AusEd: IT Infrastructure Report - Network Design and Analysis
VerifiedAdded on 2021/06/14
|11
|2589
|50
Report
AI Summary
This report provides a detailed analysis and design for the IT infrastructure of AusEd. It begins with an introduction outlining the scope of the problem, assumptions made, and a list of devices including switches, routers, servers, and security devices. A logical design diagram illustrates the network topology, followed by a budget cost analysis of hardware components from Dell, Cisco, and HP. The report justifies the hardware choices, emphasizing their compatibility and performance. Key considerations include network security, scalability, and cost-effectiveness. The report concludes with a discussion of the proposed network design, addressing the need for a secure and efficient system to support AusEd's operations, including customer relationship management and resource management for its students and staff. The design incorporates a three-layered hierarchical architecture and emphasizes the importance of managing and troubleshooting the network post-implementation.

Title: IT Infrastructure
Subtitle: Report Study for AusEd
Student Name:
Student ID
MAY 22, 2018
student name
Student ID
Subtitle: Report Study for AusEd
Student Name:
Student ID
MAY 22, 2018
student name
Student ID
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Table of Contents
Introduction.................................................................................................................................................1
Scope of the problem...................................................................................................................................2
Assumptions................................................................................................................................................3
List of Devices............................................................................................................................................3
Logical Design Diagram..............................................................................................................................4
Budget Cost Analysis..................................................................................................................................7
Justification of hardware used.....................................................................................................................8
Conclusion...................................................................................................................................................8
References...................................................................................................................................................9
Introduction.................................................................................................................................................1
Scope of the problem...................................................................................................................................2
Assumptions................................................................................................................................................3
List of Devices............................................................................................................................................3
Logical Design Diagram..............................................................................................................................4
Budget Cost Analysis..................................................................................................................................7
Justification of hardware used.....................................................................................................................8
Conclusion...................................................................................................................................................8
References...................................................................................................................................................9

Introduction
For any organization the best way to approach to a strategic plan is understanding the major
needs and making them fully stretched and met when distributing the organization resources. We
have to understand all the equipment’s that are already planted in the institution. The way the
data is being transmitted from the servers to the workstations is a major thing for any
organization to understand. There has been so many times that we do not know what exactly
happens in the background when we are sending and receiving messages. We see that we put
much concentration on the icons and the interfaces rather than understanding what happens
behind the scene. Hardware components are those devices that are tangible and we can
physically see them while the software component are those that we use when interacting with
the device. There are some steps that are followed when we are trying to analyze on the type of
IT infrastructure we are going to setup. First step is understanding the existing hardware devices
in the institution so that we are able to know what to buy and what not to. The second key
requirement is knowing all the demands and needs of AusEd from the moment we start doing the
thorough analysis and planning. After the analysis has been completed then we can be able to
categorize all the problems and be able to come up with the best solutions that will solve the
problems in existence. Third after the analysis we have to use the analysed data in coming up
with the network diagram of the institution. Understanding the type of topology to be used will
be a key thing in this assignment because it will help us to be able to come up with a good
network design. In making the design to be successful and choosing the appropriate models then
we can consider some key factors like how secure the network will be, the flexibility and
scalability, understanding the budget allocated for the setting up of the network and lastly is the
time plan where we have to give out the project schedule of how long we will take to complete
the project. (Leon, 2015). To know the ease of the network that has already been designed it is
good we know the management involved and the way they will respond to errors when asked to
troubleshoot.
The main concept the AusEd need to be brought about in this case study is creation of a system
that will help them to maintain their accounts and a continued good relationships with their
customer. They want an advanced use of the Sugar Customer Relationship management and that
of the Microsoft Exchange Server 2007 which is used for sending, when receiving and storing of
resources used within the existing network. If AusEd has more than 2000 student within the
For any organization the best way to approach to a strategic plan is understanding the major
needs and making them fully stretched and met when distributing the organization resources. We
have to understand all the equipment’s that are already planted in the institution. The way the
data is being transmitted from the servers to the workstations is a major thing for any
organization to understand. There has been so many times that we do not know what exactly
happens in the background when we are sending and receiving messages. We see that we put
much concentration on the icons and the interfaces rather than understanding what happens
behind the scene. Hardware components are those devices that are tangible and we can
physically see them while the software component are those that we use when interacting with
the device. There are some steps that are followed when we are trying to analyze on the type of
IT infrastructure we are going to setup. First step is understanding the existing hardware devices
in the institution so that we are able to know what to buy and what not to. The second key
requirement is knowing all the demands and needs of AusEd from the moment we start doing the
thorough analysis and planning. After the analysis has been completed then we can be able to
categorize all the problems and be able to come up with the best solutions that will solve the
problems in existence. Third after the analysis we have to use the analysed data in coming up
with the network diagram of the institution. Understanding the type of topology to be used will
be a key thing in this assignment because it will help us to be able to come up with a good
network design. In making the design to be successful and choosing the appropriate models then
we can consider some key factors like how secure the network will be, the flexibility and
scalability, understanding the budget allocated for the setting up of the network and lastly is the
time plan where we have to give out the project schedule of how long we will take to complete
the project. (Leon, 2015). To know the ease of the network that has already been designed it is
good we know the management involved and the way they will respond to errors when asked to
troubleshoot.
