Secured Network Design Project for B2B Company: IT Infrastructure
VerifiedAdded on 2020/04/07
|9
|1792
|86
Project
AI Summary
This project details the design of a secure network for a B2B company, addressing existing IT infrastructure and potential security threats. The project scope includes the design of a network with six routers for different departments, including finance, transport, research, sales, IT, and head office. It emphasizes implementing multiple layers of security, such as VPNs, firewalls, and IPS systems, to ensure confidentiality, integrity, availability, and authentication (CIAA). The design incorporates specific IP addressing schemes, hardware requirements (routers, switches, cables, firewalls, and web servers), and software requirements (Windows servers, web servers). The project also discusses various security threats like ransomware, software vulnerabilities, and DoS attacks, and how to mitigate these risks through the implemented security measures. The conclusion summarizes the security implementations and the importance of antivirus servers and IPS systems in protecting the network. The project references several sources for network design, security threats, and hardware information.

Table of Contents
1. Introduction.......................................................................................................................................2
2. Network Design Project Scope..........................................................................................................2
3. Security Threats.................................................................................................................................2
4. Secure Network Design.....................................................................................................................3
5. Hardware requirements and devices................................................................................................6
6. CIAA...................................................................................................................................................8
7. Conclusion..........................................................................................................................................8
8. References..........................................................................................................................................9
1
1. Introduction.......................................................................................................................................2
2. Network Design Project Scope..........................................................................................................2
3. Security Threats.................................................................................................................................2
4. Secure Network Design.....................................................................................................................3
5. Hardware requirements and devices................................................................................................6
6. CIAA...................................................................................................................................................8
7. Conclusion..........................................................................................................................................8
8. References..........................................................................................................................................9
1
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

1. Introduction
The present IT infrastructure of B2B Company will be investigated. The exisiting threats of the
present network will be studied. The secured network design with necessary IP addressing , hard
ware and software requirements will be studied. The network devices that are needed to
implement the secured network design will be explained briefly. Network diagrams and IP
addressing designs will be made.
2. Network Design Project Scope
The network planning[1] by keeping security as one of the important parameters.B2B company
has six departments and the requirement is a router across each department and hence the
network is designed with 6 routers and these six router share 500 workstations. Finance
department has 100 workstations. Transport office has 50 workstations. Research office has 25
workstations. Sales office has 25 workstations. Information technology has 250 workstations.
The head office has 50 workstations. Security devices are provided in layers to implement the
safe handling of the network. As a network security architect, the criteria to be implemented are
taken into consideration. The network is designed in such a manner that it has proper flow of
information [2]. To implement the confidentiality, the network is protected or crypted with
passwords. Web based filtering is also implemented by using proper certified website through a
web filter and also by blocking the insecure sites. Role based access control is also implemented
in the network. RBAC is used to aid the users perform specific tasks according to the
departments. The network also has IPS, firewall and webservers[3].
3. Security Threats
A security threat[5] is nothing but a risk that can create harm or damage the network's working
environment. The threat mostly comes in the form of a software threat. There are many threats
that can affect the network. Some of the security threats are
Ransom ware
Software vulnerabilities
Hacktivism
Online hacking
Cloud attacks
2
The present IT infrastructure of B2B Company will be investigated. The exisiting threats of the
present network will be studied. The secured network design with necessary IP addressing , hard
ware and software requirements will be studied. The network devices that are needed to
implement the secured network design will be explained briefly. Network diagrams and IP
addressing designs will be made.
2. Network Design Project Scope
The network planning[1] by keeping security as one of the important parameters.B2B company
has six departments and the requirement is a router across each department and hence the
network is designed with 6 routers and these six router share 500 workstations. Finance
department has 100 workstations. Transport office has 50 workstations. Research office has 25
workstations. Sales office has 25 workstations. Information technology has 250 workstations.
The head office has 50 workstations. Security devices are provided in layers to implement the
safe handling of the network. As a network security architect, the criteria to be implemented are
taken into consideration. The network is designed in such a manner that it has proper flow of
information [2]. To implement the confidentiality, the network is protected or crypted with
passwords. Web based filtering is also implemented by using proper certified website through a
web filter and also by blocking the insecure sites. Role based access control is also implemented
in the network. RBAC is used to aid the users perform specific tasks according to the
departments. The network also has IPS, firewall and webservers[3].
