Case Study Solution: Designing a Network for Big Bucks Coffee
VerifiedAdded on 2022/10/17
|8
|1016
|9
Case Study
AI Summary
This case study provides a comprehensive network design solution for Big Bucks Coffee, addressing the requirements of a growing coffee shop business. The design includes a detailed analysis of hardware and software components such as centralized servers, HP desktops, CAT six cables, wireless routers, and network printers. The document highlights the use of Comodo firewall for security and Packet Tracer for virtual network design. The network topology is based on a tree structure for efficient linking and configuration. It also specifies the number of computers, printers, Ethernet cables, repeaters, trucking pipes, and UPS units. The logical and physical design of the network is described, including server installation, domain layout, and security considerations to protect sensitive information. References are provided for further reading.

Running Head: Network Design 1
Network Design
Name
Institution Affiliation
Network Design
Name
Institution Affiliation
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Network Design 2
Q1
Hardware required.
The following networking equipment were used to do the networking in the below Big
Bucks coffee network layout.
Centralized server (Client) was used to allow users access the resources that they are
looking for during their working hours and is located at the main entrance of the building,
HP desktops found at the office to help the users access the internet.
CAT six cables running from the server to the desktops, wireless routers have been also
used to distribute wireless network and is mounted at the top of the sealing near kids’ area, green
wall and in the office itself.
There are also several printers (network) that are located on the office to enable the users
print their documents whenever they are because they are on the network.
Software needed in the implementation of the network.
Firewall. This is used to ensure that the network is secure, and the users of the network
can be attacked by the atacker outside and keeps the network secure. Comodo firewall was used
in the design of the Big Bucks coffee network.
Packet tracer. This is used to design the virtual Big Bucks coffee network for easy
implementation when it comes to the site. This makes the work of the network engineers easier
because they just follow what they did with this software.
Q1
Hardware required.
The following networking equipment were used to do the networking in the below Big
Bucks coffee network layout.
Centralized server (Client) was used to allow users access the resources that they are
looking for during their working hours and is located at the main entrance of the building,
HP desktops found at the office to help the users access the internet.
CAT six cables running from the server to the desktops, wireless routers have been also
