Risk Management and Assessment for Aztek's BYOD Project
VerifiedAdded on 2019/10/30
|18
|4841
|31
Report
AI Summary
This report provides a comprehensive risk assessment for Aztek, an Australian finance firm, regarding the implementation of a Bring Your Own Device (BYOD) project. It begins with an executive summary outlining the benefits and challenges of BYOD, including security threats across information, network, and device security, and potential insider attacks. The report details the financial and security aspects of the project, the risk assessment process, and data security considerations, including user roles and privileges. It emphasizes the importance of updating technical and logical controls, administrative policies, and physical security measures to mitigate risks. The report recommends implementing updated network intrusion detection systems, anti-malware tools, and biometric systems to enhance security. The report also covers the regulatory environment under ASIC and ASC guidelines. The document concludes with a discussion of the types of data, potential risks, and the necessary security measures required for a successful BYOD implementation at Aztek.
Aztek
Aztek: IT Risk Management
Bring Your Own Devices (BYOD)
9/25/2017
Aztek: IT Risk Management
Bring Your Own Devices (BYOD)
9/25/2017
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Aztek: Risk Management & Assessment
Executive Summary
There are different recommendations that have been given by the senior officials at Aztek, an Australian
finance firm to overcome the existing infrastructural problems and operational issues. The project
selected for implementation is the Bring Your Own Devices (BYOD) project in which the employee-
owned devices will be sanctioned and allowed to be used in Aztek for business purposes. There will be
many advantages that will be offered by this scheme along with certain challenges in the form of security
threats and risks. A risk assessment report has been prepared for the BYOD project at Aztek covering the
review of the project from financial and security aspects, risk assessment process and data security
details.
Findings and Recommendations
The report throws light on numerous security threats and attacks that may come up with the permission to
allow the employees to use their devices in office (Cioupdate, 2016).
The major types of risks identified are information security risks, network security risks, device security
risks and insider attacks. There will be methods and steps that have been recommended to prevent and
stop all of the attacks under these categories.
The proposed and recommended countermeasures comprise of three different forms of security controls
that shall be implemented.
The first form is the use and update of the technical and logical controls. There are currently many of the
technical tools that are being used to make sure that the organizational security is maintained. However,
with the implementation of BYOD in Aztek, the forms of risks and threats will increase which will
require an update on these technical controls to be done. There are many new technological ideas and
concepts that are being invented every day which shall be analyzed by the security departments in
association with BYOD security risks and Aztek security. The network security risks and attacks shall be
controlled and prevented by using updated versions of network based intrusion detections and prevention
systems along with anti-denial tools. There are also automated network scanning, Wi-Fi scanners and
network auditing tools that have been created. These tools carry out authorized monitoring of the network
activities and also maintain a network log for all the activities that are carried out. Information and device
2
Executive Summary
There are different recommendations that have been given by the senior officials at Aztek, an Australian
finance firm to overcome the existing infrastructural problems and operational issues. The project
selected for implementation is the Bring Your Own Devices (BYOD) project in which the employee-
owned devices will be sanctioned and allowed to be used in Aztek for business purposes. There will be
many advantages that will be offered by this scheme along with certain challenges in the form of security
threats and risks. A risk assessment report has been prepared for the BYOD project at Aztek covering the
review of the project from financial and security aspects, risk assessment process and data security
details.
Findings and Recommendations
The report throws light on numerous security threats and attacks that may come up with the permission to
allow the employees to use their devices in office (Cioupdate, 2016).
The major types of risks identified are information security risks, network security risks, device security
risks and insider attacks. There will be methods and steps that have been recommended to prevent and
stop all of the attacks under these categories.
The proposed and recommended countermeasures comprise of three different forms of security controls
that shall be implemented.
The first form is the use and update of the technical and logical controls. There are currently many of the
technical tools that are being used to make sure that the organizational security is maintained. However,
with the implementation of BYOD in Aztek, the forms of risks and threats will increase which will
require an update on these technical controls to be done. There are many new technological ideas and
concepts that are being invented every day which shall be analyzed by the security departments in
association with BYOD security risks and Aztek security. The network security risks and attacks shall be
controlled and prevented by using updated versions of network based intrusion detections and prevention
systems along with anti-denial tools. There are also automated network scanning, Wi-Fi scanners and
network auditing tools that have been created. These tools carry out authorized monitoring of the network
activities and also maintain a network log for all the activities that are carried out. Information and device
2

Aztek: Risk Management & Assessment
security risks shall be controlled by using the measures such as advanced encryption, anti-malware tools,
device trackers and monitors. The insider threats may be difficult to control but the technical tools like
biometric systems for user authentication, automated identity and access management systems etc. may
prove to be useful to control such attacks. The use of firewalls and proxy servers must continue to be
implemented as basic step towards security.
The next set of recommended security measures to be implemented in Aztek must include the update on
the administrative policies and procedures. The security plan that is currently implemented in Aztek
has been designed as per the information security and the nature of projects that are carried out in
the organization. There must be measures included in the IT security plan to control the risks
associated with BYOD as it is being implemented for the first time. The security department and
IT department along with Aztek’s senior management must validate the security status by
carrying out security inspections along with reviews and audits. There must be ethical trainings
provided to the employees along with the sessions on latest security practices that must be
followed.
