Case Study: IT Risk Assessment for Aztek Financial's BYOD Project
VerifiedAdded on 2020/04/01
|16
|5118
|65
Case Study
AI Summary
This report presents an IT risk assessment case study for Aztek, an Australian financial services organization, focusing on the security challenges arising from the implementation of a Bring Your Own Device (BYOD) scheme. The assessment explores the current security posture of Aztek and identifies potential risks associated with employees using their personal devices for work, including data security vulnerabilities. The study reviews relevant industry best practices, compliance requirements such as the Workplace Privacy Act and NSW acts, and analyzes how BYOD affects financial institutions. It identifies and assesses risks, utilizing a cybersecurity framework to evaluate identification, detection, protection, response, and recovery measures. The report also examines the security-related data specific to the financial industry, providing insights into the necessary measures for improving security posture and mitigating risks in a BYOD environment. The project review covers the challenges Aztek faces in managing IT infrastructure costs and the regulatory procedures associated with BYOD implementation, while also addressing application and mobile environment risks.

IT Risk Assessment Case Study
Contents
Executive Summary...............................................................................................................................1
Project Review.......................................................................................................................................2
Security Posture of Aztek.......................................................................................................................4
Risk Assessment....................................................................................................................................7
Data Security.......................................................................................................................................12
Conclusions..........................................................................................................................................13
References...........................................................................................................................................14
Executive Summary
This report includes IT risk assessment of a project of Aztek which is a financial services organization
from Australia. The objective is to explore security challenges that would result from
implementation of Bring Your Own Device scheme by the company. At BYOD deployment would
result into addition of personal devices of employees to the company infrastructure and thus, the
security posture of the organization would change upon its adoption. The report includes
exploration of security posture of the company and identification as well as assessment of risks
faced by the organization considering the new posture.
The report would begin with the exploration of the industry best practices utilized for management
of the security systems in organizations using BYOD. It would also explore how the IT project could
get affected by industrial or government needs for compliance. The processes of surveillance,
industrial standards such as Workplace Privacy Act and NSW acts are explored for exploring and
Contents
Executive Summary...............................................................................................................................1
Project Review.......................................................................................................................................2
Security Posture of Aztek.......................................................................................................................4
Risk Assessment....................................................................................................................................7
Data Security.......................................................................................................................................12
Conclusions..........................................................................................................................................13
References...........................................................................................................................................14
Executive Summary
This report includes IT risk assessment of a project of Aztek which is a financial services organization
from Australia. The objective is to explore security challenges that would result from
implementation of Bring Your Own Device scheme by the company. At BYOD deployment would
result into addition of personal devices of employees to the company infrastructure and thus, the
security posture of the organization would change upon its adoption. The report includes
exploration of security posture of the company and identification as well as assessment of risks
faced by the organization considering the new posture.
The report would begin with the exploration of the industry best practices utilized for management
of the security systems in organizations using BYOD. It would also explore how the IT project could
get affected by industrial or government needs for compliance. The processes of surveillance,
industrial standards such as Workplace Privacy Act and NSW acts are explored for exploring and
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

understanding methods that can be used to strengthen the security posture of Aztek when
deploying BYOD in the organization (Engine Yard, Inc., 2014).
The report identifies various vulnerabilities and risks that the company would face as a result of
using mobile and tablet devices of the employees for official use. It also explores various methods
that can be used to protect organization from exploitation of these vulnerabilities (European
Commission , 2010).
The risks identified in the process would be assessed using a cybersecurity framework as the
foundation. This includes formation of risk profile of Aztek, identification of the security systems
used in the company and establishing of a plan for the improvement of the security posture. The five
core functions identified in the framework are explored for assessment including identification,
detection, protection, response and recovery. For each categories and subcategories of risks, the
security controls that can be used are identified (National Treasury, 2011).
Lastly, the report would analyze the security related data of the financial industry to assess how
BYOD affects a financial organization and what specific measures are required to be used by financial
organization for brining improvements and for protecting company from security risks.
Project Review
Aztek is a financial services company based out of Australia. The management of the organization is
facing challenges in managing IT infrastructure costs and is looking forward to minimize the
investments in the IT systems. Thus, the management has decided to implement a BYOD scheme in
the organization thereby allowing its employees to use their own devices for the office work. This
project involves implementation of the components and processes involved in the BYOD scheme
development and implementation (ACHS, 2013).
deploying BYOD in the organization (Engine Yard, Inc., 2014).
