Project: Secure Network Design for B2B Solutions' Infrastructure
VerifiedAdded on 2020/04/01
|9
|1938
|35
Project
AI Summary
This project provides a secure network design for a medium-sized B2B organization with six buildings and 500 workstations. It addresses network security threats, including passive and active attacks, and proposes a network design using Cisco products to reduce costs and enhance productivity. The design incorporates routers, switches, access points, firewalls, and core switches. The project emphasizes confidentiality, integrity, availability, and authorization (CIAA) using cryptographic algorithms. The report details hardware and software requirements, justifies the CIAA principles, and concludes with a secure network infrastructure that ensures secure communication, network availability, and usability. The design includes firewalls to block unauthorized access and protect sensitive information. References are provided to support the design and analysis.

NETWORK AND SECURITY
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Table of Contents
1. Project Scope.................................................................................................................................2
2. Security Threats.............................................................................................................................2
3. Network Hardware and Software Requirements...........................................................................3
3.1 Software Requirement...........................................................................................................3
3.2 Hardware Requirement.........................................................................................................4
3.3 Requirement Specification.....................................................................................................4
4. Network Design.............................................................................................................................5
5. Justification for CIAA......................................................................................................................6
6. Conclusion.....................................................................................................................................7
References.............................................................................................................................................7
1
1. Project Scope.................................................................................................................................2
2. Security Threats.............................................................................................................................2
3. Network Hardware and Software Requirements...........................................................................3
3.1 Software Requirement...........................................................................................................3
3.2 Hardware Requirement.........................................................................................................4
3.3 Requirement Specification.....................................................................................................4
4. Network Design.............................................................................................................................5
5. Justification for CIAA......................................................................................................................6
6. Conclusion.....................................................................................................................................7
References.............................................................................................................................................7
1

1. Project Scope
Main scope of this project is to create the secure network design for B2B solutions. The B2B
solutions is medium sized organization. It interests to create the secure network design. The B2B
solutions has the six building such as finance office, Information technology office, research office,
sales office, transport office and head office. Each office contains the workstations. The Finance
offices has the 50 work stations, sales office has the 25 work stations, transport office has the 50
workstations, head office has 50 work stations and information technology office has the 250
workstations. These buildings are connected with the routers and each building has the single
subnet. The proposed network design for B2B solutions is provides the productivity and security of
the network. It uses the cisco products to reduce the maintenance and operational costs. The
Network security threats will be analysed. The network design hardware and software components
are will be addressed. The proposed network design will be ensuring the confidentiality, integrity,
availability and Authorization of the network.
2. Security Threats
The Network security threats are classified into two types such as passive threats and active threats.
The Network security threats diagram is shown in below [1].
2
Main scope of this project is to create the secure network design for B2B solutions. The B2B
solutions is medium sized organization. It interests to create the secure network design. The B2B
solutions has the six building such as finance office, Information technology office, research office,
sales office, transport office and head office. Each office contains the workstations. The Finance
offices has the 50 work stations, sales office has the 25 work stations, transport office has the 50
workstations, head office has 50 work stations and information technology office has the 250
workstations. These buildings are connected with the routers and each building has the single
subnet. The proposed network design for B2B solutions is provides the productivity and security of
the network. It uses the cisco products to reduce the maintenance and operational costs. The
Network security threats will be analysed. The network design hardware and software components
are will be addressed. The proposed network design will be ensuring the confidentiality, integrity,
availability and Authorization of the network.
2. Security Threats
The Network security threats are classified into two types such as passive threats and active threats.
The Network security threats diagram is shown in below [1].
