Big Data Ecosystem Architecture, Cloud Security Risks, and Framework
VerifiedAdded on 2021/02/21
|17
|5139
|55
Report
AI Summary
This report delves into the realms of big data and cloud security, specifically within the context of Hounslow Construction. It begins by examining a Security Assurance Framework for Evaluation (SAFE) designed to assess compliance and mitigate threats in cloud-based applications, highlighting its stages and benefits for the company. The report then critically evaluates the security risks associated with IaaS, PaaS, and SaaS cloud services, recommending the most suitable and secure options for Hounslow Construction. Furthermore, it dissects the components of a Big Data Ecosystem Architecture, identifying secure design principles and recommending security controls. The report also discusses the strengths and weaknesses of secure cloud computing and big data features, and explores professional practices to ensure compliance with legal, ethical, and social issues within the big data and cloud environment. The conclusion summarizes the key findings and recommendations, emphasizing the importance of a robust security posture for Hounslow Construction's data management and cloud operations.

Big Data and Cloud
Security
Security
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Table of Contents
INTRODUCTION...........................................................................................................................1
SECTION A.....................................................................................................................................1
1. Security Assurance Framework for evaluation for the assessment of the compliance and
threat in relation to the cloud based applications.........................................................................1
2. Critical evaluation of the security risks within IASS, PAAS and SAAS and also more
suitable and secure cloud services within the HC........................................................................3
3. Critical evaluation of the Big data Ecosystem Architecture components. Also identifying the
secure design architecture and various recommendations for security control within HC..........4
SECTION – B..................................................................................................................................6
1. Discuss about the strength and weakness of secure cloud computing and big data features...6
2. Discuss about the professional practices that help the Hounslow construction to comply
with legal, ethical and social issues with the big data and cloud environment............................9
CONCLUSION..............................................................................................................................11
REFERENCES..............................................................................................................................12
INTRODUCTION...........................................................................................................................1
SECTION A.....................................................................................................................................1
1. Security Assurance Framework for evaluation for the assessment of the compliance and
threat in relation to the cloud based applications.........................................................................1
2. Critical evaluation of the security risks within IASS, PAAS and SAAS and also more
suitable and secure cloud services within the HC........................................................................3
3. Critical evaluation of the Big data Ecosystem Architecture components. Also identifying the
secure design architecture and various recommendations for security control within HC..........4
SECTION – B..................................................................................................................................6
1. Discuss about the strength and weakness of secure cloud computing and big data features...6
2. Discuss about the professional practices that help the Hounslow construction to comply
with legal, ethical and social issues with the big data and cloud environment............................9
CONCLUSION..............................................................................................................................11
REFERENCES..............................................................................................................................12

INTRODUCTION
Big data can be considered as a field which helps in extracting the information
systematically. Big data is generally used to extract the meaningful data from the huge and
complex database which analyse large data sets computationally in order to reveal a particular
pattern. Cloud security is the protection of the data that is stored online. Cloud computing allows
data to be stored within the network and this needs a proper security in order to restrict the
unauthorised users to access such information. This report will be based on the big data analytics
and cloud security within the Hounslow construction company and this company deals with
various operations which are handled by the number of TPS and controlled by the centralised
database.
Furthermore, the report will help in understanding Security assurance framework in order
to protect the data within the network. Along with this, it will also help in understanding various
cloud based technology that is IASS, PAAS and SAAS which allows the use of the cloud
services. Moreover, it will also investigates the features of the Big data ecosystem Architecture
components. Strengths and weaknesses of secured cloud computing and big data are also been
explained.
SECTION A
1. Security Assurance Framework for evaluation for the assessment of the compliance and threat
in relation to the cloud based applications
The security assurance Framework for Evaluation (SAFE) is a structured, light weight
methodology that helps in comparative assessment of the compliance and risk in relation with the
application of the modern cloud based services. Information security assurance commonly begins
with two perspectives that is Risk and compliance (Cai and et.al., 2016). SAFE methodology
basically helps in providing the secure cloud based platform for the Hounslow construction
company. Collection of the specific policies and regulatory requirements allows the organization
to work through the series of information security checklists that helps in easily identifying the
discrepancies in practice. SAFE Framework is useful because it helps in identifying various
vulnerabilities that helps in exposing such assets in order to identify various adverse events.