The report identifies various vulnerabilities and risks that the company would face as a result of
using mobile and tablet devices of the employees for official use. It also explores various methods
that can be used to protect organization from exploitation of these vulnerabilities (European
Commission , 2010).
The risks identified in the process would be assessed using a cybersecurity framework as the
foundation. This includes formation of risk profile of Aztek, identification of the security systems
used in the company and establishing of a plan for the improvement of the security posture. The five
core functions identified in the framework are explored for assessment including identification,
detection, protection, response and recovery. For each categories and subcategories of risks, the
security controls that can be used are identified (National Treasury, 2011).
Lastly, the report would analyze the security related data of the financial industry to assess how
BYOD affects a financial organization and what specific measures are required to be used by financial
organization for brining improvements and for protecting company from security risks.
Project Review
Aztek is a financial services company based out of Australia. The management of the organization is
facing challenges in managing IT infrastructure costs and is looking forward to minimize the
investments in the IT systems. Thus, the management has decided to implement a BYOD scheme in
the organization thereby allowing its employees to use their own devices for the office work. This
project involves implementation of the components and processes involved in the BYOD scheme
development and implementation (ACHS, 2013).

With the adoption of BYOD, the management would have to comply with several regulatory
procedures and policies. Thus, before beginning implementation of BYOD, there is a need to explore
the related acts and regulatory policies. Australian Capital Territory is a key area of jurisdiction in
Australia that has defined regulator policies. At the level of the organization, policy based
surveillance system can be used for tracking communication by employees. At other levels including
territory, state or federal, there are certain laws that can be used for regulating the access to system
by employees of the organization. Use of access control systems in user devices and prohibition on
tracking or listening of employees are some of the compliance requirements of the project (APM
Group Ltd, 2017).
NSW Act has been made for employee’s management such that they can be made a part of the
surveillance system even when they are out of the premises of their offices. Surveillance can be
done by preventing them from sharing confidential records but this can go against the act. A covert
surveillance is but allowed in which the employee is monitored outside office premises only after a
notification of 14 days in advance (Afaq, et al., 2014).
Workplace Privacy Act 2011 (ACT) provides a framework for surveillance and as per this act
surveillance can be exercised by tracking what is being sent or received by an employee outside the
office premises but on their official email accounts. This may not include exploration of the resources
that employees use on a BYOD device (GILBERT, 2014).
Another applicable act is Telecommunications (Interception and Access) Act 1979 which covers the
permissions on the use of interception by employers on communication is established between two
employees without their knowledge. The act allows companies to only track the content during
interception and not any other related information which can include the email addresses used, time
of communication and other metadata. The transmissions that can be intercepted this way are
defined on the section 5F of the act. This gives protection to the employees from misuse of
resources but it is only limited (Berg, 2010).
procedures and policies. Thus, before beginning implementation of BYOD, there is a need to explore
the related acts and regulatory policies. Australian Capital Territory is a key area of jurisdiction in
Australia that has defined regulator policies. At the level of the organization, policy based
surveillance system can be used for tracking communication by employees. At other levels including
territory, state or federal, there are certain laws that can be used for regulating the access to system
by employees of the organization. Use of access control systems in user devices and prohibition on
tracking or listening of employees are some of the compliance requirements of the project (APM
Group Ltd, 2017).
NSW Act has been made for employee’s management such that they can be made a part of the
surveillance system even when they are out of the premises of their offices. Surveillance can be
done by preventing them from sharing confidential records but this can go against the act. A covert
surveillance is but allowed in which the employee is monitored outside office premises only after a
notification of 14 days in advance (Afaq, et al., 2014).
Workplace Privacy Act 2011 (ACT) provides a framework for surveillance and as per this act
surveillance can be exercised by tracking what is being sent or received by an employee outside the
office premises but on their official email accounts. This may not include exploration of the resources
that employees use on a BYOD device (GILBERT, 2014).
Another applicable act is Telecommunications (Interception and Access) Act 1979 which covers the
permissions on the use of interception by employers on communication is established between two
employees without their knowledge. The act allows companies to only track the content during
interception and not any other related information which can include the email addresses used, time
of communication and other metadata. The transmissions that can be intercepted this way are
defined on the section 5F of the act. This gives protection to the employees from misuse of
resources but it is only limited (Berg, 2010).
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

Employers create a usage policy which complies with the regulators and acts by adhering to rules on
following aspects:
Type of surveillance that tracks communication
How would surveillance be done
If surveillance is intermittent or continuous
Will it be for a limited time or throughout employment (Alali & Yeh, 2012)
As per the Privacy Act (APP 5), the policy can have following provisions:
If the content is being shared between two employees, company may have visibility to it
No personal information of consequence of the personal communicated between employee
and others may be recorded.
