Report on Designing a Secure Internet-Based Bank Network Architecture
VerifiedAdded on 2022/09/23
|22
|4168
|22
Report
AI Summary
This report presents a comprehensive security architectural design for a new, internet-based bank operating in a cloud environment, as mandated by new federal legislation. The design incorporates a three-tier LAN architecture, including core, distribution, and access layers, and addresses critical security concerns such as compliance with federal and state legislation, ensuring confidentiality, availability, and integrity of customer data, and customer privacy. The report details the technologies applied, including cloud storage, security management, intrusion detection systems, and firewalls. It outlines a multi-tiered network security architecture with web, application, and database server zones, along with security frameworks, policies, and protection measures for mobile banking, including encryption, authentication, and digital signatures. The report also covers cost estimates, equipment lists, and recommendations for implementing the network, emphasizing the importance of a holistic approach to information security and the need for continuous updates to address emerging threats and vulnerabilities.
NETWORKING
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Contents
Introduction.................................................................................................................................................2
Architectural design.....................................................................................................................................3
Technologies applied in the Network......................................................................................................5
Network Security Architecture....................................................................................................................6
The security architecture......................................................................................................................7
The protection measures for Mobile banking......................................................................................9
The physical level and detailed design......................................................................................................12
Cost estimates of implementing the network.............................................................................................14
Security services to be implemented in the network..................................................................................16
Equipment list...........................................................................................................................................17
Conclusion/Recommendation...............................................................................................................18
Introduction.................................................................................................................................................2
Architectural design.....................................................................................................................................3
Technologies applied in the Network......................................................................................................5
Network Security Architecture....................................................................................................................6
The security architecture......................................................................................................................7
The protection measures for Mobile banking......................................................................................9
The physical level and detailed design......................................................................................................12
Cost estimates of implementing the network.............................................................................................14
Security services to be implemented in the network..................................................................................16
Equipment list...........................................................................................................................................17
Conclusion/Recommendation...............................................................................................................18

Introduction
Due to the increase in population around the country many banks have been open to help the
population receive, send and save money. In today's world with the increase in the growth of
technology many customers prefer using internet banking. Security and privacy of information
are some of the major concerns of an internet banking system. Without the security of
information in the internet-based bank, a lot of information may leak into the public and once
this falls into the wrong hands it may be used by hackers steaking money from the bank of even
acquiring important information from the bank. There have many cases whereby some individual
loses money from their bank accounts without notice. This happens when their credit information
or password gets into the wrong hands. In some, cases intruder uses other people credit
information to purchase equipment from retailer websites like amazons. This happens due to the
lack of security with the banking details. That’s why it is advisable for everyone to keep the
banking details private and not to share with anybody. Several problems arise from mobile
banking is that some information might be sent to the customer as plaintext this compromises the
security of the information. In a security approach way, banks hide information in the
cryptography algorithm and send it to the customers. The customer handset or computer, on the
other hand, will decrypt information using the algorithm so that it can be read. In the current
society due to the increased fraudulent activities, bank systems should be designed with strong
security to prevent attacks from happening.
The main aim of this report is to design an internet-based architectural system for a new bank
that has been granted a new license by the federal government under the new rules of “no More
Squireelling”. The new bank has decided to carry all of its activities through the cloud. The
following are some of the security concerns that should be considered while designing the
system. The system should comply with the current legislation of the government. It should
protect the customer's information and assure the public that the information that they share with
the bank is confidential, available when requested and its integrity. More so the system should
allow customers to engage with the customers through the internet and security of all the bank
assets.