The third set of countermeasures recommended for Aztek is the use of updated physical security
checks and controls. These shall be done so that the basic security status is improved and made
stronger. The entry and exit gates of the organization must be secured with physical checks of
the employee bags and equipment so that any of the unauthorized and unsecure element does not
gain entry.
3
security risks shall be controlled by using the measures such as advanced encryption, anti-malware tools,
device trackers and monitors. The insider threats may be difficult to control but the technical tools like
biometric systems for user authentication, automated identity and access management systems etc. may
prove to be useful to control such attacks. The use of firewalls and proxy servers must continue to be
implemented as basic step towards security.
The next set of recommended security measures to be implemented in Aztek must include the update on
the administrative policies and procedures. The security plan that is currently implemented in Aztek
has been designed as per the information security and the nature of projects that are carried out in
the organization. There must be measures included in the IT security plan to control the risks
associated with BYOD as it is being implemented for the first time. The security department and
IT department along with Aztek’s senior management must validate the security status by
carrying out security inspections along with reviews and audits. There must be ethical trainings
provided to the employees along with the sessions on latest security practices that must be
followed.
The third set of countermeasures recommended for Aztek is the use of updated physical security
checks and controls. These shall be done so that the basic security status is improved and made
stronger. The entry and exit gates of the organization must be secured with physical checks of
the employee bags and equipment so that any of the unauthorized and unsecure element does not
gain entry.
3
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

Aztek: Risk Management & Assessment
Introduction...........................................................................................................................6
Aztek – Overview of the Organization............................................................................................6
BYOD: Project Overview................................................................................................................6
Project Review from Finance Service Sector.........................................................................7
BYOD Description: Financial Aspects............................................................................................7
IT Security Policies & Procedures – Changes and Updates...................................................9
Risk Assessment Procedure for BYOD................................................................................10
Risk Management.........................................................................................................................10
Risk Register.................................................................................................................................11
Data Security – Types of Data, Possible Risks, User Roles & Privileges..............................14
Conclusion............................................................................................................................15
References............................................................................................................................16
4
Introduction...........................................................................................................................6
Aztek – Overview of the Organization............................................................................................6
BYOD: Project Overview................................................................................................................6
Project Review from Finance Service Sector.........................................................................7
BYOD Description: Financial Aspects............................................................................................7
IT Security Policies & Procedures – Changes and Updates...................................................9
Risk Assessment Procedure for BYOD................................................................................10
Risk Management.........................................................................................................................10
Risk Register.................................................................................................................................11
Data Security – Types of Data, Possible Risks, User Roles & Privileges..............................14
Conclusion............................................................................................................................15
References............................................................................................................................16
4
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Aztek: Risk Management & Assessment
Introduction
Aztek – Overview of the Organization
Aztek is an organization that is based out of Australia and it is a financial firm that provides its
clients with the services in the financial sector only. There are various business sectors that are
present and have been set up in different countries that contribute in the economy of a particular
country. Some of these sectors have a lesser contribution and there are some sectors and units
that are mandatory and without the strong hold of such sectors, a successful economy will not be
developed. One of such examples is the financial sector. There comes a great responsibility as
well to the organizations under this sector to give their best so that the customer demands are
fulfilled.
Aztek has been successfully contributing towards the goal of developing strong economy for
Australia and has served its customers excellently. The organization is now expanding which is
causing certain issues in terms of the customer satisfaction levels. Owing to the current state of
problems and issues, the senior officials at Aztek have come up with different project proposals.
Some of these ideas include the permission to the employees of Aztek to bring their personal
devices at work, use of external cloud hosting solutions for information management,
outsourcing of some of the key IT functionalities and likewise.
After analyzing the current and future needs of the organization, the management has decided to
include and implement the first suggestion of allowing the employees to bring and use their
personal devices at work. The details of the project and the risk areas associated with it have
been covered in the report along with the risk management process.
BYOD: Project Overview
Bring Your Own Devices (BYOD) is a scheme that promotes the use of employee-owned
devices in a business environment. IT consumerization is one of the growing trends in the
present day business conditions and BYOD is a stepping stone towards achieving the same.
Under this scheme, employee-owned devices like Smartphones, networking gadgets, tablets,
laptops etc. are sanctioned and allowed by the business units to be used in the organization or as
part of the parallel systems.
5
Introduction
Aztek – Overview of the Organization
Aztek is an organization that is based out of Australia and it is a financial firm that provides its
clients with the services in the financial sector only. There are various business sectors that are
present and have been set up in different countries that contribute in the economy of a particular
country. Some of these sectors have a lesser contribution and there are some sectors and units
that are mandatory and without the strong hold of such sectors, a successful economy will not be
developed. One of such examples is the financial sector. There comes a great responsibility as
well to the organizations under this sector to give their best so that the customer demands are
fulfilled.
Aztek has been successfully contributing towards the goal of developing strong economy for
Australia and has served its customers excellently. The organization is now expanding which is
causing certain issues in terms of the customer satisfaction levels. Owing to the current state of
problems and issues, the senior officials at Aztek have come up with different project proposals.
