Cyber Crime in Australia: Risks, Threats, and Responses
VerifiedAdded on 2019/11/26
|16
|3636
|249
Report
AI Summary
This report provides an in-depth analysis of cyber crime in Australia, addressing the risks and issues associated with data security. It explores various contributing factors to cyber security incidents, including staff errors, poor security culture, and system vulnerabilities. The report identifies key threats such as ransomware, targeted malicious emails, and data breaches, and discusses measures to mitigate cyber intrusions, including application whitelisting, patching applications and operating systems, and restricting administrative privileges. It also outlines a four-step process for responding to externally attempted cybercrime and data security breaches, emphasizing the importance of identifying incidents, defining objectives, investigating the situation, and implementing effective response strategies. The report highlights the importance of proactive cyber security measures to protect organizations and individuals from the growing threat of cyber crime.

Running head: CYBER CRIME (AUSTRALIA)
Cyber Crime (Australia)
Name of the Student
Name of the University
Author Note
Cyber Crime (Australia)
Name of the Student
Name of the University
Author Note
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

1
CYBER CRIME (AUSTRALIA)
Table of Contents
Risks and Issues with Data Security and Cybercrime.................................................................2
Cyber Security Incident Contributing Factors.............................................................................6
Key Threats..................................................................................................................................6
Measures to Mitigate Cyber Intrusions............................................................................................8
Responds to externally attempted cybercrime and data security breach.....................................9
References:....................................................................................................................................13
CYBER CRIME (AUSTRALIA)
Table of Contents
Risks and Issues with Data Security and Cybercrime.................................................................2
Cyber Security Incident Contributing Factors.............................................................................6
Key Threats..................................................................................................................................6
Measures to Mitigate Cyber Intrusions............................................................................................8
Responds to externally attempted cybercrime and data security breach.....................................9
References:....................................................................................................................................13

2
CYBER CRIME (AUSTRALIA)
Risks and Issues with Data Security and Cybercrime
The cyber threat that is Australia facing is an unrelenting and undeniable issue that
should be concerned to the IT security professionals but the rate of vulnerabilities and attacks is
extending the room for the shareholders and individuals to get involved in this situation. Cert
Australia, the partner agency of the Australian Cyber Security Centre (ACSC) can be considered
as the primary point-of-contact for the cyber security issues that are affecting major of the
Australian businesses and firms (Jennings and Feakin 2013). Cert Australia reported that there
were 11,733 incidents that affected the firms and their businesses in 2014 – 2015. 218 among
those incidents were reported to be the national interests and critical infrastructure. With the
development of technology the cyber threats will continue to increase parallel to the
advancement in technologies (Pandey et al. 2016). Effective cyber-security is increasingly much
complex to deliver because of the following reasons:
Mobility and consumerization: The organizational boundaries are becoming blurred with
the adoption of mobile computing in the organization, which is letting IT to get closer to the
consumers and further from the firm. The organization’s data are becoming accessible
everywhere by the incorporation of bring-your-own-device and use of internet connecting via
smart-phones, tablets and other mobile devices.
Cloud: Many organizations are using cloud-based services that are being managed by the
third party including storage which is leading toward new risks (Kshetri 2013).
Change: Nowadays the organizations are adopting the post-economic-crisis world in
order to run fast and fulfill the business needs. Market expansion, introduction of new
technologies, and mergers acquisition all are expanding rapidly into the organization which is
CYBER CRIME (AUSTRALIA)
Risks and Issues with Data Security and Cybercrime
The cyber threat that is Australia facing is an unrelenting and undeniable issue that
should be concerned to the IT security professionals but the rate of vulnerabilities and attacks is
extending the room for the shareholders and individuals to get involved in this situation. Cert
Australia, the partner agency of the Australian Cyber Security Centre (ACSC) can be considered
as the primary point-of-contact for the cyber security issues that are affecting major of the
Australian businesses and firms (Jennings and Feakin 2013). Cert Australia reported that there
were 11,733 incidents that affected the firms and their businesses in 2014 – 2015. 218 among
those incidents were reported to be the national interests and critical infrastructure. With the
development of technology the cyber threats will continue to increase parallel to the
advancement in technologies (Pandey et al. 2016). Effective cyber-security is increasingly much
complex to deliver because of the following reasons:
Mobility and consumerization: The organizational boundaries are becoming blurred with
the adoption of mobile computing in the organization, which is letting IT to get closer to the
consumers and further from the firm. The organization’s data are becoming accessible
everywhere by the incorporation of bring-your-own-device and use of internet connecting via
smart-phones, tablets and other mobile devices.
