Vulnerability Assessment & Security Countermeasures: Aramco Oil Plants
VerifiedAdded on 2022/09/14
|10
|3158
|15
Report
AI Summary
This report provides a comprehensive vulnerability assessment and security countermeasures for Saudi Aramco's oil plants, focusing on the potential risks associated with drone attacks and other threats. The study delves into the context of the global oil market and the strategic importance of Aramco, highlighting past attacks and security concerns. It explores the use of Bayesian networks for risk analysis and outlines various mitigation strategies, including the HAZMAT aspects of oil fields. The report also examines the dynamics of attack scenarios and the application of dynamic attack trees. The report is a case study of Aramco oil plants and discusses security measures to prevent, reduce, or mitigate future risks. The report also includes different strategies for mitigating these security concerns in the company has been provided in the study.

Vulnerability Assessment & Security Countermeasures for Aramco’s Oil
Plants in Saudi Arabia
Academic Author Name
Department of XXX
Institution Name, City, State or Country, and Postcode
Email: author@university.edu
Public Sector Author Name
Position
XXStateXX Department of Transportation
Department (if applicable)
City, State or Country, Postcode
Email: abc@dot.gov
Private Practitioner Author Name
Position
Company
City, State or Country, Postcode
Email: enj@abc.com
Word Count: 2465 words + 1 table (250 words per table) = 2,715 words
Submitted [Submission Date]
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
Plants in Saudi Arabia
Academic Author Name
Department of XXX
Institution Name, City, State or Country, and Postcode
Email: author@university.edu
Public Sector Author Name
Position
XXStateXX Department of Transportation
Department (if applicable)
City, State or Country, Postcode
Email: abc@dot.gov
Private Practitioner Author Name
Position
Company
City, State or Country, Postcode
Email: enj@abc.com
Word Count: 2465 words + 1 table (250 words per table) = 2,715 words
Submitted [Submission Date]
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Author, Author, and Author
ACKNOWLEDGEMENT
I would first like to thank my thesis advisor _________________ of the __________________ at
_______________. The door to Prof. ____________ office was always open whenever I ran into a
trouble spot or had a question about my research or writing. He/She consistently allowed this paper to be
my own work, but steered me in the right the direction whenever he thought I needed it.
2
1
2
3
4
5
6
ACKNOWLEDGEMENT
I would first like to thank my thesis advisor _________________ of the __________________ at
_______________. The door to Prof. ____________ office was always open whenever I ran into a
trouble spot or had a question about my research or writing. He/She consistently allowed this paper to be
my own work, but steered me in the right the direction whenever he thought I needed it.
2
1
2
3
4
5
6

Author, Author, and Author
ABSTRACT
Saudi Arabia has been one of the largest players of global oil market. It has been producing more than
tenth of the world’s oil output and owns a quarter of the world resources. The Saudi Arabian Oil
Company (Saudi Aramco) has been a national petroleum producer, manufacturer, marketer and refiner of
crudeoil, petroleum and natural gas was attacked by a 25 drones. This paper will focus on vulnerability
assessment and security counterneasures for Aramco’s Oil plants in Saudi Arabia. This study will
addresses several issues and risks in the systems of Aramco Oil plants. Sevaral mitigation strategies will
be provided in this study. HAZMAT aspects of oil fields will be discussed as counter measures.
3
1
2
3
4
5
6
7
8
9
ABSTRACT
Saudi Arabia has been one of the largest players of global oil market. It has been producing more than
tenth of the world’s oil output and owns a quarter of the world resources. The Saudi Arabian Oil
Company (Saudi Aramco) has been a national petroleum producer, manufacturer, marketer and refiner of
crudeoil, petroleum and natural gas was attacked by a 25 drones. This paper will focus on vulnerability
assessment and security counterneasures for Aramco’s Oil plants in Saudi Arabia. This study will
addresses several issues and risks in the systems of Aramco Oil plants. Sevaral mitigation strategies will
be provided in this study. HAZMAT aspects of oil fields will be discussed as counter measures.
