IT Risk Management Report: ENISA Big Data Threat Landscape Case Study
VerifiedAdded on 2020/07/22
|13
|3579
|55
Report
AI Summary
This report provides an in-depth analysis of IT risk management within the realm of big data, drawing upon the ENISA Big Data Threat Landscape 2016 case study. The report begins with an overview of big data, its characteristics (volume, variety, velocity), and its growing importance in various sectors. It then identifies the most significant threat as malicious code/software/activity, detailing examples such as exploit kits, worms, and Trojans. Key threat agents, including corporations, cybercriminals, cyber terrorists, script kiddies, online social hackers, employees, and nation states, are categorized and their potential impacts are discussed. The report also explores strategies to reduce the impact of these threats, emphasizing the use of good practices and countermeasures, such as cryptography. Furthermore, it delves into the improvement of the ETL (Extract, Transform, Load) process, highlighting the importance of enhanced security measures and the implementation of security controls based on ISO and COBIT standards. The report underscores the need for a comprehensive approach to IT risk management in big data to safeguard against data breaches, unauthorized access, and other potential vulnerabilities.

IT Risk
Management
Management
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

TABLE OF CONTENTS
Introduction......................................................................................................................................1
1. Overview of the case study.....................................................................................................1
2. The most significant threat for big data..................................................................................4
3. Identification of key threat agents and what can be done to reduce its impact on the system5
4. Discussing the improvement for the ETL process .................................................................6
5. Summing up the case study ....................................................................................................8
REFERENCES ...............................................................................................................................9
Introduction......................................................................................................................................1
1. Overview of the case study.....................................................................................................1
2. The most significant threat for big data..................................................................................4
3. Identification of key threat agents and what can be done to reduce its impact on the system5
4. Discussing the improvement for the ETL process .................................................................6
5. Summing up the case study ....................................................................................................8
REFERENCES ...............................................................................................................................9

Introduction
Big Data is the accumulation of large data sets that cannot be processed by using
conventional methods. The large and complex data is collected by big data from wide sources
such as social sites like Facebook, twitter, e-commerce sites, telecom organization etc . Since the
use of big data has increased over years by organization so the systems of big data are becoming
threat targets by threat agents (ENISA Big Data security infrastructure, 2017). Appropriate
practices need to be adopted in order to reduce the impact of big data threats. The present
assignment will answer various questions based on case study of ENISA Big Data Threat
Landscape 2016.
1. Overview of the case study
In this case study, the European Union Agency for Network and Information Security
(ENISA) which is a security expertise for EU, and its citizens as analysed the threats that are
based on with big data. Big data is generally used in organization for collecting and storing of
large and complex data (Cohen, Krishnamoorthy and Wright, 2017). There are 3 Vs that lead to
the foundation of big data .They are as follows -:
Volume which is associated with quantity of data
Variety refers to number of types of data
Velocity refers to the speed of data processing.
The big data practitioner makes use of various methods to process all 3 V's. In the recent years
big data technology has gained huge name and success and is expected to play an important role
by affecting several prospects of social groups ranging from food security, health and smart
cities. The potential impact of big data is acknowledged by the European Commission in a data
driven economy by outlining plans on big data (Waemustafa and Sukri, 2016).
In order to facilitate scientific analysis of data and exploitation, big data project will be
launched and planned in various agencies of Europe and around the world. The technologies of
big data are also used in various military applications such as fighting terrorism, collecting and
evaluating intelligence from heterogeneous sources. In the recent years data intensive
environments have adopted a big data approach. For an instance Facebook, which is known for
storing the large and complex datasets worldwide (Brustbauer, 2016). In complex organizations
and communities the applications of big data can provide an efficiency and effectiveness in
1
Big Data is the accumulation of large data sets that cannot be processed by using
conventional methods. The large and complex data is collected by big data from wide sources
such as social sites like Facebook, twitter, e-commerce sites, telecom organization etc . Since the
use of big data has increased over years by organization so the systems of big data are becoming
threat targets by threat agents (ENISA Big Data security infrastructure, 2017). Appropriate
practices need to be adopted in order to reduce the impact of big data threats. The present
assignment will answer various questions based on case study of ENISA Big Data Threat
Landscape 2016.
1. Overview of the case study
In this case study, the European Union Agency for Network and Information Security
(ENISA) which is a security expertise for EU, and its citizens as analysed the threats that are
based on with big data. Big data is generally used in organization for collecting and storing of
large and complex data (Cohen, Krishnamoorthy and Wright, 2017). There are 3 Vs that lead to
the foundation of big data .They are as follows -:
Volume which is associated with quantity of data
Variety refers to number of types of data
Velocity refers to the speed of data processing.
