Network Design, IP Addressing, and Cloud for Bethseda Hospital
VerifiedAdded on 2022/11/17
|15
|3240
|6
Report
AI Summary
This report presents an IT infrastructure design for Bethseda Hospital, addressing the need for network upgrades and expansion to a new Sydney branch. It begins with an executive summary outlining the hospital's history and current IT challenges, including slow network speeds and security concerns. The paper's objectives include accommodating the new branch, recommending network security improvements, enhancing network speed and fault tolerance, and providing increased bandwidth. The geographical scope covers the hospital's locations in Melbourne and Sydney. The logical design proposes a hierarchical network design with core, distribution, and access layers. Justification for this design includes ease of design, traffic multiplexing, and security features. The report details an IP addressing scheme with subnetting to efficiently manage IP addresses and reduce broadcast traffic. It recommends Amazon as the preferred cloud provider, emphasizing its scalability, security, and HIPAA compliance. Techniques for supporting virtualization and cloud computing are discussed, along with dynamic scaling using cloud computing. The report concludes with a summary of the recommendations and references.

IT INFRASTRUCTURE 1
IT INFRASTUCTURE
By (Name)
(Course Title)
(Tutor’s Name)
(University Name)
(City)
(Date)
IT INFRASTUCTURE
By (Name)
(Course Title)
(Tutor’s Name)
(University Name)
(City)
(Date)
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

IT INFRASTRUCTURE 2
Table of Contents
Executive summary.........................................................................................................................2
Introduction......................................................................................................................................3
The project objectives..................................................................................................................4
Geographical scope..........................................................................................................................4
Logical design..................................................................................................................................5
Justification of hierarchical logical network design....................................................................7
IP addressing scheme and subnetting..............................................................................................8
Cloud providers.............................................................................................................................10
Techniques for supporting virtualization and cloud computing....................................................12
Dynamic scaling using cloud computing.......................................................................................13
Summary........................................................................................................................................14
References......................................................................................................................................15
Executive summary
Table of Contents
Executive summary.........................................................................................................................2
Introduction......................................................................................................................................3
The project objectives..................................................................................................................4
Geographical scope..........................................................................................................................4
Logical design..................................................................................................................................5
Justification of hierarchical logical network design....................................................................7
IP addressing scheme and subnetting..............................................................................................8
Cloud providers.............................................................................................................................10
Techniques for supporting virtualization and cloud computing....................................................12
Dynamic scaling using cloud computing.......................................................................................13
Summary........................................................................................................................................14
References......................................................................................................................................15
Executive summary

IT INFRASTRUCTURE 3
This paper will contain six sections. Specifically the paper will design a network for
Bethseda hospital in Australia. Bethseda is an independent hospital which is situated in Swan
River. The hospital began as a minor group of community-minded area residents who shared a
dream to create a big hospital in 1993. For 20 years, the hospital management has supported the
mission of the hospital to become one of the best hospitals in Australia. In 2013 the hospital, the
hospital celebrated 20 years of success. The hospital has used information technology to
implement its business operations. The hospital also has a website under the banner
bethseda.org.au. In addition, the hospital uses email services for each of staff member and with
more than one campus at different locations across Australia. Also, to support some of its
operations the organization has wireless network services within the hospital campuses, and
back-up servers to regularly backup its important documents and share files between its staff
members. The hospital wishes to open a new branch in one of the building located in Sydney city
Centre. The building has about eight floors where each floor has 30 rooms. As It specialist, this
paper will critically analyze the network design of Bethseda hospital and recommend the best
cloud providers that the organization can take advantage of.
Introduction
Bethseda is concerned in the elevation to its network systems. The present network
system support few specialized medical software tools and basic internet access. The network
users have complained about occasional downtime of the hospital network and the slow response
of the network especially at the peak access times. This has been brought about due to the
expansion of the network users. The hospital management would need to collect these issues
through network upgrade of their systems, but the hospital management is looking to increase
network security to be compliance with HIPPA standard and also improve productivity of its
This paper will contain six sections. Specifically the paper will design a network for
Bethseda hospital in Australia. Bethseda is an independent hospital which is situated in Swan
River. The hospital began as a minor group of community-minded area residents who shared a
dream to create a big hospital in 1993. For 20 years, the hospital management has supported the
mission of the hospital to become one of the best hospitals in Australia. In 2013 the hospital, the
hospital celebrated 20 years of success. The hospital has used information technology to
implement its business operations. The hospital also has a website under the banner
bethseda.org.au. In addition, the hospital uses email services for each of staff member and with
more than one campus at different locations across Australia. Also, to support some of its
operations the organization has wireless network services within the hospital campuses, and
back-up servers to regularly backup its important documents and share files between its staff
members. The hospital wishes to open a new branch in one of the building located in Sydney city
Centre. The building has about eight floors where each floor has 30 rooms. As It specialist, this
paper will critically analyze the network design of Bethseda hospital and recommend the best
cloud providers that the organization can take advantage of.
