Information Technology Risk Assessment for Aztek's BYOD Project
VerifiedAdded on 2020/03/28
|14
|6141
|64
Project
AI Summary
This project assesses the information technology risks associated with a Bring Your Own Device (BYOD) initiative at Aztek, an Australian financial services company. The project analyzes the potential benefits and drawbacks of BYOD, including cost savings and increased employee flexibility, while also addressing critical security concerns. It explores current IT practices, relevant government regulations, and the importance of data security. The project includes a risk assessment, identifying vulnerabilities, threats, and their consequences. Recommendations are provided to mitigate these risks, focusing on policies, procedures, and data protection measures to ensure secure implementation of BYOD. The study highlights the importance of addressing data leakage, compliance, and the overall impact on Aztek's competitive advantage in the financial sector.

Running head: RISK MANAGEMENT 1
Bring your own device (BYOD) in workplace project
Name:
Institution Affiliation:
Bring your own device (BYOD) in workplace project
Name:
Institution Affiliation:
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

RISK MANAGEMENT 2
Executive Summary
Aztek is an organization which is based in Australia and they operate in the financial service
industry. In the current times the organization has been encountering competition elements as a
result of other companies venturing in the financial industry. To be able to compete effectively
and become the market leaders in the sector there have been numerous projects which have been
proposed. Some of these project are as follows; allow the workers to bring their own devices
such as the laptops and the mobile phone devices into the workplace to be used as their main
devices to achieve the duties in the work. Other have been migrating of the business vital
programs and their associated data source to the external cloud hosting solution. Additionally,
there is project to outsource the key information technology functionality such as network,
management of desktop or the application of the development to the 3rd party. Lastly, there was
the project to upgrade or introduce major technology for example the mobile platforms and the
application, migrating to an improved networking technology, creation of the corporate wide
email for the purpose of compliance or even the upgrading the applications and the desktop
operating systems.
IT has become a critical aspect for each industry in an economy and it has played a vital role
towards the performance as well as the success of the businesses as well as the other services
particularly in the organizations. Information technology can bring many advantages to this
organizations. Nonetheless, there are also challenges which can be brought about the adaptation
of these projects.
One of the major project which the organization is aiming to implement is that of allowing the
workers to bring their devices such as the laptops, mobile phone devices and the tablets to the
workplace. This project aims to make the devices of the workers as the primary tools which will
be utilized to achieve the duties and the tasks allocated. The implementation of bring your own
device concept would provide major benefit to the organization in terms of saving as there would
be no additional funds needed to buy new equipment’s such as laptops or desktop. The
organization may opt to channel these funds which are saved to other projects in the business. As
much as this project would bring a lot of benefits to the organization it also has some information
technology risks which it bring forth.
In this research it intends to carry out analysis in the information risk which are associated to
BYOD concept which the organization is intending to implement. The primary devices which
would be discussed in the research are mobile phones, tablets and the laptops. Aztek organization
has been among the key major players of economic development in Australia financial industry
and this organization will be the basis of this case study. The research study will analyze the
information technology risks will be highlighted and what are the current IT practices which has
been employed in this organization. The current practices of organization which are utilized in
the organization would help in determing the appraisal of the technology. There would be also a
brief overview of the practices which are undertaken by the government to the organization in
the financial service sector.
The research will also highlights on the aspect of data security in the organization, for instance
when the workers are allowed to bring their own devices in the workplace and apply them to
performing on their duties it would be possible for the data for the corporation to be leaked by
the employees. The business need to address on this issue before even thinking implementing
Executive Summary
Aztek is an organization which is based in Australia and they operate in the financial service
industry. In the current times the organization has been encountering competition elements as a
result of other companies venturing in the financial industry. To be able to compete effectively
and become the market leaders in the sector there have been numerous projects which have been
proposed. Some of these project are as follows; allow the workers to bring their own devices
such as the laptops and the mobile phone devices into the workplace to be used as their main
devices to achieve the duties in the work. Other have been migrating of the business vital
programs and their associated data source to the external cloud hosting solution. Additionally,
there is project to outsource the key information technology functionality such as network,
management of desktop or the application of the development to the 3rd party. Lastly, there was
the project to upgrade or introduce major technology for example the mobile platforms and the
application, migrating to an improved networking technology, creation of the corporate wide
email for the purpose of compliance or even the upgrading the applications and the desktop
operating systems.
IT has become a critical aspect for each industry in an economy and it has played a vital role
towards the performance as well as the success of the businesses as well as the other services
particularly in the organizations. Information technology can bring many advantages to this
organizations. Nonetheless, there are also challenges which can be brought about the adaptation
of these projects.
One of the major project which the organization is aiming to implement is that of allowing the
workers to bring their devices such as the laptops, mobile phone devices and the tablets to the
workplace. This project aims to make the devices of the workers as the primary tools which will
be utilized to achieve the duties and the tasks allocated. The implementation of bring your own
device concept would provide major benefit to the organization in terms of saving as there would
be no additional funds needed to buy new equipment’s such as laptops or desktop. The
organization may opt to channel these funds which are saved to other projects in the business. As
much as this project would bring a lot of benefits to the organization it also has some information
technology risks which it bring forth.
In this research it intends to carry out analysis in the information risk which are associated to
BYOD concept which the organization is intending to implement. The primary devices which
would be discussed in the research are mobile phones, tablets and the laptops. Aztek organization
has been among the key major players of economic development in Australia financial industry
and this organization will be the basis of this case study. The research study will analyze the
information technology risks will be highlighted and what are the current IT practices which has
been employed in this organization. The current practices of organization which are utilized in
the organization would help in determing the appraisal of the technology. There would be also a
brief overview of the practices which are undertaken by the government to the organization in
the financial service sector.
The research will also highlights on the aspect of data security in the organization, for instance
when the workers are allowed to bring their own devices in the workplace and apply them to
performing on their duties it would be possible for the data for the corporation to be leaked by
the employees. The business need to address on this issue before even thinking implementing
RISK MANAGEMENT 3
this project. There has been recommendations in relation to the IT risk which has been linked to
this project.
Key information: BYOD (Bring your own device)
this project. There has been recommendations in relation to the IT risk which has been linked to
this project.
