ITC596 Case Study: Aztek's IT Risk Management & Tech Decisions
VerifiedAdded on 2020/06/06
|16
|5525
|51
Case Study
AI Summary
This case study provides an IT risk assessment for Aztek, a fictional finance company, focusing on significant technology decisions. It examines the impact of allowing employees to use personal devices, the adoption of cloud computing, and the implementation of online software and mobile apps. The report covers government and industry regulations, the company's security posture, threats, vulnerabilities, and consequences, and data security measures. It highlights the risks associated with employee-owned devices, such as reduced productivity, security breaches, and malware infections. Recommendations are provided to improve the company's security policies and procedures, enhance data protection, and increase overall productivity. The case study also touches on the impact of IT failures on stakeholders and the importance of aligning technology decisions with business objectives. Desklib offers a platform to explore similar case studies and solved assignments.

IT Risks Management
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

TABLE OF CONTENTS
1. Executive Summary.....................................................................................................................2
2. Government and industry regulation to protect companies from hacking:.............................3
3. Security posture.......................................................................................................................5
4. Threats, vulnerabilities and consequences assessment...........................................................7
5 Data security.............................................................................................................................9
CONCLUSION..............................................................................................................................10
REFERENCES..............................................................................................................................12
1
1. Executive Summary.....................................................................................................................2
2. Government and industry regulation to protect companies from hacking:.............................3
3. Security posture.......................................................................................................................5
4. Threats, vulnerabilities and consequences assessment...........................................................7
5 Data security.............................................................................................................................9
CONCLUSION..............................................................................................................................10
REFERENCES..............................................................................................................................12
1

1. Executive Summary
Information technology is one of the major part of the global industry. It has increased
productivity in the world and has taken one of the major part of the economic growth. IT
industry has taken various aspects in terms of development of the country. The organisation
which operates in this industry has to hire the best technical applicants which can help them to
resolve their technical related issues. In this report, the focus is given on IT security and risk
management which the company its facing while operating its business. The organisation has
allowed its employees to bring their laptops, tablets and mobile phones so that they can complete
their tasks easily.
Further, the Aztek has used various cloud computing technology to move their data on
the cloud. This will help the company to safely place its bulk of information on the cloud as it is
the best medium to store its several important information. Further, Aztek has implemented
various IT technologies like online software which helped the customers to transfer and pay their
amount through online. Further, it has introduced various ATMs and other system which has
reduced efforts of employees and customers. It has also made use of mobile apps networking
technologies like Ipv6 which helps in securing data and upgrading users account related
information up to date. All theses technologies has played an important role in maintaining the
business operations of Aztek in Australia.
The final assessment for ITC 596 is to deliver IT Risk Assessment Case Study in support
of a significant technology decision that is to be taken by a fictional company called Aztek. ITC
596 case study has been taken into account to understand the business operation of the company
which is working on reducing IT risks and problems. Stakeholders has also faced different
problems due to failure of IT technologies while investing their funds in companies different
policies. They have tried to find various solutions so that they can easily understand different
norms and conditions of Aztek and invest their money successfully. Stakeholders have also
made clear opinions which they have understood properly and use them directly in making their
decisions.
Further, the risk of bringing personal devices like laptops, tablets and mobile is discussed.
The organisation is facing the problem of employees distraction from their work and their less
contribution towards organisation's targets etc. Due to their insecure system Aztek is facing
problems of their system and server failure which are creating great problems for them. This has
2
Information technology is one of the major part of the global industry. It has increased
productivity in the world and has taken one of the major part of the economic growth. IT
industry has taken various aspects in terms of development of the country. The organisation
which operates in this industry has to hire the best technical applicants which can help them to
resolve their technical related issues. In this report, the focus is given on IT security and risk
management which the company its facing while operating its business. The organisation has
allowed its employees to bring their laptops, tablets and mobile phones so that they can complete
their tasks easily.
Further, the Aztek has used various cloud computing technology to move their data on
the cloud. This will help the company to safely place its bulk of information on the cloud as it is
the best medium to store its several important information. Further, Aztek has implemented
various IT technologies like online software which helped the customers to transfer and pay their
amount through online. Further, it has introduced various ATMs and other system which has
reduced efforts of employees and customers. It has also made use of mobile apps networking
technologies like Ipv6 which helps in securing data and upgrading users account related
information up to date. All theses technologies has played an important role in maintaining the
business operations of Aztek in Australia.