Some of these ideas include the permission to the employees of Aztek to bring their personal
devices at work, use of external cloud hosting solutions for information management,
outsourcing of some of the key IT functionalities and likewise.
After analyzing the current and future needs of the organization, the management has decided to
include and implement the first suggestion of allowing the employees to bring and use their
personal devices at work. The details of the project and the risk areas associated with it have
been covered in the report along with the risk management process.
BYOD: Project Overview
Bring Your Own Devices (BYOD) is a scheme that promotes the use of employee-owned
devices in a business environment. IT consumerization is one of the growing trends in the
present day business conditions and BYOD is a stepping stone towards achieving the same.
Under this scheme, employee-owned devices like Smartphones, networking gadgets, tablets,
laptops etc. are sanctioned and allowed by the business units to be used in the organization or as
part of the parallel systems.
5

Aztek: Risk Management & Assessment
This has been decided to be implemented in Aztek as well so that the load of procuring
additional tools and devices is eliminated from the organization. This will allow the accounts
department to allocate the costs that will be saved through this attempt in other important
sections which would aid the expansion of the organization and the improvement of its
infrastructure.
Project Review from Finance Service Sector
Every business activity that is carried out is regulated by certain laws and policies that vary from
one country to the other. In Australia, all the financial services, operations and activities are
regulated by a body called Australian Securities and Investments Commission (ASIC). It is an
independent body that acts as a corporate regulator for Australia. All the financial transactions
and activities that are executed by Aztek must adhere to the ASIC rules and guidelines.
There is also an ethical and professional code of conduct that is followed and implemented in
Australia irrespective of the business sector which is called Australian Code of Conduct (ASC).
The project activities must also confirm to the same.
Nowadays, the payment processes executed are mostly electronic in nature. These e-payments
are processed and managed by the e-payments code and regulation that comes under ASIC which
shall be adhered to.
Financial information comes under the classification of sensitive and critical information. It must
be protected from all sorts of security risks and attacks and therefore, Intellectual Property rights
shall be implemented in such systems.
BYOD Description: Financial Aspects
Aztek is a finance company that has its own bundle of goals, aims and objectives. Some of the
primary points in the list include:
The financial services that are provided to the clients are secure, reliable and accurate.
Employees of Aztek are satisfied and the engagement percentage with the company
grows higher in every quarter.
Customers of Aztek are satisfied and the engagement percentage with the company grows
higher in every quarter.
6
This has been decided to be implemented in Aztek as well so that the load of procuring
additional tools and devices is eliminated from the organization. This will allow the accounts
department to allocate the costs that will be saved through this attempt in other important
sections which would aid the expansion of the organization and the improvement of its
infrastructure.
Project Review from Finance Service Sector
Every business activity that is carried out is regulated by certain laws and policies that vary from
one country to the other. In Australia, all the financial services, operations and activities are
regulated by a body called Australian Securities and Investments Commission (ASIC). It is an
independent body that acts as a corporate regulator for Australia. All the financial transactions
and activities that are executed by Aztek must adhere to the ASIC rules and guidelines.
There is also an ethical and professional code of conduct that is followed and implemented in
Australia irrespective of the business sector which is called Australian Code of Conduct (ASC).
The project activities must also confirm to the same.
Nowadays, the payment processes executed are mostly electronic in nature. These e-payments
are processed and managed by the e-payments code and regulation that comes under ASIC which
shall be adhered to.
Financial information comes under the classification of sensitive and critical information. It must
be protected from all sorts of security risks and attacks and therefore, Intellectual Property rights
shall be implemented in such systems.
BYOD Description: Financial Aspects
Aztek is a finance company that has its own bundle of goals, aims and objectives. Some of the
primary points in the list include:
The financial services that are provided to the clients are secure, reliable and accurate.
Employees of Aztek are satisfied and the engagement percentage with the company
grows higher in every quarter.
Customers of Aztek are satisfied and the engagement percentage with the company grows
higher in every quarter.
6
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

Aztek: Risk Management & Assessment
Meeting the deadlines, estimates and delivery dates for every project.
BYOD project that has been approved by the management has its own goals which are in-line
with the company aims and goals.
With the implementation of the BYOD project, the employee-owned devices will be used
for the execution of the business operations. These devices will have the company tools,
applications and mechanisms deployed so that employees may use them for the execution
of business tasks and for exploring the systems as well. This will make them aware of the
in-depth functioning which will improve the reliability of the service and the productivity
of the employees as well. They will not be required to stay for enhanced period of time in
the company locations as they may operate the functions from their homes as well.
The reliability and quality of service will improve which will lead to the improvement of
the customer expectations as well. The customers will be provided with the financial
solutions as per the promised date of delivery which will enhance their engagement with
Aztek.
The entire set of activities will be streamlined and the risks associated with schedule and
budget will be avoided as a result.
There will be many of the financial benefits that will be provided to Aztek with the
implementation of BYOD.
The employees will bring their personal devices to the office which will eliminate the
cost of procurement along with the infrastructural costs of setting up these devices at the
workstations of the employees.