used to distribute wireless network and is mounted at the top of the sealing near kids’ area, green
wall and in the office itself.
There are also several printers (network) that are located on the office to enable the users
print their documents whenever they are because they are on the network.
Software needed in the implementation of the network.
Firewall. This is used to ensure that the network is secure, and the users of the network
can be attacked by the atacker outside and keeps the network secure. Comodo firewall was used
in the design of the Big Bucks coffee network.
Packet tracer. This is used to design the virtual Big Bucks coffee network for easy
implementation when it comes to the site. This makes the work of the network engineers easier
because they just follow what they did with this software.
Network Design 3
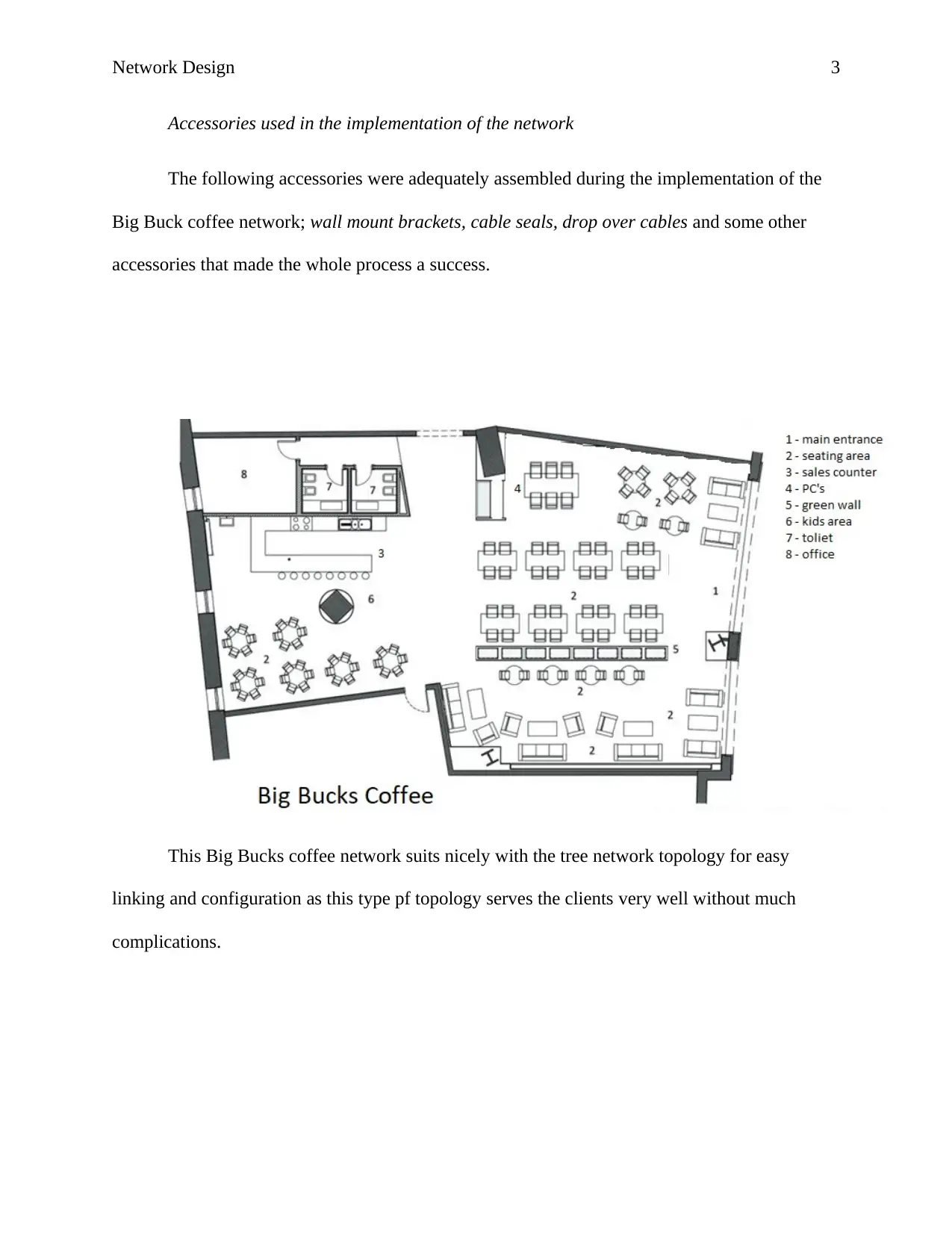
Accessories used in the implementation of the network
The following accessories were adequately assembled during the implementation of the
Big Buck coffee network; wall mount brackets, cable seals, drop over cables and some other
accessories that made the whole process a success.
This Big Bucks coffee network suits nicely with the tree network topology for easy
linking and configuration as this type pf topology serves the clients very well without much
complications.
Accessories used in the implementation of the network
The following accessories were adequately assembled during the implementation of the
Big Buck coffee network; wall mount brackets, cable seals, drop over cables and some other
accessories that made the whole process a success.
This Big Bucks coffee network suits nicely with the tree network topology for easy
linking and configuration as this type pf topology serves the clients very well without much
complications.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

Network Design 4
Q2
Computers are preferably the Hewlett Packard (HP) type because they are considerably
cheap and are durable. They are standalone computers. Since the coffee shop will increasable be
growing,50 computers are enough for the offices including the two to still be added and some to
be efficient in case backup is needed and replacements. Printers are 6 to make then enough for
each office have one
Ethernet cables are used for the connection of computers to the switches for access to the
internet. The stated quantity is enough and can have some to be used in future whenever there is
a damage or replacement.
Repeaters these are network devices that are used to amplify the network frequencies and
data packages over a network. There hence are suitable in the institution such as this coffee shop
because it has various offices in different locations where cables cannot be laid down to get
connected on the other sides.
Trucking pipes are used in laying cables to make sure the layout is presentable and no
cables running up and down with poor arrangements. Mostly are mounted on walls to cover the
running cables.