Employees must have the knowledge about what information is made visible to employer
The privacy policy can define some access and usage procedures in case of personal
communications (European Commission , 2010)
The policy can also include procedures of data reporting inside and outside of the company
(GILBERT, 2014)
Security Posture of Aztek
When BYOD devices would be added to the corporate network of the company, the security posture
of the company would change as the personal devices of employees would become a part of the
critical infrastructure of the organization. Thus, considerations should be made for the risks that can
arise as a result while building strategies for security management in the organization such that its
security posture can be bolstered (Avdoshin & Pesotskaya, 2011).
In the finance industry, there are certain barriers to implementation of BYOD because of the security
risks attached. In order to cope with these risks, regulations have been defined by various countries
following aspects:
Type of surveillance that tracks communication
How would surveillance be done
If surveillance is intermittent or continuous
Will it be for a limited time or throughout employment (Alali & Yeh, 2012)
As per the Privacy Act (APP 5), the policy can have following provisions:
If the content is being shared between two employees, company may have visibility to it
No personal information of consequence of the personal communicated between employee
and others may be recorded.
Employees must have the knowledge about what information is made visible to employer
The privacy policy can define some access and usage procedures in case of personal
communications (European Commission , 2010)
The policy can also include procedures of data reporting inside and outside of the company
(GILBERT, 2014)
Security Posture of Aztek
When BYOD devices would be added to the corporate network of the company, the security posture
of the company would change as the personal devices of employees would become a part of the
critical infrastructure of the organization. Thus, considerations should be made for the risks that can
arise as a result while building strategies for security management in the organization such that its
security posture can be bolstered (Avdoshin & Pesotskaya, 2011).
In the finance industry, there are certain barriers to implementation of BYOD because of the security
risks attached. In order to cope with these risks, regulations have been defined by various countries
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

and the industries. Aztek would need to comply with these regulations which can make it challenging
for the company to control the mobile device used by its employees outside the work premises.
However, organization can use certain ways of protection that have been used in the financial
industry such as (Bayne, 2002):
Securing Mobile Devices: Companies used to give mobile phone devices to their employees and all
these devices were mostly taken from the same manufacturer or OEM. This made it easy for the
organization to develop security policies and establish control procedures through a unified interface
for management. However, with BYOD devices coming into system, the devices would not have the
same make or OEM supplier and thus, establishing control over these devices can be much more
challenging for the organization. As the choice of device is on the employee, there would not be any
uniformity in the devices distribution and thus, the device portfolio would very dynamic (Oracle,
2009). Aztek has security controls infrastructure established for its owned devices that was used
earlier and now, there is a need to use the same to manage multitude of devices that come with
different hardware and different operating systems (RBI, RESERVE BANK OF INDIA). In such a case,
the old security controls would not work with the device specific or application specific
vulnerabilities eve in the case where device management is implemented (Bodicha, 2005).
A way of protection could be locking devices but it would prohibit users from many personal uses
which would discourage them from using their own devices for work. Thus, another approach is
needed which is both secure and flexible. Specific user requirements have to be understood by the
organization while developing a plan for the risk management in BYOD environment (Bhatta, 2008).
Risks that can arise from the use of BYOD devices can cause risks of lost or stolen devices, physical
access to device by third person, difference in the end user, lack of awareness of security aspects in
employees, and risk to data because of increased level of access. Stolen devices can pose great risk
to Aztek if it is not sufficiently protected by the employees using it. A user stealing the device can use
it for connecting to the organization VPN network and get the access to critical or confidential data
for the company to control the mobile device used by its employees outside the work premises.
However, organization can use certain ways of protection that have been used in the financial
industry such as (Bayne, 2002):
Securing Mobile Devices: Companies used to give mobile phone devices to their employees and all
these devices were mostly taken from the same manufacturer or OEM. This made it easy for the
organization to develop security policies and establish control procedures through a unified interface
for management. However, with BYOD devices coming into system, the devices would not have the
same make or OEM supplier and thus, establishing control over these devices can be much more
challenging for the organization. As the choice of device is on the employee, there would not be any
uniformity in the devices distribution and thus, the device portfolio would very dynamic (Oracle,
2009). Aztek has security controls infrastructure established for its owned devices that was used
earlier and now, there is a need to use the same to manage multitude of devices that come with
different hardware and different operating systems (RBI, RESERVE BANK OF INDIA). In such a case,
the old security controls would not work with the device specific or application specific
vulnerabilities eve in the case where device management is implemented (Bodicha, 2005).