Due to the increase in population around the country many banks have been open to help the
population receive, send and save money. In today's world with the increase in the growth of
technology many customers prefer using internet banking. Security and privacy of information
are some of the major concerns of an internet banking system. Without the security of
information in the internet-based bank, a lot of information may leak into the public and once
this falls into the wrong hands it may be used by hackers steaking money from the bank of even
acquiring important information from the bank. There have many cases whereby some individual
loses money from their bank accounts without notice. This happens when their credit information
or password gets into the wrong hands. In some, cases intruder uses other people credit
information to purchase equipment from retailer websites like amazons. This happens due to the
lack of security with the banking details. That’s why it is advisable for everyone to keep the
banking details private and not to share with anybody. Several problems arise from mobile
banking is that some information might be sent to the customer as plaintext this compromises the
security of the information. In a security approach way, banks hide information in the
cryptography algorithm and send it to the customers. The customer handset or computer, on the
other hand, will decrypt information using the algorithm so that it can be read. In the current
society due to the increased fraudulent activities, bank systems should be designed with strong
security to prevent attacks from happening.
The main aim of this report is to design an internet-based architectural system for a new bank
that has been granted a new license by the federal government under the new rules of “no More
Squireelling”. The new bank has decided to carry all of its activities through the cloud. The
following are some of the security concerns that should be considered while designing the
system. The system should comply with the current legislation of the government. It should
protect the customer's information and assure the public that the information that they share with
the bank is confidential, available when requested and its integrity. More so the system should
allow customers to engage with the customers through the internet and security of all the bank
assets.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
Architectural design
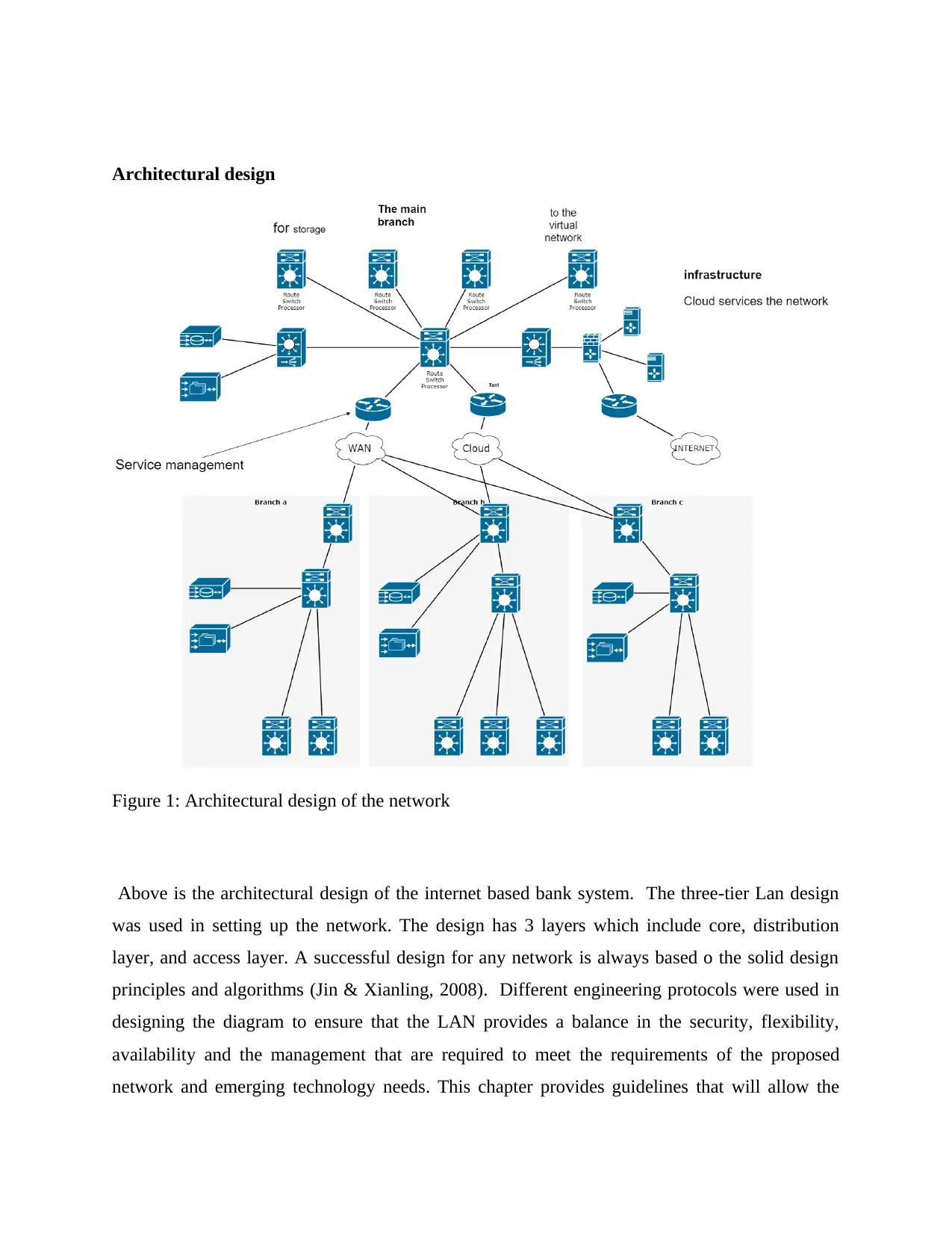
Figure 1: Architectural design of the network
Above is the architectural design of the internet based bank system. The three-tier Lan design
was used in setting up the network. The design has 3 layers which include core, distribution
layer, and access layer. A successful design for any network is always based o the solid design
principles and algorithms (Jin & Xianling, 2008). Different engineering protocols were used in
designing the diagram to ensure that the LAN provides a balance in the security, flexibility,
availability and the management that are required to meet the requirements of the proposed
network and emerging technology needs. This chapter provides guidelines that will allow the
Figure 1: Architectural design of the network
Above is the architectural design of the internet based bank system. The three-tier Lan design
was used in setting up the network. The design has 3 layers which include core, distribution
layer, and access layer. A successful design for any network is always based o the solid design
