Application Security Report: Vulnerabilities and Mitigation Strategies
VerifiedAdded on 2022/08/19
|12
|2700
|13
Report
AI Summary
This report, prepared for top management, addresses critical aspects of application security within a company. It begins with an executive summary and table of contents, followed by an introduction outlining the importance of securing applications on-premise and in the cloud. The report analyzes a currently vulnerable application, discussing its weaknesses and vulnerabilities. It then proposes strategies for new application development, including the implementation of IAST tools and hybrid approaches to address future vulnerabilities. The report details how the company's applications address the OWASP Top 10 vulnerabilities, providing guidelines and practices for secure application development. A significant portion is dedicated to explaining threat modeling for a web application running on-premise, outlining the stages of diagramming, threat enumeration, mitigation, and verification. The report concludes with recommendations for strengthening application security, including user input validation, disabling unused functionalities, conducting regular security analyses, investing in cybersecurity training, and implementing a bug reward program. The appendices include the threat model summary and diagrams.

Running head: APPLICATION SECURITY
Application Security
Name of the student:
Name of the university:
Author Note
Application Security
Name of the student:
Name of the university:
Author Note
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

1APPLICATION SECURITY
Executive summary
The AST tools are helpful in many ways like developing the speed, path coverage and ability of
various applications of testing. Tests conducted are able to scale well and is repeatable. For the
current research, the team of information security is to be taken into consideration. A necessity is
there regarding the way how one should ensure that all the applications are running on premise along
with securing the cloud. Moreover, the measures of the latest applications to be created by the team
is evaluated in the study. Thus the following assessment is useful for top managements to understand
how the measures are to be taken along with implementing strategies against any new kind of attack.
Executive summary
The AST tools are helpful in many ways like developing the speed, path coverage and ability of
various applications of testing. Tests conducted are able to scale well and is repeatable. For the
current research, the team of information security is to be taken into consideration. A necessity is
there regarding the way how one should ensure that all the applications are running on premise along
with securing the cloud. Moreover, the measures of the latest applications to be created by the team
is evaluated in the study. Thus the following assessment is useful for top managements to understand
how the measures are to be taken along with implementing strategies against any new kind of attack.

2APPLICATION SECURITY
Table of Contents
Introduction:..........................................................................................................................................3
Discussion on the developed application running currently that is vulnerable to the attacks:..............3
The new application to be developed:...................................................................................................4
New type of vulnerabilities in future:....................................................................................................4
The ways the apps can refer to every vulnerabilities that are listed in the OWASP top10:..................5
The various guidelines and different practices for the secure application development:......................6
Explaining how threat modelling is performed for one web application that continues its running on-
premise:..................................................................................................................................................7
Conclusion:............................................................................................................................................8
References:............................................................................................................................................9
Appendix:............................................................................................................................................11
Appendix1:......................................................................................................................................11
Appendix 2:.....................................................................................................................................11
Table of Contents
Introduction:..........................................................................................................................................3
Discussion on the developed application running currently that is vulnerable to the attacks:..............3
The new application to be developed:...................................................................................................4
New type of vulnerabilities in future:....................................................................................................4
The ways the apps can refer to every vulnerabilities that are listed in the OWASP top10:..................5
The various guidelines and different practices for the secure application development:......................6
Explaining how threat modelling is performed for one web application that continues its running on-
premise:..................................................................................................................................................7
Conclusion:............................................................................................................................................8
References:............................................................................................................................................9
Appendix:............................................................................................................................................11
Appendix1:......................................................................................................................................11
Appendix 2:.....................................................................................................................................11
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

3APPLICATION SECURITY
Introduction:
There are various advantages of utilizing AST tools. This helps in enhancing speed, coverage
paths and efficiency for different testing applications. Here, the tests that are conducted can scale
well and repeatable. As any test case is been developed in the tool that can be expected against
various lines of code having minute incremental expense. In the present study, the information
security team of a business is considered. There is a necessity of how they must assure every apps to
be running on premise and the cloud is been secured. The strategy for the new applications to be
developed by the development team of the business is analyzed. This report is helpful for the top
managements regarding measures taken and strategy for any new type of attacks.