3
1
2
3
4
5
6
7
8
9
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

Author, Author, and Author
Table of Contents
ABSTRACT................................................................................................................................................3
INTRODUCTION.......................................................................................................................................5
VULNERABILITY OF OIL SOURCES.....................................................................................................5
BAYESIAN NETWORK............................................................................................................................6
COUNTERMEASURES (HAZMAT aspects of oil fields).........................................................................8
CONCLUSION...........................................................................................................................................8
REFERENCES............................................................................................................................................9
4
1
2
3
4
5
6
7
8
9
10
Table of Contents
ABSTRACT................................................................................................................................................3
INTRODUCTION.......................................................................................................................................5
VULNERABILITY OF OIL SOURCES.....................................................................................................5
BAYESIAN NETWORK............................................................................................................................6
COUNTERMEASURES (HAZMAT aspects of oil fields).........................................................................8
CONCLUSION...........................................................................................................................................8
REFERENCES............................................................................................................................................9
4
1
2
3
4
5
6
7
8
9
10
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Author, Author, and Author
INTRODUCTION
“The Saudi Arabian Oil Company (Saudi Aramco) has been one of the largest oil producing company in
the Saudi Arabia. It has been concerned with producer, marketer, manufacturer and refiner of crude oil
and other petroleum products. On 14 September 2019, drones were used to attack the state-owned Saudi
Aramco oil processing facilities at Abqaiq and Khurais in eastern Saudi Arabia. The attack caused large
fires at the processing facility. Both facilities were shut down for repairs, cutting Saudi Arabia's oil
production by about half representing about 5% of global oil production and causing some destabilization
of global financial markets (Ajmi et al., 2019).”
This is attack was not the first and probably will not be the last. This paper will discuss
vulnerability assessment & countermeasures for Aramco’s oil plants to be conducted in order to prevent,
reduce, or mitigate future risks. It will also include the HAZMAT aspects of the oil fields. This study is
based on the vulnerability assessment and countermeasures towards cyber-attacks on Aramco Oil plants.
Several consequences of virus attack on Aramco have been defined in the study. Different strategies for
mitigating these security concerns in the company has been provided in the study.
CONTEXT
The Persian Gulf has been area for global oil and gas production. The area has been producing more than
22 million barrels of oil daily from these regions. In December 2006, the Financial Times titled Aramco
as the world’s biggest company. The estimated worth of Aramco has been close to $781 billion market
capitalization. The physical protection of Saudi Aramco’s infrastructure has been keen interest to the
leadership of the company (Song, 2018). After a foiled terrorist attack on massive petroleum processing
complex at Abqaiq in 2006, several concerns related to vulnerability of the company has been increased
in the market. Since Abqaiq, Aramco has been working with US experts and companies for its
contingency planning and security solutions. Aramco has been acquired with capability and recognized
for its efforts in the American Society of Industrial Security in 2010. “In the early hours of September 14,
Saudi Arabia has suffered the deadliest attack on its oil facilities in recent times when a small army of
drones attacked two major oil plants, which destroyed nearly 50 percent of the country’s global supply of
crude. The Hiouthi rebel group has focused in neighboring Yemen claimed responsibility for the attack.
However, US has been blaming Iran for this attack. This drone attacks have damaged Saudi Arabia’s oil
facilities and its intermediate fall out has been seen in the form of global surge in crude oil prices. Saudi
Arabia’s state run oil company Aramco said damage caused by drone attacks will cut the country’s oil
output by 5.7 million barrels every day” (Yuan, 2019). The US need to conduct military strikes gainst the
Islamic Revolutionary Guards Corps (IRGC) which is not necessarily in Iran preventing Iran from
splitting America from its regional partners. This fake equivocalness about who executed the assault has
filled the Iranian need of contorting the Western talk and diverting the discussion away from
concentrating on Iranian acceleration splendidly (Kim, 2019). The al Houthis professed to have hit
Abqaiq in light of Saudi activities in Yemen. Against Saudi inclination in the U.S. what's more, Europe is
as of now extraordinary after the fierce murder and dissection of Jamal Khashoggi. Indignation regarding
that awful wrongdoing has set an misrepresented story that Saudi Arabia is extraordinarily answerable for
the helpful emergency in Yemen and a large portion of the monstrosities submitted in that contention. The
al Houthi guarantee along these lines quickly presented all the annoyance toward Crown Prince
Mohammad container Salman (MBS), the true leader of Saudi Arabia, and turned part of the conversation
to the contention in Yemen rather than Iranian provincial exercises. It guaranteed that rivals of the Trump
Administration, which has remained by MBS and Riyadh and supports the Saudi-Emirati alliance battle in
Yemen, would ambush considering Saudi To be as a partner that ought to be shielded and rather advance
the idea that the Saudis had brought this sort of assault on themselves (Al Mughairi et al., 2019).
