Cloud Privacy and Security: Threats and Risks in Australian DAS
VerifiedAdded on 2020/03/01
|17
|3601
|222
Report
AI Summary
This report addresses cloud privacy and security concerns within the Australian Department of Administrative Services (DAS), focusing on the implementation of SaaS applications. It begins with an executive summary and table of contents, then introduces cloud computing and its deployment models, highlighting the risks and security threats in the DAS. The report distinguishes between SaaS cloud services and DAS services, exploring security risks such as excessive privileges, privilege abuse, input injection in the database, and malware. It also examines security challenges after implementing SaaS applications, including employee data security, privacy, digital identity issues, provider solution issues, and data sensitivity. Furthermore, the report delves into the security and risks associated with SaaS applications and the privacy of employee data within them. It analyzes the threats and risks to digital identities of government employees transitioning to SaaS applications and concludes with an overview of operational solutions using SaaS applications. The report emphasizes the importance of data privacy, security protocols, and the potential for cyber-attacks, providing a comprehensive analysis of cloud security in the context of the Australian government's administrative services.

Running head: CLOUD PRIVACY AND SECURITY
Cloud Privacy and Security
Name of the Student
Name of the University
Author’s Note
Cloud Privacy and Security
Name of the Student
Name of the University
Author’s Note
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

1
CLOUD PRIVACY AND SECURITY
Executive Summary
This report deals with the security threat and risks evolving in the Australian Stare government
with the implication of DAS in the scenario. The shared approach of the DAS has created
different security risks and threats to the government. There are various jurisdiction and laws
against the data loss has been mentioned in the report. There are various security risks and
threats are discussed in the report.
CLOUD PRIVACY AND SECURITY
Executive Summary
This report deals with the security threat and risks evolving in the Australian Stare government
with the implication of DAS in the scenario. The shared approach of the DAS has created
different security risks and threats to the government. There are various jurisdiction and laws
against the data loss has been mentioned in the report. There are various security risks and
threats are discussed in the report.

2
CLOUD PRIVACY AND SECURITY
Table of Contents
Introduction......................................................................................................................................3
The Department of Administrative Services (DAS)........................................................................3
Security risk and threats in data and information in DAS...............................................................4
Other security risks after implementing SaaS application...............................................................5
Privacy of the Employee Data.....................................................................................................6
Digital Identity Issue....................................................................................................................7
Provider Solution Issue................................................................................................................7
Data Sensitivity............................................................................................................................7
Security and risks in the SaaS application.......................................................................................8
Privacy of employee data in SaaS application.............................................................................9
Threats and risks to digital identities of Government employees from the move to SaaS
applications....................................................................................................................................11
Operational Solution using SaaS application................................................................................12
Conclusion.....................................................................................................................................13
References......................................................................................................................................14
CLOUD PRIVACY AND SECURITY
Table of Contents
Introduction......................................................................................................................................3
The Department of Administrative Services (DAS)........................................................................3
Security risk and threats in data and information in DAS...............................................................4
Other security risks after implementing SaaS application...............................................................5
Privacy of the Employee Data.....................................................................................................6
Digital Identity Issue....................................................................................................................7
Provider Solution Issue................................................................................................................7
Data Sensitivity............................................................................................................................7
Security and risks in the SaaS application.......................................................................................8
Privacy of employee data in SaaS application.............................................................................9
Threats and risks to digital identities of Government employees from the move to SaaS
applications....................................................................................................................................11
Operational Solution using SaaS application................................................................................12
Conclusion.....................................................................................................................................13
References......................................................................................................................................14
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