3. Security Threats
A security threat[5] is nothing but a risk that can create harm or damage the network's working
environment. The threat mostly comes in the form of a software threat. There are many threats
that can affect the network. Some of the security threats are
Ransom ware
Software vulnerabilities
Hacktivism
Online hacking
Cloud attacks
2
The threats may also come in the form of virus, Trojans. DoS attack is nothing but the denial of
service attack that is used to create data traffic artificially and can make a server drown very
easily. The threats can also be categorized into physical and non-physical threats. The physical
threats are nothing but the threats that cause damage to the devices. The types of physical
threats are internal, external and humans. Nonphysical threat is the one that creates loss of data
or information. The nonphysical threats are also called the logical threats. The logical threats are
more dangerous.
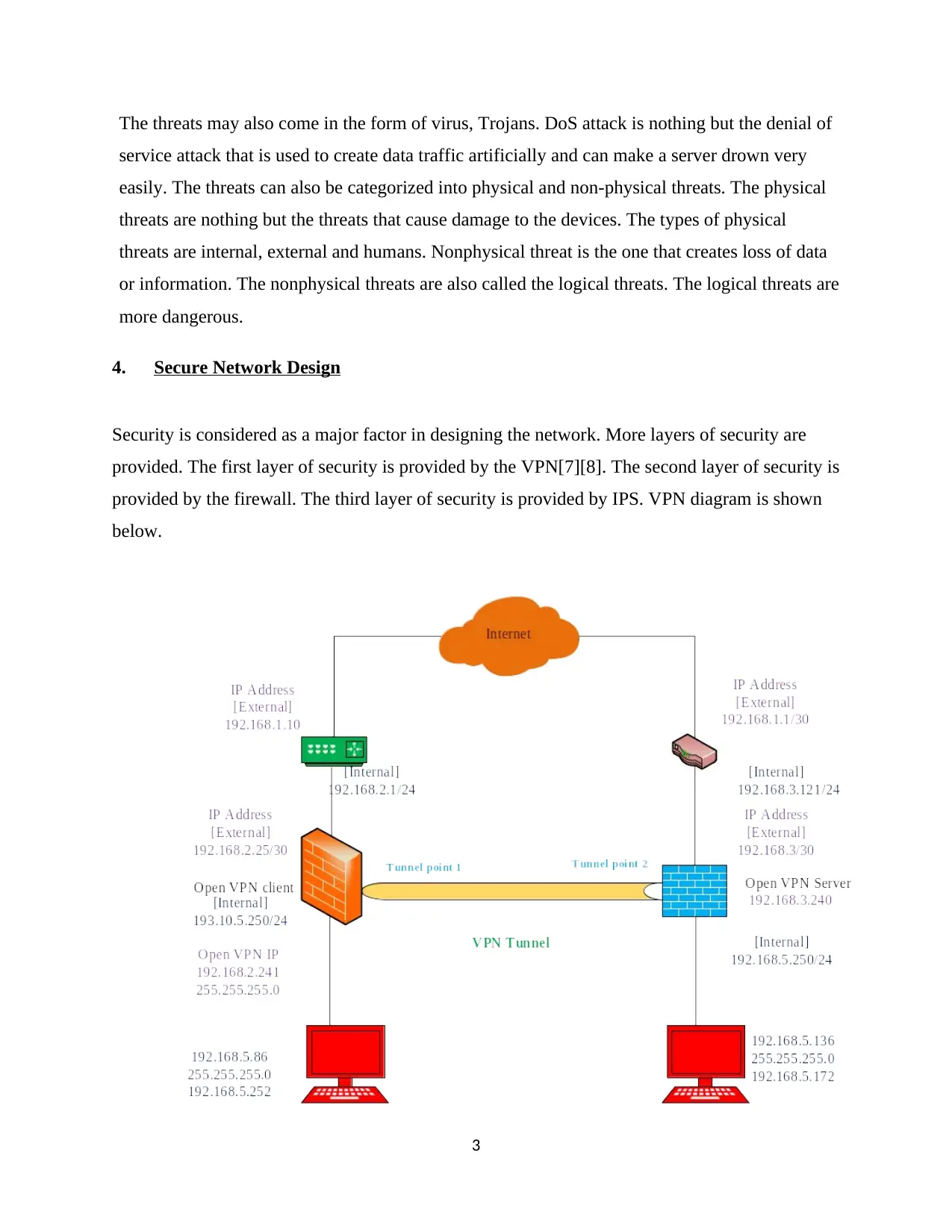
4. Secure Network Design
Security is considered as a major factor in designing the network. More layers of security are
provided. The first layer of security is provided by the VPN[7][8]. The second layer of security is
provided by the firewall. The third layer of security is provided by IPS. VPN diagram is shown
below.