2
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
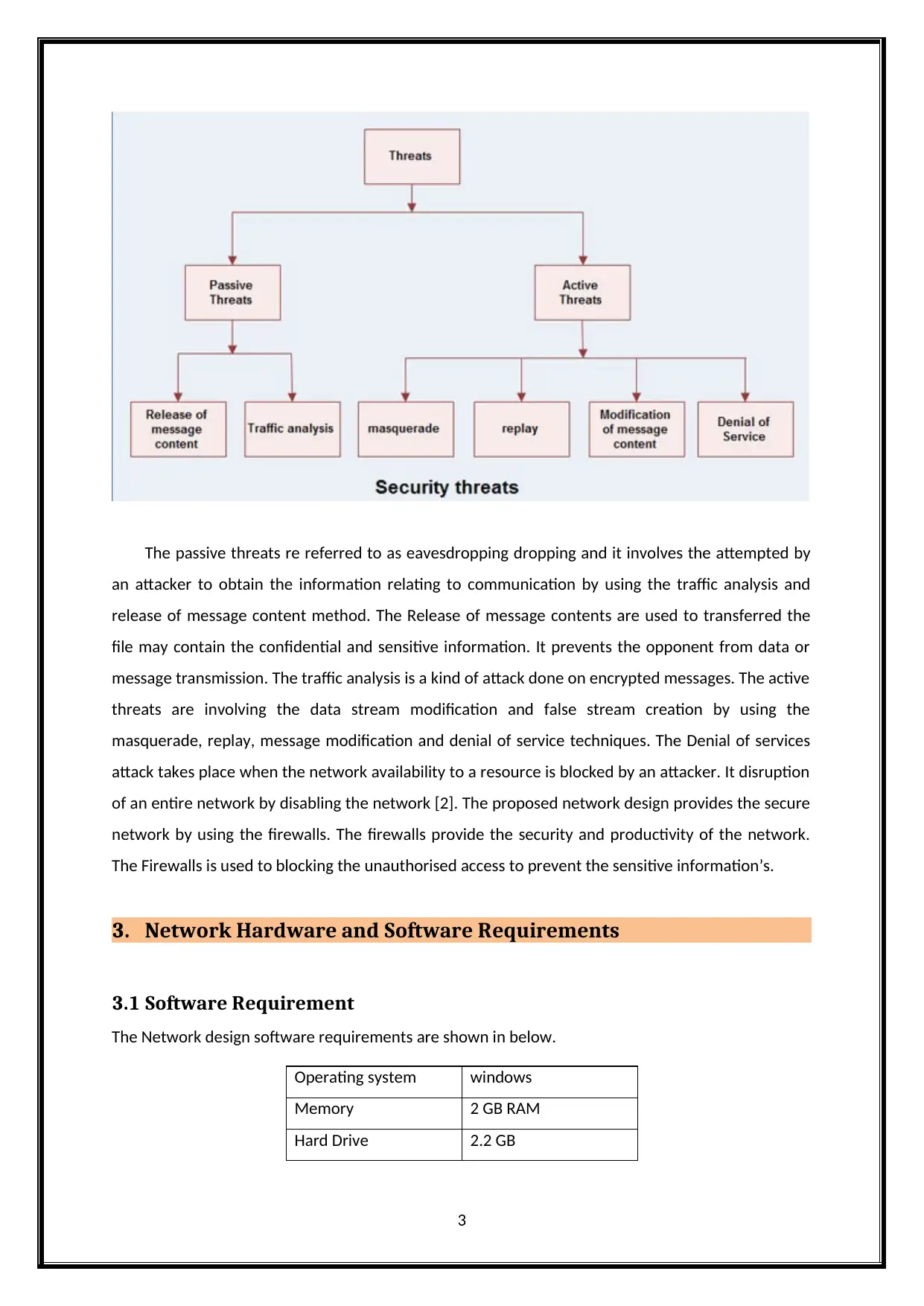
The passive threats re referred to as eavesdropping dropping and it involves the attempted by
an attacker to obtain the information relating to communication by using the traffic analysis and
release of message content method. The Release of message contents are used to transferred the
file may contain the confidential and sensitive information. It prevents the opponent from data or
message transmission. The traffic analysis is a kind of attack done on encrypted messages. The active
threats are involving the data stream modification and false stream creation by using the
masquerade, replay, message modification and denial of service techniques. The Denial of services
attack takes place when the network availability to a resource is blocked by an attacker. It disruption
of an entire network by disabling the network [2]. The proposed network design provides the secure
network by using the firewalls. The firewalls provide the security and productivity of the network.
The Firewalls is used to blocking the unauthorised access to prevent the sensitive information’s.