Key information: BYOD (Bring your own device)
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

RISK MANAGEMENT 4
Table of Contents
1.0 Introduction................................................................................................................................5
2.0 review of project in relation to financial industry.....................................................................6
2.1 Government regulation.......................................................................................................6
2.2 The financial services sector overview..............................................................................7
2.3 Current security at Aztek organization...............................................................................7
2.4 Bring your own device (BYOD) concept...........................................................................8
2.5 Factors of information technology platform that impact BYOD.......................................8
2.5.1 Benefits and drawback associated with BYOD..............................................................8
3. Risk assessment...........................................................................................................................9
4. Data security:.............................................................................................................................11
5. Recommendations:.................................................................................................................12
6. Conclusion:.............................................................................................................................12
7.0 References................................................................................................................................12
Table of Contents
1.0 Introduction................................................................................................................................5
2.0 review of project in relation to financial industry.....................................................................6
2.1 Government regulation.......................................................................................................6
2.2 The financial services sector overview..............................................................................7
2.3 Current security at Aztek organization...............................................................................7
2.4 Bring your own device (BYOD) concept...........................................................................8
2.5 Factors of information technology platform that impact BYOD.......................................8
2.5.1 Benefits and drawback associated with BYOD..............................................................8
3. Risk assessment...........................................................................................................................9
4. Data security:.............................................................................................................................11
5. Recommendations:.................................................................................................................12
6. Conclusion:.............................................................................................................................12
7.0 References................................................................................................................................12
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

RISK MANAGEMENT 5
1.0 Introduction
The advent of the information technology especially to each aspect of the human life as well as
the business has been very obvious and there is no need to accentuate it more. The information
technology continuous to be of great importance especially to the financial industry. It has been
very important as well as a priceless resource (Afreen, 2014). This concept is no longer a news
that the business now are in the information age which is characterized to the ever changing
information technology revolution as well as the information superhighway on which every
corporate organization should have, in the event it would survive in the 21st Century. The
financial industry has been affected radically by the aspect of the information technology
development (Ullman, 2011). The aspect of IT has become an important aspect to the business
resource since lack of it may lead to poor decisions and it ultimately could lead to the business
failure. The financial industry has been impacted and the organization which are operating in this
sector has implemented the use of the technology (Afreen, 2014). The information technology
has offered the industry with the wherewithal in dealing with the challenges of the aspect of new
economy poses. The information technology has been the cornerstone for the recent financial
industry reforms which are aimed in increasing of the speed as well as the reliability for any of
the financial operations as well as the initiative of strengthening the financial sector. The
revolution of the information technology has set the stage for the unprecedented increase in the
financial activity across the world. The progress in the technology development has reduced in
the costs associated to the global funds transfers.
Aztek is an organization which operate in the financial services in Australia and it is one of the
leading in the provision of these services. The company currently has been facing a lot of
competition and to achieve a competitive edge they intend to implement a project on BYOD to
enable the workers bring their devices to the workplace (Willcocks, 2013). The project is
intended to save a huge amount of income to the organization.
There would be a review of the various businesses that have allowed the workers to bring their
devices at workplace. Moreover, the advantages as well as drawbacks that are faced in these
organization. Additionally, the report will look at the effects of the application trends especially
in the landscape of information technology. This project implementation will have both some
positive remarks and shortcomings, therefore, discussing on the benefits that are associated to the
adoption of the systems and drawbacks are important to highlight. This project also encounters
the aspect of the security concern which has been captured as the project has been associated
with many of the insecurity issues. The concept of risk assessment has been discussed and it
elaborates on the various threats, consequences as well as the vulnerabilities which have resulted
from the implementation of the project of Aztek organization. The report has explored on the
recommendations which are aimed to prevent the organization from the issues of insecurity.
There are also policies as well as procedures which have been applied in the agreement of
employment to guide against the aspect of Bring Your Device applications.
In this research study, it would discuss on the aspects to consider on the project of BYOD in the
workplace. Some of the devices which the organization would recommend them to bring to the
workplace are the mobile phones, laptops as well as the tablets (Tokuyoshi, 2013). All the
aspects which relates to the business will be looked at based on the trends of the business and
how to adopt the project to leap huge benefits from it. There will be a review of the BYOD
which will be highlighted for the financial industry (Astani, Ready & Tessema, 2013). There
would also be establishment of the industrial regulation, the relevant government as well as the
1.0 Introduction
The advent of the information technology especially to each aspect of the human life as well as
the business has been very obvious and there is no need to accentuate it more. The information
technology continuous to be of great importance especially to the financial industry. It has been
very important as well as a priceless resource (Afreen, 2014). This concept is no longer a news
that the business now are in the information age which is characterized to the ever changing
information technology revolution as well as the information superhighway on which every
corporate organization should have, in the event it would survive in the 21st Century. The
financial industry has been affected radically by the aspect of the information technology
development (Ullman, 2011). The aspect of IT has become an important aspect to the business
resource since lack of it may lead to poor decisions and it ultimately could lead to the business
failure. The financial industry has been impacted and the organization which are operating in this
sector has implemented the use of the technology (Afreen, 2014). The information technology
has offered the industry with the wherewithal in dealing with the challenges of the aspect of new
economy poses. The information technology has been the cornerstone for the recent financial
industry reforms which are aimed in increasing of the speed as well as the reliability for any of
the financial operations as well as the initiative of strengthening the financial sector. The
revolution of the information technology has set the stage for the unprecedented increase in the
financial activity across the world. The progress in the technology development has reduced in
the costs associated to the global funds transfers.
Aztek is an organization which operate in the financial services in Australia and it is one of the
leading in the provision of these services. The company currently has been facing a lot of
competition and to achieve a competitive edge they intend to implement a project on BYOD to
enable the workers bring their devices to the workplace (Willcocks, 2013). The project is
intended to save a huge amount of income to the organization.
There would be a review of the various businesses that have allowed the workers to bring their
devices at workplace. Moreover, the advantages as well as drawbacks that are faced in these
organization. Additionally, the report will look at the effects of the application trends especially
in the landscape of information technology. This project implementation will have both some
positive remarks and shortcomings, therefore, discussing on the benefits that are associated to the
adoption of the systems and drawbacks are important to highlight. This project also encounters
the aspect of the security concern which has been captured as the project has been associated
with many of the insecurity issues. The concept of risk assessment has been discussed and it
elaborates on the various threats, consequences as well as the vulnerabilities which have resulted
from the implementation of the project of Aztek organization. The report has explored on the
recommendations which are aimed to prevent the organization from the issues of insecurity.
There are also policies as well as procedures which have been applied in the agreement of
employment to guide against the aspect of Bring Your Device applications.
