Comprehensive Cybersecurity Risk Assessment for Australia Post
VerifiedAdded on 2023/06/12
|20
|3411
|255
Report
AI Summary
This report presents a comprehensive cybersecurity risk assessment for Australia Post, focusing on its data center and wider network infrastructure. It begins by providing context on the organization, including its background, recent strategic decisions, and risk classifications. The report details the products and services offered by Australia Post, identifies key stakeholders, and analyzes internal and external issues impacting the business. A risk management methodology based on OCTAVE is employed, defining risk criteria, impact criteria, and creating a risk matrix. The assessment covers asset information, vulnerability threats, risk controls, and mitigation processes. The report concludes with a risk rating and tolerance level analysis, providing recommendations for improving Australia Post's cybersecurity posture. This document is available on Desklib, a platform offering study tools and solved assignments for students.

Running head: APPLIED CYBERSECURITY
APPLIED CYBERSECURITY
Name of the Student
Name of the University
Author Note:
APPLIED CYBERSECURITY
Name of the Student
Name of the University
Author Note:
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

1APPLIED CYBERSECURITY
Table of Contents
Introduction......................................................................................................................................2
Discussion........................................................................................................................................3
Context of the organization.........................................................................................................3
Risk Classification.......................................................................................................................4
Products and services...................................................................................................................5
Stakeholders.................................................................................................................................6
Internal and External Issues.........................................................................................................6
Scope............................................................................................................................................7
Risk Management Methodology..................................................................................................7
Definition of risk criteria.............................................................................................................9
Impact Criteria...........................................................................................................................10
Risk Matrix................................................................................................................................11
Risk rating and tolerance level..................................................................................................11
Assets information.....................................................................................................................12
Risk Assessment........................................................................................................................13
Conclusion.....................................................................................................................................16
References......................................................................................................................................17
Table of Contents
Introduction......................................................................................................................................2
Discussion........................................................................................................................................3
Context of the organization.........................................................................................................3
Risk Classification.......................................................................................................................4
Products and services...................................................................................................................5
Stakeholders.................................................................................................................................6
Internal and External Issues.........................................................................................................6
Scope............................................................................................................................................7
Risk Management Methodology..................................................................................................7
Definition of risk criteria.............................................................................................................9
Impact Criteria...........................................................................................................................10
Risk Matrix................................................................................................................................11
Risk rating and tolerance level..................................................................................................11
Assets information.....................................................................................................................12
Risk Assessment........................................................................................................................13
Conclusion.....................................................................................................................................16
References......................................................................................................................................17

2APPLIED CYBERSECURITY
Introduction
The following report reflects on the Australian post office which was started in the year
of 1809. Isaac Nichols founded the post office in the area of south wales (Daunton, 2015). The
business of Australian post office has changed a lot in last few years. Australian letters have
reached the highest value in the last few years. Australian post office is planning to shift to
digital communication and various kinds of online transaction which has affected a lot. Along
with this it has created many kinds of opportunities. Various people round the globe are selling
and buying their goods online by focusing on the fact that the parcels are not delivered. As a
result of this various kinds of interaction can be made for making that interaction secure, fast and
lastly convenient (Wisbauer, 2018). Working as Australian postal corporation it is considered as
one of the most trusted brand. It mainly operates Australia and along with this it has some
branches and operating more than 34,000 people. Corporation is considered to be self-funded as
it can easily make use of large number of assets and resources which can be used for earning
profit and along with this delivering of various kinds of community services.
In the coming pages of the report an idea has been provided regarding the context of the
organization that is its background. Various kinds of products and services offered by Australian
post has been discussed in details. After that various kinds of stakeholders of Australian post has
been discussed in details. An analysis has been done regarding impact of criteria of Australia
post office. In the end a risk assessment matrix has been prepared which consist of all the
necessary parameters.
Introduction
The following report reflects on the Australian post office which was started in the year
of 1809. Isaac Nichols founded the post office in the area of south wales (Daunton, 2015). The
business of Australian post office has changed a lot in last few years. Australian letters have
reached the highest value in the last few years. Australian post office is planning to shift to
digital communication and various kinds of online transaction which has affected a lot. Along
with this it has created many kinds of opportunities. Various people round the globe are selling
and buying their goods online by focusing on the fact that the parcels are not delivered. As a
result of this various kinds of interaction can be made for making that interaction secure, fast and
lastly convenient (Wisbauer, 2018). Working as Australian postal corporation it is considered as
one of the most trusted brand. It mainly operates Australia and along with this it has some
branches and operating more than 34,000 people. Corporation is considered to be self-funded as
it can easily make use of large number of assets and resources which can be used for earning
profit and along with this delivering of various kinds of community services.
