Analyzing Digital Privacy in Australia: Challenges and Solutions
VerifiedAdded on 2023/03/21
|9
|2065
|55
Report
AI Summary
This report delves into the multifaceted realm of online privacy, with a specific focus on the Australian context. It commences by defining privacy and digital privacy, highlighting the increasing exposure of personal information in Australia and the associated risks of data theft and hacking. The report outlines the Australian government's initiatives, including the Privacy Act, and emphasizes the importance of data storage and security within digital systems. It provides practical advice on protecting data, such as using strong passwords, managing privacy settings, and being cautious on social media platforms like Facebook, Google, and iCloud. Furthermore, it underscores the significance of robust digital security measures for Australian citizens and advocates for updated privacy laws. The report also examines the European Union's General Data Protection Regulation (GDPR) and suggests that Australia should strengthen its digital security laws to protect its citizens' data. The report concludes by emphasizing the need for user education and the shared responsibility of social media platforms, banks, and third-party vendors to enhance user knowledge regarding data security.

Running head: ONLINE PRIVACY
Online Privacy
Name of the student:
Name of the university:
Author Note:
Online Privacy
Name of the student:
Name of the university:
Author Note:
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

1ONLINE PRIVACY
Privacy may be defined as the capability of individuals that secludes himself or
herself or information regarding them following a selective methodology. The content of the
information that are private may differ between various cultures as well as individuals but
they share the themes that are common (Nissenbaum, 2018). Digital privacy may be stated as
the overall collective definition of the three categories that are mainly incorporated which are
likely to be privacy of information, privacy of communication as well as privacy of an
individual. Digital privacy in Australia may be stated as the fact that the information
regarding the individuals in Australia is quite exposed that may lead to bigger issues in the
country regarding data theft as well as hacking of the bank details to generate unknown
transactions (Mann, 2018). In this context, the Australian Government has come with specific
digital privacy laws that will be implemented in the country by 2020. This Privacy Act tends
to introduce innovated as well as effective set of principles related to privacy. This Act also
promises that the digital privacy will restrict approximately 86% of the privacy issues
pertaining in the country.
The issues that are being considered in the field of digital measures may be primarily
identified as the storage of the data or information of the individuals present within the digital
system (Sullivan et al., 2018). This preservation of data is very necessary as with the help of
this information a person can be identified as well as the person can also use the data from
anywhere for future purposes. These data can be used by the social media as a platform for
the storage of data. This effective storage of data can help in maintaining them as well as
accessing them for future (Esayas & Svantesson, 2018). The preservation of data maintaining
security and structure may be depicted as the important features in the concern of digital
measure.
The options that might be depicted as the useful do’s for protecting the data in the
digital fields are as follows:
Privacy may be defined as the capability of individuals that secludes himself or
herself or information regarding them following a selective methodology. The content of the
information that are private may differ between various cultures as well as individuals but
they share the themes that are common (Nissenbaum, 2018). Digital privacy may be stated as
the overall collective definition of the three categories that are mainly incorporated which are
likely to be privacy of information, privacy of communication as well as privacy of an
individual. Digital privacy in Australia may be stated as the fact that the information
regarding the individuals in Australia is quite exposed that may lead to bigger issues in the
country regarding data theft as well as hacking of the bank details to generate unknown
transactions (Mann, 2018). In this context, the Australian Government has come with specific
digital privacy laws that will be implemented in the country by 2020. This Privacy Act tends
to introduce innovated as well as effective set of principles related to privacy. This Act also
promises that the digital privacy will restrict approximately 86% of the privacy issues
pertaining in the country.
The issues that are being considered in the field of digital measures may be primarily
identified as the storage of the data or information of the individuals present within the digital
system (Sullivan et al., 2018). This preservation of data is very necessary as with the help of
this information a person can be identified as well as the person can also use the data from
anywhere for future purposes. These data can be used by the social media as a platform for
the storage of data. This effective storage of data can help in maintaining them as well as
accessing them for future (Esayas & Svantesson, 2018). The preservation of data maintaining
security and structure may be depicted as the important features in the concern of digital
measure.
The options that might be depicted as the useful do’s for protecting the data in the
digital fields are as follows:

2ONLINE PRIVACY
The basics that is usage of strong password, not visiting untrusted websites and
always keeping the software updated.
The privacy settings of the data are to be turned ON every time so that the tampering
of data can be prevented from untrusted sources.
