SIT120 Project: Confidential Internal Banking Communication Platform
VerifiedAdded on 2024/07/12
|17
|2138
|139
Project
AI Summary
This project proposes a secure internal communication platform for the banking sector to address data privacy and security concerns associated with third-party applications. The solution involves developing a hybrid application with key features like secure messaging, contact management, and an SOS function for emergencies. The project emphasizes data encryption, in-house data storage, and security measures such as firewalls and intrusion detection/prevention systems. Competitor analysis is conducted to identify best practices, and a resource analysis outlines the technologies used, including Cordova, Monaca, JavaScript, jQuery, and Node.js. The prototype features a minimalistic design approach with material design elements and considers personalization and touch ID integration for enhanced user experience and security. The document includes example app mockups and references.

CONFIDENTIAL
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

SIT120
PROJECT 1
STUDENT ID- HAR5D1802
STUDENT NAME- HARVEEN KAUR
1
PROJECT 1
STUDENT ID- HAR5D1802
STUDENT NAME- HARVEEN KAUR
1

Contents
STUDENT NAME- HARVEEN KAUR.........................................................................................1
Problem need and identification......................................................................................................3
Target audience................................................................................................................................4
Proposed solution.............................................................................................................................5
Competitor analysis.........................................................................................................................9
Resource analysis...........................................................................................................................10
Prototype Features.........................................................................................................................11
Visual Feel..................................................................................................................................... 12
Example design..............................................................................................................................13
References......................................................................................................................................16
2
STUDENT NAME- HARVEEN KAUR.........................................................................................1
Problem need and identification......................................................................................................3
Target audience................................................................................................................................4
Proposed solution.............................................................................................................................5
Competitor analysis.........................................................................................................................9
Resource analysis...........................................................................................................................10
Prototype Features.........................................................................................................................11
Visual Feel..................................................................................................................................... 12
Example design..............................................................................................................................13
References......................................................................................................................................16
2
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

Problem need and identification.
In the era of digital evolving world stay connected to everyone is a necessary evil. In the current
scenario, the internet has become a platform to help us to connect with everyone both personally
and professionally. When we talk about the professional relationship the information transmitted
through the third-party applications over the internet sometimes worth a fortune. With recent
events happing about the privacy and data breach the confidentiality of the same remains a big
question.
Our focus area is banking services which are the backbone of the current digital world. the
communication medium most of the banking services used around the world are third party
application which stores their valuable data.
We identified a problem of in-house information sharing platform to eliminate the risk of data
integrity. Initially, this will help them to communicate freely throughout the network of their
colleagues without thinking about the risk of data breach.
3
In the era of digital evolving world stay connected to everyone is a necessary evil. In the current
scenario, the internet has become a platform to help us to connect with everyone both personally
and professionally. When we talk about the professional relationship the information transmitted
through the third-party applications over the internet sometimes worth a fortune. With recent
events happing about the privacy and data breach the confidentiality of the same remains a big
question.
Our focus area is banking services which are the backbone of the current digital world. the
communication medium most of the banking services used around the world are third party
application which stores their valuable data.
We identified a problem of in-house information sharing platform to eliminate the risk of data
integrity. Initially, this will help them to communicate freely throughout the network of their
colleagues without thinking about the risk of data breach.
3
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Target audience
As we discussed above this problem is mainly concerns with the banking sector, this implies that
our target audience is the banking staff. The banking staff will act as our primary audience .all the
bank employees will act as the primary audience for our solution.
As we want to secure the transmission of information within the organization having only selected
audience will be our first important step in that regard.
Therefore there is no scope for any secondary audience in this proposed solution. Our primary
targeted audience includes all the level of employees in the banking sectors, initially, we plan to use
this proposed solution as only invitation basis to our audience. This will help us to identify the
flaws in the plan and we can make changes accordingly.
4
As we discussed above this problem is mainly concerns with the banking sector, this implies that
our target audience is the banking staff. The banking staff will act as our primary audience .all the
bank employees will act as the primary audience for our solution.
As we want to secure the transmission of information within the organization having only selected
audience will be our first important step in that regard.