Discussion on the developed application running currently that is vulnerable to
the attacks:
The SAST or Static Application Security Testing tool is at present is at use in the company.
This is similar to the white-box or white-hat testing. Here, the tester understands the information
about the software or system to be used. This involves the architecture diagram, the access towards
the source code and so on. The SAST tool examines the source code at rest for detecting and
reporting the weakness. This leads to the security vulnerabilities (Iskandar et al., 2018). Further, the
source-code analyzer is able to run on the non-complied code for checking the defects like input
validation, numerical errors, path traversals, references, pointers and race conditions. Moreover, the
byte-code and binary analyzers has been performing the same on the compiled and built code. Here,
some of the tools has been running just on the source code and few are just compiled and few on the
both (Alzahrani et al., 2017).
Introduction:
There are various advantages of utilizing AST tools. This helps in enhancing speed, coverage
paths and efficiency for different testing applications. Here, the tests that are conducted can scale
well and repeatable. As any test case is been developed in the tool that can be expected against
various lines of code having minute incremental expense. In the present study, the information
security team of a business is considered. There is a necessity of how they must assure every apps to
be running on premise and the cloud is been secured. The strategy for the new applications to be
developed by the development team of the business is analyzed. This report is helpful for the top
managements regarding measures taken and strategy for any new type of attacks.
Discussion on the developed application running currently that is vulnerable to
the attacks:
The SAST or Static Application Security Testing tool is at present is at use in the company.
This is similar to the white-box or white-hat testing. Here, the tester understands the information
about the software or system to be used. This involves the architecture diagram, the access towards
the source code and so on. The SAST tool examines the source code at rest for detecting and
reporting the weakness. This leads to the security vulnerabilities (Iskandar et al., 2018). Further, the
source-code analyzer is able to run on the non-complied code for checking the defects like input
validation, numerical errors, path traversals, references, pointers and race conditions. Moreover, the
byte-code and binary analyzers has been performing the same on the compiled and built code. Here,
some of the tools has been running just on the source code and few are just compiled and few on the
both (Alzahrani et al., 2017).
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

4APPLICATION SECURITY
The new application to be developed:
In the present situation the IAST or Interactive Application Security Testing and Hybrid
Tools must be developed. The IAST tool is the assimilation of the dynamic and static analysis
technique. Thus they can test whether the vulnerabilities within the code and exploitable actually
within the running application. Moreover, the ISAT tools use the application flow knowledge and
the flow of data for generating the developed attack scenarios and utilize the results of dynamic
results in recursive manner (Stephanow & Khajehmoogahi, 2017). Here, as the dynamic scan has
been done the tool can understanding elements regarding the applications on the basis of how that
reacts to the test cases. There are tools that can utilize the knowledge for creating the extra type of
test cases. This would then retrieve more knowledge for additional test cases and many more.
Further, the IAST tools are adept to reduce the amount of fake positives and function effectively
under the DevOps and Agile scenarios. Here, the conventional stand-alone SAST and DAST tools
are much more time intensive regarding the cycle of development (Alenezi & Javed, 2016).
New type of vulnerabilities in future:
The company can witness the injection of code. This can occur as the attacker is able to send
the untrusted and invalid information application to be the part of query or command. This attacker
also have the malicious intention for tracking application to execute the expected behavior for
collecting data and generate damage. Apart from that, the vulnerabilities of broke authentications
permits attackers n using the automatic or manual measures in gaining control on any accounts in
any systems and total controls. The exposure of sensitive information is the most leading
vulnerability for exploitation. This comprises of attacker consisting data to be secured.
The new application to be developed:
In the present situation the IAST or Interactive Application Security Testing and Hybrid
Tools must be developed. The IAST tool is the assimilation of the dynamic and static analysis
technique. Thus they can test whether the vulnerabilities within the code and exploitable actually
within the running application. Moreover, the ISAT tools use the application flow knowledge and
the flow of data for generating the developed attack scenarios and utilize the results of dynamic
results in recursive manner (Stephanow & Khajehmoogahi, 2017). Here, as the dynamic scan has
been done the tool can understanding elements regarding the applications on the basis of how that
reacts to the test cases. There are tools that can utilize the knowledge for creating the extra type of
test cases. This would then retrieve more knowledge for additional test cases and many more.
