Risk Management: Digital Security Assessment for Australian Bank
VerifiedAdded on 2023/03/23
|8
|1847
|27
Report
AI Summary
This report is divided into two parts, focusing on the data administration and security risks within an Australian bank. Part 1 provides a risk assessment, detailing potential impacts, probabilities, and mitigation strategies for issues such as unencrypted data and malware. It includes a risk register outlining inherent and residual risks. Part 2 discusses the benefits of recruiting a Chief Security Information Security Officer (CSISO), emphasizing their expertise in decision-making, risk analysis, and team leadership. The report highlights how a CSISO can improve data understanding, manage short and long-term risks, and enhance the in-house team's capabilities in data organization and security policy management. The CSISO's role includes setting privacy policies, managing the information security team, and conducting risk assessments to strengthen the bank's security measures. Desklib offers a wide range of study resources, including past papers and solved assignments.

Running head: RISK MANAGEMENT
RISK MANAGEMENT
Name of the System
Name of the University
Author Note
RISK MANAGEMENT
Name of the System
Name of the University
Author Note
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

1RISK MANAGEMENT
Abstract
This report is diverged in 2 parts. The 1st part is bothered with the functioning of the data
administration of the security issues that might be present in the commencement of the
business management of the Australian bank. The 2nd part of the report is regarding the
preparing of report stating the importance of recruiting a Chief Security Information security
officer.
Abstract
This report is diverged in 2 parts. The 1st part is bothered with the functioning of the data
administration of the security issues that might be present in the commencement of the
business management of the Australian bank. The 2nd part of the report is regarding the
preparing of report stating the importance of recruiting a Chief Security Information security
officer.

2RISK MANAGEMENT
Table of Contents
Part 1..........................................................................................................................................3
Part 2..........................................................................................................................................7
References..................................................................................................................................9
Table of Contents
Part 1..........................................................................................................................................3
Part 2..........................................................................................................................................7
References..................................................................................................................................9