In the coming pages of the report an idea has been provided regarding the context of the
organization that is its background. Various kinds of products and services offered by Australian
post has been discussed in details. After that various kinds of stakeholders of Australian post has
been discussed in details. An analysis has been done regarding impact of criteria of Australia
post office. In the end a risk assessment matrix has been prepared which consist of all the
necessary parameters.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

3APPLIED CYBERSECURITY
Discussion
Context of the organization
Background Australian post is well known government
owned organization which is owned by
commonwealth of Australia (Ginsburg, 2017).
It also provides portal services which is works
both locally and internationally. It was
founded on 25th April 1809. The headquarter
of Australian post is located in Melbourne,
Victoria, Australia. It comes up with 4,429
outlets in metropolitan. While it comes up
with 2561 outlets in rural and remote areas.
Recent corporate and strategic decision For increasing the marketing Australian post
service is looking for digital world where one
needs to establish connection with various
business and government by making use of
large number of challenges for both digital
and in- person (Robertson, 2016). The
organization is focusing to create unique kind
of relevance by making use of network by
making use of design solution for large
number of solution in abilities, ages, regions
and different ages of people.
Discussion
Context of the organization
Background Australian post is well known government
owned organization which is owned by
commonwealth of Australia (Ginsburg, 2017).
It also provides portal services which is works
both locally and internationally. It was
founded on 25th April 1809. The headquarter
of Australian post is located in Melbourne,
Victoria, Australia. It comes up with 4,429
outlets in metropolitan. While it comes up
with 2561 outlets in rural and remote areas.
Recent corporate and strategic decision For increasing the marketing Australian post
service is looking for digital world where one
needs to establish connection with various
business and government by making use of
large number of challenges for both digital
and in- person (Robertson, 2016). The
organization is focusing to create unique kind
of relevance by making use of network by
making use of design solution for large
number of solution in abilities, ages, regions
and different ages of people.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
4APPLIED CYBERSECURITY
Australian post is much focused to develop
creative people, fostering innovation and
making acceleration of various kinds of
products and services which are offered
(Brotchie et al., 2017). It is redeveloped the
system in such a way that it can easily
