Detailed System Architecture Report: ATM Transaction System
VerifiedAdded on 2021/06/17
|10
|1165
|436
Report
AI Summary
This report provides a comprehensive analysis of the ATM (Automated Teller Machine) transaction system architecture. It begins with a description of the ATM system, its functionalities, and the user interface. The report then details the three tiers of the system: presentation, logic, and data tiers, explaining their roles and interactions. Section 2 focuses on the system's design, including class, activity, sequence, and use case diagrams, along with user interface designs for the welcome and transaction selection pages. Section 3 discusses the robustness of the ATM design, covering fault tolerance, minimal recovery time, scalability, and security features. The report concludes with a list of references, providing a thorough examination of the ATM system's architecture and operational aspects. The report is a student submission to Desklib, a platform offering AI-driven study tools and resources.

Running head: SYSTEM ARCHITECTURE - TRANSACTION SYSTEM
System architecture: Transaction system “ATM”
Student Name:
University Name:
System architecture: Transaction system “ATM”
Student Name:
University Name:
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

1SYSTEM ARCHITECTURE - TRANSACTION SYSTEM
Table of Contents
Section 1.................................................................................................................................................................2
Description of the system...................................................................................................................................2
Tiers of the system.............................................................................................................................................2
Overall structure of the implementation............................................................................................................2
Section 2.................................................................................................................................................................3
Class diagram......................................................................................................................................................3
Activity diagram..................................................................................................................................................4
Sequence diagram..............................................................................................................................................5
Use case diagram................................................................................................................................................6
User interfaces design........................................................................................................................................7
Section 3.................................................................................................................................................................8
Robustness of the design....................................................................................................................................8
Fault tolerance...................................................................................................................................................8
Minimal recovery time.......................................................................................................................................8
Scalability...........................................................................................................................................................8
Security...............................................................................................................................................................8
References..............................................................................................................................................................9
Table of Contents
Section 1.................................................................................................................................................................2
Description of the system...................................................................................................................................2
Tiers of the system.............................................................................................................................................2
Overall structure of the implementation............................................................................................................2
Section 2.................................................................................................................................................................3
Class diagram......................................................................................................................................................3
Activity diagram..................................................................................................................................................4
Sequence diagram..............................................................................................................................................5
Use case diagram................................................................................................................................................6
User interfaces design........................................................................................................................................7
Section 3.................................................................................................................................................................8
Robustness of the design....................................................................................................................................8
Fault tolerance...................................................................................................................................................8
Minimal recovery time.......................................................................................................................................8
Scalability...........................................................................................................................................................8
Security...............................................................................................................................................................8
References..............................................................................................................................................................9

2SYSTEM ARCHITECTURE - TRANSACTION SYSTEM
Section 1
Description of the system
The system that has been chosen in this study is ATM (Automated Teller Machine) which is used by
bank customers for banking purposes whether it is cash deposit or withdrawal. This facility is provided to the
customers so that they are able to perform their required transactions anytime from any available ATM near
them. An ATM provides the facility for the bank customers to access their account but they are required to
register an account number and a passcode. The user interface of an ATM comprises of keypad, display
window with touchscreen or buttons for selecting option [5]. The users have to operate the ATM with the help
of provided buttons or touching the screen to complete their desired transaction. Firstly, the user inserts a card
and then the ATM asks for PIN which is entered through the keypad. If validation of the user is successful then
the user is directed to transaction page where he or she can select the choice of option to carry out the
transaction. During the processing of transaction, account of the user is accessed and updated. The completion
of transaction is followed by making another transaction or returning of card. The successful completion of
transaction is intimated to the user by displaying updated information of their transaction and providing a
receipt.
Tiers of the system
The different tiers of the Automated Teller Machine (ATM) are presented as below:
Presentation Tier: This tier is the top most level of the system which presents the interface for users.
The main function of this tier is to transform the tasks so that the users are able to easily understand the
process.
