Comprehensive Analysis of ENISA Big Data Security and IT Security
VerifiedAdded on 2019/11/25
|15
|3258
|221
Report
AI Summary
This report analyzes the ENISA's big data security infrastructure, focusing on various aspects such as threats, ETL processes, and IT security. The introduction highlights the increasing use of big data and associated security risks, particularly in cloud computing. The report addresses key questions, including an overview of the ENISA big data security infrastructure, a discussion of significant threats like web-based attacks, and an identification of threat agents like cybercriminals and cyber terrorists. It suggests improvements to the ETL process, emphasizing the need for enhanced security standards and collaboration. The report concludes by assessing ENISA's current state of IT security, offering insights into the challenges and recommendations for strengthening data protection and infrastructure resilience.
report
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Contents
Introduction......................................................................................................................................2
Question 1:.......................................................................................................................................2
Question 2:.......................................................................................................................................5
Question 3:.......................................................................................................................................7
Question 4:.......................................................................................................................................9
Question 5:.....................................................................................................................................11
Conclusion.....................................................................................................................................12
References......................................................................................................................................13
Introduction......................................................................................................................................2
Question 1:.......................................................................................................................................2
Question 2:.......................................................................................................................................5
Question 3:.......................................................................................................................................7
Question 4:.......................................................................................................................................9
Question 5:.....................................................................................................................................11
Conclusion.....................................................................................................................................12
References......................................................................................................................................13

Introduction
The big data is used in the different areas which brings a drastic change in the applications which