3. Network Hardware and Software Requirements
3.1 Software Requirement
The Network design software requirements are shown in below.
Operating system windows
Memory 2 GB RAM
Hard Drive 2.2 GB
3
an attacker to obtain the information relating to communication by using the traffic analysis and
release of message content method. The Release of message contents are used to transferred the
file may contain the confidential and sensitive information. It prevents the opponent from data or
message transmission. The traffic analysis is a kind of attack done on encrypted messages. The active
threats are involving the data stream modification and false stream creation by using the
masquerade, replay, message modification and denial of service techniques. The Denial of services
attack takes place when the network availability to a resource is blocked by an attacker. It disruption
of an entire network by disabling the network [2]. The proposed network design provides the secure
network by using the firewalls. The firewalls provide the security and productivity of the network.
The Firewalls is used to blocking the unauthorised access to prevent the sensitive information’s.
3. Network Hardware and Software Requirements
3.1 Software Requirement
The Network design software requirements are shown in below.
Operating system windows
Memory 2 GB RAM
Hard Drive 2.2 GB
3
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
3.2 Hardware Requirement
The Hardware requirements are shown in below [3].
Cisco Routers Cisco 800 Series Routers
Cisco Switches Cisco Small Business 500 Series Switch
Cisco Access Point Cisco 300 Series Access Points
Cisco Firewall Cisco ASA 5506-X with Fire POWER Services
Cisco Core switch Cisco Nexus 7000 Series Switches
3.3 Requirement Specification
Specification of network devices is shown in below.
Cisco Routers – cisco 800 Series routers
It uses maximum power consumption is 11w to 18 w.
It does not have the extended shock-vibe
It has operating temperature and altitude is 0 to 40-degree Celsius.
It has maximum 85% of humidity [4].
Cisco Switches - Cisco Small Business 500 Series Switch
It supports he standard 802.1d spanning tree protocol.
In VLAN, it supports the 4096 Vlan simultaneously port based.
In Voice VLAN, the voice traffics are automatically assigned to a voice specific VLAN.
IT blocking Head of Line
It supports the classless Inter domain routing
Cisco Access Point - Cisco 300 Series Access Points
It enhanced the mobile guest experience.
It provides the strong security [5].
Easy to set up the peer-peer video conferencing for collaboration
It easily enables the next generation connected digital classrooms.
It minimizing the total cost of ownership for the network.
Cisco Firewall - Cisco ASA 5506-X with Fire POWER Services
It provides the ASA firewall functionality, advanced breach detection and advanced threat
protection.
Highly secure and reliable access
High performance
It uses advanced malware protection like blocking, detection, analysis, remediation and
tracking to protect the enterprises [6].
4
The Hardware requirements are shown in below [3].
Cisco Routers Cisco 800 Series Routers
Cisco Switches Cisco Small Business 500 Series Switch
Cisco Access Point Cisco 300 Series Access Points
Cisco Firewall Cisco ASA 5506-X with Fire POWER Services
Cisco Core switch Cisco Nexus 7000 Series Switches
3.3 Requirement Specification
Specification of network devices is shown in below.
Cisco Routers – cisco 800 Series routers
It uses maximum power consumption is 11w to 18 w.
It does not have the extended shock-vibe
It has operating temperature and altitude is 0 to 40-degree Celsius.
It has maximum 85% of humidity [4].
Cisco Switches - Cisco Small Business 500 Series Switch
It supports he standard 802.1d spanning tree protocol.
In VLAN, it supports the 4096 Vlan simultaneously port based.
In Voice VLAN, the voice traffics are automatically assigned to a voice specific VLAN.
IT blocking Head of Line
It supports the classless Inter domain routing
Cisco Access Point - Cisco 300 Series Access Points
It enhanced the mobile guest experience.
It provides the strong security [5].
Easy to set up the peer-peer video conferencing for collaboration
It easily enables the next generation connected digital classrooms.
It minimizing the total cost of ownership for the network.
Cisco Firewall - Cisco ASA 5506-X with Fire POWER Services
It provides the ASA firewall functionality, advanced breach detection and advanced threat
protection.
