Comprehensive Risk Management Report: ENISA Big Data Security Analysis
VerifiedAdded on 2020/02/18
|16
|3661
|205
Report
AI Summary
This report provides an in-depth analysis of risk management within the context of big data, specifically focusing on the European Union Agency for Cybersecurity (ENISA). It begins with an overview of ENISA's big data infrastructure, followed by a discussion of top threats such as denial of service, malicious code, rogue certificates, inadequate security design, interception of information, nefarious activities, and identity fraud. The report identifies and evaluates various threat agents, including corporations, cybercriminals, cyber terrorists, script kiddies, hacktivists, employees, and nation-states. It also explores the impact of these threats and the probability of their occurrence. Furthermore, the report addresses strategies for minimizing the impact of threats, such as encryption, access control, and improved security design, and provides insights into threat probability trends. The study underscores the importance of robust risk management practices in safeguarding big data environments against evolving cyber threats, emphasizing the need for proactive measures to maintain data security and integrity. The report also touches upon improving the ETL process and current state of IT security.

Running head: RISK MANAGEMENT
Risk Management
Name of the Student
Name of the University
Author’s Note
Risk Management
Name of the Student
Name of the University
Author’s Note
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

RISK MANAGEMENT
Table of Contents
Introduction..........................................................................................................................2
1. Overview and ENISA big data Infrastructure.................................................................2
1.1 Overview....................................................................................................................2
2. Top Threats in Enisa and their significance....................................................................5
2.1. Most significant Threat.............................................................................................7
3. Threat agents, impact and threat probability...................................................................7
3.1. Threat Agent: Corporation........................................................................................8
3.2. Threat Agent: Cyber criminals.................................................................................8
3.3. Threat Agent: Cyber terrorists..................................................................................8
3.4. Threat Agent: Script kiddies.....................................................................................8
3.5. Threat Agent: Hacktivists or online social hackers..................................................9
3.6. Threat Agent: Employees.........................................................................................9
3.7. Threat Agent: Nation States......................................................................................9
3.8. Minimization of the Impact of the Threat.................................................................9
3.9. Threat Probability trends........................................................................................10
4. Improving ETL process.................................................................................................10
5. Current State of IT security...........................................................................................11
Conclusion.........................................................................................................................12
References..........................................................................................................................13
Table of Contents
Introduction..........................................................................................................................2
1. Overview and ENISA big data Infrastructure.................................................................2
1.1 Overview....................................................................................................................2
2. Top Threats in Enisa and their significance....................................................................5
2.1. Most significant Threat.............................................................................................7
3. Threat agents, impact and threat probability...................................................................7
3.1. Threat Agent: Corporation........................................................................................8
3.2. Threat Agent: Cyber criminals.................................................................................8
3.3. Threat Agent: Cyber terrorists..................................................................................8
3.4. Threat Agent: Script kiddies.....................................................................................8
3.5. Threat Agent: Hacktivists or online social hackers..................................................9
3.6. Threat Agent: Employees.........................................................................................9
3.7. Threat Agent: Nation States......................................................................................9
3.8. Minimization of the Impact of the Threat.................................................................9
3.9. Threat Probability trends........................................................................................10
4. Improving ETL process.................................................................................................10
5. Current State of IT security...........................................................................................11
Conclusion.........................................................................................................................12
References..........................................................................................................................13

RISK MANAGEMENT
Introduction
Big data refers to the voluminous amount of data that can be mined, examined and
utilized for business purposes. The big data can be structured, semi structured and unstructured.
Big data can be utilized to analyze the different pattern and structure of data, which can be
utilized to understand the trends in data and human behavior (Wu et al., 2014). The big data
generally remains accessible to public and therefore, different security issues arise in the
accessing and using the data. These threats are to be removed from the system in order to protect
the system from attackers. The report elaborates the security issues faced by Enisa, the threat
infrastructure, different types of threats and key threat agent (Inukollu, Arsi & Ravuri, 2014).
The impact of the threat and ETL process is elaborated in the following paragraphs.
1. Overview and ENISA big data Infrastructure
1.1 Overview
The case study discusses the different threats associated with big data, mainly with the
replication of big data storage and the frequency of outsourcing the data. This leads to the
development of new types of data breaches, leakage and degradation threat specific to big data.
