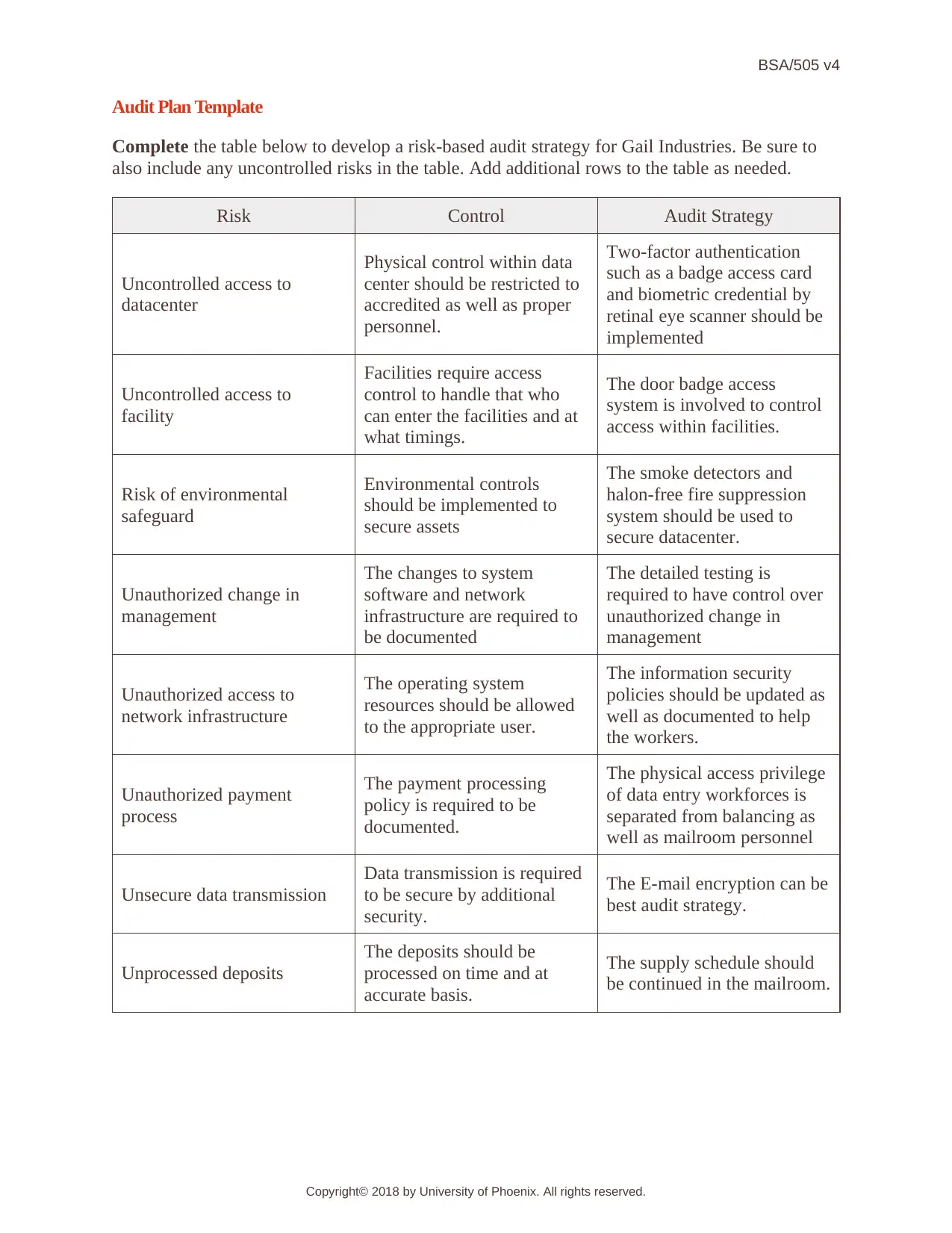
Audit Plan Template: Risk-Based Strategy for Gail Industries (BSA/505)
VerifiedAdded on 2022/11/29
|1
|339
|82
Homework Assignment
AI Summary
This assignment presents an audit plan template for Gail Industries, a company that manages digital transactions for clients like the city of Smallville. The plan involves developing a risk-based audit strategy, analyzing potential risks such as uncontrolled access to data centers, facilities, and network infrastructure, as well as unauthorized changes in system management, insecure data transmission, and unprocessed deposits. The assignment requires the inclusion of controls and corresponding audit strategies to mitigate these risks. The provided solution outlines specific strategies, like two-factor authentication, access control systems, environmental safeguards, and email encryption, to ensure data security and compliance with NIST 800-53 standards. The audit plan aims to cover the period from January 1, 2018, to December 31, 2018, with fieldwork commencing on January 3, 2019. The plan emphasizes the importance of secure data handling, access controls, and the integrity of financial transactions within Gail Industries' operations.






![[object Object]](/_next/static/media/star-bottom.7253800d.svg)