HI5019 Strategic Information Systems: Bell Studio Case Study
VerifiedAdded on 2022/11/26
|17
|2885
|479
Case Study
AI Summary
This case study analyzes the strategic information system of Bell Studio, an Adelaide distributor of workmanship suppliers, focusing on its accounting architecture and related risks. The report includes data flow diagrams for the purchase, cash disbursement, and payroll systems. It identifies weaknesses in the internal control structure, such as outdated software and vulnerabilities in the cash disbursement and payroll systems. The study explores potential risks, including unauthorized access, malware, spoofing, and sniffing, along with the threats posed by internal actors. The analysis emphasizes the need for updated security protocols and improved system management to mitigate these risks and protect the company's sensitive financial data. The report concludes with a discussion of the impact of these vulnerabilities and the importance of proactive security measures.

Running head: STRATEGIC INFORMATION SYSTEM FOR BUSINESS AND
ENTERPRISE
Strategic Information System for Business and Enterprise
Name of the Student
Name of the University
Author Note
ENTERPRISE
Strategic Information System for Business and Enterprise
Name of the Student
Name of the University
Author Note
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

1STRATEGIC INFORMATION SYSTEM FOR BUSINESS AND ENTERPRISE
Table of Contents
Introduction................................................................................................................................2
DFD of Purchase System and Cash Disbursement System.......................................................2
DFD of Payroll System..............................................................................................................3
System Flowchart of Cash Disbursement System.....................................................................5
System Flowchart of Payroll System.........................................................................................6