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
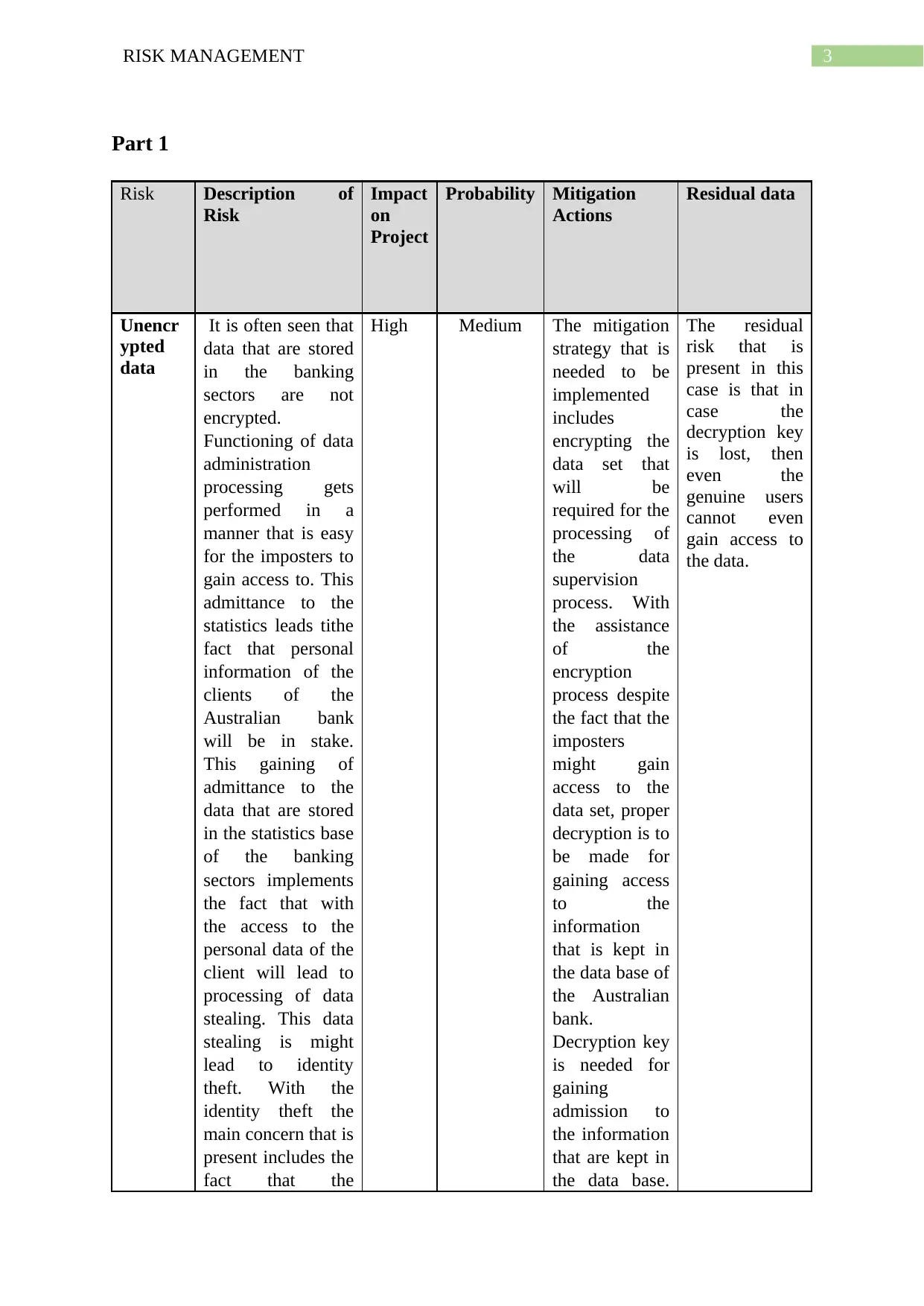
3RISK MANAGEMENT
Part 1
Risk Description of
Risk
Impact
on
Project
Probability Mitigation
Actions
Residual data
Unencr
ypted
data
It is often seen that
data that are stored
in the banking
sectors are not
encrypted.
Functioning of data
administration
processing gets
performed in a
manner that is easy
for the imposters to
gain access to. This
admittance to the
statistics leads tithe
fact that personal
information of the
clients of the
Australian bank
will be in stake.
This gaining of
admittance to the
data that are stored
in the statistics base
of the banking
sectors implements
the fact that with
the access to the
personal data of the
client will lead to
processing of data
stealing. This data
stealing is might
lead to identity
theft. With the
identity theft the
main concern that is
present includes the
fact that the
High Medium The mitigation
strategy that is
needed to be
implemented
includes
encrypting the
data set that
will be
required for the
processing of
the data
supervision
process. With
the assistance
of the
encryption
process despite
the fact that the
imposters
might gain
access to the
data set, proper
decryption is to
be made for
gaining access
to the
information
that is kept in
the data base of
the Australian
bank.
Decryption key
is needed for
gaining
admission to
the information
that are kept in
the data base.
The residual
risk that is
present in this
case is that in
case the
decryption key
is lost, then
even the
genuine users
cannot even
gain access to
the data.
Part 1
Risk Description of
Risk
Impact
on
Project
Probability Mitigation
Actions
Residual data
Unencr
ypted
data
It is often seen that
data that are stored
in the banking
sectors are not
encrypted.
Functioning of data
administration
processing gets
performed in a
manner that is easy
for the imposters to
gain access to. This
admittance to the
statistics leads tithe
fact that personal
information of the
clients of the
Australian bank
will be in stake.
This gaining of
admittance to the
data that are stored
in the statistics base
of the banking
sectors implements
the fact that with
the access to the
personal data of the
client will lead to
processing of data
stealing. This data
stealing is might
lead to identity
theft. With the
identity theft the
main concern that is
present includes the
fact that the
High Medium The mitigation
strategy that is
needed to be
implemented
includes
encrypting the
data set that
will be
required for the
processing of
the data
supervision
process. With
the assistance
of the
encryption
process despite
the fact that the
imposters
might gain
access to the
data set, proper
decryption is to
be made for
gaining access
to the
information
that is kept in
the data base of
the Australian
bank.
Decryption key
is needed for
gaining
admission to
the information
that are kept in
the data base.
