Project Proposal and Plan: BCT Applied in Cloud Computing, ITC571
VerifiedAdded on 2022/09/09
|13
|2314
|21
Project
AI Summary
This project proposal investigates the integration of Blockchain Technology (BCT) to address security and privacy concerns within cloud computing environments. The proposal begins with an introduction to the topic, outlining the benefits and drawbacks of cloud computing, particularly focusing on security vulnerabilities such as DDoS attacks, data breaches, and insider threats. The rationale emphasizes the need for enhanced data integrity and security, proposing BCT as a solution to improve these aspects. The research includes a detailed problem domain analysis, research questions, and a conceptual framework that identifies the key security and privacy challenges. The methodology section describes the research methods, data collection techniques, and ethical considerations. A project plan, including a work breakdown structure (WBS), risk analysis, Gantt chart, and references, is also provided. The proposal aims to demonstrate how BCT can be utilized to protect sensitive information and maintain data integrity in cloud environments. The project is designed to analyze the implementation of a secure system based on BCT to prevent data breaches and enhance the overall security posture of cloud computing.

Running head: BCT APPLIED IN CLOUD COMPUTING
BCT Applied in Cloud Computing
BCT Applied in Cloud Computing
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

1BCT APPLIED IN CLOUD COMPUTING
Table of Contents
Introduction................................................................................................................................3
Rationale of the proposal...........................................................................................................3
Problem domain.....................................................................................................................3
Purpose and Justification........................................................................................................4
Research Questions....................................................................................................................4
Conceptual Framework..............................................................................................................5
Motivation..............................................................................................................................5
Significance of the research...................................................................................................5
Findings of the researchers.....................................................................................................6
Materials and Methodology.......................................................................................................6
Research methods...................................................................................................................6
Data collection methods.........................................................................................................6
Ethical issues of the proposal.................................................................................................7
Compliance Requirements.....................................................................................................7
Solution of security problems................................................................................................7
Procedures of the research.....................................................................................................8
Project Plan................................................................................................................................9
Risk analysis...........................................................................................................................9
Duration................................................................................................................................10
Gantt chart............................................................................................................................11
References................................................................................................................................12
Table of Contents
Introduction................................................................................................................................3
Rationale of the proposal...........................................................................................................3
Problem domain.....................................................................................................................3
Purpose and Justification........................................................................................................4
Research Questions....................................................................................................................4
Conceptual Framework..............................................................................................................5
Motivation..............................................................................................................................5
Significance of the research...................................................................................................5
Findings of the researchers.....................................................................................................6
Materials and Methodology.......................................................................................................6
Research methods...................................................................................................................6
Data collection methods.........................................................................................................6
Ethical issues of the proposal.................................................................................................7
Compliance Requirements.....................................................................................................7
Solution of security problems................................................................................................7
Procedures of the research.....................................................................................................8
Project Plan................................................................................................................................9
Risk analysis...........................................................................................................................9
Duration................................................................................................................................10
Gantt chart............................................................................................................................11
References................................................................................................................................12

2BCT APPLIED IN CLOUD COMPUTING
Introduction
The development in Information Technology has shown growth in terms of numerous
advanced computer facilities such as cloud computing (Liu, Zhang, & Yang, 2018). There are
drawbacks and positives related to cloud computing as well. The benefits of this IT
innovation include resilient computing, accessing API, advanced online security and effective
virtualization. On the other hand, there are few drawbacks related to this IT innovation as
well, in terms of the privacy and security issues, these issues can come from both the
employees working in the data centers of the cloud computing services as well as from the
hackers (Rao, 2016). The privacy issues include data security issues, service disruption and
multi-tenancy, there are few security measures such as Multi Factor Authentication which
can be used to address these issues.
Block chain technology (BCT) can also be defined as a distributed ledger technology
and it completely based on the peer to peer technology (Thomas, Pastrana, Hutchings,
Clayton, & Beresford, 2017). BCT is much significant for its users as it allows data to be
stored globally, all the real time information can be successfully stored in data centers using
this technology.
The main inspiration and motivation of the proposal is to address the privacy and
security issues of the cloud computing facilities. This research shall be much convenient for
its readers to comprehend the capability of BCT to address the issues which are faced while
using cloud computing facilities.
Introduction
The development in Information Technology has shown growth in terms of numerous
advanced computer facilities such as cloud computing (Liu, Zhang, & Yang, 2018). There are
drawbacks and positives related to cloud computing as well. The benefits of this IT
innovation include resilient computing, accessing API, advanced online security and effective
virtualization. On the other hand, there are few drawbacks related to this IT innovation as
well, in terms of the privacy and security issues, these issues can come from both the
employees working in the data centers of the cloud computing services as well as from the
hackers (Rao, 2016). The privacy issues include data security issues, service disruption and
multi-tenancy, there are few security measures such as Multi Factor Authentication which
can be used to address these issues.