In this research study, it would discuss on the aspects to consider on the project of BYOD in the
workplace. Some of the devices which the organization would recommend them to bring to the
workplace are the mobile phones, laptops as well as the tablets (Tokuyoshi, 2013). All the
aspects which relates to the business will be looked at based on the trends of the business and
how to adopt the project to leap huge benefits from it. There will be a review of the BYOD
which will be highlighted for the financial industry (Astani, Ready & Tessema, 2013). There
would also be establishment of the industrial regulation, the relevant government as well as the

RISK MANAGEMENT 6
best guidelines which would be highlighted. This project under the research would be based to
the current security exposure of the organization. There is also review of the risk assessment
especially on the threats, vulnerabilities as well as the consequences that are adopted when it
comes to control of the project on BYOD. The research would also focus on the sector risk
recommendations for this project which is underway to implementation. Other aspects which
would be discussed are on the data security especially to Aztek organization (Astani, Ready &
Tessema, 2013). This aspect is very important part to implementation of this project since there
are issues of threats which will be exhibited when the employees are allowed to bring on their
own devices to the place of work. Security is important especially in the flow of the data and
who would have access to it (Caldwell, Zeltmann & Griffin, 2012). When this project is
implemented Aztek Corporation will significantly improve on some of the areas which are
lagging behind and it would also increase on the overall competitive advantage over the other
organization in the same industry.
2.0 review of project in relation to financial industry
2.1 Government regulation
The broad framework of regulation is determined by Australian government. They have the
responsibility to the day to day supervision of the financial organization as well as the market.
Aztek Corporation being part of an industry in the financial sector they need to comply with
certain financial conduct which are relevant to the protection of vital financial information. The
organization needs to look deeply to the privacy Act 1993 before implementing BYOD to the
workplace (Arregui, Maynard & Ahmad, 2016). They government has regulated some laws
which could govern the financial institutions in view of the BYOD aspect. The government has
highlighted that a business entity may which allow their employees to bring their own devices to
the place of work. The laws has clearly highlighted some of the devices which should be brought
are; mobile phone, tablets and laptops. Moreover, the Australian government has explained also
that the business need to outline clearly on the rule which should be aimed at governing the
workers in this aspect of BYOD in the workplace (Arregui, Maynard & Ahmad, 2016).
Moreover, they should also make sure that these rules which they will implement should not be
in collision to the freedom and the rights of the workers. In the event that the workers break the
rules which have been established by the entity they should be fined and punished. Some of the
rules which Aztek Company has established are based on these aspect; the workers should ensure
that the data of the company is not accessible to the outsiders (Caldwell, Zeltmann & Griffin,
2012). Additionally, the information of the business should not be shared to any individuals who
is not part of the company and there flow of the information should be within the business and
the employees only no other third party unless it is stipulated by the business.
In many institutions the aspect of Bring your own device (BYOD) is not supported because of
the shortcoming it bring to the business. In some of the cases the incompetence’s as well as
careless of the staffs has led to exposure of the vital information of the business to third parties or
even to the public (Medudula, Sagar & Gandhi, 2016). The rival firms could use this useful
information to highlight some of the opportunities of the organization and take advantage of the
situation.
The BYOD concept is a vital aspect when it comes to achieving on the goals and the goals of the
organization (Miller, Voas & Hurlburt, 2012). It may help in the reduction of the costs as the
funds which would be used to buy new devices could be channeled towards other projects in the
best guidelines which would be highlighted. This project under the research would be based to
the current security exposure of the organization. There is also review of the risk assessment
especially on the threats, vulnerabilities as well as the consequences that are adopted when it
comes to control of the project on BYOD. The research would also focus on the sector risk
recommendations for this project which is underway to implementation. Other aspects which
would be discussed are on the data security especially to Aztek organization (Astani, Ready &
Tessema, 2013). This aspect is very important part to implementation of this project since there
are issues of threats which will be exhibited when the employees are allowed to bring on their
own devices to the place of work. Security is important especially in the flow of the data and
who would have access to it (Caldwell, Zeltmann & Griffin, 2012). When this project is
implemented Aztek Corporation will significantly improve on some of the areas which are
lagging behind and it would also increase on the overall competitive advantage over the other
organization in the same industry.
2.0 review of project in relation to financial industry
2.1 Government regulation
The broad framework of regulation is determined by Australian government. They have the
responsibility to the day to day supervision of the financial organization as well as the market.
Aztek Corporation being part of an industry in the financial sector they need to comply with
certain financial conduct which are relevant to the protection of vital financial information. The
organization needs to look deeply to the privacy Act 1993 before implementing BYOD to the
workplace (Arregui, Maynard & Ahmad, 2016). They government has regulated some laws
which could govern the financial institutions in view of the BYOD aspect. The government has
highlighted that a business entity may which allow their employees to bring their own devices to
the place of work. The laws has clearly highlighted some of the devices which should be brought
are; mobile phone, tablets and laptops. Moreover, the Australian government has explained also
that the business need to outline clearly on the rule which should be aimed at governing the
workers in this aspect of BYOD in the workplace (Arregui, Maynard & Ahmad, 2016).
Moreover, they should also make sure that these rules which they will implement should not be
in collision to the freedom and the rights of the workers. In the event that the workers break the
rules which have been established by the entity they should be fined and punished. Some of the
rules which Aztek Company has established are based on these aspect; the workers should ensure
that the data of the company is not accessible to the outsiders (Caldwell, Zeltmann & Griffin,
2012). Additionally, the information of the business should not be shared to any individuals who
is not part of the company and there flow of the information should be within the business and
the employees only no other third party unless it is stipulated by the business.
In many institutions the aspect of Bring your own device (BYOD) is not supported because of
the shortcoming it bring to the business. In some of the cases the incompetence’s as well as
careless of the staffs has led to exposure of the vital information of the business to third parties or
even to the public (Medudula, Sagar & Gandhi, 2016). The rival firms could use this useful
information to highlight some of the opportunities of the organization and take advantage of the
situation.
The BYOD concept is a vital aspect when it comes to achieving on the goals and the goals of the
organization (Miller, Voas & Hurlburt, 2012). It may help in the reduction of the costs as the
funds which would be used to buy new devices could be channeled towards other projects in the
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

RISK MANAGEMENT 7
business. This project would rely bring forth benefits to the organization and this has been a
trend which is taking the industry by storm (Arregui, Maynard & Ahmad, 2016). BYOD would
help the business and it would likely help the workers to perform better, however, this project
would be associated with some serious shortcoming IT risks.
