Applied Research: Data Security in Cloud Computing - Methodology
VerifiedAdded on 2020/04/01
|12
|2956
|40
Report
AI Summary
This report focuses on the methodology for studying data security in cloud computing. The research identifies the problem statement, reorganizes collected literature, and describes the chosen quantitative methodology. It reviews existing methodologies, analyzes sub-problems related to data protection and security/privacy issues, and assesses their relevance. The report proposes a methodology, justifying its use and outlining its benefits and limitations. The research emphasizes the importance of encryption and addressing the challenges in cloud computing to safeguard data from unauthorized access and ensure data integrity and availability. The report also includes a review of existing technologies and a framework for the proposed methodology.

Applied research 1
Security of the data security
Name
Course
Professor
School
City
Date
Security of the data security
Name
Course
Professor
School
City
Date
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Applied research 2
Table of Contents
Table i: The table highlights the reorganization of the literature that is collected..................4
Table ii: The summary of reviewed technology...........................................................................9
Figure i: Framework of the methodology...................................................................................11
Chapter 1 Methodology
1.1 Research problem and Reorganized Collected Literature
1.1.1 Research problem statement........................................................................................2
1.1.2 Reorganized Collected Literature................................................................................3
1.2 Types of methodologies...........................................................................................................4
1.2.1 Compare and contrast of methodologies.....................................................................5
1.2. 2 Type of chosen methodology.......................................................................................6
1.3 Review, Analysis, and summary of existing methodologies.................................................6
1.3.1 Selection of sub problem...............................................................................................6
1.3.2 Analysis of the selected methodologies........................................................................6
1.3.3 Relevance of the research problem..............................................................................8
1.3.4 Summary of the reviewed technology..........................................................................8
1.4 Proposed methodology............................................................................................................9
1.4.1 Justification of the methodology..................................................................................9
1.4.2 Benefits and limitations of methodology.....................................................................9
1.4.3 Framework and Explanation.....................................................................................10
References......................................................................................................................................11
Table of Contents
Table i: The table highlights the reorganization of the literature that is collected..................4
Table ii: The summary of reviewed technology...........................................................................9
Figure i: Framework of the methodology...................................................................................11
Chapter 1 Methodology
1.1 Research problem and Reorganized Collected Literature
1.1.1 Research problem statement........................................................................................2
1.1.2 Reorganized Collected Literature................................................................................3
1.2 Types of methodologies...........................................................................................................4
1.2.1 Compare and contrast of methodologies.....................................................................5
1.2. 2 Type of chosen methodology.......................................................................................6
1.3 Review, Analysis, and summary of existing methodologies.................................................6
1.3.1 Selection of sub problem...............................................................................................6
1.3.2 Analysis of the selected methodologies........................................................................6
1.3.3 Relevance of the research problem..............................................................................8
1.3.4 Summary of the reviewed technology..........................................................................8
1.4 Proposed methodology............................................................................................................9
1.4.1 Justification of the methodology..................................................................................9
1.4.2 Benefits and limitations of methodology.....................................................................9
1.4.3 Framework and Explanation.....................................................................................10
References......................................................................................................................................11

Applied research 3
Chapter 1 Methodology
The intent behind this project 3 is determining on the methodology for the study. My study
subject is security of the data on the cloud computing. In the task 2 I would do a literature
evaluate and in this I would certainly examine the methods as well as the problems and try
identifying on the appropriate solutions to the case issues. This assignment is divided into
various tasks. The research is structured as follows. On the first assessment is to identify the
research problems,
And reorganize collected data. The other task would be to describe the methodology of the
research as well as the type of the methodology which will be used for the research. Another task
which would be analyzed is the review of the existing methodologies this would be done through
selection of sub-problem, analysis and the relevance of the research problem. The last task would
be to propose the methodology by identification and justification, as well as benefits and
limitations.
1.1 Research problem and Reorganized Collected Literature
1.1.1 Research problem statement
This research for my research is on the security of data on cloud computing. There are several
research with regards to the security of the cloud computing (Kaufman, 2009). The major
research focus has been the security techniques for protecting on the data in the cloud computing.
There is also overview of the data security and the Privacy security concerns in the cloud
computing. These are the major research article which my previous literature review focused on.
