Aztek: IT Risk Management of Bring Your Own Devices (BYOD) Project
VerifiedAdded on 2020/03/04
|18
|4571
|103
Report
AI Summary
This report provides a comprehensive risk assessment for Aztek, an Australian financial services company, focusing on its Bring Your Own Devices (BYOD) project. It examines potential risks across information, database, network, and device security. The report includes an executive summary, an introduction to Aztek's financial services, a project overview, and a financial review. It details the project's impact on the current security infrastructure, conducts a thorough risk assessment, outlines the risk management process, and presents a risk register. The report emphasizes data security measures and provides recommendations such as advanced access control, multi-factor authentication, and the use of automated security tools. It also addresses the importance of network security upgrades and the need to restrict access to sensitive information outside the office. The report aims to provide a strategic framework for Aztek to mitigate potential risks and ensure the successful implementation of the BYOD project.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Aztek – Risk Assessment & Management
Executive Summary
Aztek is an Australian company that provides its customers with the financial services and solutions.
With the expansion of the number of customers and clients, the requirements that Aztek needs to fulfill is
also increasing at the same pace. To fulfill the increasing demand and maintain the expansion of the
organization, there are various recommendations that have been put forward by the senior officials at
Aztek. Out of the several different projects that have been proposed by the senior administration at Aztek,
the one that has been selected for implementation is Bring Your Own Devices (BYOD). With this project,
there are many risks that may emerge in the areas of information security, database security, network
security, device security and many others. The report covers the risk assessment of the risks associated
with Aztek along with the financial review, security review and the risk register. The information of data
security has also been covered in the report.
Findings and Recommendations
The risks that have been identified and assessed for Aztek belong to the data and information risks along
with the risks associated with the devices and the networks (Cioupdate, 2016).
There are various countermeasures that have been recommended to put a check on all such risks and
threats. One of the basic measures that have been suggested is the advanced access control and
authentication. There are many access control mechanisms that have been created such as role based
access control, attribute based access control and many more. These access control mechanisms shall be
applied in Aztek so that the users that are privileged to access the information are provided with the
access for the same. These access control schemes shall be made applicable on all the services and the
applications that are installed on the devices of the employees.
There are also various measures that have been developed in the area of identity management and
authentication. These measures shall include multi-fold authentication with the use of mechanisms such
as One Time Passwords (OTPs) and biometric identification. The combination of these measures will
make sure that only the authorized users have the authentication and authorization to access the
information. The use of the company tools and applications by the family members and the friends of the
employees will be avoided with this practice and control measure.
There are numerous technical and logical advancements that have been coming up in the area of security.
These advancements shall be utilized for the maintenance and protection of the security of all the assets of
the organization.
2
Executive Summary
Aztek is an Australian company that provides its customers with the financial services and solutions.
With the expansion of the number of customers and clients, the requirements that Aztek needs to fulfill is
also increasing at the same pace. To fulfill the increasing demand and maintain the expansion of the
organization, there are various recommendations that have been put forward by the senior officials at
Aztek. Out of the several different projects that have been proposed by the senior administration at Aztek,
the one that has been selected for implementation is Bring Your Own Devices (BYOD). With this project,
there are many risks that may emerge in the areas of information security, database security, network
security, device security and many others. The report covers the risk assessment of the risks associated
with Aztek along with the financial review, security review and the risk register. The information of data
security has also been covered in the report.
Findings and Recommendations
The risks that have been identified and assessed for Aztek belong to the data and information risks along
with the risks associated with the devices and the networks (Cioupdate, 2016).
There are various countermeasures that have been recommended to put a check on all such risks and
threats. One of the basic measures that have been suggested is the advanced access control and
authentication. There are many access control mechanisms that have been created such as role based
access control, attribute based access control and many more. These access control mechanisms shall be
applied in Aztek so that the users that are privileged to access the information are provided with the
access for the same. These access control schemes shall be made applicable on all the services and the
applications that are installed on the devices of the employees.
There are also various measures that have been developed in the area of identity management and
authentication. These measures shall include multi-fold authentication with the use of mechanisms such
as One Time Passwords (OTPs) and biometric identification. The combination of these measures will
make sure that only the authorized users have the authentication and authorization to access the
information. The use of the company tools and applications by the family members and the friends of the
employees will be avoided with this practice and control measure.
There are numerous technical and logical advancements that have been coming up in the area of security.
These advancements shall be utilized for the maintenance and protection of the security of all the assets of
the organization.
2

Aztek – Risk Assessment & Management
There are advanced and automated tools that have been developed such as data analytics tools for
detecting the patterns and trends that are associated with the attacks. There are also tools for the detection
and prevention of the intruders. Also, there are automated tools for the monitoring and control of the
network activities and operations. It is necessary to maintain the logs as well for making sure that the
security of the services and applications is ensured. These logs will be captured automatically by these
tools which will then be analyzed by the analytics tools.