Logic Tier: This tier is responsible for coordinating the system, processing of commands, making logical
decisions and evaluating along with performing calculations [1]. It is also acts as a middle layer in between the
adjacent layers so that data can be moved to perform the input commands.
Data Tier: This tier is the lower most level of the system that relates to storing and retrieving of data
from the database [3]. This layer transfers data to the logic tier so that processing can occur and then
information is transferred to the user.
Overall structure of the implementation
The system is concerned with processing of transactions requested by users and updating the
information in the bank account of users. The processing of transactions is being carried out by validating the
credentials of the user so that proper authentication is done and the users are provided with security [4]. The
Section 1
Description of the system
The system that has been chosen in this study is ATM (Automated Teller Machine) which is used by
bank customers for banking purposes whether it is cash deposit or withdrawal. This facility is provided to the
customers so that they are able to perform their required transactions anytime from any available ATM near
them. An ATM provides the facility for the bank customers to access their account but they are required to
register an account number and a passcode. The user interface of an ATM comprises of keypad, display
window with touchscreen or buttons for selecting option [5]. The users have to operate the ATM with the help
of provided buttons or touching the screen to complete their desired transaction. Firstly, the user inserts a card
and then the ATM asks for PIN which is entered through the keypad. If validation of the user is successful then
the user is directed to transaction page where he or she can select the choice of option to carry out the
transaction. During the processing of transaction, account of the user is accessed and updated. The completion
of transaction is followed by making another transaction or returning of card. The successful completion of