principles and algorithms (Jin & Xianling, 2008). Different engineering protocols were used in
designing the diagram to ensure that the LAN provides a balance in the security, flexibility,
availability and the management that are required to meet the requirements of the proposed
network and emerging technology needs. This chapter provides guidelines that will allow the
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

bank to build an internet-based application that is secure and free from attacks. The following are
some of the principals that are used in designing the network.
The design that was implemented in the network was hierarchical due to the following reason.
Hierarchical designed enable an understanding of the roles of each device in the network.
It will simplify the management and deployment of the network.
It will also reduce the fault domains at each tier of the network.
Modularity allows it to grow easily when required.
The resiliency in the structure will satisfy user expectations.
Flexibility the architecture will allow intelligence traffic loading by using all the available
resources in the network.
The core, distribution and access layer are not independent principles (ohnson, Acedo, Kobourov
& Nusrat,2015). They work together to achieve the objectives of the system. The principles of
each layer of the network should be clearly understood to design a network that fits the
requirement of the bank. Designing the network using the above model allows the network
architects to overlay security and the mobility of the network as well as providing an
interconnect point for WAN aspects.
some of the principals that are used in designing the network.
The design that was implemented in the network was hierarchical due to the following reason.
Hierarchical designed enable an understanding of the roles of each device in the network.
It will simplify the management and deployment of the network.
It will also reduce the fault domains at each tier of the network.
Modularity allows it to grow easily when required.
The resiliency in the structure will satisfy user expectations.
Flexibility the architecture will allow intelligence traffic loading by using all the available
resources in the network.
The core, distribution and access layer are not independent principles (ohnson, Acedo, Kobourov
& Nusrat,2015). They work together to achieve the objectives of the system. The principles of
each layer of the network should be clearly understood to design a network that fits the
requirement of the bank. Designing the network using the above model allows the network
architects to overlay security and the mobility of the network as well as providing an
interconnect point for WAN aspects.

Technologies applied in the Network
The requirements of the network to meet different technologies will be applied. This technology
will have different functionality in the bank system. The technologies included in the design
include cloud storage, security management, intrusion detection systems, infrastructure security.
UCS port-security scanning.
The architecture has a checkpoint firewall with a better processing capability that protects the
network from attacks. This can also enable the activation of other features that can help in
securing the network. The firewall is specifically designed for network security and has pure
controls to secure the organization's systems against web server, database and application server
attacks. The organization should look into the acquisition of a database and web server firewall.
