Thesis on Cyber Security in Aviation: Legal Standpoint and Challenges
VerifiedAdded on 2023/04/17
|115
|33698
|384
Thesis and Dissertation
AI Summary
This thesis provides an in-depth analysis of cyber security within the aviation industry, examining the legal landscape, potential threats, and necessary security measures. It begins with an introduction to cyber security and aviation, highlighting the growing concern over cyber-attacks and their potential impact on airlines, air traffic control (ATC), and airports. The research outlines objectives, hypotheses, questions, and methodology, followed by a detailed exploration of relevant international and Indian laws and regulatory bodies, including ICAO, the IT Act 2000, and CERT-In guidelines. The thesis further investigates the three pillars of aviation—ATC, airlines, and airports—detailing specific cyber security challenges and vulnerabilities within each area. Case studies illustrate real-world examples of security breaches and their consequences. The findings are presented through a comparative analysis, leading to a conclusion and suggestions for enhancing cyber security in the aviation sector. Desklib offers students access to this thesis and many other solved assignments.
Cyber Security in Aviation
Thesis
Hp
Thesis
Hp
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Cyber Security in Aviation
Table of Contents
Chapter 1: Introduction....................................................................................................................3
1.1. Introduction to Cyber Security..........................................................................................4
1.2. Introduction to Aviation....................................................................................................7
1.3. Introduction to Cyber Security in Aviation - Airlines, ATC and Airports.......................9
1.4. Research objectives, hypothesis and questions...............................................................13
1.4.1. Research objectives.................................................................................................13
1.4.2. Research hypothesis.................................................................................................14
1.4.3. Research questions...................................................................................................14
1.5. Research methodology....................................................................................................14
1.6. Research outline (chapterization)....................................................................................15
Chapter 2: Legal standpoint and bodies.........................................................................................18
2.1. International regulator: ICAO.........................................................................................18
2.2. Law and bodies in India: IT Act and applicability in Aviation......................................24
2.2.1. BCAS.......................................................................................................................24
2.2.2. Legislative history...................................................................................................26
2.2.3. IT Act, 2000.............................................................................................................30
2.2.4. The National Cyber Security Policy, 2013..............................................................33
2.2.5. XII Five Year Plan report on Cyber Security (2017– 2022)...................................34
2.2.6. NCIIPC Guidelines and CERT-In Rules.................................................................35
pg. 1
Table of Contents
Chapter 1: Introduction....................................................................................................................3
1.1. Introduction to Cyber Security..........................................................................................4
1.2. Introduction to Aviation....................................................................................................7
1.3. Introduction to Cyber Security in Aviation - Airlines, ATC and Airports.......................9
1.4. Research objectives, hypothesis and questions...............................................................13
1.4.1. Research objectives.................................................................................................13
1.4.2. Research hypothesis.................................................................................................14
1.4.3. Research questions...................................................................................................14
1.5. Research methodology....................................................................................................14
1.6. Research outline (chapterization)....................................................................................15
Chapter 2: Legal standpoint and bodies.........................................................................................18
2.1. International regulator: ICAO.........................................................................................18
2.2. Law and bodies in India: IT Act and applicability in Aviation......................................24
2.2.1. BCAS.......................................................................................................................24
2.2.2. Legislative history...................................................................................................26
2.2.3. IT Act, 2000.............................................................................................................30
2.2.4. The National Cyber Security Policy, 2013..............................................................33
2.2.5. XII Five Year Plan report on Cyber Security (2017– 2022)...................................34
2.2.6. NCIIPC Guidelines and CERT-In Rules.................................................................35
pg. 1

Cyber Security in Aviation
2.2.7. SARPs compliance..................................................................................................36
2.2.8. Other measures........................................................................................................38
2.3. International Scenario: Law and bodies in US and applicability in Aviation.................39
2.3. International Scenario: Law and bodies in Euro Control and applicability in Aviation....44
Chapter 3: Pillars of Aviation........................................................................................................50
3.1. Cybersecurity in ATC.........................................................................................................53
3.1.1. ATC and threats looming around it.........................................................................53
3.1.2. Major events in Air Traffic control.............................................................................60
3.2. Cybersecurity in Airlines....................................................................................................62
3.3. Cybersecurity in Airports/Aerodromes...............................................................................66
Chapter 4: Aerodromes/Airports...................................................................................................69
4.1. Case Study: Application of security measures at leading airport...................................80
4.2. Case Study: Hacking of websites....................................................................................85
4.3. Case Study: Unsecured data...........................................................................................86
4.4. Case Study: Hacking computer systems........................................................................87
4.5. Case Study: Indian perspective......................................................................................88
4.6. Case law: R v Daniel Devereux......................................................................................90
Chapter 5: Findings and Comparative Analysis............................................................................92
Chapter 6: Conclusion...................................................................................................................97
Chapter 7: Suggestions................................................................................................................102
Bibliography................................................................................................................................105
pg. 2
2.2.7. SARPs compliance..................................................................................................36
2.2.8. Other measures........................................................................................................38
2.3. International Scenario: Law and bodies in US and applicability in Aviation.................39
2.3. International Scenario: Law and bodies in Euro Control and applicability in Aviation....44
Chapter 3: Pillars of Aviation........................................................................................................50
3.1. Cybersecurity in ATC.........................................................................................................53
3.1.1. ATC and threats looming around it.........................................................................53
3.1.2. Major events in Air Traffic control.............................................................................60
3.2. Cybersecurity in Airlines....................................................................................................62
3.3. Cybersecurity in Airports/Aerodromes...............................................................................66
Chapter 4: Aerodromes/Airports...................................................................................................69
4.1. Case Study: Application of security measures at leading airport...................................80
4.2. Case Study: Hacking of websites....................................................................................85
4.3. Case Study: Unsecured data...........................................................................................86
4.4. Case Study: Hacking computer systems........................................................................87
4.5. Case Study: Indian perspective......................................................................................88
4.6. Case law: R v Daniel Devereux......................................................................................90
Chapter 5: Findings and Comparative Analysis............................................................................92
Chapter 6: Conclusion...................................................................................................................97
Chapter 7: Suggestions................................................................................................................102
Bibliography................................................................................................................................105
pg. 2
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

Cyber Security in Aviation
Chapter 1: Introduction
Every other day, there is headline-grabbing story related to online attacks and the
frequency of such publications point towards the rising number of online attacks. The last decade
or so has seen a range of data breaches, which have been spread across varied industries like
health insurance, online businesses, retail and banking, amongst the others. Just the financial
impact part is enough to draw concern. As per one of the reports, the estimated cost of data
breaches on global economy by end of 2019 will be $2 trillion1. As per Accenture, these
estimates are set to rise, with the cost of such crimes for companies reaching $5.2 trillion over
the course of coming five years2. With time, cyber treats have not only grown in number, but
also in their sophistication and cost. This is present in every industry, due to rampant reliance on
technology and internet devices like mobiles presenting an open invitation for the criminals to
undertake cyber-attacks.