A way of protection could be locking devices but it would prohibit users from many personal uses
which would discourage them from using their own devices for work. Thus, another approach is
needed which is both secure and flexible. Specific user requirements have to be understood by the
organization while developing a plan for the risk management in BYOD environment (Bhatta, 2008).
Risks that can arise from the use of BYOD devices can cause risks of lost or stolen devices, physical
access to device by third person, difference in the end user, lack of awareness of security aspects in
employees, and risk to data because of increased level of access. Stolen devices can pose great risk
to Aztek if it is not sufficiently protected by the employees using it. A user stealing the device can use
it for connecting to the organization VPN network and get the access to critical or confidential data

of the organization. In such cases, protection can be enhanced if the employee used password and
encryption on the device and organization application for access (Rule Works, 2017). Aztek can
remotely establish connection to the network with the device such that it becomes possible to wipe
out the device in case of such risks. This would prevent the security posture of the company from
getting affected (HP Enterprise, 2015).
Attackers can also gain physical access to a device eve on premises or outside it which would again
pose eve higher level of risk to the company. In case the employee has been using old devices, the
risks are even more pronounced as the security measures would not be very robust then. Aztek must
define a policy stating the minimum specifications for the devices to be included in the BYOD to
ensure that the devices are not too old (CDC, 2006).
When employees use their personal devices at work, they have an ownership for the device and
thus, would like to have the highest level of control for themselves. This can cause problems of jail
breaking in to the system such that the user ends up removing critical security features without the
management knowledge. This would affect the security posture of the organization by reducing its
level of protection (Campbell, 2005).
Aztek can use certain basic security measures to enhance its security posture such as:
Investigate individual device models to identify risk scenarios
Enforce security policy through mobile device management solution
Use common industrial security practices such as device encryption and remove wiping of
devices
Set a baseline for the use of software and operating systems on the devices (Chan, Lam,
Chan, & Cheung, 2008)
encryption on the device and organization application for access (Rule Works, 2017). Aztek can
remotely establish connection to the network with the device such that it becomes possible to wipe
out the device in case of such risks. This would prevent the security posture of the company from
getting affected (HP Enterprise, 2015).
Attackers can also gain physical access to a device eve on premises or outside it which would again
pose eve higher level of risk to the company. In case the employee has been using old devices, the
risks are even more pronounced as the security measures would not be very robust then. Aztek must
define a policy stating the minimum specifications for the devices to be included in the BYOD to
ensure that the devices are not too old (CDC, 2006).
When employees use their personal devices at work, they have an ownership for the device and
thus, would like to have the highest level of control for themselves. This can cause problems of jail
breaking in to the system such that the user ends up removing critical security features without the
management knowledge. This would affect the security posture of the organization by reducing its
level of protection (Campbell, 2005).
Aztek can use certain basic security measures to enhance its security posture such as:
Investigate individual device models to identify risk scenarios
Enforce security policy through mobile device management solution
Use common industrial security practices such as device encryption and remove wiping of
devices
Set a baseline for the use of software and operating systems on the devices (Chan, Lam,
Chan, & Cheung, 2008)
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

Addressing App Risks: Application related risks can be caused because of installation of malicious
software applications in mobile devices. This software may attempt to connect to the corporate
applications and exploit its vulnerabilities. Thus, every device must have a malware protection
installed and Aztek must ensure that all employees in the BYOD scheme are taking this security
measure. Such risks can increase if the devices are not managed by the users properly. Thus, the
sensitive data of the company may be compartmentalized to reduce this risk (Chan, Lam, Chan, &
Cheung, 2008).
Managing mobile environment: Software used in a mobile device can be regularly upgraded or its
settings can be customised to enhance protection. If the devices are not updated properly then it
can lead to vulnerabilities and thus, the company must ensure that the employees of the
organization are regularly updating the patches on the mobile devices to keep the mobile
environment safe for the organization (Curtis & Carey, 2012).
Organization may define support and usage policy for the mobile devices which would include
patching and the process of patching defined for the employees. Self-service solutions may be
suggested to and used by employees to enhance support mechanism (HP Enterprise, 2015).