A database firewall and web application firewall are necessary to secure the complete
information infrastructure of the bank.
Cloud computing is also applied to the network as a backup plan it will be used in storing
information on the cloud servers .The cloud servers in the architecture include Infrastructure,
software as a service and platform as services.
The requirements of the network to meet different technologies will be applied. This technology
will have different functionality in the bank system. The technologies included in the design
include cloud storage, security management, intrusion detection systems, infrastructure security.
UCS port-security scanning.
The architecture has a checkpoint firewall with a better processing capability that protects the
network from attacks. This can also enable the activation of other features that can help in
securing the network. The firewall is specifically designed for network security and has pure
controls to secure the organization's systems against web server, database and application server
attacks. The organization should look into the acquisition of a database and web server firewall.
A database firewall and web application firewall are necessary to secure the complete
information infrastructure of the bank.
Cloud computing is also applied to the network as a backup plan it will be used in storing
information on the cloud servers .The cloud servers in the architecture include Infrastructure,
software as a service and platform as services.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

Network Security Architecture
Network security architectures have been developed for protection against hackers, malicious
code and other attacks that may cause failure or lack of confidentiality, integrity, and availability.
The network architecture described in this section is a multi-tiered network security architecture
that consists of a web, application, and database server zones. The web server is used by
customers who wish to carry out transactions, application servers are used for data processing of
customers or client requests and the database server is essential for data storage.
Routers, firewalls, data encryption using Virtual Private Networks (VPN), Intrusion Prevention
and load balancing for server acceleration provide network services that are needed in the bank
system. This is the first group of the information infrastructure that needs to be protected. The
second group is the core network services or internal network service which includes servers and
applications and databases together with the intranet.
Network security architectures have been developed for protection against hackers, malicious
code and other attacks that may cause failure or lack of confidentiality, integrity, and availability.
The network architecture described in this section is a multi-tiered network security architecture
that consists of a web, application, and database server zones. The web server is used by
customers who wish to carry out transactions, application servers are used for data processing of
customers or client requests and the database server is essential for data storage.
