Information System Security Analysis: ATM Case Study
VerifiedAdded on 2021/04/21
|5
|1413
|122
Homework Assignment
AI Summary
This assignment delves into the intricacies of ATM security, examining crucial aspects such as confidentiality, integrity, and availability to ensure the secure operation of automated teller machines. The analysis explores the implications of a security breach, such as a thief breaking keys and attempting unauthorized access, and discusses the limitations imposed by security measures like PIN entry limits. The assignment highlights the advantages of biometric authentication, including convenience and non-transferability, while also addressing potential vulnerabilities like false positives and false negatives. Additionally, the assignment demonstrates decryption techniques, using columnar transposition and Caesar cipher methods to decode encrypted text, illustrating practical applications of security principles in information systems.

Running head: INFORMATION SYSTEM
Information System for Automated Teller Machines
Name of Student-
Name of University-
Author’s Note-
Information System for Automated Teller Machines
Name of Student-
Name of University-
Author’s Note-
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

1INFORMATION SYSTEM
Question 1:
Confidentiality-
Confidentiality in ATM cards means keeping the credentials of the cards private and protects them from data breach.
The sensitive information that is the security pin, card number, the CVV number are to be kept private.
Confidentiality ensures that right person should have access to the right information and protects them to reach to wrong
people (Chen, Pande & Mohapatra, 2014).
To keep the data confidential, the experts of information security system makes the system more secured.
Integrity-
The main purpose of integrity is to maintain the trustworthiness, consistency, and accuracy of the data throughout the life cycle
of the system.
The data that is available in the ATM card should not be changed or altered by some unauthorized people in case of data
breach.
Data integrity ensures user access control and file permission access to the users.
Security should be established in case there is some alteration of data that are generally caused by human interruption.
Availability-
The availability of data ensures that the data should be available with the ATM user for the transaction to occur successful.
Availability ensures that proper functioning of the system should be there with all the software on update.
There should be proper safeguards to protect the available data that user has access (Luca et al., 2015).
There should no denial-of-service attack for the available data.
Question 2:
According to the question, the thief broke five keys of the ATM machine and also jammed the card reader of the machine.
When the customer came to withdraw money, his transaction was successful, but he was not able to take out the card, as the reader
was jammed. The customer went to seek help outside to take the card, at the mean while the thief thought of taking out some money
from the ATM. As he has broken five keys, he was only left with five keys. With those five keys, he has a total possibility of
5! /(5-4)! = 120 ways by which the thief can get the pin of the ATM.
But, the thief cannot enter 120 time the pin in the ATM because of the security purpose. The ATM machine security gives a
maximum limit of three times to enter the pin of the ATM (Kim et al., 2015). After three times wrong pin, the card will be
automatically blocked and the customer will get to know about that.
Question 3:
There are many reasons for which the users depends on biometric authentication for their security of personal and official
credentials. The advantages of biometric authentication are listed below:
Biometric authentication provides convenience to the users. The level of convenience is generally increased with the biometric
authentication. With all the practices that are involved in biometric authentication, there is no need to secure them with
Question 1:
Confidentiality-
Confidentiality in ATM cards means keeping the credentials of the cards private and protects them from data breach.
The sensitive information that is the security pin, card number, the CVV number are to be kept private.
Confidentiality ensures that right person should have access to the right information and protects them to reach to wrong
people (Chen, Pande & Mohapatra, 2014).
To keep the data confidential, the experts of information security system makes the system more secured.
Integrity-
The main purpose of integrity is to maintain the trustworthiness, consistency, and accuracy of the data throughout the life cycle
of the system.
The data that is available in the ATM card should not be changed or altered by some unauthorized people in case of data
breach.
Data integrity ensures user access control and file permission access to the users.
Security should be established in case there is some alteration of data that are generally caused by human interruption.
Availability-
The availability of data ensures that the data should be available with the ATM user for the transaction to occur successful.
Availability ensures that proper functioning of the system should be there with all the software on update.
There should be proper safeguards to protect the available data that user has access (Luca et al., 2015).
There should no denial-of-service attack for the available data.
Question 2:
According to the question, the thief broke five keys of the ATM machine and also jammed the card reader of the machine.
When the customer came to withdraw money, his transaction was successful, but he was not able to take out the card, as the reader
was jammed. The customer went to seek help outside to take the card, at the mean while the thief thought of taking out some money
from the ATM. As he has broken five keys, he was only left with five keys. With those five keys, he has a total possibility of
5! /(5-4)! = 120 ways by which the thief can get the pin of the ATM.