The final assessment for ITC 596 is to deliver IT Risk Assessment Case Study in support
of a significant technology decision that is to be taken by a fictional company called Aztek. ITC
596 case study has been taken into account to understand the business operation of the company
which is working on reducing IT risks and problems. Stakeholders has also faced different
problems due to failure of IT technologies while investing their funds in companies different
policies. They have tried to find various solutions so that they can easily understand different
norms and conditions of Aztek and invest their money successfully. Stakeholders have also
made clear opinions which they have understood properly and use them directly in making their
decisions.
Further, the risk of bringing personal devices like laptops, tablets and mobile is discussed.
The organisation is facing the problem of employees distraction from their work and their less
contribution towards organisation's targets etc. Due to their insecure system Aztek is facing
problems of their system and server failure which are creating great problems for them. This has
2
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

also included various problems like hanging, hacking of important information, lose of important
information etc. Further, this has also affected the performance and reputation of the company.
Further, this has also affected their soft running operation of the company which has adversely
affected their image in front of their customers. IT security policies and procedures are taken by
the finance company Aztek to reduce IT risks and challenges. It has employed various technical
staff which is expert in resolving technical issues and handling various challenges from hackers,
viruses and bugs. It has also hired experts which protects their company from serious and
dangerous threats of cloud computing and other technologies. The organisation has also taken
data security measures so that they can control the illegal activities of their employees in the
workplace. Thereafter, recommendation are given to improve the productivity of the company.
2. Government and industry regulation to protect companies from hacking:
To protect companies and customers from fraud, the government has made various rules
regarding their safety. They have made several policies which not only provides easy access to
financial services but also protects them from fraud things, hackers and illegal activities (Arora,
Parashar and Transforming, 2013). The main purpose of government is to increase the economy
of the country and help people to increase their living standard and reduce their life risks.
IT governance: It mainly looks after the performance and risk associated with information
technology. According to Australian Standard for Corporate of Information Technology, the
organisation which operates illegal activities like cheating with customers and encourages them
to invest in illegal policies and plans are considered as criminal and they have no right to cheat
innocent people (Beimborn and Palitza, 2013). Further, this act has also focused on evaluation of
new technology and communication technology. The ICT projects have also introduced by the
organisation to increase their productivity and reduce the risks related to IT.
Different policies and patterns are introduced by the government to increase the
awareness of digital media and services which can help customers to reduce their efforts in
crediting, withdrawing and transferring their money. The online mobile apps and websites of
Aztek has helped them to reduce their time and money (Borrett, Carter and Wespi, 2014). The
fraud level and risk of cheating from agents has also reduced to greater extent. This has not only
helped them to increase their productivity and benefits. These policies of government have
helped the organisation to make more customers and win their confidence by providing different
plans related funds, insurance etc.
3
information etc. Further, this has also affected the performance and reputation of the company.
Further, this has also affected their soft running operation of the company which has adversely
affected their image in front of their customers. IT security policies and procedures are taken by
the finance company Aztek to reduce IT risks and challenges. It has employed various technical
staff which is expert in resolving technical issues and handling various challenges from hackers,
viruses and bugs. It has also hired experts which protects their company from serious and
dangerous threats of cloud computing and other technologies. The organisation has also taken
data security measures so that they can control the illegal activities of their employees in the
workplace. Thereafter, recommendation are given to improve the productivity of the company.
2. Government and industry regulation to protect companies from hacking:
To protect companies and customers from fraud, the government has made various rules
regarding their safety. They have made several policies which not only provides easy access to
financial services but also protects them from fraud things, hackers and illegal activities (Arora,
Parashar and Transforming, 2013). The main purpose of government is to increase the economy
of the country and help people to increase their living standard and reduce their life risks.
IT governance: It mainly looks after the performance and risk associated with information
technology. According to Australian Standard for Corporate of Information Technology, the
organisation which operates illegal activities like cheating with customers and encourages them
to invest in illegal policies and plans are considered as criminal and they have no right to cheat
innocent people (Beimborn and Palitza, 2013). Further, this act has also focused on evaluation of
new technology and communication technology. The ICT projects have also introduced by the
organisation to increase their productivity and reduce the risks related to IT.
Different policies and patterns are introduced by the government to increase the
awareness of digital media and services which can help customers to reduce their efforts in
crediting, withdrawing and transferring their money. The online mobile apps and websites of
Aztek has helped them to reduce their time and money (Borrett, Carter and Wespi, 2014). The
fraud level and risk of cheating from agents has also reduced to greater extent. This has not only
helped them to increase their productivity and benefits. These policies of government have
helped the organisation to make more customers and win their confidence by providing different
plans related funds, insurance etc.