Highly secure and reliable access
High performance
It uses advanced malware protection like blocking, detection, analysis, remediation and
tracking to protect the enterprises [6].
4
It reduces operation costs.
It provides the administrative visibility.
Cisco Core Switch - Cisco Nexus 7000 Series Switches
It combines the high levels of scalability with operational flexibility.
It provides the integrated resilience combined with features.
It also provides the reliability and availability of the network.
High Performance.
It helps to ensure the system reliability [7].
4. Network Design
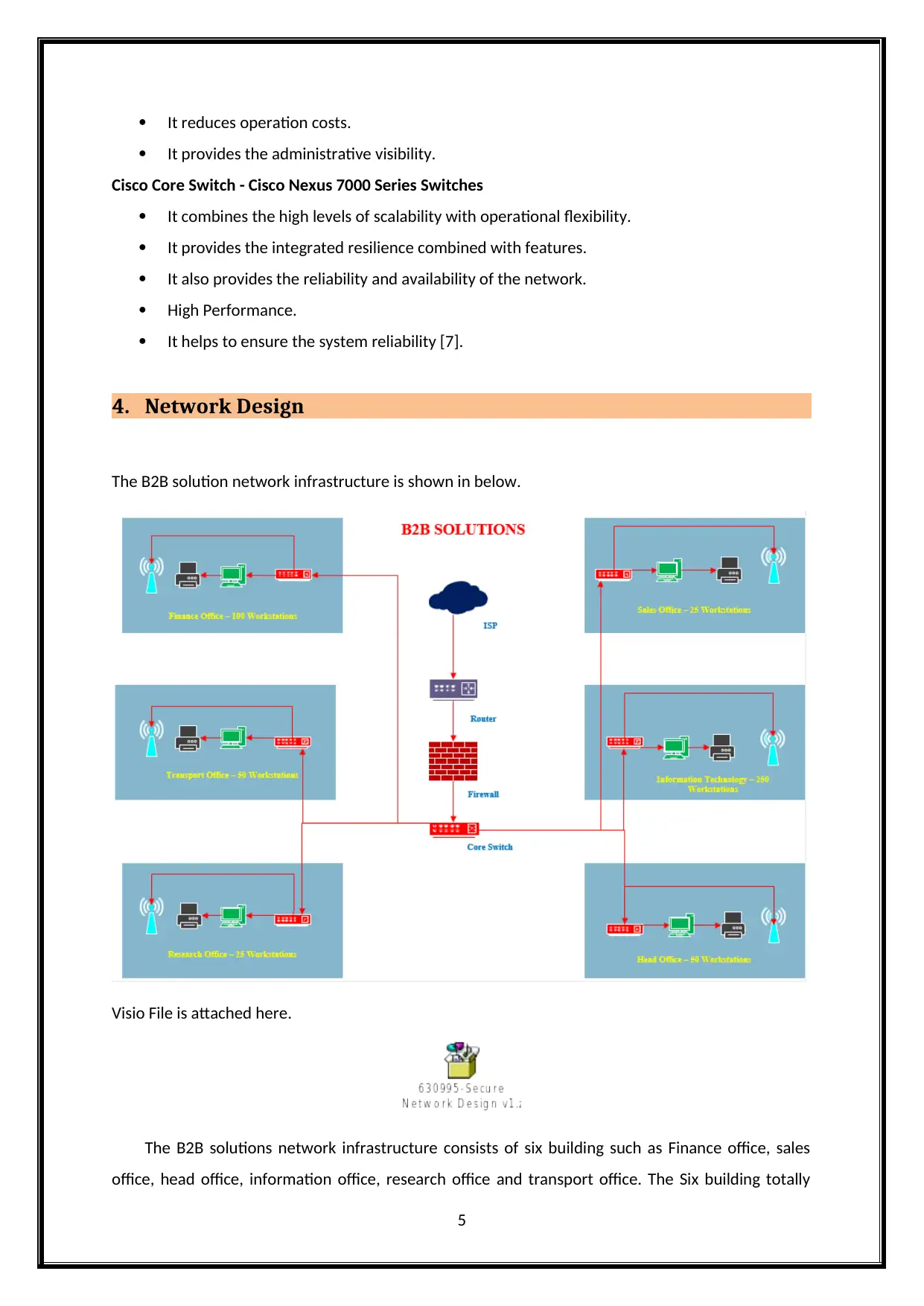
The B2B solution network infrastructure is shown in below.