The main concept the AusEd need to be brought about in this case study is creation of a system
that will help them to maintain their accounts and a continued good relationships with their
customer. They want an advanced use of the Sugar Customer Relationship management and that
of the Microsoft Exchange Server 2007 which is used for sending, when receiving and storing of
resources used within the existing network. If AusEd has more than 2000 student within the
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

school premises more than 200 people working in the institutions then we will need a network
that will be strong and that will be applied and accessible to all the people may it be the admin,
staffs, students or even lecturers. The requirements of AusEd are based on the hardware parts of
the networking from the networking devices to the resources used by the individuals in the
AusEd. Some of these hardware that must be used are such as the scanners, printers, personal
computers and much more all other workstations working or used for working in making the
network to be complete.
After the department associated with the development of the said IT infrastructure understands
all the above then it is the mandate of IT manager or the designer of the network to come with a
plan of the design to use for the network. The diagram lay down all the content used in
something that can be visualized clearly showing how the devices in the network communicates
with each other from the router to the devices such as the scanners, computers and the scanners
among many more. The other idea that has been emphasized in this category is the issue of the
security where we are advised to apply the devices such as the firewalls and the virtual Private
networks.
Scope of the problem.
The reason to as why we need the network design for AusEd is because of its future plan that it
will use in achieving its plan strategically and increasing the diversified sources of funds which
will essence in minimizing the cost of the non-core activities. Also when we understand their
technology plan will assist them in future in developing an offline Moodle for students and the
add-on Moodle for taking exams.
When we want to understand the objectives of AusEd then we can be able to setup a network
layout that will be based on the good security and the extensions in future. (Coleman, 2012).
Managing a network after being implemented is a thing will greatly needed to be observed. This
will help in predicting the problems that may come as a result of such in future hence becoming
easy to troubleshoot. Lastly but not least the other purpose of the study on the proposed network
design of AusEd is that we will need the network very secure in that we will use the devices such
as the firewall in the routers that will help filtering the of the data and the virtual private
networks that will help to maintain and keep the confidentiality and privacy of the data.
that will be strong and that will be applied and accessible to all the people may it be the admin,
staffs, students or even lecturers. The requirements of AusEd are based on the hardware parts of
the networking from the networking devices to the resources used by the individuals in the
AusEd. Some of these hardware that must be used are such as the scanners, printers, personal
computers and much more all other workstations working or used for working in making the
network to be complete.
After the department associated with the development of the said IT infrastructure understands
all the above then it is the mandate of IT manager or the designer of the network to come with a
plan of the design to use for the network. The diagram lay down all the content used in
something that can be visualized clearly showing how the devices in the network communicates
with each other from the router to the devices such as the scanners, computers and the scanners
among many more. The other idea that has been emphasized in this category is the issue of the
security where we are advised to apply the devices such as the firewalls and the virtual Private
networks.
Scope of the problem.
The reason to as why we need the network design for AusEd is because of its future plan that it
will use in achieving its plan strategically and increasing the diversified sources of funds which
will essence in minimizing the cost of the non-core activities. Also when we understand their
technology plan will assist them in future in developing an offline Moodle for students and the
add-on Moodle for taking exams.
When we want to understand the objectives of AusEd then we can be able to setup a network
layout that will be based on the good security and the extensions in future. (Coleman, 2012).
