Automated Teller Machine (ATM) and Cyber-Security Analysis Report
VerifiedAdded on 2022/10/02
|10
|3344
|141
Report
AI Summary
This report provides a comprehensive analysis of ATM security and cyber-security, exploring various aspects such as confidentiality, integrity, and availability (CIA) in the context of ATM systems. It delves into the security of PINs, examining the maximum number of possible combinations and potential vulnerabilities. The report also analyzes the use of biometric security, discussing its advantages and disadvantages, including issues of accuracy, usability, and failure points. It highlights the potential for false positives and false negatives in biometric systems and their impact on ATM security. Furthermore, the report examines cryptographic substitution methods, specifically the Caesar and Vigenere ciphers, used to secure ATM transactions, detailing their decryption processes and security strengths and weaknesses. The report underscores the importance of robust security measures in ATM systems to protect against fraud and ensure customer data privacy. This assignment is contributed by a student to be published on the website Desklib, a platform which provides all the necessary AI based study tools for students.

Running head: ATM & CYBER-SECURITY
Automated Teller Machine & Cyber-security
Name of the Student
Name of the University
Author Note
Automated Teller Machine & Cyber-security
Name of the Student
Name of the University
Author Note
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

1ATM & CYBER-SECURITY
1. Confidentiality, Integrity, and availability in ATM security.
In the present time, information technology is widely used in home and organizations.
This means the information technology networks need to apply some information security
measures. Information security uses the CIA (confidentiality, integrity, and availability)
model for securing the whole network system (Stapleton, 2014). The CIA model represents
the main goals of the security system to obtain the information security that is:
Confidentiality, Availability and Integrity. These are the most general concepts of
information security. In order to avail security, CIA model is a must use method. The
requirements of the CIA model for an Automated teller machine as follows:
i. Confidentiality: Generally, to access any bank account from an automated teller
machine requires credit or debit card. For any user, The Personal Identification
Number (PIN) is the primary way to access their bank accounts (Khan, & Xu, 2015).
The ATM PIN is totally user's responsibility and using a strong PIN is always
recommended. In terms of confidentiality, a user always wants his/her PIN should be
confidential in the host system where he or she is entering to access their personal
account. Security of the PIN is the main concern for the banking system and user both
(Tuli & Kaur, 2013). During any transaction, the bank ensures the privacy of the
interaction between the user and bank servers. The entire transaction, including PIN,
is properly encrypted to avoid hackers. Hence, it can be said that confidentiality is the
highest level of the important factor to avail proper security.
ii. Integrity: Integrity means protecting the information from the third parties to avoid
any kind of manipulation. Tampering any information of a transaction can cost badly.
In ATM transactions value deposited or withdrawn by the user is maintained and
updated frequently after a transaction (Petrlic & Sorge, 2013). However, a specific
group of people should be assigned to handling the customers who have mismatched
information of account. This also holds the degree as high in terms of security.
iii. Availability: Availability refers that the ATM is available to access by the customers.
The services like balance query or statement are also frequently used features by any
customers. ATM showing Out of Service can lead the customer to dissatisfaction
towards the service (Mwatsika, 2014). ATM which have accurate services and better
usability can attract the users. The degree of availability is moderated.
2. PIN-Security analysis.
In this case, to guess the PIN of customer’s card will require many combinational tries
for the thief. To find out the maximum numbers of the combination will require some
permutations and combinations. A basic ATM has 0-9 buttons and some navigational keys
(Khalifa & Saadan, 2013). In this scenario, the thief has already cracked the five numeric
keys. Hence, he only needs the remaining five keys to generate a combination for ATM PIN.
Though it is known that ATM pin consists of 4 digits that can be in the range from 0000 to
9999 as the 9 is the highest and 0 is least available buttons. The maximum number of
combinations can be deduced by the following expression:
5P4 = 5! / (5-4)! = 5! / 1! = (5*4*3*2*1)/1=120
Hence, the maximum number of combinations of PINs that the thief requires to input is 120.
3. Biometric Security analysis.
Biometrics are basically automatic identification of individuals based on the
biological characteristics, in recent few years, biometrics have been used increasingly in
1. Confidentiality, Integrity, and availability in ATM security.
In the present time, information technology is widely used in home and organizations.