Operational costs will also come down as the number of operational errors along with the
need to work on a particular requirement again and again will be elimiated (Gessner,
2016).
Cost of testing may be considerably high as there are many additional tools that are
necessary in certain business processes. These tools will already be available with the
employees which will bring down costs in this section as well (Retailwire, 2016).
7
Meeting the deadlines, estimates and delivery dates for every project.
BYOD project that has been approved by the management has its own goals which are in-line
with the company aims and goals.
With the implementation of the BYOD project, the employee-owned devices will be used
for the execution of the business operations. These devices will have the company tools,
applications and mechanisms deployed so that employees may use them for the execution
of business tasks and for exploring the systems as well. This will make them aware of the
in-depth functioning which will improve the reliability of the service and the productivity
of the employees as well. They will not be required to stay for enhanced period of time in
the company locations as they may operate the functions from their homes as well.
The reliability and quality of service will improve which will lead to the improvement of
the customer expectations as well. The customers will be provided with the financial
solutions as per the promised date of delivery which will enhance their engagement with
Aztek.
The entire set of activities will be streamlined and the risks associated with schedule and
budget will be avoided as a result.
There will be many of the financial benefits that will be provided to Aztek with the
implementation of BYOD.
The employees will bring their personal devices to the office which will eliminate the
cost of procurement along with the infrastructural costs of setting up these devices at the
workstations of the employees.
Operational costs will also come down as the number of operational errors along with the
need to work on a particular requirement again and again will be elimiated (Gessner,
2016).
Cost of testing may be considerably high as there are many additional tools that are
necessary in certain business processes. These tools will already be available with the
employees which will bring down costs in this section as well (Retailwire, 2016).
7
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Aztek: Risk Management & Assessment
IT Security Policies & Procedures – Changes and Updates
Lowering down of the costs is one of the major benefits that are offered by BYOD to the
organizations in which it is implemented. There are several other benefits that are provided by
this scheme in terms of improved work life balance and satisfaction levels for the employees,
streamlining of the business activities, better customer satisfaction levels and many more.
On the other hand, there may also be many challenges that may emerge with the use and
implementation of BYOD. One of the major items under the challenges that may come up
includes the security issues and risks. These security issues may fall under the categories of data
security risks, network security risks, device security risks and likewise.
The security plan that is currently implemented in Aztek has been designed as per the
information security and the nature of projects that are carried out in the organization. There are
measures suggested to control the risks associated with the current elements in association with
Aztek with no mention of BYOD as it is being implemented for the first time.
Therefore, the changes will be necessary in the security policies and procedures which will
require a risk assessment and management of all the security risks associated with the BYOD
scheme and project.
There will primarily be three categories of threats and security risks that will come up with the
use and implementation of BYOD. These will include information security risks, network
security risks and device security risks. The devices of the employees may or may not confirm to
the security requirements of Aztek. Before sanctioning the use of such employee-owned device
in the organization, the IT department must carry out a security review of these devices. It shall
be equipped with the security tools, security tags and applications for easy tracking and security
control (Coleman, 2011). The information and network security risks shall be assessed and the
controls shall accordingly be designed and implemented. There shall also be an update on the
back-up schedule that must be done along with enhanced forms of disaster recovery controls.
Apart from these three risk areas and categories, there may also be risks caused and executed
through the device owners, that is, the employees of Aztek. They might use the devices and the
organization-oriented applications in the devices on their home networks or the public networks.
This may lead to increase in the risk probability as the network security will be weak in such
8
IT Security Policies & Procedures – Changes and Updates
Lowering down of the costs is one of the major benefits that are offered by BYOD to the
organizations in which it is implemented. There are several other benefits that are provided by
this scheme in terms of improved work life balance and satisfaction levels for the employees,
streamlining of the business activities, better customer satisfaction levels and many more.
On the other hand, there may also be many challenges that may emerge with the use and
implementation of BYOD. One of the major items under the challenges that may come up
includes the security issues and risks. These security issues may fall under the categories of data
security risks, network security risks, device security risks and likewise.
The security plan that is currently implemented in Aztek has been designed as per the
information security and the nature of projects that are carried out in the organization. There are
measures suggested to control the risks associated with the current elements in association with
Aztek with no mention of BYOD as it is being implemented for the first time.
Therefore, the changes will be necessary in the security policies and procedures which will
require a risk assessment and management of all the security risks associated with the BYOD
scheme and project.
There will primarily be three categories of threats and security risks that will come up with the
use and implementation of BYOD. These will include information security risks, network
security risks and device security risks. The devices of the employees may or may not confirm to
the security requirements of Aztek. Before sanctioning the use of such employee-owned device
in the organization, the IT department must carry out a security review of these devices. It shall
be equipped with the security tools, security tags and applications for easy tracking and security
control (Coleman, 2011). The information and network security risks shall be assessed and the
controls shall accordingly be designed and implemented. There shall also be an update on the
back-up schedule that must be done along with enhanced forms of disaster recovery controls.
Apart from these three risk areas and categories, there may also be risks caused and executed
through the device owners, that is, the employees of Aztek. They might use the devices and the
organization-oriented applications in the devices on their home networks or the public networks.