Cybersecurity risk is of particular significance in the airlines industry. As per one of the
surveys undertaken by PwC, 85% of CEOs of airlines stated that they were concerned about
cybersecurity risks, as against 61% of other industry CEOs3. This 24% difference is contributed
to the complications of cyber-attack in airlines industry as compared to the other industries. This
is because such attacks in other industries are mostly related to company data or sensitive
customer information theft. However, for airlines, apart from these threats, the connectivity to
flight operations and air traffic systems increases the complications for the airlines industries.
Even though this advance integration and communication is required to improve operational and
financial performance, it does present a higher opportunity for exploiting such advancements4.
1 Zack Whittaker, Data breaches to cost global economy $2 trillion by 2019 (12 May 2015)
<https://www.zdnet.com/article/data-breaches-to-cost-2-trillion-by-2019/>
2 Alison Geib, Cybercrime Could Cost Companies US$5.2 Trillion Over Next Five Years, According to New
Research from Accenture (17 January 2019) <https://www.apnews.com/ac9bb114045c49c59089abae155045e4>
3 PwC, Getting clear of the clouds Will the upward trajectory continue? (2018)
<https://www.pwc.es/es/publicaciones/transporte/pwc_2015_global_airline_ceo_survey.pdf>
4 PwC, Tailwinds 2017 airline industry trends (2017) <https://www.pwc.fr/fr/assets/files/pdf/2017/12/2017-
tailwinds-airline-industry-trends-pwc.pdf>
pg. 3
Chapter 1: Introduction
Every other day, there is headline-grabbing story related to online attacks and the
frequency of such publications point towards the rising number of online attacks. The last decade
or so has seen a range of data breaches, which have been spread across varied industries like
health insurance, online businesses, retail and banking, amongst the others. Just the financial
impact part is enough to draw concern. As per one of the reports, the estimated cost of data
breaches on global economy by end of 2019 will be $2 trillion1. As per Accenture, these
estimates are set to rise, with the cost of such crimes for companies reaching $5.2 trillion over
the course of coming five years2. With time, cyber treats have not only grown in number, but
also in their sophistication and cost. This is present in every industry, due to rampant reliance on
technology and internet devices like mobiles presenting an open invitation for the criminals to
undertake cyber-attacks.
Cybersecurity risk is of particular significance in the airlines industry. As per one of the
surveys undertaken by PwC, 85% of CEOs of airlines stated that they were concerned about
cybersecurity risks, as against 61% of other industry CEOs3. This 24% difference is contributed
to the complications of cyber-attack in airlines industry as compared to the other industries. This
is because such attacks in other industries are mostly related to company data or sensitive
customer information theft. However, for airlines, apart from these threats, the connectivity to
flight operations and air traffic systems increases the complications for the airlines industries.
Even though this advance integration and communication is required to improve operational and
financial performance, it does present a higher opportunity for exploiting such advancements4.
1 Zack Whittaker, Data breaches to cost global economy $2 trillion by 2019 (12 May 2015)
<https://www.zdnet.com/article/data-breaches-to-cost-2-trillion-by-2019/>
2 Alison Geib, Cybercrime Could Cost Companies US$5.2 Trillion Over Next Five Years, According to New
Research from Accenture (17 January 2019) <https://www.apnews.com/ac9bb114045c49c59089abae155045e4>
3 PwC, Getting clear of the clouds Will the upward trajectory continue? (2018)
<https://www.pwc.es/es/publicaciones/transporte/pwc_2015_global_airline_ceo_survey.pdf>
4 PwC, Tailwinds 2017 airline industry trends (2017) <https://www.pwc.fr/fr/assets/files/pdf/2017/12/2017-
tailwinds-airline-industry-trends-pwc.pdf>
pg. 3
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Cyber Security in Aviation
This is the reason why this industry is constantly brining in technological advancements towards
protecting its assets and data. There is use of complicated software along with sophisticated
hardware to safeguard from instances of cyber-attacks.