Therefore there is no scope for any secondary audience in this proposed solution. Our primary
targeted audience includes all the level of employees in the banking sectors, initially, we plan to use
this proposed solution as only invitation basis to our audience. This will help us to identify the
flaws in the plan and we can make changes accordingly.
4

Proposed solution
In our proposed solution we are proposing a communication platform like any other
communication platform present already for team communication. Our proposed solution stand
different from that of all existing ones by two major areas that need to be focused:
1. Data privacy
2. Data security.
Data privacy:
As all the solutions available in market promise us the data privacy, but recent scenario suggest
that without their intentional motives there are some loopholes that sensitive information getting
leaked from their vaults.
In order to ensure this, we proposed an idea of in-house application platform which stores all the
data within the respective organization and has limited liability towards any third party app.
We also know that established a whole new infrastructure for this purpose can be troublesome for
some organization keeping that in mind we have a plan for hybrid application with limited but
necessary features available to make the whole process of developing and deploying the solution
become more cost and resource efficient.
In order to protect, private servers for the hybrid applications are set up inside the organization and
in-house clustering is used in order to connect the branches of the organization around the globe the
only place where a third party liability comes into the plat is to have an internet service provider.
To protect any threat from the ISP i.e. internet service provider state of art firewalls and IDS, IPS
will be deployed to save the internal network of the organization.
5
In our proposed solution we are proposing a communication platform like any other
communication platform present already for team communication. Our proposed solution stand
different from that of all existing ones by two major areas that need to be focused:
1. Data privacy
2. Data security.
Data privacy:
As all the solutions available in market promise us the data privacy, but recent scenario suggest
that without their intentional motives there are some loopholes that sensitive information getting
leaked from their vaults.
In order to ensure this, we proposed an idea of in-house application platform which stores all the
data within the respective organization and has limited liability towards any third party app.
We also know that established a whole new infrastructure for this purpose can be troublesome for
some organization keeping that in mind we have a plan for hybrid application with limited but
necessary features available to make the whole process of developing and deploying the solution
become more cost and resource efficient.
In order to protect, private servers for the hybrid applications are set up inside the organization and
in-house clustering is used in order to connect the branches of the organization around the globe the
only place where a third party liability comes into the plat is to have an internet service provider.
To protect any threat from the ISP i.e. internet service provider state of art firewalls and IDS, IPS
will be deployed to save the internal network of the organization.
5
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

Data security
When we talk about security that any application is as secure as it’s the weakest link. Keeping the
above in mind we will set up a number of checkpoints throughout the application to ensure the
security of data.
To secure the data while on the move encryption techniques will be used. Using encryption
technique will definitely slow the communication part but it will not affect that much despite the
level of security it is providing.
End to end encryption is used within the application to ensure the integrity of data.
To accomplish a bigger objective we must start achieving small goal first. In this trimester our aim
is to create a secure hybrid application with a limited feature to support our Idea.
Features which our hybrid app will have are as follows:
My contacts.
My messages.
Send Message.
SOS.
My profile.
My contacts:
This feature will provide the user to add their contacts within the organization. The user can add
contact and details regarding them. Adding their contacts enable them to communicate with the
added contacts. In order to save a contact of a user, the other user is asked by the app about their
consent of the same. If another user does not agree you cannot save the contact.
My messages:
In this feature, the user can see the messages which are sent by other users. A user can only see
messages only when the sender is in their contact list. This enables the receiver to receive only
relevant messages and add a layer of security to avoid the injection of malicious messages in their
inbox.
6
When we talk about security that any application is as secure as it’s the weakest link. Keeping the
above in mind we will set up a number of checkpoints throughout the application to ensure the
security of data.
To secure the data while on the move encryption techniques will be used. Using encryption
technique will definitely slow the communication part but it will not affect that much despite the
level of security it is providing.
End to end encryption is used within the application to ensure the integrity of data.
To accomplish a bigger objective we must start achieving small goal first. In this trimester our aim
is to create a secure hybrid application with a limited feature to support our Idea.
Features which our hybrid app will have are as follows:
My contacts.
My messages.
Send Message.
SOS.
My profile.