improve convenience for the customer.
It has also certain number of products and
services for our system and experts with new
kind of bill payment option.
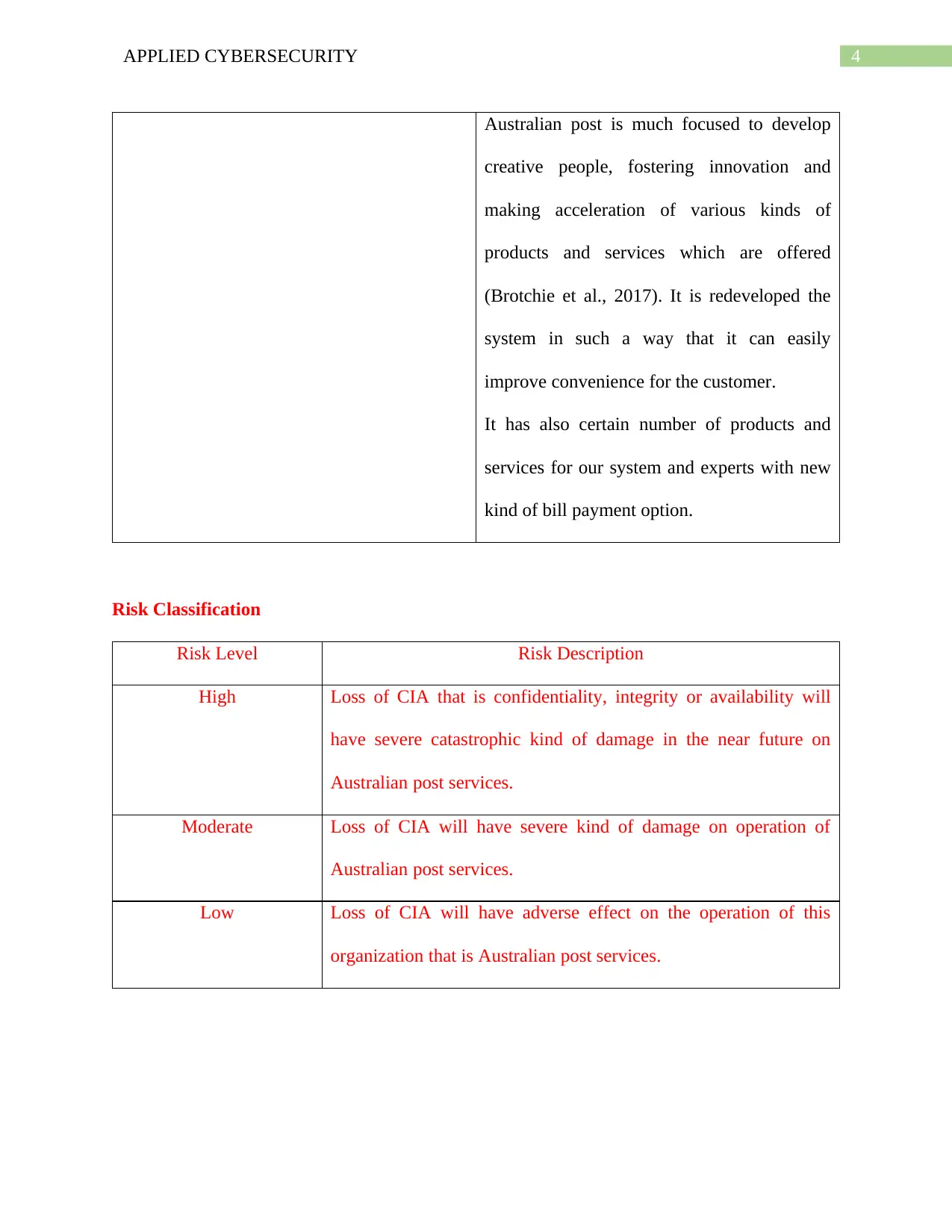
Risk Classification
Risk Level Risk Description
High Loss of CIA that is confidentiality, integrity or availability will
have severe catastrophic kind of damage in the near future on
Australian post services.
Moderate Loss of CIA will have severe kind of damage on operation of
Australian post services.
Low Loss of CIA will have adverse effect on the operation of this
organization that is Australian post services.
Australian post is much focused to develop
creative people, fostering innovation and
making acceleration of various kinds of
products and services which are offered
(Brotchie et al., 2017). It is redeveloped the
system in such a way that it can easily
improve convenience for the customer.
It has also certain number of products and
services for our system and experts with new
kind of bill payment option.
Risk Classification
Risk Level Risk Description
High Loss of CIA that is confidentiality, integrity or availability will
have severe catastrophic kind of damage in the near future on
Australian post services.
Moderate Loss of CIA will have severe kind of damage on operation of
Australian post services.
Low Loss of CIA will have adverse effect on the operation of this
organization that is Australian post services.

5APPLIED CYBERSECURITY
Products and services
Products Australian post service is more focused to
increase the basic rate of postage. It is also
much focused to provide customer service
(Topping and Wolfendale, 2017). Providing
optimization of network. Along with it much
focused on building capability for delivering
network.
Services Australian post has come up with large
number of services like
MyPost Digital Mailbox
Multi-channel marketing
Providing help to business for
managing inbound communication.
Financial, identity and commercial
services.
Merchandise Services
Providing customers with better kind
of access to services.
Modernizing the provided
infrastructure.
Products and services
Products Australian post service is more focused to
increase the basic rate of postage. It is also
much focused to provide customer service
(Topping and Wolfendale, 2017). Providing
optimization of network. Along with it much
focused on building capability for delivering
network.
Services Australian post has come up with large
number of services like
MyPost Digital Mailbox
Multi-channel marketing
Providing help to business for
managing inbound communication.
Financial, identity and commercial
services.
Merchandise Services
Providing customers with better kind
of access to services.
Modernizing the provided
infrastructure.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
6APPLIED CYBERSECURITY
Lastly investing the license network of
post office.