ENISA is facing a significant security and privacy issue that reflects on the performance level of
the organization. The case study presents and discusses different big data threats and the lack of
countermeasures to eliminate those threats into the system (Wright & De Hert, 2012). The major
Introduction
Big data refers to the voluminous amount of data that can be mined, examined and
utilized for business purposes. The big data can be structured, semi structured and unstructured.
Big data can be utilized to analyze the different pattern and structure of data, which can be
utilized to understand the trends in data and human behavior (Wu et al., 2014). The big data
generally remains accessible to public and therefore, different security issues arise in the
accessing and using the data. These threats are to be removed from the system in order to protect
the system from attackers. The report elaborates the security issues faced by Enisa, the threat
infrastructure, different types of threats and key threat agent (Inukollu, Arsi & Ravuri, 2014).
The impact of the threat and ETL process is elaborated in the following paragraphs.
1. Overview and ENISA big data Infrastructure
1.1 Overview
The case study discusses the different threats associated with big data, mainly with the
replication of big data storage and the frequency of outsourcing the data. This leads to the
development of new types of data breaches, leakage and degradation threat specific to big data.
ENISA is facing a significant security and privacy issue that reflects on the performance level of
the organization. The case study presents and discusses different big data threats and the lack of
countermeasures to eliminate those threats into the system (Wright & De Hert, 2012). The major
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

RISK MANAGEMENT
problem lies in the defective security system of the organization that is essential for securing the
data. ENISA elaborates the different threats associated with the big data and the different part of
the society affected by it. The insecure system of big data is reason fro increasing cyber attacks
and therefore should be eliminated. Powerful approaches should be undertaken in order to fight
the threats associated with big data. The case study further elaborates the concepts of threat
landscape by comparing the threats associated with big data. It focuses on the threats, assets and
the importance of the widely used data systems. The case study is of increasing use for
developing a detailed risk management plan for ensuring security in big data. The big data
architecture discussed in this case study is complex and therefore, this high level conceptual
model requires increasing security requirements ( ENISA 2017). The architecture of big data
systems includes different data sources, integration processes, data storage and different
computing models. These layers have varied function and the work in sync. Cloud computing
can be deployed as an infrastructure layer to meet the requirements of effective storage of big
data, which includes cost effectiveness, elasticity and ability of scaling (Gonzalez et al., 2012).
However, the storage of data in cloud has different security issues that are discussed in the case
study.
problem lies in the defective security system of the organization that is essential for securing the
data. ENISA elaborates the different threats associated with the big data and the different part of
the society affected by it. The insecure system of big data is reason fro increasing cyber attacks
and therefore should be eliminated. Powerful approaches should be undertaken in order to fight
the threats associated with big data. The case study further elaborates the concepts of threat
landscape by comparing the threats associated with big data. It focuses on the threats, assets and
the importance of the widely used data systems. The case study is of increasing use for
developing a detailed risk management plan for ensuring security in big data. The big data
architecture discussed in this case study is complex and therefore, this high level conceptual
model requires increasing security requirements ( ENISA 2017). The architecture of big data
systems includes different data sources, integration processes, data storage and different
computing models. These layers have varied function and the work in sync. Cloud computing
can be deployed as an infrastructure layer to meet the requirements of effective storage of big
data, which includes cost effectiveness, elasticity and ability of scaling (Gonzalez et al., 2012).