Further, the IAST tools are adept to reduce the amount of fake positives and function effectively
under the DevOps and Agile scenarios. Here, the conventional stand-alone SAST and DAST tools
are much more time intensive regarding the cycle of development (Alenezi & Javed, 2016).
New type of vulnerabilities in future:
The company can witness the injection of code. This can occur as the attacker is able to send
the untrusted and invalid information application to be the part of query or command. This attacker
also have the malicious intention for tracking application to execute the expected behavior for
collecting data and generate damage. Apart from that, the vulnerabilities of broke authentications
permits attackers n using the automatic or manual measures in gaining control on any accounts in
any systems and total controls. The exposure of sensitive information is the most leading
vulnerability for exploitation. This comprises of attacker consisting data to be secured.
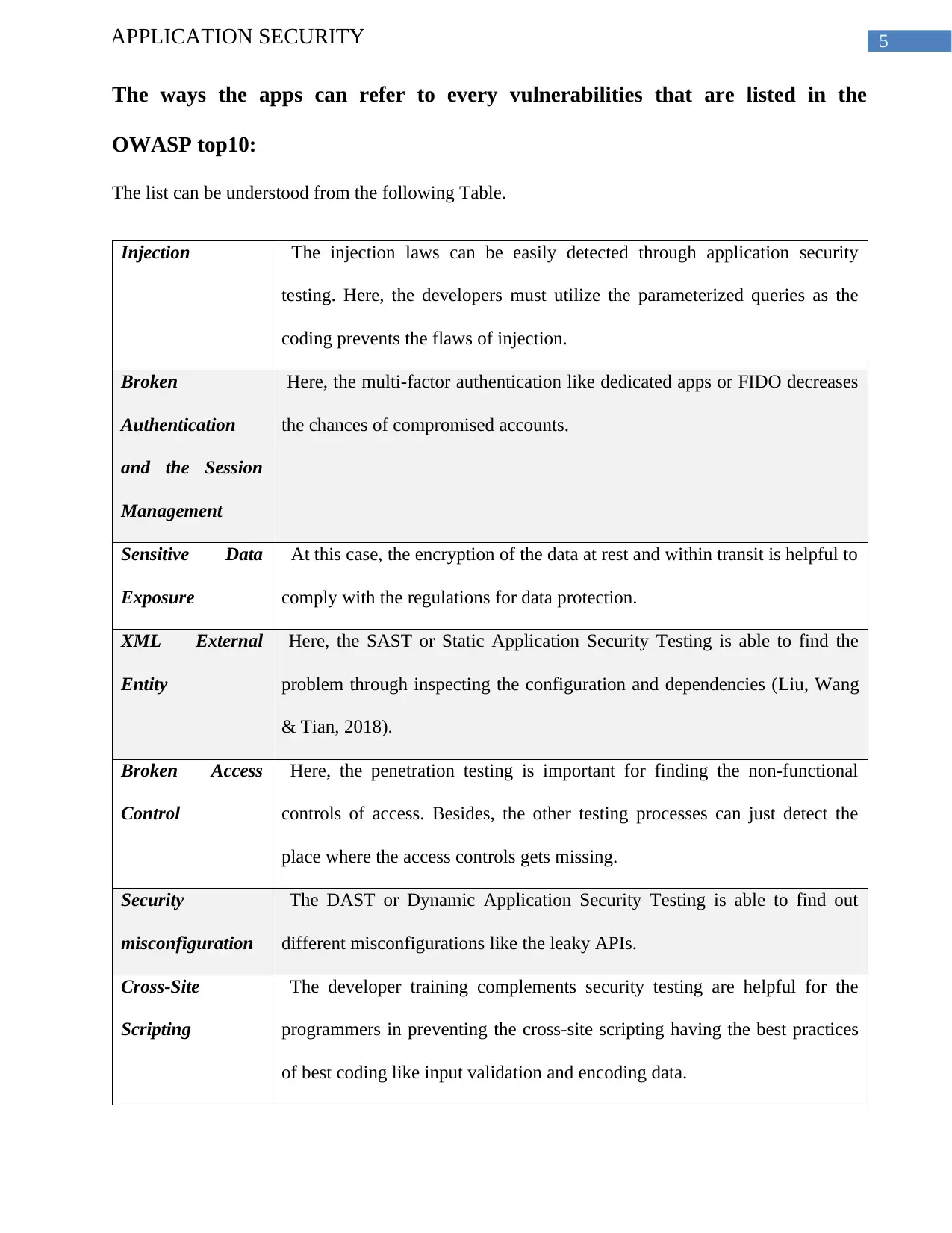
5APPLICATION SECURITY
The ways the apps can refer to every vulnerabilities that are listed in the
OWASP top10:
The list can be understood from the following Table.