Managing a network after being implemented is a thing will greatly needed to be observed. This
will help in predicting the problems that may come as a result of such in future hence becoming
easy to troubleshoot. Lastly but not least the other purpose of the study on the proposed network
design of AusEd is that we will need the network very secure in that we will use the devices such
as the firewall in the routers that will help filtering the of the data and the virtual private
networks that will help to maintain and keep the confidentiality and privacy of the data.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Assumptions
There are major assumptions that have been made for this study to be a success. Some of them
are such as.
1. We have assumed that the management is willing to pay any amount of money to make
the network design to be the best they ever though off and this will be in terms of the
networking devices listed by the IT manager.
2. We should also assume that AusEd needs to expand its network in future where we will
have to make assumptions that the network will be scaled in case we have some
additional devices that need to connected to the network.
3. We have assumed also the 3-layered hierarchical architecture will be used in this context
making it easy for us in case we want to scale or in need a network design model that is
flexible unlike in flat network design model.
4. Last assumption is that the cost used for the hardware’s might not be the actual price but
it is just an estimate of what we anticipate to be used in the market.
5. Lastly is that we will use the following three companies in buying our major products
such as the servers, pcs and switches.
Dell
Cisco
HP
List of Devices
Devices are the physical equipment’s that are used for sharing and transmitting resources from
one place to the other. They are known for they make communications between the people
within a given network to be very easy and much more convincing in all manners. Some of these
devices are listed and explained in the table below.
Device Function
Switch This is the device that communicates with the end devices directly. They
do usually have ports where they devices are connected using the RJ 45
Router This is used for connecting the local area network over the internet. It is
There are major assumptions that have been made for this study to be a success. Some of them
are such as.
1. We have assumed that the management is willing to pay any amount of money to make
the network design to be the best they ever though off and this will be in terms of the
networking devices listed by the IT manager.
2. We should also assume that AusEd needs to expand its network in future where we will
have to make assumptions that the network will be scaled in case we have some
additional devices that need to connected to the network.
3. We have assumed also the 3-layered hierarchical architecture will be used in this context
making it easy for us in case we want to scale or in need a network design model that is
flexible unlike in flat network design model.
4. Last assumption is that the cost used for the hardware’s might not be the actual price but
it is just an estimate of what we anticipate to be used in the market.
5. Lastly is that we will use the following three companies in buying our major products
such as the servers, pcs and switches.
Dell
Cisco
HP
List of Devices
Devices are the physical equipment’s that are used for sharing and transmitting resources from
one place to the other. They are known for they make communications between the people
within a given network to be very easy and much more convincing in all manners. Some of these
devices are listed and explained in the table below.
Device Function
Switch This is the device that communicates with the end devices directly. They
do usually have ports where they devices are connected using the RJ 45
Router This is used for connecting the local area network over the internet. It is
most applied by the both sides that is the ISP for passing the internet and
hence it acts as device where everything must pass through before it enter
or leaves.
cables Just like any other cable they are used for connecting the devices to help
them transmit so that they can share and transfer resources from one
person to the other (Maggie, 2014).
Servers They are of different types but they depend with the functionality. Their
main function is to store and share resources within the network.some of
these servers are such as the Application, proxy, DHCP, Mail, Web server
etc. (AdminMuba, 2015).
Access devices These are the the devices used for sharing and transferring resources that
are used directly by the end user.
Security devices These are the devices that are used for providing enough security to the
data as it is transmitted across the network. In this case we have the use
of VPN and the Firewall.
Transceiver This is a wireless access point device which broadcast WI-FI signals in
the network.
Just like in any other network there are other minor devices that are sometimes used to bring the
services close to the end user. Some of these devices are such as the use of personal computers,
scanners, printers, photocopiers, hub, bridge, modem, gateway, repeater, RJ45 connectors among
many others.
Logical Design Diagram
The figure below indicates the way the design of the network in AusEd is anticipated to be like.
hence it acts as device where everything must pass through before it enter
or leaves.
cables Just like any other cable they are used for connecting the devices to help
them transmit so that they can share and transfer resources from one
person to the other (Maggie, 2014).
Servers They are of different types but they depend with the functionality. Their
main function is to store and share resources within the network.some of
these servers are such as the Application, proxy, DHCP, Mail, Web server
etc. (AdminMuba, 2015).
Access devices These are the the devices used for sharing and transferring resources that
are used directly by the end user.
Security devices These are the devices that are used for providing enough security to the
data as it is transmitted across the network. In this case we have the use
of VPN and the Firewall.
Transceiver This is a wireless access point device which broadcast WI-FI signals in
the network.