Universal power supply. These are used for power support when there a black out. The
power supplies help the users in the network save their work when there is no power. They
produce a certain sound to alert the user of power loss for him or her save the work.
Mouse and keyboards are used together with the computers available over the network.
They help the user request a resource or information on the network by inserting the expected
inputs. They are very important on the network though may be neglected.
Q2
Computers are preferably the Hewlett Packard (HP) type because they are considerably
cheap and are durable. They are standalone computers. Since the coffee shop will increasable be
growing,50 computers are enough for the offices including the two to still be added and some to
be efficient in case backup is needed and replacements. Printers are 6 to make then enough for
each office have one
Ethernet cables are used for the connection of computers to the switches for access to the
internet. The stated quantity is enough and can have some to be used in future whenever there is
a damage or replacement.
Repeaters these are network devices that are used to amplify the network frequencies and
data packages over a network. There hence are suitable in the institution such as this coffee shop
because it has various offices in different locations where cables cannot be laid down to get
connected on the other sides.
Trucking pipes are used in laying cables to make sure the layout is presentable and no
cables running up and down with poor arrangements. Mostly are mounted on walls to cover the
running cables.
Universal power supply. These are used for power support when there a black out. The
power supplies help the users in the network save their work when there is no power. They
produce a certain sound to alert the user of power loss for him or her save the work.
Mouse and keyboards are used together with the computers available over the network.
They help the user request a resource or information on the network by inserting the expected
inputs. They are very important on the network though may be neglected.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
Network Design 5