Description of the possible weaknesses in the internal structure of the system and the risk
connected to the weaknesses identified......................................................................................7
Weaknesses prevailing in the Organization...........................................................................7
Risks.........................................................................................................................................10
Unauthorized access.............................................................................................................10
Malware................................................................................................................................10
Spoofing and Sniffing..........................................................................................................11
Conclusion................................................................................................................................13
References................................................................................................................................14
Table of Contents
Introduction................................................................................................................................2
DFD of Purchase System and Cash Disbursement System.......................................................2
DFD of Payroll System..............................................................................................................3
System Flowchart of Cash Disbursement System.....................................................................5
System Flowchart of Payroll System.........................................................................................6
Description of the possible weaknesses in the internal structure of the system and the risk
connected to the weaknesses identified......................................................................................7
Weaknesses prevailing in the Organization...........................................................................7
Risks.........................................................................................................................................10
Unauthorized access.............................................................................................................10
Malware................................................................................................................................10
Spoofing and Sniffing..........................................................................................................11
Conclusion................................................................................................................................13
References................................................................................................................................14
2STRATEGIC INFORMATION SYSTEM FOR BUSINESS AND ENTERPRISE
Introduction
The purpose of the report is to examine existing scenario in Bell Studios. Bell Studio
is an Adelaide distributer of workmanship suppliers. The organization has a uniform and
united accounting architecture. The risks are evaluated in this particular report with respect to
the internal control of the expenditure cycle and the other several processes. In this report, the
data flow diagram of the payroll system and the cash disbursement system is discussed. The
internal weaknesses in the control system of the company is briefly discussed and explored.
There exists risk in the system which is thoroughly discussed.
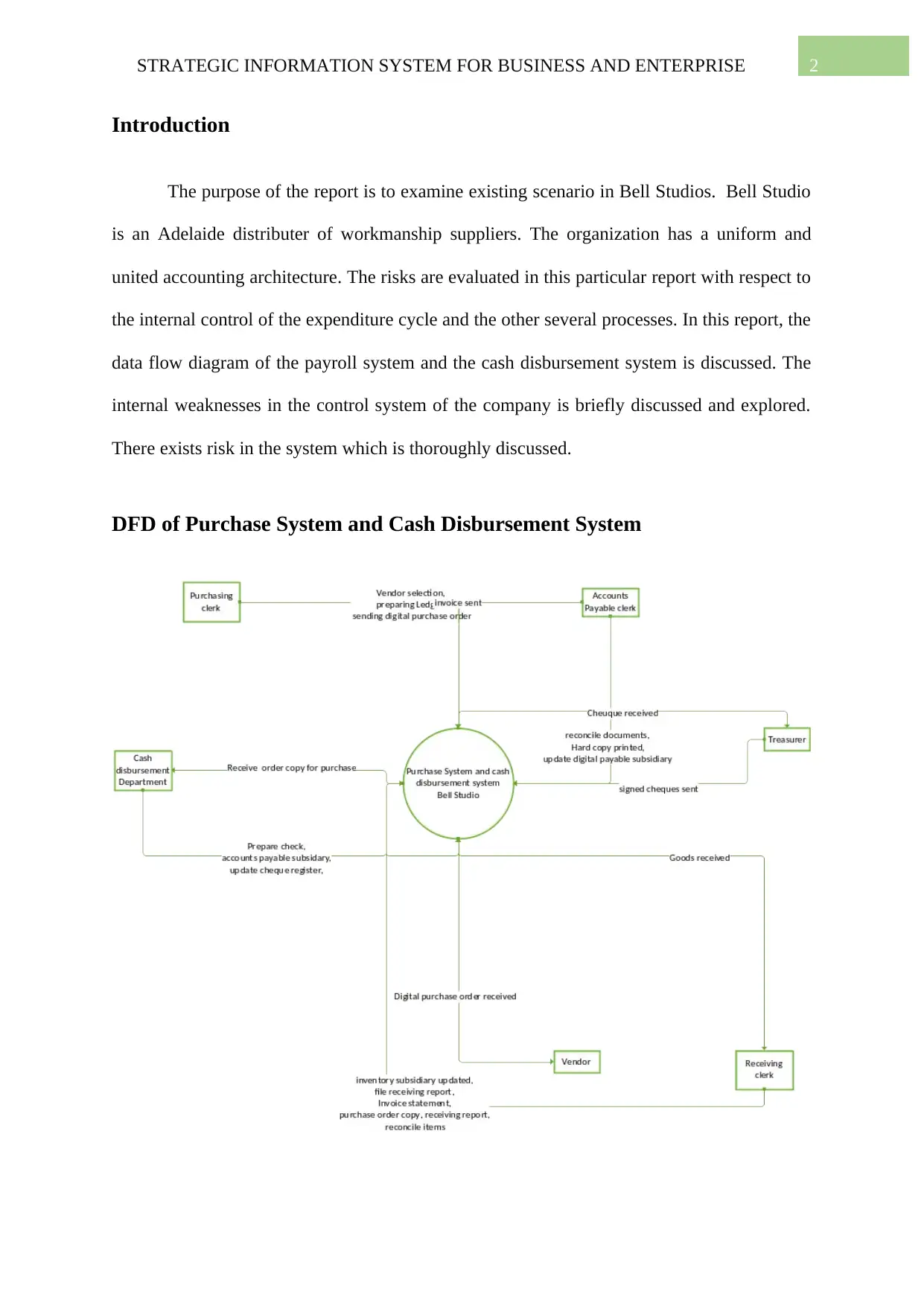
DFD of Purchase System and Cash Disbursement System
Introduction
The purpose of the report is to examine existing scenario in Bell Studios. Bell Studio
is an Adelaide distributer of workmanship suppliers. The organization has a uniform and
united accounting architecture. The risks are evaluated in this particular report with respect to
the internal control of the expenditure cycle and the other several processes. In this report, the