The big data practitioner makes use of various methods to process all 3 V's. In the recent years
big data technology has gained huge name and success and is expected to play an important role
by affecting several prospects of social groups ranging from food security, health and smart
cities. The potential impact of big data is acknowledged by the European Commission in a data
driven economy by outlining plans on big data (Waemustafa and Sukri, 2016).
In order to facilitate scientific analysis of data and exploitation, big data project will be
launched and planned in various agencies of Europe and around the world. The technologies of
big data are also used in various military applications such as fighting terrorism, collecting and
evaluating intelligence from heterogeneous sources. In the recent years data intensive
environments have adopted a big data approach. For an instance Facebook, which is known for
storing the large and complex datasets worldwide (Brustbauer, 2016). In complex organizations
and communities the applications of big data can provide an efficiency and effectiveness in
1
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

decision making. However on the other side, besides the benefits of big data there are number of
security risks and threats that are faced by big data system.
The threat agents are increasingly attacking the big data systems. The threats that have been
identified in the big data can be related to the high replication in the big data storage which may
result in leakage, breach and degradation threats. There is a significant privacy and data
protection impact on big data as the extra information which is produced may have an impact on
data leak and failure (Rampi and Viswanathan, 2016). This case study makes use of threat
landscape and good practice guide in order to understand and evaluate the actual state of security
in the area of big data. There is no alignment of interest by asset owners in the area of big data
and this may also lead to conflict. So, this leads to the creation of complete ecosystem where the
countermeasure need to planned and executed. The overall risks in the area of big data can be
reduced by applying basic privacy and security best practices. This case study recognizes big
data assets,examines the influence of these assets to threats, lists agents of these threat ,takes into
consideration weaknesses and risks and points to future practices and new researches in the
order to cope up with these threats in big data field. A gap analysis is provided in this case study,
which will represent the identified threats of big data and countermeasures that have identified
2
security risks and threats that are faced by big data system.
The threat agents are increasingly attacking the big data systems. The threats that have been
identified in the big data can be related to the high replication in the big data storage which may
result in leakage, breach and degradation threats. There is a significant privacy and data
protection impact on big data as the extra information which is produced may have an impact on
data leak and failure (Rampi and Viswanathan, 2016). This case study makes use of threat
landscape and good practice guide in order to understand and evaluate the actual state of security
in the area of big data. There is no alignment of interest by asset owners in the area of big data
and this may also lead to conflict. So, this leads to the creation of complete ecosystem where the
