BCO 6653 - Value and Risk Analysis in IT: Strategic Approaches
VerifiedAdded on 2023/04/21
|11
|920
|397
Report
AI Summary
This report explores the necessity of value and risk analysis in information technology. It highlights strategic alignment, structured portfolio management, IT and business architecture alignment, and effective IT project management as key components of value analysis. The report identifies technical, structural, financial, human, and natural threats affecting IT infrastructure and discusses protective, mitigation, recovery measures, and contingency planning as benefits of risk analysis. The conclusion emphasizes that IT value analysis is a compelling starting point for determining significant issues and that risk analysis can address risks related to specific actions or events. Desklib provides access to this and other solved assignments to support student learning.

The need for
value and risk
analysis in
information
technology
value and risk
analysis in
information
technology
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Introduction:
IT risk analysis is an important part to determine
and control practical problems affecting the IT
infrastructure. Besides, a successful value analysis
provides the IT department with proper information to
fetch things undoubtedly and to respond to the
strategic needs and the company’s preferences. In
this presentation, the necessity for risk and value
analysis is done in the sector of information
technology.
IT risk analysis is an important part to determine
and control practical problems affecting the IT
infrastructure. Besides, a successful value analysis
provides the IT department with proper information to
fetch things undoubtedly and to respond to the
strategic needs and the company’s preferences. In
this presentation, the necessity for risk and value
analysis is done in the sector of information
technology.
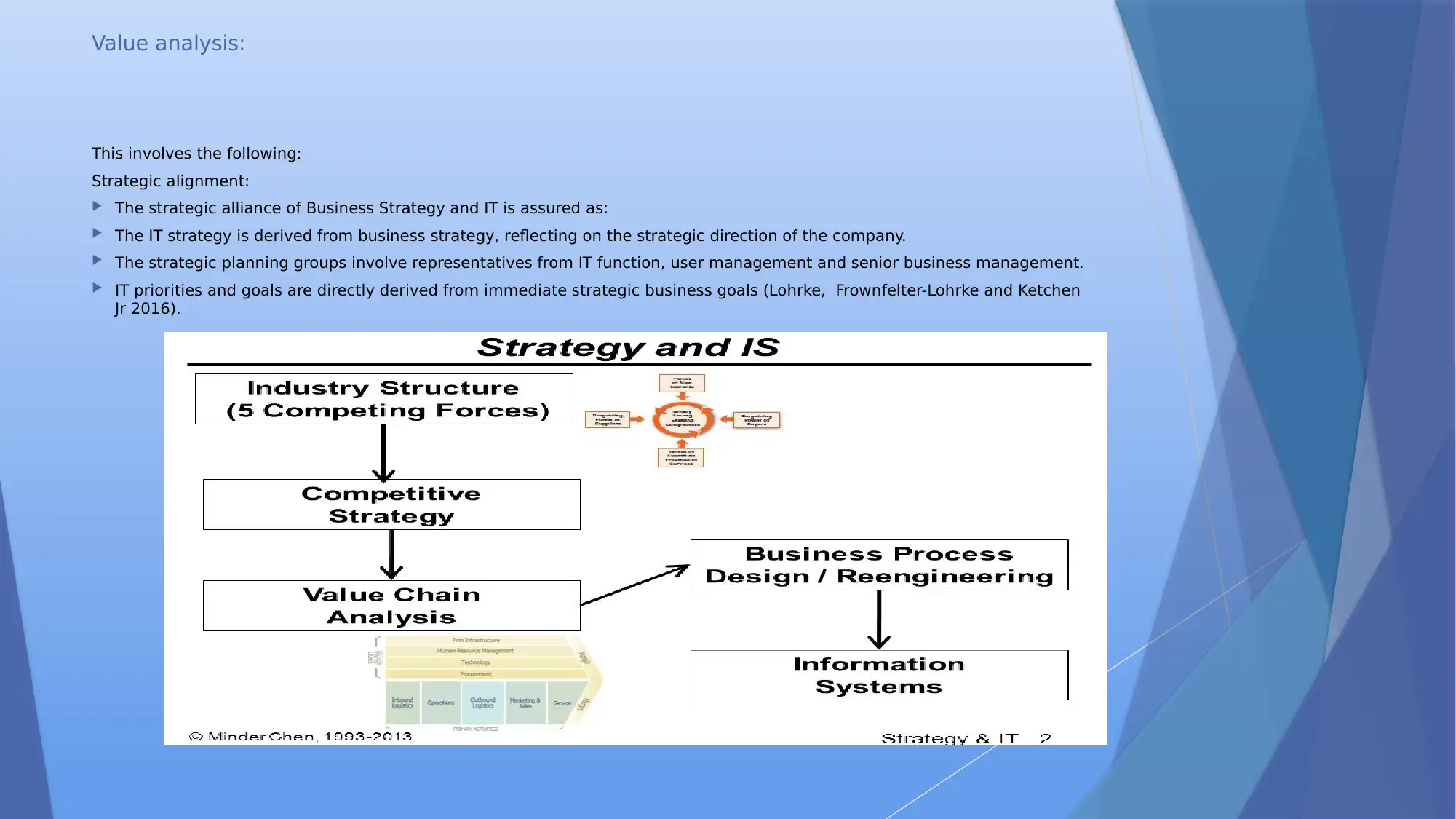
Value analysis:
This involves the following:
Strategic alignment:
The strategic alliance of Business Strategy and IT is assured as:
The IT strategy is derived from business strategy, reflecting on the strategic direction of the company.
The strategic planning groups involve representatives from IT function, user management and senior business management.
IT priorities and goals are directly derived from immediate strategic business goals (Lohrke, Frownfelter-Lohrke and Ketchen
Jr 2016).
This involves the following:
Strategic alignment:
The strategic alliance of Business Strategy and IT is assured as:
The IT strategy is derived from business strategy, reflecting on the strategic direction of the company.
The strategic planning groups involve representatives from IT function, user management and senior business management.
IT priorities and goals are directly derived from immediate strategic business goals (Lohrke, Frownfelter-Lohrke and Ketchen
Jr 2016).
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
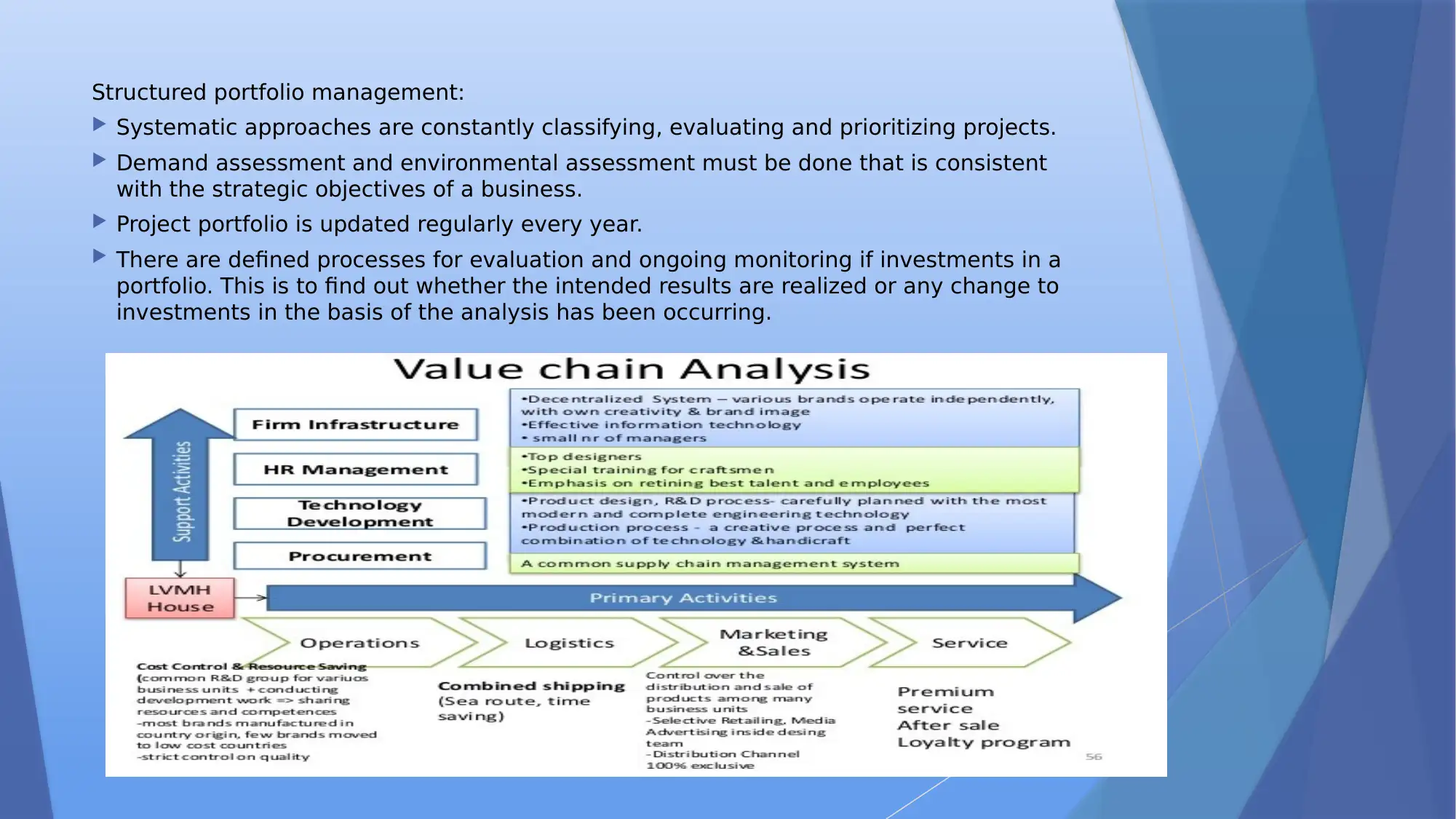
Structured portfolio management:
Systematic approaches are constantly classifying, evaluating and prioritizing projects.
Demand assessment and environmental assessment must be done that is consistent
with the strategic objectives of a business.
Project portfolio is updated regularly every year.
There are defined processes for evaluation and ongoing monitoring if investments in a
portfolio. This is to find out whether the intended results are realized or any change to
investments in the basis of the analysis has been occurring.
Systematic approaches are constantly classifying, evaluating and prioritizing projects.
Demand assessment and environmental assessment must be done that is consistent
with the strategic objectives of a business.
Project portfolio is updated regularly every year.