Although, it helps in assessing the overall risk and also helps in taking the security controls and
risk mitigation measures in order to overcome the overall risks of the company. In Hounslow
Construction company, SAFE framework helps in configure the security settings. It also allows
1
Big data can be considered as a field which helps in extracting the information
systematically. Big data is generally used to extract the meaningful data from the huge and
complex database which analyse large data sets computationally in order to reveal a particular
pattern. Cloud security is the protection of the data that is stored online. Cloud computing allows
data to be stored within the network and this needs a proper security in order to restrict the
unauthorised users to access such information. This report will be based on the big data analytics
and cloud security within the Hounslow construction company and this company deals with
various operations which are handled by the number of TPS and controlled by the centralised
database.
Furthermore, the report will help in understanding Security assurance framework in order
to protect the data within the network. Along with this, it will also help in understanding various
cloud based technology that is IASS, PAAS and SAAS which allows the use of the cloud
services. Moreover, it will also investigates the features of the Big data ecosystem Architecture
components. Strengths and weaknesses of secured cloud computing and big data are also been
explained.
SECTION A
1. Security Assurance Framework for evaluation for the assessment of the compliance and threat
in relation to the cloud based applications
The security assurance Framework for Evaluation (SAFE) is a structured, light weight
methodology that helps in comparative assessment of the compliance and risk in relation with the
application of the modern cloud based services. Information security assurance commonly begins
with two perspectives that is Risk and compliance (Cai and et.al., 2016). SAFE methodology
basically helps in providing the secure cloud based platform for the Hounslow construction
company. Collection of the specific policies and regulatory requirements allows the organization
to work through the series of information security checklists that helps in easily identifying the
discrepancies in practice. SAFE Framework is useful because it helps in identifying various
vulnerabilities that helps in exposing such assets in order to identify various adverse events.
Although, it helps in assessing the overall risk and also helps in taking the security controls and
risk mitigation measures in order to overcome the overall risks of the company. In Hounslow
Construction company, SAFE framework helps in configure the security settings. It also allows
1
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

the firm to maintain the coordination and synchronization among multiple programs. It also
helpful for the company in providing the strategic direction, investment funding and lean
governance. However, this is designed to be the lightweight in order to assess the security and
compliance rapidly without the need for the highly skilled experts.
This SAFE framework mainly focuses towards the security, compliance and risk factors.
This methodology is also used to compare multiple alternative cloud provider solution on a
consistent basis (Gai and et.al., 2016). It allows the organization to compare various alternative
methods which may comprises of the delivery models such as on-premises non-cloud based
implementation, private cloud, hosted cloud, public cloud or any other combination of cloud.
There are five stages included in the SAFE methodology and these distinct stages are described
below:
Strategic intent
This stage allows the construction company to develop the clear strategies, plans and
clear statements in order to deal with the security and compliance of the cloud based
applications. This stage assures the clear objectives along with the benefits and description of the
2
Illustration 1: Dimensions of Assurance when
using cloud services
helpful for the company in providing the strategic direction, investment funding and lean
governance. However, this is designed to be the lightweight in order to assess the security and
compliance rapidly without the need for the highly skilled experts.
This SAFE framework mainly focuses towards the security, compliance and risk factors.
This methodology is also used to compare multiple alternative cloud provider solution on a
consistent basis (Gai and et.al., 2016). It allows the organization to compare various alternative
methods which may comprises of the delivery models such as on-premises non-cloud based
implementation, private cloud, hosted cloud, public cloud or any other combination of cloud.
There are five stages included in the SAFE methodology and these distinct stages are described
below:
Strategic intent
This stage allows the construction company to develop the clear strategies, plans and
clear statements in order to deal with the security and compliance of the cloud based
applications. This stage assures the clear objectives along with the benefits and description of the
2
Illustration 1: Dimensions of Assurance when
using cloud services
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

assurance objectives. This stage basically plays the vital role in setting the overall context and
scope regarding the security and compliance to use the cloud applications in a formal way.
Laying out the internal and external requirements
It is the second stage of the Security Assurance framework for the Evaluation
methodology which helps the Construction company to identify the requirements to identify the
threats and compliance in such cloud based applications. These requirements are helpful for
Hounslow to derives from the legislations, regulatory guidance, code of conduct and supplier
agreement etc. in order to evaluate the Security and compliance of the Cloud applications
(Hashem And et.al., 2015). However, the internal requirements can be accessed from the security
policies, existing infrastructure and strategies that we derived on the first stage of the SAFE
methodology.