Cloud: Many organizations are using cloud-based services that are being managed by the
third party including storage which is leading toward new risks (Kshetri 2013).
Change: Nowadays the organizations are adopting the post-economic-crisis world in
order to run fast and fulfill the business needs. Market expansion, introduction of new
technologies, and mergers acquisition all are expanding rapidly into the organization which is
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

3
CYBER CRIME (AUSTRALIA)
increasing the complications in strengthen the cyber-security system of the organization. Internet
technology can be stated as the primary medium or path for the intruders to enter the system of
the organization and spread into different systems.
Infrastructure: Transformation of traditional close operation technologies systems into IP
addresses leading cyber threats toward the automation system and operations of the back-office
systems. This threat is also being spread to the critical infrastructure of the organization that
includes transportation systems, power generation and other automation systems.
Ecosystem: Nowadays environment are changing to the digital connectivity or digital
world which is connecting people and data, which results in increment of the likelihood of
exposing to the cybercrime both at work and home environment (VonSolms and Van Niekerk
2013).
Based on the survey among the industries including financial, banking and other sectors, made
by ACSC (Australian cyber security center 2015) following graph has been proposed:
CYBER CRIME (AUSTRALIA)
increasing the complications in strengthen the cyber-security system of the organization. Internet
technology can be stated as the primary medium or path for the intruders to enter the system of
the organization and spread into different systems.
Infrastructure: Transformation of traditional close operation technologies systems into IP
addresses leading cyber threats toward the automation system and operations of the back-office
systems. This threat is also being spread to the critical infrastructure of the organization that
includes transportation systems, power generation and other automation systems.
Ecosystem: Nowadays environment are changing to the digital connectivity or digital
world which is connecting people and data, which results in increment of the likelihood of
exposing to the cybercrime both at work and home environment (VonSolms and Van Niekerk
2013).
Based on the survey among the industries including financial, banking and other sectors, made
by ACSC (Australian cyber security center 2015) following graph has been proposed:
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
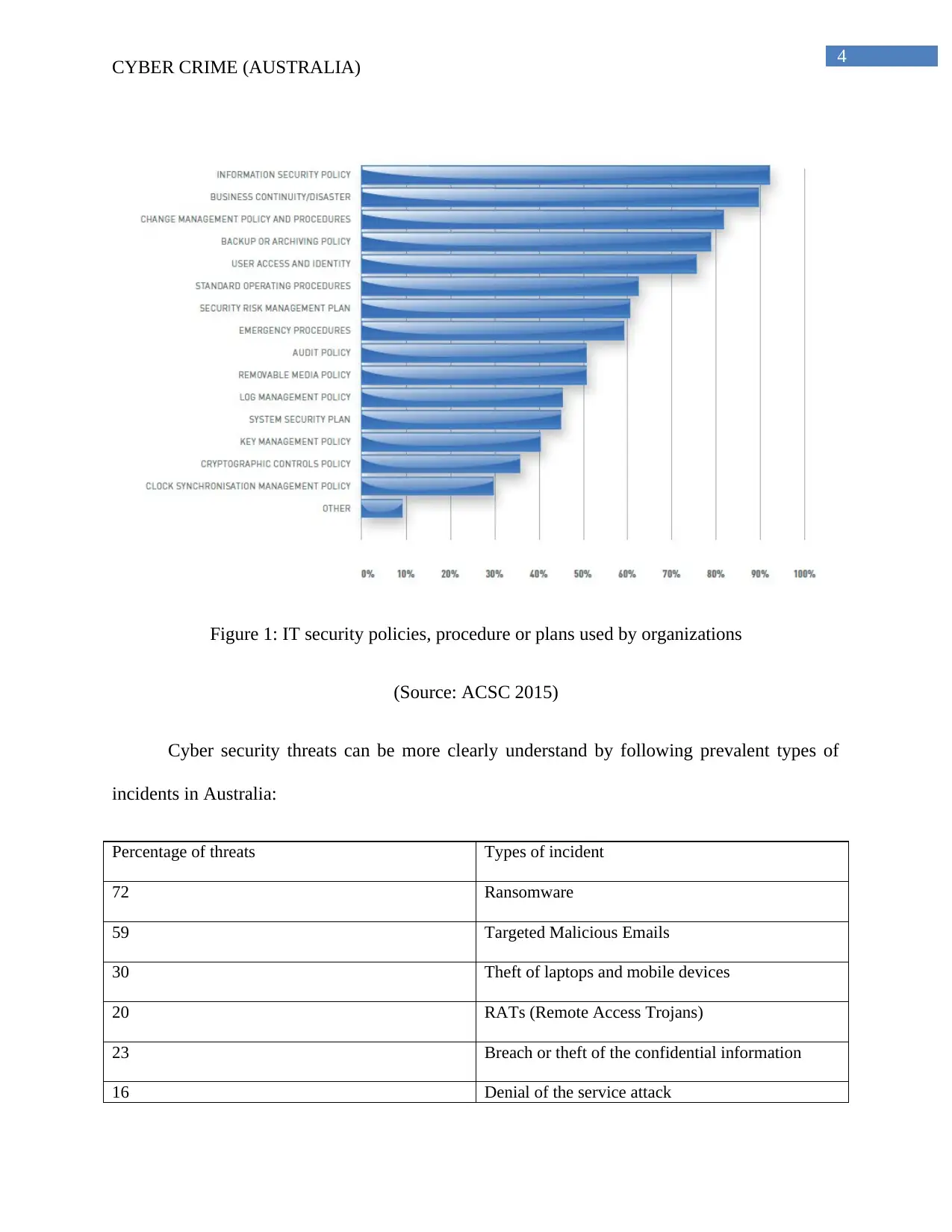
4
CYBER CRIME (AUSTRALIA)
Figure 1: IT security policies, procedure or plans used by organizations