Routers, firewalls, data encryption using Virtual Private Networks (VPN), Intrusion Prevention
and load balancing for server acceleration provide network services that are needed in the bank
system. This is the first group of the information infrastructure that needs to be protected. The
second group is the core network services or internal network service which includes servers and
applications and databases together with the intranet.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
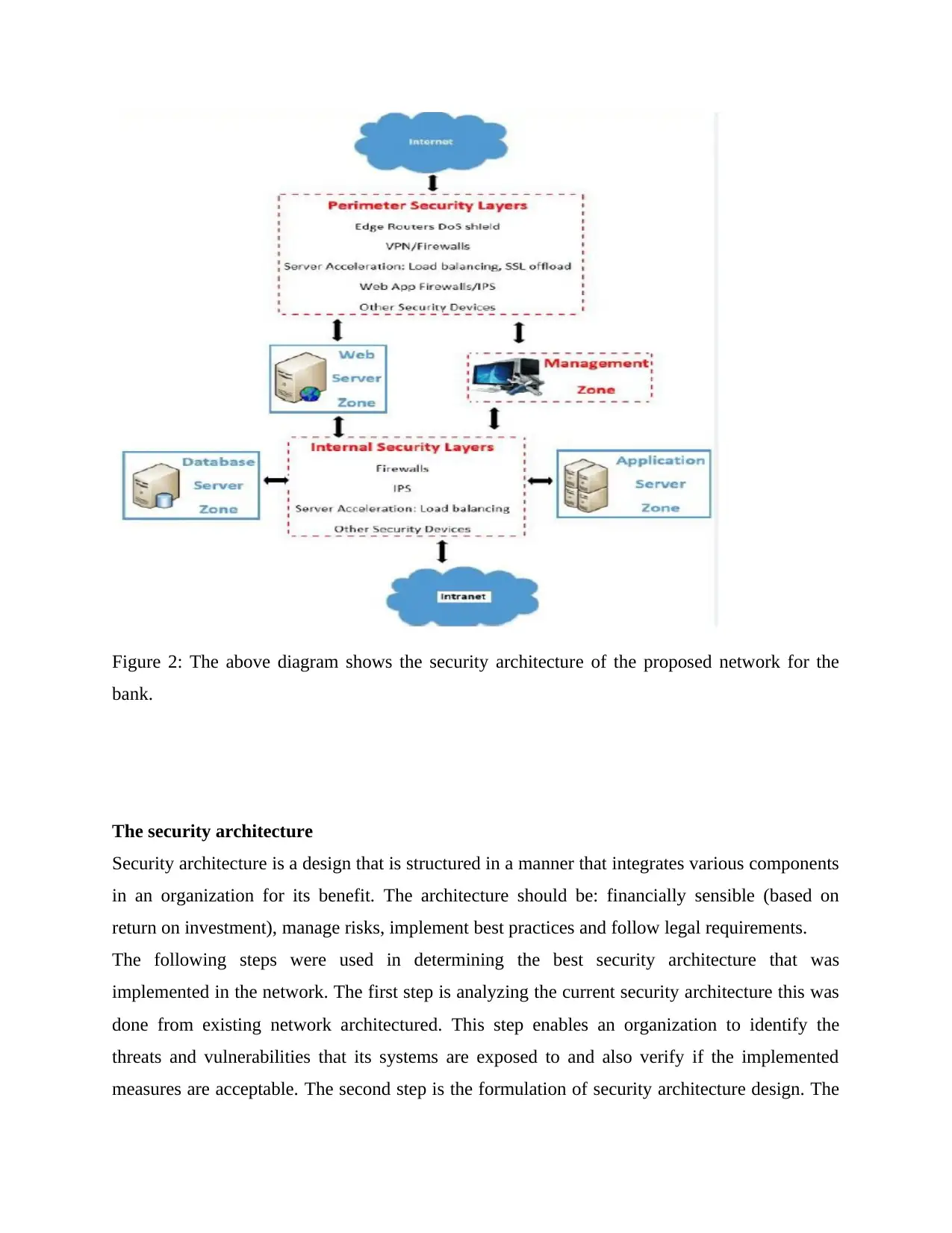
Figure 2: The above diagram shows the security architecture of the proposed network for the
bank.
The security architecture
Security architecture is a design that is structured in a manner that integrates various components
in an organization for its benefit. The architecture should be: financially sensible (based on
return on investment), manage risks, implement best practices and follow legal requirements.
The following steps were used in determining the best security architecture that was
implemented in the network. The first step is analyzing the current security architecture this was
done from existing network architectured. This step enables an organization to identify the
threats and vulnerabilities that its systems are exposed to and also verify if the implemented
measures are acceptable. The second step is the formulation of security architecture design. The
bank.
The security architecture
Security architecture is a design that is structured in a manner that integrates various components
in an organization for its benefit. The architecture should be: financially sensible (based on
return on investment), manage risks, implement best practices and follow legal requirements.
The following steps were used in determining the best security architecture that was
implemented in the network. The first step is analyzing the current security architecture this was
done from existing network architectured. This step enables an organization to identify the
threats and vulnerabilities that its systems are exposed to and also verify if the implemented
measures are acceptable. The second step is the formulation of security architecture design. The

design developed in this step entirely depends on the finding of the first phase. There are two
types of security architecture designs involved. The first is logical architecture; which involves
the processes, technology, and people involved. Understanding the flow of information is also
important in developing logical architecture. The second security architecture design is the
physical design which involves coming up with a diagram that illustrates the various firewalls,
network components, and connections that are related in architecture such as in figure 2.
designing a security architecture is coming up with policies and procedures which are meant to
define what is to be protected based on the organization’s needs. The fourth step is the
implementation of the architecture design. The fifth step after implementation is the integration
of security practices to deliver security.
The important part, however, knows the basic requirements of a security architecture.