Block chain technology (BCT) can also be defined as a distributed ledger technology
and it completely based on the peer to peer technology (Thomas, Pastrana, Hutchings,
Clayton, & Beresford, 2017). BCT is much significant for its users as it allows data to be
stored globally, all the real time information can be successfully stored in data centers using
this technology.
The main inspiration and motivation of the proposal is to address the privacy and
security issues of the cloud computing facilities. This research shall be much convenient for
its readers to comprehend the capability of BCT to address the issues which are faced while
using cloud computing facilities.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

3BCT APPLIED IN CLOUD COMPUTING
Rationale of the proposal
Problem domain
Network down time in the cloud servers can be very much vulnerable to the data
which are stored in the cloud servers. There are numerous data security attacks which are
associated to cloud computing services such as DDoS, shared cloud computing services,
negligence coming from the employees working in the data centers, phishing emails and
system vulnerabilities.
The other essential privacy issues related to the use of cloud computing are credential
ad access management, account hijacking, malicious insiders, persistent threats and loss of
sensitive data.
Purpose and Justification
The block chain ledgers are important to improve the integrity of the data which are
stored in the cloud servers. Merkle tree ensures the integrity of both the transactional data as
well as the real time data (Zhang, Deng, Liu, & Zheng, 2018). All the hash functions must be
managed sequentially, and it can help to safeguard the veracity of the fundamental data
blocks. The capabilities of BCT might be useful to address the security and privacy issues of
the cloud computing services and this proposal shall be testing the capabilities of BCT in a
systemized modus.
Inclusions of the research: The solution to the problems faced due to the security
issues of cloud coloring shall be identified only from peer reviewed journals.
Exclusions of the research: Empirical analysis shall not be a part of the solution plan
for the identified issues.
Rationale of the proposal
Problem domain
Network down time in the cloud servers can be very much vulnerable to the data
which are stored in the cloud servers. There are numerous data security attacks which are
associated to cloud computing services such as DDoS, shared cloud computing services,
negligence coming from the employees working in the data centers, phishing emails and
system vulnerabilities.
The other essential privacy issues related to the use of cloud computing are credential
ad access management, account hijacking, malicious insiders, persistent threats and loss of
sensitive data.
Purpose and Justification
The block chain ledgers are important to improve the integrity of the data which are
stored in the cloud servers. Merkle tree ensures the integrity of both the transactional data as
well as the real time data (Zhang, Deng, Liu, & Zheng, 2018). All the hash functions must be
managed sequentially, and it can help to safeguard the veracity of the fundamental data
blocks. The capabilities of BCT might be useful to address the security and privacy issues of
the cloud computing services and this proposal shall be testing the capabilities of BCT in a
systemized modus.
Inclusions of the research: The solution to the problems faced due to the security
issues of cloud coloring shall be identified only from peer reviewed journals.
Exclusions of the research: Empirical analysis shall not be a part of the solution plan
for the identified issues.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

4BCT APPLIED IN CLOUD COMPUTING
Research Questions
What are the privacy and security concerns regarding the use of cloud computing
technology?
How can the security of centralized data be maintained using BCT?
What are the changes required in the cloud computing services to prevent social
engineers from hacking the essential information?
Conceptual Framework
The conceptual framework of this proposal shall be identifying most of the security
and privacy issues faced while using cloud computing services.
Motivation
Current there the few solutions regarding the security challenges which are faced
while using the cloud computing services such as the Multi Factor Authentication (MFA),
management of the user account of the cloud service platforms, monitoring the log of each
activities of an account in cloud computing (Lin et al., 2018). Apart from this, several
authentication tools are being introduced every day for the protection of the data which are
stored in the cloud servers. Data protection regulation are there in each of the organization
who provides access of the cloud accounts as well (Zheng, Xie, Dai, Chen, & Wang, 2017).
Thus, this research proposal can be very much beneficial for the readers to comprehend the
procedure which can the security and privacy problems of cloud computing systems will be
minimized using the BCT.
Significance of the research
This proposal will be important for the readers of this proposal as it will be focusing
on the contribution of BCT to address the security issues faced in cloud computing solutions.
Research Questions
What are the privacy and security concerns regarding the use of cloud computing
technology?
How can the security of centralized data be maintained using BCT?
What are the changes required in the cloud computing services to prevent social
engineers from hacking the essential information?
Conceptual Framework
The conceptual framework of this proposal shall be identifying most of the security
and privacy issues faced while using cloud computing services.
Motivation
Current there the few solutions regarding the security challenges which are faced
while using the cloud computing services such as the Multi Factor Authentication (MFA),
management of the user account of the cloud service platforms, monitoring the log of each
activities of an account in cloud computing (Lin et al., 2018). Apart from this, several
authentication tools are being introduced every day for the protection of the data which are
stored in the cloud servers. Data protection regulation are there in each of the organization
who provides access of the cloud accounts as well (Zheng, Xie, Dai, Chen, & Wang, 2017).