My research encounters some problem which are related to various elements. The process of the
data security in the cloud computing has various challenges (Kaufman, 2009). One of the major
concern is the aspect of confidentiality. The question which could arise are all the cloud
Chapter 1 Methodology
The intent behind this project 3 is determining on the methodology for the study. My study
subject is security of the data on the cloud computing. In the task 2 I would do a literature
evaluate and in this I would certainly examine the methods as well as the problems and try
identifying on the appropriate solutions to the case issues. This assignment is divided into
various tasks. The research is structured as follows. On the first assessment is to identify the
research problems,
And reorganize collected data. The other task would be to describe the methodology of the
research as well as the type of the methodology which will be used for the research. Another task
which would be analyzed is the review of the existing methodologies this would be done through
selection of sub-problem, analysis and the relevance of the research problem. The last task would
be to propose the methodology by identification and justification, as well as benefits and
limitations.
1.1 Research problem and Reorganized Collected Literature
1.1.1 Research problem statement
This research for my research is on the security of data on cloud computing. There are several
research with regards to the security of the cloud computing (Kaufman, 2009). The major
research focus has been the security techniques for protecting on the data in the cloud computing.
There is also overview of the data security and the Privacy security concerns in the cloud
computing. These are the major research article which my previous literature review focused on.
My research encounters some problem which are related to various elements. The process of the
data security in the cloud computing has various challenges (Kaufman, 2009). One of the major
concern is the aspect of confidentiality. The question which could arise are all the cloud
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
Applied research 4
computing technologies protected from the breach? There is need to carry out a security test
which could be done to protect on the data from the malicious authorized users for example the
cross-site scripting, but the issue which could arise is that do all organization do the security
test.
Other challenge is the aspect of integrity to offer the security to the data of the client. Moreover,
the research has been faced with the aspect of availability which has been a significant issues
when it comes to the downtime which has been facing my organization.
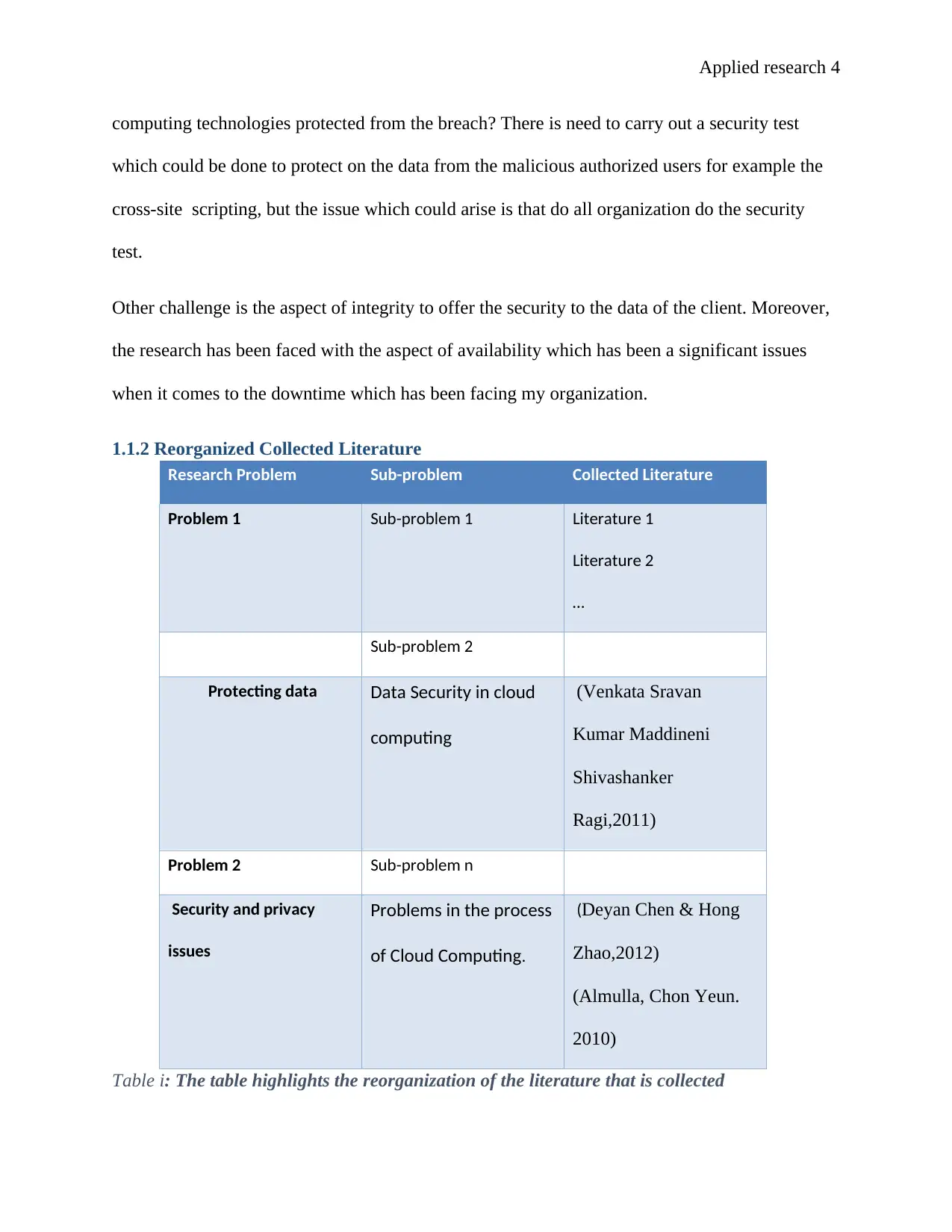
1.1.2 Reorganized Collected Literature
Research Problem Sub-problem Collected Literature
Problem 1 Sub-problem 1 Literature 1
Literature 2
…
Sub-problem 2
Protecting data Data Security in cloud
computing
(Venkata Sravan
Kumar Maddineni
Shivashanker
Ragi,2011)
Problem 2 Sub-problem n
Security and privacy
issues
Problems in the process
of Cloud Computing.