Just like in any other network there are other minor devices that are sometimes used to bring the
services close to the end user. Some of these devices are such as the use of personal computers,
scanners, printers, photocopiers, hub, bridge, modem, gateway, repeater, RJ45 connectors among
many others.
Logical Design Diagram
The figure below indicates the way the design of the network in AusEd is anticipated to be like.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
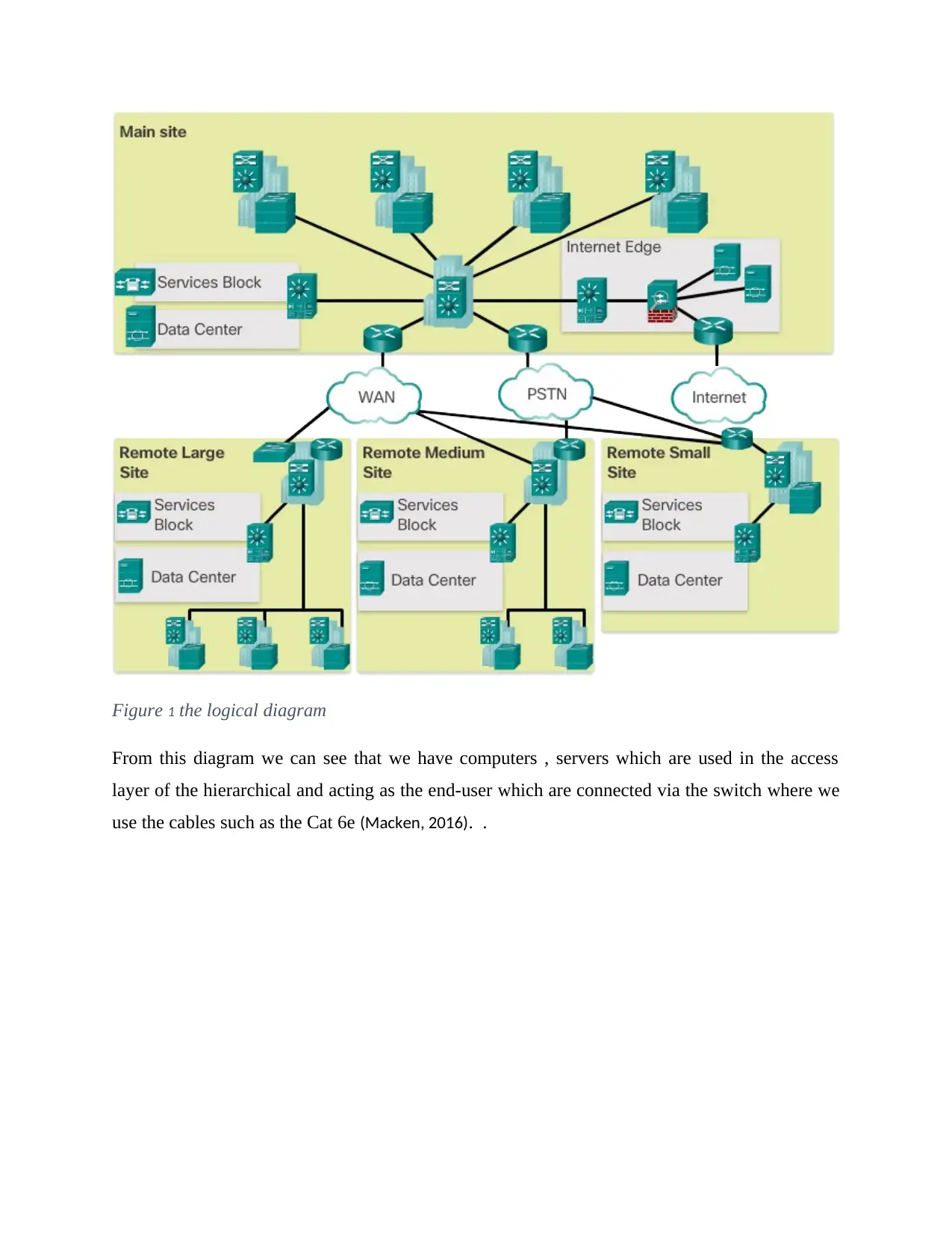
Figure 1 the logical diagram
From this diagram we can see that we have computers , servers which are used in the access
layer of the hierarchical and acting as the end-user which are connected via the switch where we
use the cables such as the Cat 6e (Macken, 2016). .