transaction is intimated to the user by displaying updated information of their transaction and providing a
receipt.
Tiers of the system
The different tiers of the Automated Teller Machine (ATM) are presented as below:
Presentation Tier: This tier is the top most level of the system which presents the interface for users.
The main function of this tier is to transform the tasks so that the users are able to easily understand the
process.
Logic Tier: This tier is responsible for coordinating the system, processing of commands, making logical
decisions and evaluating along with performing calculations [1]. It is also acts as a middle layer in between the
adjacent layers so that data can be moved to perform the input commands.
Data Tier: This tier is the lower most level of the system that relates to storing and retrieving of data
from the database [3]. This layer transfers data to the logic tier so that processing can occur and then
information is transferred to the user.
Overall structure of the implementation
The system is concerned with processing of transactions requested by users and updating the
information in the bank account of users. The processing of transactions is being carried out by validating the
credentials of the user so that proper authentication is done and the users are provided with security [4]. The
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
3SYSTEM ARCHITECTURE - TRANSACTION SYSTEM
system operates by communicating with the different tiers or layers by processing information from one layer
to another whenever a user inputs any command in the system through user interface.
Section 2
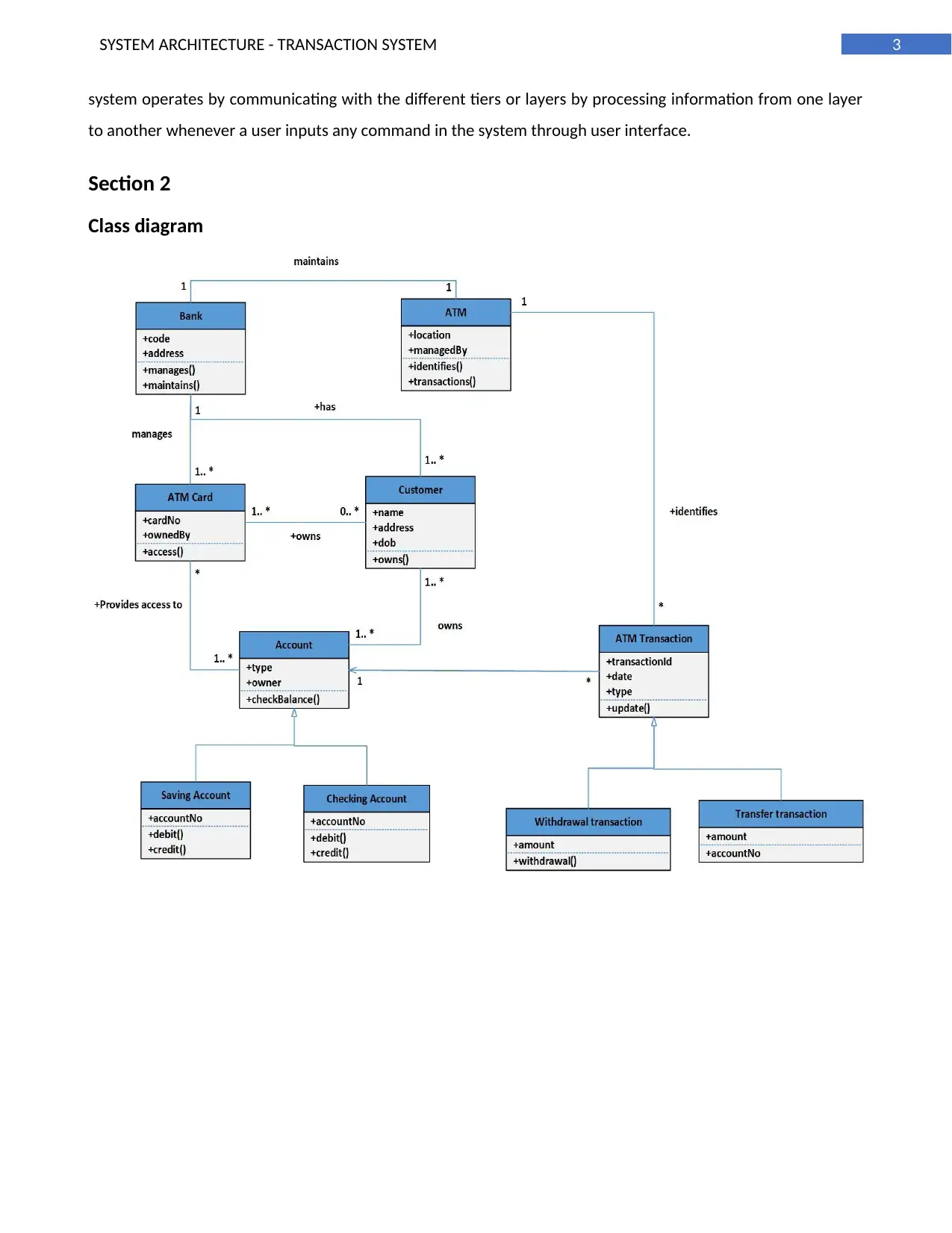
Class diagram
system operates by communicating with the different tiers or layers by processing information from one layer
to another whenever a user inputs any command in the system through user interface.
Section 2
Class diagram
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
4SYSTEM ARCHITECTURE - TRANSACTION SYSTEM
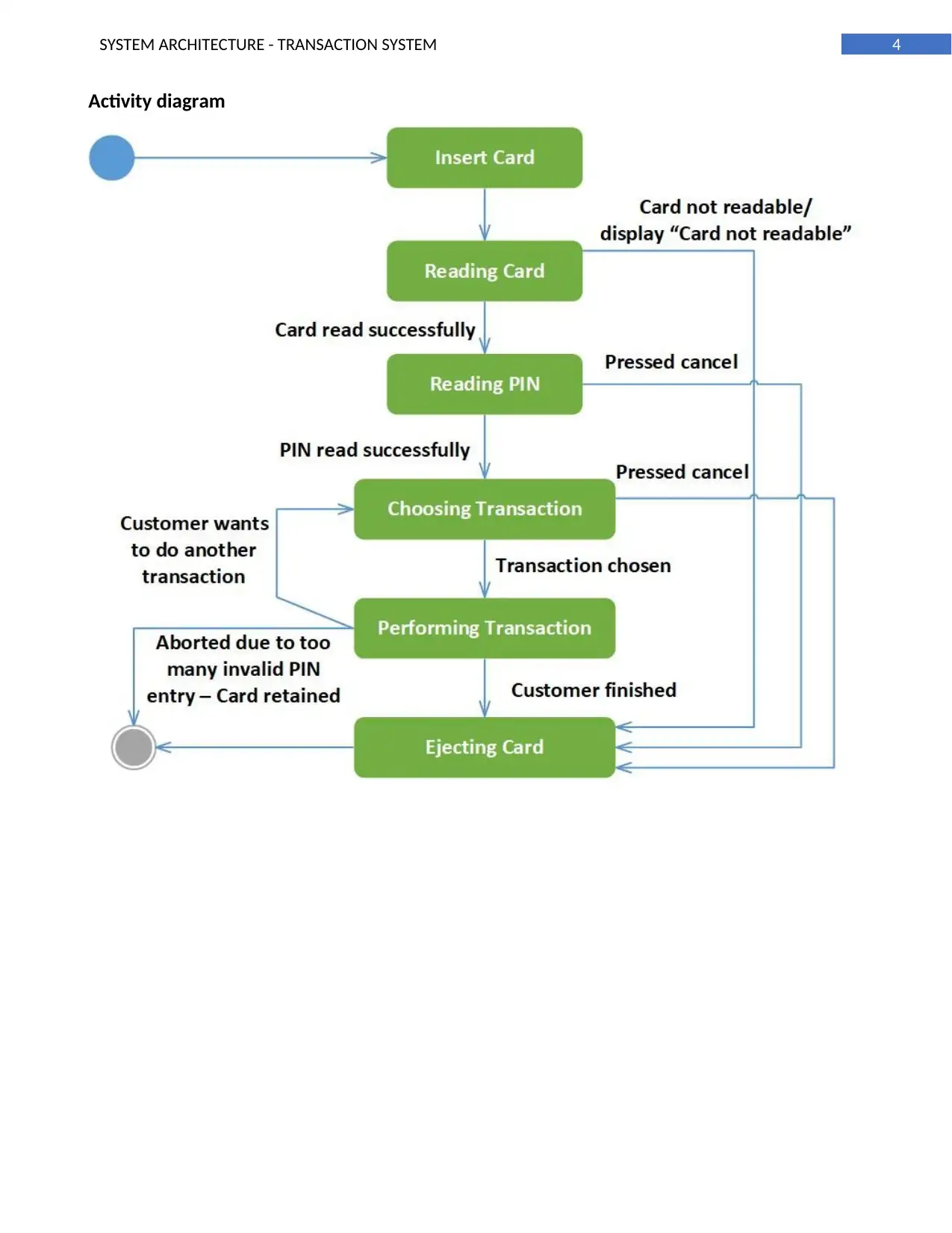
Activity diagram
Activity diagram
5SYSTEM ARCHITECTURE - TRANSACTION SYSTEM
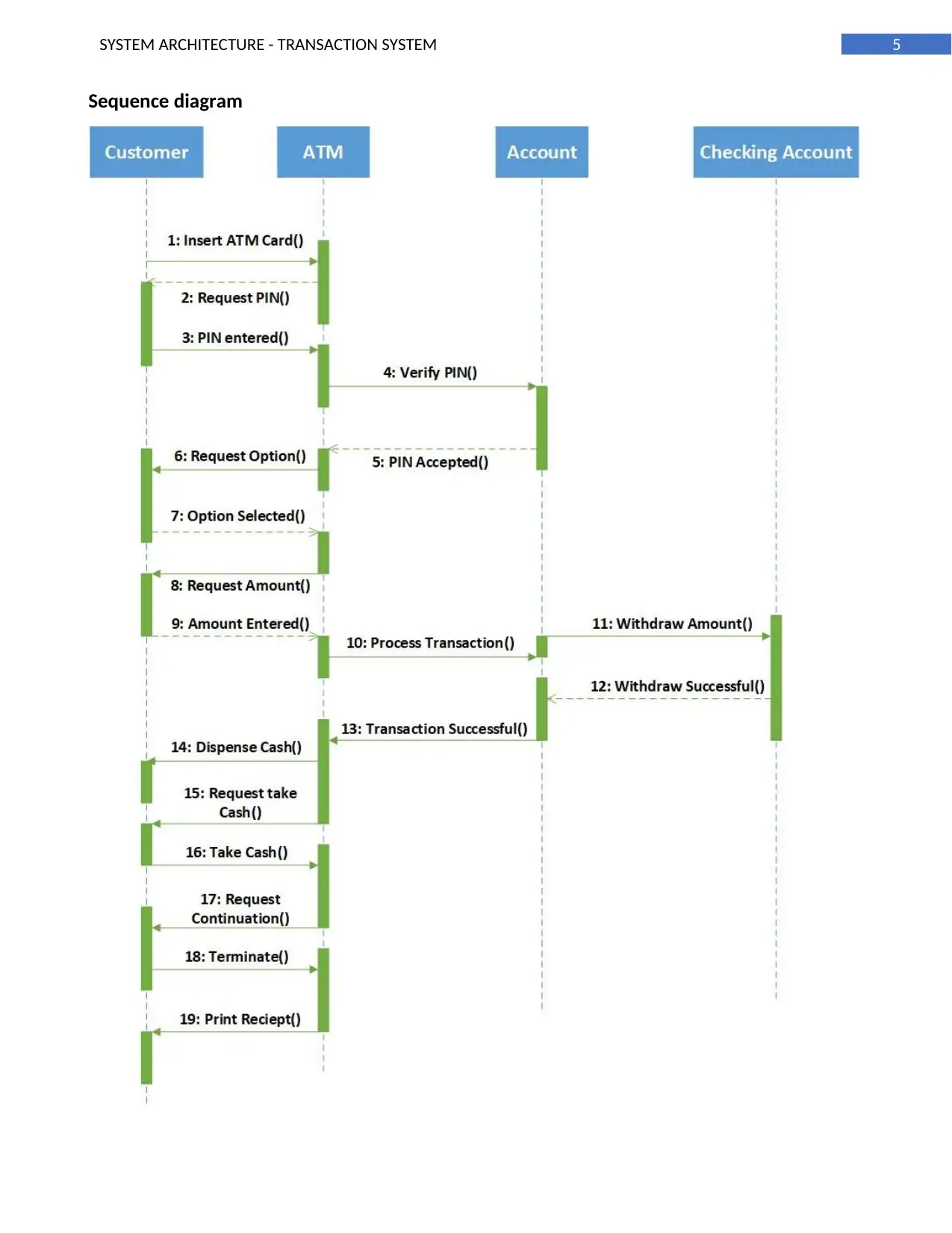