The air traffic control has been drastically modernized and this brings with it many cyber
issues, one of which is NextGen. NextGen or the “Next Generation Air Transportation System”
presented by FAA (“Federal Aviation Administration”), is over 40 years old, relying on radars
and brings forth limited connectivity. It helps in improving the efficiency of network through the
use of Global Positioning System (GPS), which is software based, and internet connected. This
very connectivity brings high security threats5. The IATA (International Air Transport
Association) has maintained that the effective way of dealing with such risks is allocating and
prioritizing resources towards protection of most valuable assets of airlines. In addition to this,
there was a need for developing such global security systems, which could adopt “an end-to-end
risk-based approach6.” Effectively there is a need to prevent, detect and react to such threats, as a
way of protecting the aviation industry from such threats.
1.1. Introduction to Cyber Security
To go into the threats posted by cyber-attacks into aviation industry, there is a need to
understand what cybersecurity actually means. In the most basic sense, cybersecurity relates to
such processes, practices and technologies, which have been designed in a manner so as to
safeguard programs, data, devices and networks from any kind of unauthorized access, attack or
damage. In short, the safeguarding of the crucial assets related to technology, there is a need to
deploy proper measures, and these are in form of cybersecurity. Anything connected with
internet, presents with it a cyber-threat, which requires strict measures to be adopted, to avoid
these threats being converted into real life incidents and this is where the role of cybersecurity
comes in.
5 PwC, Aviation perspectives 2016 special report series: Cybersecurity and the airline industry (2016)
<https://www.pwc.com/us/en/industrial-products/publications/assets/pwc-airline-industry-perspectives-
cybersecurity.pdf>
6 IATA, Remarks of Tony Tyler at the IATA 22nd AVSEC World in Istanbul (05 November 2013)
<https://www.iata.org/pressroom/speeches/Pages/2013-11-05-01.aspx>
pg. 4
This is the reason why this industry is constantly brining in technological advancements towards
protecting its assets and data. There is use of complicated software along with sophisticated
hardware to safeguard from instances of cyber-attacks.
The air traffic control has been drastically modernized and this brings with it many cyber
issues, one of which is NextGen. NextGen or the “Next Generation Air Transportation System”
presented by FAA (“Federal Aviation Administration”), is over 40 years old, relying on radars
and brings forth limited connectivity. It helps in improving the efficiency of network through the
use of Global Positioning System (GPS), which is software based, and internet connected. This
very connectivity brings high security threats5. The IATA (International Air Transport
Association) has maintained that the effective way of dealing with such risks is allocating and
prioritizing resources towards protection of most valuable assets of airlines. In addition to this,
there was a need for developing such global security systems, which could adopt “an end-to-end
risk-based approach6.” Effectively there is a need to prevent, detect and react to such threats, as a
way of protecting the aviation industry from such threats.
1.1. Introduction to Cyber Security
To go into the threats posted by cyber-attacks into aviation industry, there is a need to
understand what cybersecurity actually means. In the most basic sense, cybersecurity relates to
such processes, practices and technologies, which have been designed in a manner so as to
safeguard programs, data, devices and networks from any kind of unauthorized access, attack or
damage. In short, the safeguarding of the crucial assets related to technology, there is a need to
deploy proper measures, and these are in form of cybersecurity. Anything connected with
internet, presents with it a cyber-threat, which requires strict measures to be adopted, to avoid
these threats being converted into real life incidents and this is where the role of cybersecurity
comes in.
5 PwC, Aviation perspectives 2016 special report series: Cybersecurity and the airline industry (2016)
<https://www.pwc.com/us/en/industrial-products/publications/assets/pwc-airline-industry-perspectives-
cybersecurity.pdf>
6 IATA, Remarks of Tony Tyler at the IATA 22nd AVSEC World in Istanbul (05 November 2013)
<https://www.iata.org/pressroom/speeches/Pages/2013-11-05-01.aspx>
pg. 4

Cyber Security in Aviation
The crux of the matter is that the term cyber security is used to refer to the information
technology’s security. The goal is to safeguard the “computers, networks, programs and data”
from unauthorized use and access. The data collected by different entities, be it governments,
hospitals or even military, is not transmitted on another device, without proper approvals. The
sensitive business information and personal information needs to be protected. Similarity, the
nation’s security is protected guarded from the modern day cyber-attacks. There are many types
of actions, which can be taken as a measure to safeguard against such attacks. These include
avoidance of spywares, protecting the passwords, keeping the firewalls turned on, preventing
identity theft, making use of anti-virus software, and taking proper back up of relevant data.
The term cyber security has been coined under the Indian laws as well. The Information
Technology Act, 20007 defines cybersecurity under section 2(1)(nb)8 as:
This very definition has been adopted under certain other legislative instruments as well,
including the CERT-In Guidelines covered under the Information Technology Act, 2000. There
are many facets of the cyber threats faced by the aviation industry. These take the form of
phishing attacks, jamming attacks, remote hijacking, distributed-denial-of-service attacks and
botnet attacks, along with the Wi-Fi based attacks9. This is majorly due to the hyper-connected
world of Internet of Things (IoT), which has resulted in all kinds of networks to be
interconnected; thereby resulting in higher chances of such instances of cyber-attacks taking
place10.
