Audit Logs: Analysis of Security and Policy Settings in IT
VerifiedAdded on 2021/11/23
|9
|1051
|88
Homework Assignment
AI Summary
This assignment examines the role of audit logs in IT security, detailing the information they contain and their importance in security investigations. It explores the challenges of managing Active Directory audit policy settings and the risks associated with logging too little or too much data. The assignment also considers the impact of default audit log configurations and the complexities of auditing and log management in environments with varying numbers of computers, including cloud-hosted IaaS environments. The conclusion summarizes the use of tools and processes demonstrated in labs to secure an environment, emphasizing the creation and significance of audit logs for security purposes. The assignment covered topics such as the importance of audit logs, the risks associated with logging too little or too much data, and the challenges of managing audit policies in different environments, including cloud-based infrastructure. The student has provided a comprehensive analysis of audit logs and their role in information security.

Running Head: Audit logs 1
Audit logs
Professor’s Name
Affiliate Institution
Date
Audit logs
Professor’s Name
Affiliate Institution
Date
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Audit logs 2
Describe what information was contained in the logs and what value they might
have in a security investigation.
Audit logs in IT security are the data in which the computer stores them so that in case of
any security issue in the information system, these logs can be referenced. The information
which are contained in the logs are files pertaining all the transactions being undertaken in the
computer system. This logs can be attempts such as login success or failure or files access failure
or success. They are able to show the threats which are attempting to log into the system without
permission.
Think about the challenges of getting all of the Active Directory audit policy settings
right. For an infrastructure administrator, how important are these types of settings?
Active directory in the audit logs information system is where the users of the computer
system are assigned the permission and privileges through which they can use to access the
system. (Song, Shi, Fischer & Shankar, 2012) The challenges of getting all the active directory
settings is that it requires an expert to do all the setting policies concerning the audit logs. To
access these logs requires a skilled personnel to both set policies and extract the logs.
What are the risks associated with logging too little data or not auditing the correct
events?
Logging too little data is a security threat to an information system. Logging is like
making the information system data safe and secure. Therefore by not auditing the correct events
or logging all the data in the information system, is that whenever there are attackers trying to
Describe what information was contained in the logs and what value they might
have in a security investigation.
Audit logs in IT security are the data in which the computer stores them so that in case of
any security issue in the information system, these logs can be referenced. The information
which are contained in the logs are files pertaining all the transactions being undertaken in the
computer system. This logs can be attempts such as login success or failure or files access failure
or success. They are able to show the threats which are attempting to log into the system without
permission.
Think about the challenges of getting all of the Active Directory audit policy settings
right. For an infrastructure administrator, how important are these types of settings?
Active directory in the audit logs information system is where the users of the computer
system are assigned the permission and privileges through which they can use to access the
system. (Song, Shi, Fischer & Shankar, 2012) The challenges of getting all the active directory
settings is that it requires an expert to do all the setting policies concerning the audit logs. To
access these logs requires a skilled personnel to both set policies and extract the logs.
What are the risks associated with logging too little data or not auditing the correct
events?
Logging too little data is a security threat to an information system. Logging is like
making the information system data safe and secure. Therefore by not auditing the correct events
or logging all the data in the information system, is that whenever there are attackers trying to

Audit logs 3
hack into the system. Without the audit logs, we are not able to see that there are logon failures
or file access failures which enables us to build a strong and secure system. (Tianfield, 2012,
October).
What are the risks associated with logging too many events?
Logging too many events is also very risky. This is because when a lot of events are
logged in the information computer system. At some point, we might forget some details about a
particular event in the system. This event is so crucial and needed to be used. This means that for
you to access the event, you need to repair the whole system which may cause some other events
to get lost.
When the default configuration is to create audit logs, what impact can this have on
security incident investigations?
When default configuration is used to create audit logs, data are not that secure since
some setting are not set in the right way. (Er, Low & Ganesh, 2012). This is because, in default
configurations, the setting are for general usage, whereby certain privileges have not been set so
that it can meet the standards of logging the events in the information system.
This was just a single domain with two systems on a local LAN. How much more
complicated would auditing and log management be for 100 computers? What about an
enterprise with 10,000 computers in several domains on their LAN/WAN?