3
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

AS 8015:
This standard has been launched by Standards Australia Committee IT-030 in 2005. The
main aim of this act is to describe effective corporate governance of information technology and
communication. This policy has helped Aztek to increase their IT infrastructure and services in
the workplace (Brewer, 2014). It has given access to the company to introduce various apps and
technologies and increase their productivity. This act has helped the top management of Aztek to
monitor and evaluate the performance of ICT in response to demands of the customers.
Aztek pattern for regulating IT services:
The organisation has allowed its employees to bring their personal devices in the
workplace and use them in completing their tasks. This has provided relax and easyness to them
to complete their tagets with more accuracy and desired results. Using their own devices has not
only helped the workers of Aztek but also organisation to increase their performance (Bromiley
and et.al., 2015). This has attracted various business stakeholders to invest their amount in larger
extent. The employees which uses their mobiles and laptops finds it easy to fulfil the needs of
their customers as they do not have to waste time in understanding and operating systems of their
company.
They can easily manage their work on their own devices and achieve desired results.
The stakeholders are always interested in company's overall performance and growth and
look after their position in the market (Cameron and Green, 2015). They also evaluate technical
facilities and staff of the organisation as they are interested in comfortableness and advancement
of the organisation operations. Business stakeholders and customers also determines the
effectiveness of their websites and online services as these technologies plays an important role
in saving their time and efforts. Online websites provides them the information about different
plans insurance and funding policies of their company (Chou, 2013). They will get to know all
the details and terms and conditions of all the plans without any help of external agents and they
can make payment and premiums of these policies online. This will save their time and provides
assurance that their money is invested at correct place.
Further, interface between business stakeholders and technologists helps the company to
resolve their technical difficulties into risk language which ultimately assist the organisation to
find out effective solutions (Coso, 2014). These helps them to resolve technical issue and
increase their productivity. Technologists use their own potential and skills to solve the
4
This standard has been launched by Standards Australia Committee IT-030 in 2005. The
main aim of this act is to describe effective corporate governance of information technology and
communication. This policy has helped Aztek to increase their IT infrastructure and services in
the workplace (Brewer, 2014). It has given access to the company to introduce various apps and
technologies and increase their productivity. This act has helped the top management of Aztek to
monitor and evaluate the performance of ICT in response to demands of the customers.
Aztek pattern for regulating IT services:
The organisation has allowed its employees to bring their personal devices in the
workplace and use them in completing their tasks. This has provided relax and easyness to them
to complete their tagets with more accuracy and desired results. Using their own devices has not
only helped the workers of Aztek but also organisation to increase their performance (Bromiley
and et.al., 2015). This has attracted various business stakeholders to invest their amount in larger
extent. The employees which uses their mobiles and laptops finds it easy to fulfil the needs of
their customers as they do not have to waste time in understanding and operating systems of their
company.
They can easily manage their work on their own devices and achieve desired results.
The stakeholders are always interested in company's overall performance and growth and
look after their position in the market (Cameron and Green, 2015). They also evaluate technical
facilities and staff of the organisation as they are interested in comfortableness and advancement
of the organisation operations. Business stakeholders and customers also determines the
effectiveness of their websites and online services as these technologies plays an important role
in saving their time and efforts. Online websites provides them the information about different
plans insurance and funding policies of their company (Chou, 2013). They will get to know all
the details and terms and conditions of all the plans without any help of external agents and they
can make payment and premiums of these policies online. This will save their time and provides
assurance that their money is invested at correct place.
Further, interface between business stakeholders and technologists helps the company to
resolve their technical difficulties into risk language which ultimately assist the organisation to
find out effective solutions (Coso, 2014). These helps them to resolve technical issue and
increase their productivity. Technologists use their own potential and skills to solve the
4

technical issue which requires some time. This will affect business stakeholders as they have to
face inconvenience. This has directly influenced soft running functionality of Aztek as they have
to face different problems from their customers and they lost them when technical problems do
not resolved rapidly (Crossler and et.al., 2014). Government policies also plays an important role
in affecting the functionality of the company. Their policies and rules distract the customers and
they confused while investing their money in finance sector companies.
Different policies related to information technology of the government sometimes fails or
poorly operate on the expectations of the customers (Godfrey, Merrill and Hansen, 2009). This
will affect their performance and they lose their hope from government and finance companies
like Aztek (IT Industry,Information Technology Industry, 2010). The mobile applications and
websites of governance bodies sometimes fails to provide the promised services. This is due to
inappropriate designing of websites or unskilled technical staff which look after these services
(Hashem and et.al., 2015). Further, the technologists do not work properly to handle these
websites and technical equipments which creates more inconvenience to the people. In these
situations, customers divert to finance companies for investing their money.
