Evolution, Implications, and Future of Australian Cyber Security Laws
VerifiedAdded on 2022/08/16
|22
|6363
|15
Essay
AI Summary
This essay provides a comprehensive analysis of cyber security laws and regulations in Australia. It begins with an introduction to the growing threats in the field of IT, such as viruses, and the need for security measures like firewalls and encryption. The essay then delves into the evolutionary trends of cyber security laws, covering past legislation like the Privacy Act 1988, Telecommunications Act, Spam Act 2003, and Do Not Call Register Act 2006, detailing their impact on various sectors. The current state of cyber security laws, including the Criminal Code Act 1995 and Computer Misuse Act, is examined, along with the challenges posed by decentralized computer networking and social media. The essay also discusses the future of cyber security in Australia, highlighting the role of AI and emerging technologies, and the implications of these trends on the global landscape. It concludes by emphasizing the need for continuous revision and modification of cyber security laws to effectively address the evolving threats and protect both commercial establishments and society.

Running head: CYBER SECURITY LAWS AND REGULATION
Cyber Security Laws and Regulation
Cyber Security Laws and Regulation
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

1CYBER SECURITY LAWS AND REGULATION
Introduction
The extensive development in the field of IT has led to the growth and development
of numerous issues like viruses, worms, DoS attacks and phishing emails (Austin and Slay
2016). Numerous measures are required to be taken to deal with the threats coming from each
of these issues. To address these issues there are few security steps which are usually taken
such as the advanced firewalls, anti-virus software, diverse categories of intrusion detection
systems, different types of encryption techniques, use of complex and longer alphanumeric
passwords. These security steps are usually taken in most of the commercial establishments
all around the word to deal with these issues.
Cyber security laws are regulations are very much useful both in commercial
establishments as well as in our society. These regulations are very much useful to protect
any kinds of devices which are connected to an active internet connection. In Australia, each
of these issues falls under the category of Criminal Code Act of 1995 (Anwar Gill and
Beydoun 2018). Most of the spamming and the hacking activities related to cyber-crime is
related withy this code of jurisdiction. The maximum penalty for a contravention based on
this code is a maximum of 10 years of imprisonment. There are numerous clauses related
with this code as well such as the S.135.1 (5) and S.135.1 (3) (Lawcouncil.asn.au. 2020).
Along with these clauses there are numerous divisions related with this clause as well such
division 372 which is focussed in any identify fraudulent activities related to cyber-crime.
Previously the Crimes Act 1900 (Cth) helped the Australians to maintain law and order on
their soil.
Individual essay is defined as the type of essay which is very much coherent and well
organized in nature (Askari 2018). This essay shall focus on numerous aspects such the
evolutionary trends of the cyber security laws and regulations in Australia over the years, the
Introduction
The extensive development in the field of IT has led to the growth and development
of numerous issues like viruses, worms, DoS attacks and phishing emails (Austin and Slay
2016). Numerous measures are required to be taken to deal with the threats coming from each
of these issues. To address these issues there are few security steps which are usually taken
such as the advanced firewalls, anti-virus software, diverse categories of intrusion detection
systems, different types of encryption techniques, use of complex and longer alphanumeric
passwords. These security steps are usually taken in most of the commercial establishments
all around the word to deal with these issues.
Cyber security laws are regulations are very much useful both in commercial
establishments as well as in our society. These regulations are very much useful to protect
any kinds of devices which are connected to an active internet connection. In Australia, each
of these issues falls under the category of Criminal Code Act of 1995 (Anwar Gill and
Beydoun 2018). Most of the spamming and the hacking activities related to cyber-crime is
related withy this code of jurisdiction. The maximum penalty for a contravention based on
this code is a maximum of 10 years of imprisonment. There are numerous clauses related
with this code as well such as the S.135.1 (5) and S.135.1 (3) (Lawcouncil.asn.au. 2020).
Along with these clauses there are numerous divisions related with this clause as well such
division 372 which is focussed in any identify fraudulent activities related to cyber-crime.
Previously the Crimes Act 1900 (Cth) helped the Australians to maintain law and order on
their soil.
Individual essay is defined as the type of essay which is very much coherent and well
organized in nature (Askari 2018). This essay shall focus on numerous aspects such the
evolutionary trends of the cyber security laws and regulations in Australia over the years, the

2CYBER SECURITY LAWS AND REGULATION
consequence of each of these trends shall be discussed in this individual essay as well.