The cookies present in the visited websites is to be blocked.
The unnecessary linking of accounts to every website is to be prevented.
Firewalls and antivirus are to be maintained at every device where data is being
shared.
Stronger passwords should be used in every website where personal data is
associated.
Better browsing methodologies must be adhered for maintaining digital privacy.
Moreover, the users that visit the platform like Facebook, Google or iCloud, where a huge
amount of data is associated safe browsing methodologies are to be adapted, These
methodologies for the above stated websites may be identified separately. Thus for Facebook
the points of digital security are
Accessing of the Facebook privacy settings is needed and choosing the option of
sharing data with only the known person can restrict the visibility of the data thus
decreases the chances of the data being hampered and accessed by unknown
people (Arora & Scheiber, 2017).
The privacy check-up of the present user’s profile must be done regularly.
Facebook possesses a short but effective privacy primer.
The user must learn from the Facebook’s stated privacy settings.
The security settings provided by Facebook has a two-step verification procedure
which must be availed by any user maintaining a profile with this social media
The basics that is usage of strong password, not visiting untrusted websites and
always keeping the software updated.
The privacy settings of the data are to be turned ON every time so that the tampering
of data can be prevented from untrusted sources.
The cookies present in the visited websites is to be blocked.
The unnecessary linking of accounts to every website is to be prevented.
Firewalls and antivirus are to be maintained at every device where data is being
shared.
Stronger passwords should be used in every website where personal data is
associated.
Better browsing methodologies must be adhered for maintaining digital privacy.
Moreover, the users that visit the platform like Facebook, Google or iCloud, where a huge
amount of data is associated safe browsing methodologies are to be adapted, These
methodologies for the above stated websites may be identified separately. Thus for Facebook
the points of digital security are
Accessing of the Facebook privacy settings is needed and choosing the option of
sharing data with only the known person can restrict the visibility of the data thus
decreases the chances of the data being hampered and accessed by unknown
people (Arora & Scheiber, 2017).
The privacy check-up of the present user’s profile must be done regularly.
Facebook possesses a short but effective privacy primer.
The user must learn from the Facebook’s stated privacy settings.
The security settings provided by Facebook has a two-step verification procedure
which must be availed by any user maintaining a profile with this social media
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

3ONLINE PRIVACY
platform. This can be very effective to restrict any hacker that is trying to access
the information present in the platform.
The point of digital security for the social media platform of Google may be stated as:
The user must be well known to the overall privacy setting provided by this social
media platform.
The privacy check-up provided by Google must be carried out frequently.
The social media settings of Google + must be adhered by the user of this social
media platform.
The two factor authentication as provided by Google is also to be used by the user for
maintaining the digital security.
The point of digital security for the social media platform of iCloud may be stated as:
The users of this social media platform must effectively follow the privacy policy.
Strong password is to be provided for maintaining the data with this social media
platform.
The two factor authentication method must be adhered by every user of this social
media platform.
Every person on the internet sharing their details to any website must maintain the
minimal level of security to maintain their privacy of the data. Moreover, it can be said that
not every person present on the digital platform must need same level of security (Osbourne,
Hall & Sussan, 2016). This is due to the fact that the maintenance of privacy depends on the
data or information that is being stored by the person in the digital platforms. According to
the level of the important data, the privacy level is to be adhered. The enhanced level of
security of the data regarding transactions are to be provided more level of security that the
person who is sharing just the contact number or limited personal information over the
platform. This can be very effective to restrict any hacker that is trying to access
the information present in the platform.
The point of digital security for the social media platform of Google may be stated as:
The user must be well known to the overall privacy setting provided by this social
media platform.
The privacy check-up provided by Google must be carried out frequently.
The social media settings of Google + must be adhered by the user of this social
media platform.
The two factor authentication as provided by Google is also to be used by the user for
maintaining the digital security.
The point of digital security for the social media platform of iCloud may be stated as:
The users of this social media platform must effectively follow the privacy policy.
Strong password is to be provided for maintaining the data with this social media
platform.
The two factor authentication method must be adhered by every user of this social
media platform.
Every person on the internet sharing their details to any website must maintain the
minimal level of security to maintain their privacy of the data. Moreover, it can be said that
not every person present on the digital platform must need same level of security (Osbourne,
Hall & Sussan, 2016). This is due to the fact that the maintenance of privacy depends on the
data or information that is being stored by the person in the digital platforms. According to
the level of the important data, the privacy level is to be adhered. The enhanced level of
security of the data regarding transactions are to be provided more level of security that the
person who is sharing just the contact number or limited personal information over the
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

4ONLINE PRIVACY
internet (Leaver, 2017). The more vulnerable the data is the enhanced level of security is to
be provided.