3. Security posture
Impact on current security
Allowing employees to bring their mobile phones and other devices in the organisation
distracts them from their work. They omit the important tasks and always finds ways to complete
them fast with no accuracy. These increase the threat of reduced productivity and lose of their
customers confidence and satisfaction (Hills, 2015). Further, devices like laptops, tablets and
mobile will always increase the threat of viruses and server losing of the company. These bugs
and viruses completely corrupt important information of the company. Due to these they lose
their important information related to customers details, their account information and their
investment details. These things adversely affect the performance of the company.
Further, allowing different technical devices in the premises of Aztek will indirectly
weaken the security system of the company (Hopkin, 2017). With the help of employees
personal devices, hackers get the path to stole important information of the organisation. They
easily hack the system of workers which are operating the important tasks and stole whole
information of the company through their system. They also put their system corrupted through
which the technical experts also cannot access the information of hackers and defaulters. The
5
face inconvenience. This has directly influenced soft running functionality of Aztek as they have
to face different problems from their customers and they lost them when technical problems do
not resolved rapidly (Crossler and et.al., 2014). Government policies also plays an important role
in affecting the functionality of the company. Their policies and rules distract the customers and
they confused while investing their money in finance sector companies.
Different policies related to information technology of the government sometimes fails or
poorly operate on the expectations of the customers (Godfrey, Merrill and Hansen, 2009). This
will affect their performance and they lose their hope from government and finance companies
like Aztek (IT Industry,Information Technology Industry, 2010). The mobile applications and
websites of governance bodies sometimes fails to provide the promised services. This is due to
inappropriate designing of websites or unskilled technical staff which look after these services
(Hashem and et.al., 2015). Further, the technologists do not work properly to handle these
websites and technical equipments which creates more inconvenience to the people. In these
situations, customers divert to finance companies for investing their money.
3. Security posture
Impact on current security
Allowing employees to bring their mobile phones and other devices in the organisation
distracts them from their work. They omit the important tasks and always finds ways to complete
them fast with no accuracy. These increase the threat of reduced productivity and lose of their
customers confidence and satisfaction (Hills, 2015). Further, devices like laptops, tablets and
mobile will always increase the threat of viruses and server losing of the company. These bugs
and viruses completely corrupt important information of the company. Due to these they lose
their important information related to customers details, their account information and their
investment details. These things adversely affect the performance of the company.
Further, allowing different technical devices in the premises of Aztek will indirectly
weaken the security system of the company (Hopkin, 2017). With the help of employees
personal devices, hackers get the path to stole important information of the organisation. They
easily hack the system of workers which are operating the important tasks and stole whole
information of the company through their system. They also put their system corrupted through
which the technical experts also cannot access the information of hackers and defaulters. The
5
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

organisation at that time feel helpless as whole working of the company comes to an end from
which recovery of data is not possible (Hoyt and Liebenberg, 2011).
Another greater risks of bringing personal devices is that it increases management effort
inventory and platform management. The devices which are used by employees have more
variability in hardware's and software's versions of the company devices (Kazim and Zhu, 2015).
Due to this, it is impossible for the organisation to put security policies on it and hence
employees will get access to social networking and other websites which are denied in the
workplace.
The employees generally mix the personal and business data on their device which
increases the threat of exposing of important data of the organisation. Another threat is that
malware and viruses installed automatically with the user's device when they surf various
websites while solving their tasks (Keyes, 2013). This will corrupt their devices and prone to
more threats. The problem will take bigger form when devices of the employees lost or stolen.
This increases the risk of hackers which stole the information easily from these devices and leak
the important finance related information of the company.
Recommendations:
It is recommended that Aztek has to allow its employees to bring only that device which
are compatible from their equipments. They have to allow their devices when they make settings
of their devices according to their rules and regulations. This will help them to make their
securities more strong and effective so that they can increase their productivity. Further, it is
recommended that Aztek has to follow various rules and regulations which help them to
understand the privacy policies and data security laws. The organisation has to regularly take
updates that their employees are using the devices which are able to meet the rules of the
organisation. Workers downloads mobile apps and connect their mobiles with external Wi-Fi
spots which leads to attacks on their system. These devices lack privacy issues and data
encryption techniques which develops security holes and are more vulnerable to hackers.
Therefore, Aztek has to make strict rules in which every employee which is using personal
device has to upload antivirus software in their system.
Mitigation actions:
Allowing personal devices of employees may benefit Aztek in various ways but it also
introduces various risks which may put the company in great business loss. Therefore, it is very
6
which recovery of data is not possible (Hoyt and Liebenberg, 2011).
Another greater risks of bringing personal devices is that it increases management effort
inventory and platform management. The devices which are used by employees have more
variability in hardware's and software's versions of the company devices (Kazim and Zhu, 2015).