(Kazanavicius, Kazanaviciu, &.Venckauskas, 2012) States that a security system should ensure
or enforce confidentiality, integrity availability and accountability.
For us to be able to develop an architecture that will help with information infrastructure
protection in banks, there is a need to know the guidelines or regulations that have been put in
place. These regulations are referred to as frameworks. An IT security framework is a chain of
processes used to outline the policies and procedures for protecting the information
infrastructure. A security framework is a guide for securing information (Kazanavicius,
Kazanavicius, & A.Venckauskas.).
According to Benson Yeung (2012) in the article ‘The Security Framework for Information
Technology’, there are two major causes of vulnerabilities in information security. The first is
mistakes by users and IT engineers whom most of the time are not trained. The second is the lack
of proper guidelines for information technology professionals on how to properly implement
information infrastructure protection.
IT professionals may not understand the security issues they face in their organizations and how
to resolve these issues, the complexity of information technology has made it more difficult
(Yeung, 2012). Figure 3 shows a general security framework developed by Triware Networld
Systems that will be used in implementing the system.
types of security architecture designs involved. The first is logical architecture; which involves
the processes, technology, and people involved. Understanding the flow of information is also
important in developing logical architecture. The second security architecture design is the
physical design which involves coming up with a diagram that illustrates the various firewalls,
network components, and connections that are related in architecture such as in figure 2.
designing a security architecture is coming up with policies and procedures which are meant to
define what is to be protected based on the organization’s needs. The fourth step is the
implementation of the architecture design. The fifth step after implementation is the integration
of security practices to deliver security.
The important part, however, knows the basic requirements of a security architecture.
(Kazanavicius, Kazanaviciu, &.Venckauskas, 2012) States that a security system should ensure
or enforce confidentiality, integrity availability and accountability.
For us to be able to develop an architecture that will help with information infrastructure
protection in banks, there is a need to know the guidelines or regulations that have been put in
place. These regulations are referred to as frameworks. An IT security framework is a chain of
processes used to outline the policies and procedures for protecting the information
infrastructure. A security framework is a guide for securing information (Kazanavicius,
Kazanavicius, & A.Venckauskas.).