Introduction
Bethseda is concerned in the elevation to its network systems. The present network
system support few specialized medical software tools and basic internet access. The network
users have complained about occasional downtime of the hospital network and the slow response
of the network especially at the peak access times. This has been brought about due to the
expansion of the network users. The hospital management would need to collect these issues
through network upgrade of their systems, but the hospital management is looking to increase
network security to be compliance with HIPPA standard and also improve productivity of its
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

IT INFRASTRUCTURE 4
employees. This proposal will include significant changes in the logical network design. In
addition, to the changes in logical design, this paper also includes changes in the IP addressing
scheme. These changes will provide greater security and reliability for all the network users of
the organization network. Along with a new logical design, the new design will open door for the
hospital to explore new possibilities in using the network as well as increase the overall network
productivity. The solution provided by this paper will provide the greatest benefit for Bethseda
hospital that the management has have ever hand. The estimated cost for network upgrade is
estimated to be under 900,000 dollars which takes into account the current network issues.
The project objectives
The main objectives of this paper is to upgrade the network of Bethseda hospital so as to;
Accommodate the new Sydney branch
Recommend the best network security for the hospital
Improve the network speed and fault tolerance
Provide more bandwidth to the new Sydney location and more bandwidth to the remote
clinics (AM Fremont, 2013, p. 57).
Geographical scope
Bethseda is a medium-sized hospital which is located in Australia. Currently the hospital
have about five hundred staff members who supports up one thousand patients on daily basis. In
addition the hospital carries critical patients’ data in the organization servers and on mainframe
hosts. Currently the hospital has one main hospital at Melbourne, and about four clinics. The
main hospital located in Melbourne is located into a four floors. The hospital plans to expand its
operations in Sydney by building an eight floor building with about 30 rooms due to population
increase at the main hospital in Melbourne
employees. This proposal will include significant changes in the logical network design. In
addition, to the changes in logical design, this paper also includes changes in the IP addressing
scheme. These changes will provide greater security and reliability for all the network users of
the organization network. Along with a new logical design, the new design will open door for the
hospital to explore new possibilities in using the network as well as increase the overall network
productivity. The solution provided by this paper will provide the greatest benefit for Bethseda
hospital that the management has have ever hand. The estimated cost for network upgrade is
estimated to be under 900,000 dollars which takes into account the current network issues.
The project objectives
The main objectives of this paper is to upgrade the network of Bethseda hospital so as to;
Accommodate the new Sydney branch
Recommend the best network security for the hospital
Improve the network speed and fault tolerance
Provide more bandwidth to the new Sydney location and more bandwidth to the remote
clinics (AM Fremont, 2013, p. 57).
Geographical scope
Bethseda is a medium-sized hospital which is located in Australia. Currently the hospital
have about five hundred staff members who supports up one thousand patients on daily basis. In
addition the hospital carries critical patients’ data in the organization servers and on mainframe
hosts. Currently the hospital has one main hospital at Melbourne, and about four clinics. The
main hospital located in Melbourne is located into a four floors. The hospital plans to expand its
operations in Sydney by building an eight floor building with about 30 rooms due to population
increase at the main hospital in Melbourne
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

IT INFRASTRUCTURE 5
Logical design
The proposed logical design is a hierarchical design. This is a strategic design which is
implemented by service provides and enterprise as an efficient hardware management. One of
the reasons as to why this solution goes for a hierarchical logical design reduces workload on the
network devices. This is achieved by avoiding the hospital devices having to communicate with
other devices; it reduces the CPU adjacencies. It also minimizes on costs, facilitates changes
cheap and easy. It is also good for scalability and modularity. The main principle of this network
design is to implement and design a secure hospital network. Specifically this type of logical
design will categorize the hospital network into four layers which are the core layer, distribution,
access, and edge layers (Blanc & Cotton, 2017, p. 113).