Due to this, it is impossible for the organisation to put security policies on it and hence
employees will get access to social networking and other websites which are denied in the
workplace.
The employees generally mix the personal and business data on their device which
increases the threat of exposing of important data of the organisation. Another threat is that
malware and viruses installed automatically with the user's device when they surf various
websites while solving their tasks (Keyes, 2013). This will corrupt their devices and prone to
more threats. The problem will take bigger form when devices of the employees lost or stolen.
This increases the risk of hackers which stole the information easily from these devices and leak
the important finance related information of the company.
Recommendations:
It is recommended that Aztek has to allow its employees to bring only that device which
are compatible from their equipments. They have to allow their devices when they make settings
of their devices according to their rules and regulations. This will help them to make their
securities more strong and effective so that they can increase their productivity. Further, it is
recommended that Aztek has to follow various rules and regulations which help them to
understand the privacy policies and data security laws. The organisation has to regularly take
updates that their employees are using the devices which are able to meet the rules of the
organisation. Workers downloads mobile apps and connect their mobiles with external Wi-Fi
spots which leads to attacks on their system. These devices lack privacy issues and data
encryption techniques which develops security holes and are more vulnerable to hackers.
Therefore, Aztek has to make strict rules in which every employee which is using personal
device has to upload antivirus software in their system.
Mitigation actions:
Allowing personal devices of employees may benefit Aztek in various ways but it also
introduces various risks which may put the company in great business loss. Therefore, it is very
6
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

necessary for the organisation to take mitigation actions which helps them to protect their
business from dangerous attacks and security breaches (Lam, 2014). The company can
implement various policies and plans which helps their employees to keep their devices secure.
They have to regularly check the devices of workers as they are not misusing the resources and
freedom given by the company.
Reducing vulnerability:
To prevent the devices from viruses, it is very important to launch gatekeeper like VPN
which confirms that the data which is transferred to IT network of the company is not corrupted
and does not contain any bugs (Lemmon and Lins, 2013).
Preventing mixture of personal and business data:
Aztek has to make clear that all the employees have set passwords on their screens so that
no outsiders can login into it and access their information. Further, the organisation has to make
sure that they have set login id and password on their software on which every employee has to
login before starting their work on it (McNeil, Frey and Embrechts, 2015). These will help them
to reduce the risk of losing their data and tightening their security. The firm can also launch
enterprise mobility management software which help them to detect and control risks before they
take dangerous form.
Strong action against poorly cared devices:
The organisation has to implement remote wiping capabilities so that IT professionals can
wipe out all the unnecessary things from the device of employees. This will help them to destroy
all the irrelevant information related to the company so that they can increase the functionality of
the devices (McShane and Rustambekov, 2011). Additionally, it will give IT department to track
the location of devices which are stolen and recover all the important information of the
company from threat equipment.
Providing best IT infrastructure:
Aztek has to carry out full audit of whole IT environment to evaluate that infrastructure is
well set up and able to meet with workforce mobility. This will help in implementing effective
network layer in the workplace (Meyer and Reniers, 2016). Further, best IT infrastructure will
reduce the possibility of mistakes and errors. This will also develop effective environment as
comfortable operations will give relaxed feeling to the employees and they will work with more
7
business from dangerous attacks and security breaches (Lam, 2014). The company can
implement various policies and plans which helps their employees to keep their devices secure.
They have to regularly check the devices of workers as they are not misusing the resources and
freedom given by the company.
Reducing vulnerability:
To prevent the devices from viruses, it is very important to launch gatekeeper like VPN
which confirms that the data which is transferred to IT network of the company is not corrupted
and does not contain any bugs (Lemmon and Lins, 2013).
Preventing mixture of personal and business data:
Aztek has to make clear that all the employees have set passwords on their screens so that
no outsiders can login into it and access their information. Further, the organisation has to make
sure that they have set login id and password on their software on which every employee has to
login before starting their work on it (McNeil, Frey and Embrechts, 2015). These will help them
to reduce the risk of losing their data and tightening their security. The firm can also launch
enterprise mobility management software which help them to detect and control risks before they
take dangerous form.
Strong action against poorly cared devices:
The organisation has to implement remote wiping capabilities so that IT professionals can
wipe out all the unnecessary things from the device of employees. This will help them to destroy
all the irrelevant information related to the company so that they can increase the functionality of
the devices (McShane and Rustambekov, 2011). Additionally, it will give IT department to track
the location of devices which are stolen and recover all the important information of the
company from threat equipment.