This means the information technology networks need to apply some information security
measures. Information security uses the CIA (confidentiality, integrity, and availability)
model for securing the whole network system (Stapleton, 2014). The CIA model represents
the main goals of the security system to obtain the information security that is:
Confidentiality, Availability and Integrity. These are the most general concepts of
information security. In order to avail security, CIA model is a must use method. The
requirements of the CIA model for an Automated teller machine as follows:
i. Confidentiality: Generally, to access any bank account from an automated teller
machine requires credit or debit card. For any user, The Personal Identification
Number (PIN) is the primary way to access their bank accounts (Khan, & Xu, 2015).
The ATM PIN is totally user's responsibility and using a strong PIN is always
recommended. In terms of confidentiality, a user always wants his/her PIN should be
confidential in the host system where he or she is entering to access their personal
account. Security of the PIN is the main concern for the banking system and user both
(Tuli & Kaur, 2013). During any transaction, the bank ensures the privacy of the
interaction between the user and bank servers. The entire transaction, including PIN,
is properly encrypted to avoid hackers. Hence, it can be said that confidentiality is the
highest level of the important factor to avail proper security.
ii. Integrity: Integrity means protecting the information from the third parties to avoid
any kind of manipulation. Tampering any information of a transaction can cost badly.
In ATM transactions value deposited or withdrawn by the user is maintained and
updated frequently after a transaction (Petrlic & Sorge, 2013). However, a specific
group of people should be assigned to handling the customers who have mismatched
information of account. This also holds the degree as high in terms of security.
iii. Availability: Availability refers that the ATM is available to access by the customers.
The services like balance query or statement are also frequently used features by any
customers. ATM showing Out of Service can lead the customer to dissatisfaction
towards the service (Mwatsika, 2014). ATM which have accurate services and better
usability can attract the users. The degree of availability is moderated.
2. PIN-Security analysis.
In this case, to guess the PIN of customer’s card will require many combinational tries
for the thief. To find out the maximum numbers of the combination will require some
permutations and combinations. A basic ATM has 0-9 buttons and some navigational keys
(Khalifa & Saadan, 2013). In this scenario, the thief has already cracked the five numeric
keys. Hence, he only needs the remaining five keys to generate a combination for ATM PIN.
Though it is known that ATM pin consists of 4 digits that can be in the range from 0000 to
9999 as the 9 is the highest and 0 is least available buttons. The maximum number of
combinations can be deduced by the following expression:
5P4 = 5! / (5-4)! = 5! / 1! = (5*4*3*2*1)/1=120
Hence, the maximum number of combinations of PINs that the thief requires to input is 120.
3. Biometric Security analysis.
Biometrics are basically automatic identification of individuals based on the
biological characteristics, in recent few years, biometrics have been used increasingly in

2ATM & CYBER-SECURITY
information systems, service systems, etc (Gelb & Clark, 2013). Using Biometrics for
security purpose may seem more secure than a PIN. Biometrics can add extra security
measures in order to reduce frauds, hacks and continuous evaluation of transactions.
However, there are some problem areas where the customers will hesitate to use Biometric
validation. The issues are discussed in brief below:
i. Accuracy: Integrating any biometrics is supposed to enhance the usability and
integrity of the system. However, proper authentication using biometrics is a
major issue as it may sometimes read the details inaccurately during analyzing
body parts (DeCann & Ross, 2015). In terms of face-recognizing, the body
parts are exposed to others in general. Although a hacker can generate the PIN
using brute force, a unique PIN is a fully private thing as it remains to that
person (Karovaliya et al., 2015). Every store, Facebook and where the CCTV
cameras are capturing the facial details. Hence it makes the security
vulnerability as it is easily accessible. Also, in terms of fingerprints, it is very
widely spread and not that much reliable.
ii. Usability: Although, biometric has changed the people’s life drastically in day
to day terms. However, using biometrics in ATM will not be an easy task for
some. As, an ATM is a self-service machine, after implementing the
biometrics, the users may not understand the interaction or they may not want
to. If a person is putting their face or eye near to any scanner, they might not
trust the machine. The machine has to be 100% reliable. On the other hand,
fingerprints scanner has some limitations like, they do not work when fingers
are dirty or moist (Kauba & Uhl, 2015). Also, if a person may not have hands
to or in future lost his or fingers, then it would be impossible for the users to
access their accounts.
iii. Failure Points: Today, in every smartphone, the fingerprint is available and it
has been witnessed that many times fail to recognize or unlock. The entire
framework of the ATM network is connected, as a single failure point can
cause the shutdown of the entire system. Again, the final biometric
information will be stored in a database and it will be easier to breach and
steal the biometric identification for a hacker (Illrnan, 2018). In some extent, a
PIN is replaceable if they got stolen. On another hand, facial or Irish
information cannot be replaced by another eye’s information. Once a hacker
was able to beat Apple’s TouchID technology after the iPhone released. The
same hacker again stole the fingerprint of German Defence Minister, Ursula
von der Leyen, using high-resolution pictures of her thumb only. He used
VeriFinger software for reconstructing the thumbprint from the taken pictures
(Alsaadi & Boult, 2016).