Visio File is attached here.
The B2B solutions network infrastructure consists of six building such as Finance office, sales
office, head office, information office, research office and transport office. The Six building totally
5
It provides the administrative visibility.
Cisco Core Switch - Cisco Nexus 7000 Series Switches
It combines the high levels of scalability with operational flexibility.
It provides the integrated resilience combined with features.
It also provides the reliability and availability of the network.
High Performance.
It helps to ensure the system reliability [7].
4. Network Design
The B2B solution network infrastructure is shown in below.
Visio File is attached here.
The B2B solutions network infrastructure consists of six building such as Finance office, sales
office, head office, information office, research office and transport office. The Six building totally
5
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

contains the 500 work stations. These are connected with the routers. The router connecting the
core switch to connect the six building through cisco switches. The cisco products are providing the
secure and scalability of the network for B2B solutions. The Proposed network design is used to
provide the secure communication between the employees and organization team. It maintains
network availability and usability [8]. The Proposed network design has the flexibility and availability
of the network to delivers the secure network for entire organizations. The secure network design is
decrease the operational and maintenance costs. Because the proposed network design does not
require the maintenance costs to maintain the network. The cisco products are reduced the
operational costs. The six building are securely communicated with each other’s [9].
5. Justification for CIAA
The network design ensures the confidentiality, integrity, availability and authorization by using
the cryptographic algorithms. the cryptography plays a major role in network security. The network
security goals are based on confidentiality, integrity, availability and authorization. these are
designed to act as guide for information security policies [10].
Confidentiality
The confidentiality is protecting the information from the disclosure to unauthorised users. The
confidentially protecting the information by encrypting the information. the encryption ensures the
only the right peoples can be read the information. It provides the security for the sensitive
information [11].
Integrity
The integrity is used to protecting the information from being modified by unauthorized users.
the cryptography plays a major role in ensuring the data integrity. The to protect the integrity by
using the various methods includes hashing the data and comparing the hash messages.
Availability
The availability is used to protect and ensures the information that authorised users are able to
access the information when needed. It does not allow the unauthorised users accessing the
information. It denying the access to information has become a very common attack. To ensure the
data availability by backup the information’s. It provides the security and productivity. It reduces the
down time [12].
Authorization
6
core switch to connect the six building through cisco switches. The cisco products are providing the
secure and scalability of the network for B2B solutions. The Proposed network design is used to
provide the secure communication between the employees and organization team. It maintains
network availability and usability [8]. The Proposed network design has the flexibility and availability
of the network to delivers the secure network for entire organizations. The secure network design is
decrease the operational and maintenance costs. Because the proposed network design does not
require the maintenance costs to maintain the network. The cisco products are reduced the
operational costs. The six building are securely communicated with each other’s [9].
5. Justification for CIAA
The network design ensures the confidentiality, integrity, availability and authorization by using
the cryptographic algorithms. the cryptography plays a major role in network security. The network
security goals are based on confidentiality, integrity, availability and authorization. these are
designed to act as guide for information security policies [10].
Confidentiality
The confidentiality is protecting the information from the disclosure to unauthorised users. The
confidentially protecting the information by encrypting the information. the encryption ensures the
only the right peoples can be read the information. It provides the security for the sensitive
information [11].
Integrity
The integrity is used to protecting the information from being modified by unauthorized users.
the cryptography plays a major role in ensuring the data integrity. The to protect the integrity by
using the various methods includes hashing the data and comparing the hash messages.
Availability
The availability is used to protect and ensures the information that authorised users are able to
access the information when needed. It does not allow the unauthorised users accessing the
information. It denying the access to information has become a very common attack. To ensure the
data availability by backup the information’s. It provides the security and productivity. It reduces the
down time [12].
Authorization
6
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

The authorization is used to allow an authorised users only accessing the information. The
cryptography algorithms also provide the authorization of the users. It first authenticates the users,
after provides the accessing permission. The Cryptography authorization is used to provide the
security from attackers.