Q3
All these components are used to create the whole network as listed in the requirements
to ensure full functionating and operation of the network.
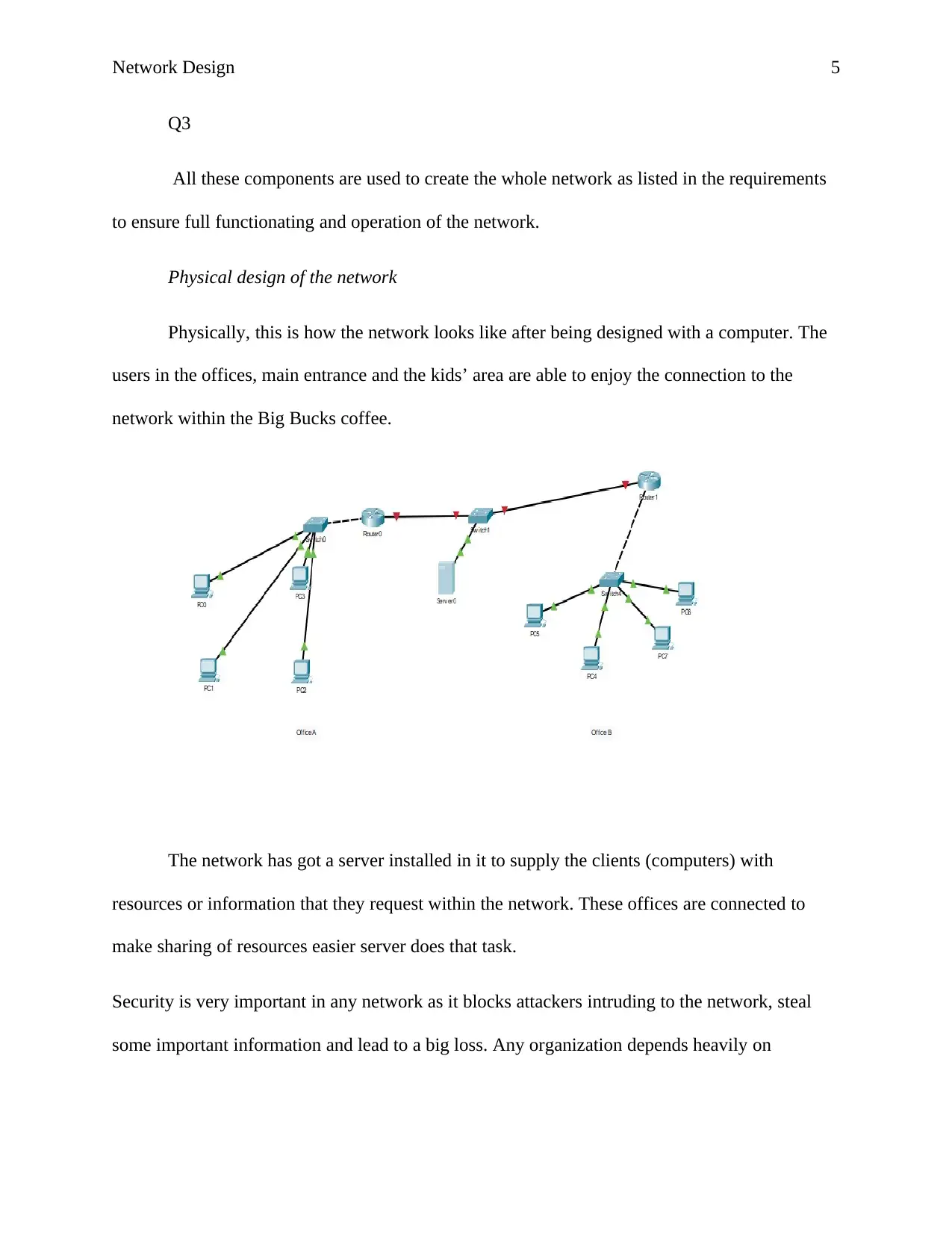
Physical design of the network
Physically, this is how the network looks like after being designed with a computer. The
users in the offices, main entrance and the kids’ area are able to enjoy the connection to the
network within the Big Bucks coffee.
The network has got a server installed in it to supply the clients (computers) with
resources or information that they request within the network. These offices are connected to
make sharing of resources easier server does that task.
Security is very important in any network as it blocks attackers intruding to the network, steal
some important information and lead to a big loss. Any organization depends heavily on
Q3
All these components are used to create the whole network as listed in the requirements
to ensure full functionating and operation of the network.
Physical design of the network
Physically, this is how the network looks like after being designed with a computer. The
users in the offices, main entrance and the kids’ area are able to enjoy the connection to the
network within the Big Bucks coffee.
The network has got a server installed in it to supply the clients (computers) with
resources or information that they request within the network. These offices are connected to
make sharing of resources easier server does that task.
Security is very important in any network as it blocks attackers intruding to the network, steal
some important information and lead to a big loss. Any organization depends heavily on
Network Design 6
information and once stolen any damage can be done so security must be catered in every
network.
Logical design of the network
Server installation
Server is the main supply supply of informatio in this nertwork. The users just send their
request via a browser and the server responses if the requested information is available. These
are the equipment used in the installation of the server being used in the network; a computer,
network router, a keyboard, monitor and broadband network connection.