The residual
risk that is
present in this
case is that in
case the
decryption key
is lost, then
even the
genuine users
cannot even
gain access to
the data.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
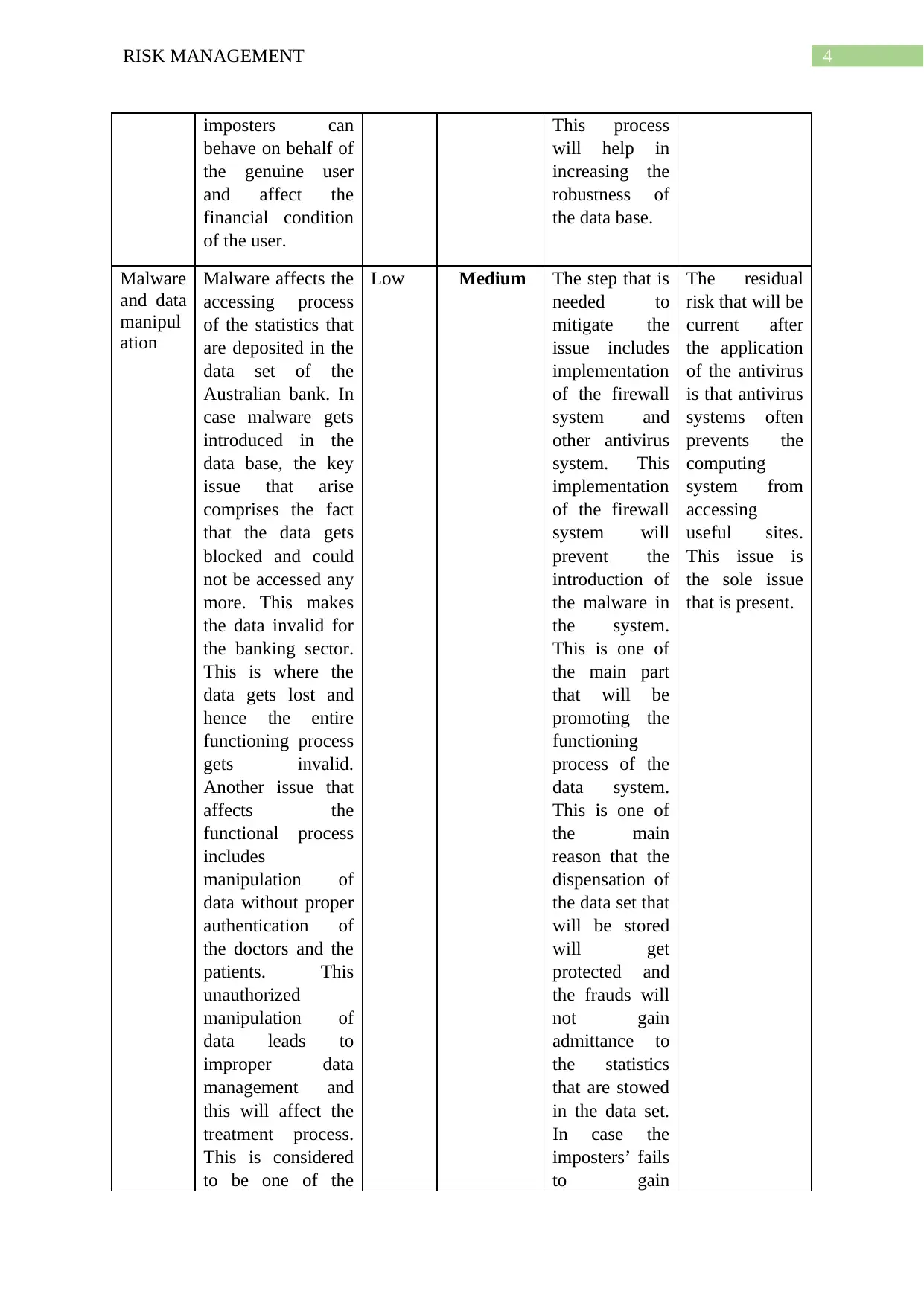
4RISK MANAGEMENT
imposters can
behave on behalf of
the genuine user
and affect the
financial condition
of the user.
This process
will help in
increasing the
robustness of
the data base.
Malware
and data
manipul
ation
Malware affects the
accessing process
of the statistics that
are deposited in the
data set of the
Australian bank. In
case malware gets
introduced in the
data base, the key
issue that arise
comprises the fact
that the data gets
blocked and could
not be accessed any
more. This makes
the data invalid for
the banking sector.