Thus, this research proposal can be very much beneficial for the readers to comprehend the
procedure which can the security and privacy problems of cloud computing systems will be
minimized using the BCT.
Significance of the research
This proposal will be important for the readers of this proposal as it will be focusing
on the contribution of BCT to address the security issues faced in cloud computing solutions.

5BCT APPLIED IN CLOUD COMPUTING
Billions of people all around the world are suffering due to the security and the privacy
concerns of the cloud computing facilities, and it is causing both reputational loss as well as
financial loss in all the major commercial establishments who are using cloud computing
services for the protection of the online assets of the business (Liang et al., 2017). Thus,
proposal will be very much useful for all the major business establishments those who are in
fear of losing their essential data, which are stored in the cloud servers.
Findings of the researchers
The researchers are trying to figure out the ways by which BCT can be successfully
used to deal with security and privacy concerns regarding the deployment of cloud computing
services. The researchers are also trying to find out whether the enactment of a secure system
that will be created on the basis of the BCT can prevent hackers from stealing essential
information from the cloud computing accounts.
Materials and Methodology
The methods which will be used in this research paper shall be stated in this section of
the proposal.
Research methods
This research proposal will be conducted on the basis of the descriptive investigation
procedure, it will be describing the behaviour of a subject using relevant models and theories
which are proposed by the reputed scholars all over the world. Probabilistic sampling
technique will be considered as the sampling technique in the research proposal, this
sampling technique can make this proposal free from sampling biasedness. The margin of
error of this proposal can also be reduced using this sampling method. The analyst of this
proposal shall be conducted using the qualitative technique. This technique will be very much
useful in interpreting the secondary data of this proposal (Kumar, Raj, & Jelciana, 2018).
Billions of people all around the world are suffering due to the security and the privacy
concerns of the cloud computing facilities, and it is causing both reputational loss as well as
financial loss in all the major commercial establishments who are using cloud computing
services for the protection of the online assets of the business (Liang et al., 2017). Thus,
proposal will be very much useful for all the major business establishments those who are in
fear of losing their essential data, which are stored in the cloud servers.
Findings of the researchers
The researchers are trying to figure out the ways by which BCT can be successfully
used to deal with security and privacy concerns regarding the deployment of cloud computing
services. The researchers are also trying to find out whether the enactment of a secure system
that will be created on the basis of the BCT can prevent hackers from stealing essential
information from the cloud computing accounts.
Materials and Methodology
The methods which will be used in this research paper shall be stated in this section of
the proposal.
Research methods
This research proposal will be conducted on the basis of the descriptive investigation
procedure, it will be describing the behaviour of a subject using relevant models and theories
which are proposed by the reputed scholars all over the world. Probabilistic sampling
technique will be considered as the sampling technique in the research proposal, this
sampling technique can make this proposal free from sampling biasedness. The margin of
error of this proposal can also be reduced using this sampling method. The analyst of this
proposal shall be conducted using the qualitative technique. This technique will be very much
useful in interpreting the secondary data of this proposal (Kumar, Raj, & Jelciana, 2018).
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

6BCT APPLIED IN CLOUD COMPUTING
Lack of sufficient time and absence of a surplus of budget are the major constraints of this
proposal.
Data collection methods
Data of this proposal shall be collected from secondary source such as Google
Scholar. Relevant and latest peer reviewed journals shall be selected to identify the solution
of the problems relayed to the deployment of cloud computing services. The gaps and threw
deficiencies of the previous researches can be identified using secondary data collection
(Johnston, 2017).
Ethical issues of the proposal
There are numerous ethical issues related to this proposal such as getting the consent
from the lecturer to select the topic of the proposal, sustaining the integrity of the data which
will be collected from the peer reviewed journal articles, respecting the original scholars of
the peer reviewed journals who have stated their solution of the current security problems
regarding the use of cloud computing services (Crosby, Pattanayak, Verma, &
Kalyanaraman, 2016).
Compliance Requirements
Considering statements coming from the Department of Industry, it can be understood
that the Australian government has a national block chain roadmap ("Regulation and
standards,"). The road map helps the Australians to make the most out of this technology, the
technology can be used for the betterment of the Australian society and the Australian
commercial organizations.
Solution of security problems
Aligning cloud computing accounts with a block chain network is beneficial to
preserve the integrity of the transactional data (Biswas & Muthukkumarasamy, 2016).
Lack of sufficient time and absence of a surplus of budget are the major constraints of this
proposal.
Data collection methods
Data of this proposal shall be collected from secondary source such as Google
Scholar. Relevant and latest peer reviewed journals shall be selected to identify the solution
of the problems relayed to the deployment of cloud computing services. The gaps and threw
deficiencies of the previous researches can be identified using secondary data collection
(Johnston, 2017).