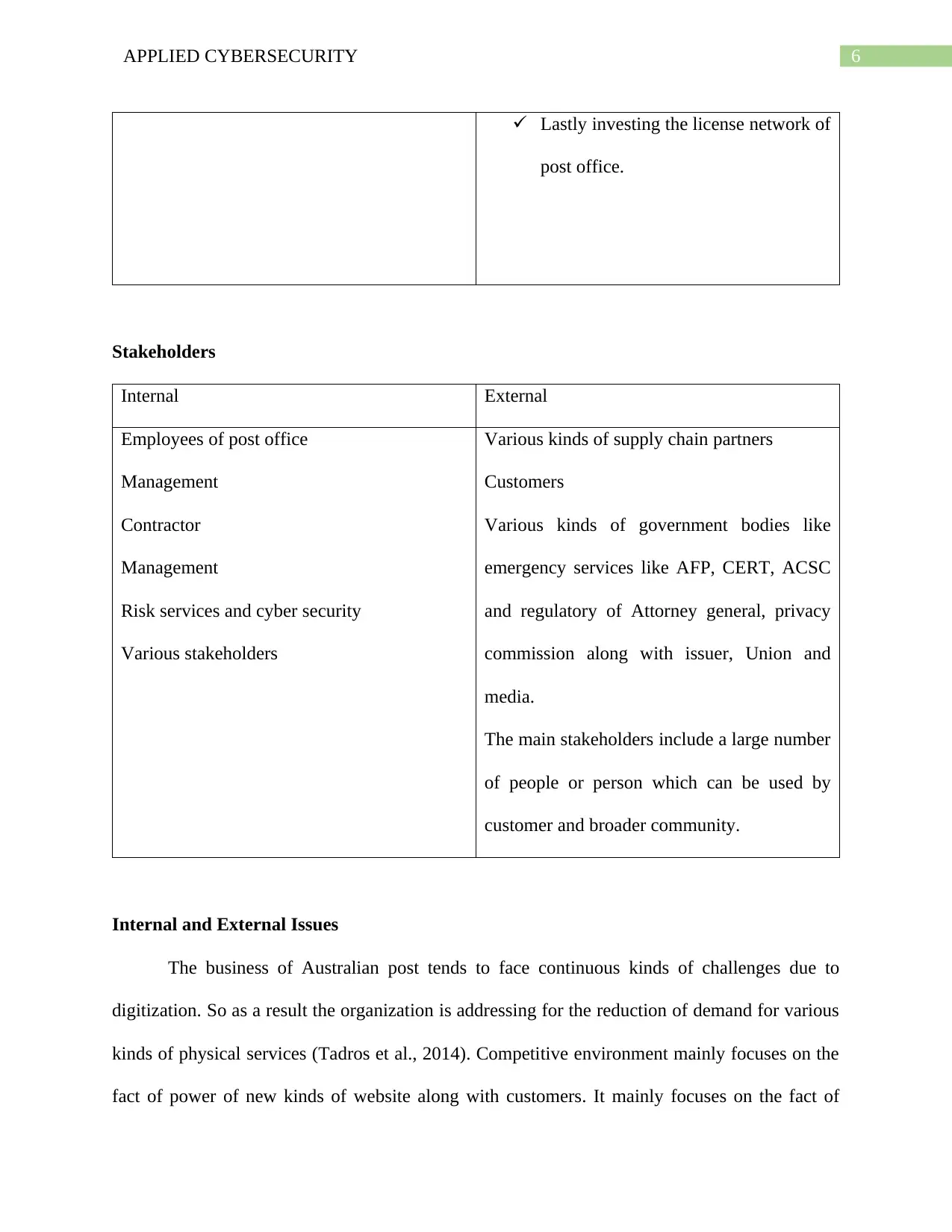
Stakeholders
Internal External
Employees of post office
Management
Contractor
Management
Risk services and cyber security
Various stakeholders
Various kinds of supply chain partners
Customers
Various kinds of government bodies like
emergency services like AFP, CERT, ACSC
and regulatory of Attorney general, privacy
commission along with issuer, Union and
media.
The main stakeholders include a large number
of people or person which can be used by
customer and broader community.
Internal and External Issues
The business of Australian post tends to face continuous kinds of challenges due to
digitization. So as a result the organization is addressing for the reduction of demand for various
kinds of physical services (Tadros et al., 2014). Competitive environment mainly focuses on the
fact of power of new kinds of website along with customers. It mainly focuses on the fact of
Lastly investing the license network of
post office.