Verifying the cloud service
This stage of the SAFE methodology helps in verifying the cloud services or application
that can actually satisfy the requirements. It can be identified by the combination of the service
provider documentation, terms of the contract and independent verification process which allows
the verification of such process. Therefore, this stage within the SAFE methodology helps in
verifying the overall cloud based application within the company Hounslow.
Holistic risk assessment
This stage is used for performing the Risk assessment which helps in identifying the
trustworthiness, resilience and adaptability of such formed strategies regarding the security,
compliance and threats of implementing the security based services. It can be benefited to the
company as it is used to lightweight, covering and conventional assurance and considerations
that allows in Risk assessments.
Recommendation for the HC to proceed such services.
This step helps in accessing the combines all the previous inputs in order to recommend
that the Hounslow construction company will proceed such applications further or not.
Recommendation section helps in improving the security and compliance measures in order to
improve the data storage facility over the cloud and thus it helps in maintaining the proper
inflows and outflows within Hounslow company.
3
scope regarding the security and compliance to use the cloud applications in a formal way.
Laying out the internal and external requirements
It is the second stage of the Security Assurance framework for the Evaluation
methodology which helps the Construction company to identify the requirements to identify the
threats and compliance in such cloud based applications. These requirements are helpful for
Hounslow to derives from the legislations, regulatory guidance, code of conduct and supplier
agreement etc. in order to evaluate the Security and compliance of the Cloud applications
(Hashem And et.al., 2015). However, the internal requirements can be accessed from the security
policies, existing infrastructure and strategies that we derived on the first stage of the SAFE
methodology.
Verifying the cloud service
This stage of the SAFE methodology helps in verifying the cloud services or application
that can actually satisfy the requirements. It can be identified by the combination of the service
provider documentation, terms of the contract and independent verification process which allows
the verification of such process. Therefore, this stage within the SAFE methodology helps in
verifying the overall cloud based application within the company Hounslow.
Holistic risk assessment
This stage is used for performing the Risk assessment which helps in identifying the
trustworthiness, resilience and adaptability of such formed strategies regarding the security,
compliance and threats of implementing the security based services. It can be benefited to the
company as it is used to lightweight, covering and conventional assurance and considerations
that allows in Risk assessments.
Recommendation for the HC to proceed such services.
This step helps in accessing the combines all the previous inputs in order to recommend
that the Hounslow construction company will proceed such applications further or not.
Recommendation section helps in improving the security and compliance measures in order to
improve the data storage facility over the cloud and thus it helps in maintaining the proper
inflows and outflows within Hounslow company.
3

2. Critical evaluation of the security risks within IASS, PAAS and SAAS and also more suitable
and secure cloud services within the HC.
Cloud computing infrastructure facilitates various things such as network, server,
operating system and storage etc. all the facilities provided by the cloud computing through
virtualisation technology (Li and et.al., 2018). So this allows the users to store the data on the
internet using three different types of models that is software as a service, Platform as a service
and infrastructure as a service. So there are various risks associated with such types of Clod
computing services. So below represented are the risks that are involved in using these cloud
technologies:
IAAS is a commonly known as Infrastructure as a service and this is basically made of
the highly scalable and automated computer resources. However, IAAS focuses on managing the
virtual machines but the major risk associated with this type of Cloud computing model is that It
includes unwarranted commandeering of services. It prevents the users to access the
information or service even at up-to the costs on Virtual machines. So there is a Risk of
Rogues users who allows them to access the data in a dishonest or unprincipled way.
On the Other hand, PAAS Is a Platform as a service which provides the cloud
components to a certain software while it delivers a framework for the developers. This
technology is mainly used by the developers to build upon and used to create the customised
applications. However, there are also Risks associated with this technology as well that includes
the Slow System Performance. As there is inherent data encryption within the PAAS
technology which may secures the data and information but it is slows downs the CPU cycle and
inefficient to provide the output. In contrast to this,
SAAS is a software as a service solution which allows the readymade software build on
the cloud and avail the facilities to the large amount of customers. It also provides the integrated
new software solutions Into the Hounslow construction company without wasting time and
money of the users in installations process (Lo’ai And et.al., 2016). Whereas it is somehow a
costly process. In contrast to this, there are various risks associated with the IAAS Technology
that is Password management as this deals with the applications on the cloud so it can be
considered as major risk factor. So in Hounslow construction company, IAAS has been a great
risk as single signing option can allows the access of the desktop as well as any cloud services
via a single password. It may arise the problem of Dangling accounts.
4
and secure cloud services within the HC.