7 Information Technology Act, 2000
8 Information Technology Act 2000, s2(1)(nb)
9 Dan Virgillito, Cyber Threat Analysis for the Aviation Industry (26 February 2015)
<https://resources.infosecinstitute.com/cyber-threat-analysis-aviation-industry/#gref>
10 Jon Stanford, Air Traffic Control and Industrial Control Systems in the Age of Cybersecurity Threats (15 July
2016) <https://www.hstoday.us/channels/federal-state-local/air-traffic-control-and-industrial-control-systems-in-the-
age-of-cybersecurity-threats/>
pg. 5
The crux of the matter is that the term cyber security is used to refer to the information
technology’s security. The goal is to safeguard the “computers, networks, programs and data”
from unauthorized use and access. The data collected by different entities, be it governments,
hospitals or even military, is not transmitted on another device, without proper approvals. The
sensitive business information and personal information needs to be protected. Similarity, the
nation’s security is protected guarded from the modern day cyber-attacks. There are many types
of actions, which can be taken as a measure to safeguard against such attacks. These include
avoidance of spywares, protecting the passwords, keeping the firewalls turned on, preventing
identity theft, making use of anti-virus software, and taking proper back up of relevant data.
The term cyber security has been coined under the Indian laws as well. The Information
Technology Act, 20007 defines cybersecurity under section 2(1)(nb)8 as:
This very definition has been adopted under certain other legislative instruments as well,
including the CERT-In Guidelines covered under the Information Technology Act, 2000. There
are many facets of the cyber threats faced by the aviation industry. These take the form of
phishing attacks, jamming attacks, remote hijacking, distributed-denial-of-service attacks and
botnet attacks, along with the Wi-Fi based attacks9. This is majorly due to the hyper-connected
world of Internet of Things (IoT), which has resulted in all kinds of networks to be
interconnected; thereby resulting in higher chances of such instances of cyber-attacks taking
place10.
7 Information Technology Act, 2000
8 Information Technology Act 2000, s2(1)(nb)
9 Dan Virgillito, Cyber Threat Analysis for the Aviation Industry (26 February 2015)
<https://resources.infosecinstitute.com/cyber-threat-analysis-aviation-industry/#gref>
10 Jon Stanford, Air Traffic Control and Industrial Control Systems in the Age of Cybersecurity Threats (15 July
2016) <https://www.hstoday.us/channels/federal-state-local/air-traffic-control-and-industrial-control-systems-in-the-
age-of-cybersecurity-threats/>
pg. 5
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

Cyber Security in Aviation
The aviation industry is highly reliant on computer system for its flight and ground
operations. The airlines system security has a direct impact over the efficiency and operational
safety of this industry; along with indirectly affecting its reputation and service11. Thus,
cybersecurity of this industry takes centre stage. This significance was garnered through the very
first airplane hijacking, resulting in huge sum being incurred yearly towards enhancing
the .cybersecurity measures. Even before the occurrence of such incidents, the aspects of
cybersecurity were present and known to this industry, but no significant contributions were
taken towards ensuring cybersecurity. With speculations rising, that disappearance of certain
plane was a result of cyber-attacks, despite the denials from aircraft manufacturers, the focus on
cybersecurity took a bullet train. Such instances, and rumours, coupled with the accelerated
information technologies’ adoption in aviation industry have seen the growth of cybersecurity
sophistication in this industry12.
The very possibility of the vital airplane functions being taken over and the control of
such airplanes being taken over by a third parties, is a key concern, and could result in instances
of hacking the plane. A plane, which has been hacked, can be made to fly at the behest of a third
party, as against the ones responsible for flying such aircraft safely and putting the safety of
crew, passengers and other parties at risk13. The biggest example of this is the September 11
attacks14. This attack resulted in death of 2,996 individuals, where 2,977 victims and 19
hijackers15. Even though this attack was carried on manually, there have been instances where
the breach of cybersecurity measures, have resulted in attacks as well. These will be covered in
the later part of this research.
Just to give an idea of catastrophes surrounding IT failures, the recent instances of flights
being grounded can be looked into. Such recent incidents have shown the cascading losses due to
11 IATA, Aviation Cyber Security Toolkit (2019) <https://www.iata.org/publications/store/Pages/aviation-cyber-
security-toolkit.aspx>
12 Adrie Stander and Jacques Ophoff, ‘Cyber security in civil aviation’ (2016)Imam Journal of Applied Sciences
<http://www.e-ijas.org/temp/ImamJApplSci1123-1857601_050936.pdf>
13 IEEE, Airline CyberSecurity (2019) <http://sites.ieee.org/ocs-cssig/?page_id=875>
14 David Dunbar and Brad Reagan, Debunking 9/11 Myths: Why Conspiracy Theories Can't Stand Up to the Facts :
Includes New Findings on World Trade Center Building 7 (Hearst Books, 2011)
15 Arthur Berm, When Reality Hits: From WW II to the New World Order (FriesenPress, 2014)
pg. 6
The aviation industry is highly reliant on computer system for its flight and ground
operations. The airlines system security has a direct impact over the efficiency and operational
safety of this industry; along with indirectly affecting its reputation and service11. Thus,
cybersecurity of this industry takes centre stage. This significance was garnered through the very
first airplane hijacking, resulting in huge sum being incurred yearly towards enhancing
the .cybersecurity measures. Even before the occurrence of such incidents, the aspects of
cybersecurity were present and known to this industry, but no significant contributions were
taken towards ensuring cybersecurity. With speculations rising, that disappearance of certain
plane was a result of cyber-attacks, despite the denials from aircraft manufacturers, the focus on
cybersecurity took a bullet train. Such instances, and rumours, coupled with the accelerated
information technologies’ adoption in aviation industry have seen the growth of cybersecurity
sophistication in this industry12.
The very possibility of the vital airplane functions being taken over and the control of
such airplanes being taken over by a third parties, is a key concern, and could result in instances
of hacking the plane. A plane, which has been hacked, can be made to fly at the behest of a third
party, as against the ones responsible for flying such aircraft safely and putting the safety of
crew, passengers and other parties at risk13. The biggest example of this is the September 11
attacks14. This attack resulted in death of 2,996 individuals, where 2,977 victims and 19
hijackers15. Even though this attack was carried on manually, there have been instances where
the breach of cybersecurity measures, have resulted in attacks as well. These will be covered in
the later part of this research.