Stakeholders
Internal External
Employees of post office
Management
Contractor
Management
Risk services and cyber security
Various stakeholders
Various kinds of supply chain partners
Customers
Various kinds of government bodies like
emergency services like AFP, CERT, ACSC
and regulatory of Attorney general, privacy
commission along with issuer, Union and
media.
The main stakeholders include a large number
of people or person which can be used by
customer and broader community.
Internal and External Issues
The business of Australian post tends to face continuous kinds of challenges due to
digitization. So as a result the organization is addressing for the reduction of demand for various
kinds of physical services (Tadros et al., 2014). Competitive environment mainly focuses on the
fact of power of new kinds of website along with customers. It mainly focuses on the fact of
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

7APPLIED CYBERSECURITY
ensuring the fact that of delivering the thing in the required way or mechanism. But with the
passage of time (Kueppers and Cooke, 2015) Australian post is addressing a large number of
issues which have arisen from disrupts of various kinds of industry.
Australian post is working hard for improving the parcel delivery system and minimizing the
carding rate from 15.5 to 10.7 percent (Heesch, Giles-Corti and Turrell, 2014). Australian post
has also invested in Customer contact centre. It has also invested in My post business for large
number of small business customer. The parcel business result in increased in size in various
domestic and international platform (Metcalfe, 2018). But at present it is addressing a large
number of issues at present market. Another kind of issue encountered in Australian post is that
customer will have to wait for longer time. So it can be easily concluded that more kind of
resources are mainly required.
Scope
Australian post is mainly committed for providing certain number of environmental
services which is committed for providing for acting like iconic status in some of leading
Australia organization (Hassanli, 2015). It mainly deals with some of the direct impacts of its
business on the environment. Australian post come across the need of managing the impact on
various business resources. It will also help in reducing cost, proper management of risk,
improvisations of customer value.
Risk Management Methodology
OCTAVE that is Operational Critical Threat, Assets and Vulnerability can be defined as
a well-known practice for risk management methodology (Hassanli, 2015). It can be easily
defined as a well-known tool which is used for evaluation of large number of risk. Various kinds
of security practices and technology are used for mitigation of large number of risk. The ultimate
ensuring the fact that of delivering the thing in the required way or mechanism. But with the
passage of time (Kueppers and Cooke, 2015) Australian post is addressing a large number of
issues which have arisen from disrupts of various kinds of industry.
Australian post is working hard for improving the parcel delivery system and minimizing the
carding rate from 15.5 to 10.7 percent (Heesch, Giles-Corti and Turrell, 2014). Australian post
has also invested in Customer contact centre. It has also invested in My post business for large
number of small business customer. The parcel business result in increased in size in various
domestic and international platform (Metcalfe, 2018). But at present it is addressing a large
number of issues at present market. Another kind of issue encountered in Australian post is that
customer will have to wait for longer time. So it can be easily concluded that more kind of
resources are mainly required.
Scope
Australian post is mainly committed for providing certain number of environmental
services which is committed for providing for acting like iconic status in some of leading
Australia organization (Hassanli, 2015). It mainly deals with some of the direct impacts of its
business on the environment. Australian post come across the need of managing the impact on
various business resources. It will also help in reducing cost, proper management of risk,
improvisations of customer value.
Risk Management Methodology
OCTAVE that is Operational Critical Threat, Assets and Vulnerability can be defined as
a well-known practice for risk management methodology (Hassanli, 2015). It can be easily
defined as a well-known tool which is used for evaluation of large number of risk. Various kinds
of security practices and technology are used for mitigation of large number of risk. The ultimate
8APPLIED CYBERSECURITY
goal of this approach is considered to be more strategical instead of tactical one. Australian post
has some kind of risk and this particular methodology can be used for accessing the risk.
OCTAVA methodology is required by Australian post for learning and making use of in-house
kind of security consultant which is used for running large number of security consultant
(Clifford et al., 2015). Various kinds of vendors make use of products under risk management
tools when understanding the vulnerability of management tools. Vulnerability management is
mainly used for identifying various kinds of holes (Chemweno et al., 2017). Risk management is
considered to be much different kind of tool. Risk management can be considered to be much
different in comparison to vulnerability management.