The core layer is where switches and high-end routers are optimized for speed and
availability. On the other hand the distribution layer implement segment traffic and policies of
the organization. The access layer connected the organization users through switches, hubs and
other devices. A Hierarchical logical network design representation for the network is as shown
by the figure below
Figure 1: Hierarchical logical network design
Logical design
The proposed logical design is a hierarchical design. This is a strategic design which is
implemented by service provides and enterprise as an efficient hardware management. One of
the reasons as to why this solution goes for a hierarchical logical design reduces workload on the
network devices. This is achieved by avoiding the hospital devices having to communicate with
other devices; it reduces the CPU adjacencies. It also minimizes on costs, facilitates changes
cheap and easy. It is also good for scalability and modularity. The main principle of this network
design is to implement and design a secure hospital network. Specifically this type of logical
design will categorize the hospital network into four layers which are the core layer, distribution,
access, and edge layers (Blanc & Cotton, 2017, p. 113).
The core layer is where switches and high-end routers are optimized for speed and
availability. On the other hand the distribution layer implement segment traffic and policies of
the organization. The access layer connected the organization users through switches, hubs and
other devices. A Hierarchical logical network design representation for the network is as shown
by the figure below
Figure 1: Hierarchical logical network design
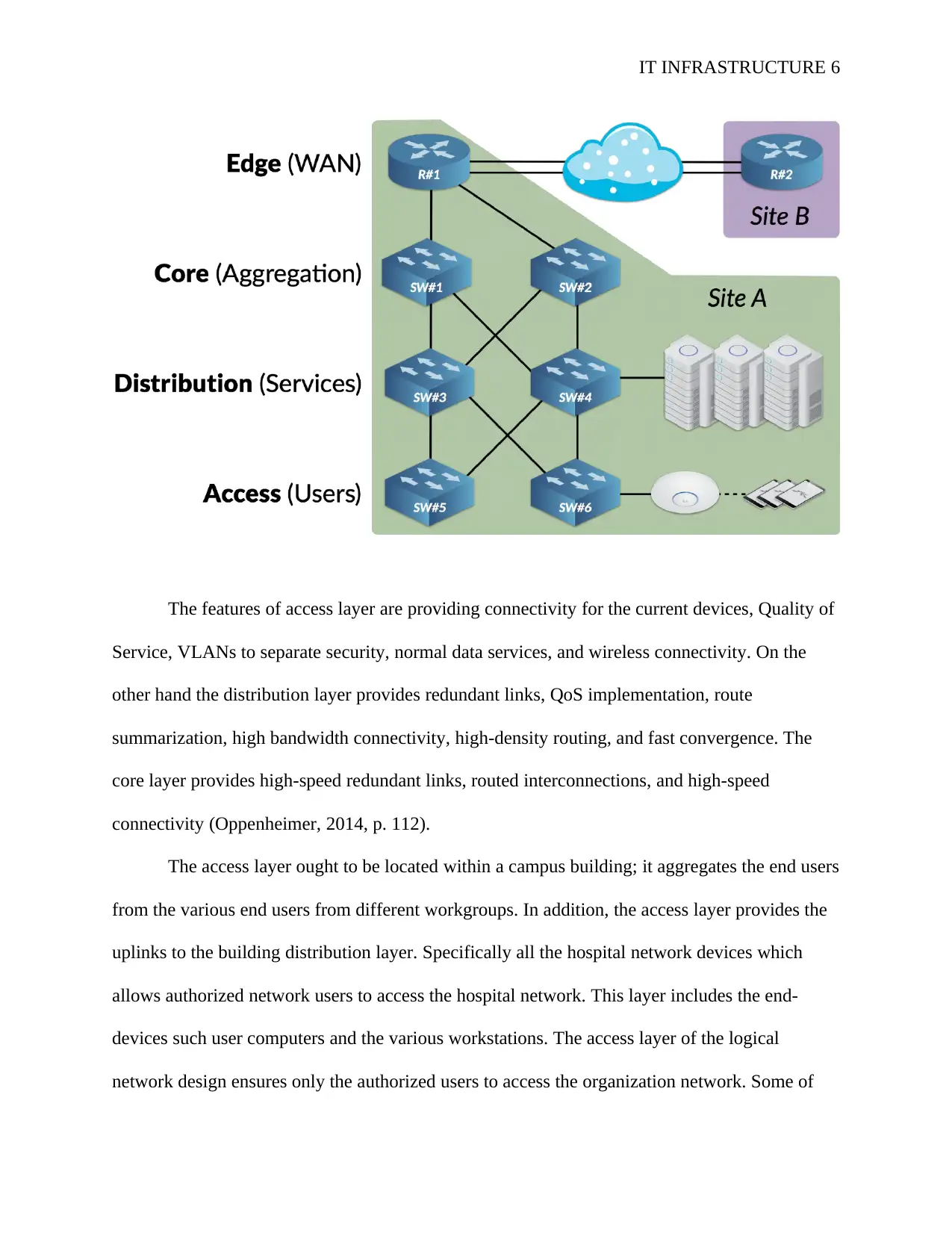
IT INFRASTRUCTURE 6
The features of access layer are providing connectivity for the current devices, Quality of
Service, VLANs to separate security, normal data services, and wireless connectivity. On the
other hand the distribution layer provides redundant links, QoS implementation, route
summarization, high bandwidth connectivity, high-density routing, and fast convergence. The
core layer provides high-speed redundant links, routed interconnections, and high-speed
connectivity (Oppenheimer, 2014, p. 112).
The access layer ought to be located within a campus building; it aggregates the end users
from the various end users from different workgroups. In addition, the access layer provides the
uplinks to the building distribution layer. Specifically all the hospital network devices which
allows authorized network users to access the hospital network. This layer includes the end-
devices such user computers and the various workstations. The access layer of the logical
network design ensures only the authorized users to access the organization network. Some of
The features of access layer are providing connectivity for the current devices, Quality of
Service, VLANs to separate security, normal data services, and wireless connectivity. On the
other hand the distribution layer provides redundant links, QoS implementation, route