According to Benson Yeung (2012) in the article ‘The Security Framework for Information
Technology’, there are two major causes of vulnerabilities in information security. The first is
mistakes by users and IT engineers whom most of the time are not trained. The second is the lack
of proper guidelines for information technology professionals on how to properly implement
information infrastructure protection.
IT professionals may not understand the security issues they face in their organizations and how
to resolve these issues, the complexity of information technology has made it more difficult
(Yeung, 2012). Figure 3 shows a general security framework developed by Triware Networld
Systems that will be used in implementing the system.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
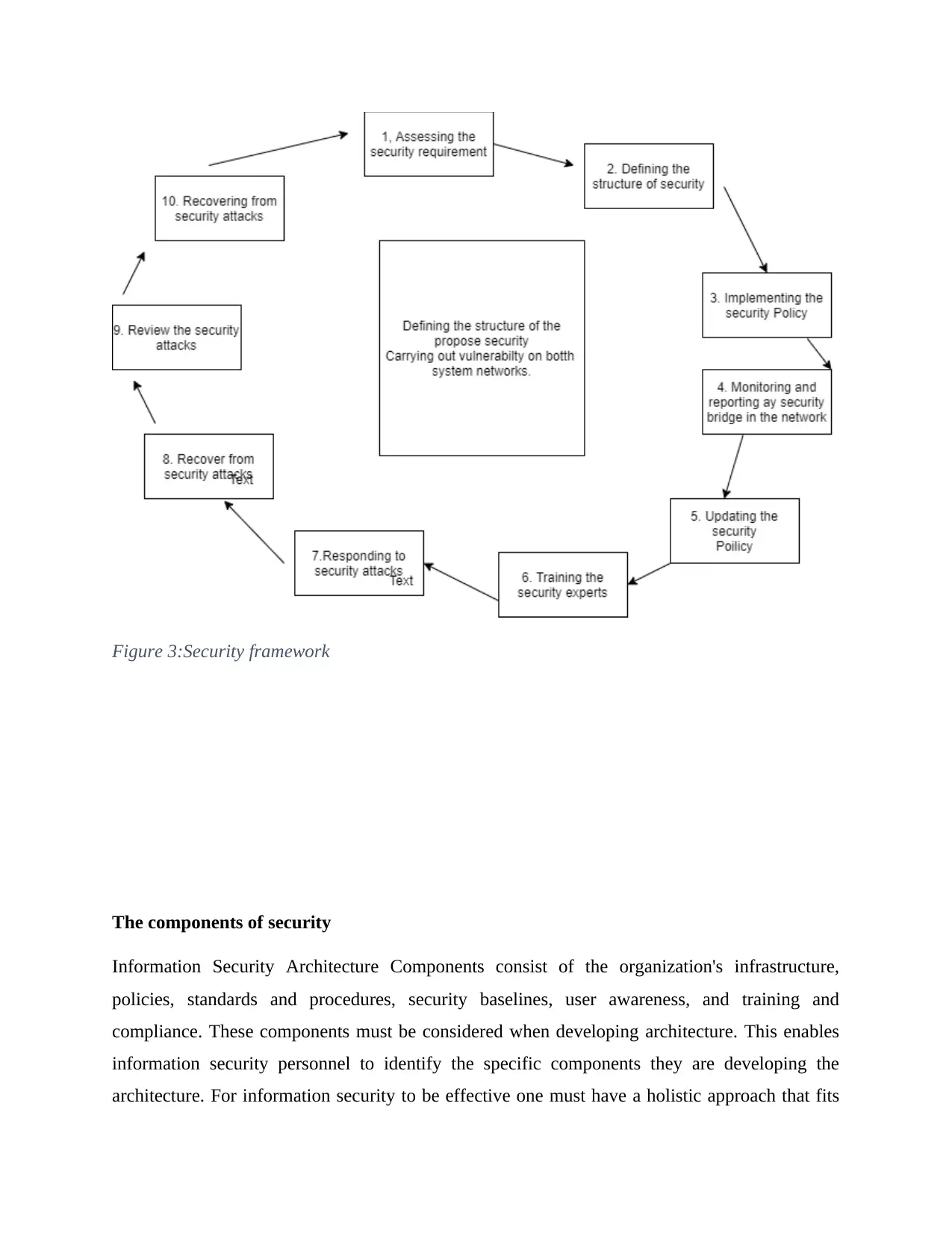
Figure 3:Security framework
The components of security
Information Security Architecture Components consist of the organization's infrastructure,
policies, standards and procedures, security baselines, user awareness, and training and
compliance. These components must be considered when developing architecture. This enables
information security personnel to identify the specific components they are developing the
architecture. For information security to be effective one must have a holistic approach that fits
The components of security
Information Security Architecture Components consist of the organization's infrastructure,
policies, standards and procedures, security baselines, user awareness, and training and
compliance. These components must be considered when developing architecture. This enables
information security personnel to identify the specific components they are developing the
architecture. For information security to be effective one must have a holistic approach that fits
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

the company’s profile. First, the identification of the critical systems for operations in the
organization can be done by knowing the important roles and responsibilities of the key
personnel in the organization. Secondly, policies, standards, and procedures are an important
aspect of creating an architecture design because they define the controls that are supposed to be
enforced in the organization. All of the above components are considered while designing the
system to fit the internet bank requirements. The system is designed in a way that it will update
users on the importance of information security.
The risks analysis needs to be done in components such as databases, networks, processing
platforms, and applications this will enable the bank to know the weakness and the
vulnerabilities of the information system.
The protection measures for Mobile banking
A mobile banking system consists of a mobile banking unit and a centre for processing banking
transactions and storing data. This functionality includes ATMs, online banking and mobile
transactions (Jin & Xianling, 2008) as shown in figure 2.4.