3
service attack that is used to create data traffic artificially and can make a server drown very
easily. The threats can also be categorized into physical and non-physical threats. The physical
threats are nothing but the threats that cause damage to the devices. The types of physical
threats are internal, external and humans. Nonphysical threat is the one that creates loss of data
or information. The nonphysical threats are also called the logical threats. The logical threats are
more dangerous.
4. Secure Network Design
Security is considered as a major factor in designing the network. More layers of security are
provided. The first layer of security is provided by the VPN[7][8]. The second layer of security is
provided by the firewall. The third layer of security is provided by IPS. VPN diagram is shown
below.
3
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
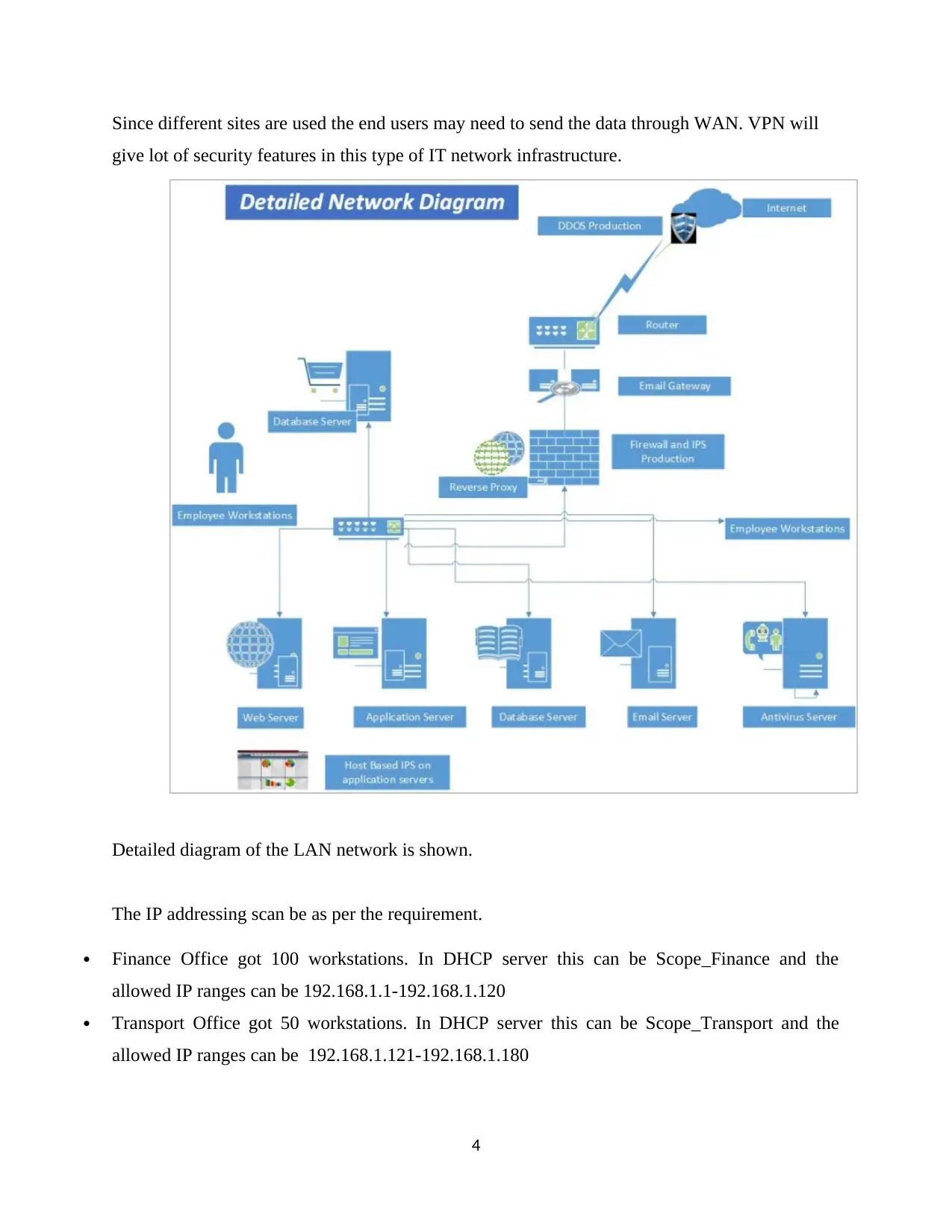
Since different sites are used the end users may need to send the data through WAN. VPN will
give lot of security features in this type of IT network infrastructure.
