A Study on Privacy and Security Issues in Big Data Implementation
VerifiedAdded on 2023/06/11
|17
|7279
|285
Report
AI Summary
This research paper identifies and analyzes the privacy and security issues associated with implementing Big Data technology in commercial environments. It emphasizes the increasing reliance on Big Data across industries and the corresponding rise in privacy and security concerns. The study explores the significance of these issues, highlighting the vulnerabilities in Big Data systems due to their complexity and the potential for unauthorized access and data breaches. It discusses the importance of safeguarding data throughout its lifecycle, from creation to deletion, and addresses challenges like managing large volumes of diverse data and the limitations of traditional security mechanisms. The paper also touches on potential solutions like Software Defined Networking (SDN) and underscores the need for continuous research and development to address the evolving security landscape in Big Data environments. The research methodology includes literature review, data analysis, and case study selection to provide a comprehensive understanding of the topic. Desklib provides access to this paper and numerous other study resources.

PAPER IDENTIFICATION NUMBER
Abstract In today’s world Information Technology has seeped into every sector of industry, financial institutions and
commercial organizations. The use of computers and their associated technologies like Internet, Networking, Cloud
computing, Grid Computing, Virtualization and Big data has made the world a better global village with their speed, ease,
connivance, capabilities and low cost features. However, the primary concerns in today’s world of information technology are
of privacy and security of the information that is stored in the computing resources like systems, servers, websites, networks or
devices. My present research project study paper has been undertaken with the primary goal of identifying the privacy and
security issues that are associated with implementing Big Data technology in a commercial environment for conducting
various business tasks.
Keywords: Privacy, security, information technology, Network, communication, firewall, Big Data, Security, Data Ownership,
Cloud computing, Social network Applications, Intrusion Detection systems, Intrusion Prevention systems, Security policies.
Table of Contents
1. INTRODUCTION..........................................................................................................................................................................3
A. what are privacy and security issues.........................................................................................................................................3
B. what is big data..........................................................................................................................................................................3
II. SIGNIFICANCE OF THE RESEARCH.......................................................................................................................................4
EMERGING TECHNOLOGIESStudent Name
Institution Affiliation
Facilitator
Course
Date
1
Abstract In today’s world Information Technology has seeped into every sector of industry, financial institutions and
commercial organizations. The use of computers and their associated technologies like Internet, Networking, Cloud
computing, Grid Computing, Virtualization and Big data has made the world a better global village with their speed, ease,
connivance, capabilities and low cost features. However, the primary concerns in today’s world of information technology are
of privacy and security of the information that is stored in the computing resources like systems, servers, websites, networks or
devices. My present research project study paper has been undertaken with the primary goal of identifying the privacy and
security issues that are associated with implementing Big Data technology in a commercial environment for conducting
various business tasks.
Keywords: Privacy, security, information technology, Network, communication, firewall, Big Data, Security, Data Ownership,
Cloud computing, Social network Applications, Intrusion Detection systems, Intrusion Prevention systems, Security policies.
Table of Contents
1. INTRODUCTION..........................................................................................................................................................................3
A. what are privacy and security issues.........................................................................................................................................3
B. what is big data..........................................................................................................................................................................3
II. SIGNIFICANCE OF THE RESEARCH.......................................................................................................................................4
EMERGING TECHNOLOGIESStudent Name
Institution Affiliation
Facilitator
Course
Date
1
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

III. ORIGINALITY OF THE RESEARCH.......................................................................................................................................4
A. Challenges................................................................................................................................................................................5
B. Problem statement....................................................................................................................................................................5
C. Research aim.............................................................................................................................................................................5
D. Research objective....................................................................................................................................................................5
IV. MATERIALS AND METHODS.................................................................................................................................................6
A. Data collection methods............................................................................................................................................................6
B. Data analysis methods..............................................................................................................................................................6
C. Results/ Outcome......................................................................................................................................................................8
V. LITERATURE REVIEW..............................................................................................................................................................9
VI. RESEARCH GAP......................................................................................................................................................................13
VII. AIM OF THE RESEARCH......................................................................................................................................................13
VIII. DISCUSSION..........................................................................................................................................................................13
IX. CONCLUSION...........................................................................................................................................................................15
X. REFERENCES............................................................................................................................................................................15
I.INTRODUCTION1
A. WHAT ARE PRIVACY AND SECURITY ISSUES?
1
A typical privacy or security attack is deliberately done
to cause potential harm to an individual user from privacy
and security issues really boils down to how much the
value of information is available online, as well as the
amount of information that can be accessed through online
resources. In other words, the hackers or crackers
A. Challenges................................................................................................................................................................................5
B. Problem statement....................................................................................................................................................................5
C. Research aim.............................................................................................................................................................................5
D. Research objective....................................................................................................................................................................5
IV. MATERIALS AND METHODS.................................................................................................................................................6
A. Data collection methods............................................................................................................................................................6
B. Data analysis methods..............................................................................................................................................................6
C. Results/ Outcome......................................................................................................................................................................8
V. LITERATURE REVIEW..............................................................................................................................................................9
VI. RESEARCH GAP......................................................................................................................................................................13
VII. AIM OF THE RESEARCH......................................................................................................................................................13
VIII. DISCUSSION..........................................................................................................................................................................13
IX. CONCLUSION...........................................................................................................................................................................15
X. REFERENCES............................................................................................................................................................................15
I.INTRODUCTION1
A. WHAT ARE PRIVACY AND SECURITY ISSUES?
1
A typical privacy or security attack is deliberately done
to cause potential harm to an individual user from privacy
and security issues really boils down to how much the
value of information is available online, as well as the
amount of information that can be accessed through online
resources. In other words, the hackers or crackers

PAPER IDENTIFICATION NUMBER
generally target the persons who have more valuable or
useable data than the others in the concerned system,
server, network or website [4]. For example a Facebook
user with more than 1000 friends and membership in more
than 100 groups are more likely to be targeted for
conducting hacking than someone who barely uses the site
and has few friends. In final words, a privacy or security
issues fundamentally occurs based on the value of data
stored and the target victims are chosen on their value
basis [5].
