PRT 571 - Asset Security and Risk Management Case Study: CDU Systems
VerifiedAdded on 2023/06/12
|9
|1441
|416
Report
AI Summary
This report provides a comprehensive analysis of asset security and risk management at Charles Darwin University (CDU). It identifies key assets, including equipment and information, and outlines potential risks such as hardware malfunctions, data loss, and unauthorized access. The report details vulnerabilities within the CDU systems and assesses the likelihood and impact of various threats. Current control measures are evaluated, and recommendations are made to improve the overall security landscape, including identifying stakeholders, developing information security strategies, and increasing security awareness among employees and students. The report emphasizes the importance of managing information security risks to ensure data confidentiality, integrity, and accessibility, ultimately aiming to achieve an acceptable risk level for the university through proactive risk mitigation strategies. This document is available on Desklib, where students can find a wealth of resources, including past papers and solved assignments.

Running head: ASSET SECURITY AND RISK MANAGEMENT
Asset Security and Risk Management: A Case Study of CDU (Charles Darwin
University) systems
Student Name:
University Name:
Asset Security and Risk Management: A Case Study of CDU (Charles Darwin
University) systems
Student Name:
University Name:
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

1ASSET SECURITY AND RISK MANAGEMENT
Table of Contents
Introduction......................................................................................................................................2
Identification of assets and risks......................................................................................................2
Asset Identification......................................................................................................................2
Risk Identification.......................................................................................................................4