Providing best IT infrastructure:
Aztek has to carry out full audit of whole IT environment to evaluate that infrastructure is
well set up and able to meet with workforce mobility. This will help in implementing effective
network layer in the workplace (Meyer and Reniers, 2016). Further, best IT infrastructure will
reduce the possibility of mistakes and errors. This will also develop effective environment as
comfortable operations will give relaxed feeling to the employees and they will work with more
7

efforts. This will help the organisation to achieve their desired results and convenience more
people to take their plans and policies.
4. Threats, vulnerabilities and consequences assessment
Aztek is operating in finance sector which looks after providing benefits to the customers
and making their IT system strong. Whole operations of the company from transaction to
providing any assistance to their customers for their policies is done through online and technical
equipments. So, there is great need for making IT system strong. They have employed skilled
technical staff to maintain their website, application and technical issues. Aztek has faced
various threats due to their technical facilities as they have to maintain large database of
customers and their organisation (Mikes and Kaplan, 2013). Further, the organisation is also
using cloud computing technology to maintain large database. Cloud computing allows the
company to access the resources on rent and pay for which it uses. It does not charge any extra
amount for the cost of leasing or renting their software and resources. It also allows placing large
database of the company on cloud (Creely, 2015). Threats and vulnerabilities which are evolved
from cloud computing and using other technical equipments are as follows:
8
people to take their plans and policies.
4. Threats, vulnerabilities and consequences assessment
Aztek is operating in finance sector which looks after providing benefits to the customers
and making their IT system strong. Whole operations of the company from transaction to
providing any assistance to their customers for their policies is done through online and technical
equipments. So, there is great need for making IT system strong. They have employed skilled
technical staff to maintain their website, application and technical issues. Aztek has faced
various threats due to their technical facilities as they have to maintain large database of
customers and their organisation (Mikes and Kaplan, 2013). Further, the organisation is also
using cloud computing technology to maintain large database. Cloud computing allows the
company to access the resources on rent and pay for which it uses. It does not charge any extra
amount for the cost of leasing or renting their software and resources. It also allows placing large
database of the company on cloud (Creely, 2015). Threats and vulnerabilities which are evolved
from cloud computing and using other technical equipments are as follows:
8
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
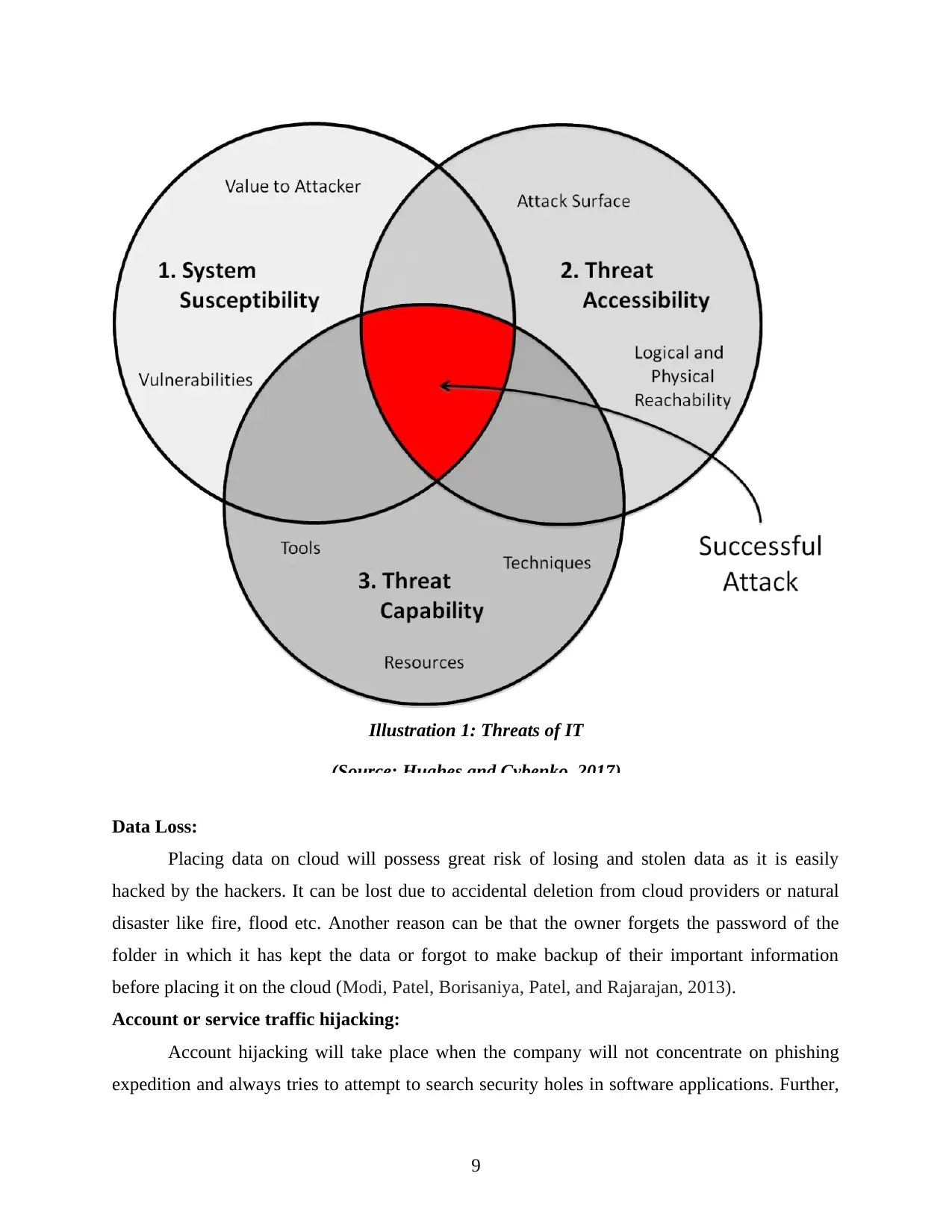
Data Loss:
Placing data on cloud will possess great risk of losing and stolen data as it is easily
hacked by the hackers. It can be lost due to accidental deletion from cloud providers or natural
disaster like fire, flood etc. Another reason can be that the owner forgets the password of the
folder in which it has kept the data or forgot to make backup of their important information
before placing it on the cloud (Modi, Patel, Borisaniya, Patel, and Rajarajan, 2013).
Account or service traffic hijacking:
Account hijacking will take place when the company will not concentrate on phishing
expedition and always tries to attempt to search security holes in software applications. Further,
9
Illustration 1: Threats of IT
(Source: Hughes and Cybenko, 2017)
Placing data on cloud will possess great risk of losing and stolen data as it is easily
hacked by the hackers. It can be lost due to accidental deletion from cloud providers or natural