Sequence diagram
Sequence diagram
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
6SYSTEM ARCHITECTURE - TRANSACTION SYSTEM
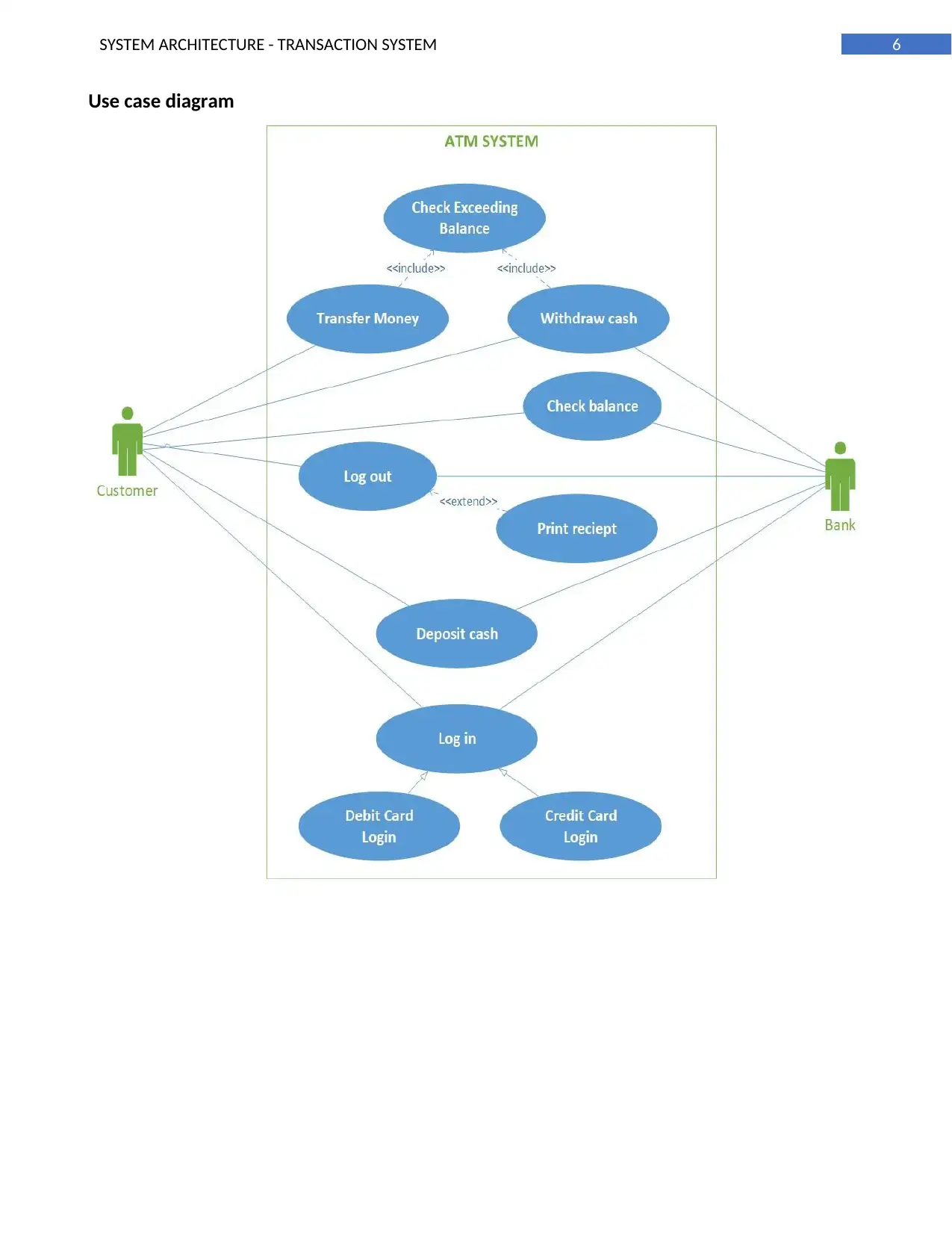
Use case diagram
Use case diagram
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
7SYSTEM ARCHITECTURE - TRANSACTION SYSTEM
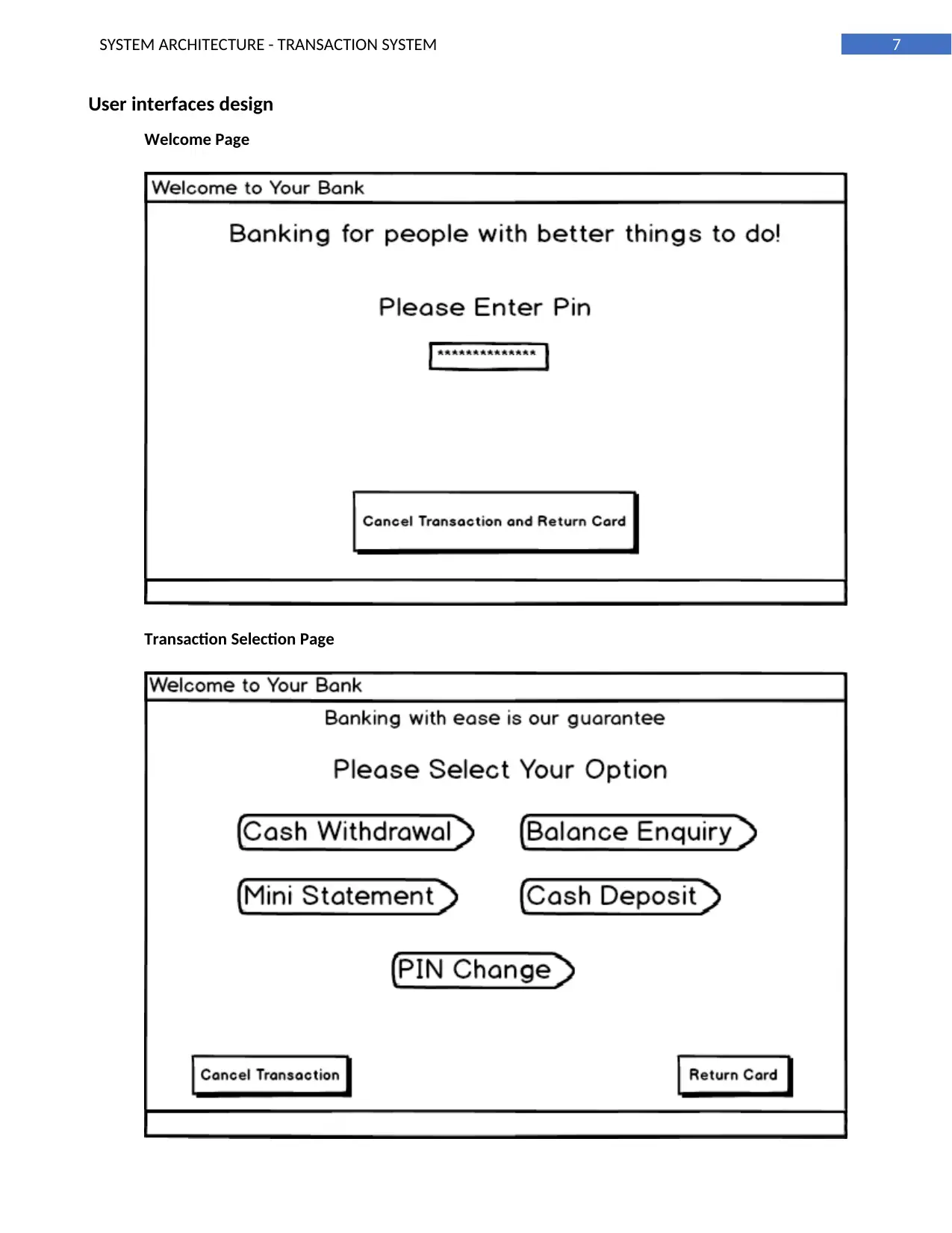
User interfaces design
Welcome Page
Transaction Selection Page
User interfaces design
Welcome Page
Transaction Selection Page

8SYSTEM ARCHITECTURE - TRANSACTION SYSTEM
Section 3
Robustness of the design
The robustness in context to ATM system design refers to resilience, resistance and stability. The
design of ATM is resilient as it supports any type of user irrespective of their technical abilities [2]. The user
interface of the ATM system is easy to understand and can be used by any person as it also supports a wide
variety of regional languages.
Fault tolerance
The ATM system has the ability to tolerate faults as evident from various cases in which the transaction
of users may fail but the account information remains the same [6]. This means that account of the user is
accessed but in case of transaction failure, it is able to roll back to the previous state of the user account.
Minimal recovery time
The minimal recovery time of an ATM system depend on the bank in which the user have registered
their account. In case of transaction failure, the amount of transaction is rolled back to user account within a 2
to 7 days of working time.
Scalability
The ATM system is scalable in nature as it can be programmed with limitations so that the user are only
able to withdraw or deposit a certain amount [1]. This feature of the ATM system is programmable thus the
limitations can be changed as per requirement of the bank through which transaction is carried out by the user.
Security
The ATM system has enhanced security modules installed in them so that unauthorized transactions
can be restricted such that the users do not feel unsecure while using the system. The ATM system requests a
passcode from the users so that they can gain access to their account and perform transactions.