3
CLOUD PRIVACY AND SECURITY
Introduction
Cloud Computing is an emerging topic in the modern world of Internet Technology. It has
created many advancement in the market of technology. The deployment models of cloud
computing has provided risks and security in the business organization. There are different types
of applications are used in the cloud computing that helps in managing the risks and security
threat issues in the business organisation.
This report deals with the risks and threats in security of the data and information in the
Department of Administrative Services (DAS). There are various risks discussed in the report
after the implementation of the SaaS application in the DAS.
This report outlines the distinguishing factor between SaaS cloud services and DAS services.
This risks and threats involved are discussed in the report.
The Department of Administrative Services (DAS)
The Department of Administrative Services acts as an administrative body for providing help
and space to save financial funds and information of different companies in the market. The
Department of Administrative Services used to store various data related to the business
organisation in the market (Carver & Wolsey, 2015). The Department of Administrative Services
includes different accounts payable application, administrative management and payroll service
in the agreement. The use of DAS has helped in maintaining the data and security of the data in
the organisation. The financial stability of the companies are maintained by securing the data and
information regarding the financial data of the company (McNeil, Frey & Embrechts, 2015). The
DAS helps in controlling the accounts and budget and other procurement services in the
organisation.
CLOUD PRIVACY AND SECURITY
Introduction
Cloud Computing is an emerging topic in the modern world of Internet Technology. It has
created many advancement in the market of technology. The deployment models of cloud
computing has provided risks and security in the business organization. There are different types
of applications are used in the cloud computing that helps in managing the risks and security
threat issues in the business organisation.
This report deals with the risks and threats in security of the data and information in the
Department of Administrative Services (DAS). There are various risks discussed in the report
after the implementation of the SaaS application in the DAS.
This report outlines the distinguishing factor between SaaS cloud services and DAS services.
This risks and threats involved are discussed in the report.
The Department of Administrative Services (DAS)
The Department of Administrative Services acts as an administrative body for providing help
and space to save financial funds and information of different companies in the market. The
Department of Administrative Services used to store various data related to the business
organisation in the market (Carver & Wolsey, 2015). The Department of Administrative Services
includes different accounts payable application, administrative management and payroll service
in the agreement. The use of DAS has helped in maintaining the data and security of the data in
the organisation. The financial stability of the companies are maintained by securing the data and
information regarding the financial data of the company (McNeil, Frey & Embrechts, 2015). The
DAS helps in controlling the accounts and budget and other procurement services in the
organisation.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

4
CLOUD PRIVACY AND SECURITY
The shared approach of DAS controls the database of the Australian State government. This
approach has helped in maintaining a centralized database management system. The data and
information of the employee of government are stored in the centralized database. This helps in
accessing the database form anywhere in the state (Lam, 2014). The communication making
different employee have enhanced with this approach. The Australian Government has also
succeeded in providing consolidated services to the employee in the organisation. The shared
approach have maintained a distinctive approach towards the security of the data and
information.
Security risk and threats in data and information in DAS
There are various security risks availing in the shared approach implemented by the DAS in the
Australian State government. Some of the major risks are mentioned below:
Excessive privileges
The use of the centralised database system in the DAS has helped in enhancing the access to the
database of the company. Different users can access the data and information of the employee at
anytime. This has caused security risks in the company (Smith et al., 2015). The unauthorised
user can leak the data and information of the employee in the market. The payroll accounting
information of the employee can be lost due to data breaching in the database. Therefore, due to
excessive privileges employee are generic to access the database and causes data loss for the
company in the market. This can be very harmful for the company regarding the financial loss of
the company.
Privilege Abuse
CLOUD PRIVACY AND SECURITY
The shared approach of DAS controls the database of the Australian State government. This
approach has helped in maintaining a centralized database management system. The data and
information of the employee of government are stored in the centralized database. This helps in
accessing the database form anywhere in the state (Lam, 2014). The communication making
different employee have enhanced with this approach. The Australian Government has also
succeeded in providing consolidated services to the employee in the organisation. The shared
approach have maintained a distinctive approach towards the security of the data and
information.
Security risk and threats in data and information in DAS
There are various security risks availing in the shared approach implemented by the DAS in the
Australian State government. Some of the major risks are mentioned below:
Excessive privileges
The use of the centralised database system in the DAS has helped in enhancing the access to the
database of the company. Different users can access the data and information of the employee at
anytime. This has caused security risks in the company (Smith et al., 2015). The unauthorised
user can leak the data and information of the employee in the market. The payroll accounting
information of the employee can be lost due to data breaching in the database. Therefore, due to
excessive privileges employee are generic to access the database and causes data loss for the
company in the market. This can be very harmful for the company regarding the financial loss of
the company.
Privilege Abuse