(Deyan Chen & Hong
Zhao,2012)
(Almulla, Chon Yeun.
2010)
Table i: The table highlights the reorganization of the literature that is collected
computing technologies protected from the breach? There is need to carry out a security test
which could be done to protect on the data from the malicious authorized users for example the
cross-site scripting, but the issue which could arise is that do all organization do the security
test.
Other challenge is the aspect of integrity to offer the security to the data of the client. Moreover,
the research has been faced with the aspect of availability which has been a significant issues
when it comes to the downtime which has been facing my organization.
1.1.2 Reorganized Collected Literature
Research Problem Sub-problem Collected Literature
Problem 1 Sub-problem 1 Literature 1
Literature 2
…
Sub-problem 2
Protecting data Data Security in cloud
computing
(Venkata Sravan
Kumar Maddineni
Shivashanker
Ragi,2011)
Problem 2 Sub-problem n
Security and privacy
issues
Problems in the process
of Cloud Computing.
(Deyan Chen & Hong
Zhao,2012)
(Almulla, Chon Yeun.
2010)
Table i: The table highlights the reorganization of the literature that is collected
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Applied research 5
1.2 Types of methodologies
Quantitative vs. qualitative
Both qualitative and quantitative models try to illustrate a certain behavior, but the former
mathematical and the latter is descriptive.
Quantitative research
As the name suggests, quantitative research is interpreted as the organized empirical exploration
of phenomena which are considered to be social through computational, mathematical, or
statistical techniques (Zissis and Lekkas, 2012). The main target of this is to develop and make
use of hypothesis and theories, mathematical models that are linked to phenomena. The main
purpose of this is to predict behavior by identifying several patterns.
Qualitative research
Qualitative research is illustrated as the examination, interpretation of observation and analysis
for the purpose of identifying further meanings and also the relationship patterns, this may need a
classification of entities and phenomena, where mathematical models are not involved in the case
(Zissis and Lekkas, 2012). Qualitative research is frequently used in the in the social science to
gain a better understanding of such things as meaning and intentionality.
1.2.1 Compare and contrast of methodologies
The qualitative along with the quantitative investigations usually are combined to provide the
general picture. The quantitative methodology could be utilized to plug the gaps which is present
in the qualitative research that occurs since the researcher might be a lot more in one place at any
one particular period.
1.2 Types of methodologies
Quantitative vs. qualitative
Both qualitative and quantitative models try to illustrate a certain behavior, but the former
mathematical and the latter is descriptive.
Quantitative research
As the name suggests, quantitative research is interpreted as the organized empirical exploration
of phenomena which are considered to be social through computational, mathematical, or
statistical techniques (Zissis and Lekkas, 2012). The main target of this is to develop and make
use of hypothesis and theories, mathematical models that are linked to phenomena. The main
purpose of this is to predict behavior by identifying several patterns.
Qualitative research
Qualitative research is illustrated as the examination, interpretation of observation and analysis
for the purpose of identifying further meanings and also the relationship patterns, this may need a
classification of entities and phenomena, where mathematical models are not involved in the case
(Zissis and Lekkas, 2012). Qualitative research is frequently used in the in the social science to
gain a better understanding of such things as meaning and intentionality.