data flow diagram of the payroll system and the cash disbursement system is discussed. The
internal weaknesses in the control system of the company is briefly discussed and explored.
There exists risk in the system which is thoroughly discussed.
DFD of Purchase System and Cash Disbursement System
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
3STRATEGIC INFORMATION SYSTEM FOR BUSINESS AND ENTERPRISE
Figure 1. DFD of Purchase System and Cash Disbursement System
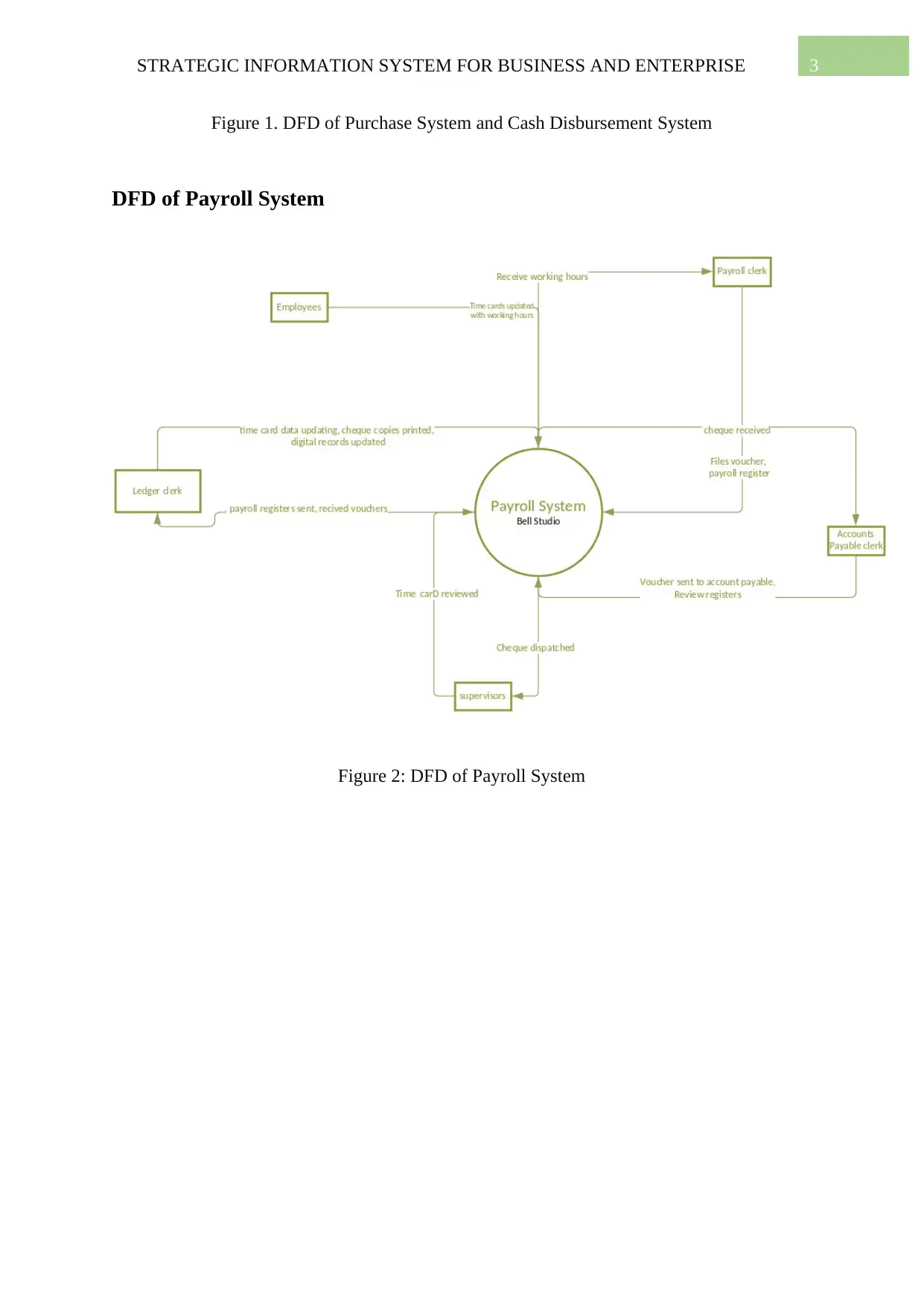
DFD of Payroll System
Figure 2: DFD of Payroll System
Figure 1. DFD of Purchase System and Cash Disbursement System
DFD of Payroll System
Figure 2: DFD of Payroll System
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
4STRATEGIC INFORMATION SYSTEM FOR BUSINESS AND ENTERPRISE
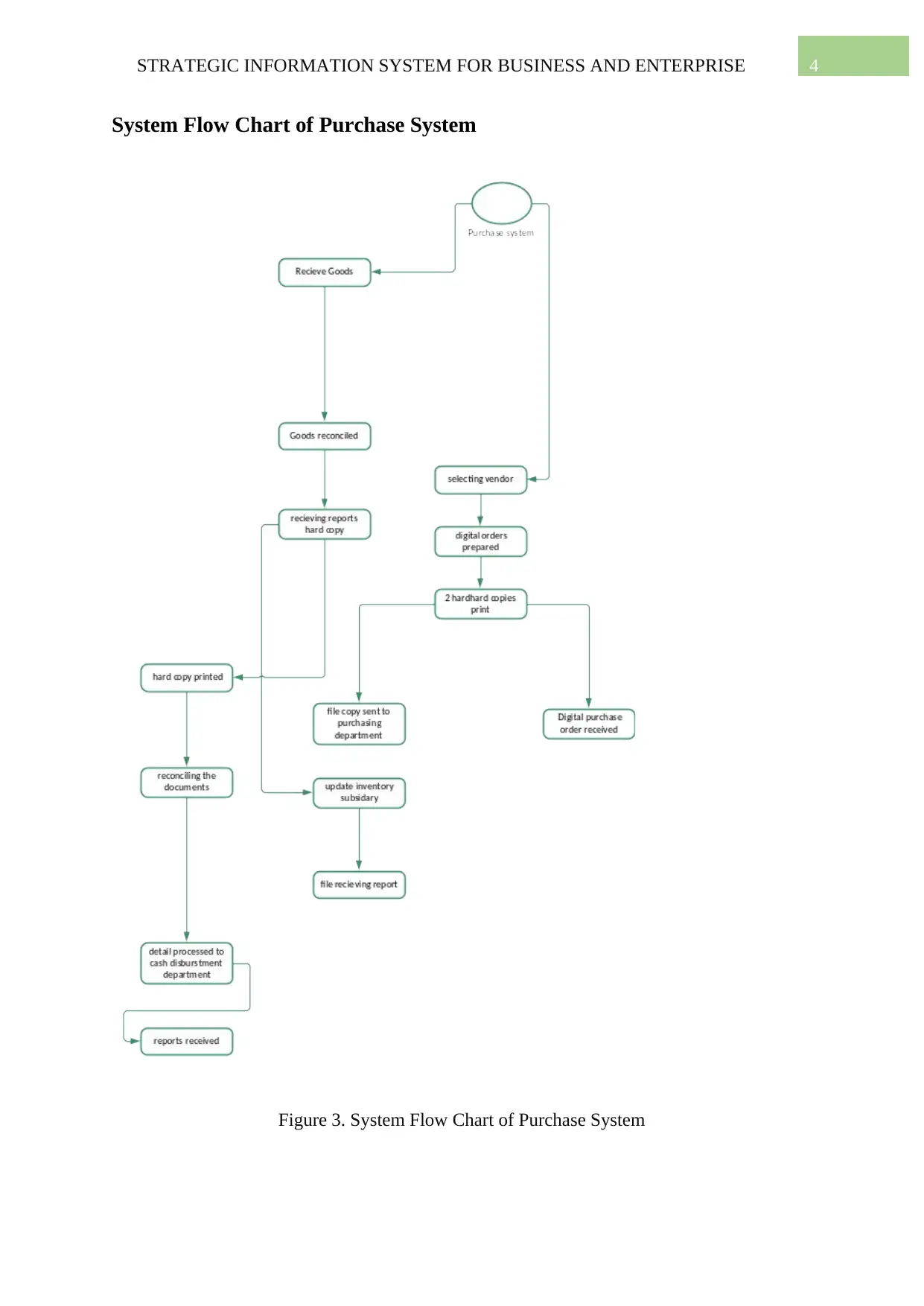
System Flow Chart of Purchase System
Figure 3. System Flow Chart of Purchase System
System Flow Chart of Purchase System
Figure 3. System Flow Chart of Purchase System
5STRATEGIC INFORMATION SYSTEM FOR BUSINESS AND ENTERPRISE
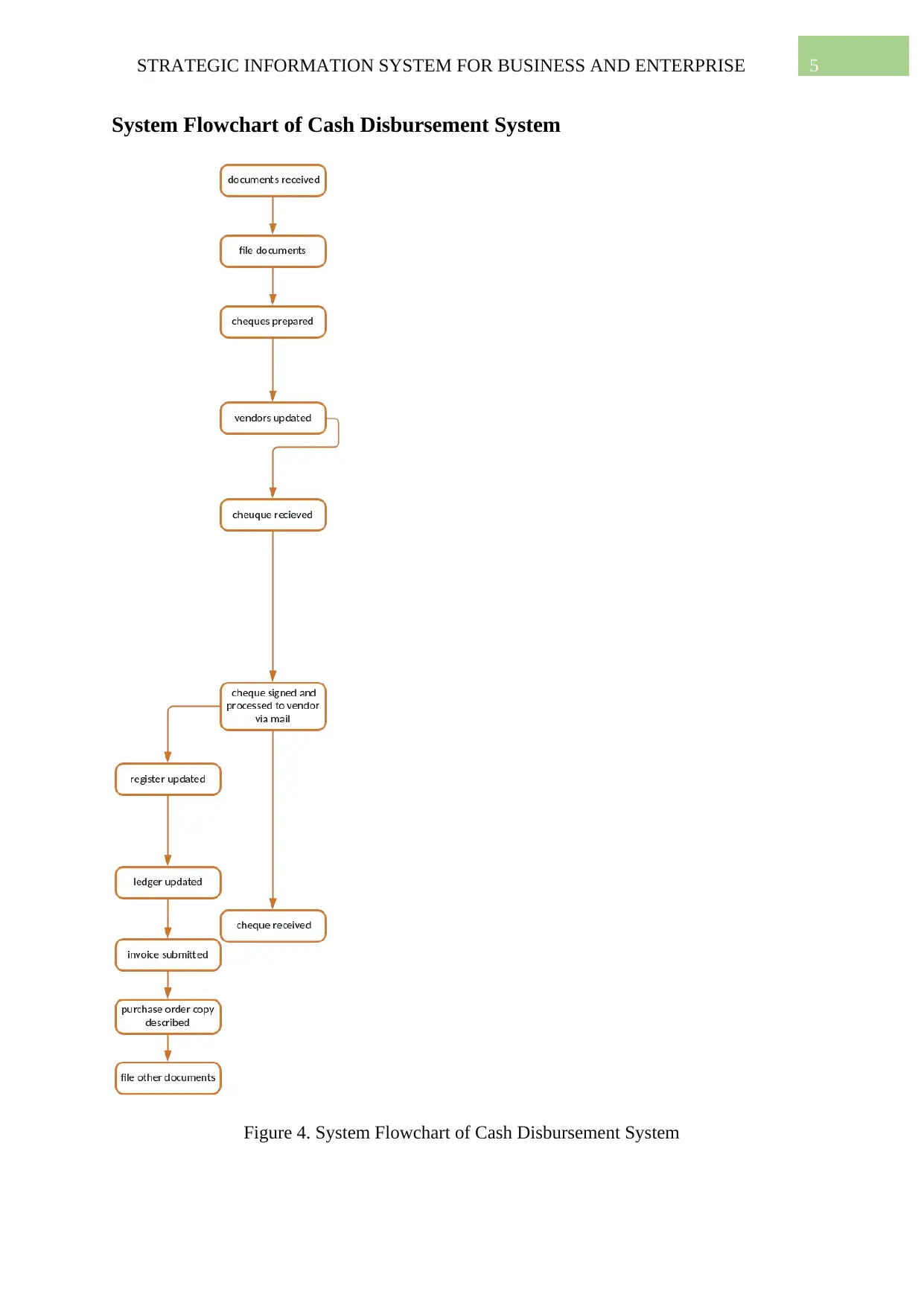
System Flowchart of Cash Disbursement System
Figure 4. System Flowchart of Cash Disbursement System
System Flowchart of Cash Disbursement System
Figure 4. System Flowchart of Cash Disbursement System
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

6STRATEGIC INFORMATION SYSTEM FOR BUSINESS AND ENTERPRISE
System Flowchart of Payroll System
System Flowchart of Payroll System
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
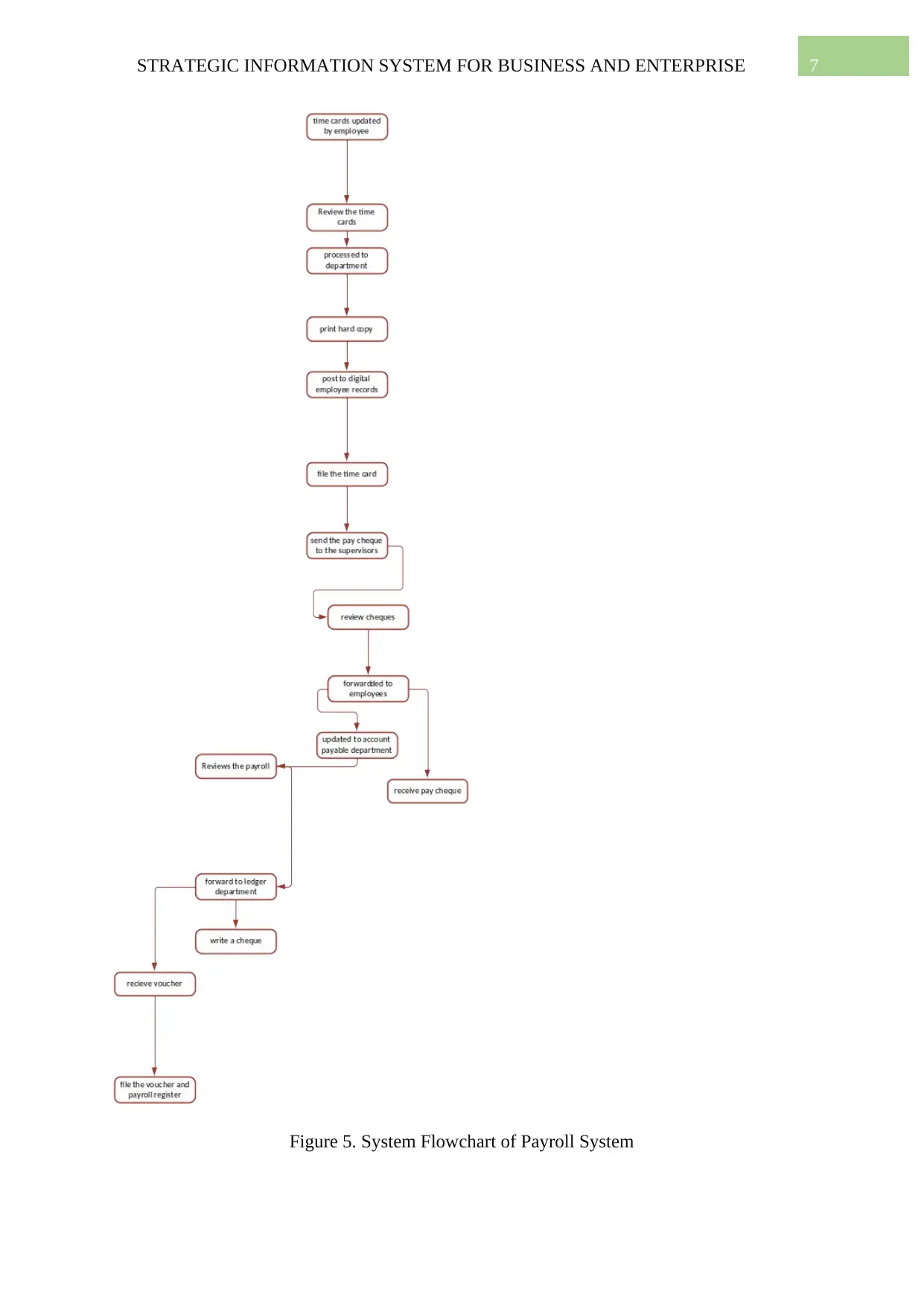
7STRATEGIC INFORMATION SYSTEM FOR BUSINESS AND ENTERPRISE
Figure 5. System Flowchart of Payroll System
Figure 5. System Flowchart of Payroll System

8STRATEGIC INFORMATION SYSTEM FOR BUSINESS AND ENTERPRISE
Description of the possible weaknesses in the internal structure of the
system and the risk connected to the weaknesses identified
Weaknesses prevailing in the Organization
Bell studios in their system have several weaknesses. There are weaknesses present in
the cash disbursement system of the company. The purchasing systems along with the payroll