This may lead to increase in the risk probability as the network security will be weak in such
8

Aztek: Risk Management & Assessment
cases. The critical applications and information shall, therefore, be locked out as soon as the
employee disconnects from the office network. This shall be included under the security policy
and only the less critical applications and public data and information shall be accessible from
other networks (Newton, 2015).
The employees shall also be provided with the knowledge and information on the best security
practices that they must follow. This shall include the preservation and protection of the devices
and information from unauthorized users, such as, their family and friends (Trendmicro, 2016).
The security procedures and policies must be upgraded as per the security state around the
BYOD scheme.
Risk Assessment Procedure for BYOD
Risk is defined as an occurrence that may cause considerable damage to the party or the system
in which it takes place. It is an event that has a specific impact that may be low to high and a
specific probability related with it and the combination of these attributes determine its level
(Crane, 2013). The impact of a risk is mostly negative and which is why it is desired to avoid the
risks that may take place.
Risk Management
The risks that are identified in association with BYOD will be required to be managed with a
defined process. The process will have five steps or phases that will be involved and it is these
steps that will determine the overall management of the risks. The five set of processes that will
be involved are shown below and a description has also been added for the same.
Risk Management for BYOD in Aztek
In order to manage the risks, it will be required to have details on the risks that may take place.
The first phase will identify the possible risks and the information regarding the same will be
investigated from different information sources (Capterra, 2016). These sources may comprise of
the organization itself, the employees of the organization, market study etc (Berg, 2016).
9
Risk
Identification
Risk
Assessmentand
Prioritization
Risk Treatment Risk Control Risk Tracking
and Report
cases. The critical applications and information shall, therefore, be locked out as soon as the
employee disconnects from the office network. This shall be included under the security policy
and only the less critical applications and public data and information shall be accessible from
other networks (Newton, 2015).
The employees shall also be provided with the knowledge and information on the best security
practices that they must follow. This shall include the preservation and protection of the devices
and information from unauthorized users, such as, their family and friends (Trendmicro, 2016).
The security procedures and policies must be upgraded as per the security state around the
BYOD scheme.
Risk Assessment Procedure for BYOD
Risk is defined as an occurrence that may cause considerable damage to the party or the system
in which it takes place. It is an event that has a specific impact that may be low to high and a
specific probability related with it and the combination of these attributes determine its level
(Crane, 2013). The impact of a risk is mostly negative and which is why it is desired to avoid the
risks that may take place.
Risk Management
The risks that are identified in association with BYOD will be required to be managed with a
defined process. The process will have five steps or phases that will be involved and it is these
steps that will determine the overall management of the risks. The five set of processes that will
be involved are shown below and a description has also been added for the same.
Risk Management for BYOD in Aztek
In order to manage the risks, it will be required to have details on the risks that may take place.
The first phase will identify the possible risks and the information regarding the same will be
investigated from different information sources (Capterra, 2016). These sources may comprise of
the organization itself, the employees of the organization, market study etc (Berg, 2016).
9
Risk
Identification
Risk
Assessmentand
Prioritization
Risk Treatment Risk Control Risk Tracking
and Report
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
Aztek: Risk Management & Assessment
One the risks are listed and identified, there specific probability and impact will be required to be
analyzed and assessed. In the second process, the risk management and security team must pick
up every identified risk one by one and determine the impact of the risk on the basis of its
probability, nature and type (Castsoftware, 2016).
The treatment of the risk will be based upon its associated impact and likelihood along with the
nature of the risk. There are different strategies and methods to treat a risk and the same shall be
evaluated and applied. The risk treatment process will be required to be closely monitored and
controlled by carrying out the security reviews and audits by the senior officials and authorities
(Microsoft, 2016).
A track on the same shall also be maintained in terms of the treatment activities that are
completed, treatment activities that are pending and likewise. A report shall be prepared for the
final submission once the risk is completely treated and the likelihood of its occurrence is
reduced to zero (Vila, 2012).
