IT Project Proposal: Blockchain for Enhanced Big Data Security
VerifiedAdded on 2022/09/13
|10
|1570
|12
Project
AI Summary
This project proposal and plan addresses the security and privacy challenges associated with big data by exploring the application of blockchain technology. The project begins with a rationale outlining the problem domain, which includes the vulnerabilities in big data storage and transfer, and justifies the need for a solution. Research questions are presented to guide the investigation into the privacy issues faced by big data and the role of blockchain in securing data. The conceptual framework draws on existing literature to highlight the security risks of big data and the benefits of blockchain's decentralized and transparent nature. The methodology involves qualitative research, including the analysis of journal articles and secondary data collection. The project plan includes deliverables like an annotated bibliography and a report, a work breakdown structure (WBS), risk analysis, duration estimates, and a Gantt chart to visualize the project timeline. The proposal emphasizes ethical considerations and compliance requirements, ensuring responsible research practices. The project aims to provide a comprehensive understanding of how blockchain can be leveraged to enhance the security and integrity of big data.

Running head: PROJECT MANAGEMENT
Emerging technology and innovation topic
Name of the Student
Name of the University
Author’s Note
Emerging technology and innovation topic
Name of the Student
Name of the University
Author’s Note
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

1
PROJECT MANAGEMENT
Table of Contents
1. Rationale......................................................................................................................................2
1.1 Problem domain.....................................................................................................................2
1.2 Purpose and justification........................................................................................................2
2. Supervisor approval.....................................................................................................................3
3. Research Questions......................................................................................................................3
4. Conceptual or theoretical framework..........................................................................................3
5. Methodology................................................................................................................................4
5.1 Analysis of sources of information........................................................................................4
5.2 Research methods..................................................................................................................4
5.3 Data collection.......................................................................................................................4
5.4 Ethical issues.........................................................................................................................4
5.5 Compliance requirements......................................................................................................5
6. Project plan.................................................................................................................................5
6.1 Deliverables...........................................................................................................................5
6.2 WBS.......................................................................................................................................5
6.3 Risk analysis..........................................................................................................................6
6.4 Duration.................................................................................................................................7
6.5 Gantt chart.............................................................................................................................7
Bibliography....................................................................................................................................8
PROJECT MANAGEMENT
Table of Contents
1. Rationale......................................................................................................................................2
1.1 Problem domain.....................................................................................................................2
1.2 Purpose and justification........................................................................................................2
2. Supervisor approval.....................................................................................................................3
3. Research Questions......................................................................................................................3
4. Conceptual or theoretical framework..........................................................................................3
5. Methodology................................................................................................................................4
5.1 Analysis of sources of information........................................................................................4
5.2 Research methods..................................................................................................................4
5.3 Data collection.......................................................................................................................4
5.4 Ethical issues.........................................................................................................................4
5.5 Compliance requirements......................................................................................................5
6. Project plan.................................................................................................................................5
6.1 Deliverables...........................................................................................................................5
6.2 WBS.......................................................................................................................................5
6.3 Risk analysis..........................................................................................................................6
6.4 Duration.................................................................................................................................7
6.5 Gantt chart.............................................................................................................................7
Bibliography....................................................................................................................................8

2
PROJECT MANAGEMENT
1. Rationale
1.1 Problem domain
The security aspect is considered as one of the significant concerns that mainly occurs
due to continuous exchange of various types of sensitive as well as confidential data. It is found
that big data mainly uses large sets of data and therefore hacking of information or data can
create huge loss (Terzi, Terzi & Sagiroglu, 2015). It is found that the data that is stored within
the storage medium including transaction logs as well as other confidential information generally
have varying levels. When data transfer take place then the size of the data gets increased and
both the availability as well as scalability makes auto-tiering important and therefore new
challenges are posed to big data storage. In addition to this, challenges like vulnerability to fake
generation of data as well as trouble in cryptographic protection also occurs.