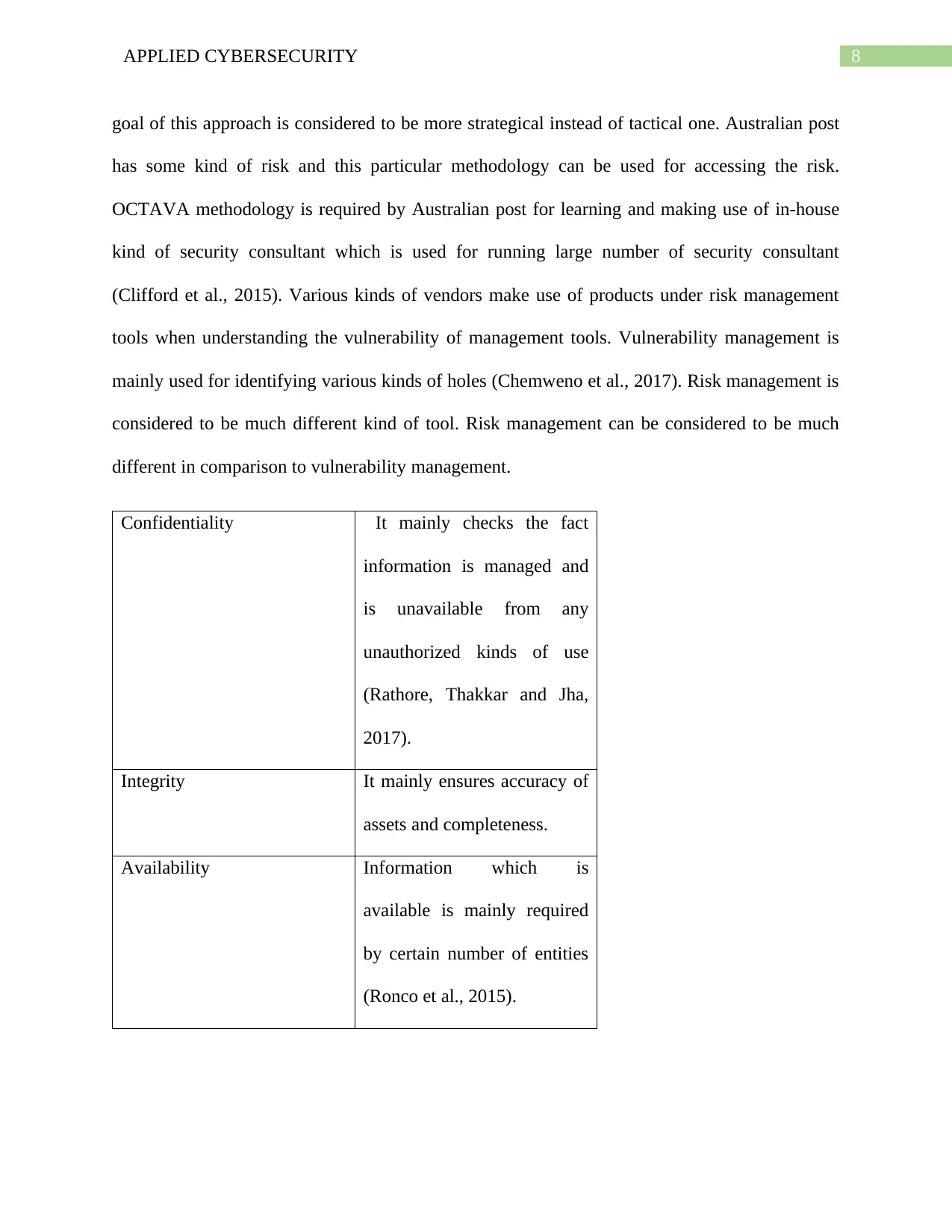
Confidentiality It mainly checks the fact
information is managed and
is unavailable from any
unauthorized kinds of use
(Rathore, Thakkar and Jha,
2017).
Integrity It mainly ensures accuracy of
assets and completeness.
Availability Information which is
available is mainly required
by certain number of entities
(Ronco et al., 2015).
goal of this approach is considered to be more strategical instead of tactical one. Australian post
has some kind of risk and this particular methodology can be used for accessing the risk.
OCTAVA methodology is required by Australian post for learning and making use of in-house
kind of security consultant which is used for running large number of security consultant
(Clifford et al., 2015). Various kinds of vendors make use of products under risk management
tools when understanding the vulnerability of management tools. Vulnerability management is
mainly used for identifying various kinds of holes (Chemweno et al., 2017). Risk management is
considered to be much different kind of tool. Risk management can be considered to be much
different in comparison to vulnerability management.