disaster like fire, flood etc. Another reason can be that the owner forgets the password of the
folder in which it has kept the data or forgot to make backup of their important information
before placing it on the cloud (Modi, Patel, Borisaniya, Patel, and Rajarajan, 2013).
Account or service traffic hijacking:
Account hijacking will take place when the company will not concentrate on phishing
expedition and always tries to attempt to search security holes in software applications. Further,
9
Illustration 1: Threats of IT
(Source: Hughes and Cybenko, 2017)
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

buffer overflow attacks and passwords loss will lead to loss of control from user account and
information system (Morrow, 2012). Further, this will affect the organisation productivity and
performance because loss of user credit card, debit card and other information will increase their
problems as they cannot be able to access their information.
Insecure API's
The organisation places its data on the cloud and vulnerable to data lost. The insecure
API will give access to third party and helps them to access important information related to user
account details and company's confidential secret information. The third party do not make any
actions which creates doubts on them by the authority of the company (Payton and Claypoole,
2014). They secretly access all the information and use that information to cheat their customers
and hijack their accounts. This will adversely affect the firm as they lose confidence of their
policy holders and members as they feel that they are cheated by the company.
Shared technology vulnerability:
Another major threat of placing the data on cloud is that it exposes all the information as
cloud computing shares its platforms to several numbers of users. These increases the risk of
losing database of the firm.
Loss of business stakeholders:
Due to improper services and increase in frauds and cheating cases, the business
stakeholders have lost their trust from Aztek. They evaluate different technologies, reliability and
performance of their plans and polices before investing their amount. Due to system failure and
other technological issues, the organisation has failed to provide effective services to their
customers on time.
The organisation has implemented various software and systems to make their business
operations more strong and flexible (Romer, 2014). It has implemented various plans and
policies to improve the performance of their employees and provide best services to the people.
The firm has taken all necessary steps to improve their IT services and employed skilled IT
experts which help them to maintain their technical issues. It has also set all antivirus and
security software in its system so that there is no chance of data corruption. This has helped them
to make healthy environment among its employees by permitting them to bring their personal
devices (Bring your own device: Security and risk considerations for your mobile device
10
information system (Morrow, 2012). Further, this will affect the organisation productivity and
performance because loss of user credit card, debit card and other information will increase their
problems as they cannot be able to access their information.
Insecure API's
The organisation places its data on the cloud and vulnerable to data lost. The insecure
API will give access to third party and helps them to access important information related to user
account details and company's confidential secret information. The third party do not make any
actions which creates doubts on them by the authority of the company (Payton and Claypoole,
2014). They secretly access all the information and use that information to cheat their customers
and hijack their accounts. This will adversely affect the firm as they lose confidence of their
policy holders and members as they feel that they are cheated by the company.