My contacts:
This feature will provide the user to add their contacts within the organization. The user can add
contact and details regarding them. Adding their contacts enable them to communicate with the
added contacts. In order to save a contact of a user, the other user is asked by the app about their
consent of the same. If another user does not agree you cannot save the contact.
My messages:
In this feature, the user can see the messages which are sent by other users. A user can only see
messages only when the sender is in their contact list. This enables the receiver to receive only
relevant messages and add a layer of security to avoid the injection of malicious messages in their
inbox.
6
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Send message:
As we can understand from the name above this feature enables the user to send messages to saved
contacts. In order to send a message to a contact, it is necessary that both sender and receiver must
have the contact of each other saved in their contact list.
My profile
This feature enables the user to see details about the user. This feature also allows the user to
control their privacy as who can see their information and how they want to share the information.
To protect data on the move user can use either system generated encryption or own passphrase to
encrypt the data Monaca.io. (2018).
SOS
Sometimes despite every measure, we take to control the outcome of the situation the situation
cannot be controlled. To take care of these type of situation an SOS feature will be given in the
application which can be used in case of breach or any uncertain circumstances.
This feature will send notifications immediately to predefined contact in order to get the help from
the concerned authorities.
7
As we can understand from the name above this feature enables the user to send messages to saved
contacts. In order to send a message to a contact, it is necessary that both sender and receiver must
have the contact of each other saved in their contact list.
My profile
This feature enables the user to see details about the user. This feature also allows the user to
control their privacy as who can see their information and how they want to share the information.
To protect data on the move user can use either system generated encryption or own passphrase to
encrypt the data Monaca.io. (2018).
SOS
Sometimes despite every measure, we take to control the outcome of the situation the situation
cannot be controlled. To take care of these type of situation an SOS feature will be given in the
application which can be used in case of breach or any uncertain circumstances.
This feature will send notifications immediately to predefined contact in order to get the help from
the concerned authorities.
7
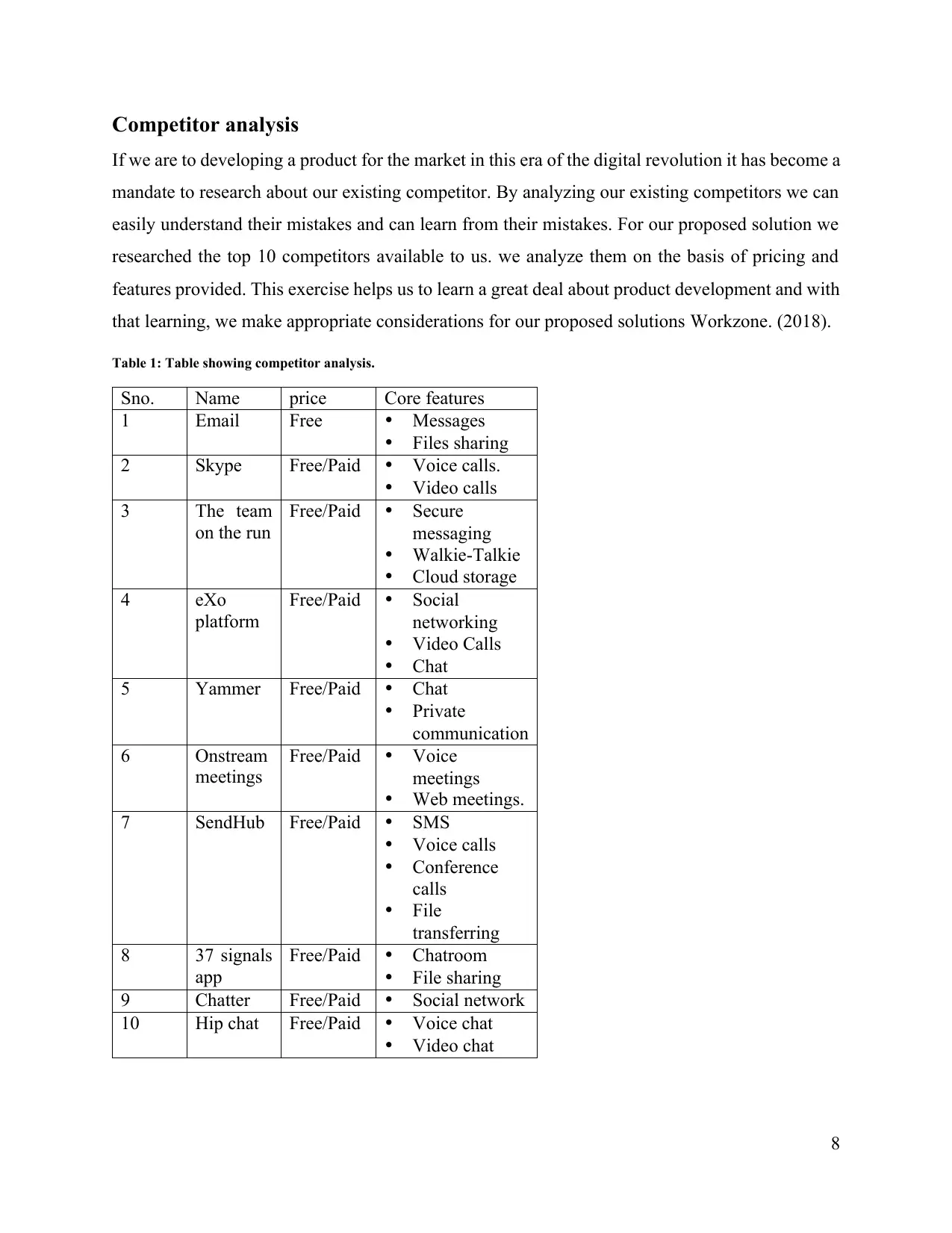
Competitor analysis