Recommendations............................................................................................................................6
Conclusion.......................................................................................................................................7
Bibliography....................................................................................................................................8
Table of Contents
Introduction......................................................................................................................................2
Identification of assets and risks......................................................................................................2
Asset Identification......................................................................................................................2
Risk Identification.......................................................................................................................4
Recommendations............................................................................................................................6
Conclusion.......................................................................................................................................7
Bibliography....................................................................................................................................8
2ASSET SECURITY AND RISK MANAGEMENT
Introduction
Asset security and risk management are referred to as a very important mechanism for
any university to secure their credential from the external attackers (Layton 2016). It has been
identified that due to lack of managerial and functional operations the Charles Darwin University
is facing huge risks and the risks associated to the University are elaborated in this. On the other
hand, students and employee’s credentials are the most important asset for the University that
should keep safe and secured. The categories of the assets, details of the assets, their type and
owners are demonstrated in this report addition to possible treatments for all the identified risks.
Identification of assets and risks
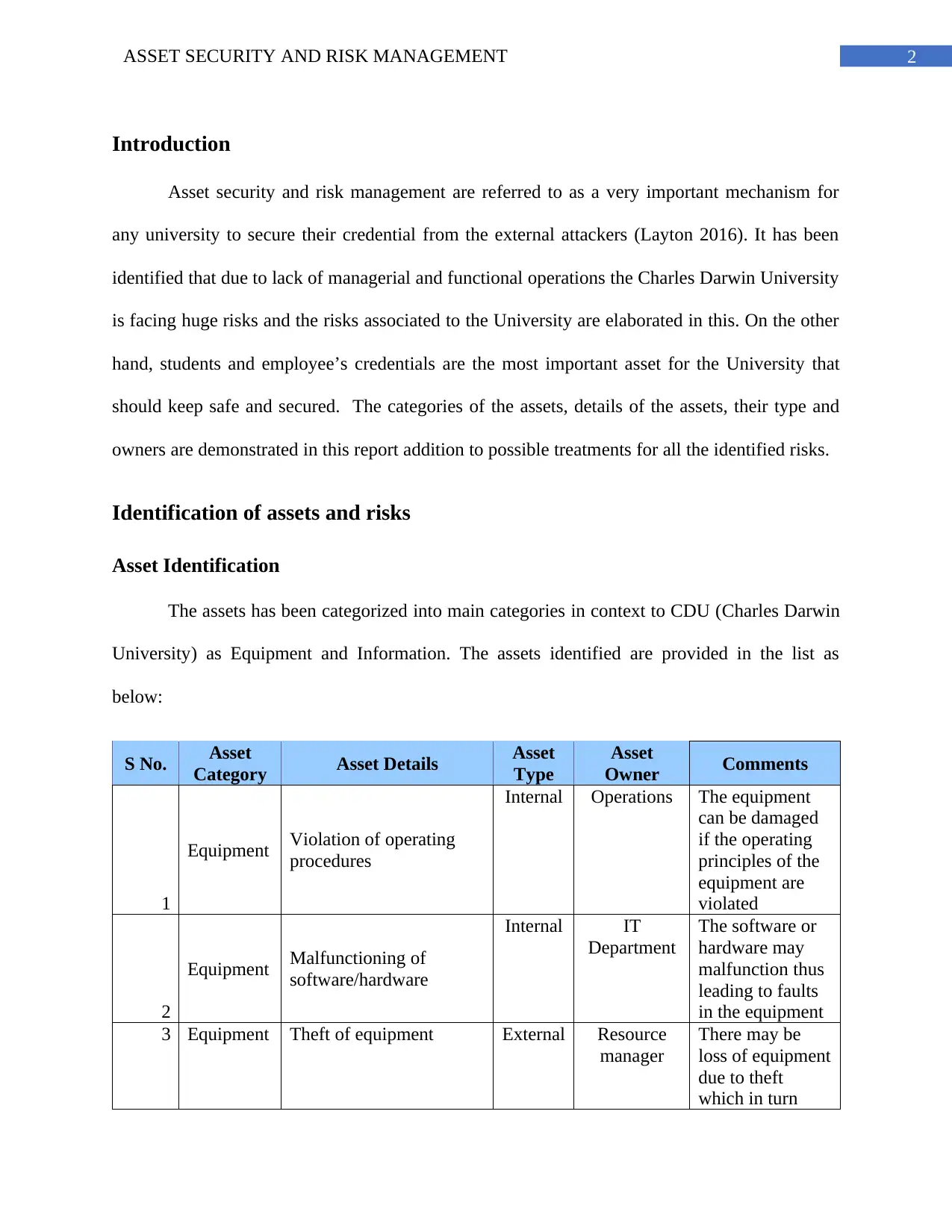
Asset Identification
The assets has been categorized into main categories in context to CDU (Charles Darwin
University) as Equipment and Information. The assets identified are provided in the list as
below:
S No. Asset
Category Asset Details Asset
Type
Asset
Owner Comments
1
Equipment Violation of operating
procedures
Internal Operations The equipment
can be damaged
if the operating
principles of the
equipment are
violated
2
Equipment Malfunctioning of
software/hardware
Internal IT
Department
The software or
hardware may
malfunction thus
leading to faults
in the equipment
3 Equipment Theft of equipment External Resource
manager
There may be
loss of equipment
due to theft
which in turn
Introduction
Asset security and risk management are referred to as a very important mechanism for
any university to secure their credential from the external attackers (Layton 2016). It has been
identified that due to lack of managerial and functional operations the Charles Darwin University
is facing huge risks and the risks associated to the University are elaborated in this. On the other
hand, students and employee’s credentials are the most important asset for the University that
should keep safe and secured. The categories of the assets, details of the assets, their type and
owners are demonstrated in this report addition to possible treatments for all the identified risks.
Identification of assets and risks
Asset Identification
The assets has been categorized into main categories in context to CDU (Charles Darwin
University) as Equipment and Information. The assets identified are provided in the list as
below:
S No. Asset
Category Asset Details Asset
Type
Asset
Owner Comments
1
Equipment Violation of operating
procedures
Internal Operations The equipment
can be damaged
if the operating
principles of the
equipment are
violated
2
Equipment Malfunctioning of
software/hardware
Internal IT
Department
The software or
hardware may
malfunction thus
leading to faults
in the equipment
3 Equipment Theft of equipment External Resource
manager
There may be
loss of equipment
due to theft
which in turn