This is where the
data gets lost and
hence the entire
functioning process
gets invalid.
Another issue that
affects the
functional process
includes
manipulation of
data without proper
authentication of
the doctors and the
patients. This
unauthorized
manipulation of
data leads to
improper data
management and
this will affect the
treatment process.
This is considered
to be one of the
Low Medium The step that is
needed to
mitigate the
issue includes
implementation
of the firewall
system and
other antivirus
system. This
implementation
of the firewall
system will
prevent the
introduction of
the malware in
the system.
This is one of
the main part
that will be
promoting the
functioning
process of the
data system.
This is one of
the main
reason that the
dispensation of
the data set that
will be stored
will get
protected and
the frauds will
not gain
admittance to
the statistics
that are stowed
in the data set.
In case the
imposters’ fails
to gain
The residual
risk that will be
current after
the application
of the antivirus
is that antivirus
systems often
prevents the
computing
system from
accessing
useful sites.
This issue is
the sole issue
that is present.
imposters can
behave on behalf of
the genuine user
and affect the
financial condition
of the user.
This process
will help in
increasing the
robustness of
the data base.
Malware
and data
manipul
ation
Malware affects the
accessing process
of the statistics that
are deposited in the
data set of the
Australian bank. In
case malware gets
introduced in the
data base, the key
issue that arise
comprises the fact
that the data gets
blocked and could
not be accessed any
more. This makes
the data invalid for
the banking sector.
This is where the
data gets lost and
hence the entire
functioning process
gets invalid.
Another issue that
affects the
functional process
includes
manipulation of
data without proper
authentication of
the doctors and the
patients. This
unauthorized
manipulation of
data leads to
improper data
management and
this will affect the
treatment process.
This is considered
to be one of the
Low Medium The step that is
needed to
mitigate the
issue includes
implementation
of the firewall
system and
other antivirus
system. This
implementation
of the firewall
system will
prevent the
introduction of
the malware in
the system.
This is one of
the main part
that will be
promoting the
functioning
process of the
data system.
This is one of
the main
reason that the
dispensation of
the data set that
will be stored
will get
protected and
the frauds will
not gain
admittance to
the statistics
that are stowed
in the data set.
In case the
imposters’ fails
to gain
The residual
risk that will be
current after
the application
of the antivirus
is that antivirus
systems often
prevents the
computing
system from
accessing
useful sites.
This issue is
the sole issue
that is present.
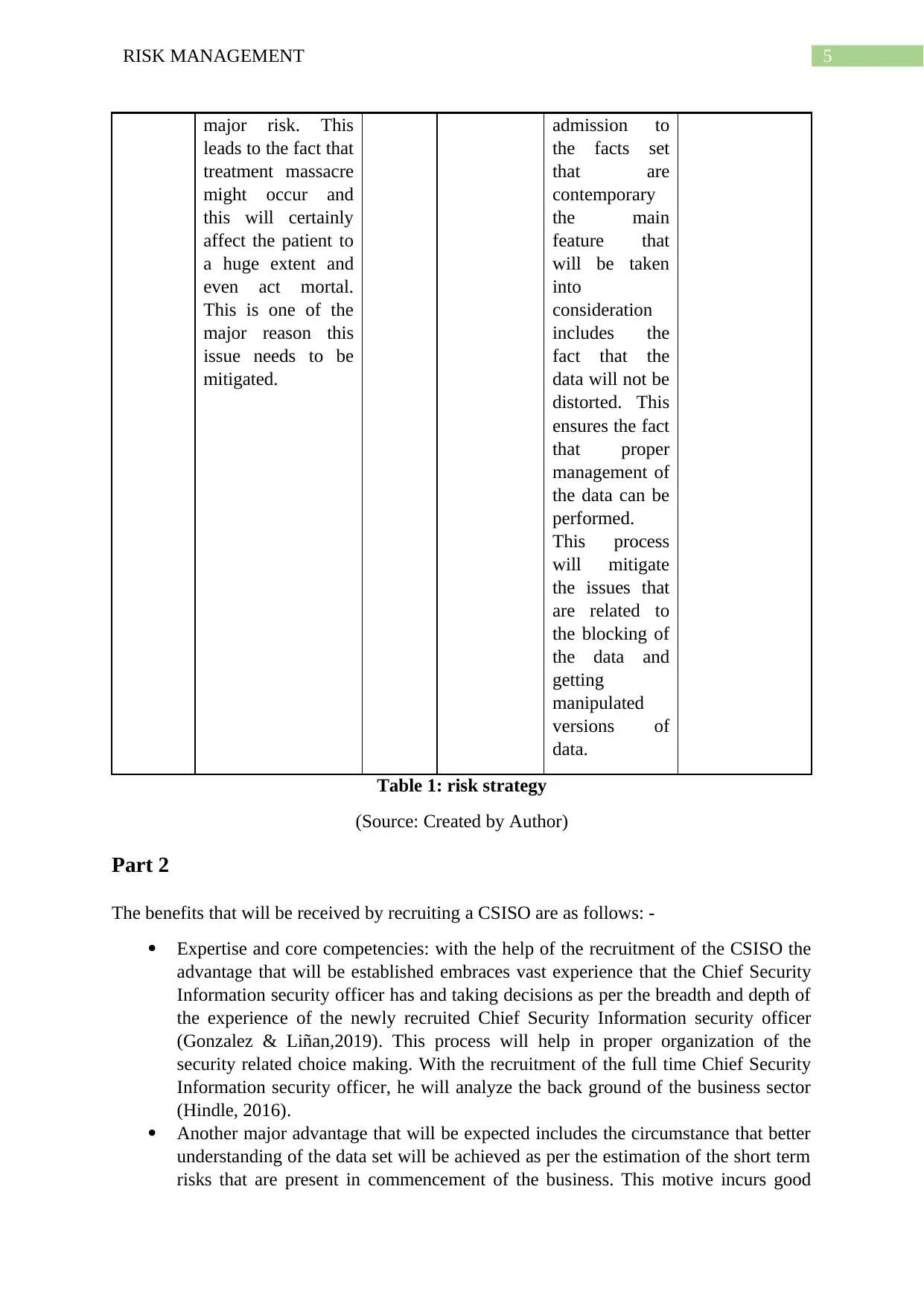
