Big Data, IT Security, and GDPR: A Case Study for Arden University
VerifiedAdded on 2022/12/01
|13
|3192
|438
Report
AI Summary
This report delves into the significance and application of big data within Arden University, exploring its benefits in decision-making, customer service, and teaching effectiveness. It identifies the different types of big data, including structured, unstructured, and semi-structured data, and discusses its key characteristics such as volume, variety, velocity, and variability. The report also addresses essential IT security and data privacy measures, including firewalls, intrusion detection systems, and virtual private networks, that organizations like Arden University must implement to protect sensitive data. Furthermore, it examines the key provisions of the General Data Protection Regulation (GDPR) and its implications for data protection practices, emphasizing the importance of compliance with GDPR to avoid penalties and maintain data security. The report concludes by highlighting the role of telecommunication and spreadsheets in data management, underscoring the importance of robust data governance in the digital age.

Technology in
Organisations
Organisations
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser


INTRODUCTION
Big data is a type of volume and the capability of data stored in a computer. it is used by many
organisations and institution that have lot of data and records in order to regulate their day-to-day
business activities. It is known as big data as it consists use files and documents that require High
spaces and volumes with which use files and documents that require high spaces and volumes
with which measure in numbers megabyte and terabyte (Asheim, 2019). This report is going to
answer the questions in which the significance types and volumes of big data will be analysed.
Along with this , the tools that Arden University needs to undertake for better security concerns
of Internet is also going to evaluate in this report.
MAIN BODY
TASK
Question 1
A) Identify and discuss in detail Big Data and its role in Arden University. Provide
examples of any two departments.
It is well known that internet is taking large growth into 20-21st century that enables many
opportunities for the organisation in terms of managing their business and its key information.
Therefore, the invention of computer was made several years ago but it does not know that it
become important for the businesses. The use of computer is almost everywhere in every field
weather it is small organisation, public or private sector, universities or in house. It becomes a
vital source for everyone to make the work faster and superior. Computer is mainly known for
storing data comma keeping records listening music , playing games , surfing internet and aware
about world situation (Connolly, and Cullen, 2018). But organisation takes the use of computer
in most significant manner by saving the data wssshich contains use volumes and size. As the
computers are accepting many software and tools that would not find anywhere else. Many
organisations are only work to collect data and earn money. For example, Face book is a social
networking app on which people connect with each other, share photos videos and conversations
Big data is a type of volume and the capability of data stored in a computer. it is used by many
organisations and institution that have lot of data and records in order to regulate their day-to-day
business activities. It is known as big data as it consists use files and documents that require High
spaces and volumes with which use files and documents that require high spaces and volumes
with which measure in numbers megabyte and terabyte (Asheim, 2019). This report is going to
answer the questions in which the significance types and volumes of big data will be analysed.
Along with this , the tools that Arden University needs to undertake for better security concerns
of Internet is also going to evaluate in this report.
MAIN BODY
TASK
Question 1
A) Identify and discuss in detail Big Data and its role in Arden University. Provide
examples of any two departments.
It is well known that internet is taking large growth into 20-21st century that enables many
opportunities for the organisation in terms of managing their business and its key information.
Therefore, the invention of computer was made several years ago but it does not know that it
become important for the businesses. The use of computer is almost everywhere in every field
weather it is small organisation, public or private sector, universities or in house. It becomes a
vital source for everyone to make the work faster and superior. Computer is mainly known for
storing data comma keeping records listening music , playing games , surfing internet and aware
about world situation (Connolly, and Cullen, 2018). But organisation takes the use of computer
in most significant manner by saving the data wssshich contains use volumes and size. As the
computers are accepting many software and tools that would not find anywhere else. Many
organisations are only work to collect data and earn money. For example, Face book is a social
networking app on which people connect with each other, share photos videos and conversations
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

by liking and commenting them. Therefore the information and data stored in the Face book is
known as big data which is 500 terabytes every day. Face book could not delete or the data
without the permission of account owner. So it requires maximum safety and possible software
tools that could store this large size of amount into much volume.
Kinds of big data
Big data have kinds that is structured unstructured and semi structured.
The structure data it is known for assessing and processing the fixed form of data. The
computer has gained its success by developing some techniques to acknowledge the format
automatically in which the data gets stored as per its volume and size. This is called structured
data which is nowadays used by many organisations. Data keep in relational database
management which is known as structured data. This database is mainly used by accounting
purpose in Arden University in order to give salaries and classify employees as per their
department.
