential functionality of the system. So these front end servers are helpful in managing
large course of database for individual. This security requirement is needed to perform all
the tasks of server which provides dynamic services to users. It is an easy method which
provides multiple functionalities so that user can retrieve the required information
without requesting to main servers (Baumann, Peinado and Hunt, 2015). It also reduced
the traffic on the main server. This will improve responding speed of request which are
generated by clients to retrieve a particular data from server. Front end servers
immediately responds to the requests of clients without any more delay. Increase use of Real time block list: This ensures the use of emails and messaging
services by authorised users. This process identifies the users and allows retrieving and
sent emails within the business. If unknown users adopt any practice to hack information
commercial of the organization then RBL automatically block user and this would be
helpful in providing access to only those people who are the correct receiver of the mails. Using Form based authentication: This will only allow the authorised users to access
the information and it will ultimately provide great security in an organisation. This
authentication ensures developer to create customised login page and it also helps
developer to control error pages. This security hardening requirement is generally needed
by the professional companies who are dealing with large source of confidential data a
regular basis (Heuser and et.al., 2016). So in this situation loss of data would not be
compromised anyway and this might be a long term disadvantage for an enterprise. This
security concern mainly deals with certified user who are allowed to use confidential
information of the firm. Form based authentication is generally provides large security to
operating system so that it can maintain secured application and services. This concept
helps server in providing access to those who are identified. This authentication asks for
user identity for accessing the data and information.
Protection of operating system and application by providing suitable cybersecurity
framework:Frameworks are considered as a simple method which provide basic structure
3
server and operating system. It is used to disable the unnecessary information or services
from operating system. The purpose of operating system is to manage and control all the
activities of the system so keeping the large source of data into the system reduces
potential functionality of the system. So these front end servers are helpful in managing
large course of database for individual. This security requirement is needed to perform all
the tasks of server which provides dynamic services to users. It is an easy method which
provides multiple functionalities so that user can retrieve the required information
without requesting to main servers (Baumann, Peinado and Hunt, 2015). It also reduced
the traffic on the main server. This will improve responding speed of request which are
generated by clients to retrieve a particular data from server. Front end servers
immediately responds to the requests of clients without any more delay. Increase use of Real time block list: This ensures the use of emails and messaging
services by authorised users. This process identifies the users and allows retrieving and
sent emails within the business. If unknown users adopt any practice to hack information
commercial of the organization then RBL automatically block user and this would be
helpful in providing access to only those people who are the correct receiver of the mails. Using Form based authentication: This will only allow the authorised users to access
the information and it will ultimately provide great security in an organisation. This
authentication ensures developer to create customised login page and it also helps
developer to control error pages. This security hardening requirement is generally needed
by the professional companies who are dealing with large source of confidential data a
regular basis (Heuser and et.al., 2016). So in this situation loss of data would not be
compromised anyway and this might be a long term disadvantage for an enterprise. This
security concern mainly deals with certified user who are allowed to use confidential
information of the firm. Form based authentication is generally provides large security to
operating system so that it can maintain secured application and services. This concept
helps server in providing access to those who are identified. This authentication asks for
user identity for accessing the data and information.
Protection of operating system and application by providing suitable cybersecurity
framework:Frameworks are considered as a simple method which provide basic structure
3

to OS and applications for securing the data into the system. It is basically a architecture
which provide security to emails and prevents it from untrusted users. These can consist
of proper standard and guidelines to provide security by protecting the delicate source of
information from cyberattacks. Generally NIST (National institutes of standards and
security) can be determined as the most suitable cybersecurity framework. This have
provided the better security feature to protect the OS and application system from any
malware practices.
Core email server applications:
Enterprise is often required to provide their own email services to employees for
establishing a strong interpersonal communication between staff members. Simple Mail Transfer
Protocol provides a powerful server to protect the information which is circulated through mails
in the business. HTTP servers are required to configured in this environment for effective
communication of staff members (Peltier, 2016 Sajid and et.al., 2016. ). it is acommon software
component is provided on server which systematically sending and receiving emails of users.
Networking interface facilitates user to communicate and establish strong interaction
within the organisation through mailing services. In this, employees communicate to other staff
members on a specific topic which contains highly confidential information of the enterprise.