Though biometric should be an additional feature in terms of security, the systems
which have biometrics are most vulnerable for attacks and spoofing. The organizations
should think of developing a sensor that can differentiate between fake and real customers.
4. Error in biometric design.
False-positive is basically when the user receives the true data for a test where he/she
should have received an error. It means, first-person successfully authenticates the second
person's account via the first person's biometric inputs (Bolle, 2013). For example, an
Antivirus software mistakenly identifies a harmless file as a malicious file. This is error type
I. Another error is false negative where the person's biometric inputs are correct, however, the
information systems, service systems, etc (Gelb & Clark, 2013). Using Biometrics for
security purpose may seem more secure than a PIN. Biometrics can add extra security
measures in order to reduce frauds, hacks and continuous evaluation of transactions.
However, there are some problem areas where the customers will hesitate to use Biometric
validation. The issues are discussed in brief below:
i. Accuracy: Integrating any biometrics is supposed to enhance the usability and
integrity of the system. However, proper authentication using biometrics is a
major issue as it may sometimes read the details inaccurately during analyzing
body parts (DeCann & Ross, 2015). In terms of face-recognizing, the body
parts are exposed to others in general. Although a hacker can generate the PIN
using brute force, a unique PIN is a fully private thing as it remains to that
person (Karovaliya et al., 2015). Every store, Facebook and where the CCTV
cameras are capturing the facial details. Hence it makes the security
vulnerability as it is easily accessible. Also, in terms of fingerprints, it is very
widely spread and not that much reliable.
ii. Usability: Although, biometric has changed the people’s life drastically in day
to day terms. However, using biometrics in ATM will not be an easy task for
some. As, an ATM is a self-service machine, after implementing the
biometrics, the users may not understand the interaction or they may not want
to. If a person is putting their face or eye near to any scanner, they might not
trust the machine. The machine has to be 100% reliable. On the other hand,
fingerprints scanner has some limitations like, they do not work when fingers
are dirty or moist (Kauba & Uhl, 2015). Also, if a person may not have hands
to or in future lost his or fingers, then it would be impossible for the users to
access their accounts.
iii. Failure Points: Today, in every smartphone, the fingerprint is available and it
has been witnessed that many times fail to recognize or unlock. The entire
framework of the ATM network is connected, as a single failure point can
cause the shutdown of the entire system. Again, the final biometric
information will be stored in a database and it will be easier to breach and
steal the biometric identification for a hacker (Illrnan, 2018). In some extent, a
PIN is replaceable if they got stolen. On another hand, facial or Irish
information cannot be replaced by another eye’s information. Once a hacker
was able to beat Apple’s TouchID technology after the iPhone released. The
same hacker again stole the fingerprint of German Defence Minister, Ursula
von der Leyen, using high-resolution pictures of her thumb only. He used
VeriFinger software for reconstructing the thumbprint from the taken pictures
(Alsaadi & Boult, 2016).
Though biometric should be an additional feature in terms of security, the systems
which have biometrics are most vulnerable for attacks and spoofing. The organizations
should think of developing a sensor that can differentiate between fake and real customers.
4. Error in biometric design.
False-positive is basically when the user receives the true data for a test where he/she
should have received an error. It means, first-person successfully authenticates the second
person's account via the first person's biometric inputs (Bolle, 2013). For example, an
Antivirus software mistakenly identifies a harmless file as a malicious file. This is error type
I. Another error is false negative where the person's biometric inputs are correct, however, the
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

3ATM & CYBER-SECURITY
system fails to recognize him (Ray, Das & Sen, 2015). This is a type II error. Since both the
types are faults in the system, the presence of type II (false negative) error is more critical
than false positive. Two possible scenarios of the false-negative are discussed below:
As it is known that biometric means the face, Irish or thumb recognition, it would be
very hectic and painful in case of any emergency situation. Urgent need of cash or
information can be obtained as the biometric data is related to that specific individual.
That is where the situation becomes false negative. Also, it is observed that the false-
negative approaches in biometric are meant to access the location details of that event.