5
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
INTRODUCTION
“The Saudi Arabian Oil Company (Saudi Aramco) has been one of the largest oil producing company in
the Saudi Arabia. It has been concerned with producer, marketer, manufacturer and refiner of crude oil
and other petroleum products. On 14 September 2019, drones were used to attack the state-owned Saudi
Aramco oil processing facilities at Abqaiq and Khurais in eastern Saudi Arabia. The attack caused large
fires at the processing facility. Both facilities were shut down for repairs, cutting Saudi Arabia's oil
production by about half representing about 5% of global oil production and causing some destabilization
of global financial markets (Ajmi et al., 2019).”
This is attack was not the first and probably will not be the last. This paper will discuss
vulnerability assessment & countermeasures for Aramco’s oil plants to be conducted in order to prevent,
reduce, or mitigate future risks. It will also include the HAZMAT aspects of the oil fields. This study is
based on the vulnerability assessment and countermeasures towards cyber-attacks on Aramco Oil plants.
Several consequences of virus attack on Aramco have been defined in the study. Different strategies for
mitigating these security concerns in the company has been provided in the study.
CONTEXT
The Persian Gulf has been area for global oil and gas production. The area has been producing more than
22 million barrels of oil daily from these regions. In December 2006, the Financial Times titled Aramco
as the world’s biggest company. The estimated worth of Aramco has been close to $781 billion market
capitalization. The physical protection of Saudi Aramco’s infrastructure has been keen interest to the
leadership of the company (Song, 2018). After a foiled terrorist attack on massive petroleum processing
complex at Abqaiq in 2006, several concerns related to vulnerability of the company has been increased
in the market. Since Abqaiq, Aramco has been working with US experts and companies for its
contingency planning and security solutions. Aramco has been acquired with capability and recognized
for its efforts in the American Society of Industrial Security in 2010. “In the early hours of September 14,
Saudi Arabia has suffered the deadliest attack on its oil facilities in recent times when a small army of
drones attacked two major oil plants, which destroyed nearly 50 percent of the country’s global supply of
crude. The Hiouthi rebel group has focused in neighboring Yemen claimed responsibility for the attack.
However, US has been blaming Iran for this attack. This drone attacks have damaged Saudi Arabia’s oil
facilities and its intermediate fall out has been seen in the form of global surge in crude oil prices. Saudi
Arabia’s state run oil company Aramco said damage caused by drone attacks will cut the country’s oil
output by 5.7 million barrels every day” (Yuan, 2019). The US need to conduct military strikes gainst the
Islamic Revolutionary Guards Corps (IRGC) which is not necessarily in Iran preventing Iran from
splitting America from its regional partners. This fake equivocalness about who executed the assault has
filled the Iranian need of contorting the Western talk and diverting the discussion away from
concentrating on Iranian acceleration splendidly (Kim, 2019). The al Houthis professed to have hit
Abqaiq in light of Saudi activities in Yemen. Against Saudi inclination in the U.S. what's more, Europe is
as of now extraordinary after the fierce murder and dissection of Jamal Khashoggi. Indignation regarding
that awful wrongdoing has set an misrepresented story that Saudi Arabia is extraordinarily answerable for
the helpful emergency in Yemen and a large portion of the monstrosities submitted in that contention. The
al Houthi guarantee along these lines quickly presented all the annoyance toward Crown Prince
Mohammad container Salman (MBS), the true leader of Saudi Arabia, and turned part of the conversation
to the contention in Yemen rather than Iranian provincial exercises. It guaranteed that rivals of the Trump
Administration, which has remained by MBS and Riyadh and supports the Saudi-Emirati alliance battle in
Yemen, would ambush considering Saudi To be as a partner that ought to be shielded and rather advance
the idea that the Saudis had brought this sort of assault on themselves (Al Mughairi et al., 2019).
5
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46

Author, Author, and Author
VULNERABILITY OF OIL SOURCES
“Security of chemical and oil and gas facilities have been a critical issue developing in the Gulf countries
including Saudi Arabia. The security risk of the pipeline have been more critical than these fixed plants as
pipelines runs thousands of kilometers through different population density areas. “Security Risk
management has been a broad organizational framework, which has complete lifecycle for defining
security objectives and evaluating risks. Effective management of security risk for chemical and
petrochemical facilities including identification and analysis of threats (Azzedin, Suwad & Alyafeai,
2017). This analysis is termed as security risk assessment (SRA) is a systematic process for evaluating
likelihood those threats against a facility and operation. The purpose of conducting the SRA has been
gaining a better understanding of the assets being protected for identifying and evaluating security risks in
the industry (Simon, 2017).