According to Jin and Xianling, (2008), mobile banking has two security zones. The first is the
mobile security zone which involves the people who use the mobile banking platform to carry
out transactions. The second is the banking security zone which lies on the bank's end. In this
zone, transactions are carried out between the banking system and the user.
Figure 4: Banking security protection
In mobile banking protection against various threats is important these threats are:
Information leakage, loss or distort
organization can be done by knowing the important roles and responsibilities of the key
personnel in the organization. Secondly, policies, standards, and procedures are an important
aspect of creating an architecture design because they define the controls that are supposed to be
enforced in the organization. All of the above components are considered while designing the
system to fit the internet bank requirements. The system is designed in a way that it will update
users on the importance of information security.
The risks analysis needs to be done in components such as databases, networks, processing
platforms, and applications this will enable the bank to know the weakness and the
vulnerabilities of the information system.
The protection measures for Mobile banking
A mobile banking system consists of a mobile banking unit and a centre for processing banking
transactions and storing data. This functionality includes ATMs, online banking and mobile
transactions (Jin & Xianling, 2008) as shown in figure 2.4.
According to Jin and Xianling, (2008), mobile banking has two security zones. The first is the
mobile security zone which involves the people who use the mobile banking platform to carry
out transactions. The second is the banking security zone which lies on the bank's end. In this
zone, transactions are carried out between the banking system and the user.
Figure 4: Banking security protection
In mobile banking protection against various threats is important these threats are:
Information leakage, loss or distort

Incomplete information caused by unstable mobile transmission channels
Denial of service attacks
The information security needs of a mobile banking system are different from the information
security needs of the banks’ network. Network protection strategy cannot be used for mobile
banking Jin and Xianling, (2008). There is a need for new technology and safety measures for
mobile banking. Mobile banking needs encryption technology to ensure there is data privacy,
system, and data integrity assurance in cases where an attacker may try to gain access to alter
information. Authentication is also important to ensure that transactions are carried out by
authorized individuals only. Digital signatures are important to ensure there are data
authentication and non-repudiation. Finally, a wireless public key infrastructure that uses a set of
standards for key and certificate management is needed to establish secure communication with
the banking system (Jin & Xianling, 2008). All of the protection measures that are mentioned
above are included in the proposed system to protect user-information from intruders.
The following properties are included in the architecture to protect customers data
Alignment: Information communication technology is used to ease management activities in an
organization. Therefore it is important to have the technology used aligned with the business.
Convergence: Information technology in an organization must all serve the purpose of achieving
the organization's goals and missions.
Maintainability: the technology used should be flexible to accommodate the changing needs of
a business.
Integrity: Data integrity and application integrity are very important.
Reliability: Availability of services is important in any organization, therefore accessibility to
services must be included.
Efficiency: helps to ensure resources and time are well maintained.
Denial of service attacks
The information security needs of a mobile banking system are different from the information
security needs of the banks’ network. Network protection strategy cannot be used for mobile
banking Jin and Xianling, (2008). There is a need for new technology and safety measures for
mobile banking. Mobile banking needs encryption technology to ensure there is data privacy,
system, and data integrity assurance in cases where an attacker may try to gain access to alter
information. Authentication is also important to ensure that transactions are carried out by
authorized individuals only. Digital signatures are important to ensure there are data
authentication and non-repudiation. Finally, a wireless public key infrastructure that uses a set of
standards for key and certificate management is needed to establish secure communication with
the banking system (Jin & Xianling, 2008). All of the protection measures that are mentioned
above are included in the proposed system to protect user-information from intruders.
The following properties are included in the architecture to protect customers data
Alignment: Information communication technology is used to ease management activities in an
organization. Therefore it is important to have the technology used aligned with the business.
Convergence: Information technology in an organization must all serve the purpose of achieving
the organization's goals and missions.
Maintainability: the technology used should be flexible to accommodate the changing needs of
a business.
Integrity: Data integrity and application integrity are very important.
Reliability: Availability of services is important in any organization, therefore accessibility to
services must be included.
Efficiency: helps to ensure resources and time are well maintained.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 22
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2025 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