However, the storage of data in cloud has different security issues that are discussed in the case
study.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
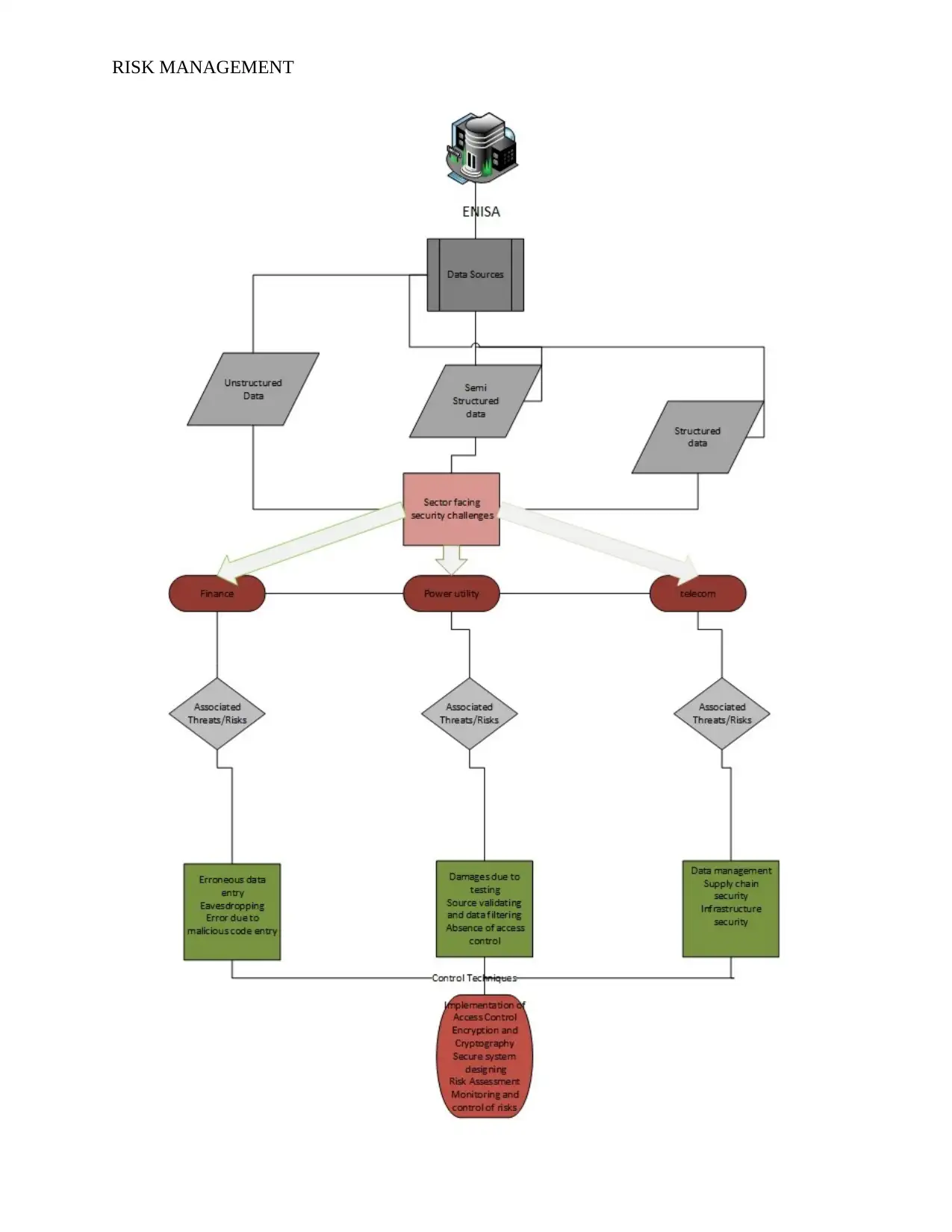
RISK MANAGEMENT

RISK MANAGEMENT
Figure 1: Representing the ENISA big data security Infrastructure
(Source: created by author using MS Visio)
2. Top Threats in Enisa and their significance
ENISA deals with the storage of different types of data, which can be structured, semi
structured or unstructured. The threats associated with the storage of data are elaborated in the
following paragraphs ( ENISA 2017)-
1) Denial of service- Big data components are prone to this attack. This attack deals with
removing the components from the network in order to exploit its vulnerabilities. In this attack,
the attacker makes the resources unavailable to the authorized user, temporarily or sometimes
permanently (Tan et al., 2014). This attack results in the decrease of system performance
considerably and ofter leads to the loss of important data and resources.
The assets that are mainly targeted by this attack are servers and networks. The risk level
of this particular is generally low and can be avoided with a proper risk management strategy.