Risk Assessment
Cybersecurity framework defines some security practices that are flexible, cost-effective, repeatable,
prioritized, and performance based. The regulatory bodies along with the industry experts have
identified these practices to include them in the security framework. The framework also gives a
mechanism for defining the security posture, defining the target state of network, prioritize
opportunities for improvement in the security posture, assessing the progress and communicating
security risks to stakeholders (Delhi Government, 2014).
software applications in mobile devices. This software may attempt to connect to the corporate
applications and exploit its vulnerabilities. Thus, every device must have a malware protection
installed and Aztek must ensure that all employees in the BYOD scheme are taking this security
measure. Such risks can increase if the devices are not managed by the users properly. Thus, the
sensitive data of the company may be compartmentalized to reduce this risk (Chan, Lam, Chan, &
Cheung, 2008).
Managing mobile environment: Software used in a mobile device can be regularly upgraded or its
settings can be customised to enhance protection. If the devices are not updated properly then it
can lead to vulnerabilities and thus, the company must ensure that the employees of the
organization are regularly updating the patches on the mobile devices to keep the mobile
environment safe for the organization (Curtis & Carey, 2012).
Organization may define support and usage policy for the mobile devices which would include
patching and the process of patching defined for the employees. Self-service solutions may be
suggested to and used by employees to enhance support mechanism (HP Enterprise, 2015).
Risk Assessment
Cybersecurity framework defines some security practices that are flexible, cost-effective, repeatable,
prioritized, and performance based. The regulatory bodies along with the industry experts have
identified these practices to include them in the security framework. The framework also gives a
mechanism for defining the security posture, defining the target state of network, prioritize
opportunities for improvement in the security posture, assessing the progress and communicating
security risks to stakeholders (Delhi Government, 2014).
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

A security checklist can be created for an organization based on the functions, categories and
references used by the organization to maintain its security posture. Functions can include risk
identification, asset protection, incident detection, response plan, and data recovery (Tasmania
Government, 2008). Categories can be access control, intrusion detection, and asset management
with subcategories like data protection, notification upon threat detection, and more. Information
references can be obtained from the guidance provide by the industry for improving security posture
of Aztek (E&Y, 2013).
Different tiers of security measures have been defined by the security framework that can be used
for move up the level of protection in Aztek (Eccles & Bruce, 2010). They include:
Tier 1: It provides partial protection to organizations with integration of risk management
programs and processes that are not formalized
Tier 2: It provides formal risk management processes and the security activities that are
prioritized (Paschke, 2014)
Tier 3: It includes risk management information, processes and security procedures that
provide repeatable protection measures. The methods defined at this level are consistent in
their usage and help organizations respond to changes to adapt security measures
accordingly such that the security posture of the organization can be maintained (Health and
Safety Authority, 2006)
Tier 4: At this level, organizations respond to changes in the organization and adapt to the
changing needs of the security systems as per the changing security landscape and added
threats. At this level, security risk management becomes the part of the culture of the
organization (Elky, 2006)
The cycbersecuirty framework can be used to review the security policies and practices in Aztek such
that if there is any need for improvement then it can be identified. Moreover, it would also serve as
references used by the organization to maintain its security posture. Functions can include risk
identification, asset protection, incident detection, response plan, and data recovery (Tasmania
Government, 2008). Categories can be access control, intrusion detection, and asset management
with subcategories like data protection, notification upon threat detection, and more. Information
references can be obtained from the guidance provide by the industry for improving security posture
of Aztek (E&Y, 2013).
Different tiers of security measures have been defined by the security framework that can be used
for move up the level of protection in Aztek (Eccles & Bruce, 2010). They include:
Tier 1: It provides partial protection to organizations with integration of risk management
programs and processes that are not formalized
Tier 2: It provides formal risk management processes and the security activities that are
prioritized (Paschke, 2014)
Tier 3: It includes risk management information, processes and security procedures that
provide repeatable protection measures. The methods defined at this level are consistent in
their usage and help organizations respond to changes to adapt security measures
accordingly such that the security posture of the organization can be maintained (Health and
Safety Authority, 2006)
Tier 4: At this level, organizations respond to changes in the organization and adapt to the
changing needs of the security systems as per the changing security landscape and added
threats. At this level, security risk management becomes the part of the culture of the
organization (Elky, 2006)
The cycbersecuirty framework can be used to review the security policies and practices in Aztek such
that if there is any need for improvement then it can be identified. Moreover, it would also serve as

a guide for communicate security risk to the stakeholders and enforcing policies for protection in the
company.
Security Profile Review: the security profile of the organization can be reviewed to understand how
company is identifying risks, detecting threats, protecting its IT assets, responding to threats and
recovering from security breaches. The currently security structure used by the company is adapted
for the traditional structure of the organization in which all the devices were used internally and
thus, the modifications are required to enhance protection levels to accommodate security
measures for BYOD devices (John Snow, Inc., 2010).