Present and the future implications of each of these security laws shall be evaluated and
discussed in this individual essay.
Cyber criminals and hackers are using new methods in each of their cyber security
activities thus, it can be suggested that these security laws has be revised and modified on a
regular interval so that the impact of these issues do not have an adverse impact on our
society and in commercial organizations (Anwar, Gill and Beydoun 2018). The changes
required in the security laws shall be recommended in the conclusive unit of this individual
essay in an organized manner.
Evolutionary view of the trend (past, current and future)
Past
Privacy Act 1988: The Australian Privacy Principles (APP) are one of the most
significant ways which will be maintained in Australia to address the threats of disclosure of
personal information, addressing the threats of an agency’s governance and accountability,
maintain the integrity of the personal information, issues related with data access. Numerous
regulatory actions are required to be taken in the future in order to deal with the increasing
number of cyber security incidents. APP is an integral part of the Privacy Act 1988
(Aph.gov.au. 2020). Most of the commercial establishments of Australia are secured with the
help of this privacy act. Numerous data which revolves around the commercial
establishments of Australia such as the tax file numbers, health and medical research and
credit reporting systems. Each of these essential documents was secured with the help of this
privacy act.
Telecommunications Act Australia: There are numerous surveillance devices which
are increasingly used in the healthcare organisations and military operations. As a result
consequence of each of these trends shall be discussed in this individual essay as well.
Present and the future implications of each of these security laws shall be evaluated and
discussed in this individual essay.
Cyber criminals and hackers are using new methods in each of their cyber security
activities thus, it can be suggested that these security laws has be revised and modified on a
regular interval so that the impact of these issues do not have an adverse impact on our
society and in commercial organizations (Anwar, Gill and Beydoun 2018). The changes
required in the security laws shall be recommended in the conclusive unit of this individual
essay in an organized manner.
Evolutionary view of the trend (past, current and future)
Past
Privacy Act 1988: The Australian Privacy Principles (APP) are one of the most
significant ways which will be maintained in Australia to address the threats of disclosure of
personal information, addressing the threats of an agency’s governance and accountability,
maintain the integrity of the personal information, issues related with data access. Numerous
regulatory actions are required to be taken in the future in order to deal with the increasing
number of cyber security incidents. APP is an integral part of the Privacy Act 1988
(Aph.gov.au. 2020). Most of the commercial establishments of Australia are secured with the
help of this privacy act. Numerous data which revolves around the commercial
establishments of Australia such as the tax file numbers, health and medical research and
credit reporting systems. Each of these essential documents was secured with the help of this
privacy act.
Telecommunications Act Australia: There are numerous surveillance devices which
are increasingly used in the healthcare organisations and military operations. As a result
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

3CYBER SECURITY LAWS AND REGULATION
maintaining security of these devices is very much critical for the growth and development of
these industries. Security issues of the tele-communication sector was having a huge impact
on the other industries of Australia, the establishment of this act was very much useful to
maintain security of the data which are accessed with the help of the Telecommunications
Act (Cyber.gov.au. 2020).
Spam act 2003 Australia: The threats coming from the electronic messages were a
huge source of concern for the Australians as it was having a direct impact on the
development of the Australian economy (Australia.gov.au. 2020). The civil penalty options
were not at all very much useful to deal with the fraudulent activities which were conducted
through the electronic messages. There are numerous provisions related to this act as well in
terms of the subsections like subsection 16(1), (6) and (9). This act was very much
successful as compared with the other cyber security acts as it helped in preventing
spamming activities in most of the healthcare industries and IT industries. Transparency of
the online procurement process was maintained after this legislation was successfully
incorporated in the Australian society.
Do Not Call Register Act 2006: In the early 2000, there were numerous cyber
security incidents in the Australian soil and to address the threats coming from these incidents
this act was established in the year 2006 (Phys.org. 2020). Threats coming from the
telemarketing calls of the spammers were a huge source of concern for the Australians and
after the establishment of this act this criminal activity was minimised to a huge extent.
Threats coming from the unsolicited marketing faxes were also minimised with the help of
this act. The threats coming from the overseas based tele-commuters to help solicit sales were
partially disrupted due to this legislation. Consumer forums were created where each of these
fraudulent activities are reported was created after the legislation was formed.
maintaining security of these devices is very much critical for the growth and development of
these industries. Security issues of the tele-communication sector was having a huge impact
on the other industries of Australia, the establishment of this act was very much useful to
maintain security of the data which are accessed with the help of the Telecommunications
Act (Cyber.gov.au. 2020).