The ANSI/API Standard 780 has been defining Security Risk as a function of Consequences of a
successful attack against an assert and the Liklihood of a successful attack against an asset. Fault Tree
analysis (FT) has been a conventional method in safety risk analysis investigating risks which are related
to safety risk analysis investigating risk which are based on safety events both qualitative and
quantitatively. This same concept can be used in Attack Tree (AT) approach (Perifanis, 2017). However,
AT has some drawbacks of static nature and unable to include time dependencies. Game theory has been
a concept that originate from mathematical and economic sciences. Game theory focuses on modelling as
intelligent attackers can best exploit opportunities for causing losses and defending can optimize
allocation of minimum damage (Ogunlade, 2017).”
BAYESIAN NETWORK
“A Bayesian network has been directed acyclic graph G to factorize a joint probability distribution P that
together satisfying Markov condition. In a BN, for a set of variables U = {A1, . . ., An}, a unique joint
probability distribution can be defined as in Eq. (1).
Where pa(Ai) are the parents of Ai in the BN. For instance, the joint probability distribution for random
variables U = {X,Y, Z,W}
P (U) = P (X,Y, Z,W) = P (X) .P (Y|X, Z) .P (Z|X) .P(W|Y, Z)
AS commented by Ogunlade, (2017), the BN approach has been extensively used in safety risk analysis
due to its flexible structure and capability for considering spatial and temporal dependencies.
The vulnerability assessment can be done by following steps:
1. Developing an attack scenario in form of DAT
2. Map the DAT to the Discrete time Bayesian Network (DTBN)
3. Calculating marginal probabilities as input of parent nodes in the DTBN
4. Developing conditional probability tables related to logic gates in the attack trees
5. Run the DTBN using values obtained
The Discrete time Bayesian Network (DTBN) approach , the time line has been divided into n+1
intervals. Each node variable has been finite number, n+1 of states. The first n states divide the time
interval into n. The last state means which has been corresponding basic component and gate output does
not fail during mission time.
Vulnerability has been the probability of a successful attack in which attack has been already launched at
the scenario (Ani et al., 2017). For successful attack, attacker needs to pass barriers and place explosive
materials on the buried pipeline and regresses. It has been assumed that bomb can be detonated
remotely.”
6
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
VULNERABILITY OF OIL SOURCES
“Security of chemical and oil and gas facilities have been a critical issue developing in the Gulf countries
including Saudi Arabia. The security risk of the pipeline have been more critical than these fixed plants as
pipelines runs thousands of kilometers through different population density areas. “Security Risk
management has been a broad organizational framework, which has complete lifecycle for defining
security objectives and evaluating risks. Effective management of security risk for chemical and
petrochemical facilities including identification and analysis of threats (Azzedin, Suwad & Alyafeai,
2017). This analysis is termed as security risk assessment (SRA) is a systematic process for evaluating
likelihood those threats against a facility and operation. The purpose of conducting the SRA has been
gaining a better understanding of the assets being protected for identifying and evaluating security risks in
the industry (Simon, 2017).
The ANSI/API Standard 780 has been defining Security Risk as a function of Consequences of a
successful attack against an assert and the Liklihood of a successful attack against an asset. Fault Tree
analysis (FT) has been a conventional method in safety risk analysis investigating risks which are related
to safety risk analysis investigating risk which are based on safety events both qualitative and
quantitatively. This same concept can be used in Attack Tree (AT) approach (Perifanis, 2017). However,
AT has some drawbacks of static nature and unable to include time dependencies. Game theory has been
a concept that originate from mathematical and economic sciences. Game theory focuses on modelling as
intelligent attackers can best exploit opportunities for causing losses and defending can optimize
allocation of minimum damage (Ogunlade, 2017).”
BAYESIAN NETWORK
“A Bayesian network has been directed acyclic graph G to factorize a joint probability distribution P that
together satisfying Markov condition. In a BN, for a set of variables U = {A1, . . ., An}, a unique joint
probability distribution can be defined as in Eq. (1).
Where pa(Ai) are the parents of Ai in the BN. For instance, the joint probability distribution for random
variables U = {X,Y, Z,W}
P (U) = P (X,Y, Z,W) = P (X) .P (Y|X, Z) .P (Z|X) .P(W|Y, Z)
AS commented by Ogunlade, (2017), the BN approach has been extensively used in safety risk analysis
due to its flexible structure and capability for considering spatial and temporal dependencies.
The vulnerability assessment can be done by following steps:
1. Developing an attack scenario in form of DAT
2. Map the DAT to the Discrete time Bayesian Network (DTBN)
3. Calculating marginal probabilities as input of parent nodes in the DTBN
4. Developing conditional probability tables related to logic gates in the attack trees
5. Run the DTBN using values obtained
The Discrete time Bayesian Network (DTBN) approach , the time line has been divided into n+1
intervals. Each node variable has been finite number, n+1 of states. The first n states divide the time
interval into n. The last state means which has been corresponding basic component and gate output does
not fail during mission time.