Core Email server application need to be configured in order to provide secure transmission of
data.
Operating system and Server auditing- It is a process where severs are kept on audit by
business. In this, frequent maintenance of server is done to identify possible threats. It also helps
in giving an insight on performance of server and its security. Besides this, it shows areas where
improvements are required.
Linux: Postfix and Dovecot and suitable web-email implementation
It can be determined as best source of transferring the emails to other persons and this is
referred as a open source of mailing and it acts as third party which provides links between
sender and receivers. It delivers the mail in a more secure manner. IBM is a major license holder
company which consists of certified authority to transfer mails on servers.
4
which provide security to emails and prevents it from untrusted users. These can consist
of proper standard and guidelines to provide security by protecting the delicate source of
information from cyberattacks. Generally NIST (National institutes of standards and
security) can be determined as the most suitable cybersecurity framework. This have
provided the better security feature to protect the OS and application system from any
malware practices.
Core email server applications:
Enterprise is often required to provide their own email services to employees for
establishing a strong interpersonal communication between staff members. Simple Mail Transfer
Protocol provides a powerful server to protect the information which is circulated through mails
in the business. HTTP servers are required to configured in this environment for effective
communication of staff members (Peltier, 2016 Sajid and et.al., 2016. ). it is acommon software
component is provided on server which systematically sending and receiving emails of users.
Networking interface facilitates user to communicate and establish strong interaction
within the organisation through mailing services. In this, employees communicate to other staff
members on a specific topic which contains highly confidential information of the enterprise.
Core Email server application need to be configured in order to provide secure transmission of
data.
Operating system and Server auditing- It is a process where severs are kept on audit by
business. In this, frequent maintenance of server is done to identify possible threats. It also helps
in giving an insight on performance of server and its security. Besides this, it shows areas where
improvements are required.
Linux: Postfix and Dovecot and suitable web-email implementation
It can be determined as best source of transferring the emails to other persons and this is
referred as a open source of mailing and it acts as third party which provides links between
sender and receivers. It delivers the mail in a more secure manner. IBM is a major license holder
company which consists of certified authority to transfer mails on servers.
4
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

Controls and measures of security hardening requirements
After determining the requirements of security hardening, it is necessary to specify
control that must be implemented along with it. This makes it easy in taking effective measures
or actions in case of emergency. Also, controls are basic policies and regulations that must be
determined. Moreover, they provide a basic framework of cyber security. Through this, it is easy
to analyze what tools and equipment’s are proper and fits in application or server. For present
case following are controls that can be used (Almorsy, Grundy and Müller, 2016). These are
described below:-
NIST framework- it consists of policies and guidance regarding protecting, detecting
and responding to cyber attacks by private organizations. Also, it includes methods and
outcomes of managing and accessing cyber attacks. In this version 1 was published in 2014 and
1..1 was issued for public. The main functions of NIST are:-
Identify- to manage risk of systems by accessing data and capabilities.
Detect- to identify activities on how to detect occurrence of security event.
Protect – here, infrastructure is deigned to ensure delivery of services.
Respond- Developing strategies on how to respond to security event.
Recover – implementation of strategies to restore services that was impacted by any
security event. Importance of NIST control measure includes:
it can be determined as reliable and well functioning and critical infrastructure which
provides security national and economic factors. It is basically a structure which contribute
towards the security of operating and application system so that confidential data can be
communicated to other members of the enterprise. If these guidelines are not applied in adopting
the security measures then it would be helpful in providing configured services to dedicated
group of people. It also protects the emails and high security data from spams and other
destructive attacks.
CSF- This security standard is based on practices or compliance approach. CSF is designed with
another framework such as ISO/IEC 27000, COBIT 5, etc. these can be customized according to
requirement’s. Basically, it has three components that are core, tiers and profiles.