5
CLOUD PRIVACY AND SECURITY
There are various legitimate issues in the databases that are identified with the shared approaches
of the DAS in the market. Many private information if the employee are stored in the database
that can be hacked and breached. The login credentials including user id and passwords are
stored in the database that might cause a big loss for the company (Neves et al., 2014). The other
employee and staffs might bad use the data and information of employee in the company. This
has caused privilege abuse of data and information of the employee.
Input Injection in Database
There are two types of database injection including NoSQL Injection and SQL Injection. The
SQL injection contains the unauthorised statement of the database caused during the input
session in web application (Koks et al., 2015). The NoSQL injection attacks can be done by
injecting malicious statements in the Big Data components. These attacks cause data breach from
the database.
Malware
There are different malwares and viruses that can be injected in the server and database to
track data and information stored in the database. Various viruses and malwares are used for
making phishing mails to breach data from database. These viruses and malwares can crash the
hardware causing full loss in data from database (DeMarco & Lister, 2013). The recovery of data
and information is a difficult process for the company to handle. Therefore, the malware attack is
a high-level risk for the database system in Department of Administrative Services.
Other security risks after implementing SaaS application
The security matter of the data and information in the database is a prime concern for the
company in the market. The DAS has implemented the SaaS application by observing the
CLOUD PRIVACY AND SECURITY
There are various legitimate issues in the databases that are identified with the shared approaches
of the DAS in the market. Many private information if the employee are stored in the database
that can be hacked and breached. The login credentials including user id and passwords are
stored in the database that might cause a big loss for the company (Neves et al., 2014). The other
employee and staffs might bad use the data and information of employee in the company. This
has caused privilege abuse of data and information of the employee.
Input Injection in Database
There are two types of database injection including NoSQL Injection and SQL Injection. The
SQL injection contains the unauthorised statement of the database caused during the input
session in web application (Koks et al., 2015). The NoSQL injection attacks can be done by
injecting malicious statements in the Big Data components. These attacks cause data breach from
the database.
Malware
There are different malwares and viruses that can be injected in the server and database to
track data and information stored in the database. Various viruses and malwares are used for
making phishing mails to breach data from database. These viruses and malwares can crash the
hardware causing full loss in data from database (DeMarco & Lister, 2013). The recovery of data
and information is a difficult process for the company to handle. Therefore, the malware attack is
a high-level risk for the database system in Department of Administrative Services.
Other security risks after implementing SaaS application
The security matter of the data and information in the database is a prime concern for the
company in the market. The DAS has implemented the SaaS application by observing the
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

6
CLOUD PRIVACY AND SECURITY
limitations in the Shared approach. The cloud computing has a trending topic in the market. The
SaaS application is based on the cloud computing that helps in enabling all the services provided
by the cloud computing (Marcelino-Sádaba et al., 2014). There are some limitations of the SaaS
applications that are mentioned below:
Security of the Employee data
The SaaS application involves the services by the cloud computing in the market. The data and
information of the employee are stored in the cloud server using internet. Therefore, there is a
chance for the cyber-attacks on the SaaS application. The SaaS application is connected with the
cloud server over the Internet (Pritchard & PMP, 2014). The security of the data and information
are maintained by different security protocols that are installed in the SaaS application. Although
there is a chance of cyber-attacks on the application that can cause data loss in the company.
Privacy of the Employee Data
The privacy of data and information of the employee in the organisation are secured properly.
The sensitive data of the employee. The cloud deployment model including the SaaS application
helps in controlling the account details of the employee in the organisation. Therefore, the
private information of the employee are stored in the SaaS application. The hacker can hack the
private data of the employee from the SaaS application (Schwalbe, 2015). The private data
include the phone number, address of the employee and other personal dat. These data loss might
cause a huge loss to the employee. The private data and information of the employee are
important to be secured by providing proper security protocol in the cloud server. The SaaS
application provide different software for the service in the company.
CLOUD PRIVACY AND SECURITY
limitations in the Shared approach. The cloud computing has a trending topic in the market. The
SaaS application is based on the cloud computing that helps in enabling all the services provided
by the cloud computing (Marcelino-Sádaba et al., 2014). There are some limitations of the SaaS
applications that are mentioned below:
Security of the Employee data
The SaaS application involves the services by the cloud computing in the market. The data and
information of the employee are stored in the cloud server using internet. Therefore, there is a
chance for the cyber-attacks on the SaaS application. The SaaS application is connected with the
cloud server over the Internet (Pritchard & PMP, 2014). The security of the data and information
are maintained by different security protocols that are installed in the SaaS application. Although
there is a chance of cyber-attacks on the application that can cause data loss in the company.
Privacy of the Employee Data
The privacy of data and information of the employee in the organisation are secured properly.
The sensitive data of the employee. The cloud deployment model including the SaaS application
helps in controlling the account details of the employee in the organisation. Therefore, the
private information of the employee are stored in the SaaS application. The hacker can hack the
private data of the employee from the SaaS application (Schwalbe, 2015). The private data
include the phone number, address of the employee and other personal dat. These data loss might
cause a huge loss to the employee. The private data and information of the employee are
important to be secured by providing proper security protocol in the cloud server. The SaaS
application provide different software for the service in the company.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