1.2 Purpose and justification
The main purpose of the project is to utilize blockchain technology for resolving the
security and privacy issues which occur due to the use of Big data. It is found that blockchain has
brough a new way of properly managing as well as operating big data in a central perspective
where all the types of data are generally brought together in a very much centralized way. In
addition to this, it is found that Blockchain generally integrates with other types of advanced
technologies like cloud, AI as well as IoT. Moreover, data that is generated through blockchain
act as a boost for big data for successful data integrity as blockchain helps in ascertaining the
origin of data.
PROJECT MANAGEMENT
1. Rationale
1.1 Problem domain
The security aspect is considered as one of the significant concerns that mainly occurs
due to continuous exchange of various types of sensitive as well as confidential data. It is found
that big data mainly uses large sets of data and therefore hacking of information or data can
create huge loss (Terzi, Terzi & Sagiroglu, 2015). It is found that the data that is stored within
the storage medium including transaction logs as well as other confidential information generally
have varying levels. When data transfer take place then the size of the data gets increased and
both the availability as well as scalability makes auto-tiering important and therefore new
challenges are posed to big data storage. In addition to this, challenges like vulnerability to fake
generation of data as well as trouble in cryptographic protection also occurs.
1.2 Purpose and justification
The main purpose of the project is to utilize blockchain technology for resolving the
security and privacy issues which occur due to the use of Big data. It is found that blockchain has
brough a new way of properly managing as well as operating big data in a central perspective
where all the types of data are generally brought together in a very much centralized way. In
addition to this, it is found that Blockchain generally integrates with other types of advanced
technologies like cloud, AI as well as IoT. Moreover, data that is generated through blockchain
act as a boost for big data for successful data integrity as blockchain helps in ascertaining the
origin of data.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

3
PROJECT MANAGEMENT
2. Supervisor approval
It is found that after analyzing the purpose of the research project, proper approval from
higher authority has been achieved and as per the approval, the project will proceed accordingly.
3. Research Questions
The various research questions are listed below:
What are the privacy issues that Big data faces?
How Blockchain technology helps in securing data?
4. Conceptual or theoretical framework
According to Mishra and Singh (2016), sensitivities related with big data privacy as well
as security is considered as one of the major hurdles which the organizations generally needs to
overcome. It is found that many of times, the tools which are associated with big data as well as
smart analytics are open source and therefore, they are not properly designed and as result a
number of security issues occur. The threats even get worse if the website utilizes different types
of vulnerable CMS including WordPress (Mahmoud, Hegazy & Khafagy, 2018). The website
CMS are considered on the radar of the hackers and this issue generally gets worse when the
companies generally store information which are confidential and sensitive.
According to Zheng et al. (2018), Blockchain generally uses consensus algorithm for
verifying transactions as it becomes quite impossible for a single unit to pose any type of threat
to the entire data network. The network is so much distributed that it becomes very much
impossible for a particular party to properly generate enough computational power for altering
validation criteria. In addition to this, the data that is mainly recorded on blockchain are
PROJECT MANAGEMENT
2. Supervisor approval
It is found that after analyzing the purpose of the research project, proper approval from
higher authority has been achieved and as per the approval, the project will proceed accordingly.
3. Research Questions
The various research questions are listed below:
What are the privacy issues that Big data faces?
How Blockchain technology helps in securing data?
4. Conceptual or theoretical framework
According to Mishra and Singh (2016), sensitivities related with big data privacy as well
as security is considered as one of the major hurdles which the organizations generally needs to
overcome. It is found that many of times, the tools which are associated with big data as well as
smart analytics are open source and therefore, they are not properly designed and as result a
number of security issues occur. The threats even get worse if the website utilizes different types
of vulnerable CMS including WordPress (Mahmoud, Hegazy & Khafagy, 2018). The website
CMS are considered on the radar of the hackers and this issue generally gets worse when the
companies generally store information which are confidential and sensitive.
According to Zheng et al. (2018), Blockchain generally uses consensus algorithm for
verifying transactions as it becomes quite impossible for a single unit to pose any type of threat
to the entire data network. The network is so much distributed that it becomes very much
impossible for a particular party to properly generate enough computational power for altering
validation criteria. In addition to this, the data that is mainly recorded on blockchain are
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

4
PROJECT MANAGEMENT
considered to be quite trustworthy as they must have gone proper verification procedure which
helps in ensuring the quality of the data. Moreover, it helps in giving transparency as the
activities which took place can be traced on the blockchain network (Pilkington, 2016).