1.2.1 Compare and contrast of methodologies
The qualitative along with the quantitative investigations usually are combined to provide the
general picture. The quantitative methodology could be utilized to plug the gaps which is present
in the qualitative research that occurs since the researcher might be a lot more in one place at any
one particular period.

Applied research 6
Utilizing of both the qualitative and the qualitative research could offer a meaning when it comes
to the bridging of the macro and the micro gulf (Zissis and Lekkas, 2012). The qualitative study
might tap into big scale structural facets of the social life while the qualitative study generally
address the small scale behavioural aspects.
The qualitative research usually facilitates on the quantitative research and the vice versa. The
qualitative research could help in providing the background information on any context or the
subject (Subashini and Kavitha, 2011). Moreover, it acts as the source for the hypotheses, aid on
the scale for the construction and the qualitative helps in the choices of the subject used in the
qualitative research.
Despite the two approaches complimenting each other there are clear differences which exists
between them (Takabi, Joshi and Ahn, 2010). The quantitative research usually focus on the
numbers as well as the quantities. Its important to understand that the quantitative studies usually
have the results which are based on the numeric analysis as well as the statistics (Subashini and
Kavitha, 2011). The studies have many participants. On the other hand when it comes to the
qualitative research methodologies it more focused on the differences which exists in the quality,
rather than focusing on the differences in quality (Zissis and Lekkas, 2012). The results are
usually word which are on the pictures rather than the numbers. This methodology has fewer
participants.
The qualitative approach usually tends to be more of open-ended questions and it probes detailed
information which illustrates nuances as well as highlighting on the diversity. On the other hand
quantitative methodologies has a specific questions to which predetermined responses are
obtained to standardize these questions.
Utilizing of both the qualitative and the qualitative research could offer a meaning when it comes
to the bridging of the macro and the micro gulf (Zissis and Lekkas, 2012). The qualitative study
might tap into big scale structural facets of the social life while the qualitative study generally
address the small scale behavioural aspects.
The qualitative research usually facilitates on the quantitative research and the vice versa. The
qualitative research could help in providing the background information on any context or the
subject (Subashini and Kavitha, 2011). Moreover, it acts as the source for the hypotheses, aid on
the scale for the construction and the qualitative helps in the choices of the subject used in the
qualitative research.
Despite the two approaches complimenting each other there are clear differences which exists
between them (Takabi, Joshi and Ahn, 2010). The quantitative research usually focus on the
numbers as well as the quantities. Its important to understand that the quantitative studies usually
have the results which are based on the numeric analysis as well as the statistics (Subashini and
Kavitha, 2011). The studies have many participants. On the other hand when it comes to the
qualitative research methodologies it more focused on the differences which exists in the quality,
rather than focusing on the differences in quality (Zissis and Lekkas, 2012). The results are
usually word which are on the pictures rather than the numbers. This methodology has fewer
participants.
The qualitative approach usually tends to be more of open-ended questions and it probes detailed
information which illustrates nuances as well as highlighting on the diversity. On the other hand
quantitative methodologies has a specific questions to which predetermined responses are
obtained to standardize these questions.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

Applied research 7
1.2. 2 Type of chosen methodology
In this research I am utilizing the quantitative methodology since it will help in predicting
behavior by identification of certain pattern thus will help to curb the problem of losing data.
Through this methodology, it will be much safer to store data since no one can access the data
except the admin.
1.3 Review, Analysis, and summary of existing methodologies
1.3.1 Selection of sub problem
There are so many issues related to security of data on cloud computing. However, my major
concern will be the issue on the problem on the process of cloud computing (Chen and Zhao,
2012). Though cloud computing came with promises that it would result in low cost, and also
more agile IT would be fostered, at first people thought that moving the application to the cloud
would solve their problems. However, at the end of the month, others would receive a bill and
start wondering how this could happen. As a result of organization building cloud architecture,
where new services and technologies are plugged in, it is realized that some data is getting
distorted and may easily be accessed by analytic professionals who end up dicing the information
and slice it.
1.3.2 Analysis of the selected methodologies
Data protection
In my first paper on the research, it is based on the protection of data. Within an environment
that is virtual, several virtual machines are in a single physical system where they are housed
together. However, this condition is normally referred to as multi-tenancy. For the purpose of
maintaining segmentation and isolation among machines that are virtual, we used a software
known as a hypervisor (Wang, Li, Ren and Lou, 2009). Luckily, there are some data hiding
methods that emerge for cloud environments. Encryption is used as the first option of protecting
1.2. 2 Type of chosen methodology
In this research I am utilizing the quantitative methodology since it will help in predicting
behavior by identification of certain pattern thus will help to curb the problem of losing data.