2.2 The financial services sector overview
Aztek Corporation has been an established financial corporation that has been offering financial
services to the clients across Australia (Astani, Ready & Tessema, 2013). The organization has
encountered various risks. Over the years the company has been concerned with the issue of
ensuring the confidentiality with their data (Mphahlele, 2016). They are aiming at ensuring they
establish objective which are more realistic to the project they want to implement which would
be significant saving of a lot of income.
In the financial services industry there has been establishment of various regulation which have
governed the functions of the organization that are in this sector (Jaumotte, Lall & Papageorgiou,
2013). The government of Australian has greatly encouraged and at the same time supported the
businesses in adopting of the information technology in all their operations since it has been
observed to reduce on the cost to the business (Caldwell, Zeltmann & Griffin, 2012). There is
need of the business in financial industry in Australia to observe all the implemented policies in
relation to the information technology in their new projects. The proposed project which Aztek
organization is aiming to venture may not likely face any critics as other organization are also
aiming to implement on the same to be able to reduce on some of the shortcoming such as
increased cost of purchasing resources.
BYOD in the workplace would likely have some negative impact to the organization as their data
would be exposed and it would be viewed by public individuals or organization (Caldwell,
Zeltmann & Griffin, 2012). Some of the notorious employees may carry data from the
organization which could be accessed by their families or even relative if they are not kept safe.
The confidentiality of the organization of the business is important and therefore, there is need to
keep it safe.
2.3 Current security at Aztek organization.
Aztek organization has been able to manage to all their applications of IT along with the
resources (Thomson, 2012). This clearly shows its security posture which are within their own
business aspects. There is no individual who can gain access to the data of the organization
unless they are connected within the network of the corporation (Mansfield-Devine, 2012). The
network of the organization has been managed by the IT professionals who are employed by this
business entity (Caldwell, Zeltmann & Griffin, 2012). There is use of the access management
systems which have been implemented to secure their system. They are able to monitor as well
as change on any framework within the system to suit their business needs (French, Guo & Shim,
2014). The organization security posture which has been utilized in Aztek Company could have
some risks concerns but the organization ensures there is security of the data (Astani, Ready &
Tessema, 2013). Aztek Company aims at implement the project on BYOD to the workplace,
employees need to use these device in performing their duties. Based on the research more than
seventy two percent of the organization support the BYOD but the threat of the data leakage has
been more prevalent than ever before, as the workers look at the access of the corporate sensitive
information on their mobile devices when they are outside the organization network.
business. This project would rely bring forth benefits to the organization and this has been a
trend which is taking the industry by storm (Arregui, Maynard & Ahmad, 2016). BYOD would
help the business and it would likely help the workers to perform better, however, this project
would be associated with some serious shortcoming IT risks.
2.2 The financial services sector overview
Aztek Corporation has been an established financial corporation that has been offering financial
services to the clients across Australia (Astani, Ready & Tessema, 2013). The organization has
encountered various risks. Over the years the company has been concerned with the issue of
ensuring the confidentiality with their data (Mphahlele, 2016). They are aiming at ensuring they
establish objective which are more realistic to the project they want to implement which would
be significant saving of a lot of income.
In the financial services industry there has been establishment of various regulation which have
governed the functions of the organization that are in this sector (Jaumotte, Lall & Papageorgiou,
2013). The government of Australian has greatly encouraged and at the same time supported the
businesses in adopting of the information technology in all their operations since it has been
observed to reduce on the cost to the business (Caldwell, Zeltmann & Griffin, 2012). There is
need of the business in financial industry in Australia to observe all the implemented policies in
relation to the information technology in their new projects. The proposed project which Aztek
organization is aiming to venture may not likely face any critics as other organization are also
aiming to implement on the same to be able to reduce on some of the shortcoming such as
increased cost of purchasing resources.
BYOD in the workplace would likely have some negative impact to the organization as their data
would be exposed and it would be viewed by public individuals or organization (Caldwell,
Zeltmann & Griffin, 2012). Some of the notorious employees may carry data from the
organization which could be accessed by their families or even relative if they are not kept safe.
The confidentiality of the organization of the business is important and therefore, there is need to
keep it safe.
2.3 Current security at Aztek organization.
Aztek organization has been able to manage to all their applications of IT along with the
resources (Thomson, 2012). This clearly shows its security posture which are within their own
business aspects. There is no individual who can gain access to the data of the organization
unless they are connected within the network of the corporation (Mansfield-Devine, 2012). The
network of the organization has been managed by the IT professionals who are employed by this
business entity (Caldwell, Zeltmann & Griffin, 2012). There is use of the access management
systems which have been implemented to secure their system. They are able to monitor as well
as change on any framework within the system to suit their business needs (French, Guo & Shim,
2014). The organization security posture which has been utilized in Aztek Company could have
some risks concerns but the organization ensures there is security of the data (Astani, Ready &
Tessema, 2013). Aztek Company aims at implement the project on BYOD to the workplace,
employees need to use these device in performing their duties. Based on the research more than
seventy two percent of the organization support the BYOD but the threat of the data leakage has
been more prevalent than ever before, as the workers look at the access of the corporate sensitive
information on their mobile devices when they are outside the organization network.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

RISK MANAGEMENT 8
The sole responsibility in relation to the data security should be shared amongst the providers
and the organization. When the data of the organization has been exposed by the employees to
the public it could lead to devastating effects (Astani, Ready & Tessema, 2013). The
organization could be sued by the customers and get fined heavily especially when the
information about the customers have been breached. The financial institution in most of the
time deals with data which is sensitive and when it is exposed by the employees there are
adverse effect of that company (Caldwell, Zeltmann & Griffin, 2012). There is need to educate
the employees on how to keep the information safe. The data of Aztek Company should only be
accessed and shared within the business. When using their own devices in the workplace there
could be encrypted and passwords so that they are only accessed by individuals who have
authentication (Song, 2014). The employees should not access this information when they leave
place of work, and any information which is accessed while they are home, it is a breach of the
policies of the organization and they could be charged when they are known (Eslahi, Naseri,
Hashim, Tahir & Saad, 2014). Deleting this information when leaving place of work would be
one of step which could be utilized.