Vulnerability has been the probability of a successful attack in which attack has been already launched at
the scenario (Ani et al., 2017). For successful attack, attacker needs to pass barriers and place explosive
materials on the buried pipeline and regresses. It has been assumed that bomb can be detonated
remotely.”
6
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
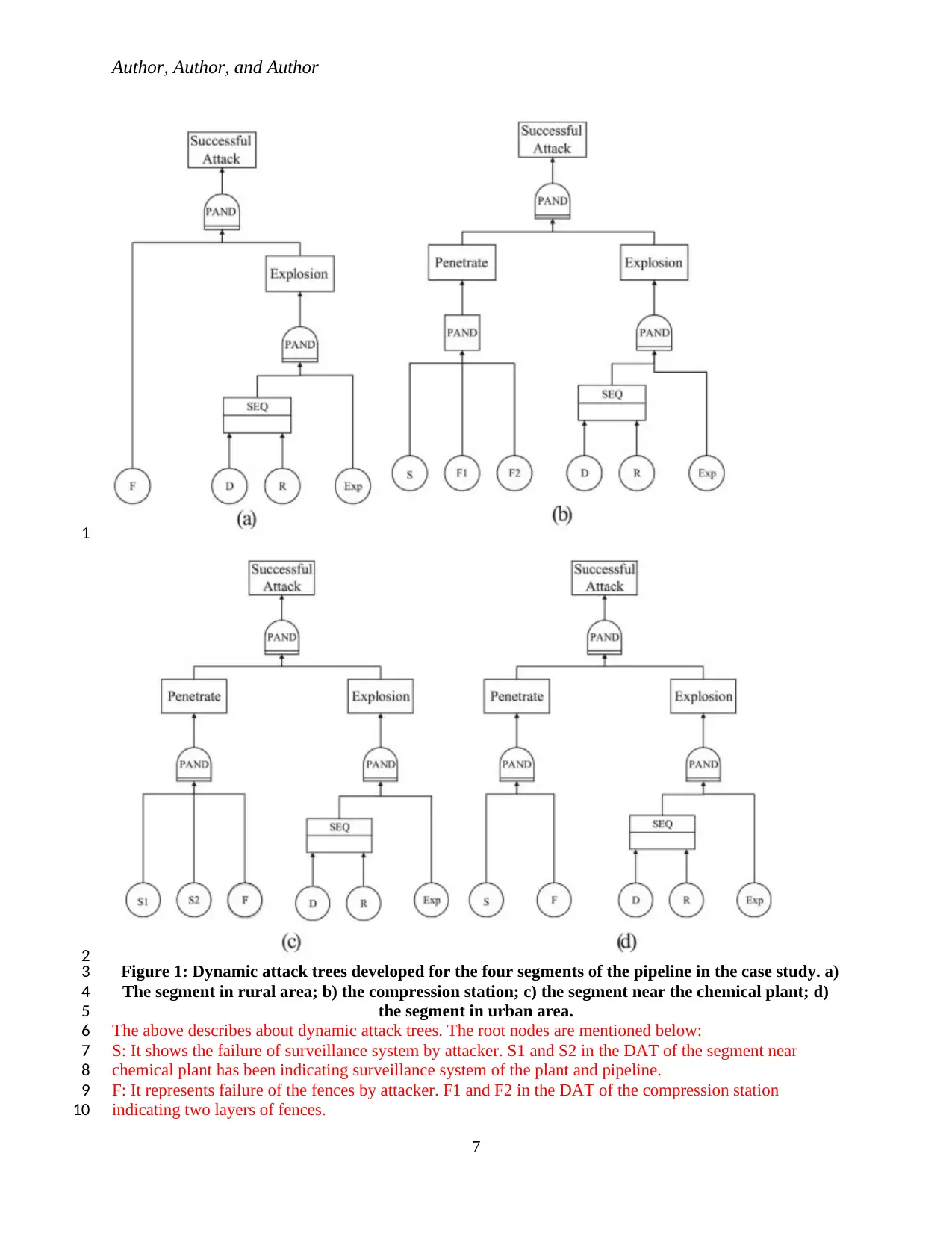
Author, Author, and Author
“Figure 1: Dynamic attack trees developed for the four segments of the pipeline in the case study. a)
The segment in rural area; b) the compression station; c) the segment near the chemical plant; d)
the segment in urban area.