Just to give an idea of catastrophes surrounding IT failures, the recent instances of flights
being grounded can be looked into. Such recent incidents have shown the cascading losses due to
11 IATA, Aviation Cyber Security Toolkit (2019) <https://www.iata.org/publications/store/Pages/aviation-cyber-
security-toolkit.aspx>
12 Adrie Stander and Jacques Ophoff, ‘Cyber security in civil aviation’ (2016)Imam Journal of Applied Sciences
<http://www.e-ijas.org/temp/ImamJApplSci1123-1857601_050936.pdf>
13 IEEE, Airline CyberSecurity (2019) <http://sites.ieee.org/ocs-cssig/?page_id=875>
14 David Dunbar and Brad Reagan, Debunking 9/11 Myths: Why Conspiracy Theories Can't Stand Up to the Facts :
Includes New Findings on World Trade Center Building 7 (Hearst Books, 2011)
15 Arthur Berm, When Reality Hits: From WW II to the New World Order (FriesenPress, 2014)
pg. 6
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Cyber Security in Aviation
IT system failures. The cancellation of two US airlines in 2016 caused major disruptions in
booking programmes and even saw the cancellations of various flights. Even though these
instances where not as a result of malware or hacking issues, still they provide insights on the
costs and level of disruption associated with such failures. Even though the actual losses from
these two cancellations were not made common knowledge, the experts have put in the estimates
between US$ 80 million and 150 million each. A basic human error resulted in nearly seventy
five thousand passengers being stranded in May 2017, that too on a busy public holiday
weekend, resulting in the British flag carrier bearing losses of nearly £80 million. This amount
does not include the cost of reputation damage16.
1.2. Introduction to Aviation
Air transport, or aviation, in the most basic sense refers to such activities, which are
present in the aircraft industry and are related to mechanical flight. Its history can be traced back
to the age of hot air balloons, to moving on to Wright brothers’ invention of airplanes, and to the
modern day aircrafts and jets17. Aviation is what connects the present communities, across the
globe, as it helps individuals in moving to places in a fast manner. The present decade is
experiencing a sharp rise in the unmanned and manned aircrafts and their systems, where there is
constant focus on bringing in new features, along with creating unprecedented applications. The
role of information technology, software and computer networks, i.e. cyber technology is
fundamental and crucial for advancement of aviation. The reason for it is that these cyber
technologies help in fulfilling the needs of ecosystem of aviation, including that of pilots,
aircraft, passengers, society, personnel and stakeholders18.
There is a growing use of aviation cyber technology in varied aspects of air travel,
including booking of tickets, airline counter checking in, clearing airport security, in-flight
entertainment and connecting to Wi-Fi in aircraft cabins. However, majority of the advancements
take place back space, including the air traffic control, airports (including the ones in space, on
16 Helga Munger, Cyber threats in aviation The sky’s the limit? (17 September 2018)
<https://www.munichre.com/topics-online/en/digitalisation/cyber/cyber-threats-in-aviation.html>
17 Dawna L. Rhoades, Evolution of International Aviation: Phoenix Rising (Routledge, 2016)
18 Jon C. Haass, Krishna Sampigethaya, and Vincent Capezzuto, ‘Aviation and Cybersecurity: Opportunities for
Applied Research’ (2016) TR News (304) <http://commons.erau.edu/publication/299>
pg. 7
IT system failures. The cancellation of two US airlines in 2016 caused major disruptions in
booking programmes and even saw the cancellations of various flights. Even though these
instances where not as a result of malware or hacking issues, still they provide insights on the
costs and level of disruption associated with such failures. Even though the actual losses from
these two cancellations were not made common knowledge, the experts have put in the estimates
between US$ 80 million and 150 million each. A basic human error resulted in nearly seventy
five thousand passengers being stranded in May 2017, that too on a busy public holiday
weekend, resulting in the British flag carrier bearing losses of nearly £80 million. This amount
does not include the cost of reputation damage16.
1.2. Introduction to Aviation
Air transport, or aviation, in the most basic sense refers to such activities, which are
present in the aircraft industry and are related to mechanical flight. Its history can be traced back
to the age of hot air balloons, to moving on to Wright brothers’ invention of airplanes, and to the
modern day aircrafts and jets17. Aviation is what connects the present communities, across the
globe, as it helps individuals in moving to places in a fast manner. The present decade is
experiencing a sharp rise in the unmanned and manned aircrafts and their systems, where there is
constant focus on bringing in new features, along with creating unprecedented applications. The
role of information technology, software and computer networks, i.e. cyber technology is
fundamental and crucial for advancement of aviation. The reason for it is that these cyber
technologies help in fulfilling the needs of ecosystem of aviation, including that of pilots,
aircraft, passengers, society, personnel and stakeholders18.
There is a growing use of aviation cyber technology in varied aspects of air travel,
including booking of tickets, airline counter checking in, clearing airport security, in-flight
entertainment and connecting to Wi-Fi in aircraft cabins. However, majority of the advancements
take place back space, including the air traffic control, airports (including the ones in space, on
16 Helga Munger, Cyber threats in aviation The sky’s the limit? (17 September 2018)
<https://www.munichre.com/topics-online/en/digitalisation/cyber/cyber-threats-in-aviation.html>
17 Dawna L. Rhoades, Evolution of International Aviation: Phoenix Rising (Routledge, 2016)
18 Jon C. Haass, Krishna Sampigethaya, and Vincent Capezzuto, ‘Aviation and Cybersecurity: Opportunities for
Applied Research’ (2016) TR News (304) <http://commons.erau.edu/publication/299>
pg. 7

Cyber Security in Aviation
the ground and airborne), infrastructure in avionics and airlines. There is a deep integration of
cyber tech in time critical fabric, which assures and controls the performance, operations and
safety of aviation19.