5. Methodology
5.1 Analysis of sources of information
After proper analysis of the journal articles it is found that the issues and challenges that
are associated with security and privacy of big data are properly elaborated. In addition to this,
the articles that are mainly reviewed helps in reflecting that use of blockchain technology are
helpful in securing and keeping data safe.
5.2 Research methods
Qualitative research method is used by the researcher and therefore they review a number
of journal articles, newspapers as well as organizational report in order to analyze the
significance that blockchain technology plays in managing the security issues that are associated
with big data (Flick, 2015).
5.3 Data collection
It is identified that out of the two data collection method, the researcher utilizes
secondary data collection method and uses a number of research papers and journal articles for
collecting information about big data and blockchain technology (Kumar, 2019).
5.4 Ethical issues
While working within the research, it is necessary to make proper agreement and act
quite effectively and sincerely for avoiding ethical issues.
PROJECT MANAGEMENT
considered to be quite trustworthy as they must have gone proper verification procedure which
helps in ensuring the quality of the data. Moreover, it helps in giving transparency as the
activities which took place can be traced on the blockchain network (Pilkington, 2016).
5. Methodology
5.1 Analysis of sources of information
After proper analysis of the journal articles it is found that the issues and challenges that
are associated with security and privacy of big data are properly elaborated. In addition to this,
the articles that are mainly reviewed helps in reflecting that use of blockchain technology are
helpful in securing and keeping data safe.
5.2 Research methods
Qualitative research method is used by the researcher and therefore they review a number
of journal articles, newspapers as well as organizational report in order to analyze the
significance that blockchain technology plays in managing the security issues that are associated
with big data (Flick, 2015).
5.3 Data collection
It is identified that out of the two data collection method, the researcher utilizes
secondary data collection method and uses a number of research papers and journal articles for
collecting information about big data and blockchain technology (Kumar, 2019).
5.4 Ethical issues
While working within the research, it is necessary to make proper agreement and act
quite effectively and sincerely for avoiding ethical issues.

5
PROJECT MANAGEMENT
Any data or information that is provided for this research must only use for academic