Establishing security program: A security program can be established by Aztek using following
steps:
Scoping and prioritizing of the security objectives for the organization considering the IT
assets and systems
Once scoping is done, the systems are studied to identify threats and vulnerabilities. For this,
Aztek can explore the financial and personal data of customers to understand if there is any
possibility of losing this data. Vulnerabilities can affect the organization when its employees
would connect the BYOD devices to the corporate network outside the secure environment
of Aztek (WatchGaurd, 2013)
The current security profile of Aztek can help define categories and subcategories for risk
management. Key categories that can be defined for the organization include identify thefts,
unauthorized access, financial fraud and financial records alteration (NCSU, 2017).
Based on the identified categories, risk assessment would be done for each risk including:
o Identity Thefts: If the data of the customers of Aztek gets stolen then it can get
misused for launching attacks on the company or to access the financial data of the
user. While identity theft can be dangerous for the customers, it can also damage
company.
Security Profile Review: the security profile of the organization can be reviewed to understand how
company is identifying risks, detecting threats, protecting its IT assets, responding to threats and
recovering from security breaches. The currently security structure used by the company is adapted
for the traditional structure of the organization in which all the devices were used internally and
thus, the modifications are required to enhance protection levels to accommodate security
measures for BYOD devices (John Snow, Inc., 2010).
Establishing security program: A security program can be established by Aztek using following
steps:
Scoping and prioritizing of the security objectives for the organization considering the IT
assets and systems
Once scoping is done, the systems are studied to identify threats and vulnerabilities. For this,
Aztek can explore the financial and personal data of customers to understand if there is any
possibility of losing this data. Vulnerabilities can affect the organization when its employees
would connect the BYOD devices to the corporate network outside the secure environment
of Aztek (WatchGaurd, 2013)
The current security profile of Aztek can help define categories and subcategories for risk
management. Key categories that can be defined for the organization include identify thefts,
unauthorized access, financial fraud and financial records alteration (NCSU, 2017).
Based on the identified categories, risk assessment would be done for each risk including:
o Identity Thefts: If the data of the customers of Aztek gets stolen then it can get
misused for launching attacks on the company or to access the financial data of the
user. While identity theft can be dangerous for the customers, it can also damage
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

the reputation of the financial organization thereby affecting the sales and revenues
of the organization as the company would lose the trust of its customers.
o Alteration of Financial Records: Some attackers use modification as a technique for
hiding the money that is with the company such that the hidden figures can be used
as a cover for taking money of customers without the knowledge of the account
holders of the organization. Such loses can grow big over time and only then does
the company have realization of the threat (La Trobe University, 2017)
o Unauthorized Access: If hackers get access to user accounts or company accounts,
they can launch attacks on the systems of the company severely affecting its security
position. DDOS is one type of attack that can be launched with unauthorized access
for causing disruption in working by blocking services from genuine users.
o Financial Frauds: Financial frauds happen when the credentials of account users are
stolen by unauthorized user. The credentials can then be used to gain monetary
benefits thereby causing losses to the financial institution. Such frauds not just affect
a single organization but also the entire finance industry as the customers would
lose trust on the security systems of financial companies.
Stakeholder profiles can be studied to identify a target profiles affected by each type of risk
and when these profiles are communicated to stakeholders, it becomes easy from them to
understand the security needs of the organization. Profiling would also help Aztek
understand its stakeholder requirements and their influence on the risks identified. Various
stakeholder requirements that can be identified for Aztek include:
Risk Category Stakeholders Requirements
Identity Thefts Aztek Employees
Account Users
Their personal information is stored with the Aztek
which needs to be protected
of the organization as the company would lose the trust of its customers.
o Alteration of Financial Records: Some attackers use modification as a technique for
hiding the money that is with the company such that the hidden figures can be used
as a cover for taking money of customers without the knowledge of the account
holders of the organization. Such loses can grow big over time and only then does
the company have realization of the threat (La Trobe University, 2017)
o Unauthorized Access: If hackers get access to user accounts or company accounts,
they can launch attacks on the systems of the company severely affecting its security
position. DDOS is one type of attack that can be launched with unauthorized access
for causing disruption in working by blocking services from genuine users.
o Financial Frauds: Financial frauds happen when the credentials of account users are
stolen by unauthorized user. The credentials can then be used to gain monetary
benefits thereby causing losses to the financial institution. Such frauds not just affect
a single organization but also the entire finance industry as the customers would
lose trust on the security systems of financial companies.