Spam act 2003 Australia: The threats coming from the electronic messages were a
huge source of concern for the Australians as it was having a direct impact on the
development of the Australian economy (Australia.gov.au. 2020). The civil penalty options
were not at all very much useful to deal with the fraudulent activities which were conducted
through the electronic messages. There are numerous provisions related to this act as well in
terms of the subsections like subsection 16(1), (6) and (9). This act was very much
successful as compared with the other cyber security acts as it helped in preventing
spamming activities in most of the healthcare industries and IT industries. Transparency of
the online procurement process was maintained after this legislation was successfully
incorporated in the Australian society.
Do Not Call Register Act 2006: In the early 2000, there were numerous cyber
security incidents in the Australian soil and to address the threats coming from these incidents
this act was established in the year 2006 (Phys.org. 2020). Threats coming from the
telemarketing calls of the spammers were a huge source of concern for the Australians and
after the establishment of this act this criminal activity was minimised to a huge extent.
Threats coming from the unsolicited marketing faxes were also minimised with the help of
this act. The threats coming from the overseas based tele-commuters to help solicit sales were
partially disrupted due to this legislation. Consumer forums were created where each of these
fraudulent activities are reported was created after the legislation was formed.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
4CYBER SECURITY LAWS AND REGULATION
Federal Information Security Management Act (FISMA): This security act was
helpful to minimise with the data security issues of the commercial establishments of
Australia (Mann et al. 2018). The protection programs of each organization are very much
useful to minimise the security threats coming from the cyber criminals. Thus, it can be said
that the security of each of these sensitive documents was secured to a huge extent after the
establishment of this law in the year 2002.
Current
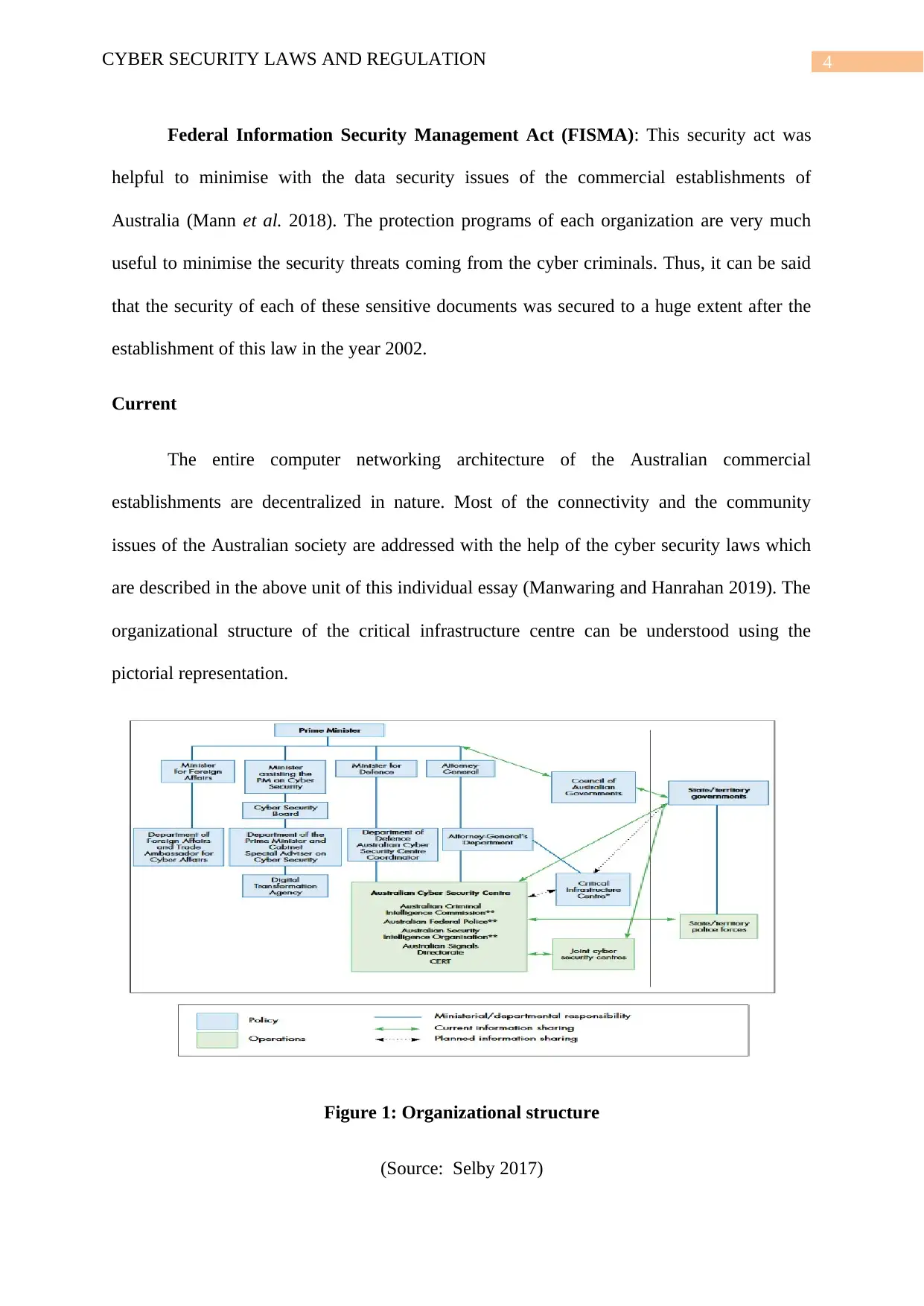
The entire computer networking architecture of the Australian commercial
establishments are decentralized in nature. Most of the connectivity and the community
issues of the Australian society are addressed with the help of the cyber security laws which
are described in the above unit of this individual essay (Manwaring and Hanrahan 2019). The
organizational structure of the critical infrastructure centre can be understood using the
pictorial representation.
Figure 1: Organizational structure
(Source: Selby 2017)
Federal Information Security Management Act (FISMA): This security act was
helpful to minimise with the data security issues of the commercial establishments of
Australia (Mann et al. 2018). The protection programs of each organization are very much
useful to minimise the security threats coming from the cyber criminals. Thus, it can be said