6. Conclusion
B2B solutions current network does not have the security. The B2B organization team
interested to create the secure network design. The network design has the six building such as
finance office, transport office, research office, sales office, head office and information technology
office. Overall B2B network infrastructure has the 500 workstations. These building are connected
with the routers. The router connecting each building by using the core switch. The six buildings are
communicated with each other. The proposed network design provides the secure network design
by using firewalls. The firewall is used to provides the productivity and security for the network. It
blocking the unauthorised users. The network security threats are identified and discussed. The
hardware and software requirements are identified and discussed in detail. The Justification of
confidentiality, availability, integrity and authorization is done by using the cryptographic algorithms.
References
[1]J. Kurose and K. Ross, Computer networking. .
[2]NETworking. [Hong Kong]: Regional NET Coordinating Team, NET Section, CDI, EDB, 2013.
[3]J. Wang, Broadband wireless communications. [Place of publication not identified]: Springer-
Verlag New York, 2013.
[4]P. Services, C. Switches and D. Sheets, "Cisco 500 Series Stackable Managed Switches Data
Sheet", Cisco, 2017. [Online]. Available:
https://www.cisco.com/c/en/us/products/collateral/switches/small-business-500-series-
stackable-managed-switches/c78-695646_data_sheet.html. [Accessed: 27- Sep- 2017].
[5]P. Services, B. Routers, C. Routers and D. Sheets, "Cisco 2900 Series Integrated Services Routers
Data Sheet", Cisco, 2017. [Online]. Available:
7
cryptography algorithms also provide the authorization of the users. It first authenticates the users,
after provides the accessing permission. The Cryptography authorization is used to provide the
security from attackers.
6. Conclusion
B2B solutions current network does not have the security. The B2B organization team
interested to create the secure network design. The network design has the six building such as
finance office, transport office, research office, sales office, head office and information technology
office. Overall B2B network infrastructure has the 500 workstations. These building are connected
with the routers. The router connecting each building by using the core switch. The six buildings are
communicated with each other. The proposed network design provides the secure network design
by using firewalls. The firewall is used to provides the productivity and security for the network. It
blocking the unauthorised users. The network security threats are identified and discussed. The
hardware and software requirements are identified and discussed in detail. The Justification of
confidentiality, availability, integrity and authorization is done by using the cryptographic algorithms.
References
[1]J. Kurose and K. Ross, Computer networking. .
[2]NETworking. [Hong Kong]: Regional NET Coordinating Team, NET Section, CDI, EDB, 2013.
[3]J. Wang, Broadband wireless communications. [Place of publication not identified]: Springer-
Verlag New York, 2013.
[4]P. Services, C. Switches and D. Sheets, "Cisco 500 Series Stackable Managed Switches Data
Sheet", Cisco, 2017. [Online]. Available:
https://www.cisco.com/c/en/us/products/collateral/switches/small-business-500-series-
stackable-managed-switches/c78-695646_data_sheet.html. [Accessed: 27- Sep- 2017].
[5]P. Services, B. Routers, C. Routers and D. Sheets, "Cisco 2900 Series Integrated Services Routers
Data Sheet", Cisco, 2017. [Online]. Available:
7

https://www.cisco.com/c/en/us/products/collateral/routers/2900-series-integrated-services-
routers-isr/data_sheet_c78_553896.html. [Accessed: 27- Sep- 2017].
[6]P. Services, C. Access, C. Series and D. Sheets, "Cisco Edge 300 Series Data Sheet", Cisco, 2017.
[Online]. Available: https://www.cisco.com/c/en/us/products/collateral/switches/edge-300-
series/data_sheet_c78-694183.html. [Accessed: 27- Sep- 2017].
[7]P. Services, C. Services and D. Sheets, "Cisco ASA with FirePOWER Services Data Sheet", Cisco,
2017. [Online]. Available: https://www.cisco.com/c/en/us/products/collateral/security/asa-
5500-series-next-generation-firewalls/datasheet-c78-733916.html. [Accessed: 27- Sep- 2017].
