Digital Forensics Report: Artifactextractor Tool Analysis and Review
VerifiedAdded on 2023/01/19
|12
|915
|63
Report
AI Summary
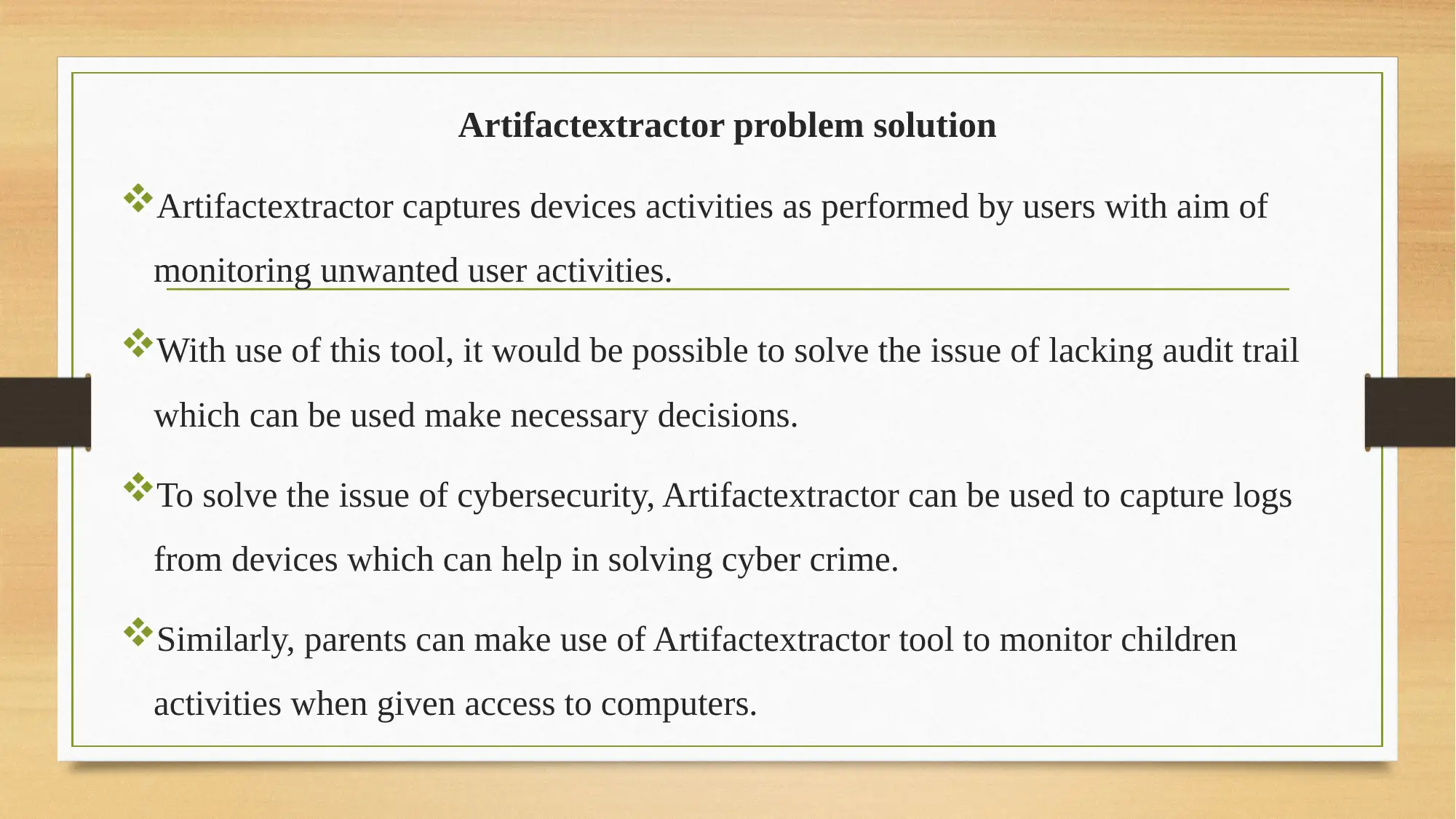
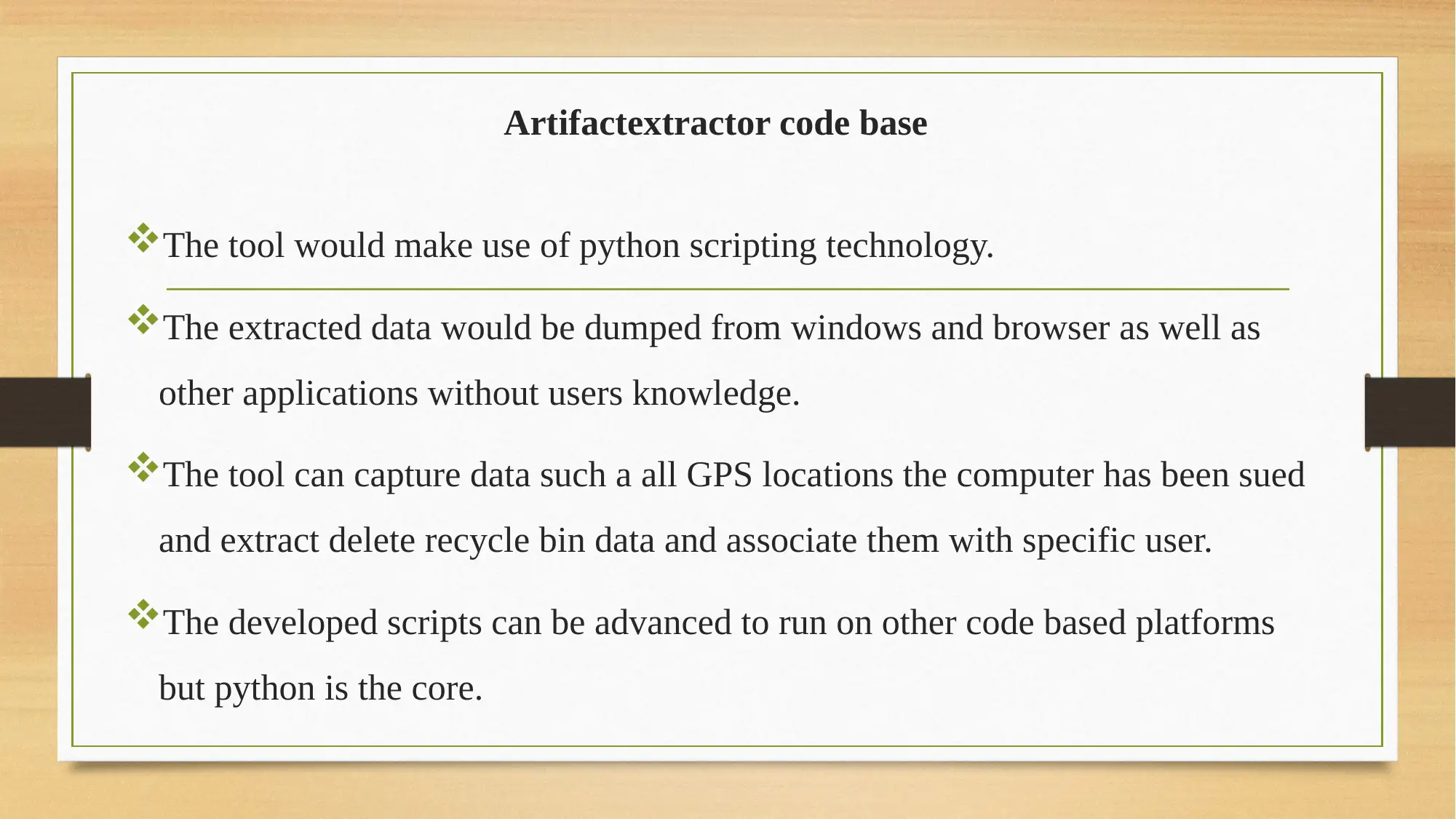
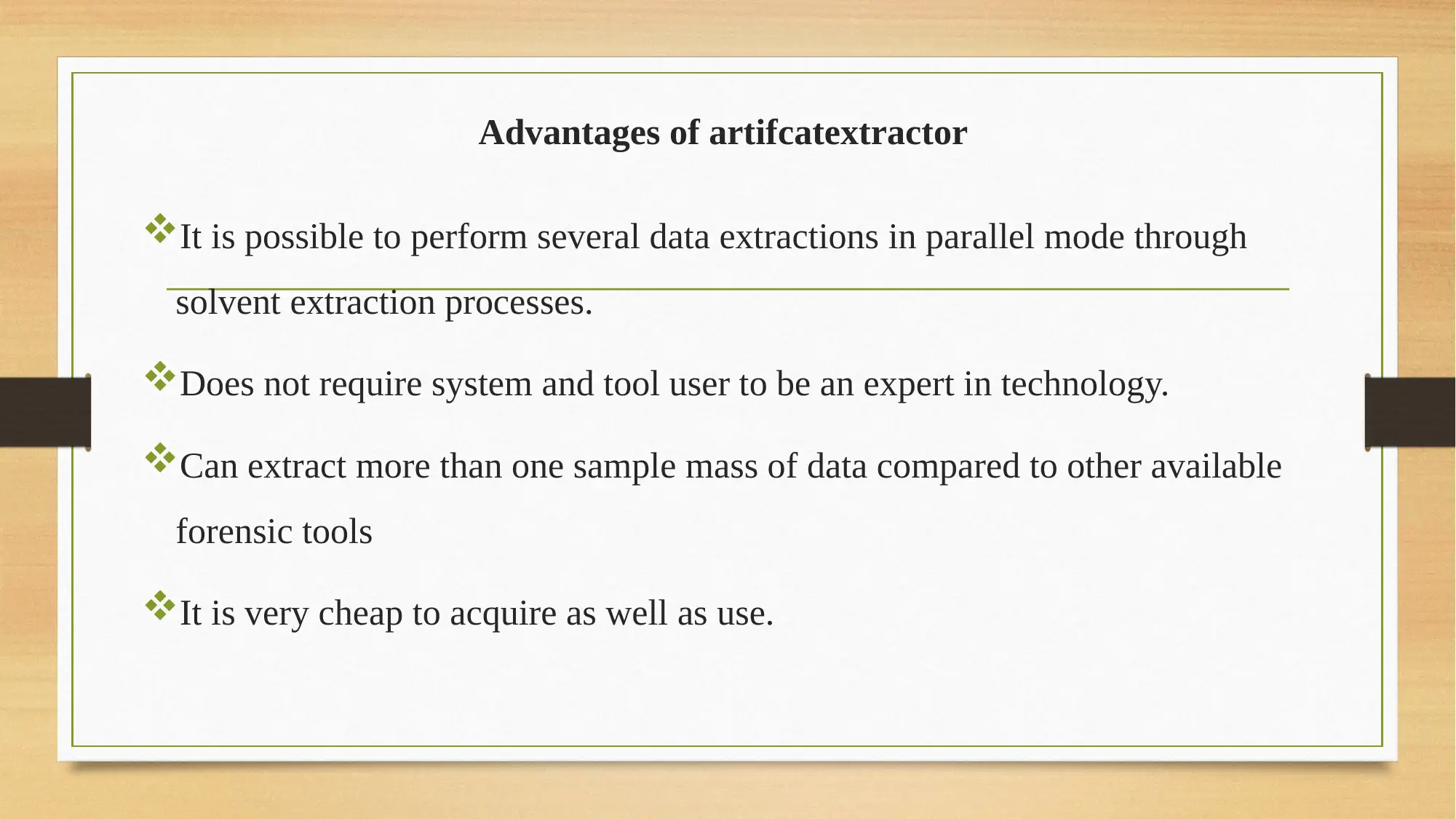
This report provides an analysis of Artifactextractor, a digital forensics tool used to extract digital evidence. It begins with an introduction to digital forensics and the role of tools like Artifactextractor in uncovering digital evidence. The report then delves into the tool's background, highlighting its application in sensitive areas such as banking and security for monitoring device activities and investigating data breaches. The solution offered by Artifactextractor is explored, including its ability to capture device activities, solve audit trail issues, and aid in cybersecurity. The report details the tool's code base, emphasizing its use of Python scripting and its ability to extract data from various sources. It also covers the operating system focus, primarily Windows, and the advantages of the tool, such as parallel data extraction and ease of use, as well as its disadvantages, including potential resource waste and automation difficulties. The report also suggests improvements, such as a mobile phone version. Finally, it concludes with recommendations, emphasizing the importance of monitoring and audit in modern business practices and the flexibility of Artifactextractor across different operating systems. References to relevant research papers are also included.
1 out of 12













![[object Object]](/_next/static/media/star-bottom.7253800d.svg)