Shared technology vulnerability:
Another major threat of placing the data on cloud is that it exposes all the information as
cloud computing shares its platforms to several numbers of users. These increases the risk of
losing database of the firm.
Loss of business stakeholders:
Due to improper services and increase in frauds and cheating cases, the business
stakeholders have lost their trust from Aztek. They evaluate different technologies, reliability and
performance of their plans and polices before investing their amount. Due to system failure and
other technological issues, the organisation has failed to provide effective services to their
customers on time.
The organisation has implemented various software and systems to make their business
operations more strong and flexible (Romer, 2014). It has implemented various plans and
policies to improve the performance of their employees and provide best services to the people.
The firm has taken all necessary steps to improve their IT services and employed skilled IT
experts which help them to maintain their technical issues. It has also set all antivirus and
security software in its system so that there is no chance of data corruption. This has helped them
to make healthy environment among its employees by permitting them to bring their personal
devices (Bring your own device: Security and risk considerations for your mobile device
10

program, 2013). Further, secure system and network layer has also helped them to make
effective image on the customers.
Consequences assessment:
Aztek has regulated its business operations by launching Ipv6 software in the mobile
system. They have also launched Ipv6 technology to increase the productivity of networking
system. Aztek has benefited lot from this technology as provides efficient routing and packet
processing which helps in making the networking layer strong and reduces the risks of data loss.
It supports multicast instead of broadcast which helps them to send multiple information at the
same time (Shostack, 2014). It also contains checksum and error control features which reduces
the risk of data corruption. Further, due to simplified network connection and directed data
flows, Ipv6 is proved to be very beneficial for the firm to increase its productivity. This has
helped the firm to operate successfully band provide the best online services to their customers
for easy payments, investments, transaction etc.
5 Data security
The organisation has implemented various plans and policies related to IT so that they
can safeguard their database and provide all the benefits to the customers. Azteck is finance
company and it is very essential for it to maintain the confidential information of the customers
and their accounts. This will help them to access all the details of that particular customer which
has to take benefits of its policies and plans (Singh anb et.al., 2017). Data security can be assured
when the organisation will carefully handle all the information and place it on the cloud. There
are several steps through which they can maintain their data safely;
Data backup:
The firm can place all its information on secure server by making its backup. This will
help them to recover their data back in the case of its loss or corruption. Data backup will help
when the it is lost due to natural disaster, deleted accidentally or hacked by third party. This will
help them to regulate their business operations and maintain their image in case of any failure.
Placing security software in the devices of all the employees:
Another method through which Aztek will secure its data from leakage and corruption is
by placing security software like antivirus and enterprise mobility management which prevents
viruses and other threats to enter in the system (Strauss, 2016). This will help IT department to
increase their productivity by detecting them at first stage.
11
effective image on the customers.
Consequences assessment:
Aztek has regulated its business operations by launching Ipv6 software in the mobile
system. They have also launched Ipv6 technology to increase the productivity of networking
system. Aztek has benefited lot from this technology as provides efficient routing and packet
processing which helps in making the networking layer strong and reduces the risks of data loss.
It supports multicast instead of broadcast which helps them to send multiple information at the
same time (Shostack, 2014). It also contains checksum and error control features which reduces
the risk of data corruption. Further, due to simplified network connection and directed data
flows, Ipv6 is proved to be very beneficial for the firm to increase its productivity. This has
helped the firm to operate successfully band provide the best online services to their customers
for easy payments, investments, transaction etc.
5 Data security
The organisation has implemented various plans and policies related to IT so that they
can safeguard their database and provide all the benefits to the customers. Azteck is finance
company and it is very essential for it to maintain the confidential information of the customers
and their accounts. This will help them to access all the details of that particular customer which
has to take benefits of its policies and plans (Singh anb et.al., 2017). Data security can be assured
when the organisation will carefully handle all the information and place it on the cloud. There
are several steps through which they can maintain their data safely;
Data backup:
The firm can place all its information on secure server by making its backup. This will
help them to recover their data back in the case of its loss or corruption. Data backup will help
when the it is lost due to natural disaster, deleted accidentally or hacked by third party. This will
help them to regulate their business operations and maintain their image in case of any failure.
Placing security software in the devices of all the employees:
Another method through which Aztek will secure its data from leakage and corruption is
by placing security software like antivirus and enterprise mobility management which prevents
viruses and other threats to enter in the system (Strauss, 2016). This will help IT department to
increase their productivity by detecting them at first stage.
11
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 16
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