Cloud computing infrastructure facilitates various things such as network, server,
operating system and storage etc. all the facilities provided by the cloud computing through
virtualisation technology (Li and et.al., 2018). So this allows the users to store the data on the
internet using three different types of models that is software as a service, Platform as a service
and infrastructure as a service. So there are various risks associated with such types of Clod
computing services. So below represented are the risks that are involved in using these cloud
technologies:
IAAS is a commonly known as Infrastructure as a service and this is basically made of
the highly scalable and automated computer resources. However, IAAS focuses on managing the
virtual machines but the major risk associated with this type of Cloud computing model is that It
includes unwarranted commandeering of services. It prevents the users to access the
information or service even at up-to the costs on Virtual machines. So there is a Risk of
Rogues users who allows them to access the data in a dishonest or unprincipled way.
On the Other hand, PAAS Is a Platform as a service which provides the cloud
components to a certain software while it delivers a framework for the developers. This
technology is mainly used by the developers to build upon and used to create the customised
applications. However, there are also Risks associated with this technology as well that includes
the Slow System Performance. As there is inherent data encryption within the PAAS
technology which may secures the data and information but it is slows downs the CPU cycle and
inefficient to provide the output. In contrast to this,
SAAS is a software as a service solution which allows the readymade software build on
the cloud and avail the facilities to the large amount of customers. It also provides the integrated
new software solutions Into the Hounslow construction company without wasting time and
money of the users in installations process (Lo’ai And et.al., 2016). Whereas it is somehow a
costly process. In contrast to this, there are various risks associated with the IAAS Technology
that is Password management as this deals with the applications on the cloud so it can be
considered as major risk factor. So in Hounslow construction company, IAAS has been a great
risk as single signing option can allows the access of the desktop as well as any cloud services
via a single password. It may arise the problem of Dangling accounts.
4
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

Suitability-
According to the requirements of the Hounslow company, IAAS will be best suited cloud
computing facility for the construction company. In addition Infrastructure as a service is most
Suited cloud computing for the Hounslow Company because it one of the most flexible cloud
computing model. It easily allow the automated deployment of the storage, networking, servers
etc. In these resources can be purchased according to the need and demand of the user. It can be
considered as one of the most suitable and secured Cloud computing service for the Hounslow
construction company because it enables the organization to provide the complete control of the
infrastructure to the organization and along with this IAAS provides the Highly scalable and
flexible services. Although, the cost also varies on the basis of the consumption of services.
3. Critical evaluation of the Big data Ecosystem Architecture components. Also identifying the
secure design architecture and various recommendations for security control within HC.
The Big data Architecture Framework is mainly introduced to address all the aspects of
the Big data Ecosystem. Infrastructural technologies are the core of the Big Data Ecosystem
which mainly used to process, store and analyse the data. In order to handle the large and
complex database, which vary according to the volume, velocity and variety. It is nothing but the
any data within the Hounslow construction company that consists of very big data which requires
proper analytics and to process such data (Sookhak and et.al., 2015). There are various different
types of components associated with the Big data Ecosystem Architecture within the Hounslow
company. Such components are as follows:
5
According to the requirements of the Hounslow company, IAAS will be best suited cloud
computing facility for the construction company. In addition Infrastructure as a service is most
Suited cloud computing for the Hounslow Company because it one of the most flexible cloud
computing model. It easily allow the automated deployment of the storage, networking, servers
etc. In these resources can be purchased according to the need and demand of the user. It can be
considered as one of the most suitable and secured Cloud computing service for the Hounslow
construction company because it enables the organization to provide the complete control of the
infrastructure to the organization and along with this IAAS provides the Highly scalable and
flexible services. Although, the cost also varies on the basis of the consumption of services.
3. Critical evaluation of the Big data Ecosystem Architecture components. Also identifying the
secure design architecture and various recommendations for security control within HC.