Detailed diagram of the LAN network is shown.
The IP addressing scan be as per the requirement.
Finance Office got 100 workstations. In DHCP server this can be Scope_Finance and the
allowed IP ranges can be 192.168.1.1-192.168.1.120
Transport Office got 50 workstations. In DHCP server this can be Scope_Transport and the
allowed IP ranges can be 192.168.1.121-192.168.1.180
4
give lot of security features in this type of IT network infrastructure.
Detailed diagram of the LAN network is shown.
The IP addressing scan be as per the requirement.
Finance Office got 100 workstations. In DHCP server this can be Scope_Finance and the
allowed IP ranges can be 192.168.1.1-192.168.1.120
Transport Office got 50 workstations. In DHCP server this can be Scope_Transport and the
allowed IP ranges can be 192.168.1.121-192.168.1.180
4
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Research Office got 25 workstations. In DHCP server this can be Scope_Research and the
allowed IP ranges can be 192.168.1.181-192.168.1.210
Sales Office got 25 workstations. In DHCP server this can be Scope_Sales and the allowed IP
ranges can be 192.168.2.1 - 192.168.2.40
Information technology got 250 workstations. In DHCP server this can be Scope_IT and the
allowed IP ranges can be 192.168.3.1-192.168.1.254
Head Office got 50 workstations. In DHCP server this can be Scope_Headoffice and the allowed
IP ranges can be 192.168.4.1-192.168.4.60
The security blocks used in the network include
Firewall
Antivirus server
IPS system
Three layers of security are implemented in the network diagram. First layer of security is
implemented by the firewall. Second layer of security is implemented by the anti-virus servers.
The third level of security is implemented by the IPS system. Firewall is installed between the
router and the server. In order to provide the security to the servers, antivirus server is also
implemented. PS is the abbreviation of Intrusion Prevention System. It protects against the
threats by examining the network traffic.
5. Hardware requirements and devices
Required hardware [6] to implement the secured network is explained below.
Routers
A router is a one that establishes connection between two or more wired or wireless devices that
frames a structured network. Router has memory and operates like a embedded device. Router is
also responsible for handling incoming and outgoing packets. Packets are basic unit of the
network. There are many types of router like Brouter, Core router, Edge router, Virtual router,
Wireless router.
5
allowed IP ranges can be 192.168.1.181-192.168.1.210
Sales Office got 25 workstations. In DHCP server this can be Scope_Sales and the allowed IP
ranges can be 192.168.2.1 - 192.168.2.40
Information technology got 250 workstations. In DHCP server this can be Scope_IT and the
allowed IP ranges can be 192.168.3.1-192.168.1.254
Head Office got 50 workstations. In DHCP server this can be Scope_Headoffice and the allowed
IP ranges can be 192.168.4.1-192.168.4.60
The security blocks used in the network include
Firewall
Antivirus server
IPS system
Three layers of security are implemented in the network diagram. First layer of security is
implemented by the firewall. Second layer of security is implemented by the anti-virus servers.
The third level of security is implemented by the IPS system. Firewall is installed between the
router and the server. In order to provide the security to the servers, antivirus server is also
implemented. PS is the abbreviation of Intrusion Prevention System. It protects against the
threats by examining the network traffic.
5. Hardware requirements and devices
Required hardware [6] to implement the secured network is explained below.
Routers
A router is a one that establishes connection between two or more wired or wireless devices that
frames a structured network. Router has memory and operates like a embedded device. Router is
also responsible for handling incoming and outgoing packets. Packets are basic unit of the
network. There are many types of router like Brouter, Core router, Edge router, Virtual router,
Wireless router.
5

Manufacturer’s Name-- Cisco
Series Series-- Integrated Services Routers
Model-- 4000
Switch
Switches are used to connect devices. Router also serves the same functionality but the
difference is that routers are used to connect the network and the witches are used to create the
network. There are two main types of switches. They are manageable switches and non-
manageable switches. Switches are considered as valuable assets for a network. Switch have
many ports. According to the port, the switch can be 2 port switch, 4 port switch or the multiple
port switch. Switch allows the flow of the network in a structured manner.