Section 3
Robustness of the design
The robustness in context to ATM system design refers to resilience, resistance and stability. The
design of ATM is resilient as it supports any type of user irrespective of their technical abilities [2]. The user
interface of the ATM system is easy to understand and can be used by any person as it also supports a wide
variety of regional languages.
Fault tolerance
The ATM system has the ability to tolerate faults as evident from various cases in which the transaction
of users may fail but the account information remains the same [6]. This means that account of the user is
accessed but in case of transaction failure, it is able to roll back to the previous state of the user account.
Minimal recovery time
The minimal recovery time of an ATM system depend on the bank in which the user have registered
their account. In case of transaction failure, the amount of transaction is rolled back to user account within a 2
to 7 days of working time.
Scalability
The ATM system is scalable in nature as it can be programmed with limitations so that the user are only
able to withdraw or deposit a certain amount [1]. This feature of the ATM system is programmable thus the
limitations can be changed as per requirement of the bank through which transaction is carried out by the user.
Security
The ATM system has enhanced security modules installed in them so that unauthorized transactions
can be restricted such that the users do not feel unsecure while using the system. The ATM system requests a
passcode from the users so that they can gain access to their account and perform transactions.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

9SYSTEM ARCHITECTURE - TRANSACTION SYSTEM
References
[1.] B. Sagar, G. Singh and R. Saket, "Design concept and network reliability evaluation of ATM
system", International Journal of Computer Aided Engineering and Technology, vol. 3, no. 1, p. 53, 2014.
[2.] H. Jung and Y. Ko, "ATM Design Applying the Universal Design Concept", Archives of Design Research,
vol. 30, no. 2, pp. 123-137, 2017.
[3.] M.B. Calayag, D.M.M. Regala, C.J.R. Rivera and D.M.N. Tancio, “A Comparative Study of Different
Automated Teller Machine and Its Effectiveness Based on Customer’s Satisfaction”, Journal of Industrial
Engineering and Management Science, vol. 1, pp.49-102, 2018.
[4.] M.O. Onyesolu and A.C. Okpala, “Improving Security Using a Three-Tier Authentication for Automated
Teller Machine (ATM)”, International Journal of Computer Network and Information Security, vol. 9, no. 10,
p.50, 2017.
[5.] Q. Yin, "Study on the New Intelligent Monitoring System of ATM", Applied Mechanics and Materials,
vol. 701-702, pp. 587-592, 2014.
[6.] R. Patriarca, "Change management in the ATM system: integrating information in the Preliminary
System Safety Assessment", International Journal of Applied Decision Sciences, vol. 9, no. 1, p. 1, 2016.
References
[1.] B. Sagar, G. Singh and R. Saket, "Design concept and network reliability evaluation of ATM
system", International Journal of Computer Aided Engineering and Technology, vol. 3, no. 1, p. 53, 2014.
[2.] H. Jung and Y. Ko, "ATM Design Applying the Universal Design Concept", Archives of Design Research,
vol. 30, no. 2, pp. 123-137, 2017.
[3.] M.B. Calayag, D.M.M. Regala, C.J.R. Rivera and D.M.N. Tancio, “A Comparative Study of Different
Automated Teller Machine and Its Effectiveness Based on Customer’s Satisfaction”, Journal of Industrial
Engineering and Management Science, vol. 1, pp.49-102, 2018.
[4.] M.O. Onyesolu and A.C. Okpala, “Improving Security Using a Three-Tier Authentication for Automated
Teller Machine (ATM)”, International Journal of Computer Network and Information Security, vol. 9, no. 10,
p.50, 2017.
[5.] Q. Yin, "Study on the New Intelligent Monitoring System of ATM", Applied Mechanics and Materials,
vol. 701-702, pp. 587-592, 2014.
[6.] R. Patriarca, "Change management in the ATM system: integrating information in the Preliminary
System Safety Assessment", International Journal of Applied Decision Sciences, vol. 9, no. 1, p. 1, 2016.
1 out of 10
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.