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
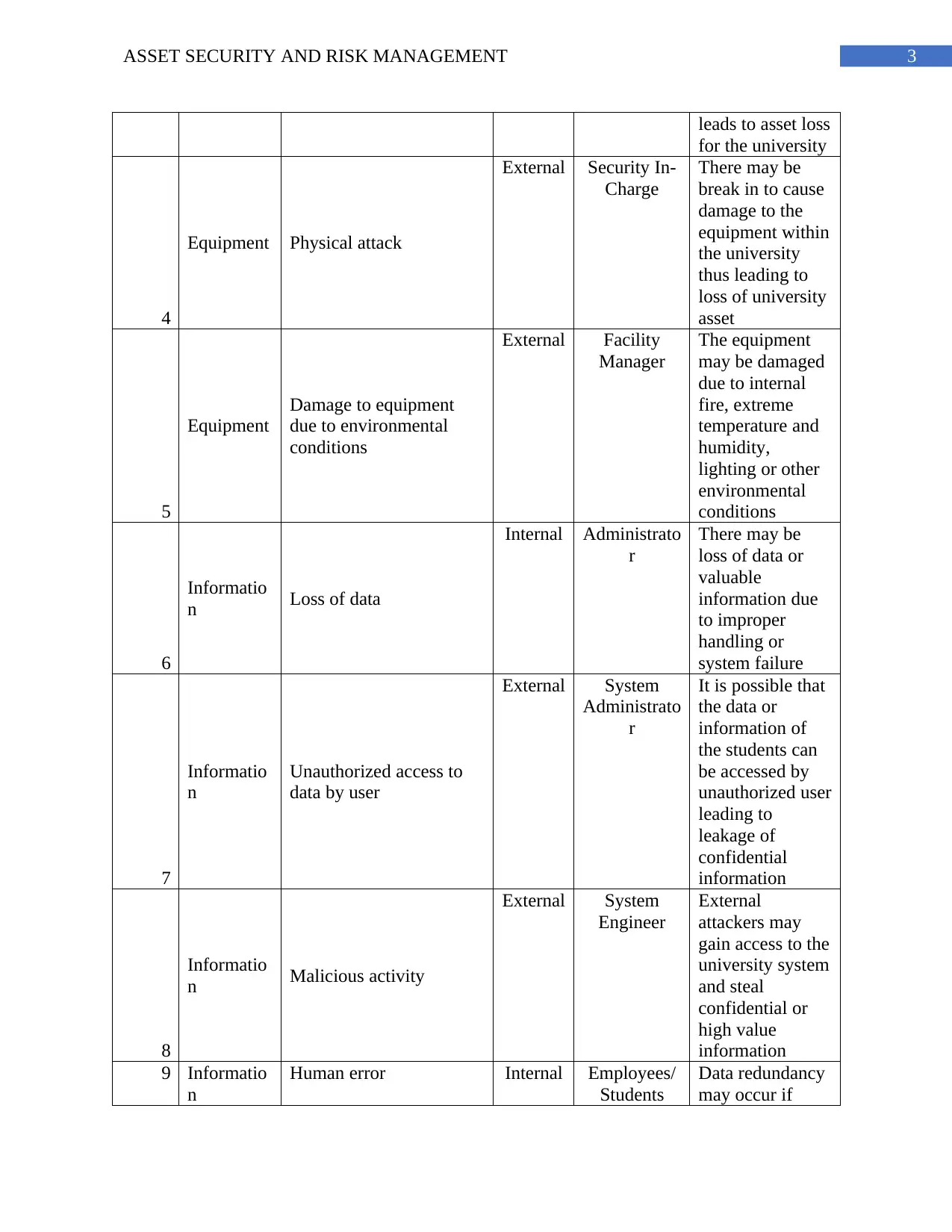
3ASSET SECURITY AND RISK MANAGEMENT
leads to asset loss
for the university
4
Equipment Physical attack
External Security In-
Charge
There may be
break in to cause
damage to the
equipment within
the university
thus leading to
loss of university
asset
5
Equipment
Damage to equipment
due to environmental
conditions
External Facility
Manager
The equipment
may be damaged
due to internal
fire, extreme
temperature and
humidity,
lighting or other
environmental
conditions
6
Informatio
n Loss of data
Internal Administrato
r
There may be
loss of data or
valuable
information due
to improper
handling or
system failure
7
Informatio
n
Unauthorized access to
data by user
External System
Administrato
r
It is possible that
the data or
information of
the students can
be accessed by
unauthorized user
leading to
leakage of
confidential
information
8
Informatio
n Malicious activity
External System
Engineer
External
attackers may
gain access to the
university system
and steal
confidential or
high value
information
9 Informatio
n
Human error Internal Employees/
Students
Data redundancy
may occur if
leads to asset loss
for the university
4
Equipment Physical attack
External Security In-
Charge
There may be
break in to cause
damage to the
equipment within
the university
thus leading to
loss of university
asset
5
Equipment
Damage to equipment
due to environmental
conditions
External Facility
Manager
The equipment
may be damaged
due to internal
fire, extreme
temperature and
humidity,
lighting or other
environmental
conditions
6
Informatio
n Loss of data
Internal Administrato
r
There may be
loss of data or
valuable
information due
to improper
handling or
system failure
7
Informatio
n
Unauthorized access to
data by user
External System
Administrato
r
It is possible that
the data or
information of
the students can
be accessed by
unauthorized user
leading to
leakage of
confidential
information
8
Informatio
n Malicious activity
External System
Engineer
External
attackers may
gain access to the
university system
and steal
confidential or
high value
information
9 Informatio
n