summarization, high bandwidth connectivity, high-density routing, and fast convergence. The
core layer provides high-speed redundant links, routed interconnections, and high-speed
connectivity (Oppenheimer, 2014, p. 112).
The access layer ought to be located within a campus building; it aggregates the end users
from the various end users from different workgroups. In addition, the access layer provides the
uplinks to the building distribution layer. Specifically all the hospital network devices which
allows authorized network users to access the hospital network. This layer includes the end-
devices such user computers and the various workstations. The access layer of the logical
network design ensures only the authorized users to access the organization network. Some of
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

IT INFRASTRUCTURE 7
the services provided in this layer are IP multicast, broadcast suppression, network access, and
protocol filtering (Kurose & Ross, 2018, p. 59).
The distribution layer of the logical network design is used to provide access between the
core and workgroups. Specifically this layer is used to provide routing and controlling access to
services by implementing access lists and filters. This layer also provides redundant links and
switches to both the access and the hospital backbone. The core layer is specifically used to
provide high speed data connection between the data server, the edge distribution, and access
layer.
Justification of hierarchical logical network design
One of the reasons as to why Bethseda needs to implement hierarchical logical design is
the ease of design. In addition, the logical design has the ability to perform traffic multiplexing,
which means that multiple users in the hospital network has the ability to communicate and send
message over the same network cables and devices. Usually a hierarchical logical network
design starts with very little multiplexing to dense traffic multiplexing. Lastly, this type of
logical design is secure, it usually allow fine-tuned access control lists, blocking of unwanted
traffic and reshaping network traffic (Calahan, 2014, p. 112).
Components used to be used to support internet connectivity
Edge routers: This devices are used to provide basic filtering
Firewalls: This device is used to provide stateful filtering of network traffic and also
forwarding of VPN traffic
SMTP mail servers: This are used to act as relay between the intranet and internet mail
servers
the services provided in this layer are IP multicast, broadcast suppression, network access, and
protocol filtering (Kurose & Ross, 2018, p. 59).
The distribution layer of the logical network design is used to provide access between the
core and workgroups. Specifically this layer is used to provide routing and controlling access to
services by implementing access lists and filters. This layer also provides redundant links and
switches to both the access and the hospital backbone. The core layer is specifically used to
provide high speed data connection between the data server, the edge distribution, and access
layer.