If we are to developing a product for the market in this era of the digital revolution it has become a
mandate to research about our existing competitor. By analyzing our existing competitors we can
easily understand their mistakes and can learn from their mistakes. For our proposed solution we
researched the top 10 competitors available to us. we analyze them on the basis of pricing and
features provided. This exercise helps us to learn a great deal about product development and with
that learning, we make appropriate considerations for our proposed solutions Workzone. (2018).
Table 1: Table showing competitor analysis.
Sno. Name price Core features
1 Email Free Messages
Files sharing
2 Skype Free/Paid Voice calls.
Video calls
3 The team
on the run
Free/Paid Secure
messaging
Walkie-Talkie
Cloud storage
4 eXo
platform
Free/Paid Social
networking
Video Calls
Chat
5 Yammer Free/Paid Chat
Private
communication
6 Onstream
meetings
Free/Paid Voice
meetings
Web meetings.
7 SendHub Free/Paid SMS
Voice calls
Conference
calls
File
transferring
8 37 signals
app
Free/Paid Chatroom
File sharing
9 Chatter Free/Paid Social network
10 Hip chat Free/Paid Voice chat
Video chat
8
If we are to developing a product for the market in this era of the digital revolution it has become a
mandate to research about our existing competitor. By analyzing our existing competitors we can
easily understand their mistakes and can learn from their mistakes. For our proposed solution we
researched the top 10 competitors available to us. we analyze them on the basis of pricing and
features provided. This exercise helps us to learn a great deal about product development and with
that learning, we make appropriate considerations for our proposed solutions Workzone. (2018).
Table 1: Table showing competitor analysis.
Sno. Name price Core features
1 Email Free Messages
Files sharing
2 Skype Free/Paid Voice calls.
Video calls
3 The team
on the run
Free/Paid Secure
messaging
Walkie-Talkie
Cloud storage
4 eXo
platform
Free/Paid Social
networking
Video Calls
Chat
5 Yammer Free/Paid Chat
Private
communication
6 Onstream
meetings
Free/Paid Voice
meetings
Web meetings.
7 SendHub Free/Paid SMS
Voice calls
Conference
calls
File
transferring
8 37 signals
app
Free/Paid Chatroom
File sharing
9 Chatter Free/Paid Social network
10 Hip chat Free/Paid Voice chat
Video chat
8
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

Resource analysis
Any type of application development cannot be done without using the resources. We also need
resources for developing this hybrid application. In order t develop this hybrid app we will use
Cordova engine in addition with Monaca technology languages which we will use for development
are javascript jquery and unseen.
The operating system which we have used to develop this application is ubuntu flavor of Linux.
The server-side language used is node.js.