7
CLOUD PRIVACY AND SECURITY
Digital Identity Issue
As mentioned by Haimes, (2015), the employees of the organisation are provided with a digital
identity that helps in controlling the data breach in the organisation. The digital identity contains
all type of data and information of the employee in the organisation. Therefore, the access to the
digital identity can cause a huge loss to the company. The hackers might hack the digital identity
and breach the data stored in the server. The digital identity acts as an authentication factor for
the employee in the organisation. There are important data and information stored in the digital
identity.
Provider Solution Issue
There are various security tools installed in the SaaS application that helps in protecting the data
loss in the organisation. The data and information are shared with the cloud service provider.
Therefore, the hackers can attack the main server of the service provider and hack the data from
there. Therefore, there is a high-level risk involved in the service provider side. The legal
standards and rights have to be strong for the cyber security over the internet.
Data Sensitivity
The sensitivity of the data and information refers to the necessity of the data in the
market. The sensitive data is stored over the internet with high security provided by the cloud
server. There is a huge risk of losing the sensitive data due to the cyber-attacks. As stated by
Teller & Kock, (2013), these cyber-attacks are severe for cracking the security protocols of the
cloud server. The security certificates of cloud server are not updated properly causing prone to
hack. The cloud industry is pushing the standards to the level that helps in maintaining the data
and information of the employee in the cloud service by the SaaS application.
CLOUD PRIVACY AND SECURITY
Digital Identity Issue
As mentioned by Haimes, (2015), the employees of the organisation are provided with a digital
identity that helps in controlling the data breach in the organisation. The digital identity contains
all type of data and information of the employee in the organisation. Therefore, the access to the
digital identity can cause a huge loss to the company. The hackers might hack the digital identity
and breach the data stored in the server. The digital identity acts as an authentication factor for
the employee in the organisation. There are important data and information stored in the digital
identity.
Provider Solution Issue
There are various security tools installed in the SaaS application that helps in protecting the data
loss in the organisation. The data and information are shared with the cloud service provider.
Therefore, the hackers can attack the main server of the service provider and hack the data from
there. Therefore, there is a high-level risk involved in the service provider side. The legal
standards and rights have to be strong for the cyber security over the internet.
Data Sensitivity
The sensitivity of the data and information refers to the necessity of the data in the
market. The sensitive data is stored over the internet with high security provided by the cloud
server. There is a huge risk of losing the sensitive data due to the cyber-attacks. As stated by
Teller & Kock, (2013), these cyber-attacks are severe for cracking the security protocols of the
cloud server. The security certificates of cloud server are not updated properly causing prone to
hack. The cloud industry is pushing the standards to the level that helps in maintaining the data
and information of the employee in the cloud service by the SaaS application.