Justification of hierarchical logical network design
One of the reasons as to why Bethseda needs to implement hierarchical logical design is
the ease of design. In addition, the logical design has the ability to perform traffic multiplexing,
which means that multiple users in the hospital network has the ability to communicate and send
message over the same network cables and devices. Usually a hierarchical logical network
design starts with very little multiplexing to dense traffic multiplexing. Lastly, this type of
logical design is secure, it usually allow fine-tuned access control lists, blocking of unwanted
traffic and reshaping network traffic (Calahan, 2014, p. 112).
Components used to be used to support internet connectivity
Edge routers: This devices are used to provide basic filtering
Firewalls: This device is used to provide stateful filtering of network traffic and also
forwarding of VPN traffic
SMTP mail servers: This are used to act as relay between the intranet and internet mail
servers
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

IT INFRASTRUCTURE 8
Public servers: The severs here will be used to provide public inf0ormation about the
hospital
DMZ servers: This is used to prevent the outside users from getting access to the hospital
data
DNS servers: This will be used to relay internal DNS requests to the wide area network
(Pkohriyal, 2016, p. 89)
IP addressing scheme and sub-netting
An Internet Protocol is used to identify any device on an IP network. Specifically an IP
address contains about 32 binary bits. When determining IP address for an organization is very
important to first determine the subnet size, compute subnet mask, and computer IP address.
Sub-netting is said to be the process of dividing the organization network into several smaller
networks. This means that within a subnet, one physical network can be divided onto various
logical units. Some of the reasons as this paper needs to use subnets is to efficiently use IP
addresses, reduce the number of collisions, reduce the broadcasting traffic, reducing the cost of
paying public IP and ISP, implementing a network structure, and reducing broadcasting traffic.
Table one shows while table two shows the subletting requirements a CIDR notation of the
Sydney office (Graham, 2017, p. 176)
Table 1: Sub-netting requirements
Floor The maximum required number of
hosts
1st 200 hosts
2nd 100 hosts
3rd 150 hosts
Public servers: The severs here will be used to provide public inf0ormation about the
hospital
DMZ servers: This is used to prevent the outside users from getting access to the hospital
data
DNS servers: This will be used to relay internal DNS requests to the wide area network
(Pkohriyal, 2016, p. 89)
IP addressing scheme and sub-netting
An Internet Protocol is used to identify any device on an IP network. Specifically an IP
address contains about 32 binary bits. When determining IP address for an organization is very
important to first determine the subnet size, compute subnet mask, and computer IP address.
Sub-netting is said to be the process of dividing the organization network into several smaller
networks. This means that within a subnet, one physical network can be divided onto various
logical units. Some of the reasons as this paper needs to use subnets is to efficiently use IP
addresses, reduce the number of collisions, reduce the broadcasting traffic, reducing the cost of
paying public IP and ISP, implementing a network structure, and reducing broadcasting traffic.
Table one shows while table two shows the subletting requirements a CIDR notation of the
Sydney office (Graham, 2017, p. 176)
Table 1: Sub-netting requirements
Floor The maximum required number of
hosts
1st 200 hosts
2nd 100 hosts
3rd 150 hosts
IT INFRASTRUCTURE 9
4th 180 hosts
5th 200 hosts
6th 150 hosts
7th 200 hosts
8th 100 hosts
Table 2: Proposed CIDR notation
Site Name Usable host
range
Broadcast
address
Subnet Mask Usable
Hosts
Maximum
number of
hosts
1st Floor 192.168.1.1-
192.168.1.254
192.168.1.255 255.255.255.0 254 256
2nd Floor 192.168.2.1-
192.168.2.254
192.168.2.255 255.255.255.0 254 256
3rd Floor 192.168.3.1-
192.168.3.254
192.168.3.255 255.255.255.0 254 256
4th Floor 192.168.4.1-
192.168.4.254
192.168.4.255 255.255.255.0 254 256
4th 180 hosts
5th 200 hosts
6th 150 hosts
7th 200 hosts
8th 100 hosts
Table 2: Proposed CIDR notation
Site Name Usable host
range
Broadcast
address
Subnet Mask Usable
Hosts
Maximum
number of
hosts
1st Floor 192.168.1.1-
192.168.1.254
192.168.1.255 255.255.255.0 254 256
2nd Floor 192.168.2.1-
192.168.2.254
192.168.2.255 255.255.255.0 254 256
3rd Floor 192.168.3.1-
192.168.3.254
192.168.3.255 255.255.255.0 254 256
4th Floor 192.168.4.1-
192.168.4.254
192.168.4.255 255.255.255.0 254 256
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
IT INFRASTRUCTURE 10
5th Floor 192.168.5.1-
192.168.5.254