Injection The injection laws can be easily detected through application security
testing. Here, the developers must utilize the parameterized queries as the
coding prevents the flaws of injection.
Broken
Authentication
and the Session
Management
Here, the multi-factor authentication like dedicated apps or FIDO decreases
the chances of compromised accounts.
Sensitive Data
Exposure
At this case, the encryption of the data at rest and within transit is helpful to
comply with the regulations for data protection.
XML External
Entity
Here, the SAST or Static Application Security Testing is able to find the
problem through inspecting the configuration and dependencies (Liu, Wang
& Tian, 2018).
Broken Access
Control
Here, the penetration testing is important for finding the non-functional
controls of access. Besides, the other testing processes can just detect the
place where the access controls gets missing.
Security
misconfiguration
The DAST or Dynamic Application Security Testing is able to find out
different misconfigurations like the leaky APIs.
Cross-Site
Scripting
The developer training complements security testing are helpful for the
programmers in preventing the cross-site scripting having the best practices
of best coding like input validation and encoding data.
The ways the apps can refer to every vulnerabilities that are listed in the
OWASP top10:
The list can be understood from the following Table.
Injection The injection laws can be easily detected through application security
testing. Here, the developers must utilize the parameterized queries as the
coding prevents the flaws of injection.
Broken
Authentication
and the Session
Management
Here, the multi-factor authentication like dedicated apps or FIDO decreases
the chances of compromised accounts.
Sensitive Data
Exposure
At this case, the encryption of the data at rest and within transit is helpful to
comply with the regulations for data protection.
XML External
Entity
Here, the SAST or Static Application Security Testing is able to find the
problem through inspecting the configuration and dependencies (Liu, Wang
& Tian, 2018).
Broken Access
Control
Here, the penetration testing is important for finding the non-functional
controls of access. Besides, the other testing processes can just detect the
place where the access controls gets missing.
Security
misconfiguration
The DAST or Dynamic Application Security Testing is able to find out
different misconfigurations like the leaky APIs.
Cross-Site
Scripting
The developer training complements security testing are helpful for the
programmers in preventing the cross-site scripting having the best practices
of best coding like input validation and encoding data.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

6APPLICATION SECURITY
Insecure
deserialization
The tools of application security are able to find the flaws of
deserialization. However, the penetration testing is commonly required for
validating the issues (Ruan & Yan, 2018).
Utilizing elements
with the
vulnerabilities
known
The analysis of software composition conducted as static analysis during
same time can determine the various insecure versions of the elements.
Insufficient
monitoring and
logging
Here, one should be thinking like the attacker and then utilize the pen
testing to seek as one have enough monitoring and investigate the logs after
the pen testing.
The various guidelines and different practices for the secure application
development:
Firstly, the OWSAP Top Ten can be followed. It comprise of the most critical web
application vulnerabilities of security. Here, the security vulnerabilities can target the availability,
integrity and confidentiality of the users, developers and applications (Krasniqi & Bejtullahu, 2018).
Moreover, they cover the attack vectors like sensitive data exposure, security misconfiguration and
session and authentication management and injection attacks. Through getting aware of them, the
ways of coding and working securely, the applications developed stand a better scope of not getting
breached. Then, an application security audit is to be received. Next, there is the implementation of
suitable logging (Monshizadeh, 2017). Furthermore, the real time security protection and monitoring
is to be used. Here, taking into consideration of application security is not complete without
considering WAFs or Web Application firewall and classic firewalls. Moreover, there is encrypting
of everything. Then everything is to be harden. Here, as every data and traffic is been encrypted, one
Insecure
deserialization
The tools of application security are able to find the flaws of
deserialization. However, the penetration testing is commonly required for
validating the issues (Ruan & Yan, 2018).