Human error Internal Employees/
Students
Data redundancy
may occur if
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
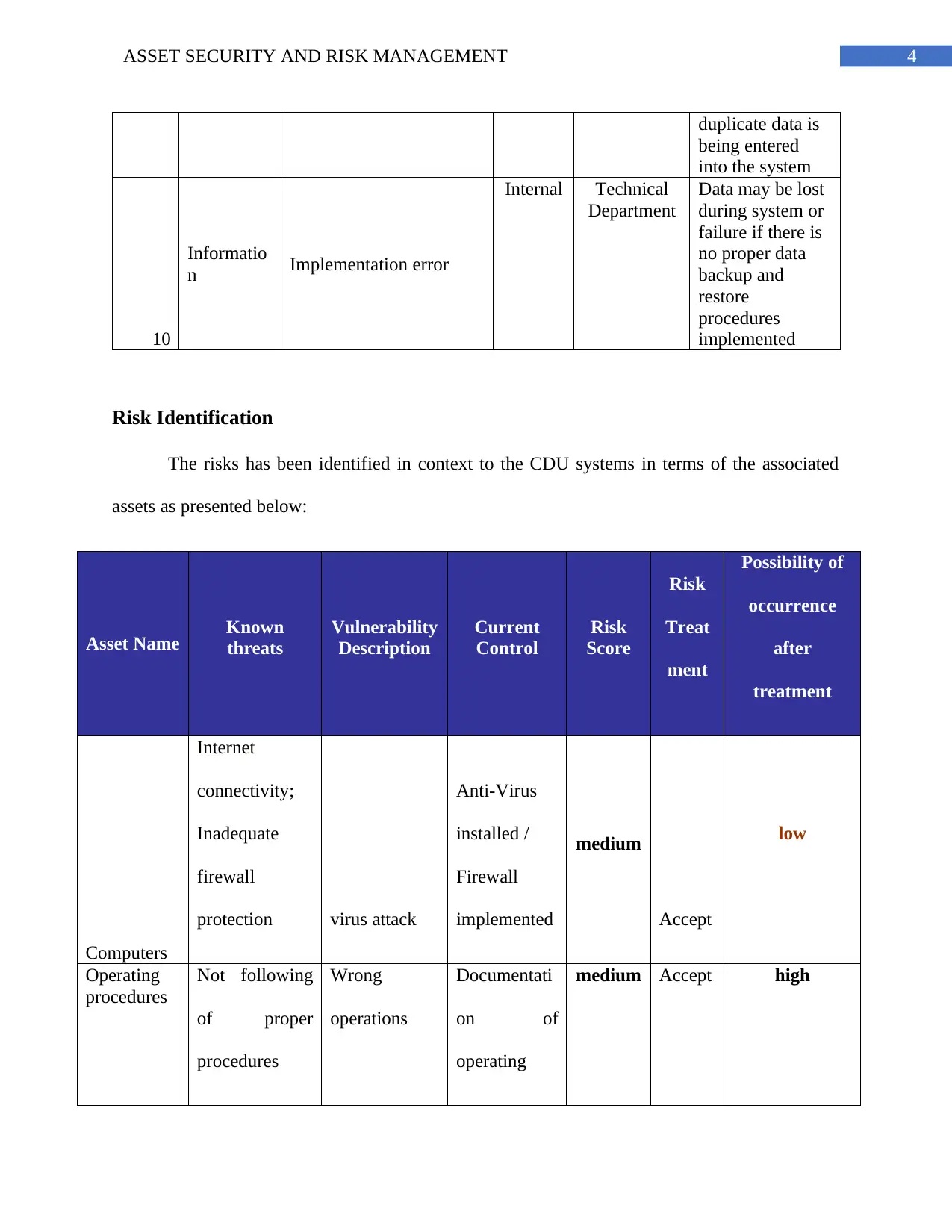
4ASSET SECURITY AND RISK MANAGEMENT
duplicate data is
being entered
into the system
10
Informatio
n Implementation error
Internal Technical
Department
Data may be lost
during system or
failure if there is
no proper data
backup and
restore
procedures
implemented
Risk Identification
The risks has been identified in context to the CDU systems in terms of the associated
assets as presented below:
Asset Name Known
threats
Vulnerability
Description
Current
Control
Risk
Score
Risk
Treat
ment
Possibility of
occurrence
after
treatment
Computers
Internet
connectivity;
Inadequate
firewall
protection virus attack
Anti-Virus
installed /
Firewall
implemented
medium
Accept
low
Operating
procedures
Not following
of proper
procedures
Wrong
operations
Documentati
on of
operating
medium Accept high
duplicate data is
being entered
into the system
10
Informatio
n Implementation error
Internal Technical
Department
Data may be lost
during system or
failure if there is
no proper data
backup and
restore
procedures
implemented
Risk Identification
The risks has been identified in context to the CDU systems in terms of the associated
assets as presented below:
Asset Name Known
threats
Vulnerability
Description
Current
Control
Risk
Score
Risk
Treat
ment
Possibility of
occurrence
after
treatment
Computers
Internet
connectivity;
Inadequate
firewall
protection virus attack
Anti-Virus
installed /
Firewall
implemented
medium
Accept
low
Operating
procedures
Not following
of proper
procedures
Wrong
operations
Documentati
on of
operating
medium Accept high
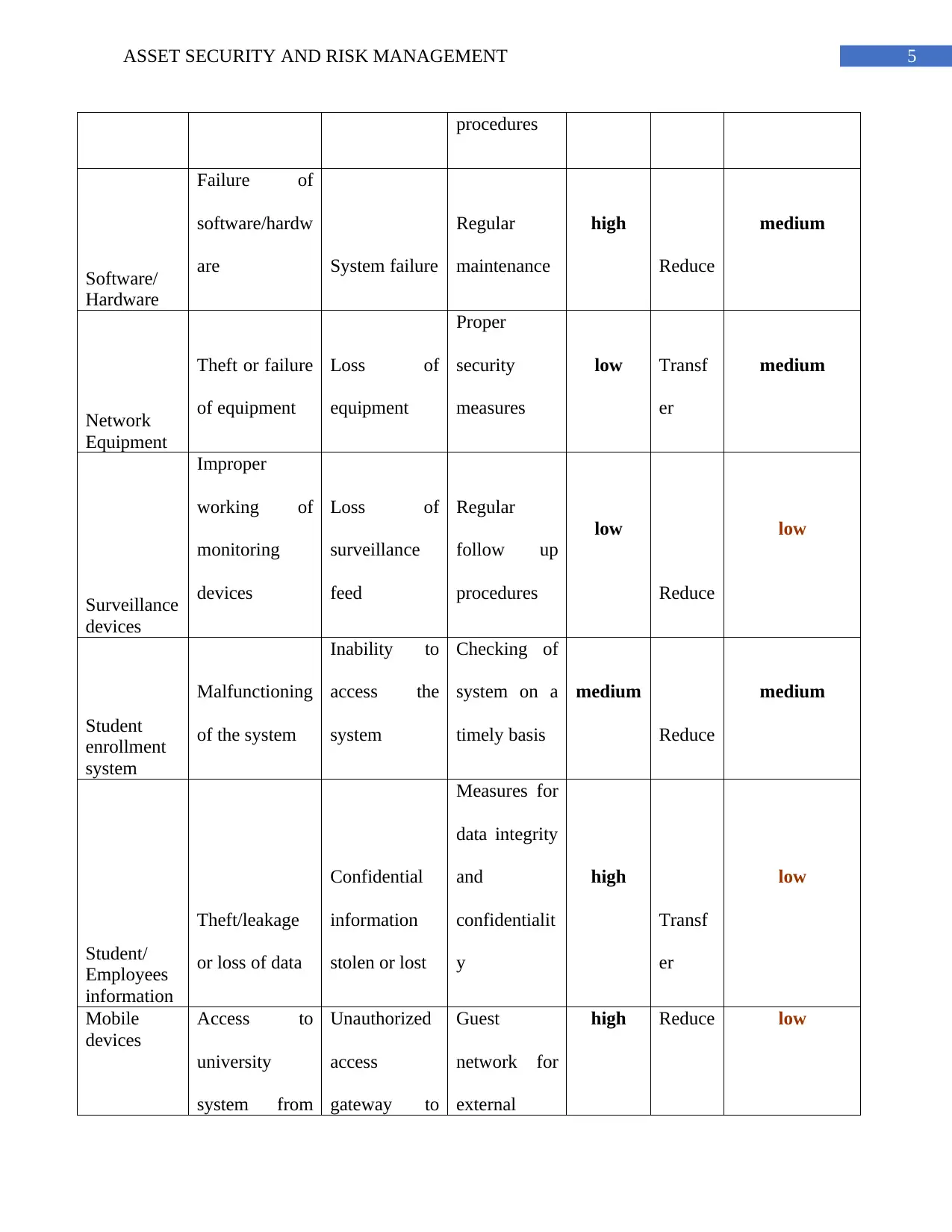
5ASSET SECURITY AND RISK MANAGEMENT
procedures
Software/
Hardware
Failure of
software/hardw
are System failure
Regular
maintenance
high
Reduce
medium
Network
Equipment
Theft or failure
of equipment
Loss of
equipment
Proper
security
measures
low Transf
er
medium
Surveillance
devices
Improper
working of
monitoring
devices
Loss of
surveillance
feed
Regular
follow up
procedures
low
Reduce
low
Student
enrollment
system
Malfunctioning