192.168.5.255 255.255.255.0 254 256
6th Floor 192.168.6.1-
192.168.6.254
192.168.6.255 255.255.255.0 254 256
7th Floor 192.168.7.1-
192.168.7.254
192.168.7.255 255.255.255.0 254 256
8th Floor 192.168.8.1-
192.168.8.254
192.168.8.255 255.255.255.0 254 256
Cloud providers
Most of the organizations are taking advantage of cloud computing; it is the current
technology. Cloud computing is defined as the on-demand availability of computer system
resources especially computing power, data storage and active management by the computer
users. The term cloud computing is used to describe the current data centers which are available
to the many users over the wide area network. Some of the reasons as to why the hospital needs
to move some of the services to cloud are;
The hospital needs to reduce on operational costs while at the same time increasing on
the effectiveness of IT processes
Patients and network users requires fast application implementation and deployment
Some of the hospital applications are experiencing an increased traffic due to the
increased number of organization uses and therefore it is becoming very difficult to scale
resources to meet the hospital increasing demand
5th Floor 192.168.5.1-
192.168.5.254
192.168.5.255 255.255.255.0 254 256
6th Floor 192.168.6.1-
192.168.6.254
192.168.6.255 255.255.255.0 254 256
7th Floor 192.168.7.1-
192.168.7.254
192.168.7.255 255.255.255.0 254 256
8th Floor 192.168.8.1-
192.168.8.254
192.168.8.255 255.255.255.0 254 256
Cloud providers
Most of the organizations are taking advantage of cloud computing; it is the current
technology. Cloud computing is defined as the on-demand availability of computer system
resources especially computing power, data storage and active management by the computer
users. The term cloud computing is used to describe the current data centers which are available
to the many users over the wide area network. Some of the reasons as to why the hospital needs
to move some of the services to cloud are;
The hospital needs to reduce on operational costs while at the same time increasing on
the effectiveness of IT processes
Patients and network users requires fast application implementation and deployment
Some of the hospital applications are experiencing an increased traffic due to the
increased number of organization uses and therefore it is becoming very difficult to scale
resources to meet the hospital increasing demand
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

IT INFRASTRUCTURE 11
Due to the increased in number of remote clinics it means that the hospital ought to
establish a disaster recovery system
Also there is a need to expand the hospital geographically
It is becoming more difficult to keep on the growing storage needs (Bowen, et al., 2017,
p. 113)
Major reasons as to Why Bethseda needs to move some of its services to cloud
The data or application they store and retrieves sensitive data
The current set-up is meeting the hospital needs and does not demand much maintenance,
availability, and scaling up
The major benefits of using cloud providers comes from economies of scale and efficiency.
Currently, there are various cloud providers such as Google, IBM, SAP, Microsoft, salesforce,
and Amazon but for Bethseda hospital they need to deploy Amazon cloud providers. Example
the hospital use Amazon to host the hospital website. In addition, cloud security at Amazon is its
highest priority. As an amazon customer, an organization benefit from a network architecture
and a data center which is built to meet the organization requirements of one of the most
security-sensitive organizations. In addition, Amazon will allow the hospital to scale and
innovate, while at the same time maintaining a secure environment. The hospital will only pay
for the services that they will use without upfront expenses like with other cloud providers
(Srinivasan, 2014, p. 56).
Since security is one of the important aspect within the hospital, Amazon will ensure that the
hospital data is safe; thus makes the hospital HIPAA compliance. In here the amazon
infrastructure puts very string safeguards in place so as to protect the safety of the hospital data.
All the data in Amazon is stored in a highly secure AWS data centers. Second Amazon meets the
Due to the increased in number of remote clinics it means that the hospital ought to
establish a disaster recovery system
Also there is a need to expand the hospital geographically
It is becoming more difficult to keep on the growing storage needs (Bowen, et al., 2017,
p. 113)
Major reasons as to Why Bethseda needs to move some of its services to cloud
The data or application they store and retrieves sensitive data
The current set-up is meeting the hospital needs and does not demand much maintenance,
availability, and scaling up
The major benefits of using cloud providers comes from economies of scale and efficiency.