Unstructured: the unstructured data is the data posses which are simple and less complex files
like images, videos, text and simple file formats. In Arden University, this data use as the pdf
and documents which is useful to teach students and give projects.
Semi- structured data: This data is the combination of both but this data is structured is
representing in XML file.
Characteristics of big data:
Volume: Volume defines the size of big data. As, it is the whole matter of size which play a very
important role in maintaining the data (Hofmann, and Ogonek, 2018). So that volume needs to be
maintained. It is considered in megabyte, terabyte zettabyte
Variety: Variety is the source and configuration of data under any type. It defines in
which source the data will be retained. Nowadays, there are many format and sources to retain a
data as there are a lot of software and technologies. Mainly the varieties include videos, email,
photo audio PDF and documents.
known as big data which is 500 terabytes every day. Face book could not delete or the data
without the permission of account owner. So it requires maximum safety and possible software
tools that could store this large size of amount into much volume.
Kinds of big data
Big data have kinds that is structured unstructured and semi structured.
The structure data it is known for assessing and processing the fixed form of data. The
computer has gained its success by developing some techniques to acknowledge the format
automatically in which the data gets stored as per its volume and size. This is called structured
data which is nowadays used by many organisations. Data keep in relational database
management which is known as structured data. This database is mainly used by accounting
purpose in Arden University in order to give salaries and classify employees as per their
department.
Unstructured: the unstructured data is the data posses which are simple and less complex files
like images, videos, text and simple file formats. In Arden University, this data use as the pdf
and documents which is useful to teach students and give projects.
Semi- structured data: This data is the combination of both but this data is structured is
representing in XML file.
Characteristics of big data:
Volume: Volume defines the size of big data. As, it is the whole matter of size which play a very
important role in maintaining the data (Hofmann, and Ogonek, 2018). So that volume needs to be
maintained. It is considered in megabyte, terabyte zettabyte
Variety: Variety is the source and configuration of data under any type. It defines in
which source the data will be retained. Nowadays, there are many format and sources to retain a
data as there are a lot of software and technologies. Mainly the varieties include videos, email,
photo audio PDF and documents.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Velocity: It is the speed of data mama it shows at which Speed the data meet the demand
of the sources. Business organisation need to have authorised networks and sources through
which the data run on high velocity.
Variability: It is the form of inconvenience and regularity of data. Sometimes data could
get hack or not presentable. In that case some variables are setup to manage time effectively.
B) Discuss the key benefits organizations like Arden University gain after adopting Big
Data.
There are many benefits that Arden University could undertake from using big data. As it can
say that the whole of University procedure is based on big data. So there are multiple benefits
which are described below:
Benefit in decision making: As the data in tables outside Intelligence and other competition for
the organisation. art and University could find the operations of other universities to attract
number of students. The university could analyse the external knowledge which is required to
take for the decisions for students Course and their future.
Making effective Customer services: Big data is mainly used to improve Customer services by
getting excess of social platforms like Facebook Twitter Instagram. The social sites connect the
university and the students in a better way. By posting pictures audios lectures, the student get
aware about University course and its feasibility for their future so that they would get keen to
take admission into Arden University(Jacobo-Romero, and Freitas, 2021). This will help
University to improve their business strategy and make the choices as per student’s requirements.
Teaching effectively: A teacher or professor always looks for a better strategy and techniques
that could influence the students and make them understand the topic appropriately. So, big data
plays a vital role in it by making teaching techniques attractive and less complex. The university
and counter projects and comments during the classroom module through which students take
interest in learning which is the main aim of the universities that create their reputation in to
market.
of the sources. Business organisation need to have authorised networks and sources through
which the data run on high velocity.
Variability: It is the form of inconvenience and regularity of data. Sometimes data could
get hack or not presentable. In that case some variables are setup to manage time effectively.
B) Discuss the key benefits organizations like Arden University gain after adopting Big
Data.
There are many benefits that Arden University could undertake from using big data. As it can
say that the whole of University procedure is based on big data. So there are multiple benefits
which are described below:
Benefit in decision making: As the data in tables outside Intelligence and other competition for
the organisation. art and University could find the operations of other universities to attract
number of students. The university could analyse the external knowledge which is required to
take for the decisions for students Course and their future.