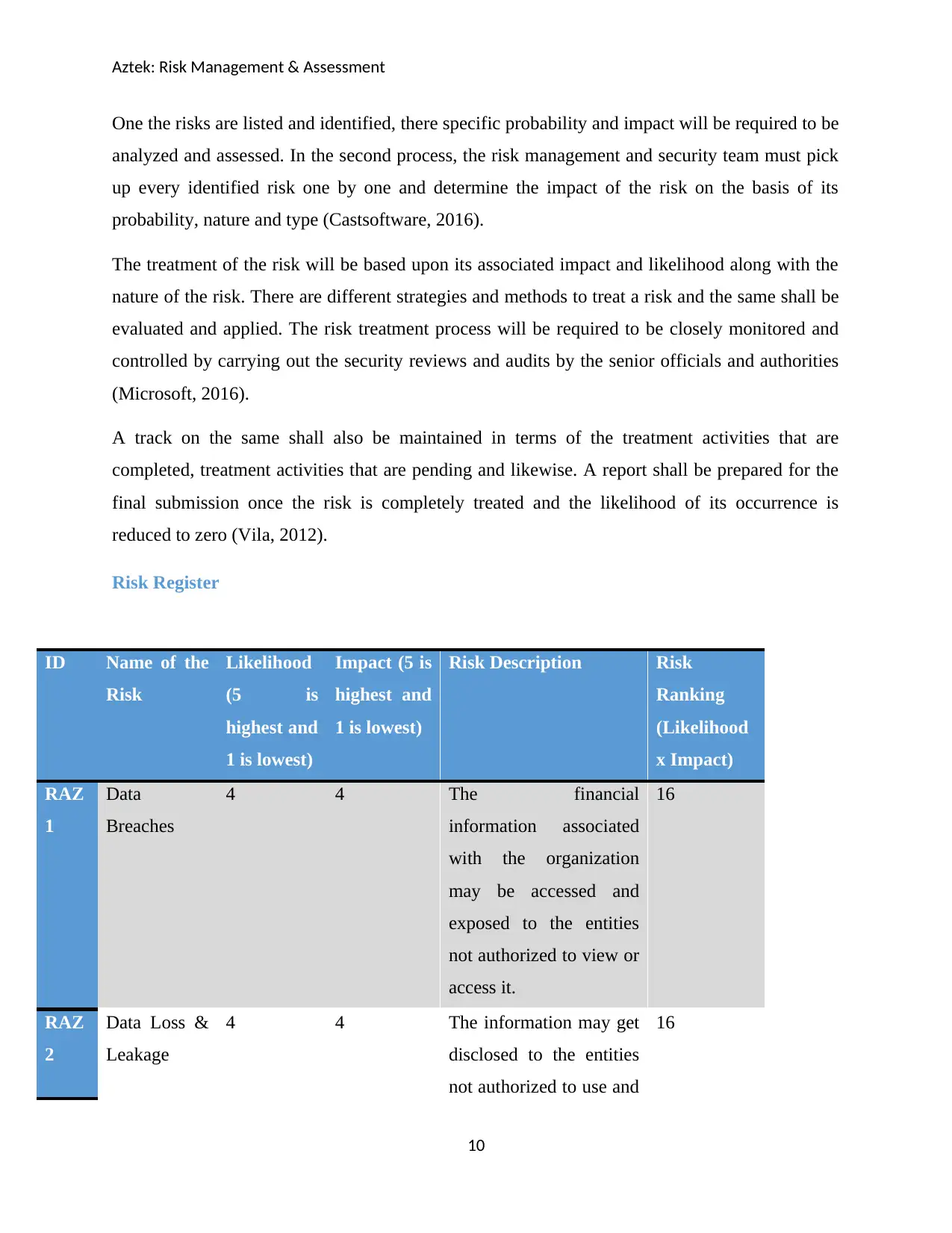
Risk Register
ID Name of the
Risk
Likelihood
(5 is
highest and
1 is lowest)
Impact (5 is
highest and
1 is lowest)
Risk Description Risk
Ranking
(Likelihood
x Impact)
RAZ
1
Data
Breaches
4 4 The financial
information associated
with the organization
may be accessed and
exposed to the entities
not authorized to view or
access it.
16
RAZ
2
Data Loss &
Leakage
4 4 The information may get
disclosed to the entities
not authorized to use and
16
10
One the risks are listed and identified, there specific probability and impact will be required to be
analyzed and assessed. In the second process, the risk management and security team must pick
up every identified risk one by one and determine the impact of the risk on the basis of its
probability, nature and type (Castsoftware, 2016).
The treatment of the risk will be based upon its associated impact and likelihood along with the
nature of the risk. There are different strategies and methods to treat a risk and the same shall be
evaluated and applied. The risk treatment process will be required to be closely monitored and
controlled by carrying out the security reviews and audits by the senior officials and authorities
(Microsoft, 2016).
A track on the same shall also be maintained in terms of the treatment activities that are
completed, treatment activities that are pending and likewise. A report shall be prepared for the
final submission once the risk is completely treated and the likelihood of its occurrence is
reduced to zero (Vila, 2012).
Risk Register
ID Name of the
Risk
Likelihood
(5 is
highest and
1 is lowest)
Impact (5 is
highest and
1 is lowest)
Risk Description Risk
Ranking
(Likelihood
x Impact)
RAZ
1
Data
Breaches
4 4 The financial
information associated
with the organization
may be accessed and
exposed to the entities
not authorized to view or
access it.