Most of the privacy and security lapses necessarily
involve the exploitation of a individual user’s private
information. Usually the targeted victims are the users
who have access to valuable data storage like
Administrators, Managers, and Security personnel. 95% of
all hacking or phreaking incidents are caused by social
engineering methodologies and expert exploit
programmers cause the rest of 5% of the security breach
incidents. Hackers entice their victims with user
participation invitations, prize winning messages,
invitations, sales deals, photos, open platform applications,
etc. —to gain access to their private information with
special focus on their professional information. Hence in
order to resolve these privacy and security issues
educating the users is the best viable solutions to prevent
the incidents of hacking, data theft, or the malicious
activities of a nefarious application developer.
B. WHAT IS BIG DATA?
The technical term “Big Data” defines a very large
volume of cloud-based storage consisting of all types of
data elements like structured, semi-structured and
unstructured elements [8]. In today’s world of information
technology computers are used in every sector of industry,
financial institutions and commercial organization for
using their features of low-cost, high processing speed,
large storage volume and versatile program capability.
This has resulted in unprecedented phenomenally
exponentially growth the computer-based storages with
time on a day-to-day basis as the enterprises conducted
their daily business activities. Such huge data sets cannot
be handled by ordinary databases or data warehouses that
exist today, as their technology does not support any
assorted data sets [6].
Hence all enterprise-level business organizations
conduct their day-to-day basis regular existential work on
Big data which can easily support these extremely large
datasets of assorted data types by arranging them in a
specific way that the data sets may be data mined to
analyze to accurately reveal interesting and useful business
intelligence like patterns, trends, spikes, surges, and
associations [10]. This allows the enterprise levels
companies, social networks, popular websites and
government IT institutions to better understand their
present scenarios and plan for their future activities based
on the acquired business intelligence.
II.SIGNIFICANCE OF THE RESEARCH
Mentioned in detail below are the four primary features of
Big Data:
1. Support for large storage volume up to Zeta bytes size
3
generally target the persons who have more valuable or
useable data than the others in the concerned system,
server, network or website [4]. For example a Facebook
user with more than 1000 friends and membership in more
than 100 groups are more likely to be targeted for
conducting hacking than someone who barely uses the site
and has few friends. In final words, a privacy or security
issues fundamentally occurs based on the value of data
stored and the target victims are chosen on their value
basis [5].
Most of the privacy and security lapses necessarily
involve the exploitation of a individual user’s private
information. Usually the targeted victims are the users
who have access to valuable data storage like
Administrators, Managers, and Security personnel. 95% of
all hacking or phreaking incidents are caused by social
engineering methodologies and expert exploit
programmers cause the rest of 5% of the security breach
incidents. Hackers entice their victims with user
participation invitations, prize winning messages,
invitations, sales deals, photos, open platform applications,
etc. —to gain access to their private information with
special focus on their professional information. Hence in
order to resolve these privacy and security issues
educating the users is the best viable solutions to prevent
the incidents of hacking, data theft, or the malicious
activities of a nefarious application developer.
B. WHAT IS BIG DATA?
The technical term “Big Data” defines a very large
volume of cloud-based storage consisting of all types of
data elements like structured, semi-structured and
unstructured elements [8]. In today’s world of information
technology computers are used in every sector of industry,
financial institutions and commercial organization for
using their features of low-cost, high processing speed,
large storage volume and versatile program capability.
This has resulted in unprecedented phenomenally
exponentially growth the computer-based storages with
time on a day-to-day basis as the enterprises conducted
their daily business activities. Such huge data sets cannot
be handled by ordinary databases or data warehouses that
exist today, as their technology does not support any
assorted data sets [6].
Hence all enterprise-level business organizations
conduct their day-to-day basis regular existential work on
Big data which can easily support these extremely large
datasets of assorted data types by arranging them in a
specific way that the data sets may be data mined to
analyze to accurately reveal interesting and useful business
intelligence like patterns, trends, spikes, surges, and
associations [10]. This allows the enterprise levels
companies, social networks, popular websites and
government IT institutions to better understand their
present scenarios and plan for their future activities based
on the acquired business intelligence.
II.SIGNIFICANCE OF THE RESEARCH
Mentioned in detail below are the four primary features of
Big Data:
1. Support for large storage volume up to Zeta bytes size
3
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

2. Support to huge variety of data sets including
structured, semi-structured and unstructured data sets,
3. High speed of processing and communication and
4. Extensive output information variability.
As any complex system will have, inbuilt vulnerabilities
will always have existing intricate structures built into it
[9]. It is just common to have vulnerabilities in Big Data
too, due to the intricate level of complexity in its
technology regarding its novel and innovative storage
methodology and data access process. As most
governments, enterprise levels companies, social
networks, popular web sites, technological companies
maintain and process valuable information, or provide
services to multiple users concurrently using Big Data
technology, it is primarily necessary to provide security
safeguards against unauthorized access, use, or
modifications of any file or computing resource[14].
Privacy and security of data is a pertinent aspect to be
addressed because users share more and more personal
data and content through their devices and computers to
social networks and public clouds. So, a security
framework to protect Big Data based websites, storage
spaces, social networks is a very immediate hot topic
research. Hence I have chosen to conduct my final year
research study on this topic.
III. ORIGINALITY OF THE APPROACH
In present time and in the future, concerns for privacy and
security are the foremost concern of every individual,
commercial organization, financial institution and
governments as they are all dependent on the use of
information technology and computer science to execute
their day to day activities. The only solution to resolve
this is to make security and privacy polices mandatorily
integral in the planning and design of computer systems
and their applications [7]. This is very difficult problem to
tackle and it has not yet been solved in the general case. In
order to prevent privacy and security issues there must be
end to end security in all stages of data life cycle starting
from data generation, data storage, data modification, data
communication, and data archival to the final stage of data
deletion [8]. This involves the below steps right from data
creation stage at Computer systems. Computers, servers,
networks and web sites are the main sources of data
generation and must be protected against unauthorized use,
malicious attacks, compromise, disruption of operations,
and physical damage [10].