5RISK MANAGEMENT
major risk. This
leads to the fact that
treatment massacre
might occur and
this will certainly
affect the patient to
a huge extent and
even act mortal.
This is one of the
major reason this
issue needs to be
mitigated.
admission to
the facts set
that are
contemporary
the main
feature that
will be taken
into
consideration
includes the
fact that the
data will not be
distorted. This
ensures the fact
that proper
management of
the data can be
performed.
This process
will mitigate
the issues that
are related to
the blocking of
the data and
getting
manipulated
versions of
data.
Table 1: risk strategy
(Source: Created by Author)
Part 2
The benefits that will be received by recruiting a CSISO are as follows: -
Expertise and core competencies: with the help of the recruitment of the CSISO the
advantage that will be established embraces vast experience that the Chief Security
Information security officer has and taking decisions as per the breadth and depth of
the experience of the newly recruited Chief Security Information security officer
(Gonzalez & Liñan,2019). This process will help in proper organization of the
security related choice making. With the recruitment of the full time Chief Security
Information security officer, he will analyze the back ground of the business sector
(Hindle, 2016).
Another major advantage that will be expected includes the circumstance that better
understanding of the data set will be achieved as per the estimation of the short term
risks that are present in commencement of the business. This motive incurs good
major risk. This
leads to the fact that
treatment massacre
might occur and
this will certainly
affect the patient to
a huge extent and
even act mortal.
This is one of the
major reason this
issue needs to be
mitigated.
admission to
the facts set
that are
contemporary
the main
feature that
will be taken
into
consideration
includes the
fact that the
data will not be
distorted. This
ensures the fact
that proper
management of
the data can be
performed.
This process
will mitigate
the issues that
are related to
the blocking of
the data and
getting
manipulated
versions of
data.
Table 1: risk strategy
(Source: Created by Author)
Part 2
The benefits that will be received by recruiting a CSISO are as follows: -
Expertise and core competencies: with the help of the recruitment of the CSISO the
advantage that will be established embraces vast experience that the Chief Security
Information security officer has and taking decisions as per the breadth and depth of
the experience of the newly recruited Chief Security Information security officer
(Gonzalez & Liñan,2019). This process will help in proper organization of the
security related choice making. With the recruitment of the full time Chief Security
Information security officer, he will analyze the back ground of the business sector
(Hindle, 2016).