Making effective Customer services: Big data is mainly used to improve Customer services by
getting excess of social platforms like Facebook Twitter Instagram. The social sites connect the
university and the students in a better way. By posting pictures audios lectures, the student get
aware about University course and its feasibility for their future so that they would get keen to
take admission into Arden University(Jacobo-Romero, and Freitas, 2021). This will help
University to improve their business strategy and make the choices as per student’s requirements.
Teaching effectively: A teacher or professor always looks for a better strategy and techniques
that could influence the students and make them understand the topic appropriately. So, big data
plays a vital role in it by making teaching techniques attractive and less complex. The university
and counter projects and comments during the classroom module through which students take
interest in learning which is the main aim of the universities that create their reputation in to
market.

Question 2: Explain the IT security and data privacy measures that an organisation must
implement. And the key provisions of GDPR.
As far and Internet is taking lead into Global world to stop it becomes because of of many
violence and misleading. In Internet world, cyber crime is the most affected thing to the
organisation in which the data gets hacked and use for personal financial purpose. There are
several cases in which organisation lead to bankruptcy due to less privacy protection and data
theft. these data are not only organisation asset but also there is addition of personal
information’s of customer and stakeholders that lead to lower down the reputation of the
organisation. Therefore data privacy measures and security is a must for every organisation with
the effect of GDPRR that is General data protection regulation(Jideani, 2018). It is not only for
business is but also for individual purpose that every person needs to secure their personal data
with unauthorised sources or connections so that the disc would be minimise. Arden University
use automated information Technologies that an IT system to better accomplished their mission
and minimise the risk of data theft. The managers of it system have their primary function to
operate and manage all the risk associated with universities data in which many personal
information’s of student are encoded and their future are in the hands of the university. In order
to protect the IT operations Arden University is used fireworks IP addresses interaction detection
systems in order to prevent their data from theft.
Firewalls: the main criteria of establishing firewalls around the data are to enable the
permissions and connection to enter into one request a device. There are two types of firewalls
that are personal and network-based in which both are extensions and Hardware application
respectively which passes the information and traffic through switches and routes. The IT
manager of Arden University does not allow the interference of any students for professors into
their data without the permission so that no cheating would be conduct on examination and there
are several issues outsourcing of revealing examination paper which would be solved through
surrounding firewalls.
Intrusion detection prevention system: it is a type of software through which the IT managers
could identify the traffic passing or existing on the ID without any allowance. Also these are
antivirus software in which any fakes ID for connections get automatically interrupted and shows
error while connecting them. It is protected with double layer of password and prevents attack
implement. And the key provisions of GDPR.
As far and Internet is taking lead into Global world to stop it becomes because of of many
violence and misleading. In Internet world, cyber crime is the most affected thing to the
organisation in which the data gets hacked and use for personal financial purpose. There are
several cases in which organisation lead to bankruptcy due to less privacy protection and data
theft. these data are not only organisation asset but also there is addition of personal
information’s of customer and stakeholders that lead to lower down the reputation of the
organisation. Therefore data privacy measures and security is a must for every organisation with
the effect of GDPRR that is General data protection regulation(Jideani, 2018). It is not only for
business is but also for individual purpose that every person needs to secure their personal data
with unauthorised sources or connections so that the disc would be minimise. Arden University
use automated information Technologies that an IT system to better accomplished their mission
and minimise the risk of data theft. The managers of it system have their primary function to
operate and manage all the risk associated with universities data in which many personal
information’s of student are encoded and their future are in the hands of the university. In order
to protect the IT operations Arden University is used fireworks IP addresses interaction detection
systems in order to prevent their data from theft.
Firewalls: the main criteria of establishing firewalls around the data are to enable the
permissions and connection to enter into one request a device. There are two types of firewalls
that are personal and network-based in which both are extensions and Hardware application
respectively which passes the information and traffic through switches and routes. The IT
manager of Arden University does not allow the interference of any students for professors into
their data without the permission so that no cheating would be conduct on examination and there
are several issues outsourcing of revealing examination paper which would be solved through
surrounding firewalls.
Intrusion detection prevention system: it is a type of software through which the IT managers
could identify the traffic passing or existing on the ID without any allowance. Also these are
antivirus software in which any fakes ID for connections get automatically interrupted and shows
error while connecting them. It is protected with double layer of password and prevents attack
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

when any person tries to login in bi too many attempts. IDS is formulated to detect and report
any critical network traffic, an IPS system goes for its further trafficking in giving the patterns a
system log (Mann, Jevon, and Bachmann, 2020). Arden University use the software’s in order to
safeguard their data by enabling antivirus to the software which are prevailing documents and
projects so that no students could stole others data. The university needs to save data from
internal sources also as there are high chances to stole others work at a university level.