Utilizing elements
with the
vulnerabilities
known
The analysis of software composition conducted as static analysis during
same time can determine the various insecure versions of the elements.
Insufficient
monitoring and
logging
Here, one should be thinking like the attacker and then utilize the pen
testing to seek as one have enough monitoring and investigate the logs after
the pen testing.
The various guidelines and different practices for the secure application
development:
Firstly, the OWSAP Top Ten can be followed. It comprise of the most critical web
application vulnerabilities of security. Here, the security vulnerabilities can target the availability,
integrity and confidentiality of the users, developers and applications (Krasniqi & Bejtullahu, 2018).
Moreover, they cover the attack vectors like sensitive data exposure, security misconfiguration and
session and authentication management and injection attacks. Through getting aware of them, the
ways of coding and working securely, the applications developed stand a better scope of not getting
breached. Then, an application security audit is to be received. Next, there is the implementation of
suitable logging (Monshizadeh, 2017). Furthermore, the real time security protection and monitoring
is to be used. Here, taking into consideration of application security is not complete without
considering WAFs or Web Application firewall and classic firewalls. Moreover, there is encrypting
of everything. Then everything is to be harden. Here, as every data and traffic is been encrypted, one
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

7APPLICATION SECURITY
require to assure that are hardened enough from the operating systems to the frameworks of software
developments. Apart from that, the servers are to be kept updated. Here, it is effective to be hardened
against present version as the packages are outdated. After that the software is to be updated, besides
the upgrading the third party libraries and application framework. Further, one should be well-aware
of the latest vulnerabilities. It is tied strongly to the prior points (Lee & Yang, 2017). Various vectors
like SQL injection, code injection, cross-site scripting, insecure reference of direct object, forgery of
cross-site request is complicated for staying abreast and understand that the latest ones are.
Ultimately, it must be kept in mind that one should never stop learning. One can be all over the
present threats witnessed by the industry and that never indicate that the latest threats are discovered
and coming.
Explaining how threat modelling is performed for one web application that
continues its running on-premise:
It has consisted to four primary stages. Firstly, there is the diagramming denoting on what
people are working. Secondly, there is the threat enumeration regarding what could be going wrong.
Thirdly, there mitigation indicating what are going to be done about that. Lastly, there is verification
indicating whether has done a good job. The threat modelling stated with diagramming as it has been
simplest method for communicating with the others regarding how the system is developed. Here,
the diagrams are easy to analyse maximum and for the popular diagrams utilized are DFD or data
flow diagrams. As the diagrams got ready, every parties involved in that looked that them from the
point of view of the attacker (Shuaibu & Ibrahim, 2017). Apart from that, the detailed level of threat
mitigation comprised of numerous techniques and tools helping to cover threat categories and then
meet the requirements of software security. Further, the verification helps to assure that the
mitigation is efficient. Here, for instance, as the threat modelling for the web applications, the
require to assure that are hardened enough from the operating systems to the frameworks of software
developments. Apart from that, the servers are to be kept updated. Here, it is effective to be hardened
against present version as the packages are outdated. After that the software is to be updated, besides
the upgrading the third party libraries and application framework. Further, one should be well-aware
of the latest vulnerabilities. It is tied strongly to the prior points (Lee & Yang, 2017). Various vectors
like SQL injection, code injection, cross-site scripting, insecure reference of direct object, forgery of
cross-site request is complicated for staying abreast and understand that the latest ones are.
Ultimately, it must be kept in mind that one should never stop learning. One can be all over the
present threats witnessed by the industry and that never indicate that the latest threats are discovered
and coming.
Explaining how threat modelling is performed for one web application that
continues its running on-premise:
It has consisted to four primary stages. Firstly, there is the diagramming denoting on what
people are working. Secondly, there is the threat enumeration regarding what could be going wrong.