The Big data Architecture Framework is mainly introduced to address all the aspects of
the Big data Ecosystem. Infrastructural technologies are the core of the Big Data Ecosystem
which mainly used to process, store and analyse the data. In order to handle the large and
complex database, which vary according to the volume, velocity and variety. It is nothing but the
any data within the Hounslow construction company that consists of very big data which requires
proper analytics and to process such data (Sookhak and et.al., 2015). There are various different
types of components associated with the Big data Ecosystem Architecture within the Hounslow
company. Such components are as follows:
5
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
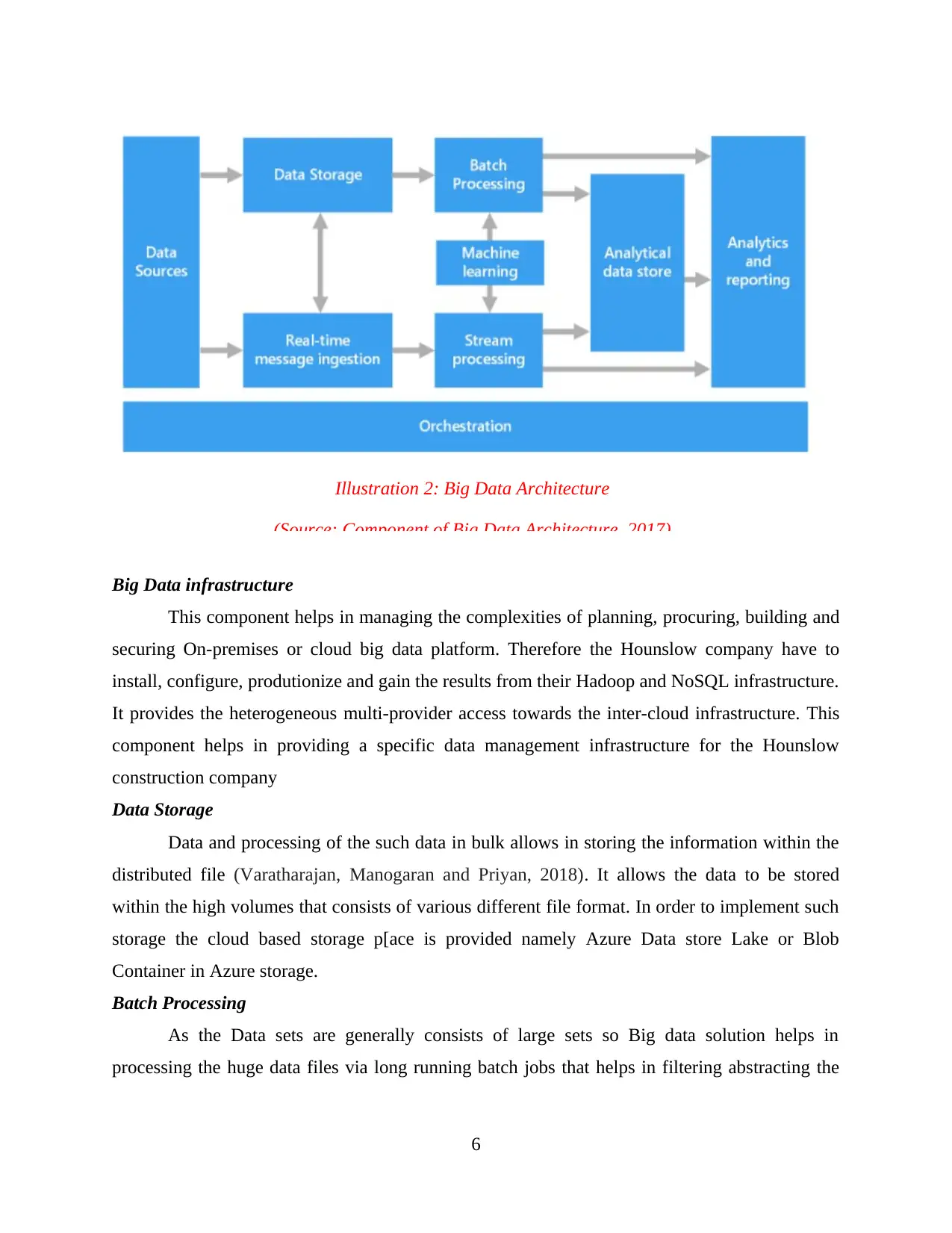
Big Data infrastructure
This component helps in managing the complexities of planning, procuring, building and
securing On-premises or cloud big data platform. Therefore the Hounslow company have to
install, configure, produtionize and gain the results from their Hadoop and NoSQL infrastructure.
It provides the heterogeneous multi-provider access towards the inter-cloud infrastructure. This
component helps in providing a specific data management infrastructure for the Hounslow
construction company
Data Storage
Data and processing of the such data in bulk allows in storing the information within the
distributed file (Varatharajan, Manogaran and Priyan, 2018). It allows the data to be stored
within the high volumes that consists of various different file format. In order to implement such
storage the cloud based storage p[ace is provided namely Azure Data store Lake or Blob
Container in Azure storage.