that the security of each of these sensitive documents was secured to a huge extent after the
establishment of this law in the year 2002.
Current
The entire computer networking architecture of the Australian commercial
establishments are decentralized in nature. Most of the connectivity and the community
issues of the Australian society are addressed with the help of the cyber security laws which
are described in the above unit of this individual essay (Manwaring and Hanrahan 2019). The
organizational structure of the critical infrastructure centre can be understood using the
pictorial representation.
Figure 1: Organizational structure
(Source: Selby 2017)

5CYBER SECURITY LAWS AND REGULATION
There are diverse categories of cyber security challenges which are faced by the
Australian citizens due to the deployment of the social media platforms. New vulnerabilities
are getting cropping up in the last few years such as the SQL injection attacks and the crypto
jacking attacks (Porcedda 2018). Each of these attacks ate having a direct impact on the
productivity of commercial organizations in the Australian soil.
Criminal Code Act 1995: It is one of the most significant codes which exist in the
Australian soil to address the security challenges which are being faced in the physical IT
systems which are used in commercial establishments for different purposes. This code is
very much useful to deal with the criminal activities related with misuse of information. The
threats of the public administration offices were restricted to a huge extent with the help of
this act ((Pandey et al. 2016). There are diverse categories offences which were saved after
the establishment of the criminal code act such as the hybrid offences, indictable offences,
and conviction offences. The impact of the issues related with negligence was also minimized
with the help of this code. Thus, it can be said that the basic value of the society was restored
with the help the help of this act as well.
Computer Misuse Act: Established in the year 1990, this law is very much useful to
manage the networking security of an organization (Brevini 2017). Most of the unauthorized
access in an organizational network can be avoided in the first place with the help of this act.
This act is also very much useful for protection the confidential information which travels
across the business unit of the commercial establishments of Australia. Based on this act,
different types of fines are enacted for the criminals. The national security of this country was
enhanced after the establishment of this law as well. Most of the illegal activities of a
commercial business organization such as the data alteration is being minimised with the help
of this code.
There are diverse categories of cyber security challenges which are faced by the
Australian citizens due to the deployment of the social media platforms. New vulnerabilities
are getting cropping up in the last few years such as the SQL injection attacks and the crypto
jacking attacks (Porcedda 2018). Each of these attacks ate having a direct impact on the
productivity of commercial organizations in the Australian soil.