Thirdly, there mitigation indicating what are going to be done about that. Lastly, there is verification
indicating whether has done a good job. The threat modelling stated with diagramming as it has been
simplest method for communicating with the others regarding how the system is developed. Here,
the diagrams are easy to analyse maximum and for the popular diagrams utilized are DFD or data
flow diagrams. As the diagrams got ready, every parties involved in that looked that them from the
point of view of the attacker (Shuaibu & Ibrahim, 2017). Apart from that, the detailed level of threat
mitigation comprised of numerous techniques and tools helping to cover threat categories and then
meet the requirements of software security. Further, the verification helps to assure that the
mitigation is efficient. Here, for instance, as the threat modelling for the web applications, the

8APPLICATION SECURITY
primary type of threat is every time mitigated and identified are the effective vulnerabilities of web
applications. As the threat enumeration goes on one might notice that the web application has been
open to the attacks of SQL Injection, the cross-site scripting and also many more (Dang & Dang,
2019). Nevertheless, here the users has also utilized the weak passwords to expose the systems under
attacks. Next, one must utilize the “web application vulnerability scanner” for thinking similar to the
attacker and then attempt for seeking vulnerabilities. During the stages of mitigation and the
verification, the total web security solution like Acunetix might help to control challenges for
checking whether they are solved. Though the tools are unable to cover every threats, this is one of
the important element for the threat mitigation and enumeration for the currently running web
application (Kong, 2016).
Conclusion:
It must be concluded by saying there are many measures to be considered while developing
application security. Firstly, one must never keep trust on the input of the users. Next, the unused
functionalities are to be disabled. Here, leaving those type of functionalities present enhances the
surface of the attack of the application. Next, regular security analysis are to be conducted. Contracts
must be established with any independent organization who are unfamiliar with systems and
infrastructures. This would make them think differently and then examine the vulnerabilities that
have glossed over. Further, one should invest on the cyber-security training that is ongoing. Lastly, a
bug reward program can be created. Through providing the monetary and additional rewards to
present researchers privately disclosing the vulnerabilities can put the team ahead of the curve in
securing the effective attacks.
primary type of threat is every time mitigated and identified are the effective vulnerabilities of web
applications. As the threat enumeration goes on one might notice that the web application has been
open to the attacks of SQL Injection, the cross-site scripting and also many more (Dang & Dang,
2019). Nevertheless, here the users has also utilized the weak passwords to expose the systems under
attacks. Next, one must utilize the “web application vulnerability scanner” for thinking similar to the
attacker and then attempt for seeking vulnerabilities. During the stages of mitigation and the
verification, the total web security solution like Acunetix might help to control challenges for
checking whether they are solved. Though the tools are unable to cover every threats, this is one of
the important element for the threat mitigation and enumeration for the currently running web
application (Kong, 2016).
Conclusion:
It must be concluded by saying there are many measures to be considered while developing
application security. Firstly, one must never keep trust on the input of the users. Next, the unused
functionalities are to be disabled. Here, leaving those type of functionalities present enhances the
surface of the attack of the application. Next, regular security analysis are to be conducted. Contracts
must be established with any independent organization who are unfamiliar with systems and
infrastructures. This would make them think differently and then examine the vulnerabilities that
have glossed over. Further, one should invest on the cyber-security training that is ongoing. Lastly, a
bug reward program can be created. Through providing the monetary and additional rewards to
present researchers privately disclosing the vulnerabilities can put the team ahead of the curve in
securing the effective attacks.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

9APPLICATION SECURITY
References:
Alenezi, M., & Javed, Y. (2016, September). Open source web application security: A static analysis
approach. In 2016 International Conference on Engineering & MIS (ICEMIS) (pp. 1-5).
IEEE.
Alzahrani, A., Alqazzaz, A., Zhu, Y., Fu, H., & Almashfi, N. (2017, May). Web application security
tools analysis. In 2017 ieee 3rd international conference on big data security on cloud
(bigdatasecurity), ieee international conference on high performance and smart computing
(hpsc), and ieee international conference on intelligent data and security (ids) (pp. 237-242).
IEEE.
Dang, T. T., & Dang, T. K. (2019). A visual model for web applications security monitoring. arXiv
preprint arXiv:1904.03320.
Iskandar, A., Tuasamu, M. R. F., Syamsu, S., Mansyur, M., Listyorini, T., Sallu, S., ... & Rahim, R.
(2018, September). Web based testing application security system using semantic
comparison method. In IOP Conference Series: Materials Science and Engineering (Vol.