(Source: ACSC 2015)
Cyber security threats can be more clearly understand by following prevalent types of
incidents in Australia:
Percentage of threats Types of incident
72 Ransomware
59 Targeted Malicious Emails
30 Theft of laptops and mobile devices
20 RATs (Remote Access Trojans)
23 Breach or theft of the confidential information
16 Denial of the service attack
CYBER CRIME (AUSTRALIA)
Figure 1: IT security policies, procedure or plans used by organizations
(Source: ACSC 2015)
Cyber security threats can be more clearly understand by following prevalent types of
incidents in Australia:
Percentage of threats Types of incident
72 Ransomware
59 Targeted Malicious Emails
30 Theft of laptops and mobile devices
20 RATs (Remote Access Trojans)
23 Breach or theft of the confidential information
16 Denial of the service attack
5
CYBER CRIME (AUSTRALIA)
66 Malware
30 Worm or virus infection
27 Trojan
25 Unauthorized access
17 Unauthorized access to the information from an
outsider
14 Unauthorized access to the information by an
insider
Ransomware could be stated as the most attempted security breach in the organization,
ransomware basically refers to the extortion that is made by the use of malicious virus or Trojans
that technically encrypt the contents of the computer and forces victim to pay ransom in
exchange of the decryption of those files (Kharraz et al. 2015). One of the most popular incidents
was the WannaCry ransomware attack which attacked the global computer and made a vast
destruction damaging several organizational and federal operations.
Failure to cover the basics of cyber security: The common exploits and vulnerabilities
used by the attackers in the past were helpful in revealing that there is lack in fundamental cyber
security measures. Less than a dozen vulnerabilities can lead the hackers to get access to the
system of the organization. For example: timely patching has blocked 78% of the internal
vulnerabilities among various organizations, which give a wide open door for the unauthorized
users to access the data (Pfleeger and Pfleeger 2012).
CYBER CRIME (AUSTRALIA)
66 Malware
30 Worm or virus infection
27 Trojan
25 Unauthorized access
17 Unauthorized access to the information from an
outsider
14 Unauthorized access to the information by an
insider
Ransomware could be stated as the most attempted security breach in the organization,
ransomware basically refers to the extortion that is made by the use of malicious virus or Trojans
that technically encrypt the contents of the computer and forces victim to pay ransom in
exchange of the decryption of those files (Kharraz et al. 2015). One of the most popular incidents
was the WannaCry ransomware attack which attacked the global computer and made a vast
destruction damaging several organizational and federal operations.