of the system
Inability to
access the
system
Checking of
system on a
timely basis
medium
Reduce
medium
Student/
Employees
information
Theft/leakage
or loss of data
Confidential
information
stolen or lost
Measures for
data integrity
and
confidentialit
y
high
Transf
er
low
Mobile
devices
Access to
university
system from
Unauthorized
access
gateway to
Guest
network for
external
high Reduce low
procedures
Software/
Hardware
Failure of
software/hardw
are System failure
Regular
maintenance
high
Reduce
medium
Network
Equipment
Theft or failure
of equipment
Loss of
equipment
Proper
security
measures
low Transf
er
medium
Surveillance
devices
Improper
working of
monitoring
devices
Loss of
surveillance
feed
Regular
follow up
procedures
low
Reduce
low
Student
enrollment
system
Malfunctioning
of the system
Inability to
access the
system
Checking of
system on a
timely basis
medium
Reduce
medium
Student/
Employees
information
Theft/leakage
or loss of data
Confidential
information
stolen or lost
Measures for
data integrity
and
confidentialit
y
high
Transf
er
low
Mobile
devices
Access to
university
system from
Unauthorized
access
gateway to
Guest
network for
external
high Reduce low
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
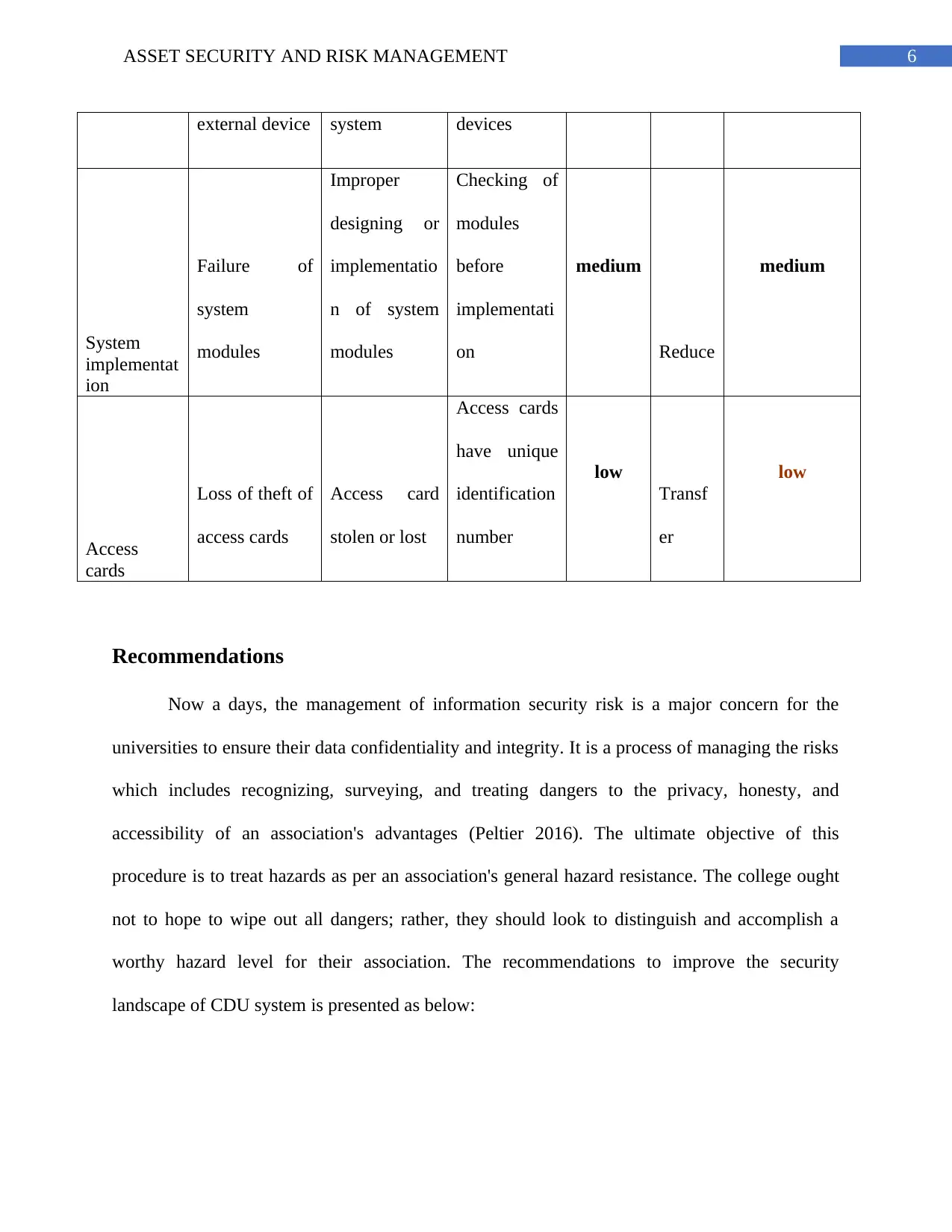
6ASSET SECURITY AND RISK MANAGEMENT
external device system devices
System
implementat
ion
Failure of
system
modules
Improper
designing or
implementatio
n of system
modules
Checking of
modules
before
implementati
on
medium
Reduce
medium
Access
cards
Loss of theft of
access cards
Access card
stolen or lost
Access cards
have unique
identification
number
low
Transf
er
low
Recommendations
Now a days, the management of information security risk is a major concern for the
universities to ensure their data confidentiality and integrity. It is a process of managing the risks
which includes recognizing, surveying, and treating dangers to the privacy, honesty, and
accessibility of an association's advantages (Peltier 2016). The ultimate objective of this
procedure is to treat hazards as per an association's general hazard resistance. The college ought