There are tools that have been developed for the backing up of the data along with the recovery of the
data in case of an attack.
Encryption of the information is another measure that shall be ensured so that the attackers do not succeed
in making use of the data and information at any time. There are various algorithms that are present for
the encryption of information such as advanced encryption algorithm. These shall be used and applied
across all the data and information sets.
3
There are advanced and automated tools that have been developed such as data analytics tools for
detecting the patterns and trends that are associated with the attacks. There are also tools for the detection
and prevention of the intruders. Also, there are automated tools for the monitoring and control of the
network activities and operations. It is necessary to maintain the logs as well for making sure that the
security of the services and applications is ensured. These logs will be captured automatically by these
tools which will then be analyzed by the analytics tools.
There are tools that have been developed for the backing up of the data along with the recovery of the
data in case of an attack.
Encryption of the information is another measure that shall be ensured so that the attackers do not succeed
in making use of the data and information at any time. There are various algorithms that are present for
the encryption of information such as advanced encryption algorithm. These shall be used and applied
across all the data and information sets.
3
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

Aztek – Risk Assessment & Management
Executive Summary.....................................................................................................................................2
Introduction.................................................................................................................................................5
Organization Description.........................................................................................................................5
Project Overview.....................................................................................................................................5
Financial Services Review...........................................................................................................................5
Project Description from Financial Perspective.......................................................................................6
Project Impact on Current Security Infrastructure.......................................................................................7
Risk Assessment..........................................................................................................................................9
Risk Management Process.......................................................................................................................9
Risk Register.........................................................................................................................................10
Data Security.............................................................................................................................................13
Conclusion.................................................................................................................................................14
References.................................................................................................................................................16
4
Executive Summary.....................................................................................................................................2
Introduction.................................................................................................................................................5
Organization Description.........................................................................................................................5
Project Overview.....................................................................................................................................5
Financial Services Review...........................................................................................................................5
Project Description from Financial Perspective.......................................................................................6
Project Impact on Current Security Infrastructure.......................................................................................7
Risk Assessment..........................................................................................................................................9
Risk Management Process.......................................................................................................................9
Risk Register.........................................................................................................................................10
Data Security.............................................................................................................................................13
Conclusion.................................................................................................................................................14
References.................................................................................................................................................16
4
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Aztek – Risk Assessment & Management
Introduction
Organization Description
Finance industry of any country is extremely critical for it in terms of the economical growth and
management of the same. There are various organizations that are present in Australia that work
in the area of financial services and solutions and one such organization is Aztek. With the
expansion of the number of customers and clients, the requirements that Aztek needs to fulfill is
also increasing at the same pace. The financial information that is associated with any of the
services that the organization provides is extremely critical and sensitive in nature. There is a
great deal of security and safety that is necessary to ensure that the financial information and the
information of the users and employees at Aztek are always protected. There are various
projects that have been proposed by the senior administration of Aztek to support the expansion
of the organization and one such initiative is to allow the members of the staff to bring their
personal devices at work for the execution of professional activities.
The report is a risk assessment report for the project that covers various aspects of the same.
Project Overview
Out of the several different projects that have been proposed by the senior administration at
Aztek, the one that has been selected for implementation is Bring Your Own Devices (BYOD).
There are various devices that the members of the staff at Aztek own such as Smartphones,
laptops, tablets, speakers and many others. In case of the procurement of these devices by the
third-parties and providing them to the employees, there would be a large share of cost that
would be involved in the process. However, with the aid of BYOD, the project will assist the
expansion phase of Aztek as the costs will be utilized in the expansion process.
Financial Services Review
Aztek is an organization that provides the financial services to the customers in Australia and
beyond. The financial information is always sensitive and critical in nature and it becomes
necessary to regulate and monitor the same with the aid of regulatory bodies. In Australia,
Australian Securities and Investments Commission (ASIC) is a body that is responsible for the
5
Introduction
Organization Description
Finance industry of any country is extremely critical for it in terms of the economical growth and
management of the same. There are various organizations that are present in Australia that work
in the area of financial services and solutions and one such organization is Aztek. With the
expansion of the number of customers and clients, the requirements that Aztek needs to fulfill is
also increasing at the same pace. The financial information that is associated with any of the
services that the organization provides is extremely critical and sensitive in nature. There is a
great deal of security and safety that is necessary to ensure that the financial information and the
information of the users and employees at Aztek are always protected. There are various
projects that have been proposed by the senior administration of Aztek to support the expansion
of the organization and one such initiative is to allow the members of the staff to bring their
personal devices at work for the execution of professional activities.
The report is a risk assessment report for the project that covers various aspects of the same.
Project Overview
Out of the several different projects that have been proposed by the senior administration at
Aztek, the one that has been selected for implementation is Bring Your Own Devices (BYOD).