After developing our hybrid application we have used android and IOS platforms for testing this
application.
Table 2: Showing the resource analysis of the hybrid application.
Type of resource resource
Engine cordova
Technology Monaca
Languages JavaScript
jQuery
onsen
Os ubuntu
Server-side language nodejs
Testing platform Android, Apple ios
9
Any type of application development cannot be done without using the resources. We also need
resources for developing this hybrid application. In order t develop this hybrid app we will use
Cordova engine in addition with Monaca technology languages which we will use for development
are javascript jquery and unseen.
The operating system which we have used to develop this application is ubuntu flavor of Linux.
The server-side language used is node.js.
After developing our hybrid application we have used android and IOS platforms for testing this
application.
Table 2: Showing the resource analysis of the hybrid application.
Type of resource resource
Engine cordova
Technology Monaca
Languages JavaScript
jQuery
onsen
Os ubuntu
Server-side language nodejs
Testing platform Android, Apple ios
9
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Prototype Features
Prototyping is the initial step in developing any product. In this phase main focus of us is to
incorporate the features which will be deployed in our first release. In a prototype of our solution,
we intended to include SOS, My contacts, My messages, and Send message features with My
profile.
These features may seem to be overrated at first glance but our solution is for a particular sector
which is banking, all the servers required for deploying this system will be set up within the
organization and added a layer of security will be added by the end to end encryption
implementation in our solution. This will protect our data on the move.
10
Prototyping is the initial step in developing any product. In this phase main focus of us is to
incorporate the features which will be deployed in our first release. In a prototype of our solution,
we intended to include SOS, My contacts, My messages, and Send message features with My
profile.
These features may seem to be overrated at first glance but our solution is for a particular sector
which is banking, all the servers required for deploying this system will be set up within the
organization and added a layer of security will be added by the end to end encryption
implementation in our solution. This will protect our data on the move.
10

Visual Feel
Visual feel is the most important component of any application. In any of the following industry,
the app should be according to people needs and behavior. After implying any of the features and
most updated UI/and UX there is always some space for improvement.
We must use the following approaches in order to make our application more user-friendly:
Minimalistic design approach:
In a minimalistic design approach, we mean what we say because minimalistic approach means
that having a simpler design in the user interface. We do not want the user to be overwhelmed with
many things. In order to make application user interface simpler, we introduced only some limited
feature in the first version of app Smashing Magazine. (2018).
Material design
Material design is the new thing in app design this has brought the design of the real world into the
hands of the user. The material design follows the real world approach and this makes the user feel
more connected towards the application. We intended to use material designing in our hybrid
application development.
Personalization
The user is connected to the app as much as they see it more personalized according to their needs.
Thus we intended to provide our users with as much personalization as possible according to our
solution. As our solution more focused on security part the scope for personalization is very
limited.
Touch ID
Now, most of the mobile devices came equipped with touch ID sensors this will provide us both
user ease of use and accessibility. We will try to incorporate the features of this touch ID in order to
secure our app and provide the user an inquisitive experience.
11
Visual feel is the most important component of any application. In any of the following industry,
the app should be according to people needs and behavior. After implying any of the features and
most updated UI/and UX there is always some space for improvement.
We must use the following approaches in order to make our application more user-friendly:
Minimalistic design approach:
In a minimalistic design approach, we mean what we say because minimalistic approach means
that having a simpler design in the user interface. We do not want the user to be overwhelmed with
many things. In order to make application user interface simpler, we introduced only some limited
feature in the first version of app Smashing Magazine. (2018).
Material design
Material design is the new thing in app design this has brought the design of the real world into the
hands of the user. The material design follows the real world approach and this makes the user feel
more connected towards the application. We intended to use material designing in our hybrid
application development.
Personalization
The user is connected to the app as much as they see it more personalized according to their needs.
Thus we intended to provide our users with as much personalization as possible according to our
solution. As our solution more focused on security part the scope for personalization is very
limited.
Touch ID
Now, most of the mobile devices came equipped with touch ID sensors this will provide us both
user ease of use and accessibility. We will try to incorporate the features of this touch ID in order to
secure our app and provide the user an inquisitive experience.
11
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 17
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