information and once stolen any damage can be done so security must be catered in every
network.
Logical design of the network
Server installation
Server is the main supply supply of informatio in this nertwork. The users just send their
request via a browser and the server responses if the requested information is available. These
are the equipment used in the installation of the server being used in the network; a computer,
network router, a keyboard, monitor and broadband network connection.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
Network Design 7
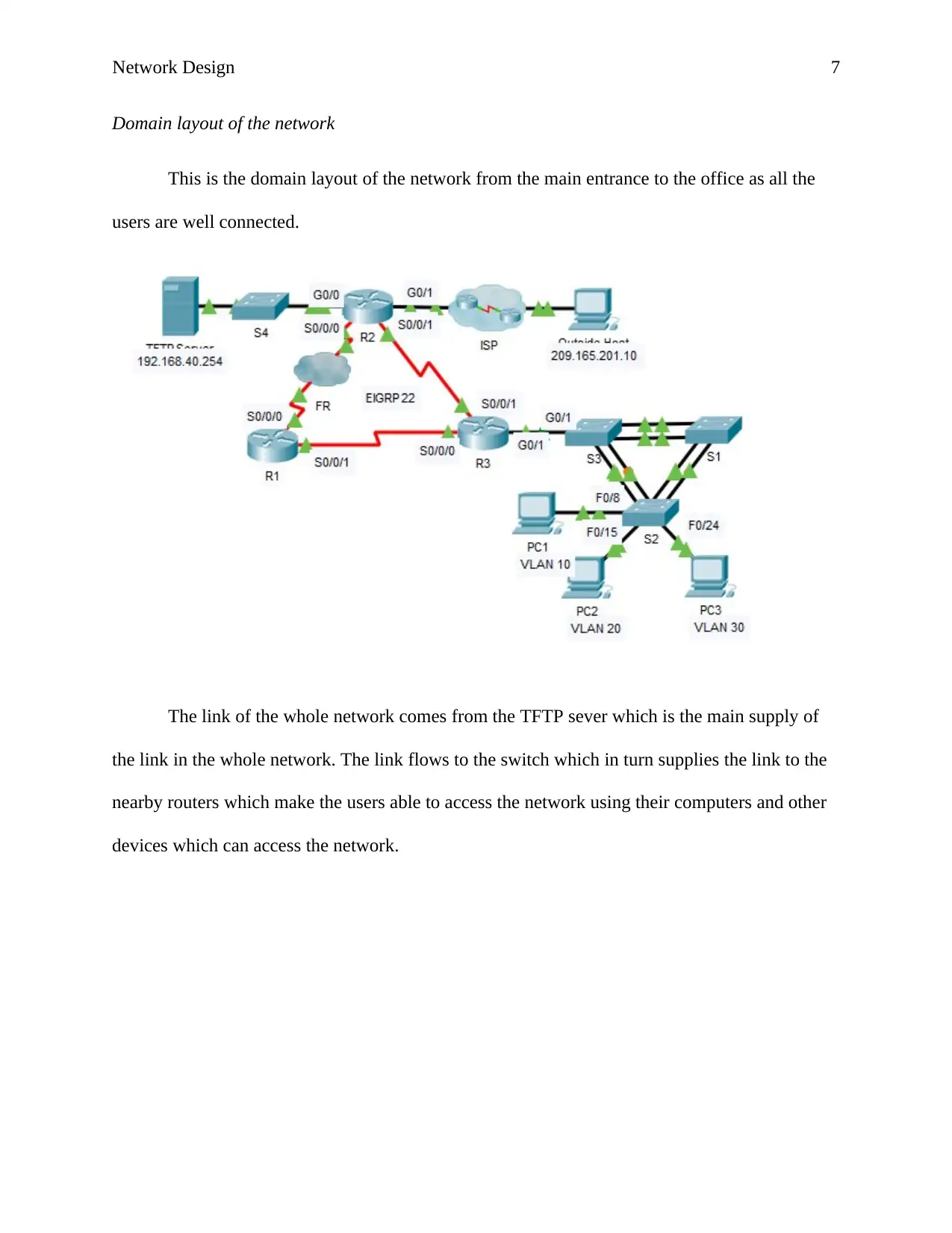
Domain layout of the network
This is the domain layout of the network from the main entrance to the office as all the
users are well connected.
The link of the whole network comes from the TFTP sever which is the main supply of
the link in the whole network. The link flows to the switch which in turn supplies the link to the
nearby routers which make the users able to access the network using their computers and other
devices which can access the network.
Domain layout of the network
This is the domain layout of the network from the main entrance to the office as all the
users are well connected.
The link of the whole network comes from the TFTP sever which is the main supply of
the link in the whole network. The link flows to the switch which in turn supplies the link to the
nearby routers which make the users able to access the network using their computers and other
devices which can access the network.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Network Design 8
References
Kong, F., Sahadat, M. N., Ghovanloo, M., & Durgin, G. (2019). A Standalone Intraoral Tongue-
Controlled Computer Interface for People with Tetraplegia. IEEE transactions on
biomedical circuits and systems.
Salz, D. (2018). U.S. Patent Application No. 15/418,454.
References
Kong, F., Sahadat, M. N., Ghovanloo, M., & Durgin, G. (2019). A Standalone Intraoral Tongue-
Controlled Computer Interface for People with Tetraplegia. IEEE transactions on
biomedical circuits and systems.
Salz, D. (2018). U.S. Patent Application No. 15/418,454.
1 out of 8
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