But, the thief cannot enter 120 time the pin in the ATM because of the security purpose. The ATM machine security gives a
maximum limit of three times to enter the pin of the ATM (Kim et al., 2015). After three times wrong pin, the card will be
automatically blocked and the customer will get to know about that.
Question 3:
There are many reasons for which the users depends on biometric authentication for their security of personal and official
credentials. The advantages of biometric authentication are listed below:
Biometric authentication provides convenience to the users. The level of convenience is generally increased with the biometric
authentication. With all the practices that are involved in biometric authentication, there is no need to secure them with
2INFORMATION SYSTEM
password. To remember passwords all the times they are changed are very difficult to remember. Biometric authentication
does not need all such difficulties.
The biometric is very easy to use as it only scans the physical parts of the body (Barbosa & Silva, 2015). The installation
process of biometric is also very easy and there is no headache of remembering the password for authentication. The
fingerprint, voice scanning, face and retina are generally used for the biometric authentication.
Another advantage of biometric authentication is that the parts that are scanned are actually non-transferable. The passwords
and user ids can be transferable and consumes much time. But the biometric authentication consumes less amount of time of
almost less than 5 seconds.
Question 4:
The false positive authentication of biometric mainly happens when the data of an un-authenticated user seems to be similar to
that of the authenticated one (Alsaadi, 2015). The database of the biometric thinks that the credentials of an authenticated user is
similar to that of un-authenticated user and allows the unauthenticated user to access the system. Whereas, biometric authentication
that is false negative generally happens when the authenticated user is rejected from the accessing the system. The system cannot
detect the authenticate user.
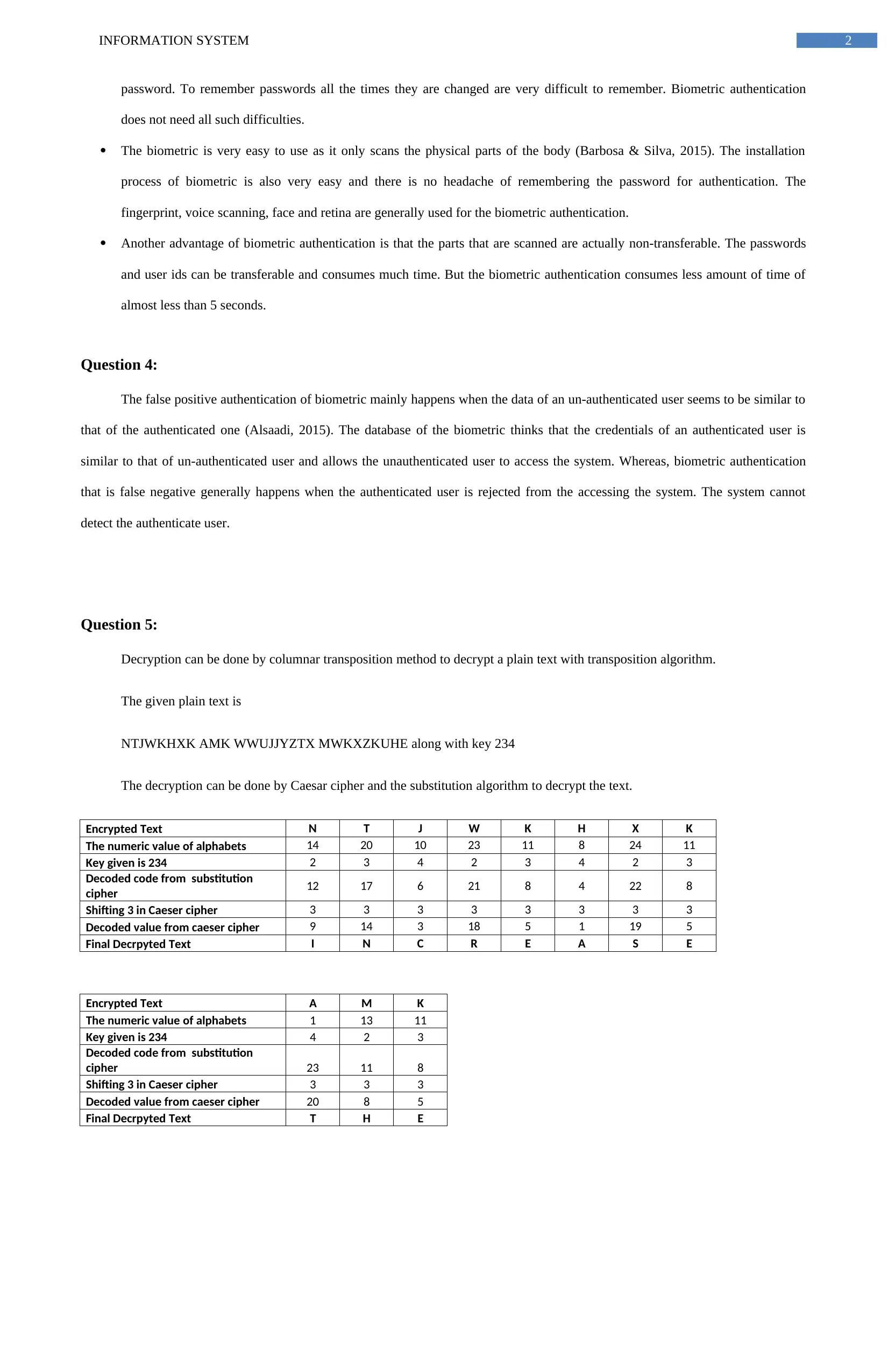
Question 5:
Decryption can be done by columnar transposition method to decrypt a plain text with transposition algorithm.
The given plain text is