Batch Processing
As the Data sets are generally consists of large sets so Big data solution helps in
processing the huge data files via long running batch jobs that helps in filtering abstracting the
6
Illustration 2: Big Data Architecture
(Source: Component of Big Data Architecture, 2017)
This component helps in managing the complexities of planning, procuring, building and
securing On-premises or cloud big data platform. Therefore the Hounslow company have to
install, configure, produtionize and gain the results from their Hadoop and NoSQL infrastructure.
It provides the heterogeneous multi-provider access towards the inter-cloud infrastructure. This
component helps in providing a specific data management infrastructure for the Hounslow
construction company
Data Storage
Data and processing of the such data in bulk allows in storing the information within the
distributed file (Varatharajan, Manogaran and Priyan, 2018). It allows the data to be stored
within the high volumes that consists of various different file format. In order to implement such
storage the cloud based storage p[ace is provided namely Azure Data store Lake or Blob
Container in Azure storage.
Batch Processing
As the Data sets are generally consists of large sets so Big data solution helps in
processing the huge data files via long running batch jobs that helps in filtering abstracting the
6
Illustration 2: Big Data Architecture
(Source: Component of Big Data Architecture, 2017)

meaningful data from the huge bulk. It mainly helps in reading the source files and processing
such files through writing the output to the new files and formats.
Real Time Message Ingestion
If the solution includes the real time sources then it allows the architecture to store the
real time messages for stream processing. In this, the incoming messages are directly dropped
into a particular folder for further processing. This can also be referred as stream buffering
Stream processing
It helps in filtering, aggregating and analysing the data as it allows the data to be
managed. These services are based on the Sql queries that allow the data to be sorted according
to their nature.
Analytical Data store
Many big data solutions prepared for the further analysis and this data is then served in a
structured format using a analytical tool (Zeydan and et.al., 2016). This components helps in
presenting the data through a low-latency which uses a NOSQL technology to process the
database in order to derive the metadata abstraction over data files.
Analysis and Reporting
This helps in providing the Big data solutions via reporting and analysing. It allows the
users to access the data as it includes via multidimensional layer using OLAP cube or tabular
data model.
Orchestration
It consists of the repeated data processing operations that is encapsulated in workflows
and it mainly helps in transforming the source data into various formats in order to process the
data into the analytical data store.
Hadoop provides the secured design architecture for the Big data and it also allows
the user to abstract and process the large amount of data within the Hounslow construction
company.
Various Recommendations are as follows:
HC should protect the authentication gateway in order to prevent the data breach within
the firm.
7
such files through writing the output to the new files and formats.
Real Time Message Ingestion
If the solution includes the real time sources then it allows the architecture to store the
real time messages for stream processing. In this, the incoming messages are directly dropped
into a particular folder for further processing. This can also be referred as stream buffering
Stream processing
It helps in filtering, aggregating and analysing the data as it allows the data to be
managed. These services are based on the Sql queries that allow the data to be sorted according
to their nature.
Analytical Data store
Many big data solutions prepared for the further analysis and this data is then served in a
structured format using a analytical tool (Zeydan and et.al., 2016). This components helps in
presenting the data through a low-latency which uses a NOSQL technology to process the
database in order to derive the metadata abstraction over data files.
Analysis and Reporting
This helps in providing the Big data solutions via reporting and analysing. It allows the
users to access the data as it includes via multidimensional layer using OLAP cube or tabular
data model.
Orchestration
It consists of the repeated data processing operations that is encapsulated in workflows
and it mainly helps in transforming the source data into various formats in order to process the
data into the analytical data store.
Hadoop provides the secured design architecture for the Big data and it also allows
the user to abstract and process the large amount of data within the Hounslow construction
company.
Various Recommendations are as follows:
HC should protect the authentication gateway in order to prevent the data breach within
the firm.
7
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

Also company should focus towards employing the principles of least privileges in order
to maintain the effective control over the tiered access control. It restricts the access of
the users to the minimal level.
Company should also use the antivirus protection in order to protect the large amount of
database within the company.
SECTION – B
1. Discuss about the strength and weakness of secure cloud computing and big data features.
Hounslow is based on the construction company that established in 1995 which has
grown the business with a turnover of 10 Million. It has maintained the centralised database that
support the large number of transaction processing system (Elhoseny and et.al., 2018). It is
mainly focused on decision making capabilities that require to improve slippages and its
problems.