Confidentiality It mainly checks the fact
information is managed and
is unavailable from any
unauthorized kinds of use
(Rathore, Thakkar and Jha,
2017).
Integrity It mainly ensures accuracy of
assets and completeness.
Availability Information which is
available is mainly required
by certain number of entities
(Ronco et al., 2015).
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

9APPLIED CYBERSECURITY
Definition of risk criteria
Group of Risk management framework mainly checks certain number of core strategies
and business process which can effectively manage various kinds of risk along with providing
clear roles and responsibility (Poirier, 2015). This roles and responsibility are mainly used for
managing various kinds of risk. GRMF and board of appetite statement has been developed by
making use of principles in various kinds of standards which is used for risk management (Kit et
al., 2014). GRMF can be easily defined as integral kind of strategic planning processes and
various kinds of decision making (Hill, 2015). Board is mainly focused in mainly responsible for
providing direct kind of insight and monitoring of risk management processes and various kinds
of associated strategies. In a culture of risk assessment GRMF is mainly fully integrated and
various areas of business are mainly accountable for identifying and analysing risk associated
along with various kinds of activities and business
Definition of risk criteria
Group of Risk management framework mainly checks certain number of core strategies
and business process which can effectively manage various kinds of risk along with providing
clear roles and responsibility (Poirier, 2015). This roles and responsibility are mainly used for
managing various kinds of risk. GRMF and board of appetite statement has been developed by
making use of principles in various kinds of standards which is used for risk management (Kit et
al., 2014). GRMF can be easily defined as integral kind of strategic planning processes and
various kinds of decision making (Hill, 2015). Board is mainly focused in mainly responsible for
providing direct kind of insight and monitoring of risk management processes and various kinds
of associated strategies. In a culture of risk assessment GRMF is mainly fully integrated and
various areas of business are mainly accountable for identifying and analysing risk associated
along with various kinds of activities and business
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
10APPLIED CYBERSECURITY
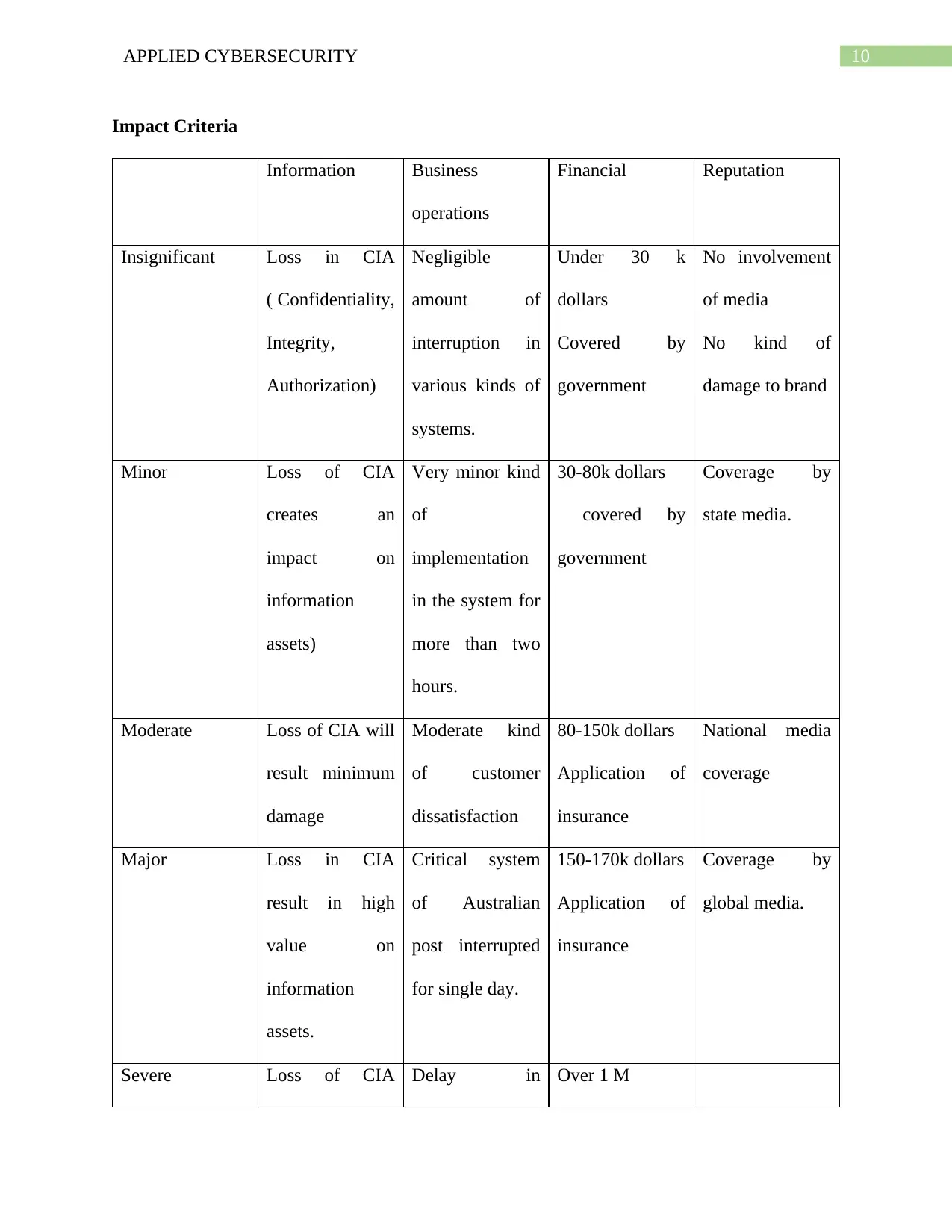
Impact Criteria
Information Business
operations
Financial Reputation
Insignificant Loss in CIA
( Confidentiality,
Integrity,
Authorization)
Negligible
amount of
interruption in
various kinds of
systems.
Under 30 k
dollars
Covered by