Through this methodology, it will be much safer to store data since no one can access the data
except the admin.
1.3 Review, Analysis, and summary of existing methodologies
1.3.1 Selection of sub problem
There are so many issues related to security of data on cloud computing. However, my major
concern will be the issue on the problem on the process of cloud computing (Chen and Zhao,
2012). Though cloud computing came with promises that it would result in low cost, and also
more agile IT would be fostered, at first people thought that moving the application to the cloud
would solve their problems. However, at the end of the month, others would receive a bill and
start wondering how this could happen. As a result of organization building cloud architecture,
where new services and technologies are plugged in, it is realized that some data is getting
distorted and may easily be accessed by analytic professionals who end up dicing the information
and slice it.
1.3.2 Analysis of the selected methodologies
Data protection
In my first paper on the research, it is based on the protection of data. Within an environment
that is virtual, several virtual machines are in a single physical system where they are housed
together. However, this condition is normally referred to as multi-tenancy. For the purpose of
maintaining segmentation and isolation among machines that are virtual, we used a software
known as a hypervisor (Wang, Li, Ren and Lou, 2009). Luckily, there are some data hiding
methods that emerge for cloud environments. Encryption is used as the first option of protecting
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Applied research 8
the data in cloud, organizations are therefore helped by a number of modern alternatives and
tools to effectively manage these encryption keys, authorization, and authentication, policies
related to protection of information and data in the cloud environments in which systems and
data are dynamically moved across other platform as well as data centers that are distinct
(Takabi, Joshi and Ahn, 2010).
The following are options used for encrypting data that reduce the need to design the
applications in a different way and re-architect system and design of a network (Kandukuri and
Rakshit, 2009). One is the volume-based encryption; this means that when the volume of storage
is removed or go offline mode, one could not access data without the encryption keys because it
is already encrypted.
File encryption is considered to be one of the most flexible encryption types that are mainly use
within cloud environment as well as virtualized (Feng, Zhang, Zhang and Xu, 2011). At the
source is where the encryption is applied, where they are managed by third parties or the
customers who are believed to be the proxies for this reason.
Security and privacy issue
Cloud computing is referred to as state of art technological innovation which helps in providing
a variety of benefits for various types of organization such governmental ones and those that are
medium sized (Krutz and Vines, 2010). There are various large organizations that apply this state
of the art to carry out their business processes, otherwise, if they would not have embraced this
art large storage capacity expensive hardware and computational power would be required.
the data in cloud, organizations are therefore helped by a number of modern alternatives and
tools to effectively manage these encryption keys, authorization, and authentication, policies
related to protection of information and data in the cloud environments in which systems and
data are dynamically moved across other platform as well as data centers that are distinct
(Takabi, Joshi and Ahn, 2010).
The following are options used for encrypting data that reduce the need to design the
applications in a different way and re-architect system and design of a network (Kandukuri and
Rakshit, 2009). One is the volume-based encryption; this means that when the volume of storage
is removed or go offline mode, one could not access data without the encryption keys because it
is already encrypted.
File encryption is considered to be one of the most flexible encryption types that are mainly use
within cloud environment as well as virtualized (Feng, Zhang, Zhang and Xu, 2011). At the
source is where the encryption is applied, where they are managed by third parties or the
customers who are believed to be the proxies for this reason.
Security and privacy issue
Cloud computing is referred to as state of art technological innovation which helps in providing
a variety of benefits for various types of organization such governmental ones and those that are
medium sized (Krutz and Vines, 2010). There are various large organizations that apply this state
of the art to carry out their business processes, otherwise, if they would not have embraced this
art large storage capacity expensive hardware and computational power would be required.
Applied research 9
In other words, novels are introduced by this technological advent as a way of information
leakage and also classified data of the user and issues of privacy since data is kept and moved to
the cloud and even it may go across the borders.
1.3.3 Relevance of the research problem
In the first problem addressed in my research it clear that it is relevant as it was focusing on the
protection of the data where encryption was used by the organization to safeguard their data.
On the second issue discussed in my research paper is the issue of security and privacy
(Dikaiakos, Katsaros, Mehra, Pallis and Vakali, 2009). This state of the art technology that
applied to businesses to carry out their daily businesses otherwise they would end up spending
more capital and large space.