Sometimes, the real person is also not identified by the system due to technical issues.
This first scenario explains where the identity of a person is unknown. For example,
an organization's whole network infrastructure is down (Kannavara & Shippy, 2013).
The main personnel can access their datacentre to retrieve the service, however, their
biometric failed to identify. Every losing minute is causing financial and reputational
loss to the company.
This type of scenario can cause in creating death like situation. An employee who has
some medical history and suddenly need medical assistance (heart attack). His
colleagues can give him assistance, however, their biometric would not get
recognized. Them instead of helping out, this can cause more damage to that person
and most dangerous when it comes to life and for the entire workplace too. Apart
from that, there are several more types of incidents where the late in the
authentication can cause harm. The false-negative case is capable of shutting down
the whole organization.
5. Cryptography substitution methods
As per the name, substitution method refers to the substituting letter for another letter.
In cryptography, it is a where plaintext is replaced by ciphertext using a fixed substitution
system (Agibalov, 2017). Some of the substitution methods for deciphering plaintexts are
discussed and solved below.
1. Caesar Cipher (mono-alphabetic):
It’s a substitution method and mono-alphabetic cipher, which can be obtained by
substituting one letter from a plain text by another letter in the ciphertext. The concept of
shift is fixed between 0 to 25. It is known as Shift Cipher. However, a shift of three is
generally known as Caesar Cipher (Jain, Dedhia & Patil, 2015). In this very basic cipher,
both sender and receiver fix a secret shift number.
Deciphering Ciphertext: PIXW PIEVR
Process:
Step 1. The alphabets are organized is their corresponding numeric values. That will be used
in decryption.
A B C D E F G H I J K L M N O P Q R S T U V W X Y Z
0 1 2 3 4 5 6 7 8 9 10 1
1
12 13 1
4
15 16 1
7
18 19 20 2
1
22 23 2
4
25
system fails to recognize him (Ray, Das & Sen, 2015). This is a type II error. Since both the
types are faults in the system, the presence of type II (false negative) error is more critical
than false positive. Two possible scenarios of the false-negative are discussed below:
As it is known that biometric means the face, Irish or thumb recognition, it would be
very hectic and painful in case of any emergency situation. Urgent need of cash or
information can be obtained as the biometric data is related to that specific individual.
That is where the situation becomes false negative. Also, it is observed that the false-
negative approaches in biometric are meant to access the location details of that event.
Sometimes, the real person is also not identified by the system due to technical issues.
This first scenario explains where the identity of a person is unknown. For example,
an organization's whole network infrastructure is down (Kannavara & Shippy, 2013).
The main personnel can access their datacentre to retrieve the service, however, their
biometric failed to identify. Every losing minute is causing financial and reputational
loss to the company.
This type of scenario can cause in creating death like situation. An employee who has
some medical history and suddenly need medical assistance (heart attack). His
colleagues can give him assistance, however, their biometric would not get
recognized. Them instead of helping out, this can cause more damage to that person
and most dangerous when it comes to life and for the entire workplace too. Apart
from that, there are several more types of incidents where the late in the
authentication can cause harm. The false-negative case is capable of shutting down
the whole organization.
5. Cryptography substitution methods
As per the name, substitution method refers to the substituting letter for another letter.
In cryptography, it is a where plaintext is replaced by ciphertext using a fixed substitution
system (Agibalov, 2017). Some of the substitution methods for deciphering plaintexts are
discussed and solved below.
1. Caesar Cipher (mono-alphabetic):
It’s a substitution method and mono-alphabetic cipher, which can be obtained by
substituting one letter from a plain text by another letter in the ciphertext. The concept of
shift is fixed between 0 to 25. It is known as Shift Cipher. However, a shift of three is
generally known as Caesar Cipher (Jain, Dedhia & Patil, 2015). In this very basic cipher,
both sender and receiver fix a secret shift number.
Deciphering Ciphertext: PIXW PIEVR
Process:
Step 1. The alphabets are organized is their corresponding numeric values. That will be used
in decryption.
A B C D E F G H I J K L M N O P Q R S T U V W X Y Z
0 1 2 3 4 5 6 7 8 9 10 1
1
12 13 1
4
15 16 1
7
18 19 20 2
1
22 23 2
4
25
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
4ATM & CYBER-SECURITY
The first word in ciphertext: PIXW, Key=4.
Step 2. Write the ciphertext with their corresponding numeric value of the letters and
shifting key is given 4.