2) Threat resulting from malicious code or software activity- this is one of the most
significant threats associated with the component of big data. Different threat agents such as
exploit kits, worms, viruses, Trojan horse, back doors and trap doors, service spoofing, injection
attacks are important responsible for this threat (Seshardi et al., 2012). Threat agents are
deployed into the system and with the help of these malicious codes, the attacker manipulate the
data of the infected system. The malware-infected nodes of the system may send malicious
Figure 1: Representing the ENISA big data security Infrastructure
(Source: created by author using MS Visio)
2. Top Threats in Enisa and their significance
ENISA deals with the storage of different types of data, which can be structured, semi
structured or unstructured. The threats associated with the storage of data are elaborated in the
following paragraphs ( ENISA 2017)-
1) Denial of service- Big data components are prone to this attack. This attack deals with
removing the components from the network in order to exploit its vulnerabilities. In this attack,
the attacker makes the resources unavailable to the authorized user, temporarily or sometimes
permanently (Tan et al., 2014). This attack results in the decrease of system performance
considerably and ofter leads to the loss of important data and resources.
The assets that are mainly targeted by this attack are servers and networks. The risk level
of this particular is generally low and can be avoided with a proper risk management strategy.
2) Threat resulting from malicious code or software activity- this is one of the most
significant threats associated with the component of big data. Different threat agents such as
exploit kits, worms, viruses, Trojan horse, back doors and trap doors, service spoofing, injection
attacks are important responsible for this threat (Seshardi et al., 2012). Threat agents are
deployed into the system and with the help of these malicious codes, the attacker manipulate the
data of the infected system. The malware-infected nodes of the system may send malicious
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

RISK MANAGEMENT
commands to the targeted servers thus spreading the infection from system to system. This type
of threat is easily spread and therefore, eliminating this treat from the system becomes
increasingly essential (Theoharidou, Tsalis & Gritzalis, 2013).
The assets targeted by this attack include database management system, relational SQL
and computing infrastructure model.
3) Generation and use of rogue certificates can act as a threat in big data. Signing into the
devices and the media encryption can be bypassed by the use of these threat agents in order to
implement an attack. These certificates are used to access data storage, which in turn leads to the
leakage of the data, and its misuse (Pearson, 2013).
The assets targeted by the threat include Data, big data analytics, software and hardware.
4) Inadequate design and planning of the security features is a major security threat to big
data. The inadequate adaption of security measures may lead to the manipulation of data and
production of ill-protected copies of data. This threat challenges the security system of big data
and proper risk mitigation technique is needed to be implemented in order to avoid this risk. This
threat can be a result of storage of redundant data present in the database (Theoharidou et al.,
2013).
The assets targeted by these attacks include data, software and storage infrastructure
models.
5) Interception of Information- The offenders can intercept communication between the
transfer of data in different nodes by targeting the communication links.
commands to the targeted servers thus spreading the infection from system to system. This type
of threat is easily spread and therefore, eliminating this treat from the system becomes
increasingly essential (Theoharidou, Tsalis & Gritzalis, 2013).
The assets targeted by this attack include database management system, relational SQL
and computing infrastructure model.
3) Generation and use of rogue certificates can act as a threat in big data. Signing into the
devices and the media encryption can be bypassed by the use of these threat agents in order to
implement an attack. These certificates are used to access data storage, which in turn leads to the
leakage of the data, and its misuse (Pearson, 2013).
The assets targeted by the threat include Data, big data analytics, software and hardware.
4) Inadequate design and planning of the security features is a major security threat to big
data. The inadequate adaption of security measures may lead to the manipulation of data and
production of ill-protected copies of data. This threat challenges the security system of big data
and proper risk mitigation technique is needed to be implemented in order to avoid this risk. This
threat can be a result of storage of redundant data present in the database (Theoharidou et al.,
2013).
The assets targeted by these attacks include data, software and storage infrastructure
models.
5) Interception of Information- The offenders can intercept communication between the
transfer of data in different nodes by targeting the communication links.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

RISK MANAGEMENT
The assets that are mainly targeted by this attack include data, applications and the back
end services.
6) Threats from nefarious activities: this threat agent make use of particular tool and
software to perform malicious activities
7) Identity fraud: this threat results in the access of personal and confidential data such as
information of credit card, payment and billing details by impersonation of someone else. This
threat mainly arises due to the storage of data in cloud and therefore implementing this type of
attack becomes easier for the attacker (Roberts, Indermaur & Spiranovic, 2013).