Stakeholder profiles can be studied to identify a target profiles affected by each type of risk
and when these profiles are communicated to stakeholders, it becomes easy from them to
understand the security needs of the organization. Profiling would also help Aztek
understand its stakeholder requirements and their influence on the risks identified. Various
stakeholder requirements that can be identified for Aztek include:
Risk Category Stakeholders Requirements
Identity Thefts Aztek Employees
Account Users
Their personal information is stored with the Aztek
which needs to be protected
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
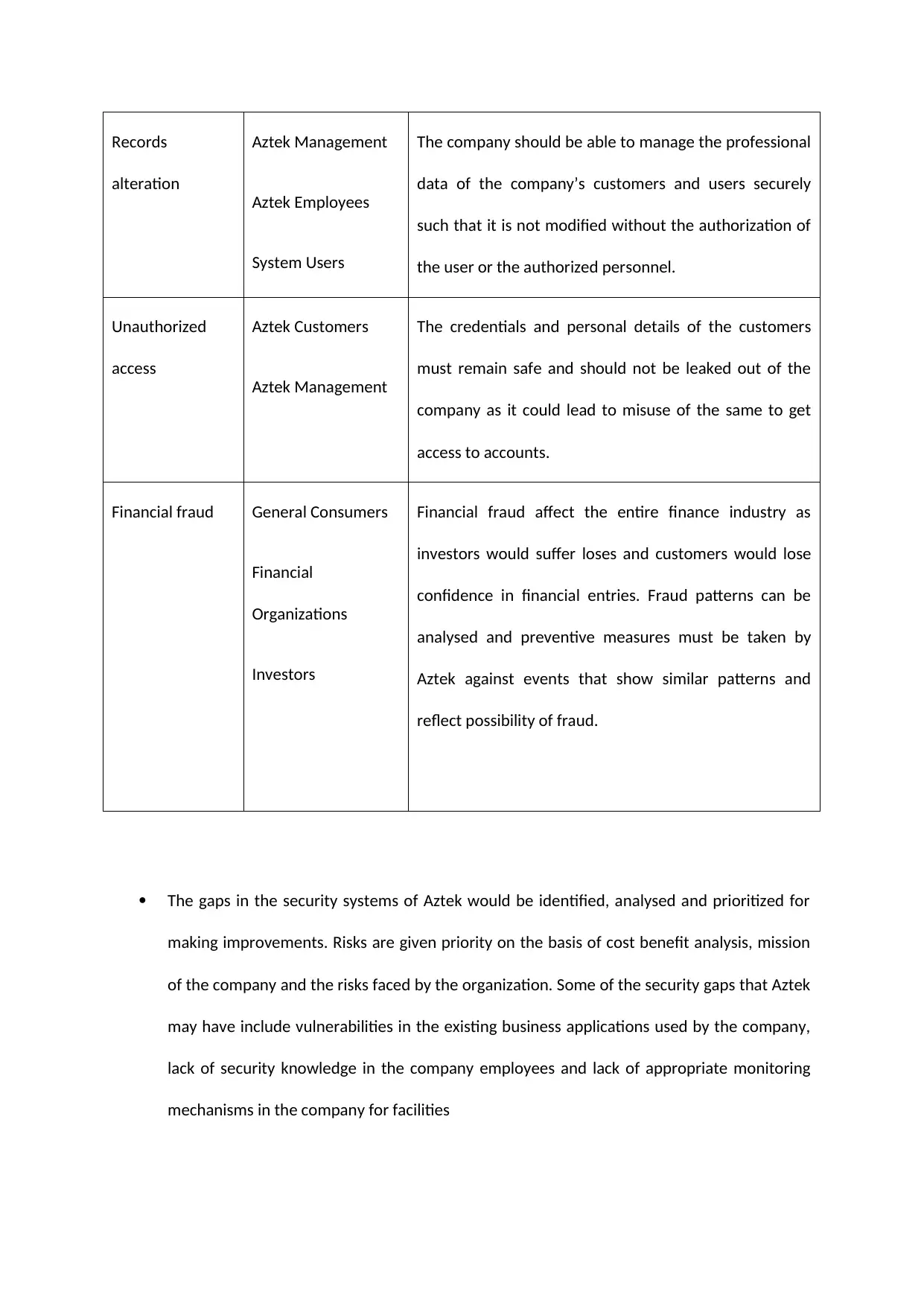
Records
alteration
Aztek Management
Aztek Employees
System Users
The company should be able to manage the professional
data of the company’s customers and users securely
such that it is not modified without the authorization of
the user or the authorized personnel.