Criminal Code Act 1995: It is one of the most significant codes which exist in the
Australian soil to address the security challenges which are being faced in the physical IT
systems which are used in commercial establishments for different purposes. This code is
very much useful to deal with the criminal activities related with misuse of information. The
threats of the public administration offices were restricted to a huge extent with the help of
this act ((Pandey et al. 2016). There are diverse categories offences which were saved after
the establishment of the criminal code act such as the hybrid offences, indictable offences,
and conviction offences. The impact of the issues related with negligence was also minimized
with the help of this code. Thus, it can be said that the basic value of the society was restored
with the help the help of this act as well.
Computer Misuse Act: Established in the year 1990, this law is very much useful to
manage the networking security of an organization (Brevini 2017). Most of the unauthorized
access in an organizational network can be avoided in the first place with the help of this act.
This act is also very much useful for protection the confidential information which travels
across the business unit of the commercial establishments of Australia. Based on this act,
different types of fines are enacted for the criminals. The national security of this country was
enhanced after the establishment of this law as well. Most of the illegal activities of a
commercial business organization such as the data alteration is being minimised with the help
of this code.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

6CYBER SECURITY LAWS AND REGULATION
There are diverse of computer misuses such as the hacking activities, data misuse,
maintaining the copyright of the software or any other project, pornographic contents,
identify and financial abuses and viruses (Chang, Zhong and Grabosky 2018). Each of these
computer misuses can be minimised using this code. Misuse of devices is also getting
addressed using this code as well.
Most of the criminal activities of the cyber-criminals are getting minimized in the first
place with the help of this criminal code as well (Coventry and Branley 2018). The inter
locking regime was also maintained with the help of this computer security laws. The
percentage of the number of actors related with the anti-cyber-crime activities can be
understood from the below pictorial representation.
Figure 2: Actors supporting anti cyber crime
(Source: Broadhurst 2017)
Future
The future of cyber security is very much on the higher side in Australia as the
government of Australia are investing millions of dollars to enhance the network (Aldawood
and Skinner 2018). New IT experts are getting hired in each every government offices as a
result the networking security of these organizations are getting enhanced each and every
day. Response management team is very much significant to deal with the cyber security
issues.
There are diverse of computer misuses such as the hacking activities, data misuse,
maintaining the copyright of the software or any other project, pornographic contents,
identify and financial abuses and viruses (Chang, Zhong and Grabosky 2018). Each of these
computer misuses can be minimised using this code. Misuse of devices is also getting
addressed using this code as well.
Most of the criminal activities of the cyber-criminals are getting minimized in the first
place with the help of this criminal code as well (Coventry and Branley 2018). The inter
locking regime was also maintained with the help of this computer security laws. The
percentage of the number of actors related with the anti-cyber-crime activities can be
understood from the below pictorial representation.
Figure 2: Actors supporting anti cyber crime
(Source: Broadhurst 2017)
Future
The future of cyber security is very much on the higher side in Australia as the
government of Australia are investing millions of dollars to enhance the network (Aldawood
and Skinner 2018). New IT experts are getting hired in each every government offices as a
result the networking security of these organizations are getting enhanced each and every
day. Response management team is very much significant to deal with the cyber security
issues.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

7CYBER SECURITY LAWS AND REGULATION
Numerous emerging technologies are being used to deal with the cyber security
threats coming from the spammers (Quisumbing 2017). IT security policies are getting
incorporated in commercial business organizations to deal with the threats coming from
inside the commercial establishments.
Australian investigative department and agencies are very much capable to deal with
most of the online security threats such as the spamming emails. Artificial Intelligence is
going to be one of the most popular technologies in most of the commercial business
establishments all around Australia. This technology shall not only help to enhance and
support the existing cyber security laws but shall also help the governing councils to create
new cyber security laws and cyber warfare (Abu-Taieh 2017). Technologies like AI can also
help Australia to make decision of the International treaties. Thus, it can be assumed that
most of the computer related time can be minimised with the help of AI as well.
The incorporation of the emerging technologies such as AI can be very much useful to
cost of managing the cybercrimes (AM Slay 2016). Most of the micro level attacks of
Australia can be avoided in the first place with the help of these technologies. In the future,
most of the cyber-attack technologies are expected to enhance the quality of the business
operations military operations. Financial gain is one of the most significant future prospects
of the different categories of cyber security laws.
Cyber security opening is one of the other positive relayed with the cyber security
laws which exists in Australia (Mackey and Nayyar 2016). Thus, it can be said that the
productivity of the cyber warfare department and digital forensics departments of Australia
has to be enhanced with the help of these cyber security laws and cyber-attack technologies.