It is very important for Australian legislators to pass new laws regarding the data privacy
of the citizens of the country. The innovated technologies that collects personal information
about the data must adhere this law and go to their restricted limits for the collection of the
data. Moreover, it is quite known that the Government is trying to implement new set of laws
in the digital security sector of the country (Chang, Gomes & Martin, 2018). The innovation
in the technological fields for the websites or platforms that uses user’s personal information
as well as important bank details will be adhered by this law. The laws proposed to be
amended must look into the purpose of the data that is being collected. There will be proper
notification methodologies when the data will be shared by any other persons present in the
internet. The law is supposed to emphasize on the factor that is the right to access the
personal information of the users by the social media platforms as well as the platforms that
are accessing eth user’s personal data (Thompson et al., 2018).
The individuals that are accessing the websites for a long time it can be said that they
should come up with their self-responsibility to protect their data. The online privacy tools or
the rules that are made by the social media platforms can be availed by the users but it should
not be limited to that (Weiss & Archick, 2016). The recent vulnerable attacks going on with
the social media platforms along with the unknown accessing of a user’s data is due to the
lack of providing the security information to the individuals. Thorough sessions must be
carried out by most of the social media platforms to provide knowledge as well as skill to the
user for enhancing the security of the user’s information. Most of the users possess very little
knowledge regarding the data that is collected as well processed online (Weber, 2015). The
responsibility for providing innovative as well as enhanced knowledge to these users for
maintaining the security measures of their own personal data must be provided by the soci8al
internet (Leaver, 2017). The more vulnerable the data is the enhanced level of security is to
be provided.
It is very important for Australian legislators to pass new laws regarding the data privacy
of the citizens of the country. The innovated technologies that collects personal information
about the data must adhere this law and go to their restricted limits for the collection of the
data. Moreover, it is quite known that the Government is trying to implement new set of laws
in the digital security sector of the country (Chang, Gomes & Martin, 2018). The innovation
in the technological fields for the websites or platforms that uses user’s personal information
as well as important bank details will be adhered by this law. The laws proposed to be
amended must look into the purpose of the data that is being collected. There will be proper
notification methodologies when the data will be shared by any other persons present in the
internet. The law is supposed to emphasize on the factor that is the right to access the
personal information of the users by the social media platforms as well as the platforms that
are accessing eth user’s personal data (Thompson et al., 2018).
The individuals that are accessing the websites for a long time it can be said that they
should come up with their self-responsibility to protect their data. The online privacy tools or
the rules that are made by the social media platforms can be availed by the users but it should
not be limited to that (Weiss & Archick, 2016). The recent vulnerable attacks going on with
the social media platforms along with the unknown accessing of a user’s data is due to the
lack of providing the security information to the individuals. Thorough sessions must be
carried out by most of the social media platforms to provide knowledge as well as skill to the
user for enhancing the security of the user’s information. Most of the users possess very little
knowledge regarding the data that is collected as well processed online (Weber, 2015). The
responsibility for providing innovative as well as enhanced knowledge to these users for
maintaining the security measures of their own personal data must be provided by the soci8al

5ONLINE PRIVACY
media platforms as well as the bank or third party vendor that carries out the transactions for
the users.
The European Union recently are following the General Data Protection Regulation that
deals with mainly data privacy and protection regarding the individuals present in the
European Union. This addresses the personal information of the citizens of the European
Union. This law states that the controllers regarding the personal data must adhere necessary
technical as well as organizational measures for implementing the data securities. In this
context, the Australian Government is also trying to implement the data security laws all over
the country so that their citizens could also be kept safe in regards to the data security
(Kerber, 2016). The Australian Government does not want to exempt the politicians from the
law and this might be a very innovative step in comparison to the digital security law as
stated by the European Union. Moreover, it is depicted that the current Australian Digital
Security laws are weak with respect to the laws amended by the European Union. This is due
to the fact that the Australian laws does not adhere politicians as many individuals does not
have the right to enforce laws in the situation that they do exist.
The mind map for the online privacy is provided below:
media platforms as well as the bank or third party vendor that carries out the transactions for
the users.