From this diagram we can see that we have computers , servers which are used in the access
layer of the hierarchical and acting as the end-user which are connected via the switch where we
use the cables such as the Cat 6e (Macken, 2016). .
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
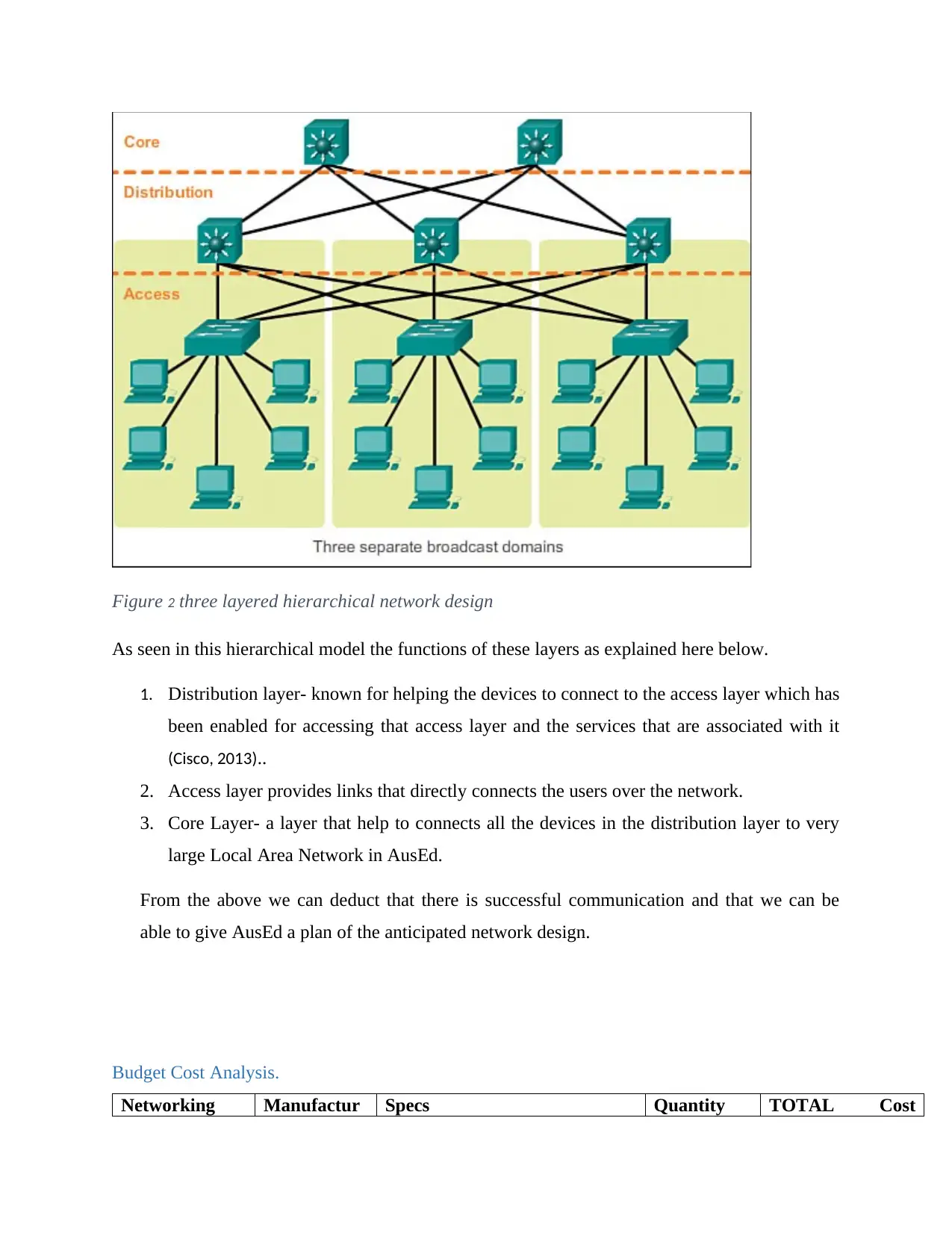
Figure 2 three layered hierarchical network design
As seen in this hierarchical model the functions of these layers as explained here below.
1. Distribution layer- known for helping the devices to connect to the access layer which has
been enabled for accessing that access layer and the services that are associated with it
(Cisco, 2013)..
2. Access layer provides links that directly connects the users over the network.
3. Core Layer- a layer that help to connects all the devices in the distribution layer to very
large Local Area Network in AusEd.