not to hope to wipe out all dangers; rather, they should look to distinguish and accomplish a
worthy hazard level for their association. The recommendations to improve the security
landscape of CDU system is presented as below:
external device system devices
System
implementat
ion
Failure of
system
modules
Improper
designing or
implementatio
n of system
modules
Checking of
modules
before
implementati
on
medium
Reduce
medium
Access
cards
Loss of theft of
access cards
Access card
stolen or lost
Access cards
have unique
identification
number
low
Transf
er
low
Recommendations
Now a days, the management of information security risk is a major concern for the
universities to ensure their data confidentiality and integrity. It is a process of managing the risks
which includes recognizing, surveying, and treating dangers to the privacy, honesty, and
accessibility of an association's advantages (Peltier 2016). The ultimate objective of this
procedure is to treat hazards as per an association's general hazard resistance. The college ought
not to hope to wipe out all dangers; rather, they should look to distinguish and accomplish a
worthy hazard level for their association. The recommendations to improve the security
landscape of CDU system is presented as below:
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

7ASSET SECURITY AND RISK MANAGEMENT
Identification of suitable stakeholders and roles: Suitable persons have to be given the
responsibility in case there is any occurrence of threat within the university. Different person will
be associated with supervising different assets of the university.
Development of proper strategy for information security: A broad risk-based and
campus wide policy should be developed to ensure that increasing security threats can be
prevented with the help of such policies.
Spreading awareness of information security: The importance of information security
should be spread among employees as well as students of the organization so that it is taken into
consideration as an essential factor. The risks associated with information security should have to
be mitigated as soon as determined otherwise it may lead to loss of confidential information.