system have vulnerabilities in them which can lead to the creation of threats and risks for the
organization (Gillett 2016). There is a possibility of the identified risk to pose great threat for
the organization and therefore the weaknesses require immediate attention. The systems
which has the potential weakness and the connected risks with them are discusses below.
The vulnerabilities in the network that can be the pathway for the cyber criminals to
disrupt the system must be checked thus protecting the system form the breaches. The
organization is liable to the attacks as it has not replaced the outdated software that is no
more effective in guarding the system from cyber attacks (Cassidy 2016). The outdated
system of the organization is not updated with software patches that make the system of the
organization vulnerable to external threats (DeLone and McLean 2016). The cash
disbursement system of the organization is a complex process and has high significance for
the organization (DeVan et al. 2015). Any improvisation in the process system can lead to
the opening of several vulnerabilities for attacks in the system. The cash disbursement system
of the organization contains valuable details of cash related objectives (Parento, Hynes and
Sahgal 2017). There can be disruption in the operations system of the cash disbursement
department if there are any changes implemented on it (Collins et al. 2016). The proper
management of the system might allow certain administrators to make a decision to delay the
updating process. Further the administrators can choose to segment the process. The
segmentation of the process can effectively prevent shutdown process or even process
Description of the possible weaknesses in the internal structure of the
system and the risk connected to the weaknesses identified
Weaknesses prevailing in the Organization
Bell studios in their system have several weaknesses. There are weaknesses present in
the cash disbursement system of the company. The purchasing systems along with the payroll