The above describes about dynamic attack trees. The root nodes are mentioned below:
S: It shows the failure of surveillance system by attacker. S1 and S2 in the DAT of the segment near
chemical plant has been indicating surveillance system of the plant and pipeline.
F: It represents failure of the fences by attacker. F1 and F2 in the DAT of the compression station
indicating two layers of fences.
7
1
2
3
4
5
6
7
8
9
10
“Figure 1: Dynamic attack trees developed for the four segments of the pipeline in the case study. a)
The segment in rural area; b) the compression station; c) the segment near the chemical plant; d)
the segment in urban area.
The above describes about dynamic attack trees. The root nodes are mentioned below:
S: It shows the failure of surveillance system by attacker. S1 and S2 in the DAT of the segment near
chemical plant has been indicating surveillance system of the plant and pipeline.
F: It represents failure of the fences by attacker. F1 and F2 in the DAT of the compression station
indicating two layers of fences.
7
1
2
3
4
5
6
7
8
9
10
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Author, Author, and Author
D: It represents state of acoustic detection system .
R: It represents success of attacker for regressing.
EXP: It represents success of the attacker for damaging pipelines by means of an explosion.
The two types of dynamic gates have been utilized in these DATs. The first one is the priority AND gate
which indicate the connected actions need to take place in a proper order from left to right (Aljabhan,
2016). The second type of dynamic gate has been a sequential gate that demonstrates nodes connected to
gate might fail sequentially.” Patrolling isn't unequivocally appeared in the DAT as a security obstruction
however its timetable straightforwardly influences the negligible likelihood esteems relating to the
achievement of the foe to handicap the obstructions. Every interim has two condition of accomplishment
(1) or disappointment (1). To ascertain the likelihood of the fruitful assault, the minor and contingent
probabilities ought to be determined also, appointed to the hubs (Ismail, Sitnikova & Slay, 2020). To
build the DTBNs, the mission time was considered as 1.0h and isolated into four equivalent interims,
15min. The fifth interim, t > 60min, demonstrates the aggressor can't pass the boundaries inside 60
minutes, and in this way the assault falls flat. For every obstruction a likelihood dissemination work was
expected. A significant presumption that was made in the likelihood estimation of the present
examination is that, the assailant will be halted if the watch shows up. Corresponding to this issue, load-
obstruction unwavering quality models are utilized in the present study to determine a disappointment
likelihood for every hindrance. The Patrolling plan is expected to follow an exponential dispersion, where
(1/h) is the appearance pace of watch inside 60 minutes (Khan & Zhaoying, 2020).”
COUNTERMEASURES (HAZMAT aspects of oil fields)
There are various hazardous materials used in the oil fields which need to removed and taken care for
countermeasures of future attacks. Some of this HAZMAT have been listed below:
Explosives: Explosives have been only one percent if the HAZMAT in oil fields. This has been used for
the military operations nearby the oil field for protection. However, this might be a self-made weapons
for oil fields in case a drone attacks these explosives. There can be huge destruction in nearby areas due
to this HAZMAT.
Gases: Compressed and liquefied gases have been making upto 18% of the HAZMAT. There have been
three types of gases in this category including flammable, toxic and non-flammable, which can be
transported in safe containers. 70 % of the liquefied and compresses gases are transported as petroleum
gases that are termed as propane and butane. Therefore, these HAZMAT need to be removed from oil
field areas which might cause any accident and serious affect on workers in the oil fields (Ogunlade
2017).
Flammable liquids: These are the highest HAZMAT having 50 % of the total HAZMAT carloads. Three
quarters of the flammable liquids need to be moved from Aramco which might cause fire in the oilfields
during a terrorist attack in future. Several flammable plastic including plastic bottles, polyester fabric and
rubber need to be removed from the oil fields.
Ergonomic HAZMAT: Oil and gas workers might be exposed to ergonomics related injuries including
lifting heavy items, reaching, and bending and pulling heavy loads while working. This might cause
heavily injury to workers during any accidents.
CONCLUSION
It can be concluded that Aramco need to be prepared for any further attacks over its factory and pipelines.
Therefore, with the use of Bayesian network, a model has been prepared that will help in predicting
8
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
D: It represents state of acoustic detection system .
R: It represents success of attacker for regressing.
EXP: It represents success of the attacker for damaging pipelines by means of an explosion.