The growing number of computer based technologies
and applications involving valuable information or assets
are directly proportional to the growing number of
criminal actions directed against these computer
applications and systems or perpetrated by using
computers. These criminal incidents underscore the need
for finding effective solutions to the Big Data privacy and
security problem [4]. This research study revises the most
important aspects in how computing infrastructures should
be configured and intelligently managed to fulfill the most
notably identifiable privacy and security aspects required
by Big Data applications [3]. My research topic of
providing privacy and security to Big data environment is
structured, semi-structured and unstructured data sets,
3. High speed of processing and communication and
4. Extensive output information variability.
As any complex system will have, inbuilt vulnerabilities
will always have existing intricate structures built into it
[9]. It is just common to have vulnerabilities in Big Data
too, due to the intricate level of complexity in its
technology regarding its novel and innovative storage
methodology and data access process. As most
governments, enterprise levels companies, social
networks, popular web sites, technological companies
maintain and process valuable information, or provide
services to multiple users concurrently using Big Data
technology, it is primarily necessary to provide security
safeguards against unauthorized access, use, or
modifications of any file or computing resource[14].
Privacy and security of data is a pertinent aspect to be
addressed because users share more and more personal
data and content through their devices and computers to
social networks and public clouds. So, a security
framework to protect Big Data based websites, storage
spaces, social networks is a very immediate hot topic
research. Hence I have chosen to conduct my final year
research study on this topic.
III. ORIGINALITY OF THE APPROACH
In present time and in the future, concerns for privacy and
security are the foremost concern of every individual,
commercial organization, financial institution and
governments as they are all dependent on the use of
information technology and computer science to execute
their day to day activities. The only solution to resolve
this is to make security and privacy polices mandatorily
integral in the planning and design of computer systems
and their applications [7]. This is very difficult problem to
tackle and it has not yet been solved in the general case. In
order to prevent privacy and security issues there must be
end to end security in all stages of data life cycle starting
from data generation, data storage, data modification, data
communication, and data archival to the final stage of data
deletion [8]. This involves the below steps right from data
creation stage at Computer systems. Computers, servers,
networks and web sites are the main sources of data
generation and must be protected against unauthorized use,
malicious attacks, compromise, disruption of operations,
and physical damage [10].
The growing number of computer based technologies
and applications involving valuable information or assets
are directly proportional to the growing number of
criminal actions directed against these computer
applications and systems or perpetrated by using
computers. These criminal incidents underscore the need
for finding effective solutions to the Big Data privacy and
security problem [4]. This research study revises the most
important aspects in how computing infrastructures should
be configured and intelligently managed to fulfill the most
notably identifiable privacy and security aspects required
by Big Data applications [3]. My research topic of
providing privacy and security to Big data environment is
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

PAPER IDENTIFICATION NUMBER
addressed in two sections of the along with their associated
case studies.
A. THE CHALLENGES
Big data is a novel and innovative technologies with
complex intricate structural environment consisting of
other information technologies like Grid Computing,
Cloud computing, Gigabit Network, Shared Pooling,
Virtualization, In Memory processing, Parallel processing
etc., Hence most of the traditional IT infrastructure
security mechanisms such as firewalls and demilitarized
zones are not suitable to be applied in computing systems
to support Big Data [14].
The ideal solution to resolve the privacy and security
issues associated with Big data environments is the
emergent SDN – software defined network [7]. SDN is a
novel and innovative network management solution that
has the potential to become a convenient mechanism to
implement security in Big Data systems. There is not
much a technical discussion or relevant research work on
my research topic of SDN which identifies open issues [6].
B. PROBLEM STATEMENT
In today’s digital world the collection, analysis, and
management of the acquired data is the core part of any
commercial or business activity. Due to the increasing rate
of computing resources usage there has been
proportionately double the workload of data management
over the Big data environment [15]. The complexity of
managing, storing, processing and visualizing data in an
Big Data environment is very vast and intricate. Hence,
any inefficiency due to system or strategic decision gets
affected to the misprocessing in retrieving data from the
huge amount of data available on a Big Data environment
[12]. Security and confidentiality of the big data
environment is the major challenge in the scheduling and
managing of the large volume of data available over the
network [13]. The Big data environment can be clearly
defined by its primary feature which is vast variety, large
volume, big veracity, high velocity, and great value.
C. RESEARCH AIM
The aim of this paper is to focus on the security and the
privacy issues, which exist with the arrangement of big
data.
D. RESEARCH OBJECTIVE
The objective of the research is to find out the privacy and
security issues, which exist with the big data management
plan. The study helps us to find out the possible solution
for the management of big data [7].
5
addressed in two sections of the along with their associated
case studies.
A. THE CHALLENGES
Big data is a novel and innovative technologies with
complex intricate structural environment consisting of
other information technologies like Grid Computing,
Cloud computing, Gigabit Network, Shared Pooling,
Virtualization, In Memory processing, Parallel processing
etc., Hence most of the traditional IT infrastructure
security mechanisms such as firewalls and demilitarized
zones are not suitable to be applied in computing systems
to support Big Data [14].
The ideal solution to resolve the privacy and security
issues associated with Big data environments is the
emergent SDN – software defined network [7]. SDN is a
novel and innovative network management solution that
has the potential to become a convenient mechanism to
implement security in Big Data systems. There is not
much a technical discussion or relevant research work on
my research topic of SDN which identifies open issues [6].
B. PROBLEM STATEMENT
In today’s digital world the collection, analysis, and
management of the acquired data is the core part of any
commercial or business activity. Due to the increasing rate
of computing resources usage there has been
proportionately double the workload of data management
over the Big data environment [15]. The complexity of
managing, storing, processing and visualizing data in an
Big Data environment is very vast and intricate. Hence,
any inefficiency due to system or strategic decision gets
affected to the misprocessing in retrieving data from the
huge amount of data available on a Big Data environment
[12]. Security and confidentiality of the big data
environment is the major challenge in the scheduling and
managing of the large volume of data available over the
network [13]. The Big data environment can be clearly
defined by its primary feature which is vast variety, large
volume, big veracity, high velocity, and great value.