Failure to cover the basics of cyber security: The common exploits and vulnerabilities
used by the attackers in the past were helpful in revealing that there is lack in fundamental cyber
security measures. Less than a dozen vulnerabilities can lead the hackers to get access to the
system of the organization. For example: timely patching has blocked 78% of the internal
vulnerabilities among various organizations, which give a wide open door for the unauthorized
users to access the data (Pfleeger and Pfleeger 2012).
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

6
CYBER CRIME (AUSTRALIA)
Cyber Security Incident Contributing Factors
Many external and internal factors can be responsible for the cyber incident; some of
them are listed below:
Staff errors, poor security culture, staff omissions, improperly configured systems, and
targeting of the incidents and sophistication are the predominant factors that might contribute to
the organization cyber incidents (Kozik and Choras 2013).
Threats are motivated financially are often appeared and broad-based factors that might
affect the firm. ‘Random attack’ can be motive to attack the functioning operations of the
organization.
Key Threats
Strategic risk: Cybercrime is a serious strategic risk for any organization and should be
given highest priority in order to keep the organization on track with its objectives and goals. 25
percent of large firms and 15 percent of small firms have reported security breaches in 2015.
Data that has been stolen through cybercrime or data breach can be distributed and replicated at
the will of the intruders, which makes it almost impossible to solve. Serious data losses might
threaten the business viability (Luiijf, Bessesling and Dre Graaf 2013).
Reputation risk: Reputation of an organization is the most important aspects for all the
organization irrespective of their sectors. Expose of personal information due to any data breach
will affect the reputation of the organization, which can affect demoralization to its employee too
(Biener, Eling and Wirfs 2015). Data breaches and cybercrime can lead to the reputational risk,
which can take the form of the major lawsuit, negative publicity of products or services and
could make the ratings lower. This could also lead to the slow death of the organization through
CYBER CRIME (AUSTRALIA)
Cyber Security Incident Contributing Factors
Many external and internal factors can be responsible for the cyber incident; some of
them are listed below:
Staff errors, poor security culture, staff omissions, improperly configured systems, and
targeting of the incidents and sophistication are the predominant factors that might contribute to
the organization cyber incidents (Kozik and Choras 2013).
Threats are motivated financially are often appeared and broad-based factors that might
affect the firm. ‘Random attack’ can be motive to attack the functioning operations of the
organization.
Key Threats
Strategic risk: Cybercrime is a serious strategic risk for any organization and should be
given highest priority in order to keep the organization on track with its objectives and goals. 25
percent of large firms and 15 percent of small firms have reported security breaches in 2015.
Data that has been stolen through cybercrime or data breach can be distributed and replicated at
the will of the intruders, which makes it almost impossible to solve. Serious data losses might
threaten the business viability (Luiijf, Bessesling and Dre Graaf 2013).
Reputation risk: Reputation of an organization is the most important aspects for all the
organization irrespective of their sectors. Expose of personal information due to any data breach
will affect the reputation of the organization, which can affect demoralization to its employee too
(Biener, Eling and Wirfs 2015). Data breaches and cybercrime can lead to the reputational risk,
which can take the form of the major lawsuit, negative publicity of products or services and
could make the ratings lower. This could also lead to the slow death of the organization through
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

7
CYBER CRIME (AUSTRALIA)
negative feedbacks and lower rating. A single data breach can give option to the suppliers to
offer less favorable terms.
Compliance risk: Cybercrimes and data breaches can lead to the compliance risk for an
organization, which can affect the future of the business. Many cyber attacks in Australia have
focused on breaching personal details of the wealthier clients of private banks, which can be a
bigger issue for financial companies with a risk of disclosure of information. After realizing the
organization’s data has been breached by cyber crime, in few times it is prove to be decisive in
terms of the organization’s ability to ameliorate its losses, including any regulatory compliance
fallout.
Financial risk: Cybercrimes increases the probability of financial risk, attacks like
wannacry, One LogIn data breach, Brooks Brothers are the example how data breaches and
cybercrimes have affected the organization financially. Unauthorized access of data that are
related to the organizational operations may give access to the intruders to their accounts and
manipulate them for personal use.