In this system was a domain with two computers associated with network. Mostly this
work was done on the server site to ensure that logs are created on the user computers. The
hack into the system. Without the audit logs, we are not able to see that there are logon failures
or file access failures which enables us to build a strong and secure system. (Tianfield, 2012,
October).
What are the risks associated with logging too many events?
Logging too many events is also very risky. This is because when a lot of events are
logged in the information computer system. At some point, we might forget some details about a
particular event in the system. This event is so crucial and needed to be used. This means that for
you to access the event, you need to repair the whole system which may cause some other events
to get lost.
When the default configuration is to create audit logs, what impact can this have on
security incident investigations?
When default configuration is used to create audit logs, data are not that secure since
some setting are not set in the right way. (Er, Low & Ganesh, 2012). This is because, in default
configurations, the setting are for general usage, whereby certain privileges have not been set so
that it can meet the standards of logging the events in the information system.
This was just a single domain with two systems on a local LAN. How much more
complicated would auditing and log management be for 100 computers? What about an
enterprise with 10,000 computers in several domains on their LAN/WAN?
In this system was a domain with two computers associated with network. Mostly this
work was done on the server site to ensure that logs are created on the user computers. The
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

Audit logs 4
complexity of the audit logs creation increases with the increased number of computers since
several users have to be created on the active directories and computers. And the most complex
in the network information system where more than 10,000 computers have to be configured.
This is when manual configuration is done. But when this configuration is done from the server
site computer, it will be able to make it a bit easier to configure since all computers are configure
from the server. (Hale, & Gamble, 2012)
Consider a cloud-hosted Infrastructure as a Service (IaaS) environment with many
new, internet-accessible systems regularly being built and brought online. What challenges
might there be managing audit policies and logs in such an environment?
To manage audit logs on the cloud environment is very difficult since you are dealing
with a very big number of computers. This computers builds logs on the databases. This
computers can be set to use intelligent systems such as firewalls to detect attempts to attacks.
Finally, conclude this week's assignment with a page explaining how the tools and
processes demonstrated in the labs might be used by an infrastructure administrator to
help secure an environment
During the lab process, a lot of skills with regards to information security were acquired.
This logs are created mainly for security issues in IT. Audit logs works at the background of the
computer information system so that it can be able to listen and ensure that all the data are kept
secured within the information system.
References
complexity of the audit logs creation increases with the increased number of computers since
several users have to be created on the active directories and computers. And the most complex
in the network information system where more than 10,000 computers have to be configured.
This is when manual configuration is done. But when this configuration is done from the server
site computer, it will be able to make it a bit easier to configure since all computers are configure
from the server. (Hale, & Gamble, 2012)
Consider a cloud-hosted Infrastructure as a Service (IaaS) environment with many
new, internet-accessible systems regularly being built and brought online. What challenges
might there be managing audit policies and logs in such an environment?
To manage audit logs on the cloud environment is very difficult since you are dealing
with a very big number of computers. This computers builds logs on the databases. This
computers can be set to use intelligent systems such as firewalls to detect attempts to attacks.
Finally, conclude this week's assignment with a page explaining how the tools and
processes demonstrated in the labs might be used by an infrastructure administrator to
help secure an environment
During the lab process, a lot of skills with regards to information security were acquired.
This logs are created mainly for security issues in IT. Audit logs works at the background of the
computer information system so that it can be able to listen and ensure that all the data are kept
secured within the information system.
References
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
Audit logs 5
Er, C. K., Low, C. M., & Ganesh, S. (2012). U.S. Patent No. 8,250,045. Washington, DC:
U.S. Patent and Trademark Office.
Hale, M. L., & Gamble, R. (2012, June). Secagreement: Advancing security risk
calculations in cloud services. In Services (SERVICES), 2012 IEEE Eighth World
Congress on (pp. 133-140). IEEE.
Song, D., Shi, E., Fischer, I., & Shankar, U. (2012). Cloud data protection for the
masses. Computer, 45(1), 39-45.