Virtual private network: it is public networks in which Communications get transfer
buy virtual connections without the use of any encrypted Technology. This network is mainly
used for alloying data of one computer to meet with the data of others or how to transfer the
communication session. Arden University is use virtual private network in order to maintain the
internal regulations and work effectively on security. They allow the VPN connections on
computers devices safely through off campus network so that the software installation and
workstation work effectively without any interruption.
Along with this not only organisation required protecting their safety of data but also government
also interfere by regulating the act which is called general data protection regulation in order to
secure and protect individuals and organisations data by confirming of lawsuit in order to keep
aware the hackers about its consequences. Therefore there are some guidelines of GDPR which
are described below:
It becomes mandatory regulation for every organisation as to protect the data through cyber
security so that no individual would get harm with the organisations practices(Nmachi, and Win,
2021). For the non compliance of GDPRR are it would lead to penalty of dollar 20 million which
is 4% of revenue. Show that every organisation need undertake GDPRR and regulation which
have some guidelines and benefits on identify and access management.
Extra territorial effect: the GDPR are comes along extra effect of personal data which
establish for businesses and citizens to monitor the behaviour of customers and a point a you
based representative who could identify and control the supervisory authority.
Data protection officer: with the effect of GDPR and regulation businesses need to appoint a
DPO officer who have indulge in public authorities and work on large scale with many
any critical network traffic, an IPS system goes for its further trafficking in giving the patterns a
system log (Mann, Jevon, and Bachmann, 2020). Arden University use the software’s in order to
safeguard their data by enabling antivirus to the software which are prevailing documents and
projects so that no students could stole others data. The university needs to save data from
internal sources also as there are high chances to stole others work at a university level.
Virtual private network: it is public networks in which Communications get transfer
buy virtual connections without the use of any encrypted Technology. This network is mainly
used for alloying data of one computer to meet with the data of others or how to transfer the
communication session. Arden University is use virtual private network in order to maintain the
internal regulations and work effectively on security. They allow the VPN connections on
computers devices safely through off campus network so that the software installation and
workstation work effectively without any interruption.
Along with this not only organisation required protecting their safety of data but also government
also interfere by regulating the act which is called general data protection regulation in order to
secure and protect individuals and organisations data by confirming of lawsuit in order to keep
aware the hackers about its consequences. Therefore there are some guidelines of GDPR which
are described below:
It becomes mandatory regulation for every organisation as to protect the data through cyber
security so that no individual would get harm with the organisations practices(Nmachi, and Win,
2021). For the non compliance of GDPRR are it would lead to penalty of dollar 20 million which
is 4% of revenue. Show that every organisation need undertake GDPRR and regulation which
have some guidelines and benefits on identify and access management.
Extra territorial effect: the GDPR are comes along extra effect of personal data which
establish for businesses and citizens to monitor the behaviour of customers and a point a you
based representative who could identify and control the supervisory authority.
Data protection officer: with the effect of GDPR and regulation businesses need to appoint a
DPO officer who have indulge in public authorities and work on large scale with many
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

individuals so that the DPO officer would fulfil their responsibility for controlling the accounts
and networks so that no conflict of interest would arise.
Consent: with the effect of GDPR, organisation needs to put consent on each personal data
which their customers give them freely and trust fully. Also the customers have their rights to
take back their data at any time which is the consent the organisation gives to their customers.
This would maintain the data operations effectively and no individual would exploit bye business
that this is.
It has shown that every organisation working under EU Regulation Act they need to fulfil the
guidelines of GDPR so that Arden University would not come under non compliance. This
would lead to make a serious cause of obliging the act in which all the regulation must be
protected against student security and other members. University require to build concern
regarding each act of GDPR are as the University has appointed DPO officer which control and
monitor all the in activities.
Question 3 Telecommunication and spreadsheets
Cellular network is advanced form of wireless Technologies such as high speed of connections
Wi-Fi or any hardware devices such as keyboards printers which give networks and commands
to the computers. It is a form of connectivity method that juice into every mobile phone or
devices that have a radio antenna. It is based on the devices which have cell and could maintain
the communication(Sanga, 2021). It develops frequency GSM, CDMA, satellite. Cellular system
Have a plan and components which are defined block
Cell: it is the type and component of cellular network which is in the shape of honeycomb in
which area of region is divided. The cell that gives command to the stations for the areas. There
is No human made picture of the cell because of many variables into it.