1.3.4 Summary of the reviewed technology
Literature Research
problem
Methodology Your sub
problem
Relevance
Literature 1 Protection of
data
quantitative Data security in
cloud computing
Very relevant
Literature 2 Security and
privacy issue
quantitative Problems
associated in the
process of cloud
computing
Strongly
relevant
Table ii: The summary of reviewed technology
1.4 Proposed methodology
In this section, there is a methodology that I am purposed which is quantitative methodology. I
selected some papers that are relevant to my topic concerning the security issue in cloud
In other words, novels are introduced by this technological advent as a way of information
leakage and also classified data of the user and issues of privacy since data is kept and moved to
the cloud and even it may go across the borders.
1.3.3 Relevance of the research problem
In the first problem addressed in my research it clear that it is relevant as it was focusing on the
protection of the data where encryption was used by the organization to safeguard their data.
On the second issue discussed in my research paper is the issue of security and privacy
(Dikaiakos, Katsaros, Mehra, Pallis and Vakali, 2009). This state of the art technology that
applied to businesses to carry out their daily businesses otherwise they would end up spending
more capital and large space.
1.3.4 Summary of the reviewed technology
Literature Research
problem
Methodology Your sub
problem
Relevance
Literature 1 Protection of
data
quantitative Data security in
cloud computing
Very relevant
Literature 2 Security and
privacy issue
quantitative Problems
associated in the
process of cloud
computing
Strongly
relevant
Table ii: The summary of reviewed technology
1.4 Proposed methodology
In this section, there is a methodology that I am purposed which is quantitative methodology. I
selected some papers that are relevant to my topic concerning the security issue in cloud
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
Applied research 10
computing. The papers I researched on were relevant to the problem statement that I intended to
explain in my research.
1.4.1 Justification of the methodology
As I stated earlier in my research, it is clear that I wanted to focus my research on the
quantitative methodology. Quantitative methodology is interpreted as an organized empirical
exploration of phenomena which are hence considered to be social through computation.
1.4.2 Benefits and limitations of methodology
Benefits
Objectivity, it is viewed as numerical, therefore, they cannot be misinterpreted. Consequently,
they can’t be easily misinterpreted. This permits one to examine the similar circumstance to
understand the investigation with similar quantitative technique (Jensen, Schwenk, Gruschka and
Iacono, 2009). It is also possible to compare its results.
In quantitative study, a statistical technique utilizes a statistical method where you are giving a
chance to utilize the statistical approach (Wang, Ren and Lou, 2010). A great deal of essential
attribute of data is understood through the use of this type of statistical data.
Additionally there is fast data collection through the application of justifiable random models,
and a survey can immediately be generalized to the residents at the whole.
Limitations of quantitative methodology
A huge sample of the population is needed, when using this type of methodology you need to go
round and get comments from a huge population (Popović and Hocenski, 2010).
When utilizing this type of study, you need to make sure that you are financially ready. Because
you need a huge number of correspondents, you need to devote more cash for printing the
computing. The papers I researched on were relevant to the problem statement that I intended to
explain in my research.
1.4.1 Justification of the methodology
As I stated earlier in my research, it is clear that I wanted to focus my research on the
quantitative methodology. Quantitative methodology is interpreted as an organized empirical
exploration of phenomena which are hence considered to be social through computation.
1.4.2 Benefits and limitations of methodology
Benefits
Objectivity, it is viewed as numerical, therefore, they cannot be misinterpreted. Consequently,
they can’t be easily misinterpreted. This permits one to examine the similar circumstance to
understand the investigation with similar quantitative technique (Jensen, Schwenk, Gruschka and
Iacono, 2009). It is also possible to compare its results.
In quantitative study, a statistical technique utilizes a statistical method where you are giving a
chance to utilize the statistical approach (Wang, Ren and Lou, 2010). A great deal of essential
attribute of data is understood through the use of this type of statistical data.
Additionally there is fast data collection through the application of justifiable random models,
and a survey can immediately be generalized to the residents at the whole.
Limitations of quantitative methodology
A huge sample of the population is needed, when using this type of methodology you need to go
round and get comments from a huge population (Popović and Hocenski, 2010).
When utilizing this type of study, you need to make sure that you are financially ready. Because
you need a huge number of correspondents, you need to devote more cash for printing the
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
Applied research 11
questionnaire, transport expenses along with a much more. This really is more expensive when
compared with qualitative study.