2.4 Bring your own device (BYOD) concept.
This concept refers to the policy of permitting the workers to bring their own devices such as the
laptops, tablets and the smartphones to their place of work, and utilize those devices in accessing
the privileged information and applications of the company (Fincham, Fleck, Procter,
Scarbrough, Tierney & Williams, 1995). This phenomenon has been referred to as the
information technology consumerisation. This concept has been making significant inroads
especially to the business world, with about seventy five workers in high growth markets
(Caldwell, Zeltmann & Griffin, 2012). Aztek organization adopting the BYOD concept will be
implemented by information technology department within the business. In this project there
would be selection of the application which are useful to implement and manage the devices
which these staff bring to the workplace (Astani, Ready & Tessema, 2013). The expert should
establish a network connection which would be utilized by the workers to enable them perform
on their duties using their devices. There are few organization which have adequate control
measures in regards to the risk associated with the adoption of this concept (Schwalbe, 2015).
Aztek corporation need to establish guideline which will govern the staff on how to use their
devices while working in the organization.
2.5 Factors of information technology platform that impact BYOD
In most of the organization today they have implemented policies in relation to protecting the
organization data and incorporating the concept of BYOD (Kulkarni, Shelke, Palwe, Solanke,
Belsare & Mohite, 2014). In the event that an employee connect their devices to the network of
the organization, the data is at risk if appropriate mechanism are not in place to address the
confidentiality of the data (Caldwell, Zeltmann & Griffin, 2012). Some of those devices at times
do not have an updated software or perhaps they have a malicious software installed on them and
the owners are not aware. Once these devices are connected they may infect the system in the
organization which could compromise on the data and in some instances leads to data loss.
2.5.1 Benefits and drawback associated with BYOD.
Benefits
Increase productivity: There is increased flexibility as well as productivity. When the workers
are granted access to the corporation data base as well as allowing them to use their own devices
The sole responsibility in relation to the data security should be shared amongst the providers
and the organization. When the data of the organization has been exposed by the employees to
the public it could lead to devastating effects (Astani, Ready & Tessema, 2013). The
organization could be sued by the customers and get fined heavily especially when the
information about the customers have been breached. The financial institution in most of the
time deals with data which is sensitive and when it is exposed by the employees there are
adverse effect of that company (Caldwell, Zeltmann & Griffin, 2012). There is need to educate
the employees on how to keep the information safe. The data of Aztek Company should only be
accessed and shared within the business. When using their own devices in the workplace there
could be encrypted and passwords so that they are only accessed by individuals who have
authentication (Song, 2014). The employees should not access this information when they leave
place of work, and any information which is accessed while they are home, it is a breach of the
policies of the organization and they could be charged when they are known (Eslahi, Naseri,
Hashim, Tahir & Saad, 2014). Deleting this information when leaving place of work would be
one of step which could be utilized.
2.4 Bring your own device (BYOD) concept.
This concept refers to the policy of permitting the workers to bring their own devices such as the
laptops, tablets and the smartphones to their place of work, and utilize those devices in accessing
the privileged information and applications of the company (Fincham, Fleck, Procter,
Scarbrough, Tierney & Williams, 1995). This phenomenon has been referred to as the
information technology consumerisation. This concept has been making significant inroads
especially to the business world, with about seventy five workers in high growth markets
(Caldwell, Zeltmann & Griffin, 2012). Aztek organization adopting the BYOD concept will be
implemented by information technology department within the business. In this project there
would be selection of the application which are useful to implement and manage the devices
which these staff bring to the workplace (Astani, Ready & Tessema, 2013). The expert should
establish a network connection which would be utilized by the workers to enable them perform
on their duties using their devices. There are few organization which have adequate control
measures in regards to the risk associated with the adoption of this concept (Schwalbe, 2015).
Aztek corporation need to establish guideline which will govern the staff on how to use their
devices while working in the organization.
2.5 Factors of information technology platform that impact BYOD
In most of the organization today they have implemented policies in relation to protecting the
organization data and incorporating the concept of BYOD (Kulkarni, Shelke, Palwe, Solanke,
Belsare & Mohite, 2014). In the event that an employee connect their devices to the network of
the organization, the data is at risk if appropriate mechanism are not in place to address the
confidentiality of the data (Caldwell, Zeltmann & Griffin, 2012). Some of those devices at times
do not have an updated software or perhaps they have a malicious software installed on them and
the owners are not aware. Once these devices are connected they may infect the system in the
organization which could compromise on the data and in some instances leads to data loss.
2.5.1 Benefits and drawback associated with BYOD.
Benefits
Increase productivity: There is increased flexibility as well as productivity. When the workers
are granted access to the corporation data base as well as allowing them to use their own devices

RISK MANAGEMENT 9
to streamline on their work it would increase on the work volume they are undertaking (Sangani,
2013).
Increase on the satisfaction of the workers: When a business permit the workers to use their own
devices at the place of work, they tend to enjoy more (Caldwell, Zeltmann & Griffin, 2012).
They would invest additional time to explore as well as understand their devices which is
relation to their duties.
Cost saving: It has been observed that organization could spend less on the software as well as
the hardware. This responsibility tends to be transferred to the employees who take it up as they
view it is a benefit on their end (Vorakulpipat, Polprasert & Siwamogsatham, 2014).
Cutting edge technology: This is a benefit of BYOD in the organization since it tends to
increase the access to the cutting edge technology (King, 2016). The workers tend to upgrade to
the latest devices, as well as accompanying software platforms much faster than the organization.
Drawbacks
Security: This is one of the greatest concern when it comes to using of the personal devices
especially in the work environment (Morrow, 2012). The security fears are in most of the times
arising around the data, since it will be Aztek asset which would be at risk (King, 2016). When
there is insufficient security particularly to the owned devices could lead to exposure of the
sensitive data of the organization to manipulation practices.
Privacy issues: The BYOD usually blur the line between the workers liability as well as the
organizational liability (Scarfo, 2012). This practice may raise various challenges when it comes
to IT department as a result of increased need for the consideration especially in the intrusion of
the privacy.
The copyrights issues: This could arise especially when it comes to the ownerships of any
creations for example the inventions which have been created as well accessed through the
devices of the employee.
3. Risk assessment.
This concept of the BYOD has been associated with the aspects of threats, vulnerabilities as well
as consequences which are the challenges (Disterer & Kleiner, 2013). There is need to carry out
a risk assessment to be able to identify those risk and vulnerabilities to enable the organization to
mitigate them. In this assessment it will identify on the threat, vulnerability, as well as the
consequence.
Management of the unknown third party access to the mobile application: many of the workers
when they install free application in their devices to use and when they utilize then for the
official duties, there could arise a situation of access by the 3rd party especially if they are not
secure hence they can access the sensitive data. This risk may not impact on Aztek organization.
In this risk it is rated as low since the organization has been able to implement mechanism to
handle on the issue.