C. RESEARCH AIM
The aim of this paper is to focus on the security and the
privacy issues, which exist with the arrangement of big
data.
D. RESEARCH OBJECTIVE
The objective of the research is to find out the privacy and
security issues, which exist with the big data management
plan. The study helps us to find out the possible solution
for the management of big data [7].
5

IV. MATERIALS AND METHODS
Fig.1. Graphical abstract of the analysis: Security and
Privacy Challenges of Big Data
A. DATA COLLECTION METHOD
For the literature review on my research topic “privacy
and security with Big Data” I have pooled the data of the
previously published research articles from 12 peer-
reviewed scientific studies that were conducted in the
previous two decades [5]. Much of the comparative data
presented in this research study is derived from them and
includes analysis results information, application
methodology, security issues, privacy issues and algorithm
development.
B. DATA ANALYSES METHOD
The pooled data of the previously published research
articles amounting to 12 peer-reviewed scientific studies
that were conducted in the previous two decades is deeply
analyzed by categorizing the collected data and displaying
emerging patterns in a diagram and table. The data sets
include state description attributes such as volume of data,
application area, and security issues that are prevalent in
that area [12]. The research methodology used allows the
resolution of the identified issues, as the specific algorithm
that is selected, is particularly used to for this purpose
only.
The focus should be given on the challenges which exist
with the management of the big data. The solution of
security dimensions should be explored for the retrieving
of data on demand. The interviews, questionnaires, study
of previous work done, and selection of the case study
should be undertaken for the data collection for the study
of security and privacy issues which exist with the
management of big data [15].
Interview: The interview should be arranged with
the professionals of the cloud environment who
deals with the management of the big data within
their organization. The research questions
undertaken should be asked for getting relevant
information regarding issues and challenges in the
big data.
Questionnaire: The large sample of IT
professionals should be taken to arrange the
questionnaire to get the solution of the research
question.
Previous work done: The study of the literature
review helps in investigating the gaps which exist
with the management of the big data.
Fig.1. Graphical abstract of the analysis: Security and
Privacy Challenges of Big Data
A. DATA COLLECTION METHOD
For the literature review on my research topic “privacy
and security with Big Data” I have pooled the data of the
previously published research articles from 12 peer-
reviewed scientific studies that were conducted in the
previous two decades [5]. Much of the comparative data
presented in this research study is derived from them and
includes analysis results information, application
methodology, security issues, privacy issues and algorithm
development.
B. DATA ANALYSES METHOD
The pooled data of the previously published research
articles amounting to 12 peer-reviewed scientific studies
that were conducted in the previous two decades is deeply
analyzed by categorizing the collected data and displaying
emerging patterns in a diagram and table. The data sets
include state description attributes such as volume of data,
application area, and security issues that are prevalent in
that area [12]. The research methodology used allows the
resolution of the identified issues, as the specific algorithm
that is selected, is particularly used to for this purpose
only.
The focus should be given on the challenges which exist
with the management of the big data. The solution of
security dimensions should be explored for the retrieving
of data on demand. The interviews, questionnaires, study
of previous work done, and selection of the case study
should be undertaken for the data collection for the study
of security and privacy issues which exist with the
management of big data [15].
Interview: The interview should be arranged with
the professionals of the cloud environment who
deals with the management of the big data within
their organization. The research questions
undertaken should be asked for getting relevant
information regarding issues and challenges in the
big data.
Questionnaire: The large sample of IT
professionals should be taken to arrange the
questionnaire to get the solution of the research
question.
Previous work done: The study of the literature
review helps in investigating the gaps which exist
with the management of the big data.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

PAPER IDENTIFICATION NUMBER
Selection of the case study: The case study based
on big data security should be undertaken for
study. The abstracts of the research papers should
be arranged in synchronised manner.
From the research study, we conclude following area of
concern which should be taken for managing the big data
analytics:
Area of concern Description
Security of Hadoop file
system
The security issues exist with
the infrastructure of the
Hadoop file system [16]. The
authenticationand authorization
mechanism is the major
concern of Hadoop security
system
Data availability It is difficult in managing on
demand supply of data from
the large volume of available
data. The complexity arises
when same data is asked by
multiple active node [14]
Security issues with the
architecture
The modification and
manipulation is required in the
infrastructure of the Hadoop
file system
Issues related with
authentication
Encrypting the data is the
major task for providing
authentication to the data.
Communication flow The flow of communication is
the major problem in the
deployment of Hadoop file
system. The network protocols
should be used for managing
the big data
The following diagram shows the major area of concern in
relation to the big data security:
The research area should be expanded for managing the
privacy issues which exist with the management of big
data over the cloud network. The confidentiality of the
data is the major issues for securing the personal details of
the user. The data leakage is the main area of concern for
keeping the data private and confidential [12]. The
confidentiality of the data can be maintained with the
inclusion of cryptographic approaches, deployment of
Anonymization model, providing access control to the
authenticated party [9]. The following diagram shows the
7
Selection of the case study: The case study based
on big data security should be undertaken for
study. The abstracts of the research papers should
be arranged in synchronised manner.
From the research study, we conclude following area of
concern which should be taken for managing the big data
analytics:
Area of concern Description
Security of Hadoop file
system
The security issues exist with
the infrastructure of the
Hadoop file system [16]. The
authenticationand authorization
mechanism is the major
concern of Hadoop security
system
Data availability It is difficult in managing on
demand supply of data from
the large volume of available
data. The complexity arises
when same data is asked by
multiple active node [14]
Security issues with the
architecture
The modification and
manipulation is required in the
infrastructure of the Hadoop
file system
Issues related with
authentication
Encrypting the data is the
major task for providing
authentication to the data.