16
RAZ
2
Data Loss &
Leakage
4 4 The information may get
disclosed to the entities
not authorized to use and
16
10
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
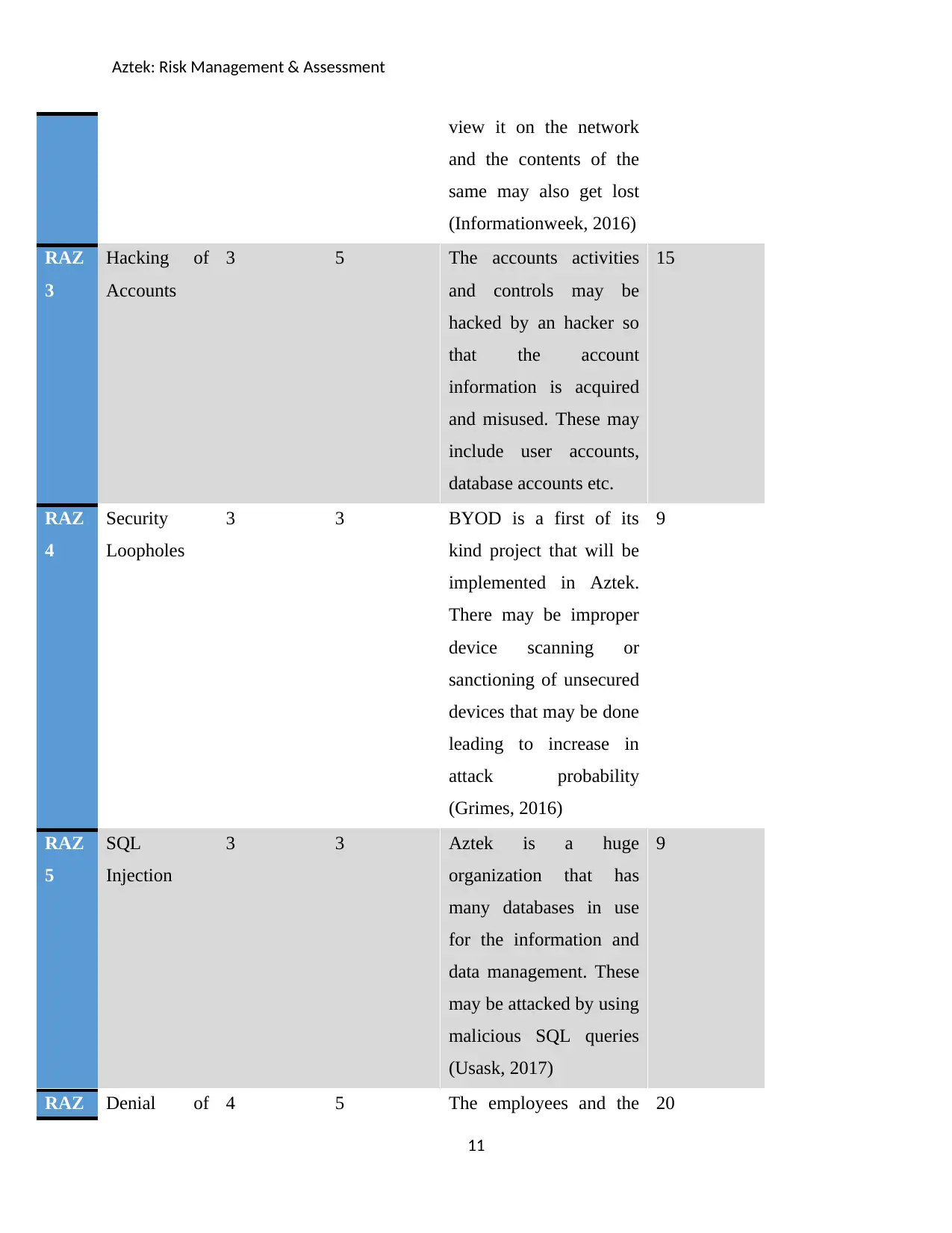
Aztek: Risk Management & Assessment
view it on the network
and the contents of the
same may also get lost
(Informationweek, 2016)
RAZ
3
Hacking of
Accounts
3 5 The accounts activities
and controls may be
hacked by an hacker so
that the account
information is acquired
and misused. These may
include user accounts,
database accounts etc.
15
RAZ
4
Security
Loopholes
3 3 BYOD is a first of its
kind project that will be
implemented in Aztek.
There may be improper
device scanning or
sanctioning of unsecured
devices that may be done
leading to increase in
attack probability
(Grimes, 2016)
9
RAZ
5
SQL
Injection
3 3 Aztek is a huge
organization that has
many databases in use
for the information and
data management. These
may be attacked by using
malicious SQL queries
(Usask, 2017)
9
RAZ Denial of 4 5 The employees and the 20
11
view it on the network
and the contents of the
same may also get lost
(Informationweek, 2016)
RAZ
3
Hacking of
Accounts
3 5 The accounts activities
and controls may be
hacked by an hacker so
that the account
information is acquired
and misused. These may
include user accounts,
database accounts etc.
15
RAZ
4
Security
Loopholes
3 3 BYOD is a first of its
kind project that will be
implemented in Aztek.