Even with the high profits, which are expected and earned, the reliance on cyber
technology exposes aviation industry to costly and dangerous world of threats. There have been
many threats made in this industry, resulting in the industry maturing its operations towards such
threats; this is in addition to the physical difficulties faced by aviation from humankind and
nature. It is also crucial to state here that saving of a single flight, or apprehending two or three
events are not enough to ensure that the threats and risks on performance and safety of aviation
industry, are managed. The cybersecurity threats are a major concern and the unpredictable
nature of such attacks make the comprehension of such risks, a difficult task. Apart from this, the
opportunities are ever rising, with the growth and development of systems and new services20.
The reason why so much emphasis is given on the aviation industry is because it acts as
the key foundation towards investments, international trade and tourism, along with being
significant towards the development of global economy. 3.5% of the GRP (Gross Domestic
Product) or 2.7 trillion dollars ride on the back of air transport industry, along with provided 9.9
million direct jobs to individuals across the globe. It has been forecasted that by the end of 2034,
the airfreight and the air passenger traffic is set to be the double of 2016 figures. It is projected
that airfreight will see a growth of 4.2% on annual basis, and would reach 466 billion FTKs
(Freight Tonne-Kilometres). It has also been estimated that the passenger traffic would see a
growth of 4.5% on annual basis, and would reach 14 trillion RPKs (Revenue Passengeer-
Kilometres)21.
Thus, the size of this industry puts forth the need for paying heed to the cyber threats
brought with the increase digitalization. Even though digitalization has increased interoperability
and intelligence on one hand, this has on the other hand brought major risks with it. There is a
19 Ibid
20 Ibid
21 Georgia Lykou, George Iakovakis, and Dimitris Gritzalis, ‘Aviation Cybersecurity and Cyber-Resilience:
Assessing Risk in Air Traffic Management’ (2019) Critical Infrastructure Security and Resilience <http://sci-
hub.tw/10.1007/978-3-030-00024-0_13>
pg. 8
the ground and airborne), infrastructure in avionics and airlines. There is a deep integration of
cyber tech in time critical fabric, which assures and controls the performance, operations and
safety of aviation19.
Even with the high profits, which are expected and earned, the reliance on cyber
technology exposes aviation industry to costly and dangerous world of threats. There have been
many threats made in this industry, resulting in the industry maturing its operations towards such
threats; this is in addition to the physical difficulties faced by aviation from humankind and
nature. It is also crucial to state here that saving of a single flight, or apprehending two or three
events are not enough to ensure that the threats and risks on performance and safety of aviation
industry, are managed. The cybersecurity threats are a major concern and the unpredictable
nature of such attacks make the comprehension of such risks, a difficult task. Apart from this, the
opportunities are ever rising, with the growth and development of systems and new services20.
The reason why so much emphasis is given on the aviation industry is because it acts as
the key foundation towards investments, international trade and tourism, along with being
significant towards the development of global economy. 3.5% of the GRP (Gross Domestic
Product) or 2.7 trillion dollars ride on the back of air transport industry, along with provided 9.9
million direct jobs to individuals across the globe. It has been forecasted that by the end of 2034,
the airfreight and the air passenger traffic is set to be the double of 2016 figures. It is projected
that airfreight will see a growth of 4.2% on annual basis, and would reach 466 billion FTKs
(Freight Tonne-Kilometres). It has also been estimated that the passenger traffic would see a
growth of 4.5% on annual basis, and would reach 14 trillion RPKs (Revenue Passengeer-
Kilometres)21.
Thus, the size of this industry puts forth the need for paying heed to the cyber threats
brought with the increase digitalization. Even though digitalization has increased interoperability
and intelligence on one hand, this has on the other hand brought major risks with it. There is a
19 Ibid
20 Ibid
21 Georgia Lykou, George Iakovakis, and Dimitris Gritzalis, ‘Aviation Cybersecurity and Cyber-Resilience:
Assessing Risk in Air Traffic Management’ (2019) Critical Infrastructure Security and Resilience <http://sci-
hub.tw/10.1007/978-3-030-00024-0_13>
pg. 8
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

Cyber Security in Aviation
need to have a high level of awareness and attention of the potential cyber threat’s future
development. The goal here needs to be to bring down the vulnerability of cyber related risks,
along with strengthening of “the air transportation systems’ resilience” in contradiction of such
cyber threats22. Thus is crucial to make certain that the industry continues to be safe, and is able
to continue contributing to economy, as was highlighted through the figures presented earlier.