Ethical issues of the proposal
There are numerous ethical issues related to this proposal such as getting the consent
from the lecturer to select the topic of the proposal, sustaining the integrity of the data which
will be collected from the peer reviewed journal articles, respecting the original scholars of
the peer reviewed journals who have stated their solution of the current security problems
regarding the use of cloud computing services (Crosby, Pattanayak, Verma, &
Kalyanaraman, 2016).
Compliance Requirements
Considering statements coming from the Department of Industry, it can be understood
that the Australian government has a national block chain roadmap ("Regulation and
standards,"). The road map helps the Australians to make the most out of this technology, the
technology can be used for the betterment of the Australian society and the Australian
commercial organizations.
Solution of security problems
Aligning cloud computing accounts with a block chain network is beneficial to
preserve the integrity of the transactional data (Biswas & Muthukkumarasamy, 2016).
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
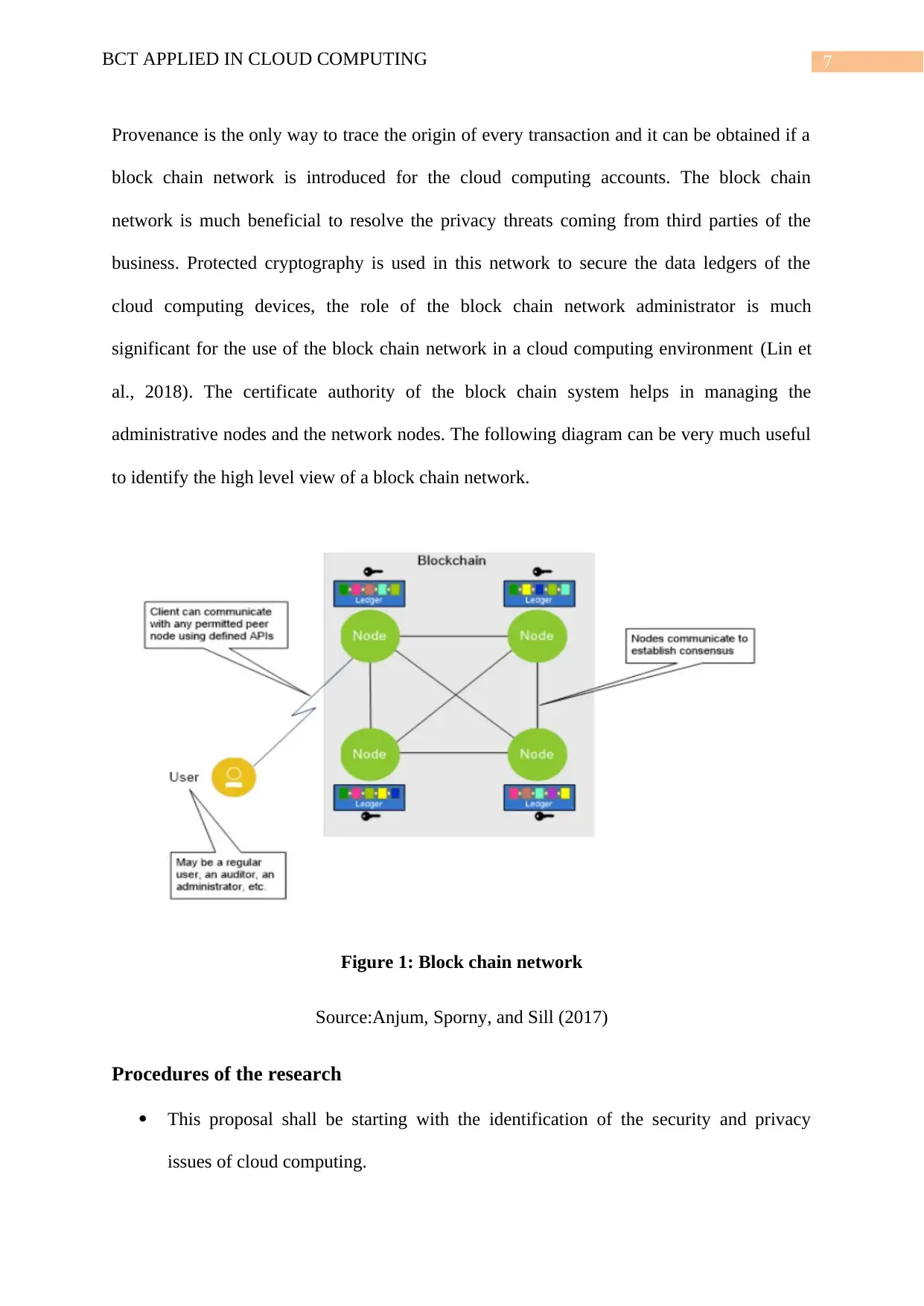
7BCT APPLIED IN CLOUD COMPUTING
Provenance is the only way to trace the origin of every transaction and it can be obtained if a
block chain network is introduced for the cloud computing accounts. The block chain
network is much beneficial to resolve the privacy threats coming from third parties of the
business. Protected cryptography is used in this network to secure the data ledgers of the
cloud computing devices, the role of the block chain network administrator is much
significant for the use of the block chain network in a cloud computing environment (Lin et
al., 2018). The certificate authority of the block chain system helps in managing the
administrative nodes and the network nodes. The following diagram can be very much useful
to identify the high level view of a block chain network.