system have vulnerabilities in them which can lead to the creation of threats and risks for the
organization (Gillett 2016). There is a possibility of the identified risk to pose great threat for
the organization and therefore the weaknesses require immediate attention. The systems
which has the potential weakness and the connected risks with them are discusses below.
The vulnerabilities in the network that can be the pathway for the cyber criminals to
disrupt the system must be checked thus protecting the system form the breaches. The
organization is liable to the attacks as it has not replaced the outdated software that is no
more effective in guarding the system from cyber attacks (Cassidy 2016). The outdated
system of the organization is not updated with software patches that make the system of the
organization vulnerable to external threats (DeLone and McLean 2016). The cash
disbursement system of the organization is a complex process and has high significance for
the organization (DeVan et al. 2015). Any improvisation in the process system can lead to
the opening of several vulnerabilities for attacks in the system. The cash disbursement system
of the organization contains valuable details of cash related objectives (Parento, Hynes and
Sahgal 2017). There can be disruption in the operations system of the cash disbursement
department if there are any changes implemented on it (Collins et al. 2016). The proper
management of the system might allow certain administrators to make a decision to delay the
updating process. Further the administrators can choose to segment the process. The
segmentation of the process can effectively prevent shutdown process or even process
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

9STRATEGIC INFORMATION SYSTEM FOR BUSINESS AND ENTERPRISE
downtime. The gaps present in the system if lies undetected in the system of the organization
can cause severe damage to the process thus costing heavily for the organization (Peppard
and Ward 2016). Any gaps lying in the system for a long time becomes the vulnerable spot
for the attack.