From the above we can deduct that there is successful communication and that we can be
able to give AusEd a plan of the anticipated network design.
Budget Cost Analysis.
Networking Manufactur Specs Quantity TOTAL Cost
As seen in this hierarchical model the functions of these layers as explained here below.
1. Distribution layer- known for helping the devices to connect to the access layer which has
been enabled for accessing that access layer and the services that are associated with it
(Cisco, 2013)..
2. Access layer provides links that directly connects the users over the network.
3. Core Layer- a layer that help to connects all the devices in the distribution layer to very
large Local Area Network in AusEd.
From the above we can deduct that there is successful communication and that we can be
able to give AusEd a plan of the anticipated network design.
Budget Cost Analysis.
Networking Manufactur Specs Quantity TOTAL Cost
Device e (Dollars $)
Computers Dell Core i5 with a RAM of 6GB,
1TB disk capacity, 3.2GHZ and
have optical drives.
1400 14000000
Laptops HP Core i5 with a RAM of 8GB,
500GB and supports AMD
graphics.
80 200000
Servers Cisco Have all the speed of up to 20G 10 12000
Switch Cisco Each switch has about 48 Ports 30 36000
Iphones cisco - Screen display is 5 inches and
they are portable
150 250,000
Switch Cisco Supports 48 10/100/1000
Ethernet ports, has forwarding
capacity of about 76Mbps
25 24000
Routers Cisco Supports up to 20G
- It has more than two
antennas
Has a frequency channel of
about 8GHZ, Supports all
WEP, WPA and the WPA2,
Its compliant to ABCs
standards of 802.11
2 8500
Cables 4000 Feet 5 rolls 5000
Firewall Cisco RV220w network that has a high
performance in filtering the data
5 75000
VPNs Cisco We will use CISCO VPN 3002 4 6500
Computers Dell Core i5 with a RAM of 6GB,
1TB disk capacity, 3.2GHZ and
have optical drives.
1400 14000000
Laptops HP Core i5 with a RAM of 8GB,
500GB and supports AMD
graphics.
80 200000
Servers Cisco Have all the speed of up to 20G 10 12000
Switch Cisco Each switch has about 48 Ports 30 36000
Iphones cisco - Screen display is 5 inches and
they are portable
150 250,000
Switch Cisco Supports 48 10/100/1000
Ethernet ports, has forwarding
capacity of about 76Mbps
25 24000
Routers Cisco Supports up to 20G
- It has more than two
antennas
Has a frequency channel of
about 8GHZ, Supports all
WEP, WPA and the WPA2,
Its compliant to ABCs
standards of 802.11
2 8500
Cables 4000 Feet 5 rolls 5000
Firewall Cisco RV220w network that has a high
performance in filtering the data
5 75000
VPNs Cisco We will use CISCO VPN 3002 4 6500
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
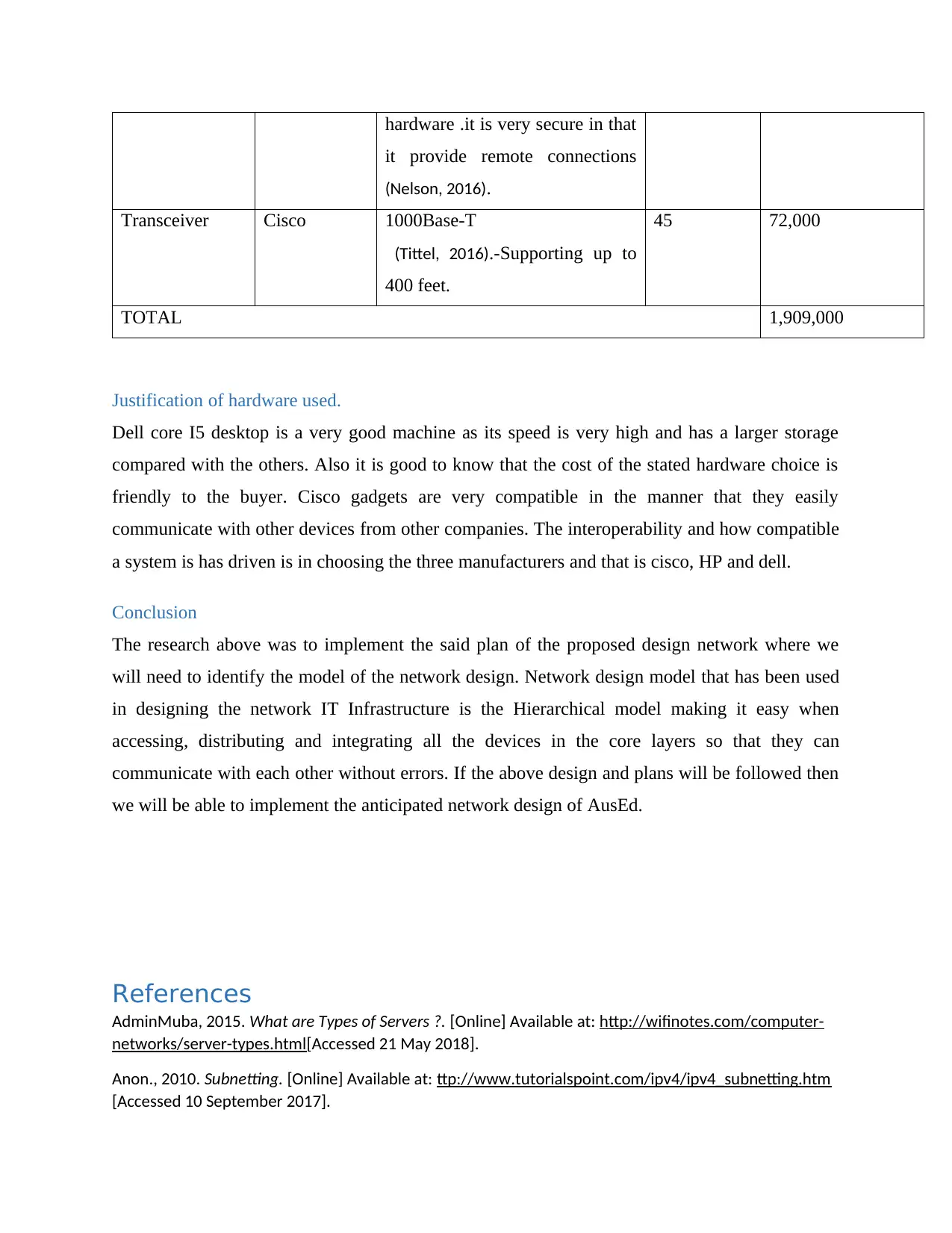