countermeasure need to planned and executed. The overall risks in the area of big data can be
reduced by applying basic privacy and security best practices. This case study recognizes big
data assets,examines the influence of these assets to threats, lists agents of these threat ,takes into
consideration weaknesses and risks and points to future practices and new researches in the
order to cope up with these threats in big data field. A gap analysis is provided in this case study,
which will represent the identified threats of big data and countermeasures that have identified
2
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
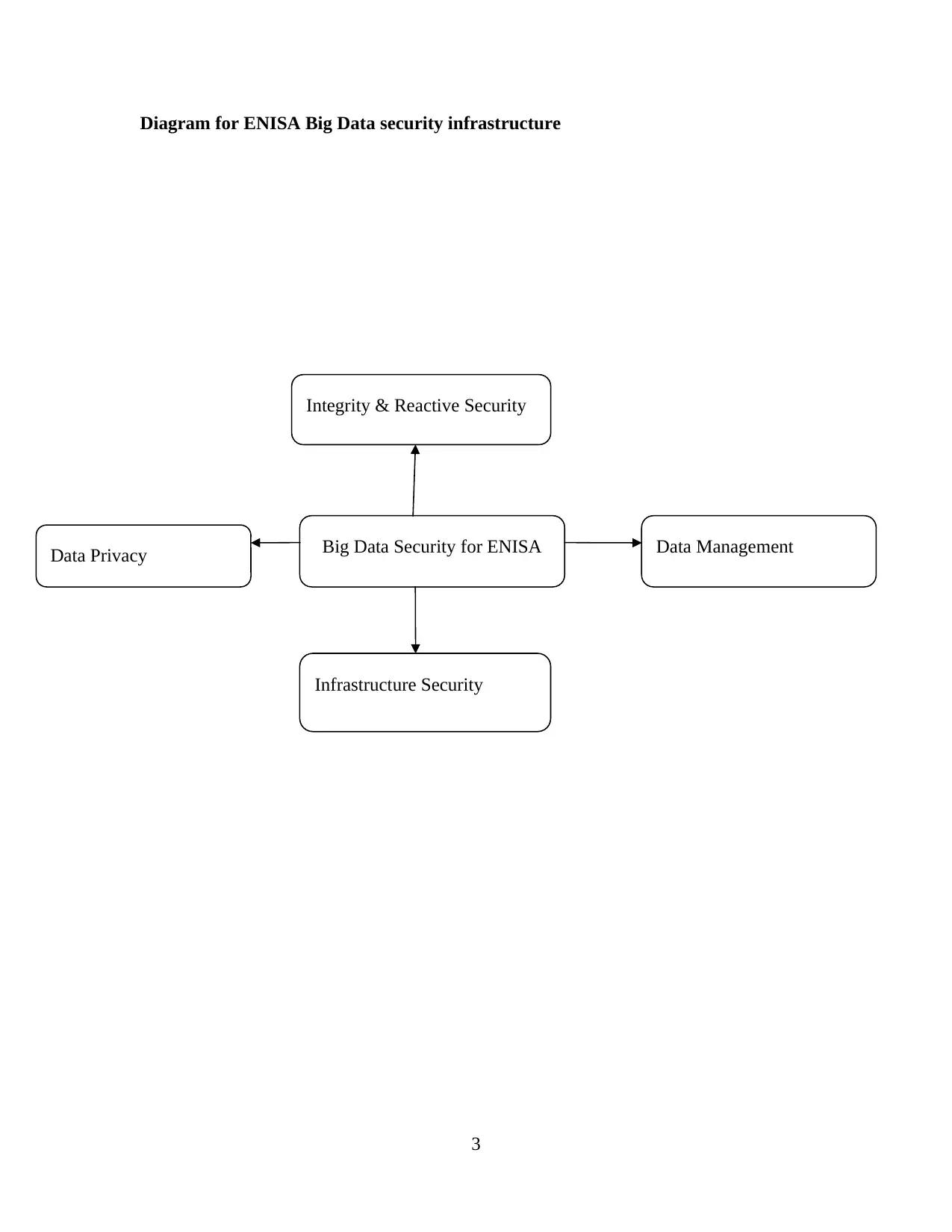
Diagram for ENISA Big Data security infrastructure
3
Big Data Security for ENISA Data Management
Integrity & Reactive Security
Data Privacy
Infrastructure Security
3
Big Data Security for ENISA Data Management
Integrity & Reactive Security
Data Privacy
Infrastructure Security

2. The most significant threat for big data
The malicious code/software/activity can be regarded as the most dangerous threat for the
big data as it affects almost all the divisions Information and Communication Technology(ICT)
of an infrastructure (Patrick and Fields, 2017). The examples of such type of threats can be: Explore Kits – This causes infections related to virus and malware Worms – In order to send copies to other nodes it may be distributed by using network. Trojans – This will aid unauthorized access to a computer system. Backdoors and trapdoors – These are undocumented entry points into computer program
that are inserted by a programmer to grant remote access to the program.
Service spoofing – It is a type of attack in which the malicious party inject false data in
order to gain access to the system.
In the field of big data, the targeted commands can be send by malware infected nodes to
other servers and their operations can be manipulated. As the worms replicate themselves,
multiple copies can be sent to other nodes thus affecting the behaviour of all components that are
working in the network. In order to facilitate access to devices particularly in context with
advance technology there are chances that the vendors of big data tools can install firmware with
access code or some hidden functionality. For an instance lets consider an example of how the
hacking with malicious code take place in the area of big data. The outcome of this hacking will
be a fault will be generated in the Hadoop logging system (Olesen, 2016).
In order to recognize potential attacks Hadoop server logs are used by System
administration. A demonstration of this hack needs a service known as flume,stream logs in SQL
based Hadoop data storage (Hcatalog). the attacker runs a malicious script and the results are
altered by changing log data before streaming flume in Hcatalog. Even though the Hadoop
services are working as per the expectation the logs can be corrupted. In the distributed
programming framework there can also be a danger of malicious software. There is a usage of
parallel computation in distributed programming frameworks and may not have trusted
components. For an instance, there is a split of input file into many chunks in the Map Reduce
frameworks: During the initial phase the mapper will reads data, performs computational and
results. In the next phase,the work is done by the reducer on these pairs and outputs the results.