The two types of dynamic gates have been utilized in these DATs. The first one is the priority AND gate
which indicate the connected actions need to take place in a proper order from left to right (Aljabhan,
2016). The second type of dynamic gate has been a sequential gate that demonstrates nodes connected to
gate might fail sequentially.” Patrolling isn't unequivocally appeared in the DAT as a security obstruction
however its timetable straightforwardly influences the negligible likelihood esteems relating to the
achievement of the foe to handicap the obstructions. Every interim has two condition of accomplishment
(1) or disappointment (1). To ascertain the likelihood of the fruitful assault, the minor and contingent
probabilities ought to be determined also, appointed to the hubs (Ismail, Sitnikova & Slay, 2020). To
build the DTBNs, the mission time was considered as 1.0h and isolated into four equivalent interims,
15min. The fifth interim, t > 60min, demonstrates the aggressor can't pass the boundaries inside 60
minutes, and in this way the assault falls flat. For every obstruction a likelihood dissemination work was
expected. A significant presumption that was made in the likelihood estimation of the present
examination is that, the assailant will be halted if the watch shows up. Corresponding to this issue, load-
obstruction unwavering quality models are utilized in the present study to determine a disappointment
likelihood for every hindrance. The Patrolling plan is expected to follow an exponential dispersion, where
(1/h) is the appearance pace of watch inside 60 minutes (Khan & Zhaoying, 2020).”
COUNTERMEASURES (HAZMAT aspects of oil fields)
There are various hazardous materials used in the oil fields which need to removed and taken care for
countermeasures of future attacks. Some of this HAZMAT have been listed below:
Explosives: Explosives have been only one percent if the HAZMAT in oil fields. This has been used for
the military operations nearby the oil field for protection. However, this might be a self-made weapons
for oil fields in case a drone attacks these explosives. There can be huge destruction in nearby areas due
to this HAZMAT.
Gases: Compressed and liquefied gases have been making upto 18% of the HAZMAT. There have been
three types of gases in this category including flammable, toxic and non-flammable, which can be
transported in safe containers. 70 % of the liquefied and compresses gases are transported as petroleum
gases that are termed as propane and butane. Therefore, these HAZMAT need to be removed from oil
field areas which might cause any accident and serious affect on workers in the oil fields (Ogunlade
2017).
Flammable liquids: These are the highest HAZMAT having 50 % of the total HAZMAT carloads. Three
quarters of the flammable liquids need to be moved from Aramco which might cause fire in the oilfields
during a terrorist attack in future. Several flammable plastic including plastic bottles, polyester fabric and
rubber need to be removed from the oil fields.
Ergonomic HAZMAT: Oil and gas workers might be exposed to ergonomics related injuries including
lifting heavy items, reaching, and bending and pulling heavy loads while working. This might cause
heavily injury to workers during any accidents.
CONCLUSION
It can be concluded that Aramco need to be prepared for any further attacks over its factory and pipelines.
Therefore, with the use of Bayesian network, a model has been prepared that will help in predicting
8
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43

Author, Author, and Author
terrorist attacks. The schematic of the DTBNs framed in light of the DATs. Since the contingent
likelihood tables of a DTBN of a situation are too large because of the quantity of interims, just a piece of
the table for the first PAND entryway is appeared and a similar rationale were utilized for the rest. There
are various HAZMAT materials discussed which can help as countermeasures against terrorist attacks on
oil fields.
9
1
2
3
4
5
terrorist attacks. The schematic of the DTBNs framed in light of the DATs. Since the contingent
likelihood tables of a DTBN of a situation are too large because of the quantity of interims, just a piece of
the table for the first PAND entryway is appeared and a similar rationale were utilized for the rest. There
are various HAZMAT materials discussed which can help as countermeasures against terrorist attacks on
oil fields.
9
1
2
3
4
5
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

REFERENCES
Ajmi, L., Alqahtani, N., Rahman, A. U., & Mahmud, M. (2019, May). A Novel Cybersecurity Framework
for Countermeasure of SME's in Saudi Arabia. In 2019 2nd International Conference on
Computer Applications & Information Security (ICCAIS) (pp. 1-9). IEEE.
Al Mughairi, B. M., Al Hajri, H. H., Karim, A. M., & Hossain, M. I. (2019). An Innovative Cyber
Security based Approach for National Infrastructure Resiliency for Sultanate of
Oman. INTERNATIONAL JOURNAL OF ACADEMIC RESEARCH IN BUSINESS AND SOCIAL
SCIENCES, 9(3).
Aljabhan, B. I. (2016). Supply chain risk management: a case study of maritime firms in the Kingdom of
Saudi Arabia (Doctoral dissertation, Anglia Ruskin University).