Operational risk: Cyber crime and data breaches are common operational risk for the
organization and a topic of concern for all the organizations, because of the level of media
attention and financial regulators. Priority should be given to this as the rise in numbers and
complexities of cyber-attacks represents threat to an organization’s profitable existence and give
rise to the operational risks. Cyber threats may lead an organization towards exposures like costs
fraud losses, lawsuits and business continuity, which can be serious risk for the organization
towards its achievements and goals (Krekel, Adams and Bakos 2012). Intrusion can be made in
order to fraud the company, for example recently FinCEN provided evidence that Robert Eisten
CYBER CRIME (AUSTRALIA)
negative feedbacks and lower rating. A single data breach can give option to the suppliers to
offer less favorable terms.
Compliance risk: Cybercrimes and data breaches can lead to the compliance risk for an
organization, which can affect the future of the business. Many cyber attacks in Australia have
focused on breaching personal details of the wealthier clients of private banks, which can be a
bigger issue for financial companies with a risk of disclosure of information. After realizing the
organization’s data has been breached by cyber crime, in few times it is prove to be decisive in
terms of the organization’s ability to ameliorate its losses, including any regulatory compliance
fallout.
Financial risk: Cybercrimes increases the probability of financial risk, attacks like
wannacry, One LogIn data breach, Brooks Brothers are the example how data breaches and
cybercrimes have affected the organization financially. Unauthorized access of data that are
related to the organizational operations may give access to the intruders to their accounts and
manipulate them for personal use.
Operational risk: Cyber crime and data breaches are common operational risk for the
organization and a topic of concern for all the organizations, because of the level of media
attention and financial regulators. Priority should be given to this as the rise in numbers and
complexities of cyber-attacks represents threat to an organization’s profitable existence and give
rise to the operational risks. Cyber threats may lead an organization towards exposures like costs
fraud losses, lawsuits and business continuity, which can be serious risk for the organization
towards its achievements and goals (Krekel, Adams and Bakos 2012). Intrusion can be made in
order to fraud the company, for example recently FinCEN provided evidence that Robert Eisten

8
CYBER CRIME (AUSTRALIA)
had made fraud in the real-estate business and made money for personal benefits. Many
organizations including banks and other sectors have developed scenarios that are related to the
catastrophic events such as a cyber-attack in order to assess the operational risk exposures like
business continuity, costs, fraud losses, lawsuits
Measures to Mitigate Cyber Intrusions
Following are the few measures that can be helpful in mitigating the data breaches in the
organization:
Application whitelisting: It is designed in order to protect against malicious wares and
unauthorized access to the system where operational data of the organization are being saved.
The main aim of this application is to ensure that only software libraries (DDLS) and specifically
selected programs can be executed to the system and stop others from getting access to the
database of the system (Pfleeger and Caputo 2012). This could be helpful in resisting the
unwanted program execution in the system in order to keep the saved data protected from
unauthorized user or any intruder.
Patching applications: It is a critical activity in making sure that the system is completely
secures by patching the applications. This can be achieved by mitigating the system with
‘extreme risk’ vulnerabilities before two days and upgrading the application that are out dated
with the latest version that is available in the market or from any service provider. This will help
in new programs and coding for the application and the intruders will be vulnerable with these
codes and will not be able to make intrusion to the system using that application (Vukovic et al.
2012).
Patching Operating Systems:
CYBER CRIME (AUSTRALIA)
had made fraud in the real-estate business and made money for personal benefits. Many
organizations including banks and other sectors have developed scenarios that are related to the
catastrophic events such as a cyber-attack in order to assess the operational risk exposures like
business continuity, costs, fraud losses, lawsuits
Measures to Mitigate Cyber Intrusions
Following are the few measures that can be helpful in mitigating the data breaches in the
organization:
Application whitelisting: It is designed in order to protect against malicious wares and
unauthorized access to the system where operational data of the organization are being saved.
The main aim of this application is to ensure that only software libraries (DDLS) and specifically
selected programs can be executed to the system and stop others from getting access to the
database of the system (Pfleeger and Caputo 2012). This could be helpful in resisting the
unwanted program execution in the system in order to keep the saved data protected from
unauthorized user or any intruder.
Patching applications: It is a critical activity in making sure that the system is completely
secures by patching the applications. This can be achieved by mitigating the system with
‘extreme risk’ vulnerabilities before two days and upgrading the application that are out dated
with the latest version that is available in the market or from any service provider. This will help
in new programs and coding for the application and the intruders will be vulnerable with these
codes and will not be able to make intrusion to the system using that application (Vukovic et al.