NTJWKHXK AMK WWUJJYZTX MWKXZKUHE along with key 234
The decryption can be done by Caesar cipher and the substitution algorithm to decrypt the text.
Encrypted Text N T J W K H X K
The numeric value of alphabets 14 20 10 23 11 8 24 11
Key given is 234 2 3 4 2 3 4 2 3
Decoded code from substitution
cipher 12 17 6 21 8 4 22 8
Shifting 3 in Caeser cipher 3 3 3 3 3 3 3 3
Decoded value from caeser cipher 9 14 3 18 5 1 19 5
Final Decrpyted Text I N C R E A S E
Encrypted Text A M K
The numeric value of alphabets 1 13 11
Key given is 234 4 2 3
Decoded code from substitution
cipher 23 11 8
Shifting 3 in Caeser cipher 3 3 3
Decoded value from caeser cipher 20 8 5
Final Decrpyted Text T H E
password. To remember passwords all the times they are changed are very difficult to remember. Biometric authentication
does not need all such difficulties.
The biometric is very easy to use as it only scans the physical parts of the body (Barbosa & Silva, 2015). The installation
process of biometric is also very easy and there is no headache of remembering the password for authentication. The
fingerprint, voice scanning, face and retina are generally used for the biometric authentication.
Another advantage of biometric authentication is that the parts that are scanned are actually non-transferable. The passwords
and user ids can be transferable and consumes much time. But the biometric authentication consumes less amount of time of
almost less than 5 seconds.
Question 4:
The false positive authentication of biometric mainly happens when the data of an un-authenticated user seems to be similar to
that of the authenticated one (Alsaadi, 2015). The database of the biometric thinks that the credentials of an authenticated user is
similar to that of un-authenticated user and allows the unauthenticated user to access the system. Whereas, biometric authentication
that is false negative generally happens when the authenticated user is rejected from the accessing the system. The system cannot
detect the authenticate user.
Question 5:
Decryption can be done by columnar transposition method to decrypt a plain text with transposition algorithm.
The given plain text is
NTJWKHXK AMK WWUJJYZTX MWKXZKUHE along with key 234
The decryption can be done by Caesar cipher and the substitution algorithm to decrypt the text.