The business organization has major weaknesses in the system process.
Numerous vulnerabilities jeopardize the security system of the company and thus increasing
its potential security risks. External threats can be of a serious concern for the organization.
The hard files of the organization contain sensitive information and confidential data
regarding the business dealings of the company. Any leakage of the data or misuse can put
the organization in a compromised position. The purchase and the payroll system of the
company hold important financial and confidential invoices of the company. The database
holds crucial information and invoices of the business dealing of the organization. The
storage location of the invoices is highly prone to the external attacks. The attacks can cause
damage to the company’s reputation and the brand value will suffer severely. Financial data
loss will highly damage the company. The vulnerabilities in the system make it easy for the
hackers to find a suitable path to launch attack on the system of the organization. The attacks
will get easy access to the company data and the invoices stored in the database (Marabelli,
and Galliers 2017). Modern technology has also improved the technique and the magnitude
of attacks. The attackers using modern method can easily cause high damage to the database
of the organization. The professional records that are stored in the company’s database are
prone to the external attacks and any failure in the implementation of security protocols can
lead to damage and exploiting of data. The organization can implement system security
strategies to avoid network breaches and external attacks. The organization should update the
security protocols to immediately identify redundant breaches in the system and take prompt
action against it.
downtime. The gaps present in the system if lies undetected in the system of the organization
can cause severe damage to the process thus costing heavily for the organization (Peppard
and Ward 2016). Any gaps lying in the system for a long time becomes the vulnerable spot
for the attack.
The business organization has major weaknesses in the system process.
Numerous vulnerabilities jeopardize the security system of the company and thus increasing
its potential security risks. External threats can be of a serious concern for the organization.
The hard files of the organization contain sensitive information and confidential data
regarding the business dealings of the company. Any leakage of the data or misuse can put
the organization in a compromised position. The purchase and the payroll system of the
company hold important financial and confidential invoices of the company. The database
holds crucial information and invoices of the business dealing of the organization. The
storage location of the invoices is highly prone to the external attacks. The attacks can cause
damage to the company’s reputation and the brand value will suffer severely. Financial data
loss will highly damage the company. The vulnerabilities in the system make it easy for the
hackers to find a suitable path to launch attack on the system of the organization. The attacks
will get easy access to the company data and the invoices stored in the database (Marabelli,
and Galliers 2017). Modern technology has also improved the technique and the magnitude
of attacks. The attackers using modern method can easily cause high damage to the database
of the organization. The professional records that are stored in the company’s database are
prone to the external attacks and any failure in the implementation of security protocols can
lead to damage and exploiting of data. The organization can implement system security
strategies to avoid network breaches and external attacks. The organization should update the
security protocols to immediately identify redundant breaches in the system and take prompt
action against it.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

10STRATEGIC INFORMATION SYSTEM FOR BUSINESS AND ENTERPRISE
The breaches happen due to the vulnerabilities present in the system of the
organization. The weak points are gate through which the attacks are launched into the
system. The outdated versions put the company in a position of major risk as the version has
lost its strength to avoid and prevent modern attacks (Morecroft 2015). The outdated system
can lead the company to face data theft or cyber attacks. The outdated system makes the data
of the company vulnerable to the cyber criminals who can destroy the data completely
(Kamariotou and Kitsios 2019). The cyber attackers can also modify the data to cause
problem in the organization’s financial records. Siphoning of data becomes easy as the data
in the system lies unprotected or unsecured. Data can easily be siphoned through the system.
The potential weaknesses have been discussed yet the company faces an additional
risks. This risk is from the employees of the company. Certain employees in the organization
can have the motive to take revenge on the company. The company performs network
diagnosis through the backdoor of the network system to understand the traffic flow of the
network channel. The employee can use the backdoor unethically to launch internal attacks in
the organization of the company. Such employees of the organization pose to be major risks
for the organization. The employees can deny to follow the security protocols of the
organization. The employees can mislead the procedures set by the organization. These are
the unconventional risks the organization starts facing from the employees.