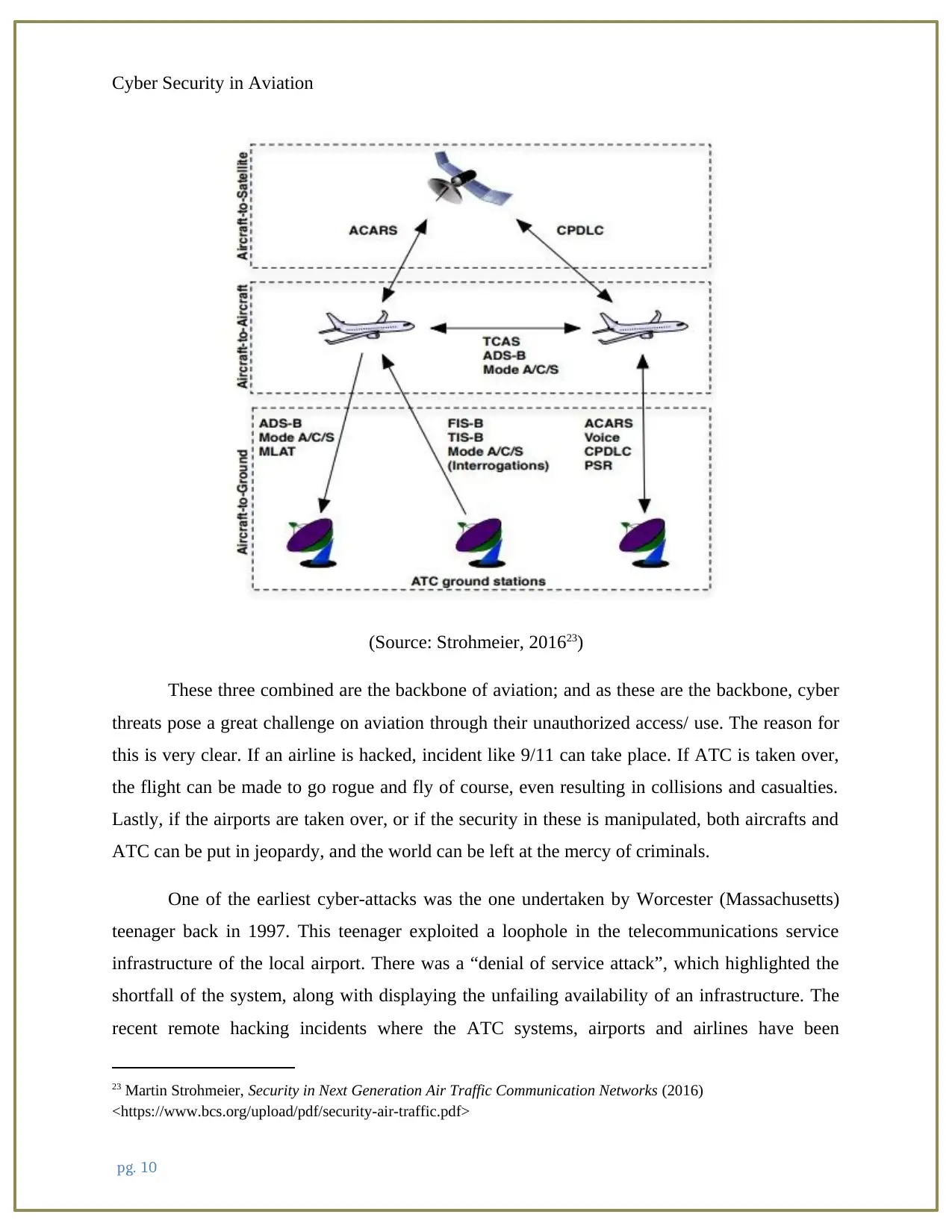
1.3. Introduction to Cyber Security in Aviation - Airlines, ATC and Airports
There are three key pillars of aviation industry, i.e. the airlines, the ATC (Air Traffic
Control), and the airports. The airlines are the flights and are the medium of air travel; the
airports are where the airlines are made available; and the ATC is the service that the ground
based air traffic controllers provide for directing the flights. ATC covers the communications
with the aircraft for assisting in maintaining separation. This ensures that the aircraft is far
enough (be it vertically or horizontally), to pose no risk of collision. A depiction of ATC,
covering how wireless technology is used in ATC between satellites, aircraft and ground station,
is covered below. Each of the arrows shows the communication direction for every protocol.
22 Ibid
pg. 9
need to have a high level of awareness and attention of the potential cyber threat’s future
development. The goal here needs to be to bring down the vulnerability of cyber related risks,
along with strengthening of “the air transportation systems’ resilience” in contradiction of such
cyber threats22. Thus is crucial to make certain that the industry continues to be safe, and is able
to continue contributing to economy, as was highlighted through the figures presented earlier.
1.3. Introduction to Cyber Security in Aviation - Airlines, ATC and Airports
There are three key pillars of aviation industry, i.e. the airlines, the ATC (Air Traffic
Control), and the airports. The airlines are the flights and are the medium of air travel; the
airports are where the airlines are made available; and the ATC is the service that the ground
based air traffic controllers provide for directing the flights. ATC covers the communications
with the aircraft for assisting in maintaining separation. This ensures that the aircraft is far
enough (be it vertically or horizontally), to pose no risk of collision. A depiction of ATC,
covering how wireless technology is used in ATC between satellites, aircraft and ground station,
is covered below. Each of the arrows shows the communication direction for every protocol.
22 Ibid
pg. 9
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
Cyber Security in Aviation
(Source: Strohmeier, 201623)
These three combined are the backbone of aviation; and as these are the backbone, cyber
threats pose a great challenge on aviation through their unauthorized access/ use. The reason for
this is very clear. If an airline is hacked, incident like 9/11 can take place. If ATC is taken over,
the flight can be made to go rogue and fly of course, even resulting in collisions and casualties.
Lastly, if the airports are taken over, or if the security in these is manipulated, both aircrafts and
ATC can be put in jeopardy, and the world can be left at the mercy of criminals.