Communication flow The flow of communication is
the major problem in the
deployment of Hadoop file
system. The network protocols
should be used for managing
the big data
The following diagram shows the major area of concern in
relation to the big data security:
The research area should be expanded for managing the
privacy issues which exist with the management of big
data over the cloud network. The confidentiality of the
data is the major issues for securing the personal details of
the user. The data leakage is the main area of concern for
keeping the data private and confidential [12]. The
confidentiality of the data can be maintained with the
inclusion of cryptographic approaches, deployment of
Anonymization model, providing access control to the
authenticated party [9]. The following diagram shows the
7
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
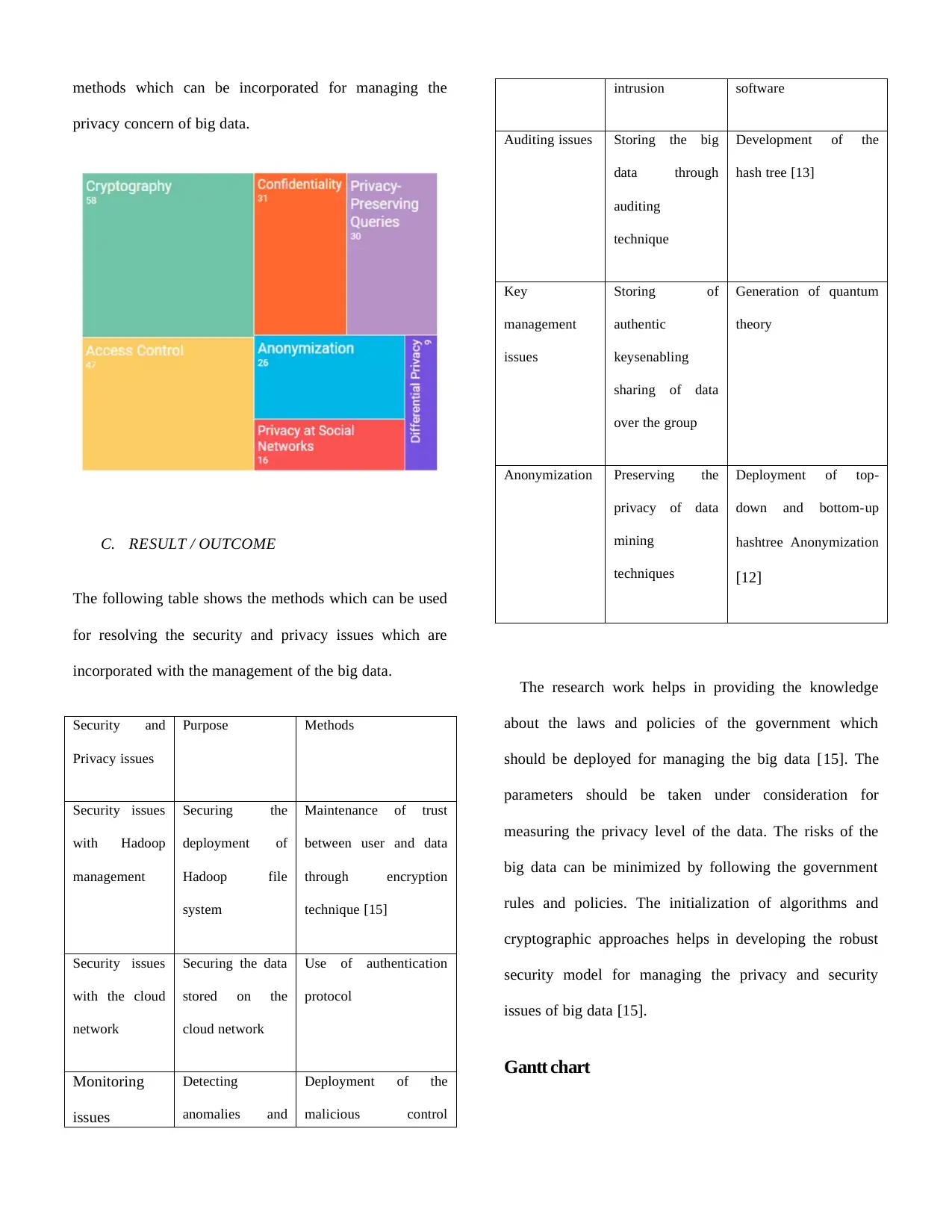
methods which can be incorporated for managing the
privacy concern of big data.
C. RESULT / OUTCOME
The following table shows the methods which can be used
for resolving the security and privacy issues which are
incorporated with the management of the big data.
Security and
Privacy issues
Purpose Methods
Security issues
with Hadoop
management
Securing the
deployment of
Hadoop file
system
Maintenance of trust
between user and data
through encryption
technique [15]
Security issues
with the cloud
network
Securing the data
stored on the
cloud network
Use of authentication
protocol
Monitoring
issues
Detecting
anomalies and
Deployment of the
malicious control
intrusion software
Auditing issues Storing the big
data through
auditing
technique
Development of the
hash tree [13]
Key
management
issues
Storing of
authentic
keysenabling
sharing of data
over the group
Generation of quantum
theory
Anonymization Preserving the
privacy of data
mining
techniques
Deployment of top-
down and bottom-up
hashtree Anonymization
[12]
The research work helps in providing the knowledge
about the laws and policies of the government which
should be deployed for managing the big data [15]. The
parameters should be taken under consideration for
measuring the privacy level of the data. The risks of the
big data can be minimized by following the government
rules and policies. The initialization of algorithms and
cryptographic approaches helps in developing the robust
security model for managing the privacy and security
issues of big data [15].
Gantt chart
privacy concern of big data.
C. RESULT / OUTCOME
The following table shows the methods which can be used
for resolving the security and privacy issues which are
incorporated with the management of the big data.
Security and
Privacy issues
Purpose Methods
Security issues
with Hadoop
management
Securing the
deployment of
Hadoop file
system
Maintenance of trust
between user and data
through encryption
technique [15]
Security issues
with the cloud
network
Securing the data
stored on the
cloud network
Use of authentication
protocol
Monitoring
issues
Detecting
anomalies and
Deployment of the
malicious control
intrusion software
Auditing issues Storing the big
data through
auditing
technique
Development of the
hash tree [13]
Key
management
issues
Storing of
authentic
keysenabling
sharing of data
over the group
Generation of quantum
theory
Anonymization Preserving the
privacy of data
mining
techniques
Deployment of top-
down and bottom-up
hashtree Anonymization
[12]
The research work helps in providing the knowledge
about the laws and policies of the government which
should be deployed for managing the big data [15]. The
parameters should be taken under consideration for
measuring the privacy level of the data. The risks of the
big data can be minimized by following the government
rules and policies. The initialization of algorithms and
cryptographic approaches helps in developing the robust
security model for managing the privacy and security
issues of big data [15].