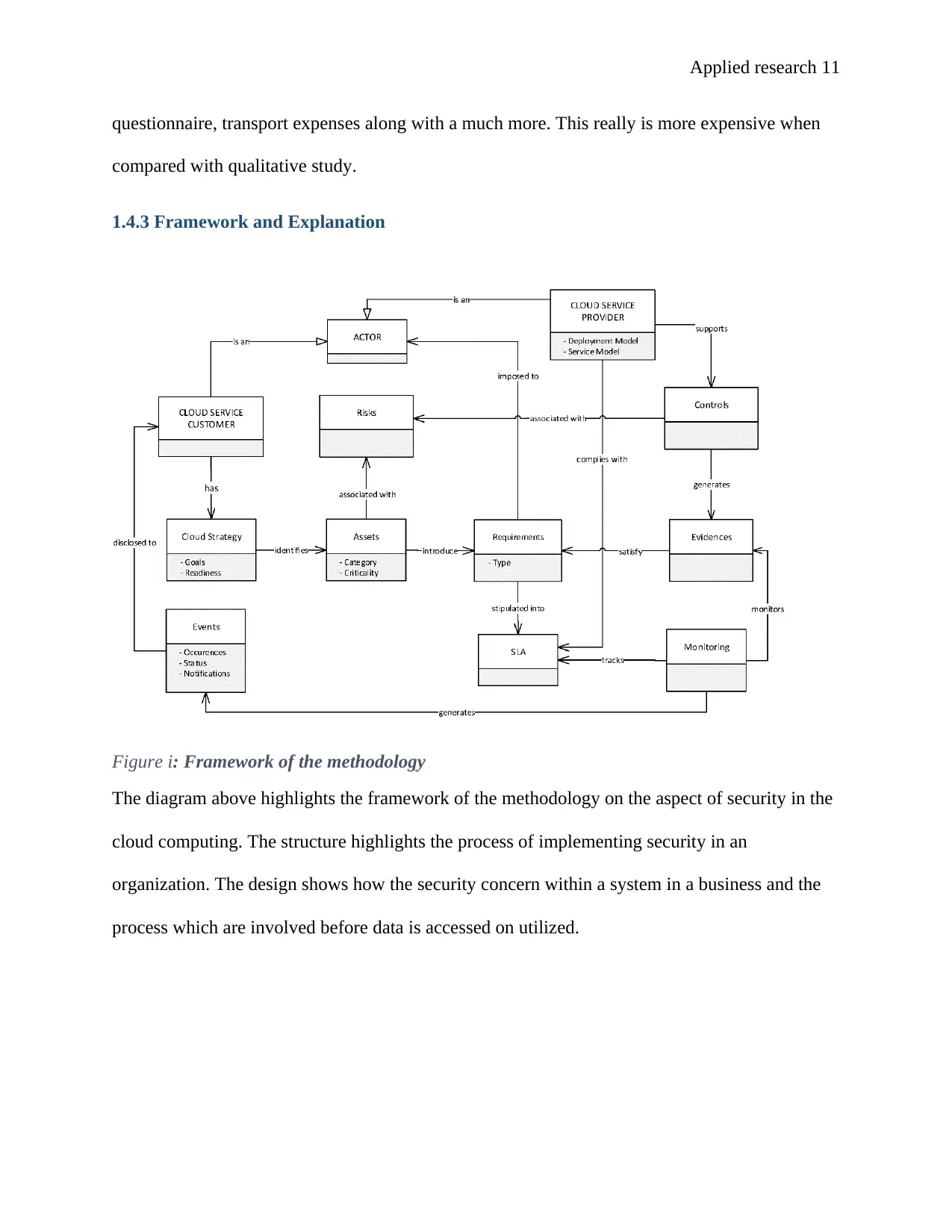
1.4.3 Framework and Explanation
Figure i: Framework of the methodology
The diagram above highlights the framework of the methodology on the aspect of security in the
cloud computing. The structure highlights the process of implementing security in an
organization. The design shows how the security concern within a system in a business and the
process which are involved before data is accessed on utilized.
questionnaire, transport expenses along with a much more. This really is more expensive when
compared with qualitative study.
1.4.3 Framework and Explanation
Figure i: Framework of the methodology
The diagram above highlights the framework of the methodology on the aspect of security in the
cloud computing. The structure highlights the process of implementing security in an
organization. The design shows how the security concern within a system in a business and the
process which are involved before data is accessed on utilized.

Applied research 12
References
Chen, D. and Zhao, H., 2012, March. Data security and privacy protection issues in cloud
computing. In Computer Science and Electronics Engineering (ICCSEE), 2012 International
Conference on (Vol. 1, pp. 647-651). IEEE.
Dikaiakos, M.D., Katsaros, D., Mehra, P., Pallis, G. and Vakali, A., 2009. Cloud computing:
Distributed internet computing for IT and scientific research. IEEE Internet computing, 13(5).