There are various devices that the members of the staff at Aztek own such as Smartphones,
laptops, tablets, speakers and many others. In case of the procurement of these devices by the
third-parties and providing them to the employees, there would be a large share of cost that
would be involved in the process. However, with the aid of BYOD, the project will assist the
expansion phase of Aztek as the costs will be utilized in the expansion process.
Financial Services Review
Aztek is an organization that provides the financial services to the customers in Australia and
beyond. The financial information is always sensitive and critical in nature and it becomes
necessary to regulate and monitor the same with the aid of regulatory bodies. In Australia,
Australian Securities and Investments Commission (ASIC) is a body that is responsible for the
5

Aztek – Risk Assessment & Management
regulation of all the financial activities along with the payments and adherence to the best
practices.
The project of BYOD that will be implemented in Aztek will be required to adhere to the
guidelines as specified under the policies of ASIC.
In the services that will be provided by Aztek, there will also be many electronic payments that
will be involved. All such payments will be reviewed, inspected and managed with the aid of an
e-Payments code that has been stated by ASIC.
There are Intellectual property guidelines that have also been stated by the Australian
Government which shall be complied at all times and in all of the project activities.
Project Description from Financial Perspective
Aztek has a set of organizational goals and objectives which are listed below.
To provide the best quality financial services to the customers in minimum amount of
time with greater accuracy.
To gain better employee satisfaction and to implement strategies for better employee
engagement.
To gain better customer satisfaction and to implement strategies for better customer
engagement.
To stick to the budget that has been estimated for the projects.
There will be many different activities and tasks that will be made possible with the
implementation of BYOD which will align with the organizational goals as well.
BYOD will provide the employees with the opportunity to make use of the devices that
they are already familiar with. This will enhance the productivity levels of the employees
and the level of their satisfaction with the organization will also go up.
The employees will be able to perform better which will make them capable to fulfill the
customer expectations and as a result, customer engagement will improve.
BYOD will cut down on the costs associated with the devices and their maintenance
which would allow the maintenance of the estimated budget.
6
regulation of all the financial activities along with the payments and adherence to the best
practices.
The project of BYOD that will be implemented in Aztek will be required to adhere to the
guidelines as specified under the policies of ASIC.
In the services that will be provided by Aztek, there will also be many electronic payments that
will be involved. All such payments will be reviewed, inspected and managed with the aid of an
e-Payments code that has been stated by ASIC.
There are Intellectual property guidelines that have also been stated by the Australian
Government which shall be complied at all times and in all of the project activities.
Project Description from Financial Perspective
Aztek has a set of organizational goals and objectives which are listed below.
To provide the best quality financial services to the customers in minimum amount of
time with greater accuracy.
To gain better employee satisfaction and to implement strategies for better employee
engagement.
To gain better customer satisfaction and to implement strategies for better customer
engagement.
To stick to the budget that has been estimated for the projects.
There will be many different activities and tasks that will be made possible with the
implementation of BYOD which will align with the organizational goals as well.
BYOD will provide the employees with the opportunity to make use of the devices that
they are already familiar with. This will enhance the productivity levels of the employees
and the level of their satisfaction with the organization will also go up.
The employees will be able to perform better which will make them capable to fulfill the
customer expectations and as a result, customer engagement will improve.
BYOD will cut down on the costs associated with the devices and their maintenance
which would allow the maintenance of the estimated budget.
6
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

Aztek – Risk Assessment & Management
The project will offer many benefits to the employees of Aztek and to the entire organization as
well.
The employees will have the ability to carry out dummy tasks and activities at any
location before the actual execution of the project activities. In this way, the employees
will come to know about the common risks and mistakes that may occur and the same
will be avoided in the project life cycle.
The devices owned by the employees will be installed with the reporting tools and the
email engine of the organization which will keep them connected with their respective
project team and management at all times (Gessner, 2016).
There are many tools that are normally required during the testing activities. With the aid
of BYOD, the need to procure such devices will be avoided and the employees will be
able to test the project related activities from the office or any other location.
There are many other organizational tools that have been developed for easier tracking
and management of the resources which will be installed on the devices of the employees
(Retailwire, 2016).
BYOD is a project that will be suitable and applicable for the aspect of the budget and finances
that are associated with the organization. Also, it would be feasible to stick to the set of
guidelines and best practices as stated by the Australian Government and regulatory bodies.
Project Impact on Current Security Infrastructure
There are many risks that are associated with the project of the implementation of BYOD in
Aztek. Every attack that will be possible and connected with Aztek will have a threat agent
mapped with it. These agents may be the networks that will be used by the employees on their
device, the employees themselves, application interfaces and databases that will be used and
many more. All of such risks and issues will be required to be handled with a suitable security
plan and strategy.