Gantt chart

PAPER IDENTIFICATION NUMBER
V. LITERATURE REVIEW
In todays, information age, where data and its security is
paramount to all commercial, non-commercial, public and
governmental organizations, Big data is the only
technological solution that provides all the vital 3 v’s
features – vast storage capacity, very high speed data
streaming capability, and a variety of data comprising of
structured data, semi structured data and unstructured data.
My research study identifies reviews, evaluates and offers
appropriate solutions to assure security and privacy of the
data stored in Big data environment.
In the first research paper [1], the authors have
discussed the importance of Big data and reviewed its
security and privacy issues in great detail. Security and
privacy of Big data is a complex issue when taking into
account the different sources and different types of
datasets that constitutes the Big Data. The scholars have
specifically reviewed the security and privacy issues
related to various sources of big data like healthcare,
social media, IOT, mobile apps and social networks. The
issues in each domain have been discussed in detail, the
study also elaborates on the privacy and security concerns
of various future domains of Big Data as they emerge,
from time to time due to the ongoing technological
advancement in this information age. This study paper [1]
has provided me with very valuable data pertaining to
security and privacy issue of implementing Big Data in
various data sets domains. However it does not prescribe
any resolutions to the detected issues and thus can be used
only to gain academic knowledge and not functional
knowledge.
The authors of the second research study paper [2] have
discussed in details all the types of security and privacy
issues affecting Big Data due to its unique technology and
vast environment footprint. The authors also discuss the
steps taken by DARPA, NIST, OWASP, ISOC, MUSE and
other associated technology governing bodies on the topic
of Big data security and privacy issues. The study
elaborates on the various frameworks, procedures and
policies devised and framed by these organizations to
resolve the issues of Big Data security and privacy. The
complexity of implementing security and privacy when
using the innovative technologies like IOT, BYOD, Cloud
Computing, JS, etc., increase with the extent of their
usage. However the authors[2] have correctly segmented
the security and privacy issues of Big data technology
implementation into four major divisions namely as 1)
9
V. LITERATURE REVIEW
In todays, information age, where data and its security is
paramount to all commercial, non-commercial, public and
governmental organizations, Big data is the only
technological solution that provides all the vital 3 v’s
features – vast storage capacity, very high speed data
streaming capability, and a variety of data comprising of
structured data, semi structured data and unstructured data.
My research study identifies reviews, evaluates and offers
appropriate solutions to assure security and privacy of the
data stored in Big data environment.
In the first research paper [1], the authors have
discussed the importance of Big data and reviewed its
security and privacy issues in great detail. Security and
privacy of Big data is a complex issue when taking into
account the different sources and different types of
datasets that constitutes the Big Data. The scholars have
specifically reviewed the security and privacy issues
related to various sources of big data like healthcare,
social media, IOT, mobile apps and social networks. The
issues in each domain have been discussed in detail, the
study also elaborates on the privacy and security concerns
of various future domains of Big Data as they emerge,
from time to time due to the ongoing technological
advancement in this information age. This study paper [1]
has provided me with very valuable data pertaining to
security and privacy issue of implementing Big Data in
various data sets domains. However it does not prescribe
any resolutions to the detected issues and thus can be used
only to gain academic knowledge and not functional
knowledge.
The authors of the second research study paper [2] have
discussed in details all the types of security and privacy
issues affecting Big Data due to its unique technology and
vast environment footprint. The authors also discuss the
steps taken by DARPA, NIST, OWASP, ISOC, MUSE and
other associated technology governing bodies on the topic
of Big data security and privacy issues. The study
elaborates on the various frameworks, procedures and
policies devised and framed by these organizations to
resolve the issues of Big Data security and privacy. The
complexity of implementing security and privacy when
using the innovative technologies like IOT, BYOD, Cloud
Computing, JS, etc., increase with the extent of their
usage. However the authors[2] have correctly segmented
the security and privacy issues of Big data technology
implementation into four major divisions namely as 1)
9
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

Infrastructure security (can be resolved by implementing
secure distributed computations using Map Reduce), 2)
Data privacy (can be resolved by using implementing
authorised data mining that preserves privacy by granular
access authorization, 3) data security (can be resolved by
implementing secure data provenance and storage) and 4)
Integrity and reactive security (can be resolved by
implementing real time monitoring of anomalies and
attacks using IDS and IPS device). Also the study does not
discuss about the true challenges on maintaining end to
end data security and privacy in a big data environment
from the stage of ‘data creation’ to the stage of ‘data
usage’.
The research scholars of the third study paper [3]
reviewed the several security and privacy issues of Big
data in the perspective of cloud computing platform. The
authors described the several advantageous features of Big
data, cloud computing, virtualization and DevOps
technologies along with their associated security and
privacy issue concerns. The authors list the identified
security and privacy factors, that affect the activities of
cloud based service providers and the legal processioning
of consumer data in the context of genomic sequencing.
Although the study paper [3] also discusses the various
security and privacy solutions like Homomorphic
encryption, Anonymization, SAIL, ScaBIA, RBAC, PKI.
DPD, Bio Bank Cloud etc., it does not discuss the other
aspects of Big data security and privacy and thus lacks
holistic approach to resolve the security and privacy
concerns of Big data.
The concerned research article [4] discusses the various
benefits of using Big data technology to resolve the over
whelming information crisis in today’s information age.