Cluster: cluster is known as 8 together forms of cells. 18 channel been used in two cells will not
again reuse into the cluster.
Frequency reuse: does the cell use less number of radio frequency which is available in two
mobile devices there is still researching for the use of radio frequency so that one self could use
for more channels at a time (Yang, 2019). The cellular concept of frequency reuse is not still
and networks so that no conflict of interest would arise.
Consent: with the effect of GDPR, organisation needs to put consent on each personal data
which their customers give them freely and trust fully. Also the customers have their rights to
take back their data at any time which is the consent the organisation gives to their customers.
This would maintain the data operations effectively and no individual would exploit bye business
that this is.
It has shown that every organisation working under EU Regulation Act they need to fulfil the
guidelines of GDPR so that Arden University would not come under non compliance. This
would lead to make a serious cause of obliging the act in which all the regulation must be
protected against student security and other members. University require to build concern
regarding each act of GDPR are as the University has appointed DPO officer which control and
monitor all the in activities.
Question 3 Telecommunication and spreadsheets
Cellular network is advanced form of wireless Technologies such as high speed of connections
Wi-Fi or any hardware devices such as keyboards printers which give networks and commands
to the computers. It is a form of connectivity method that juice into every mobile phone or
devices that have a radio antenna. It is based on the devices which have cell and could maintain
the communication(Sanga, 2021). It develops frequency GSM, CDMA, satellite. Cellular system
Have a plan and components which are defined block
Cell: it is the type and component of cellular network which is in the shape of honeycomb in
which area of region is divided. The cell that gives command to the stations for the areas. There
is No human made picture of the cell because of many variables into it.
Cluster: cluster is known as 8 together forms of cells. 18 channel been used in two cells will not
again reuse into the cluster.
Frequency reuse: does the cell use less number of radio frequency which is available in two
mobile devices there is still researching for the use of radio frequency so that one self could use
for more channels at a time (Yang, 2019). The cellular concept of frequency reuse is not still

instrumented only exist on a small geographical area. These groups are known as the footprint
and a limited to the channels so that this frequency does not interrupt between the connections.
Cell splitting: economy, there is a concept of fuller utilization of system into a small area as the
organization do to cover their cost. So that, the operators find the concept of lifting the cells
which is available for many users into a small area. This feature is mainly to provide the
acceptance into urban areas where there is a large traffic and less expensive cells are induced to
monitor rural areas.
B) Explain the benefits of a cellular network to a business.
There are various benefits indulge into business organization through a cellular network which is
defined below:
It Give the benefit of superficial connections my giving data transfer speed and to 2 small
regions such as mobile phones and tablets. It allows 4G, 3G per MMS, GSM and SMS
Technologies into the mobile phone full stop in current situation there is also
development of 5G connectivity which is the superior from all the connections.
Also in business organization this network play a vital role as all the work is dependent
on internet and mobile technologies in which communication and transfer of information
become a most vital part (Tilca, Mare, and Apatean, 2018) . Without cellular networks
no one can transform or communicate information to the others and the work will become
more complex. So that cellular network has results in alien and wireless connections
which give a contact free roaming when an individual move through one country to
another.
C) Spreadsheet from the Payroll department of Weaning Entertainment Ltd.
i.
and a limited to the channels so that this frequency does not interrupt between the connections.
Cell splitting: economy, there is a concept of fuller utilization of system into a small area as the
organization do to cover their cost. So that, the operators find the concept of lifting the cells
which is available for many users into a small area. This feature is mainly to provide the
acceptance into urban areas where there is a large traffic and less expensive cells are induced to
monitor rural areas.
B) Explain the benefits of a cellular network to a business.
There are various benefits indulge into business organization through a cellular network which is
defined below:
It Give the benefit of superficial connections my giving data transfer speed and to 2 small
regions such as mobile phones and tablets. It allows 4G, 3G per MMS, GSM and SMS
Technologies into the mobile phone full stop in current situation there is also
development of 5G connectivity which is the superior from all the connections.