2012).
Patching Operating Systems:
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

9
CYBER CRIME (AUSTRALIA)
The older version of the operating systems that are being used in the system is vulnerable
to the cyber-attack by the intruders. It is another critical activity in the steps of ensuring the
system security from vulnerable attacks. Similar to the applications, operating system also needs
to be upgraded with the latest updates in order to protect the system from any unauthorized
intrusions.
Restricting administrative privileges: Malicious actors generally attacked the
administrator accounts rather than other user accounts as they have more privilege to access than
other user accounts. The likelihood of compromising data can be reduced by restricting the
administrative privileges in the operating systems and neither allowing checking emails nor any
web browsing.
Responds to externally attempted cybercrime and data security breach
Responds to any external cyber crime and data breach can be done following four steps:
Step 1 Identifying Cyber Security Incidents: In order to identify cyber security incidents
an individual needs to analyze the level of the security breach and then confirm the type of
incident that which type of intrusion have been made. Some incidents are very easily detectable
whereas some are impossible to be detected as it recently happened to the Brook Brothers, stores
which had reported that the intrusion was detected after a year. For a year the personal
information of the individual were at stake (Hong, Liu and Govindarasu 2014). Many of these
incidents are made to steal confidential and credential information or data generally attempted by
the group of hackers in order to obtain the sensitive information and intellectual property of the
organization. This results, these are mostly unobtrusive and non-destructive (not all, some are
destructive), and undetectable, as the tracks have been covered by the intruders. Following are
CYBER CRIME (AUSTRALIA)
The older version of the operating systems that are being used in the system is vulnerable
to the cyber-attack by the intruders. It is another critical activity in the steps of ensuring the
system security from vulnerable attacks. Similar to the applications, operating system also needs
to be upgraded with the latest updates in order to protect the system from any unauthorized
intrusions.
Restricting administrative privileges: Malicious actors generally attacked the
administrator accounts rather than other user accounts as they have more privilege to access than
other user accounts. The likelihood of compromising data can be reduced by restricting the
administrative privileges in the operating systems and neither allowing checking emails nor any
web browsing.
Responds to externally attempted cybercrime and data security breach
Responds to any external cyber crime and data breach can be done following four steps:
Step 1 Identifying Cyber Security Incidents: In order to identify cyber security incidents
an individual needs to analyze the level of the security breach and then confirm the type of
incident that which type of intrusion have been made. Some incidents are very easily detectable
whereas some are impossible to be detected as it recently happened to the Brook Brothers, stores
which had reported that the intrusion was detected after a year. For a year the personal
information of the individual were at stake (Hong, Liu and Govindarasu 2014). Many of these
incidents are made to steal confidential and credential information or data generally attempted by
the group of hackers in order to obtain the sensitive information and intellectual property of the
organization. This results, these are mostly unobtrusive and non-destructive (not all, some are
destructive), and undetectable, as the tracks have been covered by the intruders. Following are
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

10
CYBER CRIME (AUSTRALIA)
the actions that can help in detecting the cyber security incidents: Technical monitoring system
that can generate alert if any data is being transferred, stolen or manipulation of data can be
helpful in detecting these incidents and apply measures at early stage (Shin, Son and Heo 2015).
Example of these systems is DLP (Data Loss Prevention), IDS (Intrusion Detection System), log
analysis and antivirus. Anomalies detected by reviews or investigations, or by audits.
Step 2 Define Objectives and Investigate Situation: There are some questions that need to be
answered before reaching any conclusion about defining objective and situation, which are:
Who was the intruder?
What is the scope and extent of the attack?
When the attack started?
What is the loss?
Why the intrusion was made?
Following are the objectives that an individual will have to learn about the intruder in order
to take counter measures based on the behavior of the intruder. An individual should determine
what methodologies attackers were using to access the data or information of the system.
Determining the motivation or intention of the intruders like whether it was made for extortion,
fraud, or it was made to steal intellectual property, or revenge or critical services could help an
individual in defining the objective and situation of the case. Another point that should be
determined for defining the situation and objective is the focus of the intruders, whether they
were focusing the organization, or individual, or the market of the organization (Singh et al.