Feng, D.G., Zhang, M., Zhang, Y. and Xu, Z., 2011. Study on cloud computing security. Journal
of software, 22(1), pp.71-83.
Jensen, M., Schwenk, J., Gruschka, N. and Iacono, L.L., 2009, September. On technical security
issues in cloud computing. In Cloud Computing, 2009. CLOUD'09. IEEE International
Conference on (pp. 109-116). IEEE.
Kaufman, L.M., 2009. Data security in the world of cloud computing. IEEE Security & Privacy,
7(4).
Kandukuri, B.R. and Rakshit, A., 2009, September. Cloud security issues. In Services
Computing, 2009. SCC'09. IEEE International Conference on (pp. 517-520). IEEE.
Krutz, R.L. and Vines, R.D., 2010. Cloud security: A comprehensive guide to secure cloud
computing. Wiley Publishing.
Popović, K. and Hocenski, Ž., 2010, May. Cloud computing security issues and challenges. In
MIPRO, 2010 proceedings of the 33rd international convention (pp. 344-349). IEEE.
Subashini, S. and Kavitha, V., 2011. A survey on security issues in service delivery models of
cloud computing. Journal of network and computer applications, 34(1), pp.1-11.
Takabi, H., Joshi, J.B. and Ahn, G.J., 2010. Security and privacy challenges in cloud computing
environments. IEEE Security & Privacy, 8(6), pp.24-31.
Wang, C., Wang, Q., Ren, K. and Lou, W., 2010, March. Privacy-preserving public auditing for data
storage security in cloud computing. In Infocom, 2010 proceedings ieee (pp. 1-9). Ieee.
Wang, Q., Wang, C., Li, J., Ren, K. and Lou, W., 2009. Enabling public verifiability and data
dynamics for storage security in cloud computing. Computer Security–ESORICS 2009, pp.355-
370.
Zissis, D. and Lekkas, D., 2012. Addressing cloud computing security issues. Future Generation
computer systems, 28(3), pp.583-592.
References
Chen, D. and Zhao, H., 2012, March. Data security and privacy protection issues in cloud
computing. In Computer Science and Electronics Engineering (ICCSEE), 2012 International
Conference on (Vol. 1, pp. 647-651). IEEE.
Dikaiakos, M.D., Katsaros, D., Mehra, P., Pallis, G. and Vakali, A., 2009. Cloud computing:
Distributed internet computing for IT and scientific research. IEEE Internet computing, 13(5).
Feng, D.G., Zhang, M., Zhang, Y. and Xu, Z., 2011. Study on cloud computing security. Journal
of software, 22(1), pp.71-83.
Jensen, M., Schwenk, J., Gruschka, N. and Iacono, L.L., 2009, September. On technical security
issues in cloud computing. In Cloud Computing, 2009. CLOUD'09. IEEE International
Conference on (pp. 109-116). IEEE.
Kaufman, L.M., 2009. Data security in the world of cloud computing. IEEE Security & Privacy,
7(4).
Kandukuri, B.R. and Rakshit, A., 2009, September. Cloud security issues. In Services
Computing, 2009. SCC'09. IEEE International Conference on (pp. 517-520). IEEE.
Krutz, R.L. and Vines, R.D., 2010. Cloud security: A comprehensive guide to secure cloud
computing. Wiley Publishing.
Popović, K. and Hocenski, Ž., 2010, May. Cloud computing security issues and challenges. In
MIPRO, 2010 proceedings of the 33rd international convention (pp. 344-349). IEEE.
Subashini, S. and Kavitha, V., 2011. A survey on security issues in service delivery models of
cloud computing. Journal of network and computer applications, 34(1), pp.1-11.
Takabi, H., Joshi, J.B. and Ahn, G.J., 2010. Security and privacy challenges in cloud computing
environments. IEEE Security & Privacy, 8(6), pp.24-31.
Wang, C., Wang, Q., Ren, K. and Lou, W., 2010, March. Privacy-preserving public auditing for data
storage security in cloud computing. In Infocom, 2010 proceedings ieee (pp. 1-9). Ieee.
Wang, Q., Wang, C., Li, J., Ren, K. and Lou, W., 2009. Enabling public verifiability and data
dynamics for storage security in cloud computing. Computer Security–ESORICS 2009, pp.355-
370.
Zissis, D. and Lekkas, D., 2012. Addressing cloud computing security issues. Future Generation
computer systems, 28(3), pp.583-592.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 12
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