Probable challenge of the management of data and the compliance: Many of the businesses
ensures that their security is intact especially that of the data. They ensures that both their cloud
based as well as storage hardware devices are secure. Aztec organization due to the nature of
to streamline on their work it would increase on the work volume they are undertaking (Sangani,
2013).
Increase on the satisfaction of the workers: When a business permit the workers to use their own
devices at the place of work, they tend to enjoy more (Caldwell, Zeltmann & Griffin, 2012).
They would invest additional time to explore as well as understand their devices which is
relation to their duties.
Cost saving: It has been observed that organization could spend less on the software as well as
the hardware. This responsibility tends to be transferred to the employees who take it up as they
view it is a benefit on their end (Vorakulpipat, Polprasert & Siwamogsatham, 2014).
Cutting edge technology: This is a benefit of BYOD in the organization since it tends to
increase the access to the cutting edge technology (King, 2016). The workers tend to upgrade to
the latest devices, as well as accompanying software platforms much faster than the organization.
Drawbacks
Security: This is one of the greatest concern when it comes to using of the personal devices
especially in the work environment (Morrow, 2012). The security fears are in most of the times
arising around the data, since it will be Aztek asset which would be at risk (King, 2016). When
there is insufficient security particularly to the owned devices could lead to exposure of the
sensitive data of the organization to manipulation practices.
Privacy issues: The BYOD usually blur the line between the workers liability as well as the
organizational liability (Scarfo, 2012). This practice may raise various challenges when it comes
to IT department as a result of increased need for the consideration especially in the intrusion of
the privacy.
The copyrights issues: This could arise especially when it comes to the ownerships of any
creations for example the inventions which have been created as well accessed through the
devices of the employee.
3. Risk assessment.
This concept of the BYOD has been associated with the aspects of threats, vulnerabilities as well
as consequences which are the challenges (Disterer & Kleiner, 2013). There is need to carry out
a risk assessment to be able to identify those risk and vulnerabilities to enable the organization to
mitigate them. In this assessment it will identify on the threat, vulnerability, as well as the
consequence.
Management of the unknown third party access to the mobile application: many of the workers
when they install free application in their devices to use and when they utilize then for the
official duties, there could arise a situation of access by the 3rd party especially if they are not
secure hence they can access the sensitive data. This risk may not impact on Aztek organization.
In this risk it is rated as low since the organization has been able to implement mechanism to
handle on the issue.
Probable challenge of the management of data and the compliance: Many of the businesses
ensures that their security is intact especially that of the data. They ensures that both their cloud
based as well as storage hardware devices are secure. Aztec organization due to the nature of
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
RISK MANAGEMENT 10
their business usually deals with data that is very sensitive particularly the one containing the
information of the clients. Further, the organization has been able to employ mechanism to
prevent such information from being access by unauthorized individuals.
Probable challenge of the management of the data and compliance: Aztek organization would
likely encounter various challenges especially to the implementation of the data administration
along with the support to compliance. The organization intends clearly outline on the compliance
aspects in relation to the third party applications.
Data leakage as a result of loss of the employee’s devices: many of the devices which are used
by the employees in the workplace do not have a password which is installed in them. In the
event that they get loss, there could be devastating repercussion to the organization if the
information get accessed by another person. To ensure this the organization has urged the
employees to input passwords as well as the data they access is encrypted.
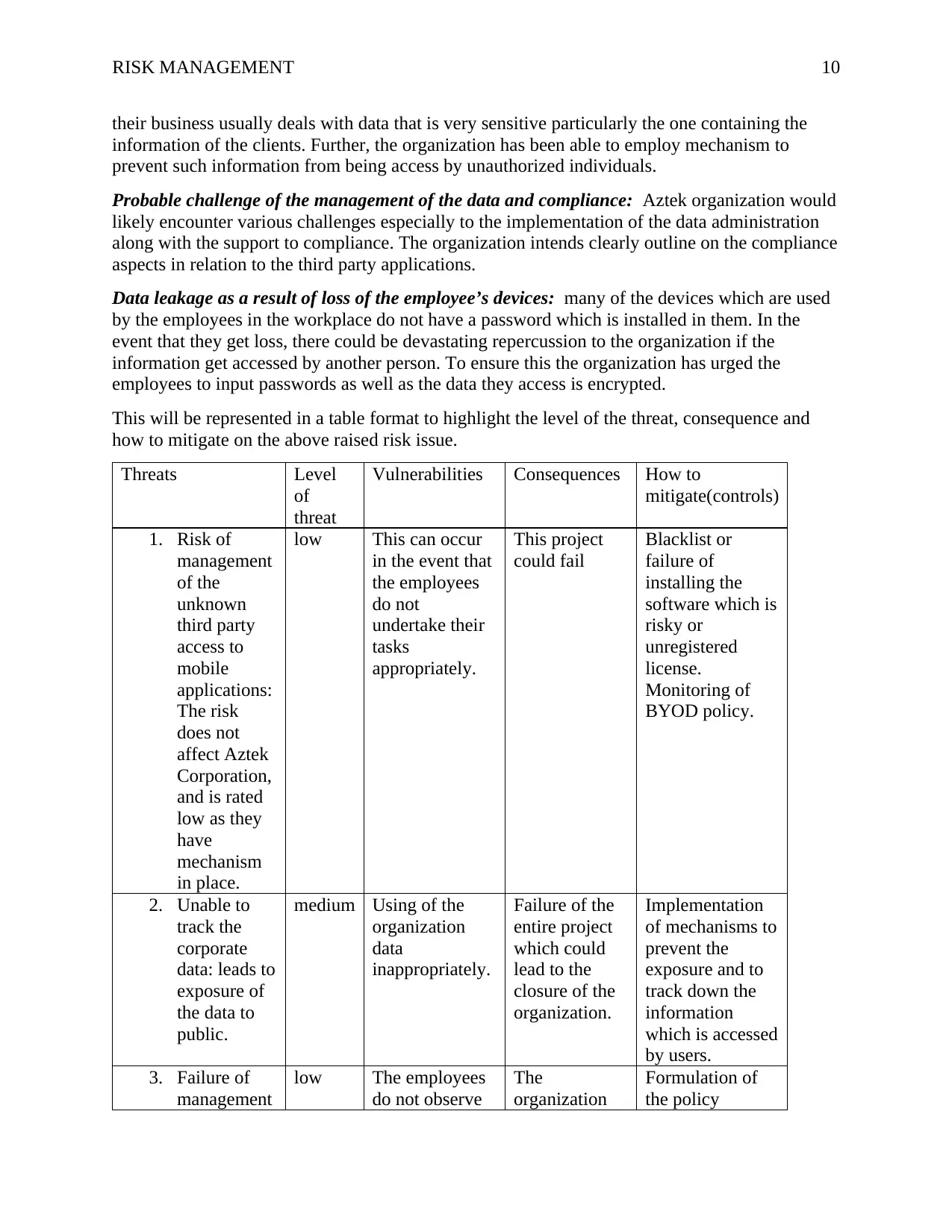
This will be represented in a table format to highlight the level of the threat, consequence and
how to mitigate on the above raised risk issue.