Another major advantage that will be expected includes the circumstance that better
understanding of the data set will be achieved as per the estimation of the short term
risks that are present in commencement of the business. This motive incurs good
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

6RISK MANAGEMENT
thoughtful of the statistics set will get improved (González, Ríos & García, 2018).
This estimation of issues that might be present includes the fact that proper risk
mitigation process can be performed. The importance of the Chief Security
Information security officer recruitment process is highly recommended (Garousi,
Felderer & Mäntylä, 2016). For example, in case a Chief Security Information
security officer is recruited he will be having a precise and accurate understanding of
the issues that might arise in the short term period (Brooks, Wells & Pratt, 2017).
This understanding of the risks that might occur will affect the functioning process
of the business management process in a better manner. This is one of the main
reason that better understanding of the scenario. This proper underhanging of the
scenario helps in better understanding of the long term issues that might arise
(Laplante, 2017). This process is performed with the help of constant monitoring of
the business case.
This process of recruiting a CSISO will help in bettering of the strength of the in
house team (Braude & Bernstein, 2016). This increasing of the strength of the in-
house team will incur the fact that development of strategic and responsibilities as
per the commencing of the data organization scheme as this the reason that proper
management and mentoring of the staffs will be performed (Molléri, Mendes &
Petersen, 2019). This is the main reason that the level C employees were not very
pleased with the recruitment process of the Chief Security Information security
officer. Additional training can also be provided by them. The in house team work
load also gets diverted and work load balance increases (Butler, Howard& Green,
2018).
The tasks that are handled by the CSISO includes the functioning of the setting of
the directing privacy and security policies (Marseu, Kolberg & Birtel, 2016).
Another characteristic that is taken into thought includes the fact that managing of
the information security team is responsible for the processing of the executive
management (Schmitz, Mahapatra & Nerur, 2018). Running of risk assessment as
per the operational security has been one of the major aspect that provides better
understanding of the enterprise security measures that are needed for increasing the
robustness of the platform.
thoughtful of the statistics set will get improved (González, Ríos & García, 2018).
This estimation of issues that might be present includes the fact that proper risk
mitigation process can be performed. The importance of the Chief Security
Information security officer recruitment process is highly recommended (Garousi,
Felderer & Mäntylä, 2016). For example, in case a Chief Security Information
security officer is recruited he will be having a precise and accurate understanding of
the issues that might arise in the short term period (Brooks, Wells & Pratt, 2017).
This understanding of the risks that might occur will affect the functioning process
of the business management process in a better manner. This is one of the main
reason that better understanding of the scenario. This proper underhanging of the
scenario helps in better understanding of the long term issues that might arise
(Laplante, 2017). This process is performed with the help of constant monitoring of
the business case.
This process of recruiting a CSISO will help in bettering of the strength of the in
house team (Braude & Bernstein, 2016). This increasing of the strength of the in-
house team will incur the fact that development of strategic and responsibilities as
per the commencing of the data organization scheme as this the reason that proper
management and mentoring of the staffs will be performed (Molléri, Mendes &
Petersen, 2019). This is the main reason that the level C employees were not very
pleased with the recruitment process of the Chief Security Information security
officer. Additional training can also be provided by them. The in house team work
load also gets diverted and work load balance increases (Butler, Howard& Green,
2018).
The tasks that are handled by the CSISO includes the functioning of the setting of
the directing privacy and security policies (Marseu, Kolberg & Birtel, 2016).
Another characteristic that is taken into thought includes the fact that managing of
the information security team is responsible for the processing of the executive
management (Schmitz, Mahapatra & Nerur, 2018). Running of risk assessment as
per the operational security has been one of the major aspect that provides better
understanding of the enterprise security measures that are needed for increasing the
robustness of the platform.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

7RISK MANAGEMENT
References
Zambonelli, F. (2016). Towards a general software engineering methodology for the Internet
of Things. arXiv preprint arXiv:1601.05569.