The concept of big data and cloud computing is a major force of innovation that across
the corporate world. These are two important concepts that enable the computing resources
which provided the information technology. It is based on the high quality of efficiency and
performance to maintain and secure the large amount of data in proper manner. The cloud helps
for HC firm and enables to increase the demand of provisioning of server and its resources such
as analyse big data, storage data, bandwidth and control in proper manner. These are service
platform to support the infrastructure of organization system in effective ways.
Cloud computing is a type of model that enables for managing the demand of network
access in the computing resources (Kobusińska and et.al., 2018). These are different type of
features of secure cloud computing and big data such as Resource pooling, Easy maintenance, on
demand self-services, Availability, large network access and automatic system etc. These are
important features that applicable in the cloud system of Hounslow Construction firm but they
are faced the problem and issue related the construction slippages in the organization. In this
way, Hounslow Construction firm will make plan to develop the same type of system and
afterwards, it can compare the old system to understand the problems. These are multiple
features of cloud computing describe in given below:
Features of Cloud Computing:
Resource Pooling- It is basically term that can use in the cloud computing environment
to identify the situation of multiple client on different servers. It useful for adjusting to
8
to maintain the effective control over the tiered access control. It restricts the access of
the users to the minimal level.
Company should also use the antivirus protection in order to protect the large amount of
database within the company.
SECTION – B
1. Discuss about the strength and weakness of secure cloud computing and big data features.
Hounslow is based on the construction company that established in 1995 which has
grown the business with a turnover of 10 Million. It has maintained the centralised database that
support the large number of transaction processing system (Elhoseny and et.al., 2018). It is
mainly focused on decision making capabilities that require to improve slippages and its
problems.
The concept of big data and cloud computing is a major force of innovation that across
the corporate world. These are two important concepts that enable the computing resources
which provided the information technology. It is based on the high quality of efficiency and
performance to maintain and secure the large amount of data in proper manner. The cloud helps
for HC firm and enables to increase the demand of provisioning of server and its resources such
as analyse big data, storage data, bandwidth and control in proper manner. These are service
platform to support the infrastructure of organization system in effective ways.
Cloud computing is a type of model that enables for managing the demand of network
access in the computing resources (Kobusińska and et.al., 2018). These are different type of
features of secure cloud computing and big data such as Resource pooling, Easy maintenance, on
demand self-services, Availability, large network access and automatic system etc. These are
important features that applicable in the cloud system of Hounslow Construction firm but they
are faced the problem and issue related the construction slippages in the organization. In this
way, Hounslow Construction firm will make plan to develop the same type of system and
afterwards, it can compare the old system to understand the problems. These are multiple
features of cloud computing describe in given below:
Features of Cloud Computing:
Resource Pooling- It is basically term that can use in the cloud computing environment
to identify the situation of multiple client on different servers. It useful for adjusting to
8
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

suit each client needs without being changes (Langmead and Nellore,). This type of
feature is sharing the computing capabilities which leads to increase the resource
utilization rate.
On demand self-service- It is another feature of cloud computing to provide the services
of HC that enable the provision of cloud resource according to the demand. It has
required for Hounslow construction to provide the services where user can access the
information through online control panel. It is the prime features in cloud that offering
where use can scale the infrastructure of system.
Security- Cloud security is the important technologies that design to maintain the
security aspects of information. This feature is associated with the application to secure
and protect the information. It includes the backup where enterprises continuity can be
maintained in proper manner.
Strength
Resource Pooling is main feature of cloud computing in HC firm that help to reduce the
costs and improve the services in corporate world.
On demand self-service is playing role that help to maintain and control the situation on
time. In this way, it easily fixed the problem and issue in proper manner.
The strength of security features to protect the sensitive information of business such as
transaction processing etc. In case, it has been improved the services if the data can be
lost so that it helps to recover in proper manner (Stergiou and et.al., 2018).
Weakness
Cloud computing is providing the high availability services on demand but it is still
overwhelming the service provides. It also minimizes the connectivity during the
services.
Cloud provides the high quality of security standards but it has increased the risk if cloud
resources can share in publicly to others.
Features of big data
Raw Data Processing- It is an essential feature in big data for organizing and collecting
the relevant data in proper manner. It takes the complex data set to represent in the visual
forms through diagrams. HC firm must be collected the data from different data source in
unique formats (Rehman and e.tal., 2018)
9
feature is sharing the computing capabilities which leads to increase the resource
utilization rate.