Implication of the trend to the world that we live in:
Numerous emerging technologies are being used to deal with the cyber security
threats coming from the spammers (Quisumbing 2017). IT security policies are getting
incorporated in commercial business organizations to deal with the threats coming from
inside the commercial establishments.
Australian investigative department and agencies are very much capable to deal with
most of the online security threats such as the spamming emails. Artificial Intelligence is
going to be one of the most popular technologies in most of the commercial business
establishments all around Australia. This technology shall not only help to enhance and
support the existing cyber security laws but shall also help the governing councils to create
new cyber security laws and cyber warfare (Abu-Taieh 2017). Technologies like AI can also
help Australia to make decision of the International treaties. Thus, it can be assumed that
most of the computer related time can be minimised with the help of AI as well.
The incorporation of the emerging technologies such as AI can be very much useful to
cost of managing the cybercrimes (AM Slay 2016). Most of the micro level attacks of
Australia can be avoided in the first place with the help of these technologies. In the future,
most of the cyber-attack technologies are expected to enhance the quality of the business
operations military operations. Financial gain is one of the most significant future prospects
of the different categories of cyber security laws.
Cyber security opening is one of the other positive relayed with the cyber security
laws which exists in Australia (Mackey and Nayyar 2016). Thus, it can be said that the
productivity of the cyber warfare department and digital forensics departments of Australia
has to be enhanced with the help of these cyber security laws and cyber-attack technologies.
Implication of the trend to the world that we live in:

8CYBER SECURITY LAWS AND REGULATION
In 2016, more than 10000 cyber-crimes was recorded in Australia and there were
more than 1 million cases which were recorded based on the cyber security threats. Security
breaches are getting observed in most of the SMEs (Quisumbing 2017). Australian
Cybercrime Online Reporting Network is currently working hard on the ways to improve
the ways to improve the risk identification procedures which are adopted by most of the
commercial establishments all over Australia.
The needs and requirements of our society as well as the commercial business
establishments keep on changing every moment. New technologies and business practices
are getting introduced in most of the contemporary business establishments. Every aspect of
the society is now related with different types of computer systems which are connected with
active internet connection. The productivity of each of the diverse categories of industries is
getting enhanced due to the improvement of the data management capability of business
organizations (Shackelford, Russell and Kuehn 2016). As a result of using diverse categories
of systems, there is a direct threat coming from both the users of the systems as well as
from the cyber criminals.
The cyber security skills gap is also one of the major limitations of most of the
Australian commercial establishments who are trying to make their mark outside Australia
(AM Slay 2016). Most of these commercial establishments make the most out of the cloud
computing services as they want to store and manage their essential business documents and
there is numerous security concerns related with the use of cloud computing as well.
Integration and Automation are the other cyber security trends related with most of the
commercial establishments. Growing awareness of the cyber security is one of the other
cyber security trends in the last two years. State sponsored cyber-attacks are one of the other
current trends of the cyber security as well. At the same time, it can also be decided that there
In 2016, more than 10000 cyber-crimes was recorded in Australia and there were
more than 1 million cases which were recorded based on the cyber security threats. Security
breaches are getting observed in most of the SMEs (Quisumbing 2017). Australian
Cybercrime Online Reporting Network is currently working hard on the ways to improve
the ways to improve the risk identification procedures which are adopted by most of the
commercial establishments all over Australia.
The needs and requirements of our society as well as the commercial business
establishments keep on changing every moment. New technologies and business practices
are getting introduced in most of the contemporary business establishments. Every aspect of
the society is now related with different types of computer systems which are connected with
active internet connection. The productivity of each of the diverse categories of industries is
getting enhanced due to the improvement of the data management capability of business
organizations (Shackelford, Russell and Kuehn 2016). As a result of using diverse categories
of systems, there is a direct threat coming from both the users of the systems as well as
from the cyber criminals.
The cyber security skills gap is also one of the major limitations of most of the
Australian commercial establishments who are trying to make their mark outside Australia
(AM Slay 2016). Most of these commercial establishments make the most out of the cloud
computing services as they want to store and manage their essential business documents and
there is numerous security concerns related with the use of cloud computing as well.