González, A. G., Ríos, A. S., García, C. J. C., & Salgado, D. R. (2018). A proposed
methodology to evaluate educational competences in engineering degrees based on
electronic devices and open access software. The International journal of engineering
education, 34(4), 1150-1158.
Brooks, A., Wells, K., Pratt, M., & Clarke, M. (2017). WoeCatheretic: A Methodology for
the Visualization of Component-Based. Software engineering and CS Journal, 12(1).
Laplante, P. A. (2017). Requirements engineering for software and systems. Auerbach
Publications.
Molléri, J. S., Mendes, E., Petersen, K., & Felderer, M. (2019). Aligning the Views of
Research Quality in Empirical Software Engineering. ACM Transactions on Software
Engineering and Methodology.
Marseu, E., Kolberg, D., Birtel, M., & Zühlke, D. (2016). Interdisciplinary engineering
methodology for changeable cyber-physical production systems. IFAC-
PapersOnLine, 49(31), 85-90.
Schmitz, K., Mahapatra, R., & Nerur, S. (2018). User engagement in the era of hybrid agile
methodology. IEEE Software.
Braude, E. J., & Bernstein, M. E. (2016). Software engineering: modern approaches.
Waveland Press.
Butler, J., Howard, D., & Green, D. (2018). A Methodology for the Visualization of Sensor
Networks. Software engineering and CS Journal, 11(1).
Hindle, A. (2016, March). Green software engineering: the curse of methodology. In 2016
IEEE 23rd International Conference on Software Analysis, Evolution, and
Reengineering (SANER) (Vol. 5, pp. 46-55). IEEE.
Garousi, V., Felderer, M., & Mäntylä, M. V. (2016, June). The need for multivocal literature
reviews in software engineering: complementing systematic literature reviews with
grey literature. In Proceedings of the 20th international conference on evaluation and
assessment in software engineering (p. 26). ACM.
Gonzalez, C., & Liñan, E. (2019, March). A Software Engineering Methodology for
Developing Secure Obfuscated Software. In Future of Information and
Communication Conference (pp. 1069-1078). Springer, Cham.
References
Zambonelli, F. (2016). Towards a general software engineering methodology for the Internet
of Things. arXiv preprint arXiv:1601.05569.
González, A. G., Ríos, A. S., García, C. J. C., & Salgado, D. R. (2018). A proposed
methodology to evaluate educational competences in engineering degrees based on
electronic devices and open access software. The International journal of engineering
education, 34(4), 1150-1158.
Brooks, A., Wells, K., Pratt, M., & Clarke, M. (2017). WoeCatheretic: A Methodology for
the Visualization of Component-Based. Software engineering and CS Journal, 12(1).
Laplante, P. A. (2017). Requirements engineering for software and systems. Auerbach
Publications.
Molléri, J. S., Mendes, E., Petersen, K., & Felderer, M. (2019). Aligning the Views of
Research Quality in Empirical Software Engineering. ACM Transactions on Software
Engineering and Methodology.
Marseu, E., Kolberg, D., Birtel, M., & Zühlke, D. (2016). Interdisciplinary engineering
methodology for changeable cyber-physical production systems. IFAC-
PapersOnLine, 49(31), 85-90.
Schmitz, K., Mahapatra, R., & Nerur, S. (2018). User engagement in the era of hybrid agile
methodology. IEEE Software.
Braude, E. J., & Bernstein, M. E. (2016). Software engineering: modern approaches.
Waveland Press.
Butler, J., Howard, D., & Green, D. (2018). A Methodology for the Visualization of Sensor
Networks. Software engineering and CS Journal, 11(1).
Hindle, A. (2016, March). Green software engineering: the curse of methodology. In 2016
IEEE 23rd International Conference on Software Analysis, Evolution, and
Reengineering (SANER) (Vol. 5, pp. 46-55). IEEE.
Garousi, V., Felderer, M., & Mäntylä, M. V. (2016, June). The need for multivocal literature
reviews in software engineering: complementing systematic literature reviews with
grey literature. In Proceedings of the 20th international conference on evaluation and
assessment in software engineering (p. 26). ACM.
Gonzalez, C., & Liñan, E. (2019, March). A Software Engineering Methodology for
Developing Secure Obfuscated Software. In Future of Information and
Communication Conference (pp. 1069-1078). Springer, Cham.
1 out of 8
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