Manufacturer’s Name Cisco
Series Catalyst Switch
Model 6880-X
Cables
Network cables are used to connect one device to the other device physically.There are many
types of cables used in network.They are
Twisted pair
Fiber optic
Coaxial
Patch
Power lines
Twisted pair cable is one which has pairs of wires in twisted form.Fibre optic cable is one which
has glass core in the center that is surrounded by many protective materials.The protective layer
is nothing but the layer of insulating jacket. Patch cable is one which is mostly used for
connecting electrical devices
6
Series Series-- Integrated Services Routers
Model-- 4000
Switch
Switches are used to connect devices. Router also serves the same functionality but the
difference is that routers are used to connect the network and the witches are used to create the
network. There are two main types of switches. They are manageable switches and non-
manageable switches. Switches are considered as valuable assets for a network. Switch have
many ports. According to the port, the switch can be 2 port switch, 4 port switch or the multiple
port switch. Switch allows the flow of the network in a structured manner.
Manufacturer’s Name Cisco
Series Catalyst Switch
Model 6880-X
Cables
Network cables are used to connect one device to the other device physically.There are many
types of cables used in network.They are
Twisted pair
Fiber optic
Coaxial
Patch
Power lines
Twisted pair cable is one which has pairs of wires in twisted form.Fibre optic cable is one which
has glass core in the center that is surrounded by many protective materials.The protective layer
is nothing but the layer of insulating jacket. Patch cable is one which is mostly used for
connecting electrical devices
6
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

Manufacturer’s Name Hitech Products Private Limited (falcon Cables)
Series Networking cable
Model CAT-5
Firewall
Like a wall which gives security to the buildings, firewall also refers to the system which
provides security to the networks. Firewall blocks the authorized access. Firewall can be a
software application or a hard ware device.
Web Server
A webserver is one that aids one to browse or handle webpages. The webserver works with the
help of HHTP.HTTP is a type of protocol. They share the viewing and editing control of
webpages upon request
Software Requirements
Windows servers need Windows 2012 R2 Operating system[10]. Web server can be
implemented in Apache/IIS. Routers and switche3s will be having inbuilt OS.
6. CIAA
CIAA stands for confidentiality, integrity, availability and authentication[8]. In the present
network VPN is configured. So the data confidentiality is ensured. Integrity can be checked by
using many techniques like parities. Availability can be implements for keeping the data in
multiple palces. Authentication can be achieved by using active directory in this design
7. Conclusion
The security implementation to the various blocks used in the network diagram is clearly
explained. The misconfiguration of webserver by an attacker is prevented by using the antivirus
server. The antivirus server protects the application server from vulnerable software. Suppose a
malicious document gets opened by an employee, it can be considered as a threat. The threat can
7
Series Networking cable
Model CAT-5
Firewall
Like a wall which gives security to the buildings, firewall also refers to the system which
provides security to the networks. Firewall blocks the authorized access. Firewall can be a
software application or a hard ware device.
Web Server
A webserver is one that aids one to browse or handle webpages. The webserver works with the
help of HHTP.HTTP is a type of protocol. They share the viewing and editing control of
webpages upon request
Software Requirements
Windows servers need Windows 2012 R2 Operating system[10]. Web server can be
implemented in Apache/IIS. Routers and switche3s will be having inbuilt OS.
6. CIAA
CIAA stands for confidentiality, integrity, availability and authentication[8]. In the present
network VPN is configured. So the data confidentiality is ensured. Integrity can be checked by
using many techniques like parities. Availability can be implements for keeping the data in
multiple palces. Authentication can be achieved by using active directory in this design
7. Conclusion
The security implementation to the various blocks used in the network diagram is clearly
explained. The misconfiguration of webserver by an attacker is prevented by using the antivirus
server. The antivirus server protects the application server from vulnerable software. Suppose a
malicious document gets opened by an employee, it can be considered as a threat. The threat can
7
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

be avoided by taking care of the network traffic using the IPS system. DNS server is also kept
away from the cache poisoning using the IPS system.
8. References
[1]"Network design checklist: How to design a LAN", SearchITChannel, 2017. [Online].
Available: http://searchitchannel.techtarget.com/feature/Network-design-checklist-Six-
factors-to-consider-when-designing-LANs. [Accessed: 29- Sep- 2017].