There are defined processes for evaluation and ongoing monitoring if investments in a
portfolio. This is to find out whether the intended results are realized or any change to
investments in the basis of the analysis has been occurring.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
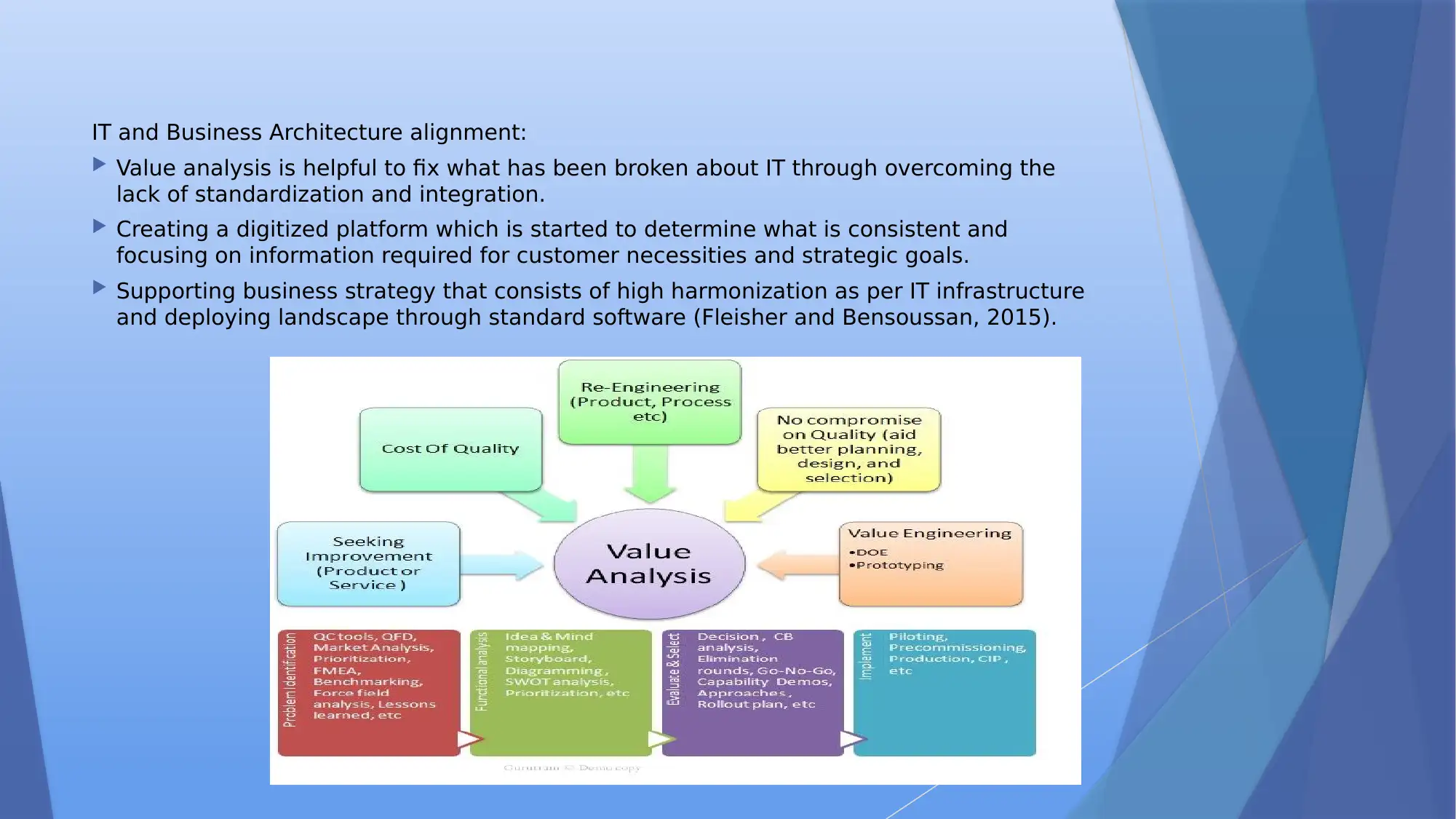
IT and Business Architecture alignment:
Value analysis is helpful to fix what has been broken about IT through overcoming the
lack of standardization and integration.
Creating a digitized platform which is started to determine what is consistent and
focusing on information required for customer necessities and strategic goals.
Supporting business strategy that consists of high harmonization as per IT infrastructure
and deploying landscape through standard software (Fleisher and Bensoussan, 2015).
Value analysis is helpful to fix what has been broken about IT through overcoming the
lack of standardization and integration.
Creating a digitized platform which is started to determine what is consistent and
focusing on information required for customer necessities and strategic goals.
Supporting business strategy that consists of high harmonization as per IT infrastructure
and deploying landscape through standard software (Fleisher and Bensoussan, 2015).