hardware .it is very secure in that
it provide remote connections
(Nelson, 2016).
Transceiver Cisco 1000Base-T
(Tittel, 2016).-Supporting up to
400 feet.
45 72,000
TOTAL 1,909,000
Justification of hardware used.
Dell core I5 desktop is a very good machine as its speed is very high and has a larger storage
compared with the others. Also it is good to know that the cost of the stated hardware choice is
friendly to the buyer. Cisco gadgets are very compatible in the manner that they easily
communicate with other devices from other companies. The interoperability and how compatible
a system is has driven is in choosing the three manufacturers and that is cisco, HP and dell.
Conclusion
The research above was to implement the said plan of the proposed design network where we
will need to identify the model of the network design. Network design model that has been used
in designing the network IT Infrastructure is the Hierarchical model making it easy when
accessing, distributing and integrating all the devices in the core layers so that they can
communicate with each other without errors. If the above design and plans will be followed then
we will be able to implement the anticipated network design of AusEd.
References
AdminMuba, 2015. What are Types of Servers ?. [Online] Available at: http://wifinotes.com/computer-
networks/server-types.html[Accessed 21 May 2018].
Anon., 2010. Subnetting. [Online] Available at: ttp://www.tutorialspoint.com/ipv4/ipv4_subnetting.htm
[Accessed 10 September 2017].
it provide remote connections
(Nelson, 2016).
Transceiver Cisco 1000Base-T
(Tittel, 2016).-Supporting up to
400 feet.
45 72,000
TOTAL 1,909,000
Justification of hardware used.
Dell core I5 desktop is a very good machine as its speed is very high and has a larger storage
compared with the others. Also it is good to know that the cost of the stated hardware choice is
friendly to the buyer. Cisco gadgets are very compatible in the manner that they easily
communicate with other devices from other companies. The interoperability and how compatible
a system is has driven is in choosing the three manufacturers and that is cisco, HP and dell.
Conclusion
The research above was to implement the said plan of the proposed design network where we
will need to identify the model of the network design. Network design model that has been used
in designing the network IT Infrastructure is the Hierarchical model making it easy when
accessing, distributing and integrating all the devices in the core layers so that they can
communicate with each other without errors. If the above design and plans will be followed then
we will be able to implement the anticipated network design of AusEd.