Ciphertext P I X W
Corresponding numeric value 15 8 23 22
Key 4 4 4 4
Step 3. Apply this mathematical expression to find the decoded cipher.
P = (X-K) mod 26
Here P = plaintext letter’s corresponding numeric value.
X= ciphertext letter's corresponding numeric value.
K= key.
For example: for the first ciphertext letter it will be.
P = (15-4) mod 26
P = 11 mod 26
Hence the First Plaintext letter’s corresponding numeric value is 11.
Similarly, decode all the letter by applying this expression.
Decoded from Caesar cipher 11 4 19 18
Plaintext L E T S
Hence, the first plaintext word is ‘LETS’
The second word in Cipher Text: PIEVR, Key=4.
Repeat the same steps.
Ciphertext P I E V R
Corresponding numeric value 15 8 4 21 17
Key 4 4 4 4 4
Decoded from Caesar cipher 11 4 0 17 13
Plaintext L E A R N
The first word in ciphertext: PIXW, Key=4.
Step 2. Write the ciphertext with their corresponding numeric value of the letters and
shifting key is given 4.
Ciphertext P I X W
Corresponding numeric value 15 8 23 22
Key 4 4 4 4
Step 3. Apply this mathematical expression to find the decoded cipher.
P = (X-K) mod 26
Here P = plaintext letter’s corresponding numeric value.
X= ciphertext letter's corresponding numeric value.
K= key.
For example: for the first ciphertext letter it will be.
P = (15-4) mod 26
P = 11 mod 26
Hence the First Plaintext letter’s corresponding numeric value is 11.
Similarly, decode all the letter by applying this expression.
Decoded from Caesar cipher 11 4 19 18
Plaintext L E T S
Hence, the first plaintext word is ‘LETS’
The second word in Cipher Text: PIEVR, Key=4.
Repeat the same steps.
Ciphertext P I E V R
Corresponding numeric value 15 8 4 21 17
Key 4 4 4 4 4
Decoded from Caesar cipher 11 4 0 17 13
Plaintext L E A R N
5ATM & CYBER-SECURITY
Hence, the Second Cipher text word is ‘LEARN’. As it can be seen that there are only 26
keys to find out, it can not be said secure. Any hacker can brute force to get the keys.
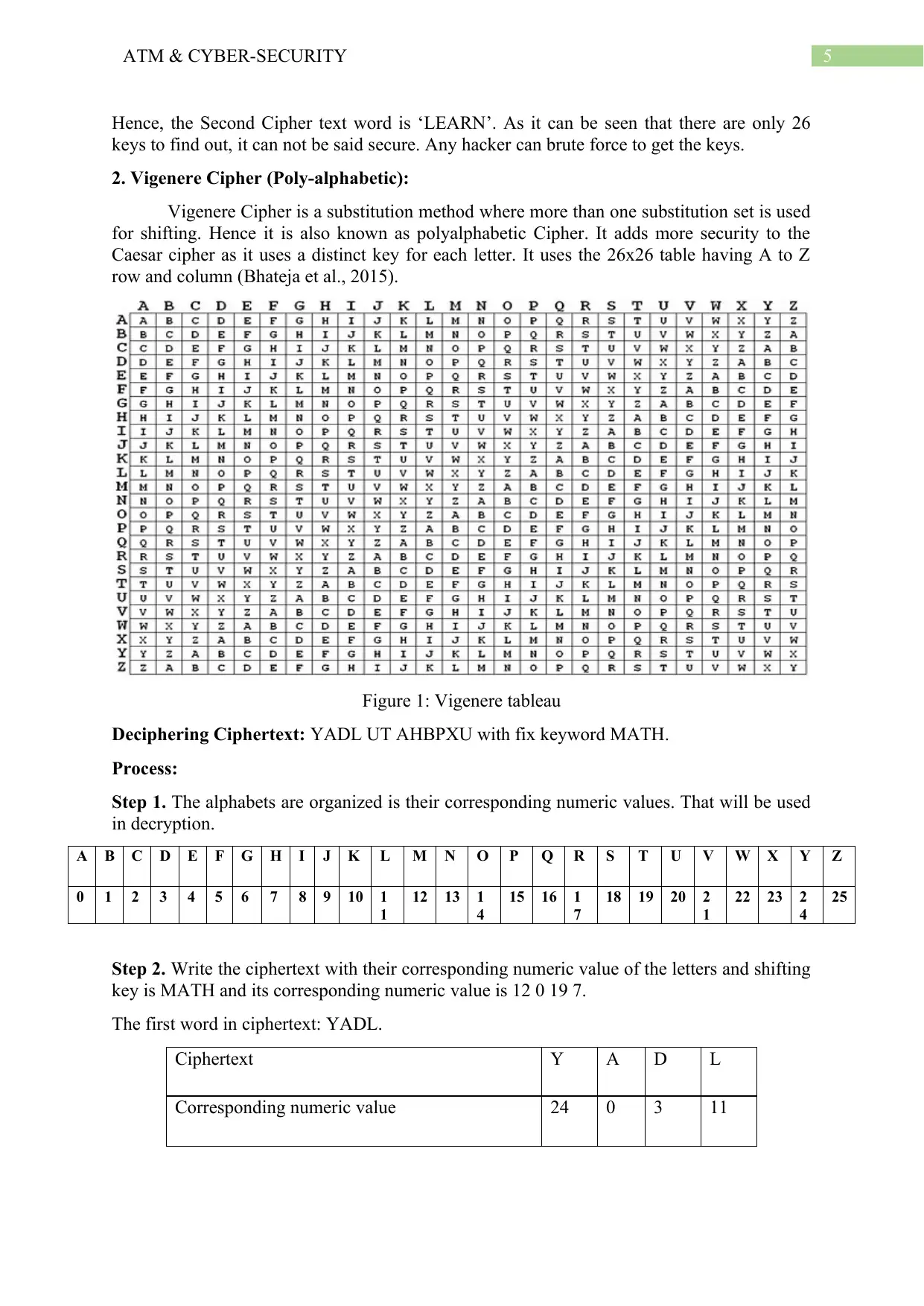
2. Vigenere Cipher (Poly-alphabetic):
Vigenere Cipher is a substitution method where more than one substitution set is used
for shifting. Hence it is also known as polyalphabetic Cipher. It adds more security to the
Caesar cipher as it uses a distinct key for each letter. It uses the 26x26 table having A to Z