2016). Under this section there are some measures that can help in mitigating these threats,
which are using cyber threat intelligence (CREST), conducting triage (This includes Classifying,
CYBER CRIME (AUSTRALIA)
the actions that can help in detecting the cyber security incidents: Technical monitoring system
that can generate alert if any data is being transferred, stolen or manipulation of data can be
helpful in detecting these incidents and apply measures at early stage (Shin, Son and Heo 2015).
Example of these systems is DLP (Data Loss Prevention), IDS (Intrusion Detection System), log
analysis and antivirus. Anomalies detected by reviews or investigations, or by audits.
Step 2 Define Objectives and Investigate Situation: There are some questions that need to be
answered before reaching any conclusion about defining objective and situation, which are:
Who was the intruder?
What is the scope and extent of the attack?
When the attack started?
What is the loss?
Why the intrusion was made?
Following are the objectives that an individual will have to learn about the intruder in order
to take counter measures based on the behavior of the intruder. An individual should determine
what methodologies attackers were using to access the data or information of the system.
Determining the motivation or intention of the intruders like whether it was made for extortion,
fraud, or it was made to steal intellectual property, or revenge or critical services could help an
individual in defining the objective and situation of the case. Another point that should be
determined for defining the situation and objective is the focus of the intruders, whether they
were focusing the organization, or individual, or the market of the organization (Singh et al.
2016). Under this section there are some measures that can help in mitigating these threats,
which are using cyber threat intelligence (CREST), conducting triage (This includes Classifying,

11
CYBER CRIME (AUSTRALIA)
Prioritizing, and Assigning), carrying out first response, and performing initial analysis could
have helped JP Morgan Chase & Co. to keep the information more secured. These steps could
also help in preventing the intrusions like this, if ever happened again (Skully 2014).
Step 3 Take appropriate actions: Containing the cyber security incident is the first key of
action that should be taken after the initial investigation process, which includes:
Blocking malware programs or sources like websites and email addresses.
Logging and blocking of unauthorized user access, as an unauthorized user can
manipulate or expose the information to the world, which is not acceptable for any
organization with respect to the competitive market.
Upgraded and filtered firewall, which could give resistance to the viruses from using the
system as platform to execute further damage (Heckman et al. 2013).
Closing particular mails and ports servers which have the capability to upload malicious
program into the system. Many of the malicious viruses are generated using the emails
with malicious coding that can hamper the organization by manipulating the saved data
and information (Vacca 2013).
Isolating the system means, not any type connections between the systems that are being
applicable in the organization could prevent the spread of malicious program to every
system. This will let the intruders to get access to only one system, which is also not good
for the organization but could help in minimizing the damage that intruders can do with
the information.
Relocating website home pages, as it will make intruders impossible to track the coding
again and again and prepare for the intrusion.
CYBER CRIME (AUSTRALIA)
Prioritizing, and Assigning), carrying out first response, and performing initial analysis could
have helped JP Morgan Chase & Co. to keep the information more secured. These steps could
also help in preventing the intrusions like this, if ever happened again (Skully 2014).
Step 3 Take appropriate actions: Containing the cyber security incident is the first key of
action that should be taken after the initial investigation process, which includes:
Blocking malware programs or sources like websites and email addresses.
Logging and blocking of unauthorized user access, as an unauthorized user can
manipulate or expose the information to the world, which is not acceptable for any
organization with respect to the competitive market.
Upgraded and filtered firewall, which could give resistance to the viruses from using the
system as platform to execute further damage (Heckman et al. 2013).
Closing particular mails and ports servers which have the capability to upload malicious
program into the system. Many of the malicious viruses are generated using the emails
with malicious coding that can hamper the organization by manipulating the saved data
and information (Vacca 2013).
Isolating the system means, not any type connections between the systems that are being
applicable in the organization could prevent the spread of malicious program to every
system. This will let the intruders to get access to only one system, which is also not good
for the organization but could help in minimizing the damage that intruders can do with
the information.
Relocating website home pages, as it will make intruders impossible to track the coding
again and again and prepare for the intrusion.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 16
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.




![Cyber Security Research Paper Abstract - [University] - [Course Name]](/_next/image/?url=https%3A%2F%2Fdesklib.com%2Fmedia%2Fimages%2Fbd%2F04151bc652ee49f480e5594ea23a69c7.jpg&w=256&q=75)