8
CLOUD PRIVACY AND SECURITY
Security and risks in the SaaS application
The Department of Administrative Services has able to apply the Cloud first approach that
helpsmin maintaining te data and information in the ckiud server. There are vatius risks and
security threats of the data I the database (Kerzner, 2013). The unauthenticated users of the
database might cause breach in the database. The attacker tries to access the security protocol
installed in the cloud server. The accountancy payroll and financial information of the employee
are stored in the cloud server that might be lost due to these stacks. Therefore, the private
information of the employee are stored in the SaaS application. The secured data and information
of the employee are stored in the SaaS application. The centralized data format provides access
to all the data and information of the employee in the organisation. Therefore, this is a high-level
risk in the security of the data and information of the employee. The SaaS application involves
the services by the cloud computing in the market. The data and information of the employee are
stored in the cloud server-using internet. Therefore, there is a chance for the cyber-attacks on the
SaaS application. The SaaS application is connected with the cloud server over the Internet. The
security of the data and information are maintained by different security protocols that are
installed in the SaaS application. Although there is a chance of cyber-attacks on the application
that can cause data loss in the company.
CLOUD PRIVACY AND SECURITY
Security and risks in the SaaS application
The Department of Administrative Services has able to apply the Cloud first approach that
helpsmin maintaining te data and information in the ckiud server. There are vatius risks and
security threats of the data I the database (Kerzner, 2013). The unauthenticated users of the
database might cause breach in the database. The attacker tries to access the security protocol
installed in the cloud server. The accountancy payroll and financial information of the employee
are stored in the cloud server that might be lost due to these stacks. Therefore, the private
information of the employee are stored in the SaaS application. The secured data and information
of the employee are stored in the SaaS application. The centralized data format provides access
to all the data and information of the employee in the organisation. Therefore, this is a high-level
risk in the security of the data and information of the employee. The SaaS application involves
the services by the cloud computing in the market. The data and information of the employee are
stored in the cloud server-using internet. Therefore, there is a chance for the cyber-attacks on the
SaaS application. The SaaS application is connected with the cloud server over the Internet. The
security of the data and information are maintained by different security protocols that are
installed in the SaaS application. Although there is a chance of cyber-attacks on the application
that can cause data loss in the company.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