References
AdminMuba, 2015. What are Types of Servers ?. [Online] Available at: http://wifinotes.com/computer-
networks/server-types.html[Accessed 21 May 2018].
Anon., 2010. Subnetting. [Online] Available at: ttp://www.tutorialspoint.com/ipv4/ipv4_subnetting.htm
[Accessed 10 September 2017].
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Cisco, 2009. Benefits of a Hierarchical Network, s.l.: Cisco.
Cisco, 2012. Cisco Router. [Online] Available at: http://www.router-switch.com New and Used Cisco
network equipment, cisco router,cisco switch[Accessed 20 May 2018].
Cisco, 2013. Small Enterprise Design Profile Reference Guide, s.l.: cisco.
CISCO, 2014. Campus Design Summary, Singapore: Cisco.
Coleman, N., 2012. Happy Haven Day care network design proposal, Michigan: Network Solution Inc.
Hope, C., 2017. Router. [Online] Available at: https://www.computerhope.com/jargon/r/router.htm
[Accessed 03 may 2018].
Hope, C., 2017. Server. [Online] Available at: https://www.computerhope.com/jargon/s/server.htm
[Accessed 03 May 2018].
JoshWepman, 2015. techwalla. [Online] Available at: https://www.techwalla.com/articles/what-are-the-
benefits-of-hierarchical-network-design
Leon, A., 2015. 5 Fundamental Requirements For High-Performing Networks. A new set of network
essentials is necessary to meet the challenges of today's network administration and management, pp.
23-36.
Macken, T., 2016. Azure Resource Manager and Classic Deployment, s.l.: Microsoft.
Maggie, R., 2014. server. Types of servers, 23(12), pp. 23-40.
Meena, R., 2017. How to configure DHCP , DNS, HTTP Server in Cisco packet tracer along with switches..
Technoheper24, pp. 1-9.
Mitchell, B., 2017. Internet and Network. What is Computer Networking?, pp. 1-3.
Nelson, T., 2016. VPN requirements and components: What do you need to set up a VPN?. [Online]
Available at: https://searchenterprisewan.techtarget.com/photostory/4500270544/The-best-VPNs-for-
enterprise-use/4/VPN-requirements-and-components-What-do-you-need-to-set-up-a-VPN
[Accessed 20 May 2018].
requirement, N., 2014. Network Requirements for a Small Office , s.l.: requirements network.
Cisco, 2012. Cisco Router. [Online] Available at: http://www.router-switch.com New and Used Cisco
network equipment, cisco router,cisco switch[Accessed 20 May 2018].
Cisco, 2013. Small Enterprise Design Profile Reference Guide, s.l.: cisco.
CISCO, 2014. Campus Design Summary, Singapore: Cisco.
Coleman, N., 2012. Happy Haven Day care network design proposal, Michigan: Network Solution Inc.
Hope, C., 2017. Router. [Online] Available at: https://www.computerhope.com/jargon/r/router.htm
[Accessed 03 may 2018].
Hope, C., 2017. Server. [Online] Available at: https://www.computerhope.com/jargon/s/server.htm
[Accessed 03 May 2018].
JoshWepman, 2015. techwalla. [Online] Available at: https://www.techwalla.com/articles/what-are-the-
benefits-of-hierarchical-network-design
Leon, A., 2015. 5 Fundamental Requirements For High-Performing Networks. A new set of network
essentials is necessary to meet the challenges of today's network administration and management, pp.
23-36.
Macken, T., 2016. Azure Resource Manager and Classic Deployment, s.l.: Microsoft.
Maggie, R., 2014. server. Types of servers, 23(12), pp. 23-40.
Meena, R., 2017. How to configure DHCP , DNS, HTTP Server in Cisco packet tracer along with switches..
Technoheper24, pp. 1-9.
Mitchell, B., 2017. Internet and Network. What is Computer Networking?, pp. 1-3.
Nelson, T., 2016. VPN requirements and components: What do you need to set up a VPN?. [Online]
Available at: https://searchenterprisewan.techtarget.com/photostory/4500270544/The-best-VPNs-for-
enterprise-use/4/VPN-requirements-and-components-What-do-you-need-to-set-up-a-VPN
[Accessed 20 May 2018].
requirement, N., 2014. Network Requirements for a Small Office , s.l.: requirements network.
1 out of 11
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