Tianfield, H. (2012, October). Security issues in cloud computing. In Systems, Man, and
Cybernetics (SMC), 2012 IEEE International Conference on (pp. 1082-1089).
IEEE.
Appendices
Er, C. K., Low, C. M., & Ganesh, S. (2012). U.S. Patent No. 8,250,045. Washington, DC:
U.S. Patent and Trademark Office.
Hale, M. L., & Gamble, R. (2012, June). Secagreement: Advancing security risk
calculations in cloud services. In Services (SERVICES), 2012 IEEE Eighth World
Congress on (pp. 133-140). IEEE.
Song, D., Shi, E., Fischer, I., & Shankar, U. (2012). Cloud data protection for the
masses. Computer, 45(1), 39-45.
Tianfield, H. (2012, October). Security issues in cloud computing. In Systems, Man, and
Cybernetics (SMC), 2012 IEEE International Conference on (pp. 1082-1089).
IEEE.
Appendices
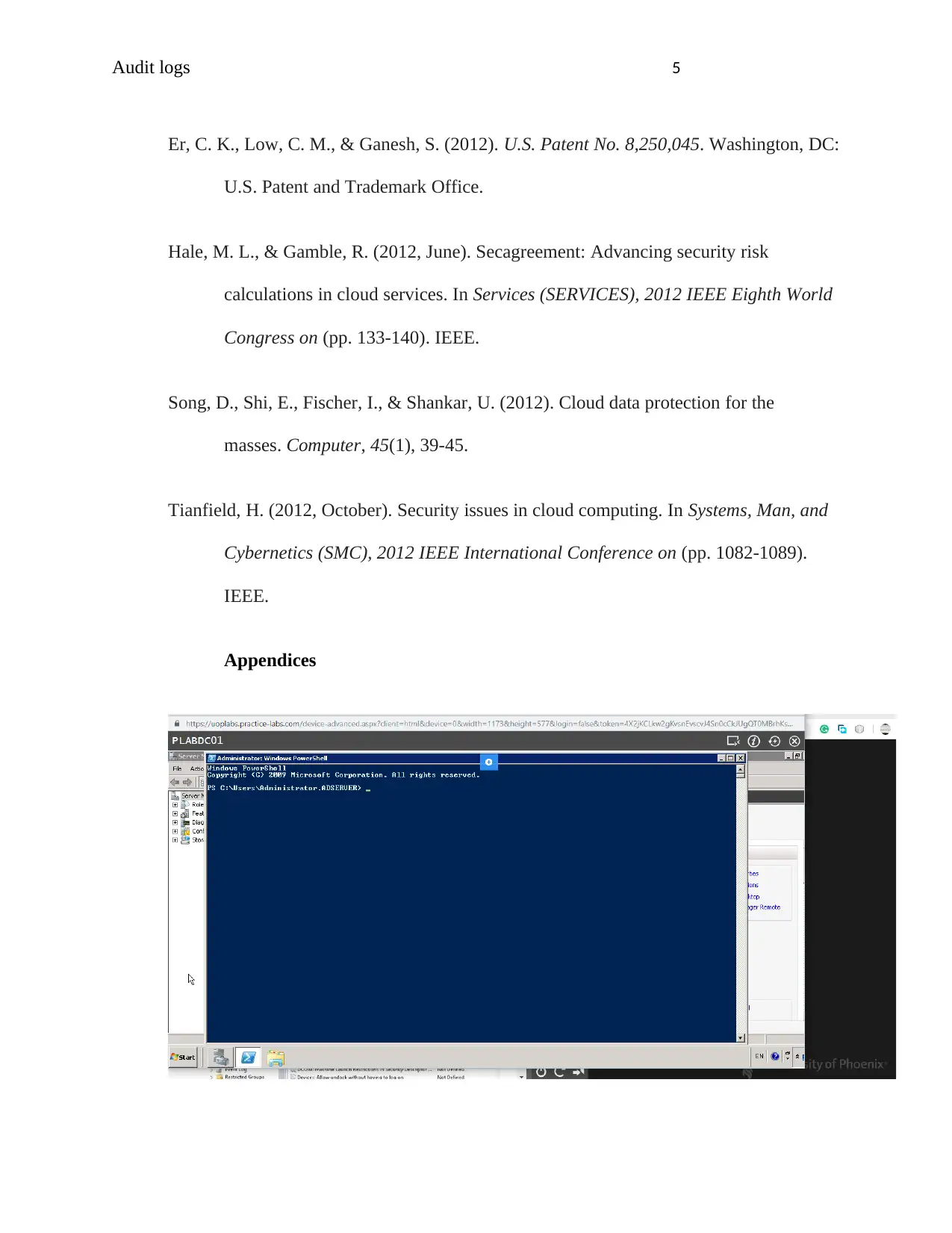
Audit logs 6
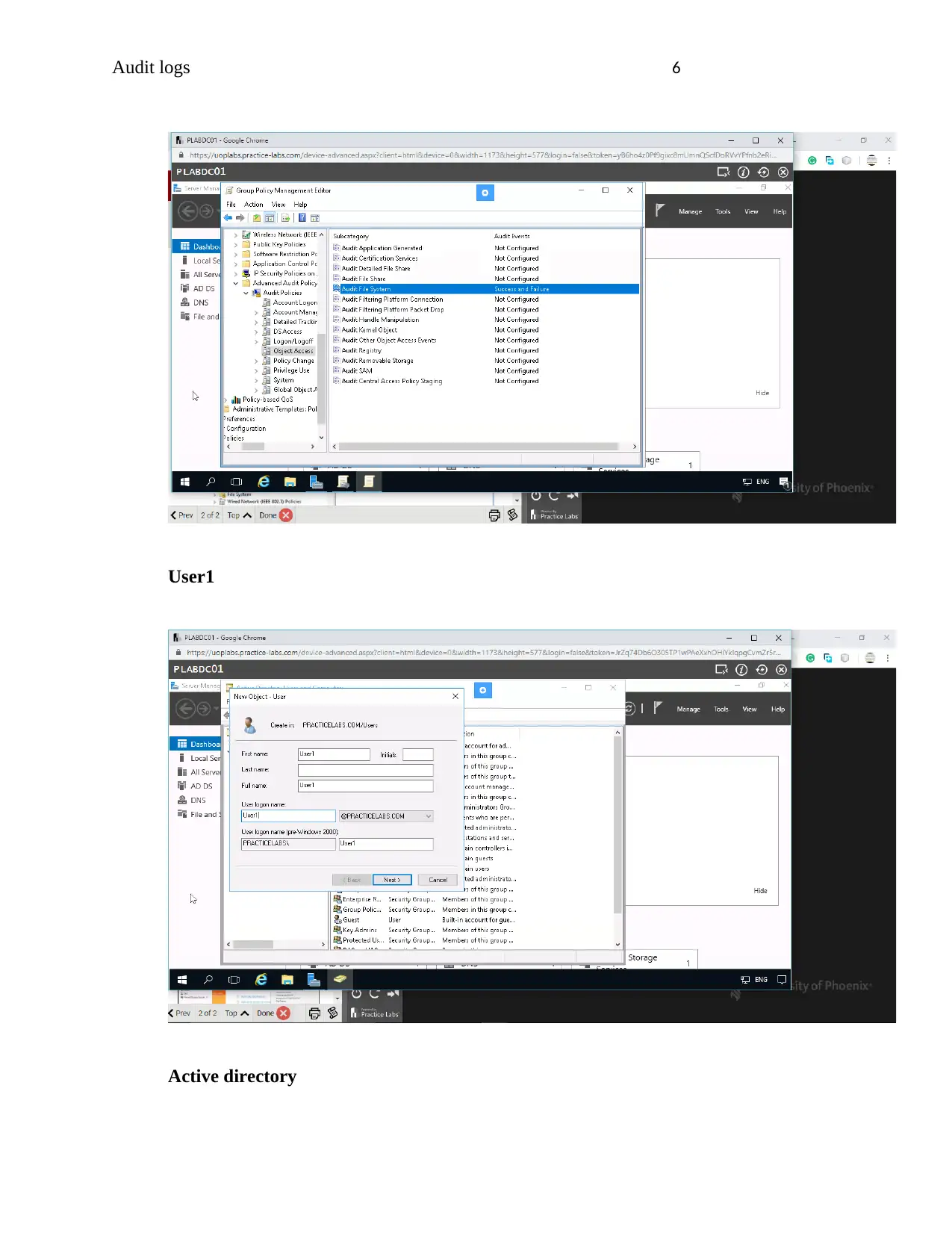
User1
Active directory
User1
Active directory
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