However this study is concentrated on providing personal
privacy in the domain of big data platform. The authors of
the study elucidate four aspects to resolve the problem of
protecting personal privacy. The authors state their opinion
that only a combination of the technical means and legal
means can resolve the problem of security and personal
privacy of a data user in Big data environment. They
propose four innovative methods for ensuring personal and
data privacy in a big data environment, which are 1)
Implementing anonymity protection by implementing user
identity anonymity, attributes anonymity and relationship
anonymity, 2) Implementing digital watermarking
technology by embedding imperceptible watermarks
within the data carrier, database and text files 3)
Implementing Data Provence labelling technology to
accurately determine the source of the data in the data
warehouse. 4) Implement Role-based access control
(RBAC) to permissions set, to restrict unauthorized data
access and usage. The study [4] provides valuable policy
based security and privacy protection techniques to my
research but the authors fail to recommend any uniform
policy design structure for implementing data security and
personal privacy. However it focuses on a single aspect of
personal privacy security of all the various security and
secure distributed computations using Map Reduce), 2)
Data privacy (can be resolved by using implementing
authorised data mining that preserves privacy by granular
access authorization, 3) data security (can be resolved by
implementing secure data provenance and storage) and 4)
Integrity and reactive security (can be resolved by
implementing real time monitoring of anomalies and
attacks using IDS and IPS device). Also the study does not
discuss about the true challenges on maintaining end to
end data security and privacy in a big data environment
from the stage of ‘data creation’ to the stage of ‘data
usage’.
The research scholars of the third study paper [3]
reviewed the several security and privacy issues of Big
data in the perspective of cloud computing platform. The
authors described the several advantageous features of Big
data, cloud computing, virtualization and DevOps
technologies along with their associated security and
privacy issue concerns. The authors list the identified
security and privacy factors, that affect the activities of
cloud based service providers and the legal processioning
of consumer data in the context of genomic sequencing.
Although the study paper [3] also discusses the various
security and privacy solutions like Homomorphic
encryption, Anonymization, SAIL, ScaBIA, RBAC, PKI.
DPD, Bio Bank Cloud etc., it does not discuss the other
aspects of Big data security and privacy and thus lacks
holistic approach to resolve the security and privacy
concerns of Big data.
The concerned research article [4] discusses the various
benefits of using Big data technology to resolve the over
whelming information crisis in today’s information age.
However this study is concentrated on providing personal
privacy in the domain of big data platform. The authors of
the study elucidate four aspects to resolve the problem of
protecting personal privacy. The authors state their opinion
that only a combination of the technical means and legal
means can resolve the problem of security and personal
privacy of a data user in Big data environment. They
propose four innovative methods for ensuring personal and
data privacy in a big data environment, which are 1)
Implementing anonymity protection by implementing user
identity anonymity, attributes anonymity and relationship
anonymity, 2) Implementing digital watermarking
technology by embedding imperceptible watermarks
within the data carrier, database and text files 3)
Implementing Data Provence labelling technology to
accurately determine the source of the data in the data
warehouse. 4) Implement Role-based access control
(RBAC) to permissions set, to restrict unauthorized data
access and usage. The study [4] provides valuable policy
based security and privacy protection techniques to my
research but the authors fail to recommend any uniform
policy design structure for implementing data security and
personal privacy. However it focuses on a single aspect of
personal privacy security of all the various security and
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

PAPER IDENTIFICATION NUMBER
privacy issues facing Big data environment
implementation.
In the fifth paper [5], the authors have collected
adequate literature data on successful implementation of
privacy preservation methods in Big Data platform. They
first discuss about the numerous advantages and
drawbacks of implementing big data along with the
various presented privacy and security issues in each phase
of big data lifecycle in the context of big healthcare
domain. The study stresses on using encryption,
anonymization methods, Attribute based encryption
algorithm, Access control, Homomorphic encryption,
Storage path encryption and enhanced biometric devices.
However the study [5] fails to provide any future direction
or enhancement perspectives on the context of achieving
effective solutions in privacy and security in the era of big
data based healthcare data. Hence I suggest a detailed
further study based on the present study of protecting big
data based health care data.
In the sixth study paper [6] the research scholars have
initially detailed the various advantages and disadvantages
of implementing Big Data platform in citizen health care
domain. The authors propose to develop a holistic strategy
to protect and manage the sensitive health care data. In
today’s World, most companies are developing advanced
state of art business intelligence extraction techniques and
decision-making intelligence capabilities. However in Big
data it is a complex challenge due to its inherent extremely
large data volumes and high speed streaming velocities
and wide variety of structured, semi structured and
unstructured data formats. However the authors [6] fail to
provide a holistic strategy to resolve the be financial,
personal, and other types of data issues but their report
will helped me to clearly understand how to control and
protect sensitive information in the era of big data
augmented information age.
In the seventh article [7], Advantech a hardware vendor
company elaborates on the concerns about the security of
Big Data. To resolve the security and privacy issues they
suggest a software and hardware encryption technology
that operates on live selected data or on an entire data
warehouse, or on data at rest. But the challenge is
implementing software-based encryption adds a significant
extra load on a database server’s CPU and hence increases
the operational costs, along with operational complexity.
To resolve this issue Advantech recommends the usage of
Intel Distribution for Apache Hadoop software for
providing an enterprise ready Big Data analytics platform
which is highly optimized for performance, stability,
manageability, and security. This product accelerates the
data encryption process by up to 5.3 x and data decryption
by up to 19.8x thus providing a high-speed performance
and better security. Although the proposed Advantech
platforms [7] based on Intel Architecture for Apache
Hadoop processing, analytics and communications
Infrastructure provide a greater configurability, scalability
and performance it is not a holistic approach and focuses
11
privacy issues facing Big data environment
implementation.
In the fifth paper [5], the authors have collected
adequate literature data on successful implementation of
privacy preservation methods in Big Data platform. They
first discuss about the numerous advantages and
drawbacks of implementing big data along with the
various presented privacy and security issues in each phase
of big data lifecycle in the context of big healthcare
domain. The study stresses on using encryption,
anonymization methods, Attribute based encryption
algorithm, Access control, Homomorphic encryption,
Storage path encryption and enhanced biometric devices.
However the study [5] fails to provide any future direction
or enhancement perspectives on the context of achieving
effective solutions in privacy and security in the era of big
data based healthcare data. Hence I suggest a detailed
further study based on the present study of protecting big
data based health care data.