Figure 1: Block chain network
Source:Anjum, Sporny, and Sill (2017)
Procedures of the research
This proposal shall be starting with the identification of the security and privacy
issues of cloud computing.
Provenance is the only way to trace the origin of every transaction and it can be obtained if a
block chain network is introduced for the cloud computing accounts. The block chain
network is much beneficial to resolve the privacy threats coming from third parties of the
business. Protected cryptography is used in this network to secure the data ledgers of the
cloud computing devices, the role of the block chain network administrator is much
significant for the use of the block chain network in a cloud computing environment (Lin et
al., 2018). The certificate authority of the block chain system helps in managing the
administrative nodes and the network nodes. The following diagram can be very much useful
to identify the high level view of a block chain network.
Figure 1: Block chain network
Source:Anjum, Sporny, and Sill (2017)
Procedures of the research
This proposal shall be starting with the identification of the security and privacy
issues of cloud computing.

8BCT APPLIED IN CLOUD COMPUTING
The previous solutions and the existing solutions shall be identified in the following
step. Based on the existing solution, research questions shall be formed.
The inspiration of the research and how this proposal can be useful to address the
identified issues shall be described thoroughly in the conceptual framework.
The ensuing step is the detailed description of the methodologies of the proposal like
the sampling method and data collection method.