One of the earliest cyber-attacks was the one undertaken by Worcester (Massachusetts)
teenager back in 1997. This teenager exploited a loophole in the telecommunications service
infrastructure of the local airport. There was a “denial of service attack”, which highlighted the
shortfall of the system, along with displaying the unfailing availability of an infrastructure. The
recent remote hacking incidents where the ATC systems, airports and airlines have been
23 Martin Strohmeier, Security in Next Generation Air Traffic Communication Networks (2016)
<https://www.bcs.org/upload/pdf/security-air-traffic.pdf>
pg. 10
(Source: Strohmeier, 201623)
These three combined are the backbone of aviation; and as these are the backbone, cyber
threats pose a great challenge on aviation through their unauthorized access/ use. The reason for
this is very clear. If an airline is hacked, incident like 9/11 can take place. If ATC is taken over,
the flight can be made to go rogue and fly of course, even resulting in collisions and casualties.
Lastly, if the airports are taken over, or if the security in these is manipulated, both aircrafts and
ATC can be put in jeopardy, and the world can be left at the mercy of criminals.
One of the earliest cyber-attacks was the one undertaken by Worcester (Massachusetts)
teenager back in 1997. This teenager exploited a loophole in the telecommunications service
infrastructure of the local airport. There was a “denial of service attack”, which highlighted the
shortfall of the system, along with displaying the unfailing availability of an infrastructure. The
recent remote hacking incidents where the ATC systems, airports and airlines have been
23 Martin Strohmeier, Security in Next Generation Air Traffic Communication Networks (2016)
<https://www.bcs.org/upload/pdf/security-air-traffic.pdf>
pg. 10

Cyber Security in Aviation
targeted, highlight that the cyber risks are constantly evolving, where the crew, baggage control
systems, airport passport control and airlines passengers are targeted frequently24.
Over seventy-five airports in US reports phishing emails in 2013, where the goal was
defrauding users, so that their financial information was revealed. The very same year saw over
twenty thousand-hack attempts on daily basis on Miami International Airport. There were around
2.9 million hacking attempts and over sixty thousand internet misuse attempts blocked by Los
Angeles World airports. A Tunisian hacking team targeted computer and communication
systems of US airport in 2014. LOT Polish Airlines saw the flights being grounded in summer of
2015 at Warsaw airport as a result of hackers disabling the flight plans meant for the outbound
aircraft. There have been some cyber advances that have helped in operations of this industry,
including the use of commercial technologies (like internet protocols, virtualization, cloud
computing, GPS and Wi-Fi). These have contributed to the faster, interoperable and cheaper
aviation systems across the globe; but their inherent vulnerabilities are often take advantage of
by the cyber adversaries25.
The powerful, open sourced and cheap tools allow for such vulnerabilities to be exploited
with ease, making the occurrence of cyber-attacks far less complicated. A leading example of
this is the White Sands Missile Range test exercise, which clearly highlighted the possibility of
accessing drones and unmanned aircrafts through use of GPS signals. These can be used to
access these devices remotely and to guide such devices into erroneous paths. There has also
been a reiteration of feasibility of attacking ATC systems through use of cheap equipment, at the
hacker conferences’ simulation studies. A cyber-attack could be undertaken in a way where the
ATC controllers and pilots see a bogus aircraft on their screens, resulting in unwarranted
performance losses and unsafe actions being undertaken. Apart from this, one of the recent
instances where a suicide pilot (as per allegations) crashed the Germanwings flight, showing the
possibility of insider threats. This further emphasizes on the need for bringing improvement in
people management, particularly when entrusted with authorized access to ATC systems26.
24 At 18 (Jon C. Haass)
25 Ibid
26 Ibid
pg. 11
targeted, highlight that the cyber risks are constantly evolving, where the crew, baggage control
systems, airport passport control and airlines passengers are targeted frequently24.
Over seventy-five airports in US reports phishing emails in 2013, where the goal was
defrauding users, so that their financial information was revealed. The very same year saw over
twenty thousand-hack attempts on daily basis on Miami International Airport. There were around
2.9 million hacking attempts and over sixty thousand internet misuse attempts blocked by Los
Angeles World airports. A Tunisian hacking team targeted computer and communication
systems of US airport in 2014. LOT Polish Airlines saw the flights being grounded in summer of
2015 at Warsaw airport as a result of hackers disabling the flight plans meant for the outbound
aircraft. There have been some cyber advances that have helped in operations of this industry,
including the use of commercial technologies (like internet protocols, virtualization, cloud
computing, GPS and Wi-Fi). These have contributed to the faster, interoperable and cheaper
aviation systems across the globe; but their inherent vulnerabilities are often take advantage of
by the cyber adversaries25.
The powerful, open sourced and cheap tools allow for such vulnerabilities to be exploited
with ease, making the occurrence of cyber-attacks far less complicated. A leading example of
this is the White Sands Missile Range test exercise, which clearly highlighted the possibility of
accessing drones and unmanned aircrafts through use of GPS signals. These can be used to
access these devices remotely and to guide such devices into erroneous paths. There has also
been a reiteration of feasibility of attacking ATC systems through use of cheap equipment, at the
hacker conferences’ simulation studies. A cyber-attack could be undertaken in a way where the
ATC controllers and pilots see a bogus aircraft on their screens, resulting in unwarranted
performance losses and unsafe actions being undertaken. Apart from this, one of the recent
instances where a suicide pilot (as per allegations) crashed the Germanwings flight, showing the
possibility of insider threats. This further emphasizes on the need for bringing improvement in
people management, particularly when entrusted with authorized access to ATC systems26.
24 At 18 (Jon C. Haass)
25 Ibid
26 Ibid
pg. 11
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 115
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2025 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.