government
No involvement
of media
No kind of
damage to brand
Minor Loss of CIA
creates an
impact on
information
assets)
Very minor kind
of
implementation
in the system for
more than two
hours.
30-80k dollars
covered by
government
Coverage by
state media.
Moderate Loss of CIA will
result minimum
damage
Moderate kind
of customer
dissatisfaction
80-150k dollars
Application of
insurance
National media
coverage
Major Loss in CIA
result in high
value on
information
assets.
Critical system
of Australian
post interrupted
for single day.
150-170k dollars
Application of
insurance
Coverage by
global media.
Severe Loss of CIA Delay in Over 1 M
Impact Criteria
Information Business
operations
Financial Reputation
Insignificant Loss in CIA
( Confidentiality,
Integrity,
Authorization)
Negligible
amount of
interruption in
various kinds of
systems.
Under 30 k
dollars
Covered by
government
No involvement
of media
No kind of
damage to brand
Minor Loss of CIA
creates an
impact on
information
assets)
Very minor kind
of
implementation
in the system for
more than two
hours.
30-80k dollars
covered by
government
Coverage by
state media.
Moderate Loss of CIA will
result minimum
damage
Moderate kind
of customer
dissatisfaction
80-150k dollars
Application of
insurance
National media
coverage
Major Loss in CIA
result in high
value on
information
assets.
Critical system
of Australian
post interrupted
for single day.
150-170k dollars
Application of
insurance
Coverage by
global media.
Severe Loss of CIA Delay in Over 1 M
11APPLIED CYBERSECURITY
results in High
value assets of
information
Multiple value
of asset of
Australian post
impacted.
delivery of
parcels for more
than three days.
Insurance
application
Risk Matrix
Insignificant Minor Moderate Major Severe
Almost
certain
Medium High High Extreme Extreme
Likely Medium Medium High High Extreme
Possible Low Medium Medium High High
Unlikely Low Medium Medium High High
Rare Low Low Low Medium High
Risk rating and tolerance level
Risk rating description
Low Accepting various kinds of risk
No new kinds of application is needed
Medium Accepted value of risk
results in High
value assets of
information
Multiple value
of asset of
Australian post
impacted.
delivery of
parcels for more
than three days.
Insurance
application
Risk Matrix
Insignificant Minor Moderate Major Severe
Almost
certain
Medium High High Extreme Extreme
Likely Medium Medium High High Extreme
Possible Low Medium Medium High High
Unlikely Low Medium Medium High High
Rare Low Low Low Medium High
Risk rating and tolerance level
Risk rating description
Low Accepting various kinds of risk
No new kinds of application is needed
Medium Accepted value of risk
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 20
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.