The proposal shall be concluding with a solution for all the identified glitches
regarding the use of cloud computing.
The previous solutions and the existing solutions shall be identified in the following
step. Based on the existing solution, research questions shall be formed.
The inspiration of the research and how this proposal can be useful to address the
identified issues shall be described thoroughly in the conceptual framework.
The ensuing step is the detailed description of the methodologies of the proposal like
the sampling method and data collection method.
The proposal shall be concluding with a solution for all the identified glitches
regarding the use of cloud computing.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
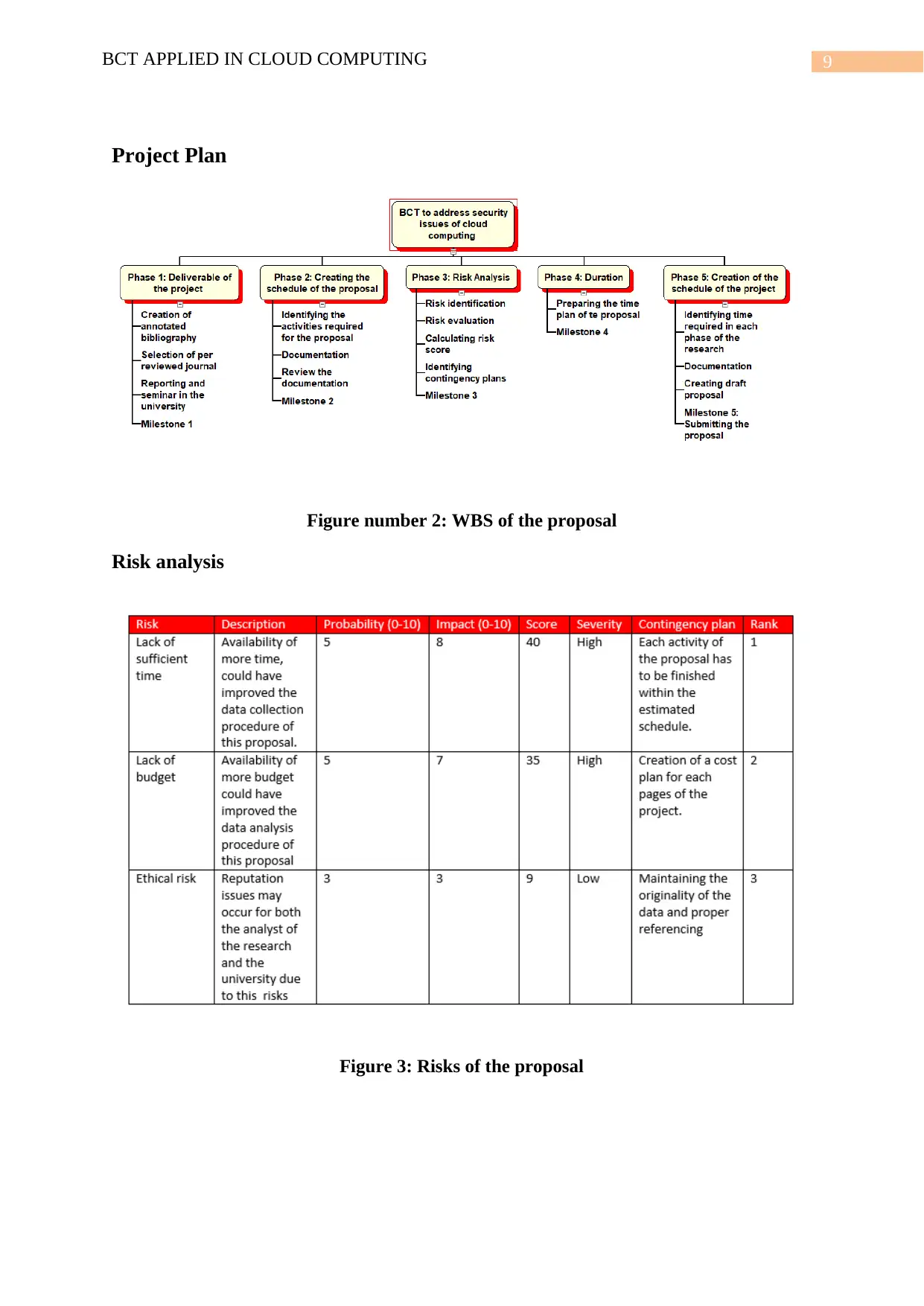
9BCT APPLIED IN CLOUD COMPUTING
Project Plan
Figure number 2: WBS of the proposal
Risk analysis
Figure 3: Risks of the proposal
Project Plan
Figure number 2: WBS of the proposal
Risk analysis
Figure 3: Risks of the proposal
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
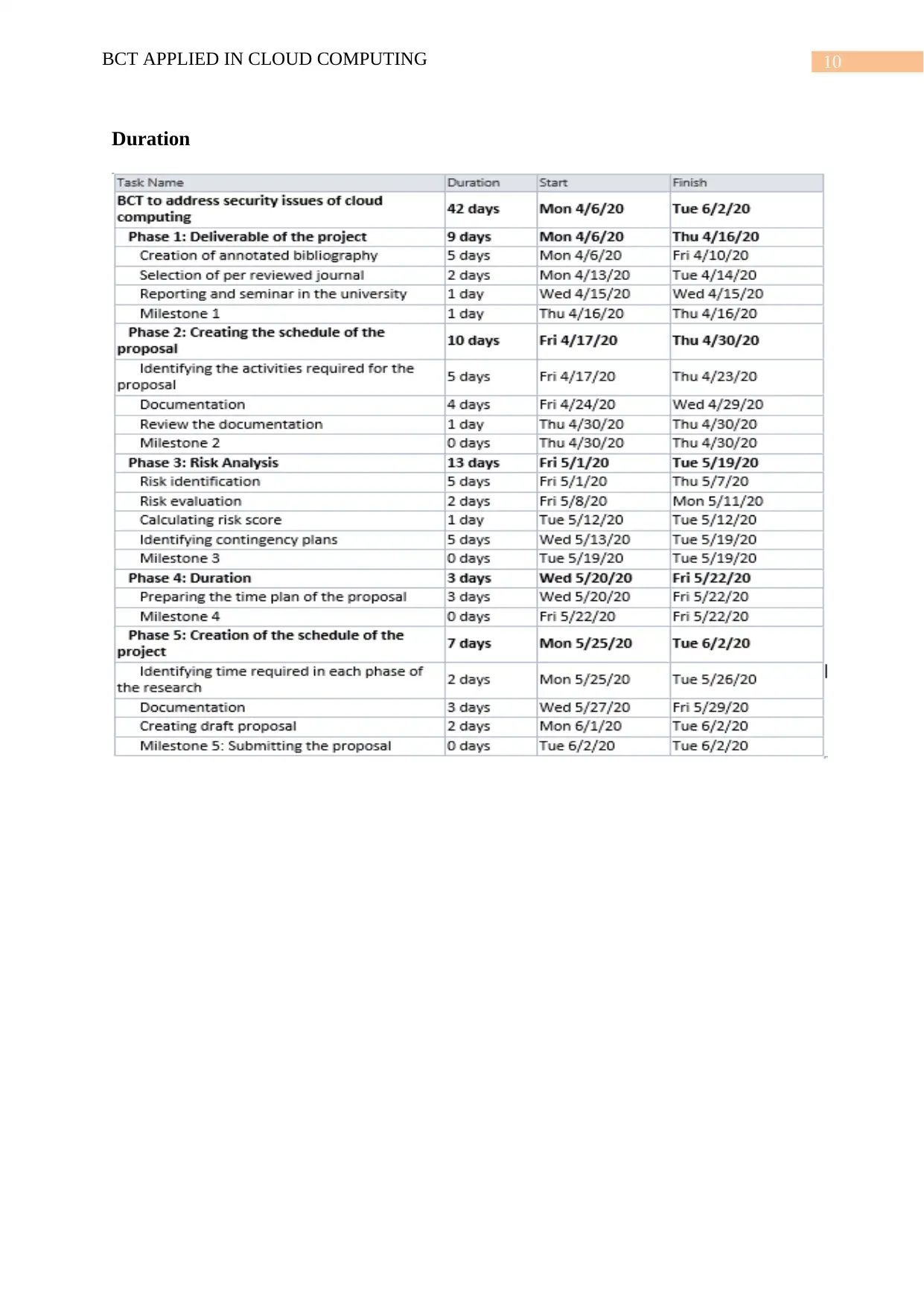
10BCT APPLIED IN CLOUD COMPUTING
Duration
Duration
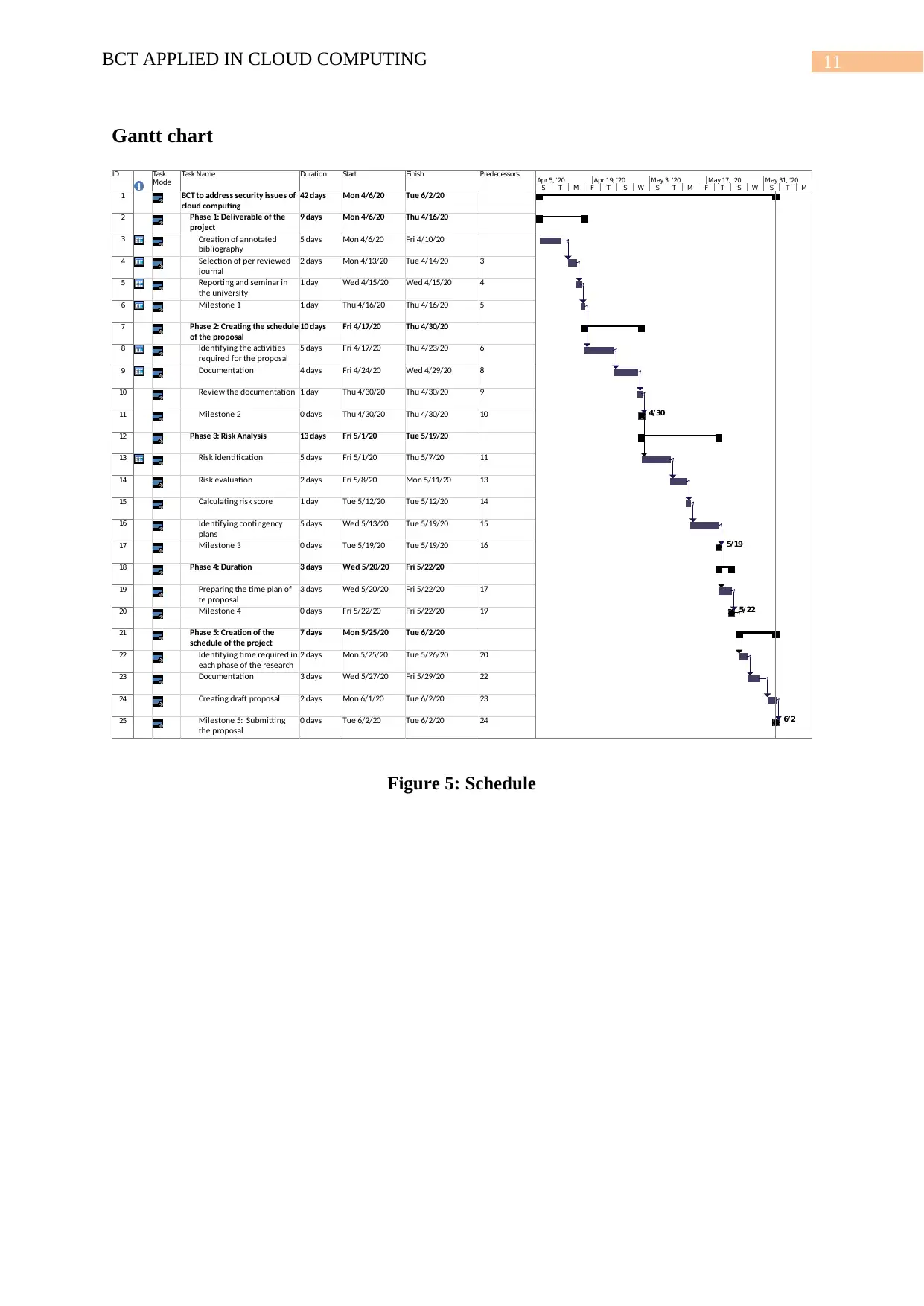
11BCT APPLIED IN CLOUD COMPUTING
Gantt chart
ID Task
Mode
Task Name Duration Start Finish Predecessors
1 BCT to address security issues of
cloud computing
42 days Mon 4/6/20 Tue 6/2/20
2 Phase 1: Deliverable of the
project
9 days Mon 4/6/20 Thu 4/16/20
3 Creation of annotated
bibliography
5 days Mon 4/6/20 Fri 4/10/20
4 Selection of per reviewed
journal
2 days Mon 4/13/20 Tue 4/14/20 3
5 Reporting and seminar in
the university