9
CLOUD PRIVACY AND SECURITY
Figure 1: SaaS
(Source: Haimes, 2015)
The HR department of the organisation provides various information of the employee in
the organisation. The Shared approach have caused difficulties for the employee as there
information are shared to everyone in the organisation. The Australian government has able to
provide different consolidated service to the employee by the use of the shared approach of
Department of Administrative Services. The framework for the security issues has been prepared
for maintaining various vulnerabilities of cloud security problems.
Privacy of employee data in SaaS application
The private data of the employee including mobile number and address are stored in the database
of the cloud server. This information is used for creation of an account in the database of the
company. The data privacy is a confidential part of the company and data integrity has to be
CLOUD PRIVACY AND SECURITY
Figure 1: SaaS
(Source: Haimes, 2015)
The HR department of the organisation provides various information of the employee in
the organisation. The Shared approach have caused difficulties for the employee as there
information are shared to everyone in the organisation. The Australian government has able to
provide different consolidated service to the employee by the use of the shared approach of
Department of Administrative Services. The framework for the security issues has been prepared
for maintaining various vulnerabilities of cloud security problems.
Privacy of employee data in SaaS application
The private data of the employee including mobile number and address are stored in the database
of the cloud server. This information is used for creation of an account in the database of the
company. The data privacy is a confidential part of the company and data integrity has to be
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
10
CLOUD PRIVACY AND SECURITY
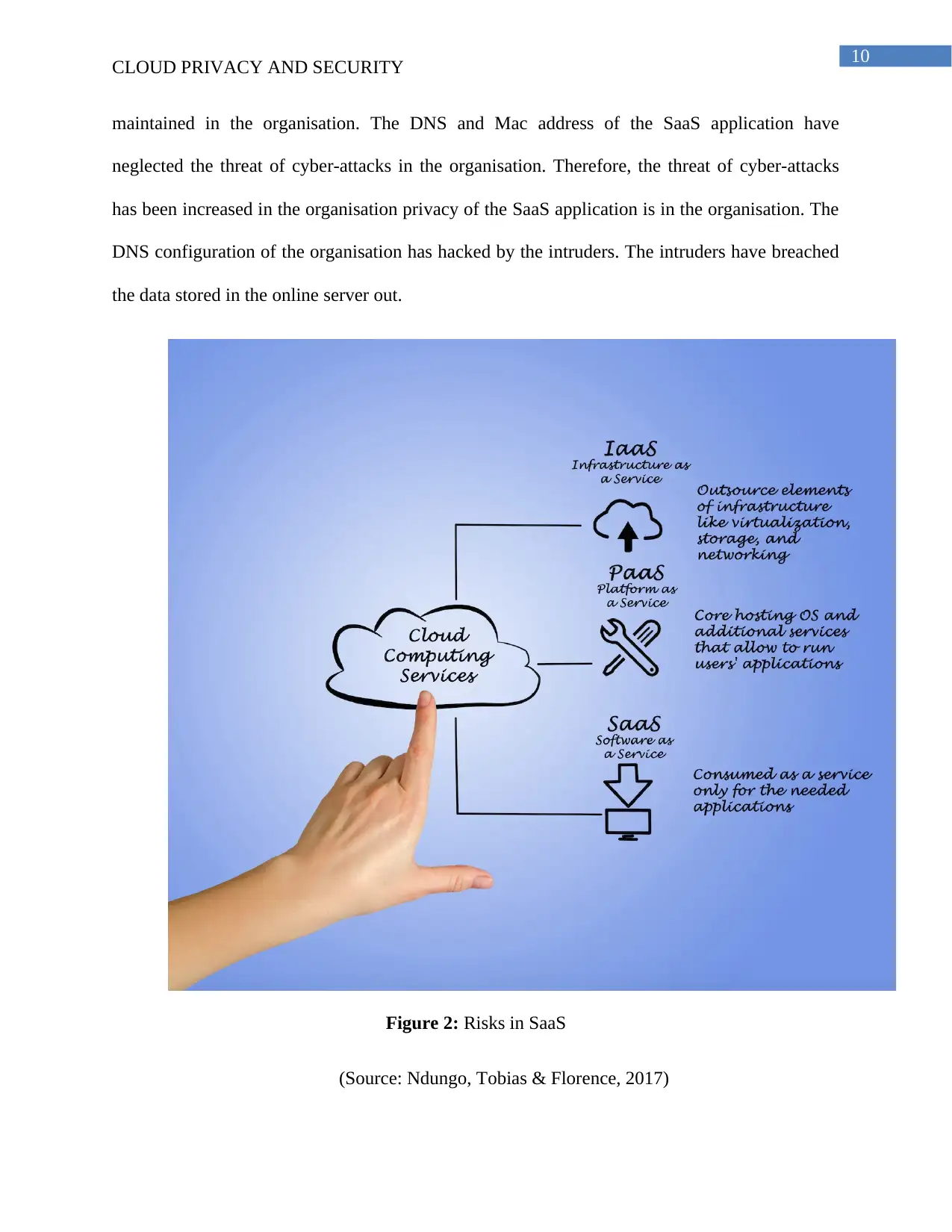
maintained in the organisation. The DNS and Mac address of the SaaS application have
neglected the threat of cyber-attacks in the organisation. Therefore, the threat of cyber-attacks
has been increased in the organisation privacy of the SaaS application is in the organisation. The
DNS configuration of the organisation has hacked by the intruders. The intruders have breached
the data stored in the online server out.
Figure 2: Risks in SaaS
(Source: Ndungo, Tobias & Florence, 2017)
CLOUD PRIVACY AND SECURITY
maintained in the organisation. The DNS and Mac address of the SaaS application have
neglected the threat of cyber-attacks in the organisation. Therefore, the threat of cyber-attacks
has been increased in the organisation privacy of the SaaS application is in the organisation. The
DNS configuration of the organisation has hacked by the intruders. The intruders have breached
the data stored in the online server out.
Figure 2: Risks in SaaS
(Source: Ndungo, Tobias & Florence, 2017)

11
CLOUD PRIVACY AND SECURITY
Threats and risks to digital identities of Government employees from the move to SaaS
applications
The government has provided the digital identities to the employee. This digital identity contains
all the necessary information. The digital identity of the employee helps in authenticating the
employability in the company (Ndungo, Tobias & Florence, 2017). The external attackers can be
effective for the security if the infrastructure of the company in the market. The risks
management in the company has been initiated for maintaining the risks and security treats
involved in it. The employee have to upload the data at a fixed time to complete the data
transparency in the organization.
Figure 3: Risk management in cloud
(Source: No et al., 2017)
CLOUD PRIVACY AND SECURITY
Threats and risks to digital identities of Government employees from the move to SaaS
applications
The government has provided the digital identities to the employee. This digital identity contains
all the necessary information. The digital identity of the employee helps in authenticating the
employability in the company (Ndungo, Tobias & Florence, 2017). The external attackers can be
effective for the security if the infrastructure of the company in the market. The risks
management in the company has been initiated for maintaining the risks and security treats
involved in it. The employee have to upload the data at a fixed time to complete the data
transparency in the organization.
Figure 3: Risk management in cloud
(Source: No et al., 2017)
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 17
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