The current security policy and infrastructure that is followed in Aztek does not cover the risks
that are associated with BYOD. It is because of the reason that such a project is being
implemented for the first time in the organization. As an impact, there would be many updates
that will be required to be made to the security strategy and infrastructure.
7
The project will offer many benefits to the employees of Aztek and to the entire organization as
well.
The employees will have the ability to carry out dummy tasks and activities at any
location before the actual execution of the project activities. In this way, the employees
will come to know about the common risks and mistakes that may occur and the same
will be avoided in the project life cycle.
The devices owned by the employees will be installed with the reporting tools and the
email engine of the organization which will keep them connected with their respective
project team and management at all times (Gessner, 2016).
There are many tools that are normally required during the testing activities. With the aid
of BYOD, the need to procure such devices will be avoided and the employees will be
able to test the project related activities from the office or any other location.
There are many other organizational tools that have been developed for easier tracking
and management of the resources which will be installed on the devices of the employees
(Retailwire, 2016).
BYOD is a project that will be suitable and applicable for the aspect of the budget and finances
that are associated with the organization. Also, it would be feasible to stick to the set of
guidelines and best practices as stated by the Australian Government and regulatory bodies.
Project Impact on Current Security Infrastructure
There are many risks that are associated with the project of the implementation of BYOD in
Aztek. Every attack that will be possible and connected with Aztek will have a threat agent
mapped with it. These agents may be the networks that will be used by the employees on their
device, the employees themselves, application interfaces and databases that will be used and
many more. All of such risks and issues will be required to be handled with a suitable security
plan and strategy.
The current security policy and infrastructure that is followed in Aztek does not cover the risks
that are associated with BYOD. It is because of the reason that such a project is being
implemented for the first time in the organization. As an impact, there would be many updates
that will be required to be made to the security strategy and infrastructure.
7
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Aztek – Risk Assessment & Management
The primary step that will be necessary to take will include the up-gradation of security as per
the new sets of the risks and security threats that are identified. The devices that the employees
may bring in the organization may already be affected and injected by several different malware.
It would be necessary to develop the measures to identify the malware and prevent their attack
on the system and information associated with the organization. The employee devices shall be
marked with an identification to make sure that it is approved by the security team and there
shall be anti-viruses and anti-malware that shall be installed in the devices that are brought by the
employees.
Most of the attacks on the security that normally take place make use of the networks as the
primary threat agents. It will therefore be required for Aztek to upgrade the network security
scheme that is currently implemented in its security architecture. Network security has seen
many advancement and developments in the recent times. There are newer and advanced tools
that have been released in the market for the safety and protection of the networks. Such tools
such as network based security systems, intrusion detection tools and monitoring applications
shall be installed across the networks that are implemented in Aztek (Coleman, 2011).
The devices that will be owned by the employees will be used by them outside of the office
location as well. This will again put the information and the devices at risk of the network
security attacks. Some of the critical information and the applications with sensitive data must
not be accessible by the employees outside of office. There can be another option that may be
followed by the setting up of a virtual private network for avoiding such attacks (Newton, 2015).
The probability of the insider threats and attacks will also increase with the implementation of
BYOD in Aztek. It is because of the reason that the employees will gain the privilege to make
use of the organizational tools, applications and information at any location. These attacks may
be deliberate or may also be accidental in nature (Trendmicro, 2016).
Respective security strategies will be necessary to be included in the security infrastructure for
the deliberate and accidental insider attacks. The measures will be stated and involved in the
security plans and the same will be required to be communicated to the entire security team as
well.
8
The primary step that will be necessary to take will include the up-gradation of security as per
the new sets of the risks and security threats that are identified. The devices that the employees
may bring in the organization may already be affected and injected by several different malware.
It would be necessary to develop the measures to identify the malware and prevent their attack
on the system and information associated with the organization. The employee devices shall be
marked with an identification to make sure that it is approved by the security team and there
shall be anti-viruses and anti-malware that shall be installed in the devices that are brought by the
employees.
Most of the attacks on the security that normally take place make use of the networks as the
primary threat agents. It will therefore be required for Aztek to upgrade the network security
scheme that is currently implemented in its security architecture. Network security has seen
many advancement and developments in the recent times. There are newer and advanced tools
that have been released in the market for the safety and protection of the networks. Such tools
such as network based security systems, intrusion detection tools and monitoring applications
shall be installed across the networks that are implemented in Aztek (Coleman, 2011).
The devices that will be owned by the employees will be used by them outside of the office
location as well. This will again put the information and the devices at risk of the network
security attacks. Some of the critical information and the applications with sensitive data must
not be accessible by the employees outside of office. There can be another option that may be
followed by the setting up of a virtual private network for avoiding such attacks (Newton, 2015).