The European Union recently are following the General Data Protection Regulation that
deals with mainly data privacy and protection regarding the individuals present in the
European Union. This addresses the personal information of the citizens of the European
Union. This law states that the controllers regarding the personal data must adhere necessary
technical as well as organizational measures for implementing the data securities. In this
context, the Australian Government is also trying to implement the data security laws all over
the country so that their citizens could also be kept safe in regards to the data security
(Kerber, 2016). The Australian Government does not want to exempt the politicians from the
law and this might be a very innovative step in comparison to the digital security law as
stated by the European Union. Moreover, it is depicted that the current Australian Digital
Security laws are weak with respect to the laws amended by the European Union. This is due
to the fact that the Australian laws does not adhere politicians as many individuals does not
have the right to enforce laws in the situation that they do exist.
The mind map for the online privacy is provided below:
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
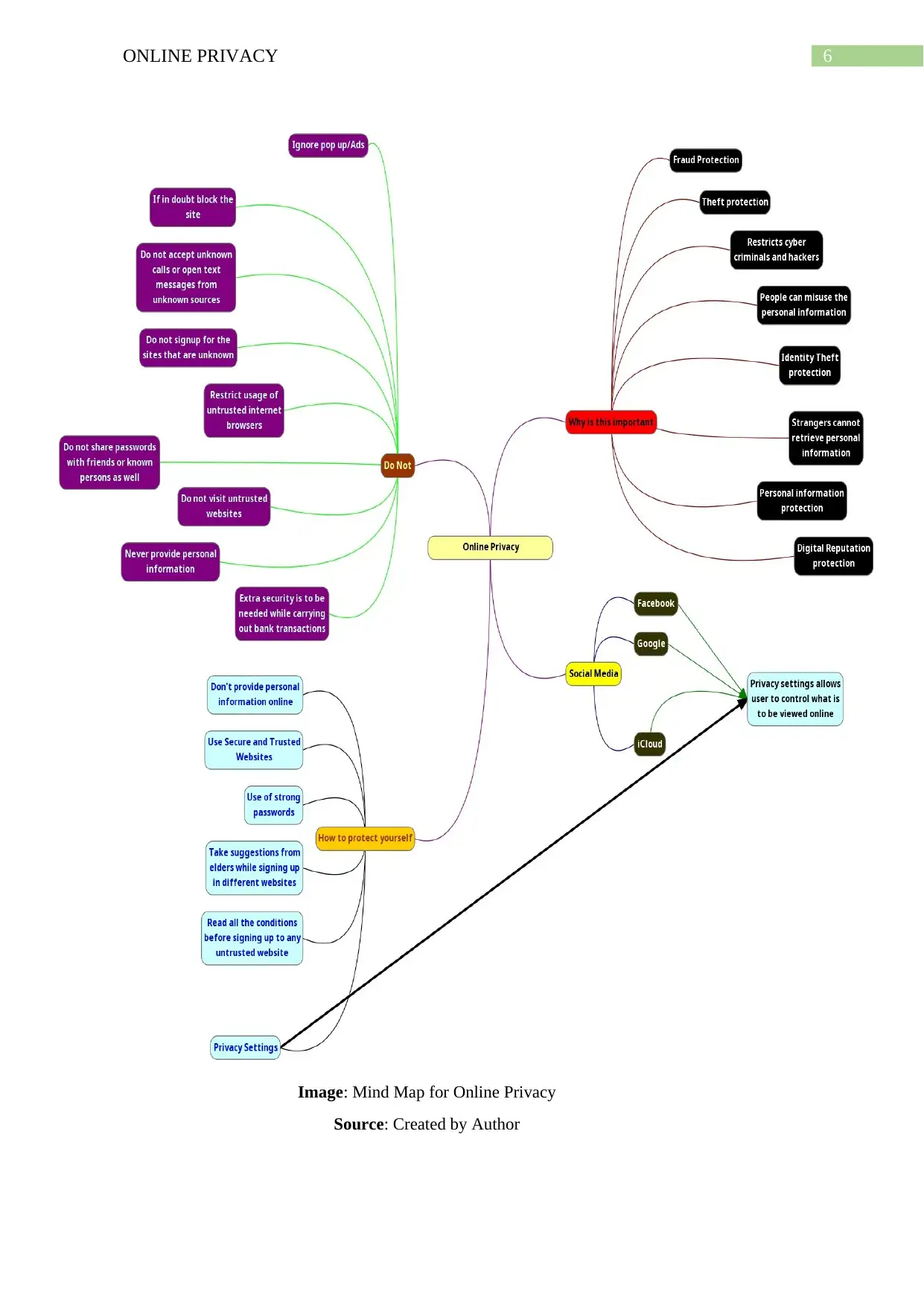
6ONLINE PRIVACY
Image: Mind Map for Online Privacy
Source: Created by Author
Image: Mind Map for Online Privacy
Source: Created by Author
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

7ONLINE PRIVACY
References
Arora, P., & Scheiber, L. (2017). Slumdog romance: Facebook love and digital privacy at the
margins. Media, Culture & Society, 39(3), 408-422.