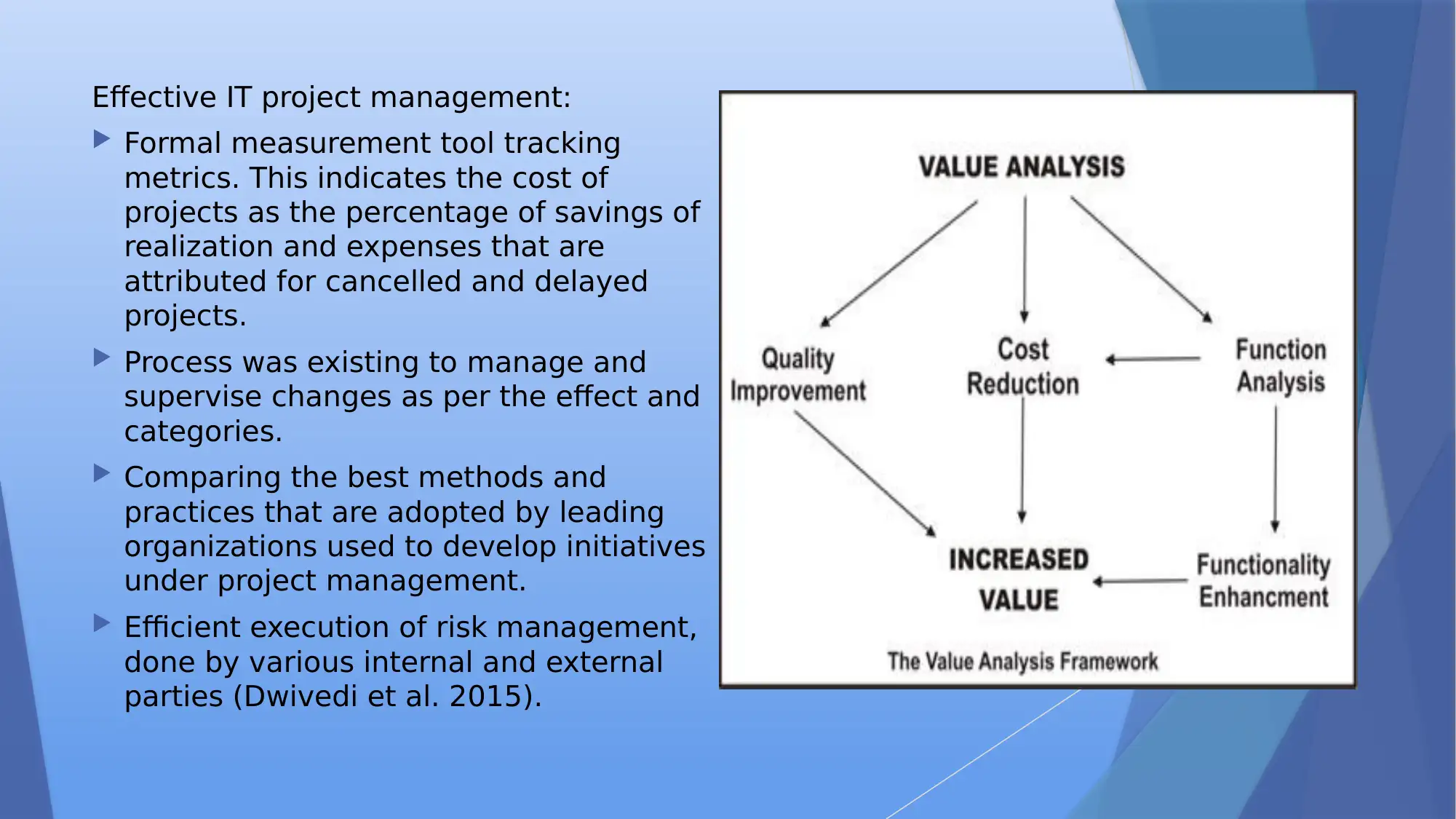
Effective IT project management:
Formal measurement tool tracking
metrics. This indicates the cost of
projects as the percentage of savings of
realization and expenses that are
attributed for cancelled and delayed
projects.
Process was existing to manage and
supervise changes as per the effect and
categories.
Comparing the best methods and
practices that are adopted by leading
organizations used to develop initiatives
under project management.
Efficient execution of risk management,
done by various internal and external
parties (Dwivedi et al. 2015).
Formal measurement tool tracking
metrics. This indicates the cost of
projects as the percentage of savings of
realization and expenses that are
attributed for cancelled and delayed
projects.
Process was existing to manage and
supervise changes as per the effect and
categories.
Comparing the best methods and
practices that are adopted by leading
organizations used to develop initiatives
under project management.
Efficient execution of risk management,
done by various internal and external
parties (Dwivedi et al. 2015).