The probability of the insider threats and attacks will also increase with the implementation of
BYOD in Aztek. It is because of the reason that the employees will gain the privilege to make
use of the organizational tools, applications and information at any location. These attacks may
be deliberate or may also be accidental in nature (Trendmicro, 2016).
Respective security strategies will be necessary to be included in the security infrastructure for
the deliberate and accidental insider attacks. The measures will be stated and involved in the
security plans and the same will be required to be communicated to the entire security team as
well.
8

Aztek – Risk Assessment & Management
Risk Assessment
It will be required for the security team at Aztek to have a complete account of the risks that may
get executed along with the steps that may be applied to deal with them. These risks will be
required to be assessed on the basis of the impact, probability and level of the risks. Risk
assessment is a procedure that may be applied in Aztek in terms of the risks and threats that will
emerge with the implementation of BYOD scheme (Crane, 2013).
Risk Management Process
There will be many risks that will come up in front of Aztek with the implementation of the
BYOD scheme in the organization. There are measures and mechanisms that have been
developed in order to deal with such risks and issues.
Risk Management process is one such approach that comprises of the six phases as illustrated in
the diagram below to treat the risks that are identified.
Risk Assessment and Management at Aztek
In the first phase, the risks associated with BYOD shall be identified on the basis of various
threat agents that may lead to the occurrence of the risks. The risk areas shall be identified along
with the specific risk categories (Capterra, 2016). There may be flow charts that may be designed
for the purpose (Berg, 2016).
The second step in the process shall include the assessment and prioritization of the risks
including the determination of their impact and likelihood along with the priority in which the
risks shall be treated (Castsoftware, 2016).
Planning and treatment of the risks that are associated with BYOD shall classify the risks which
can be and cannot be mitigated. The specific treatment strategies shall then be mapped with the
risks on the basis of their assessment and evaluation results (Microsoft, 2016).
The application of the treatment strategies to manage every risk shall be reviewed and tracked.
The results shall be included in the form of a formal report. Aztek must also take and implement
numerous controls to put a check on the risks at the initiation level only (Development, 2013).
9
Risk
Identification
Risk
Assessmentand
Prioritization
Risk Planning Risk Tracking
and Report Risk Control Monitor and
Review
Risk Assessment
It will be required for the security team at Aztek to have a complete account of the risks that may
get executed along with the steps that may be applied to deal with them. These risks will be
required to be assessed on the basis of the impact, probability and level of the risks. Risk
assessment is a procedure that may be applied in Aztek in terms of the risks and threats that will
emerge with the implementation of BYOD scheme (Crane, 2013).
Risk Management Process
There will be many risks that will come up in front of Aztek with the implementation of the
BYOD scheme in the organization. There are measures and mechanisms that have been
developed in order to deal with such risks and issues.
Risk Management process is one such approach that comprises of the six phases as illustrated in
the diagram below to treat the risks that are identified.
Risk Assessment and Management at Aztek
In the first phase, the risks associated with BYOD shall be identified on the basis of various
threat agents that may lead to the occurrence of the risks. The risk areas shall be identified along
with the specific risk categories (Capterra, 2016). There may be flow charts that may be designed
for the purpose (Berg, 2016).
The second step in the process shall include the assessment and prioritization of the risks
including the determination of their impact and likelihood along with the priority in which the
risks shall be treated (Castsoftware, 2016).
Planning and treatment of the risks that are associated with BYOD shall classify the risks which
can be and cannot be mitigated. The specific treatment strategies shall then be mapped with the
risks on the basis of their assessment and evaluation results (Microsoft, 2016).
The application of the treatment strategies to manage every risk shall be reviewed and tracked.
The results shall be included in the form of a formal report. Aztek must also take and implement
numerous controls to put a check on the risks at the initiation level only (Development, 2013).
9
Risk
Identification
Risk
Assessmentand
Prioritization
Risk Planning Risk Tracking
and Report Risk Control Monitor and
Review
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
Aztek – Risk Assessment & Management
There are a number of preventive and detection controls along with correct controls that shall be
implemented. The completion of the risk treatment strategy shall be closely monitored (Vila,
2012).