The major problem is how to protect the mapper as the untrusted mapper may modify the
outputs. If the data sets are a large, it becomes difficult to recognize the malicious mappers.
4
The malicious code/software/activity can be regarded as the most dangerous threat for the
big data as it affects almost all the divisions Information and Communication Technology(ICT)
of an infrastructure (Patrick and Fields, 2017). The examples of such type of threats can be: Explore Kits – This causes infections related to virus and malware Worms – In order to send copies to other nodes it may be distributed by using network. Trojans – This will aid unauthorized access to a computer system. Backdoors and trapdoors – These are undocumented entry points into computer program
that are inserted by a programmer to grant remote access to the program.
Service spoofing – It is a type of attack in which the malicious party inject false data in
order to gain access to the system.
In the field of big data, the targeted commands can be send by malware infected nodes to
other servers and their operations can be manipulated. As the worms replicate themselves,
multiple copies can be sent to other nodes thus affecting the behaviour of all components that are
working in the network. In order to facilitate access to devices particularly in context with
advance technology there are chances that the vendors of big data tools can install firmware with
access code or some hidden functionality. For an instance lets consider an example of how the
hacking with malicious code take place in the area of big data. The outcome of this hacking will
be a fault will be generated in the Hadoop logging system (Olesen, 2016).
In order to recognize potential attacks Hadoop server logs are used by System
administration. A demonstration of this hack needs a service known as flume,stream logs in SQL
based Hadoop data storage (Hcatalog). the attacker runs a malicious script and the results are
altered by changing log data before streaming flume in Hcatalog. Even though the Hadoop
services are working as per the expectation the logs can be corrupted. In the distributed
programming framework there can also be a danger of malicious software. There is a usage of
parallel computation in distributed programming frameworks and may not have trusted
components. For an instance, there is a split of input file into many chunks in the Map Reduce
frameworks: During the initial phase the mapper will reads data, performs computational and
results. In the next phase,the work is done by the reducer on these pairs and outputs the results.
The major problem is how to protect the mapper as the untrusted mapper may modify the
outputs. If the data sets are a large, it becomes difficult to recognize the malicious mappers.
4
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

This threat is significant because it will attack the Hadoop server log systems and also the
outputs can changed by the untrusted mapper in the map reducer framework (Meyer and Reniers,
2016).
Identification of key threat agents and what can be done to reduce its impact on the system
3. Identification of key threat agents and what can be done to reduce its impact on the system
The various categories of threat agents can be as follows -:
Corporation - These are associated with system or enterprises that are involved in offending
tactics. They can be considered as aggressive threat agents and their main goal is to make a
competing benefit over competition. The significant capabilities are possessed by corporation
depending upon their size and sector. This may range from technology to ability of human
engineering, particularly in the field of expertise.
Cyber criminals – There nature is more hostile. The level of skill is higher and their motivation is
usually to gain financial profit (Lewis, Warner and Green, 2016).
Cyber terrorists- There is an expansion of activities by these cyber terrorists and they get
involve in cyber-attacks. Their abilities may range from low to high and main motivation is
political or religious. The critical infrastructures such as public health, telecommunication
department are the preferred targets of cyber terrorists. Such type of target is being selected by
these terrorist as their occurrence will have an adverse impact on government and society. In the
analysis of public material , the image of cyber terrorists is still not clear.
Script Kiddies – They are not skilled people who make use of scripts, program that are made by
others in order to attack computer system and disfigure websites.
Online social hackers – In order to protect and promote their cause the online social hackers
make use of computer systems. They are socially and politically motivated people. The high
profile websites, corporations, intelligence agencies are mainly targets by such hackers.
Employees- In a company they are mainly referred to security guards, staff, contractors etc. An
inside access to company's resources can be attacked by these people (Hallikas and Lintukangas,
2016). In order to place an effective attack against assets of their organisation these type threat
agents have a significant amount of knowledge.
Nation states – They may possess offending cyber abilities and can be used against an adversary.
The consideration of cyber weapons due to deployment of sophisticated attacks has made nation
5
outputs can changed by the untrusted mapper in the map reducer framework (Meyer and Reniers,
2016).
Identification of key threat agents and what can be done to reduce its impact on the system
3. Identification of key threat agents and what can be done to reduce its impact on the system
The various categories of threat agents can be as follows -:
Corporation - These are associated with system or enterprises that are involved in offending
tactics. They can be considered as aggressive threat agents and their main goal is to make a
competing benefit over competition. The significant capabilities are possessed by corporation
depending upon their size and sector. This may range from technology to ability of human
engineering, particularly in the field of expertise.