Conclusion
From the overall discussion it can be concluded that with the help of proper risk
management or risk mitigation strategies the assets of the Charles Darwin University can be
stored securely and in a simultaneous manner all the risks can be mitigated. It has been found
that the risk assessment methodologies can ensure the risk assessments produce the comparable
and reproducible results for the Charles Darwin University. After identification of the risks those
are needed to be prioritized based on their negative impact. Risk management is somewhere
relayed to the asset management. The University also maintains some accurate risk management
strategies. In order to keep the assets secured from the external attackers the university also
adopted different advanced security and management strategies. Basically, with the help of the
risk management and risk treatment Charles Darwin University can reach the security goal.
Identification of suitable stakeholders and roles: Suitable persons have to be given the
responsibility in case there is any occurrence of threat within the university. Different person will
be associated with supervising different assets of the university.
Development of proper strategy for information security: A broad risk-based and
campus wide policy should be developed to ensure that increasing security threats can be
prevented with the help of such policies.
Spreading awareness of information security: The importance of information security
should be spread among employees as well as students of the organization so that it is taken into
consideration as an essential factor. The risks associated with information security should have to
be mitigated as soon as determined otherwise it may lead to loss of confidential information.
Conclusion
From the overall discussion it can be concluded that with the help of proper risk
management or risk mitigation strategies the assets of the Charles Darwin University can be
stored securely and in a simultaneous manner all the risks can be mitigated. It has been found
that the risk assessment methodologies can ensure the risk assessments produce the comparable
and reproducible results for the Charles Darwin University. After identification of the risks those
are needed to be prioritized based on their negative impact. Risk management is somewhere
relayed to the asset management. The University also maintains some accurate risk management
strategies. In order to keep the assets secured from the external attackers the university also
adopted different advanced security and management strategies. Basically, with the help of the
risk management and risk treatment Charles Darwin University can reach the security goal.

8ASSET SECURITY AND RISK MANAGEMENT
Bibliography
Ahmad, A., Maynard, S.B. and Park, S., 2014. Information security strategies: towards an
organizational multi-strategy perspective. Journal of Intelligent Manufacturing, 25(2), pp.357-
370.
Fenz, S., Heurix, J., Neubauer, T. and Pechstein, F., 2014. Current challenges in information
security risk management. Information Management & Computer Security, 22(5), pp.410-430.
Layton, T.P., 2016. Information Security: Design, implementation, measurement, and
compliance. CRC Press.
McIlwraith, A., 2016. Information security and employee behaviour: how to reduce risk through
employee education, training and awareness. Routledge.
Peltier, T.R., 2016. Information Security Policies, Procedures, and Standards: guidelines for
effective information security management. CRC Press.
Safa, N.S. and Von Solms, R., 2016. An information security knowledge sharing model in
organizations. Computers in Human Behavior, 57, pp.442-451.
Safa, N.S., Von Solms, R. and Futcher, L., 2016. Human aspects of information security in
organisations. Computer Fraud & Security, 2016(2), pp.15-18.
Webb, J., Ahmad, A., Maynard, S.B. and Shanks, G., 2014. A situation awareness model for
information security risk management. Computers & security, 44, pp.1-15.
Bibliography
Ahmad, A., Maynard, S.B. and Park, S., 2014. Information security strategies: towards an
organizational multi-strategy perspective. Journal of Intelligent Manufacturing, 25(2), pp.357-
370.
Fenz, S., Heurix, J., Neubauer, T. and Pechstein, F., 2014. Current challenges in information
security risk management. Information Management & Computer Security, 22(5), pp.410-430.
Layton, T.P., 2016. Information Security: Design, implementation, measurement, and
compliance. CRC Press.
McIlwraith, A., 2016. Information security and employee behaviour: how to reduce risk through
employee education, training and awareness. Routledge.
Peltier, T.R., 2016. Information Security Policies, Procedures, and Standards: guidelines for
effective information security management. CRC Press.
Safa, N.S. and Von Solms, R., 2016. An information security knowledge sharing model in
organizations. Computers in Human Behavior, 57, pp.442-451.
Safa, N.S., Von Solms, R. and Futcher, L., 2016. Human aspects of information security in
organisations. Computer Fraud & Security, 2016(2), pp.15-18.
Webb, J., Ahmad, A., Maynard, S.B. and Shanks, G., 2014. A situation awareness model for
information security risk management. Computers & security, 44, pp.1-15.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 9
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