Encrypted Text N T J W K H X K
The numeric value of alphabets 14 20 10 23 11 8 24 11
Key given is 234 2 3 4 2 3 4 2 3
Decoded code from substitution
cipher 12 17 6 21 8 4 22 8
Shifting 3 in Caeser cipher 3 3 3 3 3 3 3 3
Decoded value from caeser cipher 9 14 3 18 5 1 19 5
Final Decrpyted Text I N C R E A S E
Encrypted Text A M K
The numeric value of alphabets 1 13 11
Key given is 234 4 2 3
Decoded code from substitution
cipher 23 11 8
Shifting 3 in Caeser cipher 3 3 3
Decoded value from caeser cipher 20 8 5
Final Decrpyted Text T H E
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
3INFORMATION SYSTEM
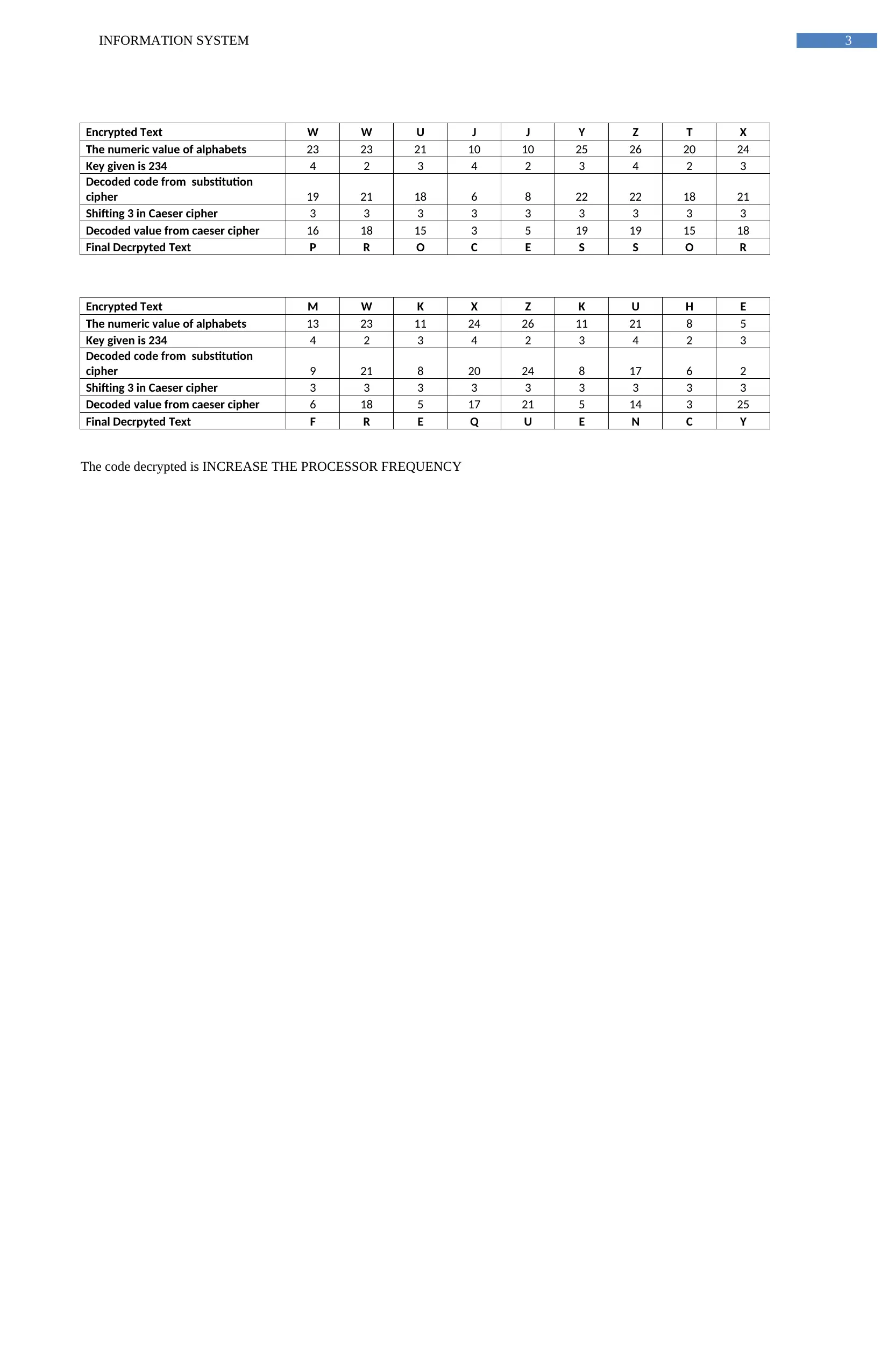
Encrypted Text W W U J J Y Z T X
The numeric value of alphabets 23 23 21 10 10 25 26 20 24
Key given is 234 4 2 3 4 2 3 4 2 3
Decoded code from substitution
cipher 19 21 18 6 8 22 22 18 21
Shifting 3 in Caeser cipher 3 3 3 3 3 3 3 3 3
Decoded value from caeser cipher 16 18 15 3 5 19 19 15 18
Final Decrpyted Text P R O C E S S O R
Encrypted Text M W K X Z K U H E
The numeric value of alphabets 13 23 11 24 26 11 21 8 5
Key given is 234 4 2 3 4 2 3 4 2 3
Decoded code from substitution
cipher 9 21 8 20 24 8 17 6 2
Shifting 3 in Caeser cipher 3 3 3 3 3 3 3 3 3
Decoded value from caeser cipher 6 18 5 17 21 5 14 3 25
Final Decrpyted Text F R E Q U E N C Y
The code decrypted is INCREASE THE PROCESSOR FREQUENCY
Encrypted Text W W U J J Y Z T X
The numeric value of alphabets 23 23 21 10 10 25 26 20 24
Key given is 234 4 2 3 4 2 3 4 2 3
Decoded code from substitution
cipher 19 21 18 6 8 22 22 18 21
Shifting 3 in Caeser cipher 3 3 3 3 3 3 3 3 3
Decoded value from caeser cipher 16 18 15 3 5 19 19 15 18
Final Decrpyted Text P R O C E S S O R
Encrypted Text M W K X Z K U H E
The numeric value of alphabets 13 23 11 24 26 11 21 8 5
Key given is 234 4 2 3 4 2 3 4 2 3
Decoded code from substitution
cipher 9 21 8 20 24 8 17 6 2
Shifting 3 in Caeser cipher 3 3 3 3 3 3 3 3 3
Decoded value from caeser cipher 6 18 5 17 21 5 14 3 25
Final Decrpyted Text F R E Q U E N C Y
The code decrypted is INCREASE THE PROCESSOR FREQUENCY
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

4INFORMATION SYSTEM
References
Alsaadi, I. M. (2015). Physiological Biometric Authentication Systems, Advantages, Disadvantages And Future Development: A
Review. International Journal Of Scientific & Technology Research, 4(8), 285-289.