Ani, U. P. D., He, H., & Tiwari, A. (2017). Review of cybersecurity issues in industrial critical
infrastructure: manufacturing in perspective. Journal of Cyber Security Technology, 1(1), 32-74.
Azzedin, F., Suwad, H., & Alyafeai, Z. (2017, July). Countermeasureing Zero Day Attacks: Asset-Based
Approach. In 2017 International Conference on High Performance Computing & Simulation
(HPCS) (pp. 854-857). IEEE.
Ismail, S., Sitnikova, E., & Slay, J. (2020). SCADA Systems Cyber Security for Critical Infrastructures:
Case Studies in Multiple Sectors. In Cyber Warfare and Terrorism: Concepts, Methodologies,
Tools, and Applications (pp. 446-464). IGI Global.
Khan, A., & Zhaoying, H. (2020). Conflict escalation in the Middle East revisited: thinking through
interstate rivalries and state-sponsored terrorism. Israel Affairs, 26(2), 242-256.
Kim, I. (2019). A crude bargain: Great powers, oil states, and petro-alignment. Security Studies, 28(5),
833-869.
Ogunlade, A. (2017). Developing a framework to mitigate the growing incidents of cyber-security threats
on process control networks (pcn): a case study of the petrochemical industry.
Perifanis, T. (2017). An analysis on Saudi Arabia's crude oil production strategy (Master's thesis,
Πανεπιστήμιο Πειραιώς).
Simon, T. (2017). Chapter seven: Critical infrastructure and the internet of things. Cyber Security in a
Volatile World, 93.
Song, G. (2018). Dynamic safety and security risk management of hazardous operations (Doctoral
dissertation, Memorial University of Newfoundland).
Yuan, S. (2019). Total Quality Management Practices Saudi Arabian Petrochemical Performance.
In Modern Management Forum (Vol. 3, No. 1).
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
Ajmi, L., Alqahtani, N., Rahman, A. U., & Mahmud, M. (2019, May). A Novel Cybersecurity Framework
for Countermeasure of SME's in Saudi Arabia. In 2019 2nd International Conference on
Computer Applications & Information Security (ICCAIS) (pp. 1-9). IEEE.
Al Mughairi, B. M., Al Hajri, H. H., Karim, A. M., & Hossain, M. I. (2019). An Innovative Cyber
Security based Approach for National Infrastructure Resiliency for Sultanate of
Oman. INTERNATIONAL JOURNAL OF ACADEMIC RESEARCH IN BUSINESS AND SOCIAL
SCIENCES, 9(3).
Aljabhan, B. I. (2016). Supply chain risk management: a case study of maritime firms in the Kingdom of
Saudi Arabia (Doctoral dissertation, Anglia Ruskin University).
Ani, U. P. D., He, H., & Tiwari, A. (2017). Review of cybersecurity issues in industrial critical
infrastructure: manufacturing in perspective. Journal of Cyber Security Technology, 1(1), 32-74.
Azzedin, F., Suwad, H., & Alyafeai, Z. (2017, July). Countermeasureing Zero Day Attacks: Asset-Based
Approach. In 2017 International Conference on High Performance Computing & Simulation
(HPCS) (pp. 854-857). IEEE.
Ismail, S., Sitnikova, E., & Slay, J. (2020). SCADA Systems Cyber Security for Critical Infrastructures:
Case Studies in Multiple Sectors. In Cyber Warfare and Terrorism: Concepts, Methodologies,
Tools, and Applications (pp. 446-464). IGI Global.
Khan, A., & Zhaoying, H. (2020). Conflict escalation in the Middle East revisited: thinking through
interstate rivalries and state-sponsored terrorism. Israel Affairs, 26(2), 242-256.
Kim, I. (2019). A crude bargain: Great powers, oil states, and petro-alignment. Security Studies, 28(5),
833-869.
Ogunlade, A. (2017). Developing a framework to mitigate the growing incidents of cyber-security threats
on process control networks (pcn): a case study of the petrochemical industry.
Perifanis, T. (2017). An analysis on Saudi Arabia's crude oil production strategy (Master's thesis,
Πανεπιστήμιο Πειραιώς).
Simon, T. (2017). Chapter seven: Critical infrastructure and the internet of things. Cyber Security in a
Volatile World, 93.
Song, G. (2018). Dynamic safety and security risk management of hazardous operations (Doctoral
dissertation, Memorial University of Newfoundland).
Yuan, S. (2019). Total Quality Management Practices Saudi Arabian Petrochemical Performance.
In Modern Management Forum (Vol. 3, No. 1).
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
1 out of 10
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2025 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.