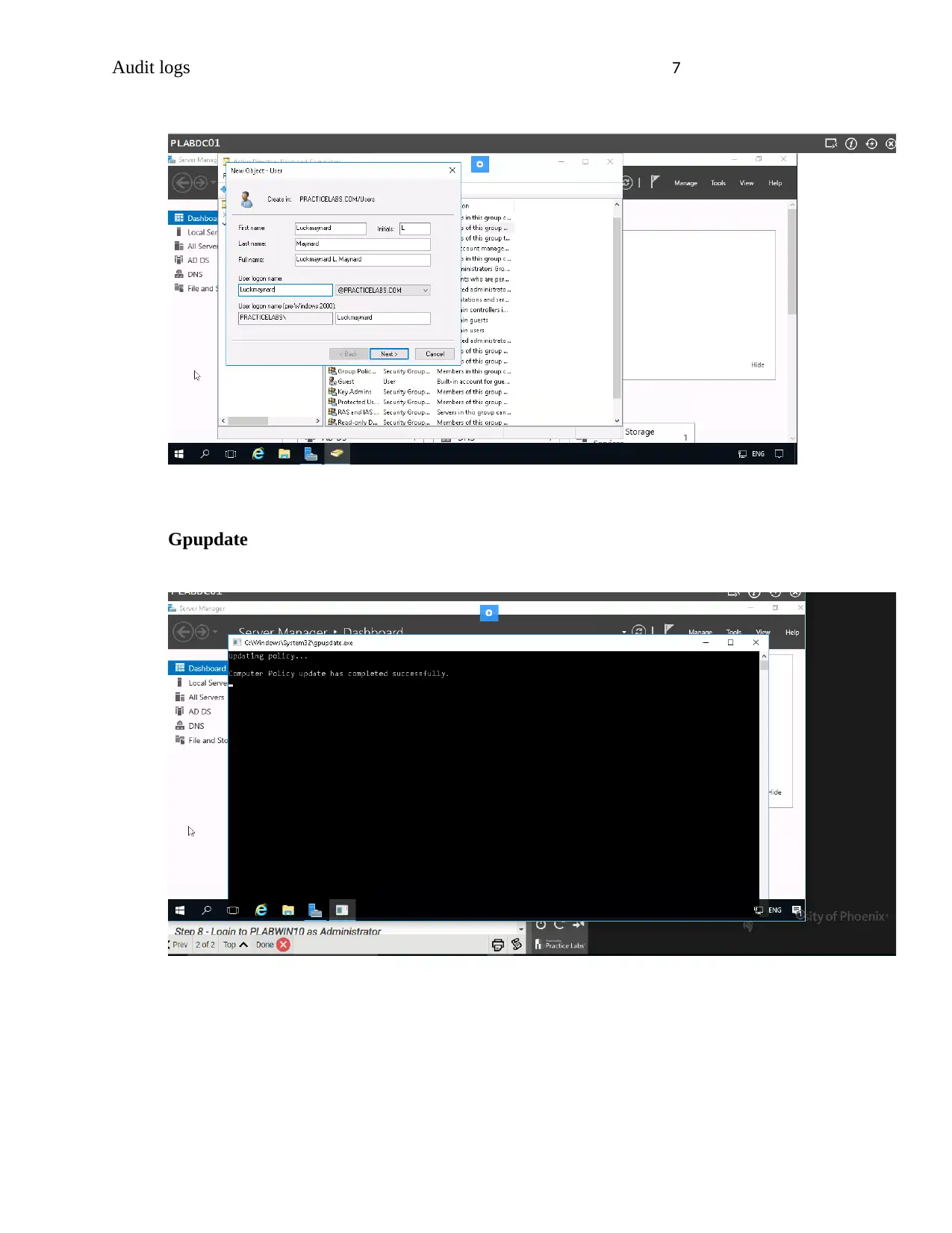
Audit logs 7
Gpupdate
Gpupdate
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
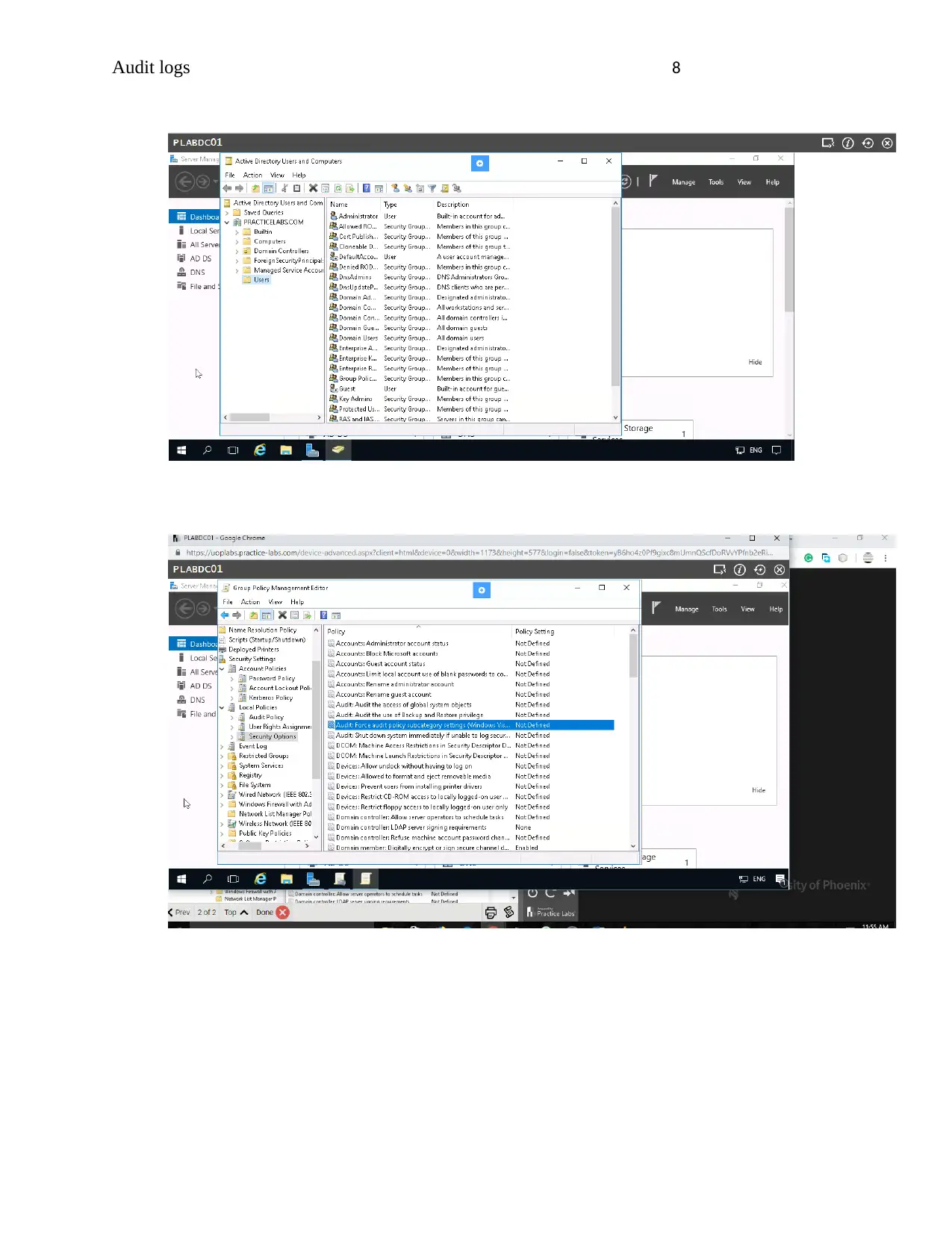
Audit logs 8
Audit logs 9
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 9
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