Cyber criminals – There nature is more hostile. The level of skill is higher and their motivation is
usually to gain financial profit (Lewis, Warner and Green, 2016).
Cyber terrorists- There is an expansion of activities by these cyber terrorists and they get
involve in cyber-attacks. Their abilities may range from low to high and main motivation is
political or religious. The critical infrastructures such as public health, telecommunication
department are the preferred targets of cyber terrorists. Such type of target is being selected by
these terrorist as their occurrence will have an adverse impact on government and society. In the
analysis of public material , the image of cyber terrorists is still not clear.
Script Kiddies – They are not skilled people who make use of scripts, program that are made by
others in order to attack computer system and disfigure websites.
Online social hackers – In order to protect and promote their cause the online social hackers
make use of computer systems. They are socially and politically motivated people. The high
profile websites, corporations, intelligence agencies are mainly targets by such hackers.
Employees- In a company they are mainly referred to security guards, staff, contractors etc. An
inside access to company's resources can be attacked by these people (Hallikas and Lintukangas,
2016). In order to place an effective attack against assets of their organisation these type threat
agents have a significant amount of knowledge.
Nation states – They may possess offending cyber abilities and can be used against an adversary.
The consideration of cyber weapons due to deployment of sophisticated attacks has made nation
5
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

states a prominent threat agent. The nation states possess a huge amount of resource and have a
high level of skill and talent.
Minimising impact of threat agents
In order to reduce the impact good practices and countermeasures can be used in order to protect
the assets of big data. A consistent results have been shown by good practice method. To
recognize the threats of big data different sources can be gathered, monitored, and mapped. In
order to secure the assets and counteracting the threats good practices is published by institutions
to specify vulnerabilities,recommendations and control (Glendon, Clarke and McKenna, 2016).
To deal with the unauthorized access by any employees to any sensitive data ISO 27001
have recommended the use of cryptography. The usage of cryptography in big data will not only
secure file and disk but it will also protect logical and physical fragments. The better security
design can be sued for big data in order to sop leakages in web applications .
Trends in threat probability
There is being use of countermeasures and good practices in order to reduce ad measure
the threat probability Various methods such as use of cryptography and encryption method is
beige used to reduce impact on unauthorized access and leaked data.
4. Discussing the improvement for the ETL process
There is a need to make ETL process more effective as there are various threats that can
be applied to big data (Giannakis and Papadopoulos, 2016 ). There is a share responsibility for
security and infrastructure engagement for big data which is collection of input channels from
networks, storage and computing system. In order to enhance the protection of each parties that
is data consumers and data provider countermeasures and good practices need to be implemented
by ETL. The proposed security controls that are being implemented by ISO terminology can be
implemented. The best practices that are introduced by COBIT in order to bridge the gap
between control requirements, technical problems and business risks, can also be adopted by
ETL.
In order to cope up with the unintentional damage or loss of assets or any data related to
IT the ISO group have suggested the use of cryptography to deal with unplanned leakages and
forbid the unauthorized access to private data and systems. The protection in the big data can be
achieved by using the method of encryption in blocks which works well while Hadop is running.
6
high level of skill and talent.
Minimising impact of threat agents
In order to reduce the impact good practices and countermeasures can be used in order to protect
the assets of big data. A consistent results have been shown by good practice method. To
recognize the threats of big data different sources can be gathered, monitored, and mapped. In
order to secure the assets and counteracting the threats good practices is published by institutions
to specify vulnerabilities,recommendations and control (Glendon, Clarke and McKenna, 2016).
To deal with the unauthorized access by any employees to any sensitive data ISO 27001
have recommended the use of cryptography. The usage of cryptography in big data will not only
secure file and disk but it will also protect logical and physical fragments. The better security
design can be sued for big data in order to sop leakages in web applications .
Trends in threat probability
There is being use of countermeasures and good practices in order to reduce ad measure
the threat probability Various methods such as use of cryptography and encryption method is
beige used to reduce impact on unauthorized access and leaked data.
4. Discussing the improvement for the ETL process
There is a need to make ETL process more effective as there are various threats that can
be applied to big data (Giannakis and Papadopoulos, 2016 ). There is a share responsibility for
security and infrastructure engagement for big data which is collection of input channels from
networks, storage and computing system. In order to enhance the protection of each parties that
is data consumers and data provider countermeasures and good practices need to be implemented
by ETL. The proposed security controls that are being implemented by ISO terminology can be
implemented. The best practices that are introduced by COBIT in order to bridge the gap
between control requirements, technical problems and business risks, can also be adopted by
ETL.