Chang, S., Gomes, C., & Martin, F. (2018). Navigating Online Down Under: International
Students' Digital Journeys in Australia.
Esayas, S., & Svantesson, D. (2018). Digital platforms under fire: What Australia can learn
from recent developments in Europe. Alternative Law Journal, 43(4), 275-282.
Kerber, W. (2016). Digital markets, data, and privacy: competition law, consumer law and
data protection. Journal of Intellectual Property Law & Practice, 11(11), 856-866.
Leaver, T. (2017). Born digital? Presence, privacy, and intimate surveillance.
Mann, M. (2018). Privacy in Australia: Brief to UN Special Rapporteur on Right to Privacy.
Nissenbaum, H. (2018, October). Achieving Meaningful Privacy in Digital Systems. In
Proceedings of the 2018 ACM SIGSAC Conference on Computer and
Communications Security (pp. 1-2). ACM.
Osbourne, C., Hall, R., & Sussan, F. (2016). Digital Privacy: Philosophical Underpinnings. In
ICSB World Conference Proceedings (pp. 1-2). International Council for Small
Business (ICSB).
Sullivan, M., Rainey, H., Cross, W., & Nakasone, S. (2018). Digital Safety and Privacy:
Raising Awareness Through Library Outreach.
Thompson, N., Bunn, A., Kininmonth, J., & McGill, T. (2018). Privacy Concerns and
Acceptance of Government Surveillance in Australia. In 29th Australasian
Conference on Information Systems (ACIS2018).
References
Arora, P., & Scheiber, L. (2017). Slumdog romance: Facebook love and digital privacy at the
margins. Media, Culture & Society, 39(3), 408-422.
Chang, S., Gomes, C., & Martin, F. (2018). Navigating Online Down Under: International
Students' Digital Journeys in Australia.
Esayas, S., & Svantesson, D. (2018). Digital platforms under fire: What Australia can learn
from recent developments in Europe. Alternative Law Journal, 43(4), 275-282.
Kerber, W. (2016). Digital markets, data, and privacy: competition law, consumer law and
data protection. Journal of Intellectual Property Law & Practice, 11(11), 856-866.
Leaver, T. (2017). Born digital? Presence, privacy, and intimate surveillance.
Mann, M. (2018). Privacy in Australia: Brief to UN Special Rapporteur on Right to Privacy.
Nissenbaum, H. (2018, October). Achieving Meaningful Privacy in Digital Systems. In
Proceedings of the 2018 ACM SIGSAC Conference on Computer and
Communications Security (pp. 1-2). ACM.
Osbourne, C., Hall, R., & Sussan, F. (2016). Digital Privacy: Philosophical Underpinnings. In
ICSB World Conference Proceedings (pp. 1-2). International Council for Small
Business (ICSB).
Sullivan, M., Rainey, H., Cross, W., & Nakasone, S. (2018). Digital Safety and Privacy:
Raising Awareness Through Library Outreach.
Thompson, N., Bunn, A., Kininmonth, J., & McGill, T. (2018). Privacy Concerns and
Acceptance of Government Surveillance in Australia. In 29th Australasian
Conference on Information Systems (ACIS2018).

8ONLINE PRIVACY
Weber, R. H. (2015). The digital future–A challenge for privacy?. Computer Law & Security
Review, 31(2), 234-242.
Weiss, M. A., & Archick, K. (2016). US-EU data privacy: from safe harbor to privacy shield.
Weber, R. H. (2015). The digital future–A challenge for privacy?. Computer Law & Security
Review, 31(2), 234-242.
Weiss, M. A., & Archick, K. (2016). US-EU data privacy: from safe harbor to privacy shield.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 9
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