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
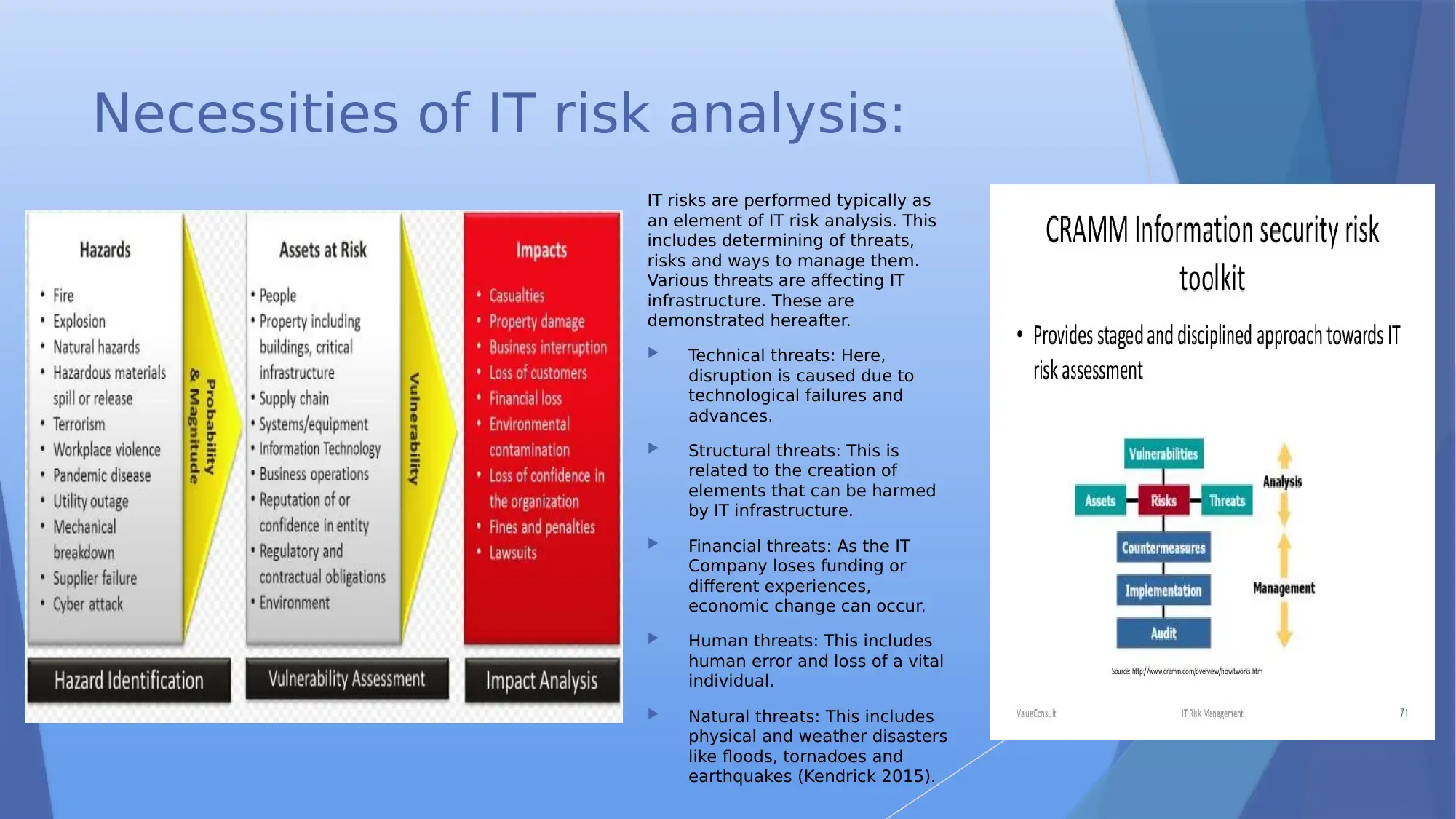
Necessities of IT risk analysis:
IT risks are performed typically as
an element of IT risk analysis. This
includes determining of threats,
risks and ways to manage them.
Various threats are affecting IT
infrastructure. These are
demonstrated hereafter.
Technical threats: Here,
disruption is caused due to
technological failures and
advances.
Structural threats: This is
related to the creation of
elements that can be harmed
by IT infrastructure.
Financial threats: As the IT
Company loses funding or
different experiences,
economic change can occur.
Human threats: This includes
human error and loss of a vital
individual.
Natural threats: This includes
physical and weather disasters
like floods, tornadoes and
earthquakes (Kendrick 2015).
IT risks are performed typically as
an element of IT risk analysis. This
includes determining of threats,
risks and ways to manage them.