[8]P. Support, C. Switches and I. Guides, "Cisco Nexus 7000 Series Site Preparation Guide - Technical
Specifications [Cisco Nexus 7000 Series Switches]", Cisco, 2017. [Online]. Available:
https://www.cisco.com/c/en/us/td/docs/switches/datacenter/hw/nexus7000/site_prep/
guide/nexus7k_siteprep_book/siteprep_tech_specs.html. [Accessed: 27- Sep- 2017].
[9]"Network Security – What is Network Security Threats?", Ecomputernotes.com, 2017. [Online].
Available: http://ecomputernotes.com/computernetworkingnotes/security/network-security-
threats. [Accessed: 27- Sep- 2017].
[10]"Firewalls and Internet Security - The Internet Protocol Journal - Volume 2, No. 2", Cisco, 2017.
[Online]. Available: https://www.cisco.com/c/en/us/about/press/internet-protocol-journal/
back-issues/table-contents-1/ipj-archive/article09186a00800c85ae.html. [Accessed: 27- Sep-
2017].
[11]"Goals of Security Confidentiality, Integrity, and Availability", ExamCollection, 2017. [Online].
Available: https://www.examcollection.com/certification-training/security-plus-goals-of-
security-confidentiality-integrity-availability.html. [Accessed: 27- Sep- 2017].
[12]T. Chia, "Confidentiality, Integrity, Availability: The three components of the CIA Triad « Stack
Exchange Security Blog", Security.blogoverflow.com, 2017. [Online]. Available:
http://security.blogoverflow.com/2012/08/confidentiality-integrity-availability-the-three-
components-of-the-cia-triad/. [Accessed: 27- Sep- 2017].
8
routers-isr/data_sheet_c78_553896.html. [Accessed: 27- Sep- 2017].
[6]P. Services, C. Access, C. Series and D. Sheets, "Cisco Edge 300 Series Data Sheet", Cisco, 2017.
[Online]. Available: https://www.cisco.com/c/en/us/products/collateral/switches/edge-300-
series/data_sheet_c78-694183.html. [Accessed: 27- Sep- 2017].
[7]P. Services, C. Services and D. Sheets, "Cisco ASA with FirePOWER Services Data Sheet", Cisco,
2017. [Online]. Available: https://www.cisco.com/c/en/us/products/collateral/security/asa-
5500-series-next-generation-firewalls/datasheet-c78-733916.html. [Accessed: 27- Sep- 2017].
[8]P. Support, C. Switches and I. Guides, "Cisco Nexus 7000 Series Site Preparation Guide - Technical
Specifications [Cisco Nexus 7000 Series Switches]", Cisco, 2017. [Online]. Available:
https://www.cisco.com/c/en/us/td/docs/switches/datacenter/hw/nexus7000/site_prep/
guide/nexus7k_siteprep_book/siteprep_tech_specs.html. [Accessed: 27- Sep- 2017].
[9]"Network Security – What is Network Security Threats?", Ecomputernotes.com, 2017. [Online].
Available: http://ecomputernotes.com/computernetworkingnotes/security/network-security-
threats. [Accessed: 27- Sep- 2017].
[10]"Firewalls and Internet Security - The Internet Protocol Journal - Volume 2, No. 2", Cisco, 2017.
[Online]. Available: https://www.cisco.com/c/en/us/about/press/internet-protocol-journal/
back-issues/table-contents-1/ipj-archive/article09186a00800c85ae.html. [Accessed: 27- Sep-
2017].
[11]"Goals of Security Confidentiality, Integrity, and Availability", ExamCollection, 2017. [Online].
Available: https://www.examcollection.com/certification-training/security-plus-goals-of-
security-confidentiality-integrity-availability.html. [Accessed: 27- Sep- 2017].
[12]T. Chia, "Confidentiality, Integrity, Availability: The three components of the CIA Triad « Stack
Exchange Security Blog", Security.blogoverflow.com, 2017. [Online]. Available:
http://security.blogoverflow.com/2012/08/confidentiality-integrity-availability-the-three-
components-of-the-cia-triad/. [Accessed: 27- Sep- 2017].
8
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 9
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