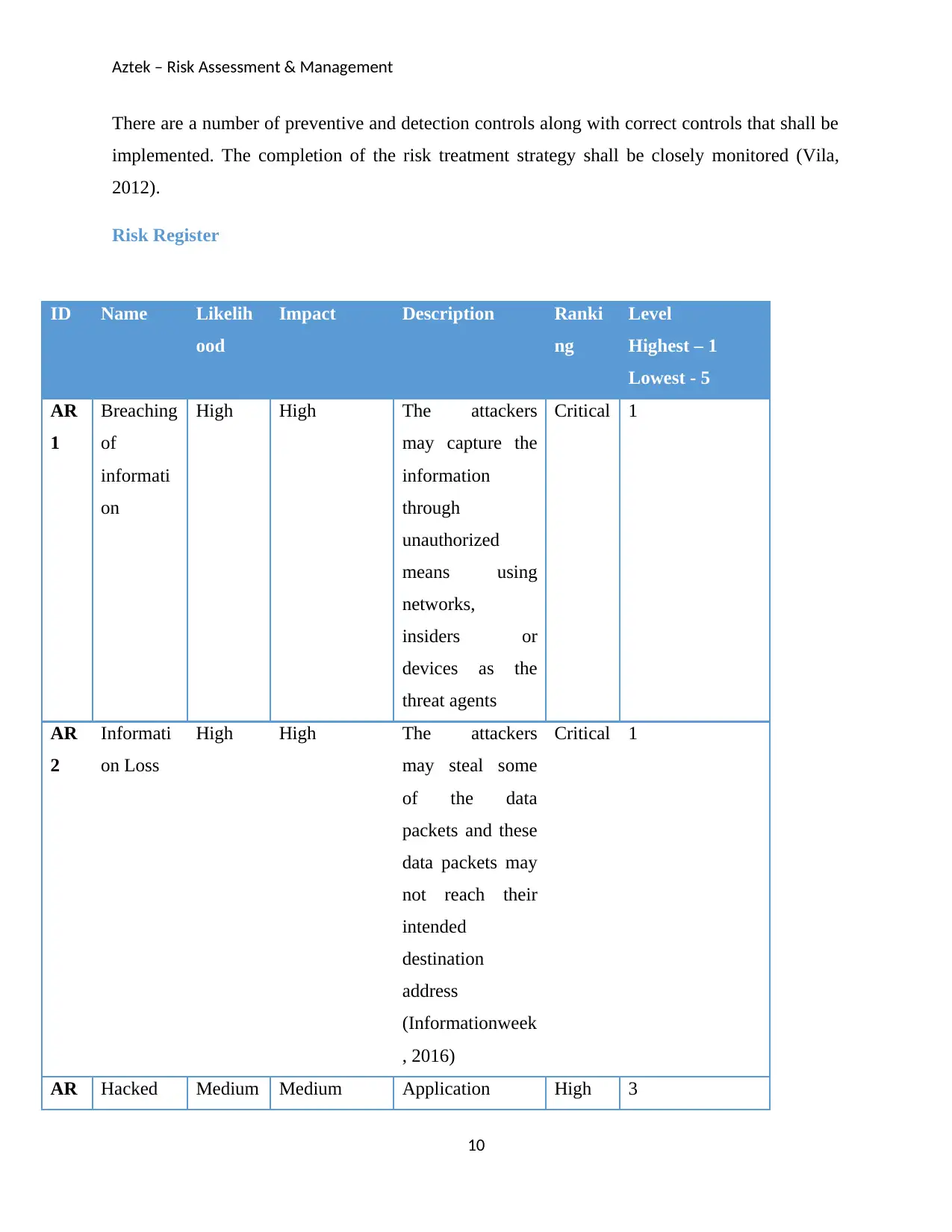
Risk Register
ID Name Likelih
ood
Impact Description Ranki
ng
Level
Highest – 1
Lowest - 5
AR
1
Breaching
of
informati
on
High High The attackers
may capture the
information
through
unauthorized
means using
networks,
insiders or
devices as the
threat agents
Critical 1
AR
2
Informati
on Loss
High High The attackers
may steal some
of the data
packets and these
data packets may
not reach their
intended
destination
address
(Informationweek
, 2016)
Critical 1
AR Hacked Medium Medium Application High 3
10
There are a number of preventive and detection controls along with correct controls that shall be
implemented. The completion of the risk treatment strategy shall be closely monitored (Vila,
2012).
