Exploring the Architecture and Security Threats in Healthcare Networks
VerifiedAdded on 2023/06/05
|7
|338
|124
Report
AI Summary
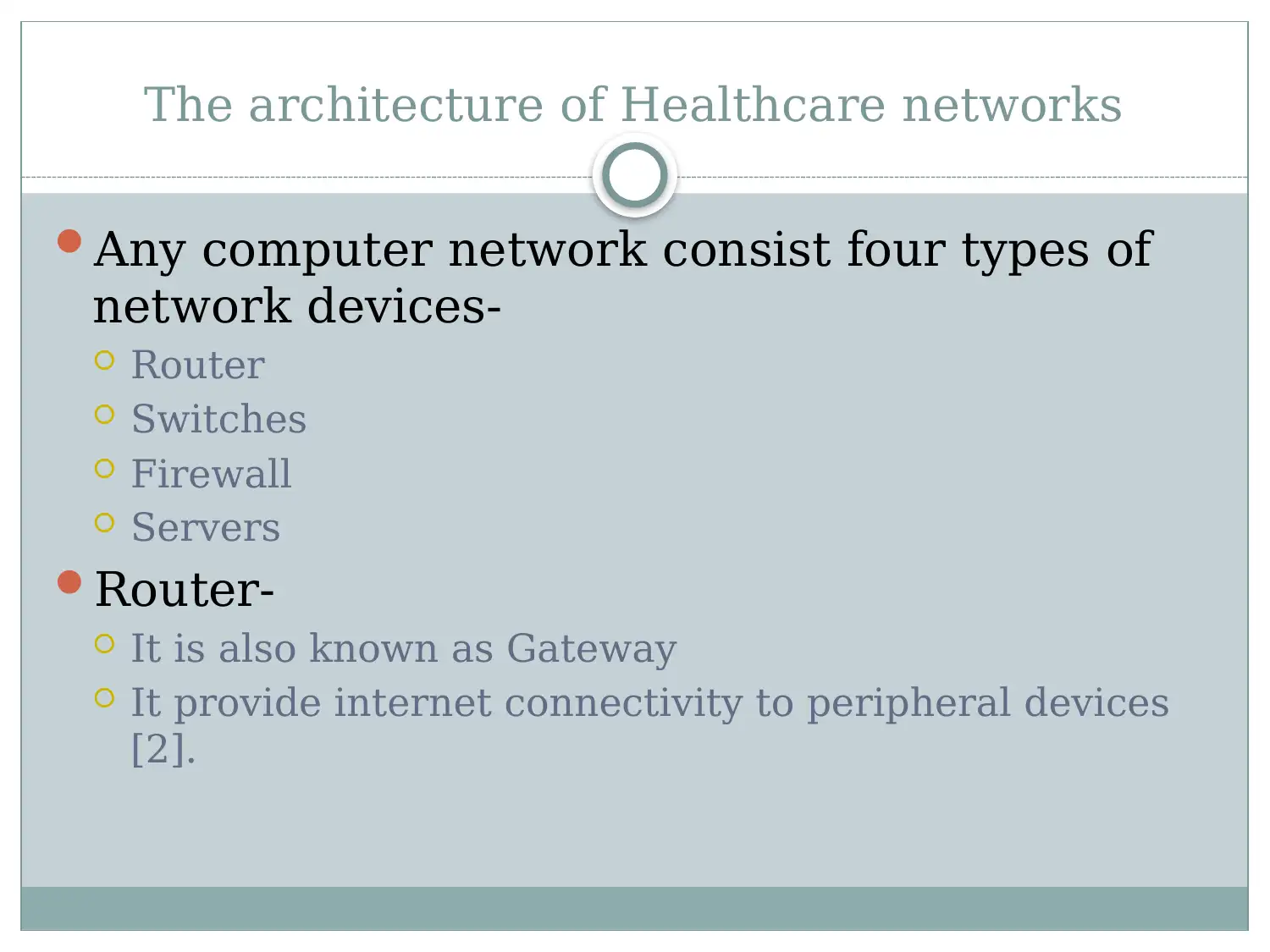
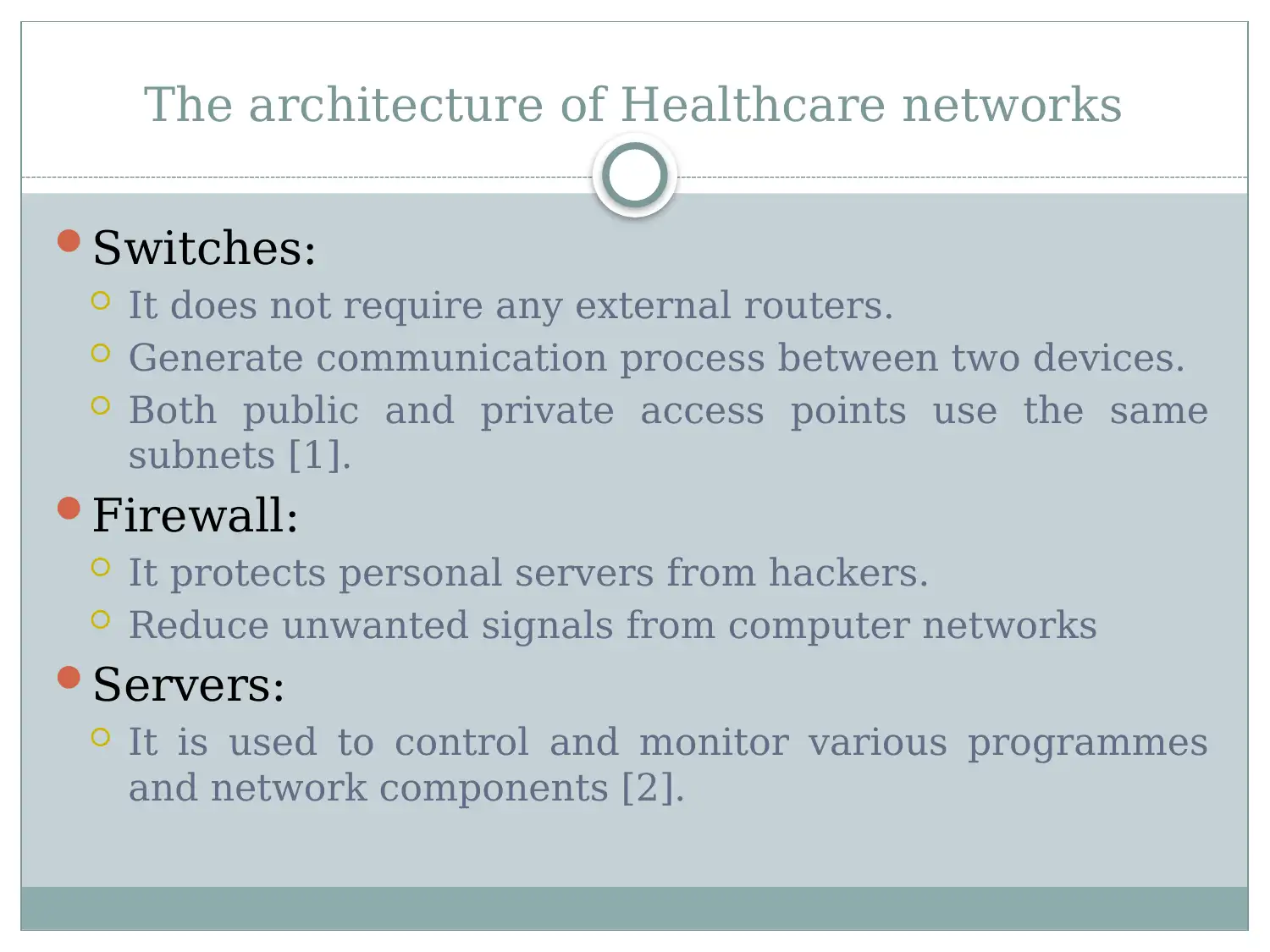
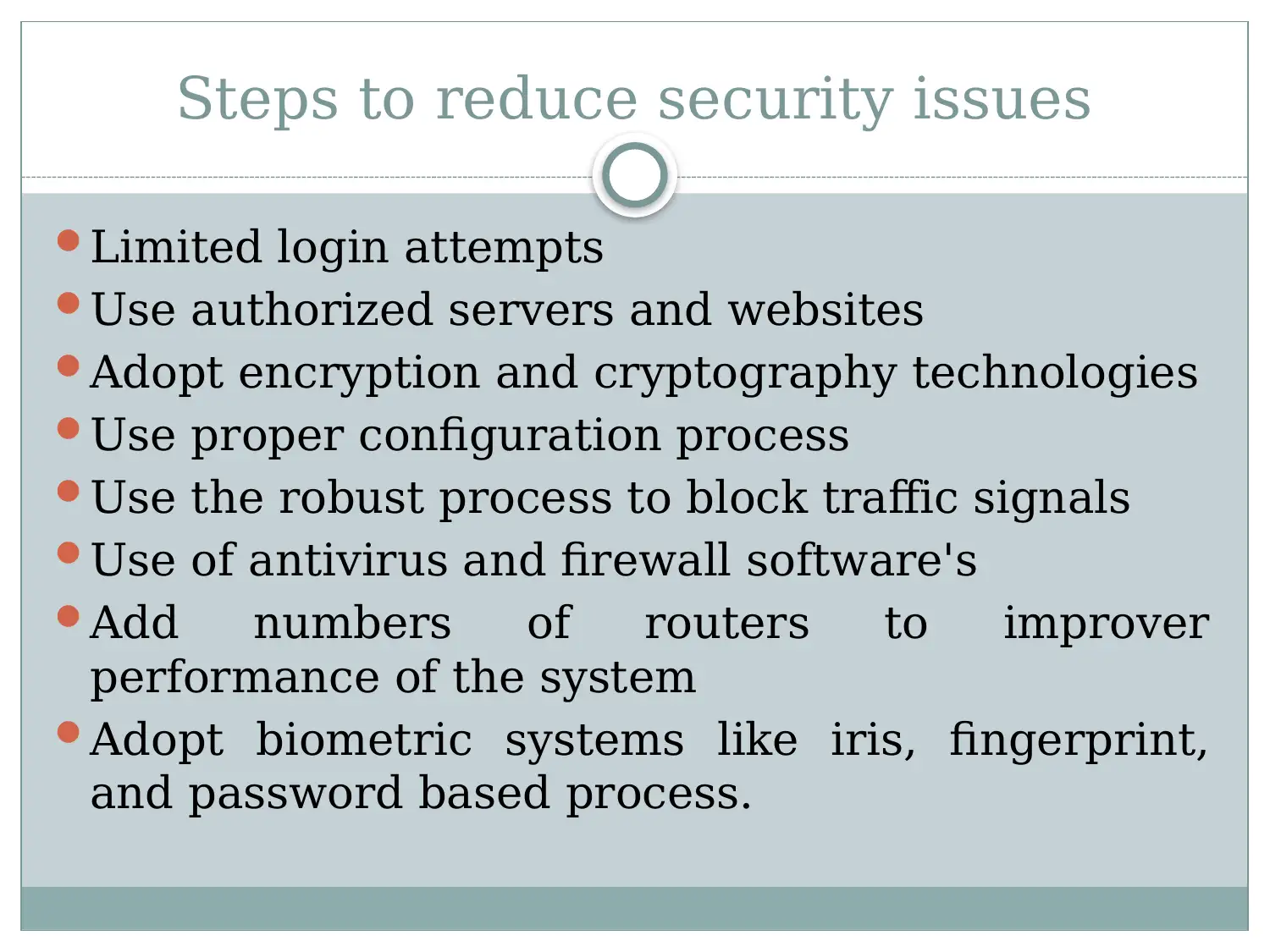
This report provides an overview of healthcare networks, highlighting the critical role computer networks play within the healthcare system. It details the architecture of these networks, including essential components like routers, switches, firewalls, and servers, explaining their functions in maintaining network operations and security. The report further identifies key security threats such as data breaches, configuration conflicts, DOS attacks, system interoperability issues, and malware. Finally, it proposes several steps to mitigate these security risks, including limiting login attempts, using authorized servers, adopting encryption technologies, implementing proper configuration processes, blocking unwanted traffic, using antivirus software, adding routers for improved performance, and adopting biometric authentication methods. The document concludes by citing references that support the information presented.
1 out of 7










![[object Object]](/_next/static/media/star-bottom.7253800d.svg)