1 day Wed 4/15/20 Wed 4/15/20 4
6 Milestone 1 1 day Thu 4/16/20 Thu 4/16/20 5
7 Phase 2: Creating the schedule
of the proposal
10 days Fri 4/17/20 Thu 4/30/20
8 Identifying the activities
required for the proposal
5 days Fri 4/17/20 Thu 4/23/20 6
9 Documentation 4 days Fri 4/24/20 Wed 4/29/20 8
10 Review the documentation 1 day Thu 4/30/20 Thu 4/30/20 9
11 Milestone 2 0 days Thu 4/30/20 Thu 4/30/20 10
12 Phase 3: Risk Analysis 13 days Fri 5/1/20 Tue 5/19/20
13 Risk identification 5 days Fri 5/1/20 Thu 5/7/20 11
14 Risk evaluation 2 days Fri 5/8/20 Mon 5/11/20 13
15 Calculating risk score 1 day Tue 5/12/20 Tue 5/12/20 14
16 Identifying contingency
plans
5 days Wed 5/13/20 Tue 5/19/20 15
17 Milestone 3 0 days Tue 5/19/20 Tue 5/19/20 16
18 Phase 4: Duration 3 days Wed 5/20/20 Fri 5/22/20
19 Preparing the time plan of
te proposal
3 days Wed 5/20/20 Fri 5/22/20 17
20 Milestone 4 0 days Fri 5/22/20 Fri 5/22/20 19
21 Phase 5: Creation of the
schedule of the project
7 days Mon 5/25/20 Tue 6/2/20
22 Identifying time required in
each phase of the research
2 days Mon 5/25/20 Tue 5/26/20 20
23 Documentation 3 days Wed 5/27/20 Fri 5/29/20 22
24 Creating draft proposal 2 days Mon 6/1/20 Tue 6/2/20 23
25 Milestone 5: Submitting
the proposal
0 days Tue 6/2/20 Tue 6/2/20 24
4/30
5/19
5/22
6/2
S T M F T S W S T M F T S W S T M
Apr 5, '20 Apr 19, '20 May 3, '20 May 17, '20 May 31, '20
Figure 5: Schedule
Gantt chart
ID Task
Mode
Task Name Duration Start Finish Predecessors
1 BCT to address security issues of
cloud computing
42 days Mon 4/6/20 Tue 6/2/20
2 Phase 1: Deliverable of the
project
9 days Mon 4/6/20 Thu 4/16/20
3 Creation of annotated
bibliography