Also in business organization this network play a vital role as all the work is dependent
on internet and mobile technologies in which communication and transfer of information
become a most vital part (Tilca, Mare, and Apatean, 2018) . Without cellular networks
no one can transform or communicate information to the others and the work will become
more complex. So that cellular network has results in alien and wireless connections
which give a contact free roaming when an individual move through one country to
another.
C) Spreadsheet from the Payroll department of Weaning Entertainment Ltd.
i.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
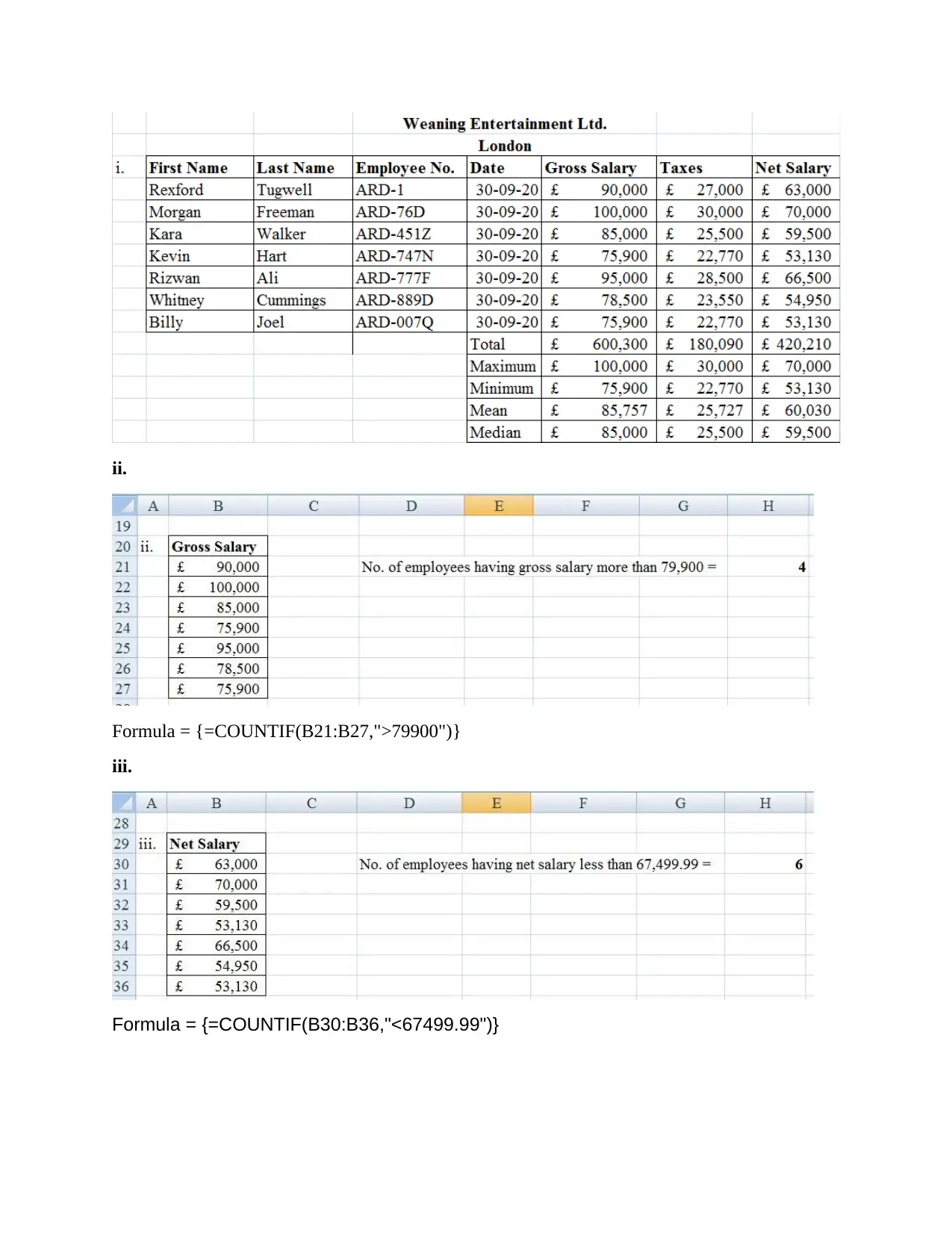
ii.
Formula = {=COUNTIF(B21:B27,">79900")}
iii.
Formula = {=COUNTIF(B30:B36,"<67499.99")}
Formula = {=COUNTIF(B21:B27,">79900")}
iii.