In the sixth study paper [6] the research scholars have
initially detailed the various advantages and disadvantages
of implementing Big Data platform in citizen health care
domain. The authors propose to develop a holistic strategy
to protect and manage the sensitive health care data. In
today’s World, most companies are developing advanced
state of art business intelligence extraction techniques and
decision-making intelligence capabilities. However in Big
data it is a complex challenge due to its inherent extremely
large data volumes and high speed streaming velocities
and wide variety of structured, semi structured and
unstructured data formats. However the authors [6] fail to
provide a holistic strategy to resolve the be financial,
personal, and other types of data issues but their report
will helped me to clearly understand how to control and
protect sensitive information in the era of big data
augmented information age.
In the seventh article [7], Advantech a hardware vendor
company elaborates on the concerns about the security of
Big Data. To resolve the security and privacy issues they
suggest a software and hardware encryption technology
that operates on live selected data or on an entire data
warehouse, or on data at rest. But the challenge is
implementing software-based encryption adds a significant
extra load on a database server’s CPU and hence increases
the operational costs, along with operational complexity.
To resolve this issue Advantech recommends the usage of
Intel Distribution for Apache Hadoop software for
providing an enterprise ready Big Data analytics platform
which is highly optimized for performance, stability,
manageability, and security. This product accelerates the
data encryption process by up to 5.3 x and data decryption
by up to 19.8x thus providing a high-speed performance
and better security. Although the proposed Advantech
platforms [7] based on Intel Architecture for Apache
Hadoop processing, analytics and communications
Infrastructure provide a greater configurability, scalability
and performance it is not a holistic approach and focuses
11

mainly on a hardware solution. An ideal solution must
contain both a hardware and software component to
provide security and privacy for the data and the user.
In the eight research paper [8] the research scholars
study various literature articles on the topic of providing
security and privacy in Big Data platform. They clearly
admit that it is impossible in the present day scenario to
design and implement a single perfect data management
solution for the cloud computing platform of Big Data as
each security systems protects only a single aspect in the
issue, and hence multiple open issue will remain. Hence
they propose a three step method to resolve the issue
starting with the first step of characterizing the different
consistency semantics such that they can be provided at
different scales, secondly implement effective techniques
for load balancing and lastly design scalable, elastic, and
autonomic multitenant database systems. Although the
study paper [8] provides valuable data on the best methods
to resolve security and privacy concern in big data
environment for my research study it fails to provide any
policy based strategy to resolve the concerns and hence it
does not adequately resolve the issue of security and
privacy of big data
In the ninth research paper [9], the authors suggest an
Open SDRM (Open Source Digital Rights Management)
system that allows content producers and providers to
create their own customized business model at a very
attractive price using a set of adaptive and standardized
components. The framework for this standard is being
developed by MOSES EC RTD project. As the existing
DRM schemes base their security on proprietary protection
methods, the authors propose an open source approach for
Digital Rights Management by designing OSDRM
platform. OSDRM provides open-source technology and
standards on an integrated architecture to enable content
producers to create custom protective measures for their
data. This research study paper [9] provides a very
innovative and holistic approach to resolve the security
and privacy concerns in Big data but does not provide
solutions to the other aspects of security and privacy of big
data. However the solution is novel that uses existing open
source technology to resolve Big data security and privacy
issues.
In the tenth research paper [10], the researchers have
proposed the implementation of a CTSMC model of an
intrusion tolerant system to be used with a dual mode of
switching time from an automatic detection mode to a
manual detection mode. The appropriate switching time
has been previously derived analytically using a statistical
estimation algorithm of 50 to 100 parallel SITAR
operations. Hence the optimal switching technique
effectively improves the system availability/MTTSF. In
the previous research studies, it has been clearly proved
that the combination of intrusion tolerance architecture
and a control of detection mode for intrusions were very
effective to manage the critical computer-based systems.
Although the research study paper [10] provides valuable
data for my research study of an efficient technique to
resolve security and privacy concerns in Big data
contain both a hardware and software component to
provide security and privacy for the data and the user.
In the eight research paper [8] the research scholars
study various literature articles on the topic of providing
security and privacy in Big Data platform. They clearly
admit that it is impossible in the present day scenario to
design and implement a single perfect data management
solution for the cloud computing platform of Big Data as
each security systems protects only a single aspect in the
issue, and hence multiple open issue will remain. Hence
they propose a three step method to resolve the issue
starting with the first step of characterizing the different
consistency semantics such that they can be provided at
different scales, secondly implement effective techniques
for load balancing and lastly design scalable, elastic, and
autonomic multitenant database systems. Although the
study paper [8] provides valuable data on the best methods
to resolve security and privacy concern in big data
environment for my research study it fails to provide any
policy based strategy to resolve the concerns and hence it
does not adequately resolve the issue of security and
privacy of big data
In the ninth research paper [9], the authors suggest an
Open SDRM (Open Source Digital Rights Management)
system that allows content producers and providers to
create their own customized business model at a very
attractive price using a set of adaptive and standardized
components. The framework for this standard is being
developed by MOSES EC RTD project. As the existing
DRM schemes base their security on proprietary protection
methods, the authors propose an open source approach for
Digital Rights Management by designing OSDRM
platform. OSDRM provides open-source technology and
standards on an integrated architecture to enable content
producers to create custom protective measures for their
data. This research study paper [9] provides a very
innovative and holistic approach to resolve the security
and privacy concerns in Big data but does not provide
solutions to the other aspects of security and privacy of big
data. However the solution is novel that uses existing open
source technology to resolve Big data security and privacy
issues.
In the tenth research paper [10], the researchers have
proposed the implementation of a CTSMC model of an
intrusion tolerant system to be used with a dual mode of
switching time from an automatic detection mode to a
manual detection mode. The appropriate switching time
has been previously derived analytically using a statistical
estimation algorithm of 50 to 100 parallel SITAR
operations. Hence the optimal switching technique
effectively improves the system availability/MTTSF. In
the previous research studies, it has been clearly proved
that the combination of intrusion tolerance architecture
and a control of detection mode for intrusions were very
effective to manage the critical computer-based systems.
Although the research study paper [10] provides valuable
data for my research study of an efficient technique to
resolve security and privacy concerns in Big data
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 17
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.