row and column (Bhateja et al., 2015).
Figure 1: Vigenere tableau
Deciphering Ciphertext: YADL UT AHBPXU with fix keyword MATH.
Process:
Step 1. The alphabets are organized is their corresponding numeric values. That will be used
in decryption.
A B C D E F G H I J K L M N O P Q R S T U V W X Y Z
0 1 2 3 4 5 6 7 8 9 10 1
1
12 13 1
4
15 16 1
7
18 19 20 2
1
22 23 2
4
25
Step 2. Write the ciphertext with their corresponding numeric value of the letters and shifting
key is MATH and its corresponding numeric value is 12 0 19 7.
The first word in ciphertext: YADL.
Ciphertext Y A D L
Corresponding numeric value 24 0 3 11
Hence, the Second Cipher text word is ‘LEARN’. As it can be seen that there are only 26
keys to find out, it can not be said secure. Any hacker can brute force to get the keys.
2. Vigenere Cipher (Poly-alphabetic):
Vigenere Cipher is a substitution method where more than one substitution set is used
for shifting. Hence it is also known as polyalphabetic Cipher. It adds more security to the
Caesar cipher as it uses a distinct key for each letter. It uses the 26x26 table having A to Z
row and column (Bhateja et al., 2015).
Figure 1: Vigenere tableau
Deciphering Ciphertext: YADL UT AHBPXU with fix keyword MATH.
Process:
Step 1. The alphabets are organized is their corresponding numeric values. That will be used
in decryption.
A B C D E F G H I J K L M N O P Q R S T U V W X Y Z
0 1 2 3 4 5 6 7 8 9 10 1
1
12 13 1
4
15 16 1
7
18 19 20 2
1
22 23 2
4
25
Step 2. Write the ciphertext with their corresponding numeric value of the letters and shifting
key is MATH and its corresponding numeric value is 12 0 19 7.
The first word in ciphertext: YADL.
Ciphertext Y A D L
Corresponding numeric value 24 0 3 11
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

6ATM & CYBER-SECURITY
Key 12 0 19 7
Step 3. Apply the following mathematical expression to find the decoded cipher.
Dk (Ci) = (Ci – Ki) mod 26
Here Dk (Ci) = Plaintext letter’s corresponding numeric value from that Cipher text’s
letter.
Ci= Selected ciphertext letter's corresponding numeric value.
Ki= Select Cipher text letter’ Corresponding key.
For example: for the first ciphertext letter it will be.
D12 (C24) = (24-12) mod 26
D12 (C24) = 12 mod 26
For second letter,
D0 (C0) = (0-0) mod 26
D0 (C0) = 0 mod 26.