The assets targeted by these threats include personal identifiable information, \application
and back end services and servers.
2.1. Most significant Threat
Out of the various threats discussed above, the most significant threat that is associated
with the big data is definitely the loss of data due to the effect of malicious code and software
activity. The threats includes malicious ransomware, viruses, Trojan horses and injection attacks.
The use of insecure API is a major cause of this vulnerability (Chen & Zhao, 2012).
The threat arising due to the acts of malicious programs and codes are most significant
because the attacker can easily manipulate the data present with the help of the malicious codes.
The threat can be easily spread by spreading of the malicious code (Pavlyushchik, 2014).
Hacking is a process of inducing malicious code into the system and after installing the
malicious code, the attacker gains full control over the system.
3. Threat agents, impact and threat probability
The assets that are mainly targeted by this attack include data, applications and the back
end services.
6) Threats from nefarious activities: this threat agent make use of particular tool and
software to perform malicious activities
7) Identity fraud: this threat results in the access of personal and confidential data such as
information of credit card, payment and billing details by impersonation of someone else. This
threat mainly arises due to the storage of data in cloud and therefore implementing this type of
attack becomes easier for the attacker (Roberts, Indermaur & Spiranovic, 2013).
The assets targeted by these threats include personal identifiable information, \application
and back end services and servers.
2.1. Most significant Threat
Out of the various threats discussed above, the most significant threat that is associated
with the big data is definitely the loss of data due to the effect of malicious code and software
activity. The threats includes malicious ransomware, viruses, Trojan horses and injection attacks.
The use of insecure API is a major cause of this vulnerability (Chen & Zhao, 2012).
The threat arising due to the acts of malicious programs and codes are most significant
because the attacker can easily manipulate the data present with the help of the malicious codes.
The threat can be easily spread by spreading of the malicious code (Pavlyushchik, 2014).
Hacking is a process of inducing malicious code into the system and after installing the
malicious code, the attacker gains full control over the system.
3. Threat agents, impact and threat probability

RISK MANAGEMENT
The key threat agents, impact of the threat and the threat probability of ENISA are
elaborated in the following paragraphs-
3.1. Threat Agent: Corporation
The threat agents associated with the big data security threats include the organization
that uses offensive tactics to gain competitive advantage over their competitors. These
organizations have capabilities to manipulate the data.
3.2. Threat Agent: Cyber criminals
Cyber criminal is one of the most important threat agents associated with the security of
big data. The cyber criminals may steal and manipulate the data by hacking into the system and
make use of that data for financial benefit. The attacks launched by the cyber criminals are
complex and therefore proper risk management strategy is needed to be implemented, which
includes proper security of the data.
3.3. Threat Agent: Cyber terrorists
Cyber terrorist are more dangerous than cyber criminals and one of the most significant
threat agents (Taylor, Fritsch & Liederbach, 2014). Cyber terrorists mainly target the critical
infrastructures, which includes energy production, telecommunication and public health. They
target these organizations as failure of this organization or data breach in the organization causes
severe impact in the society and government.
3.4. Threat Agent: Script kiddies
Script kiddies are minor threat agents as they pose an attack with an already developed
program or codes. They do not have power to manipulate or break into a proper security system.
The key threat agents, impact of the threat and the threat probability of ENISA are
elaborated in the following paragraphs-
3.1. Threat Agent: Corporation
The threat agents associated with the big data security threats include the organization
that uses offensive tactics to gain competitive advantage over their competitors. These
organizations have capabilities to manipulate the data.
3.2. Threat Agent: Cyber criminals
Cyber criminal is one of the most important threat agents associated with the security of
big data. The cyber criminals may steal and manipulate the data by hacking into the system and
make use of that data for financial benefit. The attacks launched by the cyber criminals are
complex and therefore proper risk management strategy is needed to be implemented, which
includes proper security of the data.