Currently, there are various cloud providers such as Google, IBM, SAP, Microsoft, salesforce,
and Amazon but for Bethseda hospital they need to deploy Amazon cloud providers. Example
the hospital use Amazon to host the hospital website. In addition, cloud security at Amazon is its
highest priority. As an amazon customer, an organization benefit from a network architecture
and a data center which is built to meet the organization requirements of one of the most
security-sensitive organizations. In addition, Amazon will allow the hospital to scale and
innovate, while at the same time maintaining a secure environment. The hospital will only pay
for the services that they will use without upfront expenses like with other cloud providers
(Srinivasan, 2014, p. 56).
Since security is one of the important aspect within the hospital, Amazon will ensure that the
hospital data is safe; thus makes the hospital HIPAA compliance. In here the amazon
infrastructure puts very string safeguards in place so as to protect the safety of the hospital data.
All the data in Amazon is stored in a highly secure AWS data centers. Second Amazon meets the

IT INFRASTRUCTURE 12
compliance requirements; this means that the HIPPA requirements have already been completed
at Amazon. Third security scale quickly at Amazon and also cuts costs.
Other benefits for the hospital customers for moving to Amazon cloud providers
Amazon offers added advantage such office 365; these means that some of the hospital services
will be accesses anywhere so long as the client is connected to the wide area network, Seamless,
team collaboration, threat intelligence, flexible plans, mobile device management, and automatic
and regular updates (Mosco, 2018, p. 134).
Techniques for supporting virtualization and cloud computing
Virtualization in cloud computing is the creation of virtual servers, computing resources,
devices, and infrastructure. It changes the software and hardware relations and it is one of the
foundation elements which is found in cloud computing. The aspect assists in utilizing cloud
computing capabilities to its fullest. The virtualization aspect in cloud describes delivery of
shared computing resources, on-demand services, and SaaS. There various techniques of
virtualization and cloud computing that an organization such as Bethseda hospital can take
advantage of; one of the techniques is network virtualization. This methodology of combining
the available resources in an organization network by splitting the available bandwidth into
various channels where each channel is separated and distinguished. Another aspect is storage
virtualization, this method gives the users that ability to pool the hardware storage space from
various interconnected storage devices into a simulated singe storage. This technique is
commonly utilized in those networks that supports storage area network. The hospital
management can implement this method with its software applications or by employing software
and hardware hybrid appliances. Desktop virtualization technique will enable the hospital
emulate a workstation load rather than the organization server. This in turn will allow the user
compliance requirements; this means that the HIPPA requirements have already been completed
at Amazon. Third security scale quickly at Amazon and also cuts costs.
Other benefits for the hospital customers for moving to Amazon cloud providers
Amazon offers added advantage such office 365; these means that some of the hospital services
will be accesses anywhere so long as the client is connected to the wide area network, Seamless,
team collaboration, threat intelligence, flexible plans, mobile device management, and automatic
and regular updates (Mosco, 2018, p. 134).
Techniques for supporting virtualization and cloud computing
Virtualization in cloud computing is the creation of virtual servers, computing resources,
devices, and infrastructure. It changes the software and hardware relations and it is one of the
foundation elements which is found in cloud computing. The aspect assists in utilizing cloud
computing capabilities to its fullest. The virtualization aspect in cloud describes delivery of
shared computing resources, on-demand services, and SaaS. There various techniques of
virtualization and cloud computing that an organization such as Bethseda hospital can take
advantage of; one of the techniques is network virtualization. This methodology of combining
the available resources in an organization network by splitting the available bandwidth into
various channels where each channel is separated and distinguished. Another aspect is storage
virtualization, this method gives the users that ability to pool the hardware storage space from
various interconnected storage devices into a simulated singe storage. This technique is
commonly utilized in those networks that supports storage area network. The hospital
management can implement this method with its software applications or by employing software
and hardware hybrid appliances. Desktop virtualization technique will enable the hospital
emulate a workstation load rather than the organization server. This in turn will allow the user
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 15
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