420, No. 1, p. 012122). IOP Publishing.
Kong, F. (2016). Research on Security Technology based on WEB Application.
Krasniqi, G., & Bejtullahu, V. (2018). Vulnerability Assessment & Penetration Testing: Case study
on web application security.
Lee, H. Y., & Yang, H. S. (2017). Construction of Security Evaluation Criteria for Web Application
Firewall. Journal of digital Convergence, 15(5), 197-205.
References:
Alenezi, M., & Javed, Y. (2016, September). Open source web application security: A static analysis
approach. In 2016 International Conference on Engineering & MIS (ICEMIS) (pp. 1-5).
IEEE.
Alzahrani, A., Alqazzaz, A., Zhu, Y., Fu, H., & Almashfi, N. (2017, May). Web application security
tools analysis. In 2017 ieee 3rd international conference on big data security on cloud
(bigdatasecurity), ieee international conference on high performance and smart computing
(hpsc), and ieee international conference on intelligent data and security (ids) (pp. 237-242).
IEEE.
Dang, T. T., & Dang, T. K. (2019). A visual model for web applications security monitoring. arXiv
preprint arXiv:1904.03320.
Iskandar, A., Tuasamu, M. R. F., Syamsu, S., Mansyur, M., Listyorini, T., Sallu, S., ... & Rahim, R.
(2018, September). Web based testing application security system using semantic
comparison method. In IOP Conference Series: Materials Science and Engineering (Vol.
420, No. 1, p. 012122). IOP Publishing.
Kong, F. (2016). Research on Security Technology based on WEB Application.
Krasniqi, G., & Bejtullahu, V. (2018). Vulnerability Assessment & Penetration Testing: Case study
on web application security.
Lee, H. Y., & Yang, H. S. (2017). Construction of Security Evaluation Criteria for Web Application
Firewall. Journal of digital Convergence, 15(5), 197-205.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

10APPLICATION SECURITY
Liu, Y., Wang, Z., & Tian, S. (2018, August). Security Against Network Attacks on Web
Application System. In China Cyber Security Annual Conference (pp. 145-152). Springer,
Singapore.
Monshizadeh, M. (2017). Inferring Specifications for Web Application Security (Doctoral
dissertation).
Ruan, Y. L., & Yan, X. Q. (2018). Research on Key Technology of Web Application Security Test
Platform. DEStech Transactions on Social Science, Education and Human Science, (emss).
Shuaibu, M. B., & Ibrahim, R. A. (2017, November). Web application development model with
security concern in the entire life-cycle. In 2017 4th IEEE International Conference on
Engineering Technologies and Applied Sciences (ICETAS) (pp. 1-6). IEEE.
Stephanow, P., & Khajehmoogahi, K. (2017, March). Towards continuous security certification of
software-as-a-service applications using web application testing techniques. In 2017 IEEE
31st International Conference on Advanced Information Networking and Applications
(AINA) (pp. 931-938). IEEE.
Liu, Y., Wang, Z., & Tian, S. (2018, August). Security Against Network Attacks on Web
Application System. In China Cyber Security Annual Conference (pp. 145-152). Springer,
Singapore.
Monshizadeh, M. (2017). Inferring Specifications for Web Application Security (Doctoral
dissertation).
Ruan, Y. L., & Yan, X. Q. (2018). Research on Key Technology of Web Application Security Test
Platform. DEStech Transactions on Social Science, Education and Human Science, (emss).
Shuaibu, M. B., & Ibrahim, R. A. (2017, November). Web application development model with
security concern in the entire life-cycle. In 2017 4th IEEE International Conference on
Engineering Technologies and Applied Sciences (ICETAS) (pp. 1-6). IEEE.
Stephanow, P., & Khajehmoogahi, K. (2017, March). Towards continuous security certification of
software-as-a-service applications using web application testing techniques. In 2017 IEEE
31st International Conference on Advanced Information Networking and Applications
(AINA) (pp. 931-938). IEEE.