In order to cope up with the unintentional damage or loss of assets or any data related to
IT the ISO group have suggested the use of cryptography to deal with unplanned leakages and
forbid the unauthorized access to private data and systems. The protection in the big data can be
achieved by using the method of encryption in blocks which works well while Hadop is running.
6

Various ad-hoc solutions related to data encryption and key management tools to protect big data
have been provided (Cvitanić, Possamaï and Touzi, 2017).
The leakages that is produced in big data via web applications such as improper
adaptation of software, unsecure API can be handled with more secure design. For this,
cryptography can be used. In order to avoid injections NIST Big Data publications proposes
regular data integrity check.
In order to reduce the eavesdropping, interception, hijacking threat ETL can make use of
cryptography that are introduced by ISO 27001. To handle the encryption key management in
big data can be difficult. So it is advised to make use of ad-hoc key management tools. To
recognize any fraud that is taking place “information classification” is being proposed by ISO
27001. It is good practice which will assist in recognition of the data that needs to be protected.
If any information is accessed from or sent to cloud, internet or another resources then the data
need to be secured based on its classification (Corrales and Djemame, 2017). It is highly
recommended to use only trustworthy processing platforms. The protection of personal data need
to be assures by the providers in big data system while incorporating payment platforms. The
merchants are advised to accept credit cards with strict international standards such Payment
Card Industry(PCI).
To reduce the impact of denial of service threat ETL should ask the ISP or cloud provider
to implement prevention controls and the security professionals should request ISPs to take
initiative to install prevention measures. To reduce the impact of malicious code the ETL should
make use of proper technical vulnerabilities management and user awareness that are proposed
by ISO 27001 and COBIT in order to protect malware. All the manufactures of big data should
take initiative to protect all devices (Cole, Giné and Vickery, 2017). The user awareness can
given through training and education. To cope up with the failures of business process ETL need
to make use of ISO controls that have proposed models and methods in order to protect the
private information.
All these methods and tools need to be used by ETL that are proposed by ISO 27001,
Cobit in order to reduce the number of threats that are arising in the field of big data.
5. Summing up the case study
ENISA should be satisfied with the current state of security as there are number of
threats that can be applied to area of big data can be reduced with the solution provided in this
7
have been provided (Cvitanić, Possamaï and Touzi, 2017).
The leakages that is produced in big data via web applications such as improper
adaptation of software, unsecure API can be handled with more secure design. For this,
cryptography can be used. In order to avoid injections NIST Big Data publications proposes
regular data integrity check.
In order to reduce the eavesdropping, interception, hijacking threat ETL can make use of
cryptography that are introduced by ISO 27001. To handle the encryption key management in
big data can be difficult. So it is advised to make use of ad-hoc key management tools. To
recognize any fraud that is taking place “information classification” is being proposed by ISO
27001. It is good practice which will assist in recognition of the data that needs to be protected.
If any information is accessed from or sent to cloud, internet or another resources then the data
need to be secured based on its classification (Corrales and Djemame, 2017). It is highly
recommended to use only trustworthy processing platforms. The protection of personal data need
to be assures by the providers in big data system while incorporating payment platforms. The
merchants are advised to accept credit cards with strict international standards such Payment
Card Industry(PCI).
To reduce the impact of denial of service threat ETL should ask the ISP or cloud provider
to implement prevention controls and the security professionals should request ISPs to take
initiative to install prevention measures. To reduce the impact of malicious code the ETL should
make use of proper technical vulnerabilities management and user awareness that are proposed
by ISO 27001 and COBIT in order to protect malware. All the manufactures of big data should
take initiative to protect all devices (Cole, Giné and Vickery, 2017). The user awareness can
given through training and education. To cope up with the failures of business process ETL need
to make use of ISO controls that have proposed models and methods in order to protect the
private information.
All these methods and tools need to be used by ETL that are proposed by ISO 27001,
Cobit in order to reduce the number of threats that are arising in the field of big data.
5. Summing up the case study
ENISA should be satisfied with the current state of security as there are number of
threats that can be applied to area of big data can be reduced with the solution provided in this
7
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

case study. The use of cryptography alone is not sufficient to control the unauthorized access that
is taking place in organization (Cohen, Krishnamoorthy and Wright, 2017). The risks that are
associated to administrators and security professionals with equivalent privileges are high
especially when the threats are related with data leakage and sharing due to human errors. An
improved design of computing and storage models is needed for the leakage of data via web
applications, inadequate design, improperly adaptation etc. The current solution cannot mitigate
with the confidentiality issues faced during streaming data from sensors.