Unauthorized
access
Aztek Customers
Aztek Management
The credentials and personal details of the customers
must remain safe and should not be leaked out of the
company as it could lead to misuse of the same to get
access to accounts.
Financial fraud General Consumers
Financial
Organizations
Investors
Financial fraud affect the entire finance industry as
investors would suffer loses and customers would lose
confidence in financial entries. Fraud patterns can be
analysed and preventive measures must be taken by
Aztek against events that show similar patterns and
reflect possibility of fraud.
The gaps in the security systems of Aztek would be identified, analysed and prioritized for
making improvements. Risks are given priority on the basis of cost benefit analysis, mission
of the company and the risks faced by the organization. Some of the security gaps that Aztek
may have include vulnerabilities in the existing business applications used by the company,
lack of security knowledge in the company employees and lack of appropriate monitoring
mechanisms in the company for facilities
alteration
Aztek Management
Aztek Employees
System Users
The company should be able to manage the professional
data of the company’s customers and users securely
such that it is not modified without the authorization of
the user or the authorized personnel.
Unauthorized
access
Aztek Customers
Aztek Management
The credentials and personal details of the customers
must remain safe and should not be leaked out of the
company as it could lead to misuse of the same to get
access to accounts.
Financial fraud General Consumers
Financial
Organizations
Investors
Financial fraud affect the entire finance industry as
investors would suffer loses and customers would lose
confidence in financial entries. Fraud patterns can be
analysed and preventive measures must be taken by
Aztek against events that show similar patterns and
reflect possibility of fraud.
The gaps in the security systems of Aztek would be identified, analysed and prioritized for
making improvements. Risks are given priority on the basis of cost benefit analysis, mission
of the company and the risks faced by the organization. Some of the security gaps that Aztek
may have include vulnerabilities in the existing business applications used by the company,
lack of security knowledge in the company employees and lack of appropriate monitoring
mechanisms in the company for facilities

The security plan would be implemented for managing risks in each category as well as
subcategory (NIST, 2014).
Opportunity Identification: Common industry practices used for developing security programs can
be studied to identify best practices and the same can be learned from for developing security plan
of Aztek. Various industry best practices may be studied to indentify opportunities for improvement
in the security program. Some security best practices used in the finance industry are:
Use of a layered infrastructure that can differentiate between the trusted and untrusted
access methods on devices.
Use of stringent control mechanisms for authentication over the mobile devices for gaining
access to critical business applications (NIST, 2014)
An awareness program must be run in the company for employees to understand the
security related threats, their implications and protective measures to be taken
Data Security
A major risk in IT today is the probability of losing critical data of an organization. If appropriate
policies are defined for various aspects such as remote access, wireless access, incidence response,
privacy, social media usage and code of conduct, it can help reduce risks to data. Devices can be
secured through the use of multiple security measures such as authorization, encryption, tracking,
MDM, remote wiping, control compensation, sandboxing and security inventory processing.
Employees can be trained on how to use the devices securely and what can cause vulnerabilities in
the system if they used their own devices (Paschke, 2014).
Biggest security risks could be faced by Aztek when using BYOD devices due to increased exposure of
the corporate data as they would be connected to the end points. If BYOD devices have to be
subcategory (NIST, 2014).
Opportunity Identification: Common industry practices used for developing security programs can
be studied to identify best practices and the same can be learned from for developing security plan
of Aztek. Various industry best practices may be studied to indentify opportunities for improvement
in the security program. Some security best practices used in the finance industry are:
Use of a layered infrastructure that can differentiate between the trusted and untrusted
access methods on devices.
Use of stringent control mechanisms for authentication over the mobile devices for gaining
access to critical business applications (NIST, 2014)
An awareness program must be run in the company for employees to understand the
security related threats, their implications and protective measures to be taken
Data Security
A major risk in IT today is the probability of losing critical data of an organization. If appropriate
policies are defined for various aspects such as remote access, wireless access, incidence response,
privacy, social media usage and code of conduct, it can help reduce risks to data. Devices can be
secured through the use of multiple security measures such as authorization, encryption, tracking,
MDM, remote wiping, control compensation, sandboxing and security inventory processing.
Employees can be trained on how to use the devices securely and what can cause vulnerabilities in
the system if they used their own devices (Paschke, 2014).
Biggest security risks could be faced by Aztek when using BYOD devices due to increased exposure of
the corporate data as they would be connected to the end points. If BYOD devices have to be
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 16
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