3.3. Threat Agent: Cyber terrorists
Cyber terrorist are more dangerous than cyber criminals and one of the most significant
threat agents (Taylor, Fritsch & Liederbach, 2014). Cyber terrorists mainly target the critical
infrastructures, which includes energy production, telecommunication and public health. They
target these organizations as failure of this organization or data breach in the organization causes
severe impact in the society and government.
3.4. Threat Agent: Script kiddies
Script kiddies are minor threat agents as they pose an attack with an already developed
program or codes. They do not have power to manipulate or break into a proper security system.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

RISK MANAGEMENT
3.5. Threat Agent: Hacktivists or online social hackers
These are minor threat agents as well. They make use of computer systems to protests
and promote their views. Hacktivists mainly target high profile websites and agencies in order to
reach a wider audience.
3.6. Threat Agent: Employees
Employees of an organization have a significant knowledge about the security systems of
the organization in which they are working. Therefore, employees can be an important threat
agent. They can easily manipulate and modify the data and therefore considered as threat insider.
3.7. Threat Agent: Nation States
This is a sophisticated cyber criminal as they are capable of launching well structured
attacks using different cyber weapons. They have high level of skills and expertise and therefore,
it can be considered as a most prominent threat in cyber world.
3.8. Minimization of the Impact of the Threat
There are different threats associated with the use and access of big data and
minimization of the impact of these threats are essential. The different process that can be
implemented to minimize the impact of the threat are listed below-
1) Proper security measures such as encryption and cryptography can be implemented in
order to protect the data and prevent it from unauthorized access. Ensuring the encryption of data
and proper cryptographic method can be beneficial for an organization as it considerably helps in
data protection thus ensuring the protection of big data (Stallings & Tahiliani, 2014).
3.5. Threat Agent: Hacktivists or online social hackers
These are minor threat agents as well. They make use of computer systems to protests
and promote their views. Hacktivists mainly target high profile websites and agencies in order to
reach a wider audience.
3.6. Threat Agent: Employees
Employees of an organization have a significant knowledge about the security systems of
the organization in which they are working. Therefore, employees can be an important threat
agent. They can easily manipulate and modify the data and therefore considered as threat insider.
3.7. Threat Agent: Nation States
This is a sophisticated cyber criminal as they are capable of launching well structured
attacks using different cyber weapons. They have high level of skills and expertise and therefore,
it can be considered as a most prominent threat in cyber world.
3.8. Minimization of the Impact of the Threat
There are different threats associated with the use and access of big data and
minimization of the impact of these threats are essential. The different process that can be
implemented to minimize the impact of the threat are listed below-
1) Proper security measures such as encryption and cryptography can be implemented in
order to protect the data and prevent it from unauthorized access. Ensuring the encryption of data
and proper cryptographic method can be beneficial for an organization as it considerably helps in
data protection thus ensuring the protection of big data (Stallings & Tahiliani, 2014).
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

RISK MANAGEMENT
2) Access control: Access control is another effective process of data security. Access
control prevents the unauthorized access of data. Data theft is a major issue in storage of data in
cloud computing. The host of the cloud service provider should implement access control in
order to prevent the unauthorized access of data (Brucker et al., 2012).
3) Implementing a better security design can help in protection of data that is associated
with the insecure APIs.
4) Training the staffs of the organization is also essential to prevent the erroneous data
entry and data manipulation by mistake. Creating an awareness of information security and
taking proper measures is essential for ensuring the security of big data.
3.9. Threat Probability trends
The threat associated with the big data is increasing day by data and the attackers are
planning different and new attack technologies every day. The threat probability can be
decreased by ensuring proper security measures in protecting the data. The threat of data
breaches and data manipulation is increasing, which should be controlled in order to ensure
proper data security. Proper measures can be implemented to get a positive result and the
identified threats if not controlled can definitely be mitigated.
4. Improving ETL process
ETL refers to the ENISA threat landscape that reports the different threats associated
with the organization. ETL identifies the threats that are applicable to the information and
communication technology assets that are associated with big data (ENISA 2017). The major
problem with the Enisa threat landscape is that, it only identifies the threats associated with the
2) Access control: Access control is another effective process of data security. Access
control prevents the unauthorized access of data. Data theft is a major issue in storage of data in
cloud computing. The host of the cloud service provider should implement access control in
order to prevent the unauthorized access of data (Brucker et al., 2012).