5
After determining the requirements of security hardening, it is necessary to specify
control that must be implemented along with it. This makes it easy in taking effective measures
or actions in case of emergency. Also, controls are basic policies and regulations that must be
determined. Moreover, they provide a basic framework of cyber security. Through this, it is easy
to analyze what tools and equipment’s are proper and fits in application or server. For present
case following are controls that can be used (Almorsy, Grundy and Müller, 2016). These are
described below:-
NIST framework- it consists of policies and guidance regarding protecting, detecting
and responding to cyber attacks by private organizations. Also, it includes methods and
outcomes of managing and accessing cyber attacks. In this version 1 was published in 2014 and
1..1 was issued for public. The main functions of NIST are:-
Identify- to manage risk of systems by accessing data and capabilities.
Detect- to identify activities on how to detect occurrence of security event.
Protect – here, infrastructure is deigned to ensure delivery of services.
Respond- Developing strategies on how to respond to security event.
Recover – implementation of strategies to restore services that was impacted by any
security event. Importance of NIST control measure includes:
it can be determined as reliable and well functioning and critical infrastructure which
provides security national and economic factors. It is basically a structure which contribute
towards the security of operating and application system so that confidential data can be
communicated to other members of the enterprise. If these guidelines are not applied in adopting
the security measures then it would be helpful in providing configured services to dedicated
group of people. It also protects the emails and high security data from spams and other
destructive attacks.
CSF- This security standard is based on practices or compliance approach. CSF is designed with
another framework such as ISO/IEC 27000, COBIT 5, etc. these can be customized according to
requirement’s. Basically, it has three components that are core, tiers and profiles.
5
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
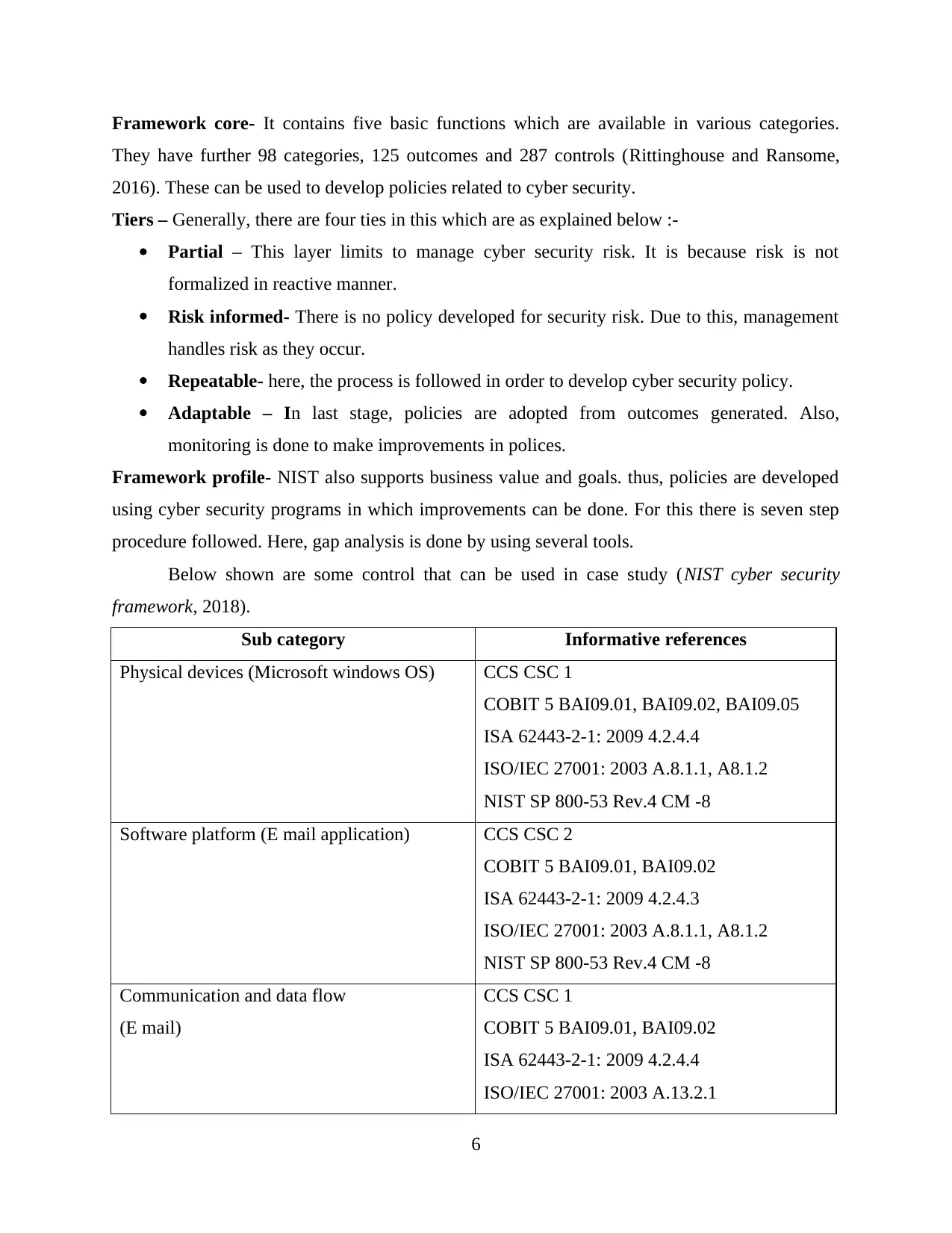
Framework core- It contains five basic functions which are available in various categories.