purpose for maintaining confidentiality of information.
5.5 Compliance requirements
Health, safety as well as welfare regulations must be applied to different aspects of
working so that the workers can be able to get proper environment while undertaking the
research.
As per government regulation, safety of the workplace must be maintained so that the
workers do not face issues.
6. Project plan
6.1 Deliverables
The deliverables include:
Annotated bibliography
Journal paper
Report
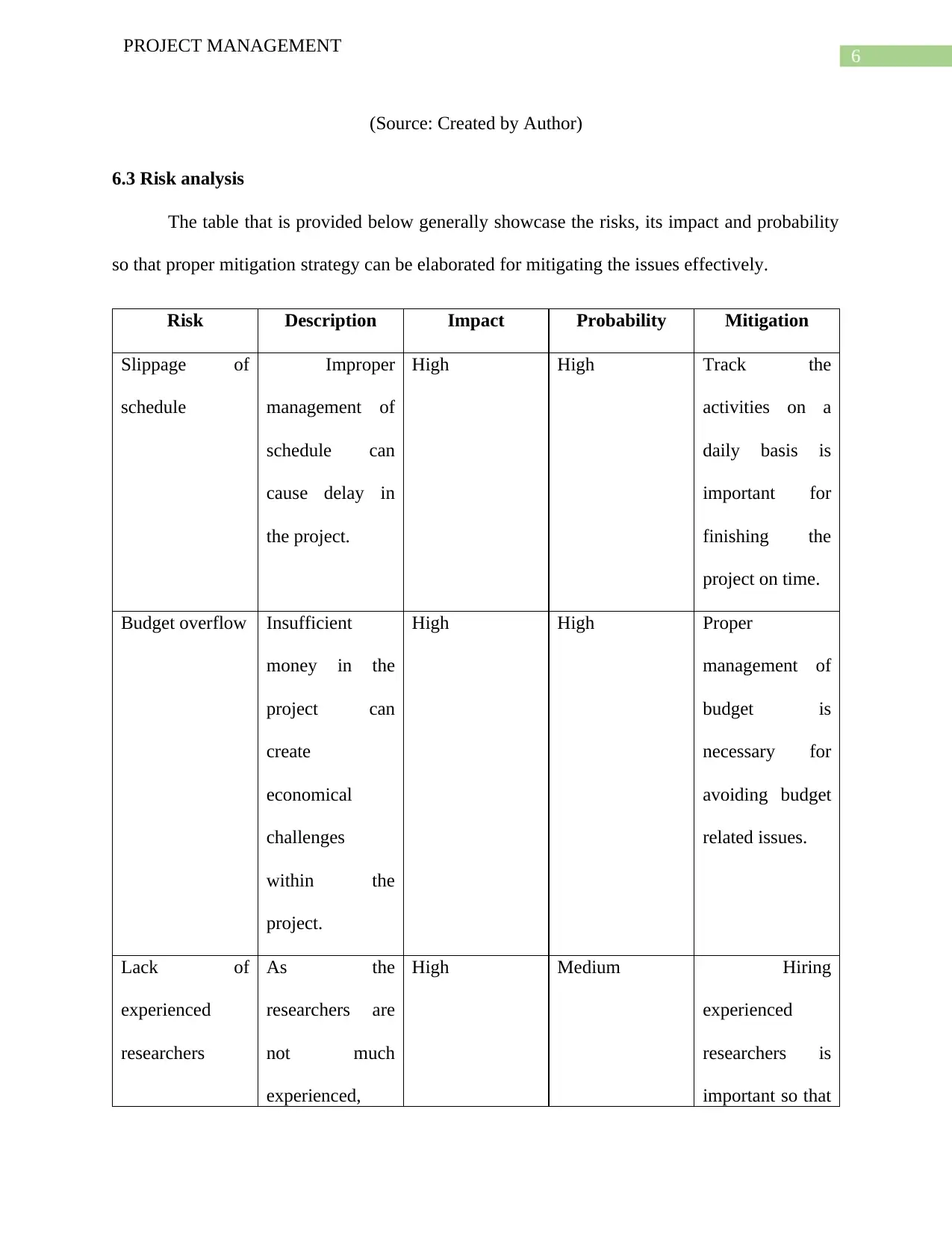
6.2 WBS
Figure 1: WBS
PROJECT MANAGEMENT
Any data or information that is provided for this research must only use for academic
purpose for maintaining confidentiality of information.
5.5 Compliance requirements
Health, safety as well as welfare regulations must be applied to different aspects of
working so that the workers can be able to get proper environment while undertaking the
research.
As per government regulation, safety of the workplace must be maintained so that the
workers do not face issues.
6. Project plan
6.1 Deliverables
The deliverables include:
Annotated bibliography
Journal paper
Report
6.2 WBS
Figure 1: WBS
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
6
PROJECT MANAGEMENT
(Source: Created by Author)
6.3 Risk analysis
The table that is provided below generally showcase the risks, its impact and probability
so that proper mitigation strategy can be elaborated for mitigating the issues effectively.
Risk Description Impact Probability Mitigation
Slippage of
schedule
Improper
management of
schedule can
cause delay in
the project.
High High Track the
activities on a
daily basis is
important for
finishing the
project on time.
Budget overflow Insufficient
money in the
project can
create
economical
challenges
within the
project.
High High Proper
management of
budget is
necessary for
avoiding budget
related issues.
Lack of
experienced
researchers
As the
researchers are
not much
experienced,
High Medium Hiring
experienced
researchers is
important so that
PROJECT MANAGEMENT
(Source: Created by Author)
6.3 Risk analysis
The table that is provided below generally showcase the risks, its impact and probability
so that proper mitigation strategy can be elaborated for mitigating the issues effectively.
Risk Description Impact Probability Mitigation
Slippage of
schedule
Improper
management of
schedule can
cause delay in
the project.
High High Track the
activities on a
daily basis is
important for
finishing the
project on time.
Budget overflow Insufficient
money in the
project can
create
economical
challenges
within the
project.
High High Proper
management of
budget is
necessary for
avoiding budget
related issues.