There is a risk to personal identifiable information when the best practices are widely
used and calls for privacy -oriented offending practices. There is a risk to models of computing
infrastructure due to malicious code and activities. The final users may also be affected due to
violation of laws or regulations, breach of legislation and abuse of personal data (Calomiris and
Carlson, 2016). Due to use of good practices and countermeasures in this case study the various
types of threat such as interception of information, inadequate design or incorrect adaptation,
leakage of data via web application and skill shortage have been recognized in this case study
and appropriate solution have been provided to reduce its impact on big data. To identify the
threats in the area of big data, various recommendations, countermeasures and good practices
have been used. To reduce the threat of violations of any law or regulations NIST Big data
Working Group advised “data residency “ as a requirement to distinct regions. This will allow
storing of all data into single location. There has been implementation of physical and logical
system audit and records by COBIT.
Various recommendations have also been made to the stakeholders of big data. The
stakeholders should try to reduce the use of existing products to big data. New assets, threats,
risks and challenged should be introduced to big data (Brustbauer, 2016). The new products that
are needed must provide effective countermeasures and enhance the trustworthiness on the big
data environment.
8
is taking place in organization (Cohen, Krishnamoorthy and Wright, 2017). The risks that are
associated to administrators and security professionals with equivalent privileges are high
especially when the threats are related with data leakage and sharing due to human errors. An
improved design of computing and storage models is needed for the leakage of data via web
applications, inadequate design, improperly adaptation etc. The current solution cannot mitigate
with the confidentiality issues faced during streaming data from sensors.
There is a risk to personal identifiable information when the best practices are widely
used and calls for privacy -oriented offending practices. There is a risk to models of computing
infrastructure due to malicious code and activities. The final users may also be affected due to
violation of laws or regulations, breach of legislation and abuse of personal data (Calomiris and
Carlson, 2016). Due to use of good practices and countermeasures in this case study the various
types of threat such as interception of information, inadequate design or incorrect adaptation,
leakage of data via web application and skill shortage have been recognized in this case study
and appropriate solution have been provided to reduce its impact on big data. To identify the
threats in the area of big data, various recommendations, countermeasures and good practices
have been used. To reduce the threat of violations of any law or regulations NIST Big data
Working Group advised “data residency “ as a requirement to distinct regions. This will allow
storing of all data into single location. There has been implementation of physical and logical
system audit and records by COBIT.
Various recommendations have also been made to the stakeholders of big data. The
stakeholders should try to reduce the use of existing products to big data. New assets, threats,
risks and challenged should be introduced to big data (Brustbauer, 2016). The new products that
are needed must provide effective countermeasures and enhance the trustworthiness on the big
data environment.
8
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

REFERENCES
Books and journals
Brustbauer, J., 2016. Enterprise risk management in SMEs: Towards a structural model.
International Small Business Journal. 34(1), pp.70-85.
Calomiris, C.W. and Carlson, M., 2016. Corporate governance and risk management at
unprotected banks: National banks in the 1890s. Journal of Financial Economics. 119(3),
pp.512-532.
Cohen, J., Krishnamoorthy, G. and Wright, A., 2017. Enterprise risk management and the
financial reporting process: The experiences of audit committee members, CFOs, and
external auditors. Contemporary Accounting Research. 34(2). pp.1178-1209.
Cole, S., Giné, X. and Vickery, J., 2017. How does risk management influence production
decisions? Evidence from a field experiment. The Review of Financial Studies. 30(6),
pp.1935-1970.
Corrales, M. and Djemame, K., 2017. A Brokering Framework for Assessing Legal Risks in Big
Data and the Cloud. In New Technology, Big Data and the Law (pp. 187-222). Springer,
Singapore.
Cvitanić, J., Possamaï, D. and Touzi, N., 2016. Moral hazard in dynamic risk management.
Management Science.
Giannakis, M. and Papadopoulos, T., 2016. Supply chain sustainability: A risk management
approach. International Journal of Production Economics. 171, pp.455-470.
Glendon, A.I., Clarke, S. and McKenna, E., 2016. Human safety and risk management. Crc
Press.
Hallikas, J. and Lintukangas, K., 2016. Purchasing and supply: An investigation of risk
management performance. International Journal of Production Economics. 171, pp.487-
494.