Threats Level
of
threat
Vulnerabilities Consequences How to
mitigate(controls)
1. Risk of
management
of the
unknown
third party
access to
mobile
applications:
The risk
does not
affect Aztek
Corporation,
and is rated
low as they
have
mechanism
in place.
low This can occur
in the event that
the employees
do not
undertake their
tasks
appropriately.
This project
could fail
Blacklist or
failure of
installing the
software which is
risky or
unregistered
license.
Monitoring of
BYOD policy.
2. Unable to
track the
corporate
data: leads to
exposure of
the data to
public.
medium Using of the
organization
data
inappropriately.
Failure of the
entire project
which could
lead to the
closure of the
organization.
Implementation
of mechanisms to
prevent the
exposure and to
track down the
information
which is accessed
by users.
3. Failure of
management
low The employees
do not observe
The
organization
Formulation of
the policy
their business usually deals with data that is very sensitive particularly the one containing the
information of the clients. Further, the organization has been able to employ mechanism to
prevent such information from being access by unauthorized individuals.
Probable challenge of the management of the data and compliance: Aztek organization would
likely encounter various challenges especially to the implementation of the data administration
along with the support to compliance. The organization intends clearly outline on the compliance
aspects in relation to the third party applications.
Data leakage as a result of loss of the employee’s devices: many of the devices which are used
by the employees in the workplace do not have a password which is installed in them. In the
event that they get loss, there could be devastating repercussion to the organization if the
information get accessed by another person. To ensure this the organization has urged the
employees to input passwords as well as the data they access is encrypted.
This will be represented in a table format to highlight the level of the threat, consequence and
how to mitigate on the above raised risk issue.
Threats Level
of
threat
Vulnerabilities Consequences How to
mitigate(controls)
1. Risk of
management
of the
unknown
third party
access to
mobile
applications:
The risk
does not
affect Aztek
Corporation,
and is rated
low as they
have
mechanism
in place.
low This can occur
in the event that
the employees
do not
undertake their
tasks
appropriately.
This project
could fail
Blacklist or
failure of
installing the
software which is
risky or
unregistered
license.
Monitoring of
BYOD policy.
2. Unable to
track the
corporate
data: leads to
exposure of
the data to
public.
medium Using of the
organization
data
inappropriately.
Failure of the
entire project
which could
lead to the
closure of the
organization.
Implementation
of mechanisms to
prevent the
exposure and to
track down the
information
which is accessed
by users.
3. Failure of
management
low The employees
do not observe
The
organization
Formulation of
the policy
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
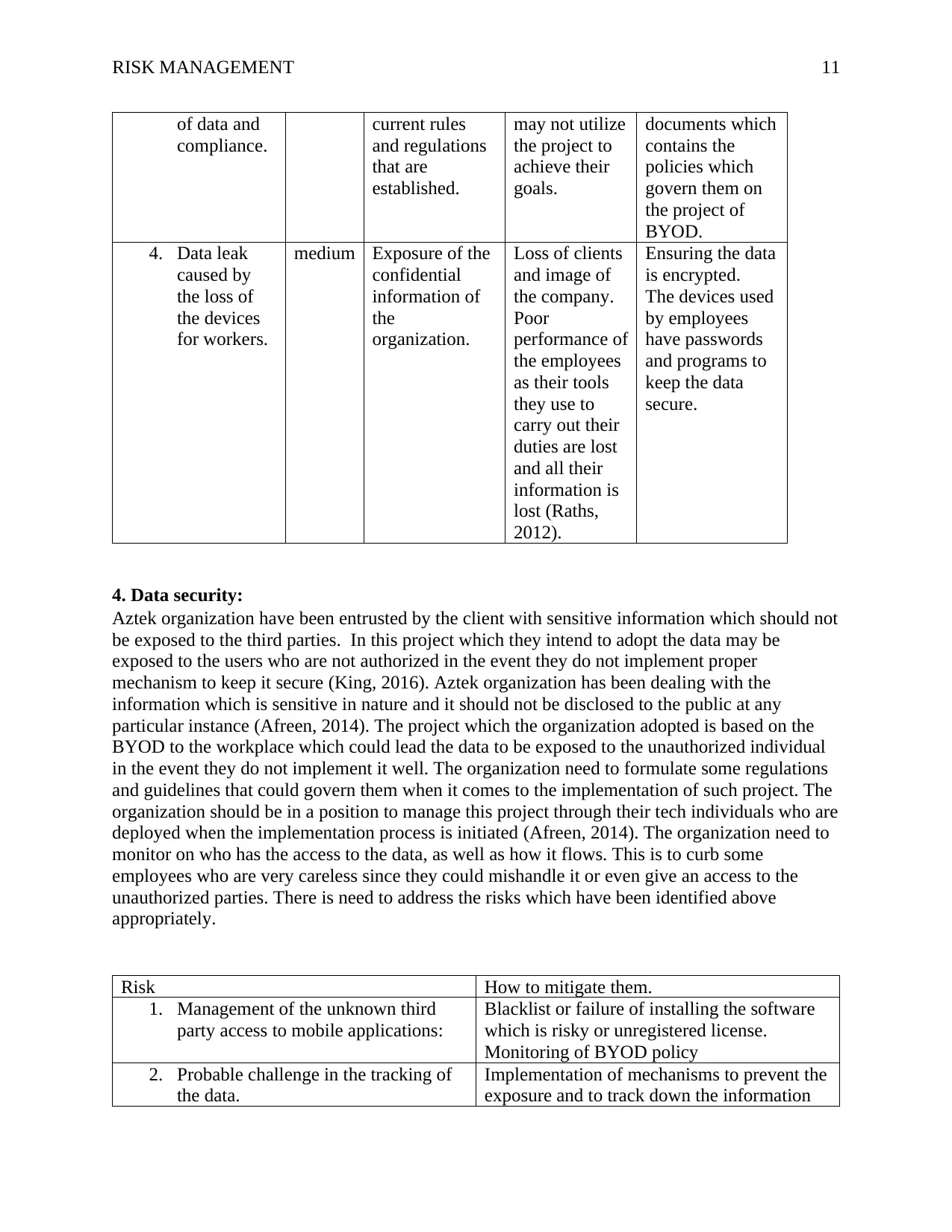
RISK MANAGEMENT 11
of data and
compliance.
current rules
and regulations
that are
established.
may not utilize
the project to
achieve their
goals.
documents which
contains the
policies which
govern them on
the project of
BYOD.