Integration and Automation are the other cyber security trends related with most of the
commercial establishments. Growing awareness of the cyber security is one of the other
cyber security trends in the last two years. State sponsored cyber-attacks are one of the other
current trends of the cyber security as well. At the same time, it can also be decided that there
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

9CYBER SECURITY LAWS AND REGULATION
are diverse categories of risks related with the use of IT systems which optimises business
operations.
Based on the current trends, it can be saved that there are numerous cyber security
vulnerabilities related with most of the commercial business organizations such as the threat
coming from inside the organization as well as from the diverse categories of cyber security
threats such as ransomware. Thus, securing the network security vulnerabilities is one of the
recent trends related with the cyber security laws which are practised in the Australian
conditions (Min, Chai and Han 2015). Having a better security is one of the prime trends
which is being followed in most of the commercial establishments all around Australia due to
the threats coming from the Korean and Japanese hackers.
Numerous manufacturing industries are making the most out of the cyber security
programs to optimise different business operations. Cost of maintenance of services has
drastically reduced after the deployments of numerous Information Security policies (Kshetri
2015). There are numerous data security threats like data alteration and data
encapsulation, which can be minimised using Information Security policies as well. The data
collection procedure of the Australian organizations has enhanced a lot in the last five years
as compared to what it was in the mid-90s.
Current most of the social engineers all around the world are using diverse categories
of mobile devices as an attack vector (Persadha, Waskita and Yazid 2015). Most of the
business communications are managed in the first place with the help of these mobile
devices, thus it is very much easier for the cyber criminals to compromise the data from these
mobile devices.
There are numerous legal complication related with the role of the government when
a cyber-security attack occurs. Currently, most of the ransomware attacks come from the
are diverse categories of risks related with the use of IT systems which optimises business
operations.
Based on the current trends, it can be saved that there are numerous cyber security
vulnerabilities related with most of the commercial business organizations such as the threat
coming from inside the organization as well as from the diverse categories of cyber security
threats such as ransomware. Thus, securing the network security vulnerabilities is one of the
recent trends related with the cyber security laws which are practised in the Australian
conditions (Min, Chai and Han 2015). Having a better security is one of the prime trends
which is being followed in most of the commercial establishments all around Australia due to
the threats coming from the Korean and Japanese hackers.
Numerous manufacturing industries are making the most out of the cyber security
programs to optimise different business operations. Cost of maintenance of services has
drastically reduced after the deployments of numerous Information Security policies (Kshetri
2015). There are numerous data security threats like data alteration and data
encapsulation, which can be minimised using Information Security policies as well. The data
collection procedure of the Australian organizations has enhanced a lot in the last five years
as compared to what it was in the mid-90s.
Current most of the social engineers all around the world are using diverse categories
of mobile devices as an attack vector (Persadha, Waskita and Yazid 2015). Most of the
business communications are managed in the first place with the help of these mobile
devices, thus it is very much easier for the cyber criminals to compromise the data from these
mobile devices.
There are numerous legal complication related with the role of the government when
a cyber-security attack occurs. Currently, most of the ransomware attacks come from the
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

10CYBER SECURITY LAWS AND REGULATION
malware bytes. Presently, most of the commercial establishments are creating new data
privacy policies to make sure that there are no real threats coming from the employees of an
organization (Slay and Austin 2018). Maintaining the privacy standards is very much useful
to identify the exact network vulnerability. Uses of latest encryption techniques are also very
much useful to restrict issues like data alteration, as this phenomenon has a direct impact on
the market reputation of commercial establishments.
Recently, numerous new technologies are being created in the IT laboratories of
Australia to deal with the cyber security issues like DevSecOps (Mikolic-Torreira et al.
2017). This software is beneficial to address cloud security issues related with most of the
commercial establishments of Australia. The collaboration of the engineers of a commercial
establishment and security teams is getting enhanced due to the use of DevSecOps.
Considering the most recent trends, it can be said that ransomware attacks of 2019
was very much different this this attack which was carried out in the previous years. In 2019,
most of the social engineers set a target or a specific business; as a result the cyber attackers
can cause maximum business disruption. Thus, huge amount of money in the bit coins are
taken from the victims.
Nowadays, phishing mail attacks can also be conducted with the help of an email
account, new attack vectors were identified by the social engineers all around the world
which can be useful tom extract any type of sensitive data (Kenderdine 2017). SMS texts are
used by the social engineers to spread this cyber security attack. The use of the diverse
categories of online social platforms like Facebook can also lead to a phishing attack as well.