Risks
Unauthorized access
Unauthorized access to the database of the system puts the organization in a
dangerous state. The company runs the risk to losing all its sensitive and confidential data.
The hackers can compromise the data of the organization leading to the mismanagement in
The breaches happen due to the vulnerabilities present in the system of the
organization. The weak points are gate through which the attacks are launched into the
system. The outdated versions put the company in a position of major risk as the version has
lost its strength to avoid and prevent modern attacks (Morecroft 2015). The outdated system
can lead the company to face data theft or cyber attacks. The outdated system makes the data
of the company vulnerable to the cyber criminals who can destroy the data completely
(Kamariotou and Kitsios 2019). The cyber attackers can also modify the data to cause
problem in the organization’s financial records. Siphoning of data becomes easy as the data
in the system lies unprotected or unsecured. Data can easily be siphoned through the system.
The potential weaknesses have been discussed yet the company faces an additional
risks. This risk is from the employees of the company. Certain employees in the organization
can have the motive to take revenge on the company. The company performs network
diagnosis through the backdoor of the network system to understand the traffic flow of the
network channel. The employee can use the backdoor unethically to launch internal attacks in
the organization of the company. Such employees of the organization pose to be major risks
for the organization. The employees can deny to follow the security protocols of the
organization. The employees can mislead the procedures set by the organization. These are
the unconventional risks the organization starts facing from the employees.
Risks
Unauthorized access
Unauthorized access to the database of the system puts the organization in a
dangerous state. The company runs the risk to losing all its sensitive and confidential data.
The hackers can compromise the data of the organization leading to the mismanagement in

11STRATEGIC INFORMATION SYSTEM FOR BUSINESS AND ENTERPRISE
the system. Recently the cyber criminals are using advance technologies to enter the system
of the organization. The hackers with acquired skills keep the attack unidentified in the
system for a long time and slowly collect information out of the system.
Malware
Organization face risk attacks from malware. Malware are programs so designed to
draw information from the system and stay undetected on the system for a long time. Viruses
are software devised to gain entrance into the network system of the organization. The
viruses can lie undetected in the system for a very long time and enters the system without
any permission from the administrator (Rajesh, Reddy and Reddy 2015). The virus on
entering the network system slowly spreads into the network system and channel of the
organization (Jingbing et al 2018). The virus on spreading into the length and breadth of the
channel, tamper the flow of the network traffic and continuously duplicates itself within the
system. The duplication crowds the network system and causes congestion in data flow
(Mousavi, Rad and Wah 2016). The system slows down and finally crashes. The crash leads
to the massive data loss. The damage sometime occurs due to program fault or can be
accidental.
The damages the company faces can be either purposeful attacks or accidental attacks.
The actions results from the thoughts of industrial sabotage. The employees in the company
hold and have access to numerous confidential company data and information. If these data
are used against the company or a matter of fact altered, the company will face immense
damage. The attackers get an upper hand as they already know the vulnerabilities in the
system. The identified vulnerabilities can be sued to attack the software and also cause
damage to the hardware of the company (White, Fisch and Pooch 2017). Data acquired can
the system. Recently the cyber criminals are using advance technologies to enter the system
of the organization. The hackers with acquired skills keep the attack unidentified in the
system for a long time and slowly collect information out of the system.
Malware
Organization face risk attacks from malware. Malware are programs so designed to
draw information from the system and stay undetected on the system for a long time. Viruses
are software devised to gain entrance into the network system of the organization. The
viruses can lie undetected in the system for a very long time and enters the system without
any permission from the administrator (Rajesh, Reddy and Reddy 2015). The virus on
entering the network system slowly spreads into the network system and channel of the
organization (Jingbing et al 2018). The virus on spreading into the length and breadth of the
channel, tamper the flow of the network traffic and continuously duplicates itself within the
system. The duplication crowds the network system and causes congestion in data flow
(Mousavi, Rad and Wah 2016). The system slows down and finally crashes. The crash leads
to the massive data loss. The damage sometime occurs due to program fault or can be
accidental.
The damages the company faces can be either purposeful attacks or accidental attacks.
The actions results from the thoughts of industrial sabotage. The employees in the company
hold and have access to numerous confidential company data and information. If these data
are used against the company or a matter of fact altered, the company will face immense
damage. The attackers get an upper hand as they already know the vulnerabilities in the
system. The identified vulnerabilities can be sued to attack the software and also cause
damage to the hardware of the company (White, Fisch and Pooch 2017). Data acquired can
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 17
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2025 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