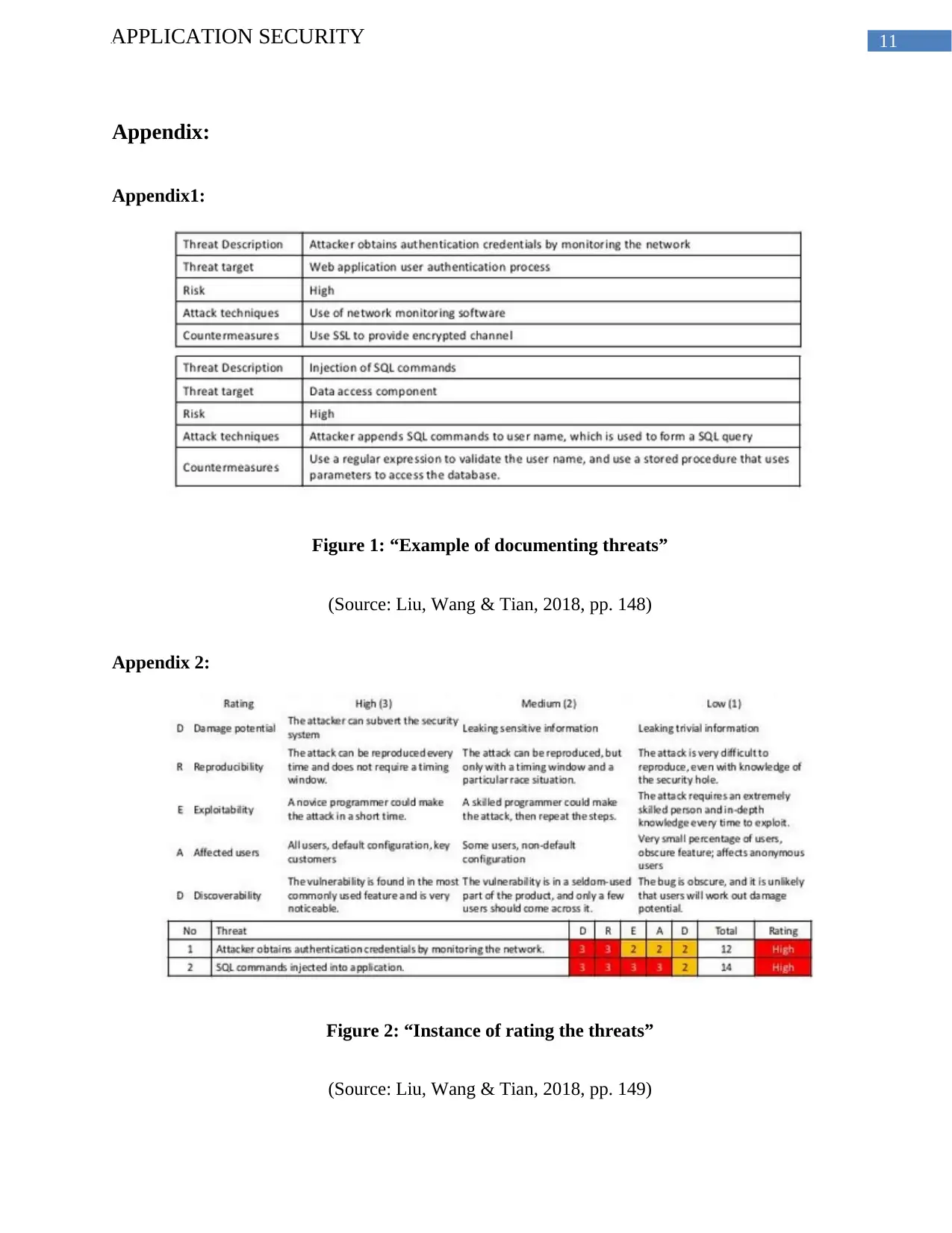
11APPLICATION SECURITY
Appendix:
Appendix1:
Figure 1: “Example of documenting threats”
(Source: Liu, Wang & Tian, 2018, pp. 148)
Appendix 2:
Figure 2: “Instance of rating the threats”
(Source: Liu, Wang & Tian, 2018, pp. 149)
Appendix:
Appendix1:
Figure 1: “Example of documenting threats”
(Source: Liu, Wang & Tian, 2018, pp. 148)
Appendix 2:
Figure 2: “Instance of rating the threats”
(Source: Liu, Wang & Tian, 2018, pp. 149)
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 12
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.