The use of the mobile banking malware have increased over the years, the availability
of the malware developers is one of the notable reasons behind the over use of this virus.
Multi vector generation V cyber-attacks are also one of the trending topics which are related
malware bytes. Presently, most of the commercial establishments are creating new data
privacy policies to make sure that there are no real threats coming from the employees of an
organization (Slay and Austin 2018). Maintaining the privacy standards is very much useful
to identify the exact network vulnerability. Uses of latest encryption techniques are also very
much useful to restrict issues like data alteration, as this phenomenon has a direct impact on
the market reputation of commercial establishments.
Recently, numerous new technologies are being created in the IT laboratories of
Australia to deal with the cyber security issues like DevSecOps (Mikolic-Torreira et al.
2017). This software is beneficial to address cloud security issues related with most of the
commercial establishments of Australia. The collaboration of the engineers of a commercial
establishment and security teams is getting enhanced due to the use of DevSecOps.
Considering the most recent trends, it can be said that ransomware attacks of 2019
was very much different this this attack which was carried out in the previous years. In 2019,
most of the social engineers set a target or a specific business; as a result the cyber attackers
can cause maximum business disruption. Thus, huge amount of money in the bit coins are
taken from the victims.
Nowadays, phishing mail attacks can also be conducted with the help of an email
account, new attack vectors were identified by the social engineers all around the world
which can be useful tom extract any type of sensitive data (Kenderdine 2017). SMS texts are
used by the social engineers to spread this cyber security attack. The use of the diverse
categories of online social platforms like Facebook can also lead to a phishing attack as well.
The use of the mobile banking malware have increased over the years, the availability
of the malware developers is one of the notable reasons behind the over use of this virus.
Multi vector generation V cyber-attacks are also one of the trending topics which are related

11CYBER SECURITY LAWS AND REGULATION
with most of the IoT devices which are either used in a corporate establishment or in a
society (Botton and Lee-Makiyama 2018). Inspite of taking numerous holistic approaches
these threats is a huge source of concern for both the citizens of our society as well as for the
employees of commercial establishments.
Most of the cyber criminals are using AI to identify the networking vulnerabilities and
the ways which will be most feasible for them to compromise a network. Development of
evasive software is supported from this technology as well. Based on the current cyber
security trends, it can be said that traditional pen testing has become obsolete due to the
creation of better attack simulation technologies by the social engineers. The risk of the micro
breaches has increased considerable due to the cyber security activities such as the
gamification, document hunt and bug bounty.
Application of legal and legislative considerations
What is yet to happen?
The level of connectivity among each of the commercial business organizations is
expected to get enhanced due to the cyber security laws. Each of the diverse categories of
laws is expected to be very much useful for organizations to deal with the networking threats
and the legal problems faced due to the cyber security threats. Based on the current trends, it
can be said that human behaviour is also expected to get tracked with the help of the cyber
security laws as well (Sabillon, Cavaller and Cano 2016). The global reach of most of the
reputed Australian commercial establishments is also expected to get enhanced due to the
cyber security laws. The productivity of the investigative departments of commercial
establishments is also expected to enhance due to the current trends of cyber security
programs.
with most of the IoT devices which are either used in a corporate establishment or in a
society (Botton and Lee-Makiyama 2018). Inspite of taking numerous holistic approaches
these threats is a huge source of concern for both the citizens of our society as well as for the
employees of commercial establishments.
Most of the cyber criminals are using AI to identify the networking vulnerabilities and
the ways which will be most feasible for them to compromise a network. Development of
evasive software is supported from this technology as well. Based on the current cyber
security trends, it can be said that traditional pen testing has become obsolete due to the
creation of better attack simulation technologies by the social engineers. The risk of the micro
breaches has increased considerable due to the cyber security activities such as the
gamification, document hunt and bug bounty.
Application of legal and legislative considerations
What is yet to happen?
The level of connectivity among each of the commercial business organizations is
expected to get enhanced due to the cyber security laws. Each of the diverse categories of
laws is expected to be very much useful for organizations to deal with the networking threats
and the legal problems faced due to the cyber security threats. Based on the current trends, it
can be said that human behaviour is also expected to get tracked with the help of the cyber
security laws as well (Sabillon, Cavaller and Cano 2016). The global reach of most of the
reputed Australian commercial establishments is also expected to get enhanced due to the
cyber security laws. The productivity of the investigative departments of commercial
establishments is also expected to enhance due to the current trends of cyber security
programs.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 22
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.