Risk Register
ID Name Likelih
ood
Impact Description Ranki
ng
Level
Highest – 1
Lowest - 5
AR
1
Breaching
of
informati
on
High High The attackers
may capture the
information
through
unauthorized
means using
networks,
insiders or
devices as the
threat agents
Critical 1
AR
2
Informati
on Loss
High High The attackers
may steal some
of the data
packets and these
data packets may
not reach their
intended
destination
address
(Informationweek
, 2016)
Critical 1
AR Hacked Medium Medium Application High 3
10
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
Aztek – Risk Assessment & Management
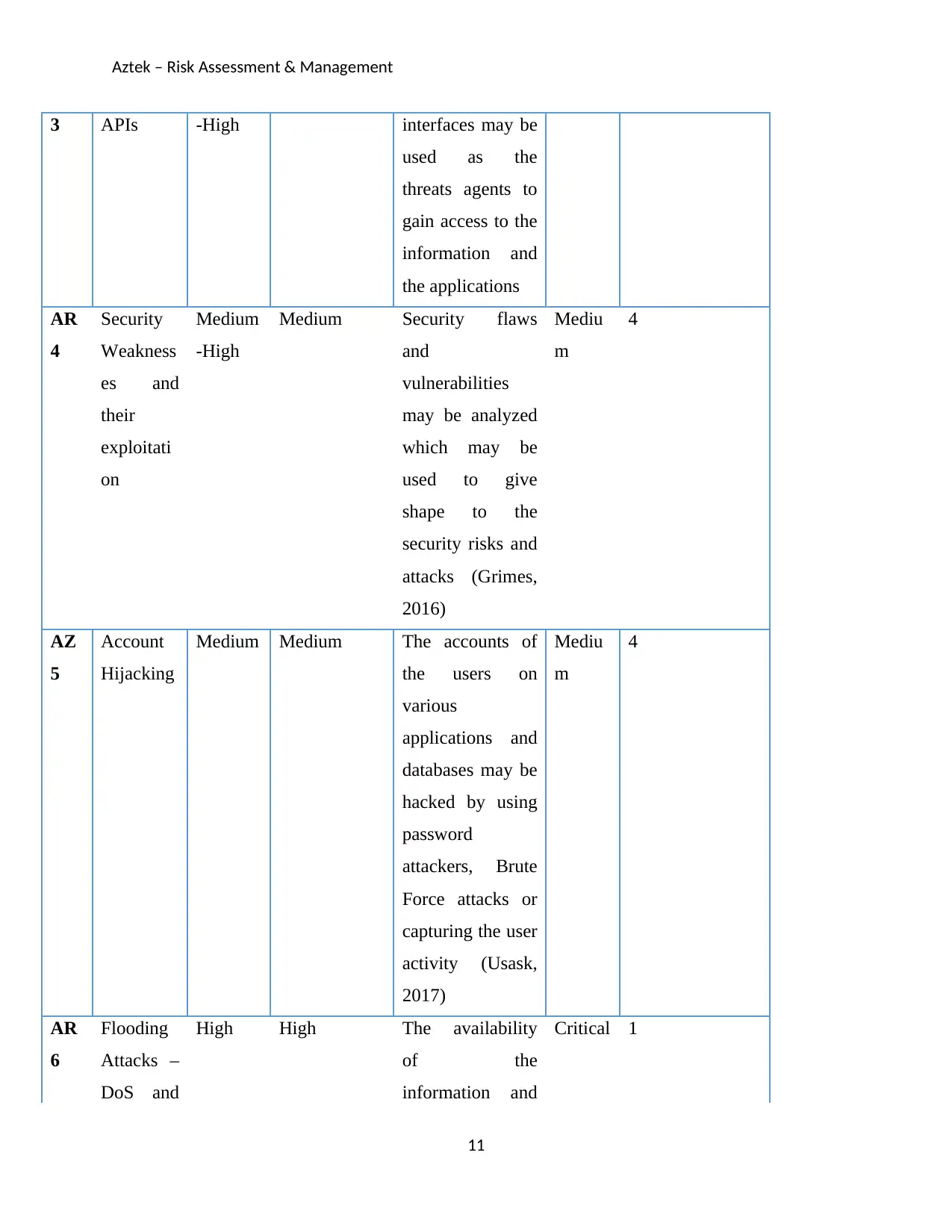
3 APIs -High interfaces may be
used as the
threats agents to
gain access to the
information and
the applications
AR
4
Security
Weakness
es and
their
exploitati
on
Medium
-High
Medium Security flaws
and
vulnerabilities
may be analyzed
which may be
used to give
shape to the
security risks and
attacks (Grimes,
2016)
Mediu
m
4
AZ
5
Account
Hijacking
Medium Medium The accounts of
the users on
various
applications and
databases may be
hacked by using
password
attackers, Brute
Force attacks or
capturing the user
activity (Usask,
2017)
Mediu
m
4
AR
6
Flooding
Attacks –
DoS and
High High The availability
of the
information and
Critical 1
11
3 APIs -High interfaces may be
used as the
threats agents to
gain access to the
information and
the applications
AR
4
Security
Weakness
es and
their
exploitati
on
Medium
-High
Medium Security flaws
and
vulnerabilities
may be analyzed
which may be
used to give
shape to the
security risks and
attacks (Grimes,
2016)
Mediu
m
4
AZ
5
Account
Hijacking
Medium Medium The accounts of
the users on