There may be improper
device scanning or
sanctioning of unsecured
devices that may be done
leading to increase in
attack probability
(Grimes, 2016)
9
RAZ
5
SQL
Injection
3 3 Aztek is a huge
organization that has
many databases in use
for the information and
data management. These
may be attacked by using
malicious SQL queries
(Usask, 2017)
9
RAZ Denial of 4 5 The employees and the 20
11
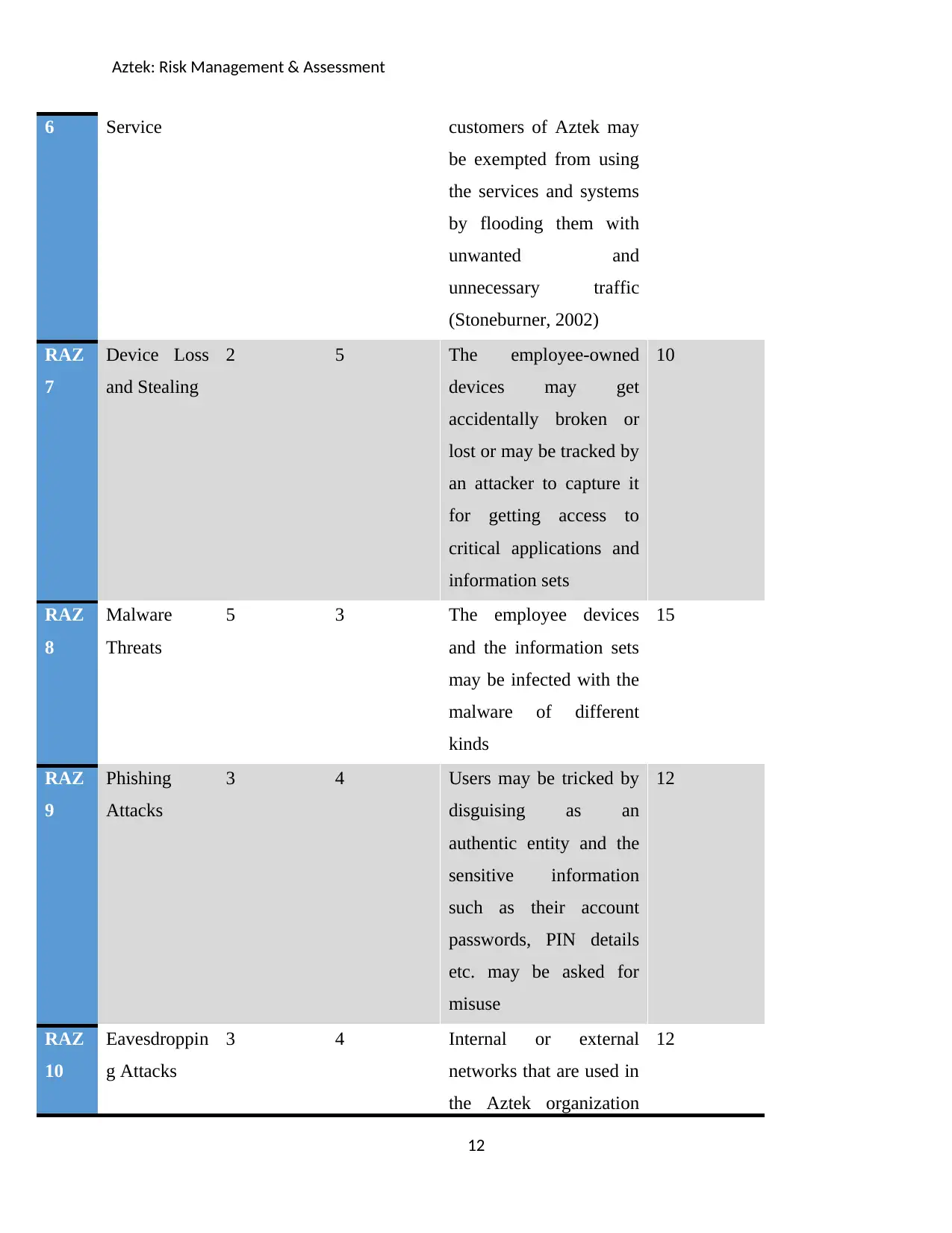
Aztek: Risk Management & Assessment
6 Service customers of Aztek may
be exempted from using
the services and systems
by flooding them with
unwanted and
unnecessary traffic
(Stoneburner, 2002)
RAZ
7
Device Loss
and Stealing
2 5 The employee-owned
devices may get
accidentally broken or
lost or may be tracked by
an attacker to capture it
for getting access to
critical applications and
information sets
10
RAZ
8
Malware
Threats
5 3 The employee devices
and the information sets
may be infected with the
malware of different
kinds
15
RAZ
9
Phishing
Attacks
3 4 Users may be tricked by
disguising as an
authentic entity and the
sensitive information
such as their account
passwords, PIN details
etc. may be asked for
misuse
12
RAZ
10
Eavesdroppin
g Attacks
3 4 Internal or external
networks that are used in
the Aztek organization
12
12
6 Service customers of Aztek may
be exempted from using
the services and systems
by flooding them with
unwanted and
unnecessary traffic
(Stoneburner, 2002)
RAZ
7
Device Loss
and Stealing
2 5 The employee-owned
devices may get
accidentally broken or
lost or may be tracked by
an attacker to capture it
for getting access to
critical applications and
information sets
10
RAZ
8
Malware
Threats
5 3 The employee devices
and the information sets
may be infected with the
malware of different
kinds
15
RAZ
9
Phishing
Attacks
3 4 Users may be tricked by
disguising as an
authentic entity and the
sensitive information
such as their account
passwords, PIN details
etc. may be asked for
misuse
12
RAZ
10
Eavesdroppin
g Attacks
3 4 Internal or external
networks that are used in
the Aztek organization
12
12
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 18
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