Hence the First and Second Plaintext letter’s corresponding numeric value is 12 and 0
respectively.
Similarly, decode all the letter by applying this expression.
Decode from Vigenere Cipher 12 0 10 4
Plain text M A K E
Hence, the first plaintext word is ‘MAKE’.
The second word in Cipher Text: UT
Repeat the same steps.
Ciphertext U T
Corresponding numeric value 20 19
Key 12 0
Decode from Vigenere Cipher 8 19
Plain text I T
Hence, the second plaintext word is ‘IT’.
Key 12 0 19 7
Step 3. Apply the following mathematical expression to find the decoded cipher.
Dk (Ci) = (Ci – Ki) mod 26
Here Dk (Ci) = Plaintext letter’s corresponding numeric value from that Cipher text’s
letter.
Ci= Selected ciphertext letter's corresponding numeric value.
Ki= Select Cipher text letter’ Corresponding key.
For example: for the first ciphertext letter it will be.
D12 (C24) = (24-12) mod 26
D12 (C24) = 12 mod 26
For second letter,
D0 (C0) = (0-0) mod 26
D0 (C0) = 0 mod 26.
Hence the First and Second Plaintext letter’s corresponding numeric value is 12 and 0
respectively.
Similarly, decode all the letter by applying this expression.
Decode from Vigenere Cipher 12 0 10 4
Plain text M A K E
Hence, the first plaintext word is ‘MAKE’.
The second word in Cipher Text: UT
Repeat the same steps.
Ciphertext U T
Corresponding numeric value 20 19
Key 12 0
Decode from Vigenere Cipher 8 19
Plain text I T
Hence, the second plaintext word is ‘IT’.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
7ATM & CYBER-SECURITY
The third word in Cipher Text: AHBPXU
Repeat the same steps.
Ciphertext A H B P X U
Corresponding numeric value 0 7 1 15 23 20
Key 19 7 12 0 19 7
Decode from Vigenere Cipher 7 0 15 15 4 13
Plain text H A P P E N
and, the third plaintext word is ‘HAPPEN’. The maximum possible combination of vigenere
cipher is 26the length of the message. Hence it is next to impossible to crack the key and it provides
more security.
The third word in Cipher Text: AHBPXU
Repeat the same steps.
Ciphertext A H B P X U
Corresponding numeric value 0 7 1 15 23 20
Key 19 7 12 0 19 7
Decode from Vigenere Cipher 7 0 15 15 4 13
Plain text H A P P E N
and, the third plaintext word is ‘HAPPEN’. The maximum possible combination of vigenere
cipher is 26the length of the message. Hence it is next to impossible to crack the key and it provides
more security.

8ATM & CYBER-SECURITY
References
Agibalov, G. P. (2017). Substitution block ciphers with functional keys. Прикладная
дискретная математика, (4 (38)).
Alsaadi, F. E., & Boult, T. E. (2016). Perpetuating Biometrics for Authentication.
In Information Technology: New Generations (pp. 161-176). Springer, Cham.
Bhateja, A. K., Bhateja, A., Chaudhury, S., & Saxena, P. K. (2015). Cryptanalysis of
vigenere cipher using cuckoo search. Applied Soft Computing, 26, 315-324.
Bolle, R. M., Connell, J. H., Pankanti, S., Ratha, N. K., & Senior, A. W. (2013). Guide to
biometrics. Springer Science & Business Media.
DeCann, B., & Ross, A. (2015). Modelling errors in a biometric re-identification system. IET
Biometrics, 4(4), 209-219.
Gelb, A., & Clark, J. (2013). Identification for development: The biometrics revolution.
Center for Global Development Working Paper, (315).
Illrnan, E. J. (2018). Data Privacy Laws Targeting Biometric and Geolocation Technologies.
Jain, A., Dedhia, R., & Patil, A. (2015). Enhancing the security of caesar cipher substitution
method using a randomized approach for more secure communication. arXiv preprint
arXiv:1512.05483.
Kannavara, R., & Shippy, K. L. (2013). Topics in biometric human-machine interaction
security. IEEE Potentials, 32(6), 18-25.
Karovaliya, M., Karedia, S., Oza, S., & Kalbande, D. R. (2015). Enhanced security for ATM
machine with OTP and Facial recognition features. Procedia Computer Science, 45,
390-396.