3) Implementing a better security design can help in protection of data that is associated
with the insecure APIs.
4) Training the staffs of the organization is also essential to prevent the erroneous data
entry and data manipulation by mistake. Creating an awareness of information security and
taking proper measures is essential for ensuring the security of big data.
3.9. Threat Probability trends
The threat associated with the big data is increasing day by data and the attackers are
planning different and new attack technologies every day. The threat probability can be
decreased by ensuring proper security measures in protecting the data. The threat of data
breaches and data manipulation is increasing, which should be controlled in order to ensure
proper data security. Proper measures can be implemented to get a positive result and the
identified threats if not controlled can definitely be mitigated.
4. Improving ETL process
ETL refers to the ENISA threat landscape that reports the different threats associated
with the organization. ETL identifies the threats that are applicable to the information and
communication technology assets that are associated with big data (ENISA 2017). The major
problem with the Enisa threat landscape is that, it only identifies the threats associated with the

RISK MANAGEMENT
big data assets. The process of ETL can be improvised by including the risk agent and the
classification of risks into the report. The attack patterns included in the report can be identified
and included in the report in details (Cherdantseva et al,. 2016). The threats agents have
increased sophistication of their attack using more innovative tools and therefore ETL should
include a more through scanning in order to identify the source of the risk. The pattern of attack
should be properly indicated in the report so that managing of the threat becomes easier. ENISA
is a center of network and information security expertise and therefore, proper detailing of the
report, which includes the results of the identifies threat becomes necessary need. By
improvising the process of ETL, the different attacks related to big data can be controlled or
mitigated and therefore ETL process should definitely be improvised by ENISA.
5. Current State of IT security
The IT security of ENISA can be improved and therefore ENISA should not be satisfied
with the current security state. The increasing concern with the security of big data is alarming
and therefore proper measures are needed to be taken as soon as possible. Absence of proper and
up to date security essentials are one of the major reasons of the increasing threats and data loss.
Different security measures discussed in this report can be considered in order to increase the
security and effectively of the big data (Von Solms & Van Niekerk, 2013). The different security
measures are encryption, access control and proper training of the users along with the use of up
to date and well designed security systems. These security measures are needed to be taken in
order to reduce the risks associated with big data. proper risk control ad mitigation is essential in
order to lessen the impact of the risk. ENISA lacks proper risk management strategy. Moreover,
the use of insecure APIs should be avoided in order to eliminate the risk of intrusion into the
system. Proper intrusion detection system and firewall should be implemented in order to protect
big data assets. The process of ETL can be improvised by including the risk agent and the
classification of risks into the report. The attack patterns included in the report can be identified
and included in the report in details (Cherdantseva et al,. 2016). The threats agents have
increased sophistication of their attack using more innovative tools and therefore ETL should
include a more through scanning in order to identify the source of the risk. The pattern of attack
should be properly indicated in the report so that managing of the threat becomes easier. ENISA
is a center of network and information security expertise and therefore, proper detailing of the
report, which includes the results of the identifies threat becomes necessary need. By
improvising the process of ETL, the different attacks related to big data can be controlled or
mitigated and therefore ETL process should definitely be improvised by ENISA.
5. Current State of IT security
The IT security of ENISA can be improved and therefore ENISA should not be satisfied
with the current security state. The increasing concern with the security of big data is alarming
and therefore proper measures are needed to be taken as soon as possible. Absence of proper and
up to date security essentials are one of the major reasons of the increasing threats and data loss.
Different security measures discussed in this report can be considered in order to increase the
security and effectively of the big data (Von Solms & Van Niekerk, 2013). The different security
measures are encryption, access control and proper training of the users along with the use of up
to date and well designed security systems. These security measures are needed to be taken in
order to reduce the risks associated with big data. proper risk control ad mitigation is essential in
order to lessen the impact of the risk. ENISA lacks proper risk management strategy. Moreover,
the use of insecure APIs should be avoided in order to eliminate the risk of intrusion into the
system. Proper intrusion detection system and firewall should be implemented in order to protect
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 16
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