4. Data leak
caused by
the loss of
the devices
for workers.
medium Exposure of the
confidential
information of
the
organization.
Loss of clients
and image of
the company.
Poor
performance of
the employees
as their tools
they use to
carry out their
duties are lost
and all their
information is
lost (Raths,
2012).
Ensuring the data
is encrypted.
The devices used
by employees
have passwords
and programs to
keep the data
secure.
4. Data security:
Aztek organization have been entrusted by the client with sensitive information which should not
be exposed to the third parties. In this project which they intend to adopt the data may be
exposed to the users who are not authorized in the event they do not implement proper
mechanism to keep it secure (King, 2016). Aztek organization has been dealing with the
information which is sensitive in nature and it should not be disclosed to the public at any
particular instance (Afreen, 2014). The project which the organization adopted is based on the
BYOD to the workplace which could lead the data to be exposed to the unauthorized individual
in the event they do not implement it well. The organization need to formulate some regulations
and guidelines that could govern them when it comes to the implementation of such project. The
organization should be in a position to manage this project through their tech individuals who are
deployed when the implementation process is initiated (Afreen, 2014). The organization need to
monitor on who has the access to the data, as well as how it flows. This is to curb some
employees who are very careless since they could mishandle it or even give an access to the
unauthorized parties. There is need to address the risks which have been identified above
appropriately.
Risk How to mitigate them.
1. Management of the unknown third
party access to mobile applications:
Blacklist or failure of installing the software
which is risky or unregistered license.
Monitoring of BYOD policy
2. Probable challenge in the tracking of
the data.
Implementation of mechanisms to prevent the
exposure and to track down the information
of data and
compliance.
current rules
and regulations
that are
established.
may not utilize
the project to
achieve their
goals.
documents which
contains the
policies which
govern them on
the project of
BYOD.
4. Data leak
caused by
the loss of
the devices
for workers.
medium Exposure of the
confidential
information of
the
organization.
Loss of clients
and image of
the company.
Poor
performance of
the employees
as their tools
they use to
carry out their
duties are lost
and all their
information is
lost (Raths,
2012).
Ensuring the data
is encrypted.
The devices used
by employees
have passwords
and programs to
keep the data
secure.
4. Data security:
Aztek organization have been entrusted by the client with sensitive information which should not
be exposed to the third parties. In this project which they intend to adopt the data may be
exposed to the users who are not authorized in the event they do not implement proper
mechanism to keep it secure (King, 2016). Aztek organization has been dealing with the
information which is sensitive in nature and it should not be disclosed to the public at any
particular instance (Afreen, 2014). The project which the organization adopted is based on the
BYOD to the workplace which could lead the data to be exposed to the unauthorized individual
in the event they do not implement it well. The organization need to formulate some regulations
and guidelines that could govern them when it comes to the implementation of such project. The
organization should be in a position to manage this project through their tech individuals who are
deployed when the implementation process is initiated (Afreen, 2014). The organization need to
monitor on who has the access to the data, as well as how it flows. This is to curb some
employees who are very careless since they could mishandle it or even give an access to the
unauthorized parties. There is need to address the risks which have been identified above
appropriately.
Risk How to mitigate them.
1. Management of the unknown third
party access to mobile applications:
Blacklist or failure of installing the software
which is risky or unregistered license.
Monitoring of BYOD policy
2. Probable challenge in the tracking of
the data.
Implementation of mechanisms to prevent the
exposure and to track down the information

RISK MANAGEMENT 12
which is accessed by users.
3. Probable challenge of management of
data and compliance
Formulation of the policy documents which
contains the policies which govern them on
the project of BYOD.
4. Data leakage as a result of loss of the
employee’s devices.
Encryption of the data and password
programs to prevent access of the data and
keep it secure.
5. Recommendations:
The Aztek organization should be able to establish a clear guidelines in regards to the aspect of
BYOD to the workplace. On their guideline policy document it should pertains on the standards
which the employees should act upon when they bring their devices in the workplace. This
should also be incorporated in the employment agreement to curb those employees who would
want to link the information for their own personal gain. Moreover, the organization should train
the employees on this project bring forth the benefits it would bring to both the business and the
employees.
6. Conclusion:
The technology has had a major impact towards the delivery of the financial services especially
to the Aztek organization. Aztek organization is planning to implement the project of BYOD in
the workplace especially the mobile devices such as mobile devices, tablets along with the
laptop. This provide is expected to bring many benefits to the organization, but it is also likely to
bring IT risks. One of the major risk which has been identified in the research is data security
during the implementation process of the project. To be able to mitigate on this issue would be
formulation of regulation that can govern in the implementation of this project. Once the issues
relating to the data security are resolved the project will bring many benefits to both the
organization and the employees.
which is accessed by users.
3. Probable challenge of management of
data and compliance
Formulation of the policy documents which
contains the policies which govern them on
the project of BYOD.
4. Data leakage as a result of loss of the
employee’s devices.
Encryption of the data and password
programs to prevent access of the data and
keep it secure.
5. Recommendations:
The Aztek organization should be able to establish a clear guidelines in regards to the aspect of
BYOD to the workplace. On their guideline policy document it should pertains on the standards
which the employees should act upon when they bring their devices in the workplace. This
should also be incorporated in the employment agreement to curb those employees who would
want to link the information for their own personal gain. Moreover, the organization should train
the employees on this project bring forth the benefits it would bring to both the business and the
employees.
6. Conclusion:
The technology has had a major impact towards the delivery of the financial services especially
to the Aztek organization. Aztek organization is planning to implement the project of BYOD in
the workplace especially the mobile devices such as mobile devices, tablets along with the
laptop. This provide is expected to bring many benefits to the organization, but it is also likely to
bring IT risks. One of the major risk which has been identified in the research is data security
during the implementation process of the project. To be able to mitigate on this issue would be
formulation of regulation that can govern in the implementation of this project. Once the issues
relating to the data security are resolved the project will bring many benefits to both the
organization and the employees.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 14
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