Leenes, R., van Brakel, R., Gutwirth, S. and De Hert, P., 2017. Data Protection and Privacy:(In)
visibilities and Infrastructures. Issues in Privacy and Data Protection. 36(1).
Lewis, K.A., Warner, D.J. and Green, A., 2016. An international database for pesticide risk
assessments and management. Human and Ecological Risk Assessment: An International
Journal. 22(4), pp.1050-1064
Meyer, T. and Reniers, G., 2016. Engineering risk management. Walter de Gruyter GmbH & Co
KG.
Olesen, N., 2016. European Public-Private Partnerships on Cybersecurity-An Instrument to
Support the Fight Against Cybercrime and Cyberterrorism. In Combatting Cybercrime
and Cyberterrorism (pp. 259-278). Springer International Publishing.
Patrick, H. and Fields, Z., 2017. A Need for Cyber Security Creativity. Collective Creativity for
Responsible and Sustainable Business Practice, pp.42-61.
Rampini, A.A. and Viswanathan, S., 2016. Household risk management (No. w22293). National
Bureau of Economic Research.
Waemustafa, W. and Sukri, S., 2016. Systematic and unsystematic risk determinants of liquidity
risk between Islamic and conventional banks.
Online
ENISA Big Data security infrastructure. 2017. [Online]. Available through:
<https://www.enisa.europa.eu/publications/big-data-security/> [Accessed on 11th 2017].
9
Books and journals
Brustbauer, J., 2016. Enterprise risk management in SMEs: Towards a structural model.
International Small Business Journal. 34(1), pp.70-85.
Calomiris, C.W. and Carlson, M., 2016. Corporate governance and risk management at
unprotected banks: National banks in the 1890s. Journal of Financial Economics. 119(3),
pp.512-532.
Cohen, J., Krishnamoorthy, G. and Wright, A., 2017. Enterprise risk management and the
financial reporting process: The experiences of audit committee members, CFOs, and
external auditors. Contemporary Accounting Research. 34(2). pp.1178-1209.
Cole, S., Giné, X. and Vickery, J., 2017. How does risk management influence production
decisions? Evidence from a field experiment. The Review of Financial Studies. 30(6),
pp.1935-1970.
Corrales, M. and Djemame, K., 2017. A Brokering Framework for Assessing Legal Risks in Big
Data and the Cloud. In New Technology, Big Data and the Law (pp. 187-222). Springer,
Singapore.
Cvitanić, J., Possamaï, D. and Touzi, N., 2016. Moral hazard in dynamic risk management.
Management Science.
Giannakis, M. and Papadopoulos, T., 2016. Supply chain sustainability: A risk management
approach. International Journal of Production Economics. 171, pp.455-470.
Glendon, A.I., Clarke, S. and McKenna, E., 2016. Human safety and risk management. Crc
Press.
Hallikas, J. and Lintukangas, K., 2016. Purchasing and supply: An investigation of risk
management performance. International Journal of Production Economics. 171, pp.487-
494.
Leenes, R., van Brakel, R., Gutwirth, S. and De Hert, P., 2017. Data Protection and Privacy:(In)
visibilities and Infrastructures. Issues in Privacy and Data Protection. 36(1).
Lewis, K.A., Warner, D.J. and Green, A., 2016. An international database for pesticide risk
assessments and management. Human and Ecological Risk Assessment: An International
Journal. 22(4), pp.1050-1064
Meyer, T. and Reniers, G., 2016. Engineering risk management. Walter de Gruyter GmbH & Co
KG.
Olesen, N., 2016. European Public-Private Partnerships on Cybersecurity-An Instrument to
Support the Fight Against Cybercrime and Cyberterrorism. In Combatting Cybercrime
and Cyberterrorism (pp. 259-278). Springer International Publishing.
Patrick, H. and Fields, Z., 2017. A Need for Cyber Security Creativity. Collective Creativity for
Responsible and Sustainable Business Practice, pp.42-61.
Rampini, A.A. and Viswanathan, S., 2016. Household risk management (No. w22293). National
Bureau of Economic Research.
Waemustafa, W. and Sukri, S., 2016. Systematic and unsystematic risk determinants of liquidity
risk between Islamic and conventional banks.
Online
ENISA Big Data security infrastructure. 2017. [Online]. Available through:
<https://www.enisa.europa.eu/publications/big-data-security/> [Accessed on 11th 2017].
9

10
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 13
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