On demand self-service- It is another feature of cloud computing to provide the services
of HC that enable the provision of cloud resource according to the demand. It has
required for Hounslow construction to provide the services where user can access the
information through online control panel. It is the prime features in cloud that offering
where use can scale the infrastructure of system.
Security- Cloud security is the important technologies that design to maintain the
security aspects of information. This feature is associated with the application to secure
and protect the information. It includes the backup where enterprises continuity can be
maintained in proper manner.
Strength
Resource Pooling is main feature of cloud computing in HC firm that help to reduce the
costs and improve the services in corporate world.
On demand self-service is playing role that help to maintain and control the situation on
time. In this way, it easily fixed the problem and issue in proper manner.
The strength of security features to protect the sensitive information of business such as
transaction processing etc. In case, it has been improved the services if the data can be
lost so that it helps to recover in proper manner (Stergiou and et.al., 2018).
Weakness
Cloud computing is providing the high availability services on demand but it is still
overwhelming the service provides. It also minimizes the connectivity during the
services.
Cloud provides the high quality of security standards but it has increased the risk if cloud
resources can share in publicly to others.
Features of big data
Raw Data Processing- It is an essential feature in big data for organizing and collecting
the relevant data in proper manner. It takes the complex data set to represent in the visual
forms through diagrams. HC firm must be collected the data from different data source in
unique formats (Rehman and e.tal., 2018)
9

Fraud Management- This feature will help to detect functionalities of fraud in the
system. When it comes to the fraud detection operations that include multiple fraud
analytics. This feature should be performed the testing procedure on the data set at any
time. It can be determined the threats quickly in the system in proper manner.
Reporting Feature- It is the most efficient features to present the data in organized form
such as Metrics and KPIs. It useful for HC firm to make decision according to the report.
It should be customised the report and target only particular data set.
Strength
Raw data processing is main feature that automatically back up of database stored in the
files.
Reporting is important feature that support the enterprise to collect and store all
information in the form of digital reports. It is generated due to the digital platform to
produce proper result or outcome (Varatharajan Manogaran and Priyan, 2018). It is
strength of HC firm to maintain and control the overall information about the
construction and other financial records.
Fraud Management is helping the organization to control the activities of unauthorised
access. It is automatically detected the unauthorised access and give the notification of
system.
Weakness
During raw data processing, it is possible that the same type of information may be
duplicated in other files. In this way, it leads to data redundancy in the memory
management.
There are challenges faced by HC firm when it has increased the risk during transaction
processing because it is very hard to identify the authentication and verification with
faceless. It is generated more risk of fraudulent in the processing.
2. Discuss about the professional practices that help the Hounslow construction to comply with
legal, ethical and social issues with the big data and cloud environment.
Professional Practices is generally use of the knowledge in the particular profession. It always
influences the business by using policies, procedures and expertise etc. It provides the
accessibility and useful information about the professional practices in Hounslow Construction
Company (Varatharajan Manogaran and Priyan, 2018).
10
system. When it comes to the fraud detection operations that include multiple fraud
analytics. This feature should be performed the testing procedure on the data set at any
time. It can be determined the threats quickly in the system in proper manner.
Reporting Feature- It is the most efficient features to present the data in organized form
such as Metrics and KPIs. It useful for HC firm to make decision according to the report.
It should be customised the report and target only particular data set.
Strength
Raw data processing is main feature that automatically back up of database stored in the
files.
Reporting is important feature that support the enterprise to collect and store all
information in the form of digital reports. It is generated due to the digital platform to
produce proper result or outcome (Varatharajan Manogaran and Priyan, 2018). It is
strength of HC firm to maintain and control the overall information about the
construction and other financial records.
Fraud Management is helping the organization to control the activities of unauthorised
access. It is automatically detected the unauthorised access and give the notification of
system.
Weakness
During raw data processing, it is possible that the same type of information may be
duplicated in other files. In this way, it leads to data redundancy in the memory
management.
There are challenges faced by HC firm when it has increased the risk during transaction
processing because it is very hard to identify the authentication and verification with
faceless. It is generated more risk of fraudulent in the processing.
2. Discuss about the professional practices that help the Hounslow construction to comply with
legal, ethical and social issues with the big data and cloud environment.
Professional Practices is generally use of the knowledge in the particular profession. It always
influences the business by using policies, procedures and expertise etc. It provides the
accessibility and useful information about the professional practices in Hounslow Construction
Company (Varatharajan Manogaran and Priyan, 2018).
10
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 17
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