Lack of
experienced
researchers
As the
researchers are
not much
experienced,
High Medium Hiring
experienced
researchers is
important so that
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
7
PROJECT MANAGEMENT
they are not able
to review the
articles properly.
the review can
be conducted
successfully.
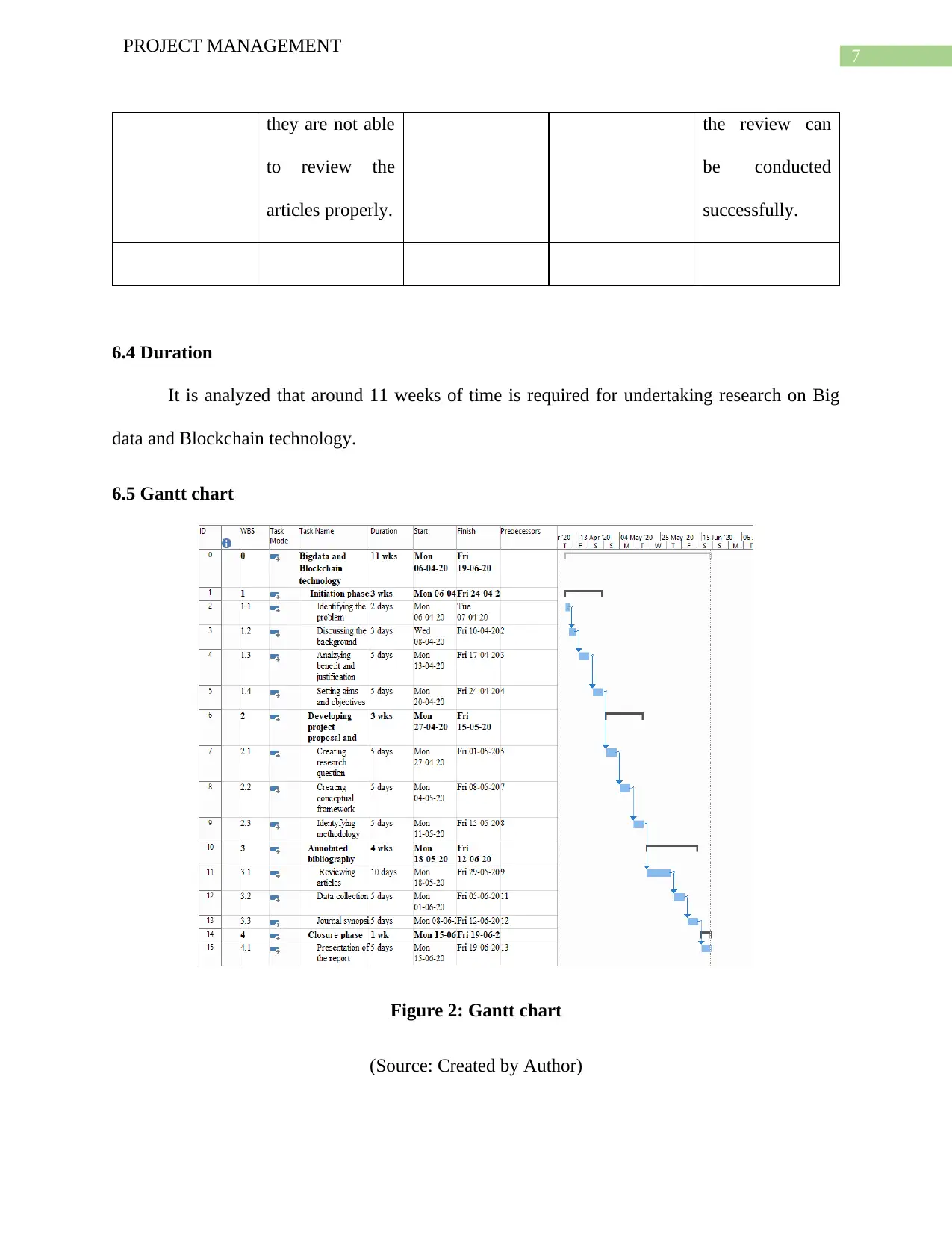
6.4 Duration
It is analyzed that around 11 weeks of time is required for undertaking research on Big
data and Blockchain technology.