They have further 98 categories, 125 outcomes and 287 controls (Rittinghouse and Ransome,
2016). These can be used to develop policies related to cyber security.
Tiers – Generally, there are four ties in this which are as explained below :-
Partial – This layer limits to manage cyber security risk. It is because risk is not
formalized in reactive manner.
Risk informed- There is no policy developed for security risk. Due to this, management
handles risk as they occur.
Repeatable- here, the process is followed in order to develop cyber security policy.
Adaptable – In last stage, policies are adopted from outcomes generated. Also,
monitoring is done to make improvements in polices.
Framework profile- NIST also supports business value and goals. thus, policies are developed
using cyber security programs in which improvements can be done. For this there is seven step
procedure followed. Here, gap analysis is done by using several tools.
Below shown are some control that can be used in case study (NIST cyber security
framework, 2018).
Sub category Informative references
Physical devices (Microsoft windows OS) CCS CSC 1
COBIT 5 BAI09.01, BAI09.02, BAI09.05
ISA 62443-2-1: 2009 4.2.4.4
ISO/IEC 27001: 2003 A.8.1.1, A8.1.2
NIST SP 800-53 Rev.4 CM -8
Software platform (E mail application) CCS CSC 2
COBIT 5 BAI09.01, BAI09.02
ISA 62443-2-1: 2009 4.2.4.3
ISO/IEC 27001: 2003 A.8.1.1, A8.1.2
NIST SP 800-53 Rev.4 CM -8
Communication and data flow
(E mail)
CCS CSC 1
COBIT 5 BAI09.01, BAI09.02
ISA 62443-2-1: 2009 4.2.4.4
ISO/IEC 27001: 2003 A.13.2.1
6
They have further 98 categories, 125 outcomes and 287 controls (Rittinghouse and Ransome,
2016). These can be used to develop policies related to cyber security.
Tiers – Generally, there are four ties in this which are as explained below :-
Partial – This layer limits to manage cyber security risk. It is because risk is not
formalized in reactive manner.
Risk informed- There is no policy developed for security risk. Due to this, management
handles risk as they occur.
Repeatable- here, the process is followed in order to develop cyber security policy.
Adaptable – In last stage, policies are adopted from outcomes generated. Also,
monitoring is done to make improvements in polices.
Framework profile- NIST also supports business value and goals. thus, policies are developed
using cyber security programs in which improvements can be done. For this there is seven step
procedure followed. Here, gap analysis is done by using several tools.
Below shown are some control that can be used in case study (NIST cyber security
framework, 2018).
Sub category Informative references
Physical devices (Microsoft windows OS) CCS CSC 1
COBIT 5 BAI09.01, BAI09.02, BAI09.05
ISA 62443-2-1: 2009 4.2.4.4
ISO/IEC 27001: 2003 A.8.1.1, A8.1.2
NIST SP 800-53 Rev.4 CM -8
Software platform (E mail application) CCS CSC 2
COBIT 5 BAI09.01, BAI09.02
ISA 62443-2-1: 2009 4.2.4.3
ISO/IEC 27001: 2003 A.8.1.1, A8.1.2
NIST SP 800-53 Rev.4 CM -8
Communication and data flow
(E mail)
CCS CSC 1
COBIT 5 BAI09.01, BAI09.02
ISA 62443-2-1: 2009 4.2.4.4
ISO/IEC 27001: 2003 A.13.2.1
6

NSIT SP 800-53 Rev.4 AC -4
By using the above controls in security requirements, it will easy to protect E mail
application and operating system. Also, through proper implementation of policy tools will be
installed. Moreover, framework gives an insight on what action or measure should be taken in
case of cyber attack (Criswell, Dautenhahn and Adve, 2014). Other than this, NIST describes
configuration of security tools along with their requirement. It clarifies a process on how to
detect, measure and identify cyber crime.