5 days Mon 4/6/20 Fri 4/10/20
4 Selection of per reviewed
journal
2 days Mon 4/13/20 Tue 4/14/20 3
5 Reporting and seminar in
the university
1 day Wed 4/15/20 Wed 4/15/20 4
6 Milestone 1 1 day Thu 4/16/20 Thu 4/16/20 5
7 Phase 2: Creating the schedule
of the proposal
10 days Fri 4/17/20 Thu 4/30/20
8 Identifying the activities
required for the proposal
5 days Fri 4/17/20 Thu 4/23/20 6
9 Documentation 4 days Fri 4/24/20 Wed 4/29/20 8
10 Review the documentation 1 day Thu 4/30/20 Thu 4/30/20 9
11 Milestone 2 0 days Thu 4/30/20 Thu 4/30/20 10
12 Phase 3: Risk Analysis 13 days Fri 5/1/20 Tue 5/19/20
13 Risk identification 5 days Fri 5/1/20 Thu 5/7/20 11
14 Risk evaluation 2 days Fri 5/8/20 Mon 5/11/20 13
15 Calculating risk score 1 day Tue 5/12/20 Tue 5/12/20 14
16 Identifying contingency
plans
5 days Wed 5/13/20 Tue 5/19/20 15
17 Milestone 3 0 days Tue 5/19/20 Tue 5/19/20 16
18 Phase 4: Duration 3 days Wed 5/20/20 Fri 5/22/20
19 Preparing the time plan of
te proposal
3 days Wed 5/20/20 Fri 5/22/20 17
20 Milestone 4 0 days Fri 5/22/20 Fri 5/22/20 19
21 Phase 5: Creation of the
schedule of the project
7 days Mon 5/25/20 Tue 6/2/20
22 Identifying time required in
each phase of the research
2 days Mon 5/25/20 Tue 5/26/20 20
23 Documentation 3 days Wed 5/27/20 Fri 5/29/20 22
24 Creating draft proposal 2 days Mon 6/1/20 Tue 6/2/20 23
25 Milestone 5: Submitting
the proposal
0 days Tue 6/2/20 Tue 6/2/20 24
4/30
5/19
5/22
6/2
S T M F T S W S T M F T S W S T M
Apr 5, '20 Apr 19, '20 May 3, '20 May 17, '20 May 31, '20
Figure 5: Schedule
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 13
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.