6.5 Gantt chart
Figure 2: Gantt chart
(Source: Created by Author)
PROJECT MANAGEMENT
they are not able
to review the
articles properly.
the review can
be conducted
successfully.
6.4 Duration
It is analyzed that around 11 weeks of time is required for undertaking research on Big
data and Blockchain technology.
6.5 Gantt chart
Figure 2: Gantt chart
(Source: Created by Author)

8
PROJECT MANAGEMENT
Bibliography
Flick, U. (2015). Introducing research methodology: A beginner's guide to doing a research
project. Sage.
Huh, S., Cho, S. & Kim, S., (.2017). February. Managing IoT devices using blockchain platform.
In 2017 19th international conference on advanced communication technology
(ICACT) (pp. 464-467). IEEE.
Kumar, R. (2019). Research methodology: A step-by-step guide for beginners. Sage Publications
Limited.
Mahmoud, H., Hegazy, A. & Khafagy, M.H. (2018). February. An approach for big data security
based on Hadoop distributed file system. In 2018 International Conference on Innovative
Trends in Computer Engineering (ITCE) (pp. 109-114). IEEE.
Mishra, A.D. & Singh, Y.B. (2016). April. Big data analytics for security and privacy challenges.
In 2016 International Conference on Computing, Communication and Automation
(ICCCA) (pp. 50-53). IEEE.
Pilkington, M. (2016). Blockchain technology: principles and applications. In Research
handbook on digital transformations. Edward Elgar Publishing.
Terzi, D.S., Terzi, R. & Sagiroglu, S. (2015). December. A survey on security and privacy issues
in big data. In 2015 10th International Conference for Internet Technology and Secured
Transactions (ICITST) (pp. 202-207). IEEE.
PROJECT MANAGEMENT
Bibliography
Flick, U. (2015). Introducing research methodology: A beginner's guide to doing a research
project. Sage.
Huh, S., Cho, S. & Kim, S., (.2017). February. Managing IoT devices using blockchain platform.
In 2017 19th international conference on advanced communication technology
(ICACT) (pp. 464-467). IEEE.
Kumar, R. (2019). Research methodology: A step-by-step guide for beginners. Sage Publications
Limited.
Mahmoud, H., Hegazy, A. & Khafagy, M.H. (2018). February. An approach for big data security
based on Hadoop distributed file system. In 2018 International Conference on Innovative
Trends in Computer Engineering (ITCE) (pp. 109-114). IEEE.
Mishra, A.D. & Singh, Y.B. (2016). April. Big data analytics for security and privacy challenges.
In 2016 International Conference on Computing, Communication and Automation
(ICCCA) (pp. 50-53). IEEE.
Pilkington, M. (2016). Blockchain technology: principles and applications. In Research
handbook on digital transformations. Edward Elgar Publishing.
Terzi, D.S., Terzi, R. & Sagiroglu, S. (2015). December. A survey on security and privacy issues
in big data. In 2015 10th International Conference for Internet Technology and Secured
Transactions (ICITST) (pp. 202-207). IEEE.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

9
PROJECT MANAGEMENT
Zheng, Z., Xie, S., Dai, H.N., Chen, X. & Wang, H. (2018). Blockchain challenges and
opportunities: A survey. International Journal of Web and Grid Services, 14(4), pp.352-
375.
Zheng, Z., Xie, S., Dai, H., Chen, X. & Wang, H. (2017). June. An overview of blockchain
technology: Architecture, consensus, and future trends. In 2017 IEEE international
congress on big data (BigData congress) (pp. 557-564). IEEE.
PROJECT MANAGEMENT
Zheng, Z., Xie, S., Dai, H.N., Chen, X. & Wang, H. (2018). Blockchain challenges and
opportunities: A survey. International Journal of Web and Grid Services, 14(4), pp.352-
375.
Zheng, Z., Xie, S., Dai, H., Chen, X. & Wang, H. (2017). June. An overview of blockchain
technology: Architecture, consensus, and future trends. In 2017 IEEE international
congress on big data (BigData congress) (pp. 557-564). IEEE.
1 out of 10
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