various
applications and
databases may be
hacked by using
password
attackers, Brute
Force attacks or
capturing the user
activity (Usask,
2017)
Mediu
m
4
AR
6
Flooding
Attacks –
DoS and
High High The availability
of the
information and
Critical 1
11
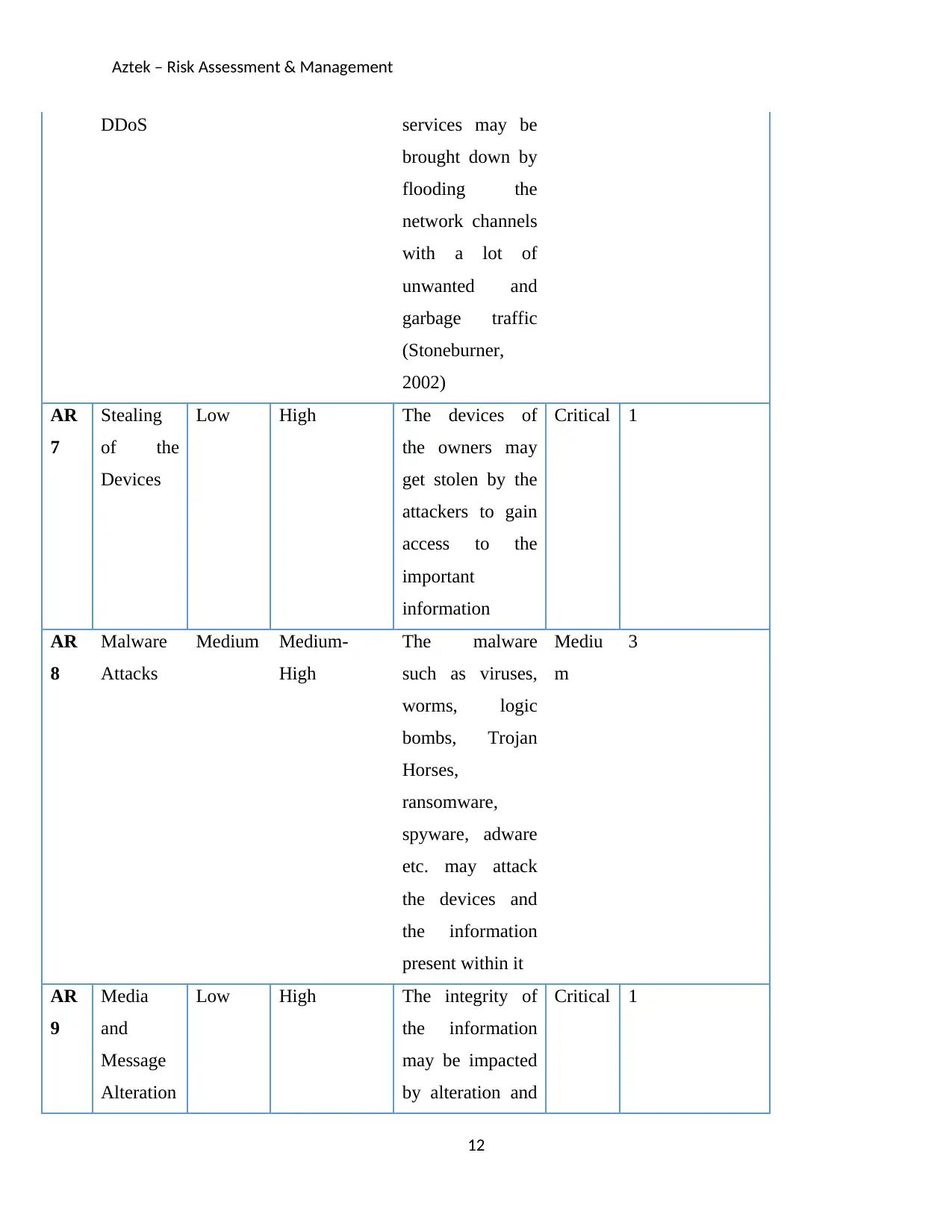
Aztek – Risk Assessment & Management
DDoS services may be
brought down by
flooding the
network channels
with a lot of
unwanted and
garbage traffic
(Stoneburner,
2002)
AR
7
Stealing
of the
Devices
Low High The devices of
the owners may
get stolen by the
attackers to gain
access to the
important
information
Critical 1
AR
8
Malware
Attacks
Medium Medium-
High
The malware
such as viruses,
worms, logic
bombs, Trojan
Horses,
ransomware,
spyware, adware
etc. may attack
the devices and
the information
present within it
Mediu
m
3
AR
9
Media
and
Message
Alteration
Low High The integrity of
the information
may be impacted
by alteration and
Critical 1
12
DDoS services may be
brought down by
flooding the
network channels
with a lot of
unwanted and
garbage traffic
(Stoneburner,
2002)
AR
7
Stealing
of the
Devices
Low High The devices of
the owners may
get stolen by the
attackers to gain
access to the
important
information
Critical 1
AR
8
Malware
Attacks
Medium Medium-
High
The malware
such as viruses,
worms, logic
bombs, Trojan
Horses,
ransomware,
spyware, adware
etc. may attack
the devices and
the information
present within it
Mediu
m
3
AR
9
Media
and
Message
Alteration
Low High The integrity of
the information
may be impacted
by alteration and
Critical 1
12
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 18
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