Here, it is important to determine configuration of security tools so that effective and
proper policies are developed.
Importance of CFS in security of application and operating system includes the following
features such as it prevents the business and government from losing the security of mailing
documents. This encrypts the data which is transmitted by the sender in order to establish
communication between both the parties (Puthal and et.al., 2015). The encrypted information is
hard to understand by any unauthorized person and this data when reach to targeted receiver then
one applies the private key to decry pt the data and therefore it is most reliable and secured way
to exchange private information on server. by applying the NIST security policy it will be easy to
protect systems and applications from cyber attacks. also, it will help in taking actions in
systematic way so that issues and problems are solved effectively. the policies will be beneficial
for long term as changes can be made while determining requirements.
CONCLUSION
This report had provided a brief view about security hardening requirements of operating
systems and applications. The study had focussed towards the need of dedicated SMTP servers
which provide support in securing the data. It had also mentioned security measures which
controls the activities of operating system and application system. The report was totally based
on hardening requirements to application and OS. It had also covered some points related to
email services which might be the greatest threat in disclosing the confidentiality of organisation.
Furthermore, it had also focussed on the methods which are useful for preventing the data from
unauthorised users.
7
By using the above controls in security requirements, it will easy to protect E mail
application and operating system. Also, through proper implementation of policy tools will be
installed. Moreover, framework gives an insight on what action or measure should be taken in
case of cyber attack (Criswell, Dautenhahn and Adve, 2014). Other than this, NIST describes
configuration of security tools along with their requirement. It clarifies a process on how to
detect, measure and identify cyber crime.
Here, it is important to determine configuration of security tools so that effective and
proper policies are developed.
Importance of CFS in security of application and operating system includes the following
features such as it prevents the business and government from losing the security of mailing
documents. This encrypts the data which is transmitted by the sender in order to establish
communication between both the parties (Puthal and et.al., 2015). The encrypted information is
hard to understand by any unauthorized person and this data when reach to targeted receiver then
one applies the private key to decry pt the data and therefore it is most reliable and secured way
to exchange private information on server. by applying the NIST security policy it will be easy to
protect systems and applications from cyber attacks. also, it will help in taking actions in
systematic way so that issues and problems are solved effectively. the policies will be beneficial
for long term as changes can be made while determining requirements.
CONCLUSION
This report had provided a brief view about security hardening requirements of operating
systems and applications. The study had focussed towards the need of dedicated SMTP servers
which provide support in securing the data. It had also mentioned security measures which
controls the activities of operating system and application system. The report was totally based
on hardening requirements to application and OS. It had also covered some points related to
email services which might be the greatest threat in disclosing the confidentiality of organisation.
Furthermore, it had also focussed on the methods which are useful for preventing the data from
unauthorised users.
7
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

REFERENCES
Books and journals
Almorsy, M., Grundy, J. and Müller, I., 2016. An analysis of the cloud computing security
problem. arXiv preprint arXiv:1609.01107.
Baumann, A., Peinado, M. and Hunt, G., 2015. Shielding applications from an untrusted
cloud with haven. ACM Transactions on Computer Systems (TOCS). 33(3). pp.8.
Criswell, J., Dautenhahn, N. and Adve, V., 2014. Virtual ghost: Protecting applications
from hostile operating systems. ACM SIGARCH Computer Architecture News. 42(1). pp.81-96.
Heuser, S., and et.al., 2016, February. DroidAuditor: Forensic Analysis of Application-
Layer Privilege Escalation Attacks on Android (Short Paper). In International Conference on
Financial Cryptography and Data Security (pp. 260-268). Springer, Berlin, Heidelberg.