Kauba, C., & Uhl, A. (2015, September). Robustness evaluation of hand vein recognition
systems. In 2015 International Conference of the Biometrics Special Interest Group
(BIOSIG) (pp. 1-5). IEEE.
Khalifa, S. S., & Saadan, K. (2013). The formal design model of an automatic teller machine
(ATM). world, 3, 4.
Khan, R., Hasan, R., & Xu, J. (2015, March). SEPIA: Secure-PIN-authentication-as-a-service
for ATM using mobile and wearable devices. In 2015 3rd IEEE International
Conference on Mobile Cloud Computing, Services, and Engineering (pp. 41-50).
IEEE.
Mwatsika, C. (2014). Customers satisfaction with ATM banking in Malawi. African journal
of business management, 8(7), 218-227.
Petrlic, R., & Sorge, C. (2013). Establishing user trust in automated teller machine
integrity. IET Information Security, 8(2), 132-139.
Ray, S., Das, S., & Sen, A. (2015, December). An intelligent vision system for monitoring
security and surveillance of ATM. In 2015 Annual IEEE India Conference
(INDICON) (pp. 1-5). IEEE.
Stapleton, J. J. (2014). Security without obscurity: A guide to confidentiality, authentication,
and integrity. Auerbach Publications.
References
Agibalov, G. P. (2017). Substitution block ciphers with functional keys. Прикладная
дискретная математика, (4 (38)).
Alsaadi, F. E., & Boult, T. E. (2016). Perpetuating Biometrics for Authentication.
In Information Technology: New Generations (pp. 161-176). Springer, Cham.
Bhateja, A. K., Bhateja, A., Chaudhury, S., & Saxena, P. K. (2015). Cryptanalysis of
vigenere cipher using cuckoo search. Applied Soft Computing, 26, 315-324.
Bolle, R. M., Connell, J. H., Pankanti, S., Ratha, N. K., & Senior, A. W. (2013). Guide to
biometrics. Springer Science & Business Media.
DeCann, B., & Ross, A. (2015). Modelling errors in a biometric re-identification system. IET
Biometrics, 4(4), 209-219.
Gelb, A., & Clark, J. (2013). Identification for development: The biometrics revolution.
Center for Global Development Working Paper, (315).
Illrnan, E. J. (2018). Data Privacy Laws Targeting Biometric and Geolocation Technologies.
Jain, A., Dedhia, R., & Patil, A. (2015). Enhancing the security of caesar cipher substitution
method using a randomized approach for more secure communication. arXiv preprint
arXiv:1512.05483.
Kannavara, R., & Shippy, K. L. (2013). Topics in biometric human-machine interaction
security. IEEE Potentials, 32(6), 18-25.
Karovaliya, M., Karedia, S., Oza, S., & Kalbande, D. R. (2015). Enhanced security for ATM
machine with OTP and Facial recognition features. Procedia Computer Science, 45,
390-396.
Kauba, C., & Uhl, A. (2015, September). Robustness evaluation of hand vein recognition
systems. In 2015 International Conference of the Biometrics Special Interest Group
(BIOSIG) (pp. 1-5). IEEE.
Khalifa, S. S., & Saadan, K. (2013). The formal design model of an automatic teller machine
(ATM). world, 3, 4.
Khan, R., Hasan, R., & Xu, J. (2015, March). SEPIA: Secure-PIN-authentication-as-a-service
for ATM using mobile and wearable devices. In 2015 3rd IEEE International
Conference on Mobile Cloud Computing, Services, and Engineering (pp. 41-50).
IEEE.
Mwatsika, C. (2014). Customers satisfaction with ATM banking in Malawi. African journal
of business management, 8(7), 218-227.
Petrlic, R., & Sorge, C. (2013). Establishing user trust in automated teller machine
integrity. IET Information Security, 8(2), 132-139.
Ray, S., Das, S., & Sen, A. (2015, December). An intelligent vision system for monitoring
security and surveillance of ATM. In 2015 Annual IEEE India Conference
(INDICON) (pp. 1-5). IEEE.
Stapleton, J. J. (2014). Security without obscurity: A guide to confidentiality, authentication,
and integrity. Auerbach Publications.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

9ATM & CYBER-SECURITY
Tuli, K., & Kaur, G. (2013). ATM SAFETY & SECURITY. International Journal of
Advanced Research in IT and Engineering, 1-4.
Tuli, K., & Kaur, G. (2013). ATM SAFETY & SECURITY. International Journal of
Advanced Research in IT and Engineering, 1-4.
1 out of 10
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.