Formula = {=COUNTIF(B30:B36,"<67499.99")}
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

CONCLUSION
From the above-mentioned report, technology can be concluded that plays an important role in
the operations of the company in which the changing business environment presents the
company with many challenges and competition. Big data collects all the information needed and
thus increases the data size exponentially over time. These data are used by the company to
provide customers with insight and forecast their behaviour. This type of data helps insurance
companies to better retain their customers. It can be seen that cellular networks are a wireless
communication method that facilitates communication and interaction through the use of such
media.
From the above-mentioned report, technology can be concluded that plays an important role in
the operations of the company in which the changing business environment presents the
company with many challenges and competition. Big data collects all the information needed and
thus increases the data size exponentially over time. These data are used by the company to
provide customers with insight and forecast their behaviour. This type of data helps insurance
companies to better retain their customers. It can be seen that cellular networks are a wireless
communication method that facilitates communication and interaction through the use of such
media.

References
Books and journals:
Asheim, B.T., 2019. Smart specialisation, innovation policy and regional innovation systems:
what about new path development in less innovative regions?. Innovation: The
European Journal of Social Science Research, 32(1), pp.8-25.
Connolly, L. and Cullen, J.G., 2018. Animals and organisations: An ethic of care
framework. Organization & Environment, 31(4), pp.406-424.
Hofmann, S. and Ogonek, N., 2018. Different but still the same? How public and private sector
organisations deal with new digital competences. Electronic Journal of e-
Government, 16(2), pp.127-135.
Jacobo-Romero, M. and Freitas, A., 2021, March. Microeconomic foundations of decentralised
organisations. In Proceedings of the 36th Annual ACM Symposium on Applied
Computing (pp. 282-290).
Jideani, P.C., 2018. Towards a cybersecurity framework for South African e-retail
organisations (Doctoral dissertation, Cape Peninsula University of Technology).
Mann, G., Jevon, S. and Bachmann, B., 2020. How Are Firms Measuring Digital Transformation
at a Corporate-Level in Organisations?.
Nmachi, W.P. and Win, T., 2021, January. Mitigating Phishing Attack in Organisations: A
Literature Review. In CS & IT Conference Proceedings (Vol. 11, No. 1). CS & IT
Conference Proceedings.
Sanga, S.A., 2021. Macroeconomic Instabilities and Cost-Recovery Potentials of Public Sector
Organisations. Journal of Economic Science Research| Volume, 4(02).
Tilca, M., Mare, E. and Apatean, A., 2018. A model to measure the performance of human
resources in organisations. Studia Universitatis Vasile Goldiș Arad, Seria Științe
Economice, 28(1), pp.57-73.
Books and journals:
Asheim, B.T., 2019. Smart specialisation, innovation policy and regional innovation systems:
what about new path development in less innovative regions?. Innovation: The
European Journal of Social Science Research, 32(1), pp.8-25.
Connolly, L. and Cullen, J.G., 2018. Animals and organisations: An ethic of care
framework. Organization & Environment, 31(4), pp.406-424.
Hofmann, S. and Ogonek, N., 2018. Different but still the same? How public and private sector
organisations deal with new digital competences. Electronic Journal of e-
Government, 16(2), pp.127-135.
Jacobo-Romero, M. and Freitas, A., 2021, March. Microeconomic foundations of decentralised
organisations. In Proceedings of the 36th Annual ACM Symposium on Applied
Computing (pp. 282-290).
Jideani, P.C., 2018. Towards a cybersecurity framework for South African e-retail
organisations (Doctoral dissertation, Cape Peninsula University of Technology).
Mann, G., Jevon, S. and Bachmann, B., 2020. How Are Firms Measuring Digital Transformation
at a Corporate-Level in Organisations?.
Nmachi, W.P. and Win, T., 2021, January. Mitigating Phishing Attack in Organisations: A
Literature Review. In CS & IT Conference Proceedings (Vol. 11, No. 1). CS & IT
Conference Proceedings.
Sanga, S.A., 2021. Macroeconomic Instabilities and Cost-Recovery Potentials of Public Sector
Organisations. Journal of Economic Science Research| Volume, 4(02).
Tilca, M., Mare, E. and Apatean, A., 2018. A model to measure the performance of human
resources in organisations. Studia Universitatis Vasile Goldiș Arad, Seria Științe
Economice, 28(1), pp.57-73.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 13
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.