[2]I. Cisco Systems, "Introduction to Cisco Network Design > Designing Campus
Networks",Ciscopress.com, 2017. [Online]. Available:
http://www.ciscopress.com/articles/article.asp?p=25259. [Accessed: 29- Sep- 2017].
[3]"Campus Network Design Models", Network Computing, 2017. [Online]. Available:
http://www.networkcomputing.com/data-centers/campus-network-design-models/
1685370612. [Accessed: 29- Sep- 2017].
[4]P. Oppenheimer, Top-down network design. Indianapolis, Ind.: Cisco Press, 2011.
[5]"Security Threats", Msdn.microsoft.com, 2017. [Online]. Available:
https://msdn.microsoft.com/en-us/library/cc723507.aspx. [Accessed: 29- Sep- 2017].
[6]"Network Devices", 2017. [Online]. Available:
http://www.certiology.com/computing/computer-networking/network-devices.html.
[Accessed: 29- Sep- 2017].
[7]"How VPN Works: Virtual Private Network (VPN)", Technet.microsoft.com, 2017. [Online].
Available: https://technet.microsoft.com/en-us/library/cc779919(v=ws.10).aspx. [Accessed:
29- Sep- 2017].
[8]"Information Security Concepts +1: Confidentiality, Integrity, Availablity, and
Authenticity", Bright Hub, 2017. [Online]. Available:
http://www.brighthub.com/computing/smb-security/articles/29153.aspx. [Accessed: 29-
Sep- 2017].
[9]V. Ltd., "Network solutions, network monitoring, network filrewall systems, network security
- VirtueWorld - Website Design and Development", Virtueworld.com, 2017. [Online].
Available:
8
away from the cache poisoning using the IPS system.
8. References
[1]"Network design checklist: How to design a LAN", SearchITChannel, 2017. [Online].
Available: http://searchitchannel.techtarget.com/feature/Network-design-checklist-Six-
factors-to-consider-when-designing-LANs. [Accessed: 29- Sep- 2017].
[2]I. Cisco Systems, "Introduction to Cisco Network Design > Designing Campus
Networks",Ciscopress.com, 2017. [Online]. Available:
http://www.ciscopress.com/articles/article.asp?p=25259. [Accessed: 29- Sep- 2017].
[3]"Campus Network Design Models", Network Computing, 2017. [Online]. Available:
http://www.networkcomputing.com/data-centers/campus-network-design-models/
1685370612. [Accessed: 29- Sep- 2017].
[4]P. Oppenheimer, Top-down network design. Indianapolis, Ind.: Cisco Press, 2011.
[5]"Security Threats", Msdn.microsoft.com, 2017. [Online]. Available:
https://msdn.microsoft.com/en-us/library/cc723507.aspx. [Accessed: 29- Sep- 2017].
[6]"Network Devices", 2017. [Online]. Available:
http://www.certiology.com/computing/computer-networking/network-devices.html.
[Accessed: 29- Sep- 2017].
[7]"How VPN Works: Virtual Private Network (VPN)", Technet.microsoft.com, 2017. [Online].
Available: https://technet.microsoft.com/en-us/library/cc779919(v=ws.10).aspx. [Accessed:
29- Sep- 2017].
[8]"Information Security Concepts +1: Confidentiality, Integrity, Availablity, and
Authenticity", Bright Hub, 2017. [Online]. Available:
http://www.brighthub.com/computing/smb-security/articles/29153.aspx. [Accessed: 29-
Sep- 2017].
[9]V. Ltd., "Network solutions, network monitoring, network filrewall systems, network security
- VirtueWorld - Website Design and Development", Virtueworld.com, 2017. [Online].
Available:
8

http://www.virtueworld.com/network_solutions/designing_and_implementation_of_vpn_net
works.html. [Accessed: 29- Sep- 2017].
[10]"Windows Networking Design Implementation Guide", Cisco, 2017. [Online]. Available:
https://www.cisco.com/c/en/us/support/docs/additional-legacy-protocols/ms-windows-
networking/10624-winnt-dg.html. [Accessed: 29- Sep- 2017].
9
works.html. [Accessed: 29- Sep- 2017].
[10]"Windows Networking Design Implementation Guide", Cisco, 2017. [Online]. Available:
https://www.cisco.com/c/en/us/support/docs/additional-legacy-protocols/ms-windows-
networking/10624-winnt-dg.html. [Accessed: 29- Sep- 2017].
9
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 9
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