Various threats are affecting IT
infrastructure. These are
demonstrated hereafter.
Technical threats: Here,
disruption is caused due to
technological failures and
advances.
Structural threats: This is
related to the creation of
elements that can be harmed
by IT infrastructure.
Financial threats: As the IT
Company loses funding or
different experiences,
economic change can occur.
Human threats: This includes
human error and loss of a vital
individual.
Natural threats: This includes
physical and weather disasters
like floods, tornadoes and
earthquakes (Kendrick 2015).
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Benefits of risk analysis:
As the IT Company has listed the above risks,
they must consider the following measures of risk
analysis.
Protective measures: This decreases the scopes
as the listed risks take place.
Mitigation measures: This declines the severity of
disaster as it takes place.
Activities of recovery: This restores the
infrastructure of systems affecting the company
for common business operations.
Contingency planning: This reveals what to be
done as a disruptive event or any dangerous
event take place (Slovic 2016).
As the IT Company has listed the above risks,
they must consider the following measures of risk
analysis.
Protective measures: This decreases the scopes
as the listed risks take place.
Mitigation measures: This declines the severity of
disaster as it takes place.
Activities of recovery: This restores the
infrastructure of systems affecting the company
for common business operations.
Contingency planning: This reveals what to be
done as a disruptive event or any dangerous
event take place (Slovic 2016).

Conclusion:
The IT value analysis is a compelling beginning point for determining
the most significant issues. Here, the key is to define the scopes were
having the most significant effect and earlier success such as the
establishment of continuous and formalized business-relationship
management. Besides, the presentation highlights how risk analysis
can also be referred to risks related to specific action or event. This
applies to projects, security problems, information technology and
effects where the risks are examined on a qualitative and quantitative
basis.
The IT value analysis is a compelling beginning point for determining
the most significant issues. Here, the key is to define the scopes were
having the most significant effect and earlier success such as the
establishment of continuous and formalized business-relationship
management. Besides, the presentation highlights how risk analysis
can also be referred to risks related to specific action or event. This
applies to projects, security problems, information technology and
effects where the risks are examined on a qualitative and quantitative
basis.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

References:
Dwivedi, Y.K., Wastell, D., Laumer, S., Henriksen, H.Z., Myers,
M.D., Bunker, D., Elbanna, A., Ravishankar, M.N. and Srivastava,
S.C., 2015. Research on information systems failures and
successes: Status update and future directions. Information
Systems Frontiers, 17(1), pp.143-157.
Fleisher, C.S. and Bensoussan, B.E., 2015. Business and
competitive analysis: effective application of new and classic
methods. FT Press.
Kendrick, T., 2015. Identifying and managing project risk:
essential tools for failure-proofing your project. Amacom.
Lohrke, F.T., Frownfelter-Lohrke, C. and Ketchen Jr, D.J., 2016.
The role of information technology systems in the performance
of mergers and acquisitions. Business Horizons, 59(1), pp.7-12.
Slovic, P., 2016. The perception of risk. Routledge.
Dwivedi, Y.K., Wastell, D., Laumer, S., Henriksen, H.Z., Myers,
M.D., Bunker, D., Elbanna, A., Ravishankar, M.N. and Srivastava,
S.C., 2015. Research on information systems failures and
successes: Status update and future directions. Information
Systems Frontiers, 17(1), pp.143-157.
Fleisher, C.S. and Bensoussan, B.E., 2015. Business and
competitive analysis: effective application of new and classic
methods. FT Press.
Kendrick, T., 2015. Identifying and managing project risk:
essential tools for failure-proofing your project. Amacom.
Lohrke, F.T., Frownfelter-Lohrke, C. and Ketchen Jr, D.J., 2016.
The role of information technology systems in the performance
of mergers and acquisitions. Business Horizons, 59(1), pp.7-12.
Slovic, P., 2016. The perception of risk. Routledge.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

1 out of 11
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.

![Information Systems Governance Report Analysis - [University Name]](/_next/image/?url=https%3A%2F%2Fdesklib.com%2Fmedia%2Fimages%2Fdb%2F573cbc5eb2ed4d5d86d3a5bdd74a0903.jpg&w=256&q=75)