Jing, Q., and et.al., 2014. Security of the Internet of Things: perspectives and
challenges. Wireless Networks. 20(8). pp.2481-2501.
Peltier, T.R., 2016. Information Security Policies, Procedures, and Standards: guidelines
for effective information security management. Auerbach Publications.
Puthal, D., and et.al., 2015, January. Cloud computing features, issues, and challenges: a
big picture. In Computational Intelligence and Networks (CINE), 2015 International Conference
on (pp. 116-123). IEEE.
Rittinghouse, J.W. and Ransome, J.F., 2016. Cloud computing: implementation,
management, and security. CRC press.
Roesner, F., Kohno, T. and Molnar, D., 2014. Security and privacy for augmented reality
systems. Communications of the ACM. 57(4). pp.88-96.
Sajid, A., Abbas, H. and Saleem, K., 2016. Cloud-assisted IoT-based SCADA systems
security: A review of the state of the art and future challenges. IEEE Access. 4. pp.1375-1384.
Sajid, A., and et.al., 2016. An Analysis on Host Vulnerability Evaluation of Modern
Operating Systems. INTERNATIONAL JOURNAL OF ADVANCED COMPUTER SCIENCE
AND APPLICATIONS, 7(4). pp.245-254.
Shaghaghi, A. and et.al., 2018. Gwardar: Towards Protecting a Software-Defined Network
from Malicious Network Operating Systems. arXiv preprint arXiv:1809.06988.
Online
8
Books and journals
Almorsy, M., Grundy, J. and Müller, I., 2016. An analysis of the cloud computing security
problem. arXiv preprint arXiv:1609.01107.
Baumann, A., Peinado, M. and Hunt, G., 2015. Shielding applications from an untrusted
cloud with haven. ACM Transactions on Computer Systems (TOCS). 33(3). pp.8.
Criswell, J., Dautenhahn, N. and Adve, V., 2014. Virtual ghost: Protecting applications
from hostile operating systems. ACM SIGARCH Computer Architecture News. 42(1). pp.81-96.
Heuser, S., and et.al., 2016, February. DroidAuditor: Forensic Analysis of Application-
Layer Privilege Escalation Attacks on Android (Short Paper). In International Conference on
Financial Cryptography and Data Security (pp. 260-268). Springer, Berlin, Heidelberg.
Jing, Q., and et.al., 2014. Security of the Internet of Things: perspectives and
challenges. Wireless Networks. 20(8). pp.2481-2501.
Peltier, T.R., 2016. Information Security Policies, Procedures, and Standards: guidelines
for effective information security management. Auerbach Publications.
Puthal, D., and et.al., 2015, January. Cloud computing features, issues, and challenges: a
big picture. In Computational Intelligence and Networks (CINE), 2015 International Conference
on (pp. 116-123). IEEE.
Rittinghouse, J.W. and Ransome, J.F., 2016. Cloud computing: implementation,
management, and security. CRC press.
Roesner, F., Kohno, T. and Molnar, D., 2014. Security and privacy for augmented reality
systems. Communications of the ACM. 57(4). pp.88-96.
Sajid, A., Abbas, H. and Saleem, K., 2016. Cloud-assisted IoT-based SCADA systems
security: A review of the state of the art and future challenges. IEEE Access. 4. pp.1375-1384.
Sajid, A., and et.al., 2016. An Analysis on Host Vulnerability Evaluation of Modern
Operating Systems. INTERNATIONAL JOURNAL OF ADVANCED COMPUTER SCIENCE
AND APPLICATIONS, 7(4). pp.245-254.
Shaghaghi, A. and et.al., 2018. Gwardar: Towards Protecting a Software-Defined Network
from Malicious Network Operating Systems. arXiv preprint arXiv:1809.06988.
Online
8
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

NIST cyber security framework. 2018. [online]. Available through:
https://www.securitymagazine.com/blogs/14-security-blog/post/88890-how-to-use-the-
nist-cybersecurity-framework
9
https://www.securitymagazine.com/blogs/14-security-blog/post/88890-how-to-use-the-
nist-cybersecurity-framework
9

10
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 12
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2025 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.