Barbosa, F. G., & Silva, W. L. S. (2015, November). Support vector machines, Mel-Frequency Cepstral Coefficients and the Discrete
Cosine Transform applied on voice based biometric authentication. In SAI Intelligent Systems Conference (IntelliSys),
2015 (pp. 1032-1039). IEEE.
Chen, S., Pande, A., & Mohapatra, P. (2014, June). Sensor-assisted facial recognition: an enhanced biometric authentication system
for smartphones. In Proceedings of the 12th annual international conference on Mobile systems, applications, and
services (pp. 109-122). ACM.
De Luca, A., Hang, A., Von Zezschwitz, E., & Hussmann, H. (2015, April). I feel like I'm taking selfies all day!: towards
understanding biometric authentication on smartphones. In Proceedings of the 33rd Annual ACM Conference on Human
Factors in Computing Systems (pp. 1411-1414). ACM.
Kim, H., Park, J., Lee, J., & Ryou, J. (2015). Biometric authentication technology trends in smart device environment. In Mobile and
Wireless Technology 2015 (pp. 199-206). Springer, Berlin, Heidelberg.
References
Alsaadi, I. M. (2015). Physiological Biometric Authentication Systems, Advantages, Disadvantages And Future Development: A
Review. International Journal Of Scientific & Technology Research, 4(8), 285-289.
Barbosa, F. G., & Silva, W. L. S. (2015, November). Support vector machines, Mel-Frequency Cepstral Coefficients and the Discrete
Cosine Transform applied on voice based biometric authentication. In SAI Intelligent Systems Conference (IntelliSys),
2015 (pp. 1032-1039). IEEE.
Chen, S., Pande, A., & Mohapatra, P. (2014, June). Sensor-assisted facial recognition: an enhanced biometric authentication system
for smartphones. In Proceedings of the 12th annual international conference on Mobile systems, applications, and
services (pp. 109-122). ACM.
De Luca, A., Hang, A., Von Zezschwitz, E., & Hussmann, H. (2015, April). I feel like I'm taking selfies all day!: towards
understanding biometric authentication on smartphones. In Proceedings of the 33rd Annual ACM Conference on Human
Factors in Computing Systems (pp. 1411-1414). ACM.
Kim, H., Park, J., Lee, J., & Ryou, J. (2015). Biometric authentication technology trends in smart device environment. In Mobile and
Wireless Technology 2015 (pp. 199-206). Springer, Berlin, Heidelberg.
1 out of 5
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.