are being used. Along with this, there is a proper setup of the changes with the implementation of
the security risk patterns as well (Ko et al., 2016). . The analysis is based on how ENISA is
involved in the cloud computing and the big data which includes the applications focusing on the
different given sectors. The standards are set for the research with the focus on processing all the
personal information which is set in context to the serious privacy concerns. It includes the wide
scale technologies, profiling and disclosures for handling the surveillance, profiling and the
disclosures of the different private data patterns (Takabi et al., 2010).
Question 1:
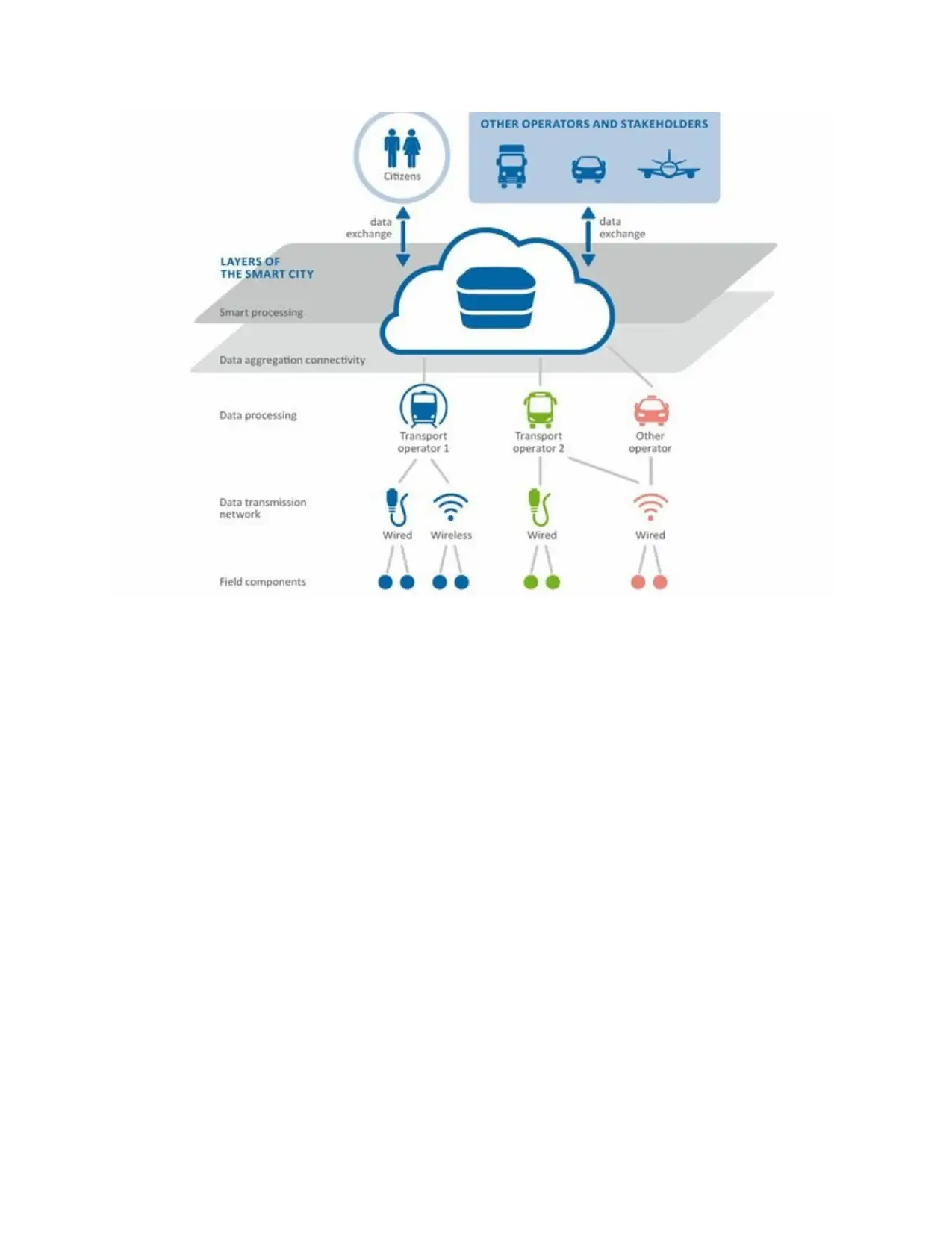
1) Provide a brief overview of the case study and prepare a diagram for the ENISA Big
Data security infrastructure.
The aim of the work is to focus on the ENISA data security infrastructure which includes the
organisation working in the different sectors. The analysis is based on handling and working
over the research centres, public organisations and in the different government agencies. The
new business models are based on the aggregation and the analysis of the larger and the fast
growing of the data. with this, it is also possible to work on the relative wide scale functioning
through the use of profiling and the electronic surveillance. The importance is mainly to integrate
the systems and improve the data protection safeguard methods with the analytical value chain
analysisThe analysis is based on data protection safeguards with the analytics set for the value
chain. The aim of the report is to focus on the challenges and the technology for big data. This
includes the different technologies and the opportunities mainly for the privacy standards. The
The big data is used in the different areas which brings a drastic change in the applications which
are being used. Along with this, there is a proper setup of the changes with the implementation of
the security risk patterns as well (Ko et al., 2016). . The analysis is based on how ENISA is
involved in the cloud computing and the big data which includes the applications focusing on the
different given sectors. The standards are set for the research with the focus on processing all the
personal information which is set in context to the serious privacy concerns. It includes the wide
scale technologies, profiling and disclosures for handling the surveillance, profiling and the
disclosures of the different private data patterns (Takabi et al., 2010).
Question 1:
1) Provide a brief overview of the case study and prepare a diagram for the ENISA Big
Data security infrastructure.
The aim of the work is to focus on the ENISA data security infrastructure which includes the
organisation working in the different sectors. The analysis is based on handling and working
over the research centres, public organisations and in the different government agencies. The
new business models are based on the aggregation and the analysis of the larger and the fast
growing of the data. with this, it is also possible to work on the relative wide scale functioning
through the use of profiling and the electronic surveillance. The importance is mainly to integrate
the systems and improve the data protection safeguard methods with the analytical value chain
analysisThe analysis is based on data protection safeguards with the analytics set for the value
chain. The aim of the report is to focus on the challenges and the technology for big data. This
includes the different technologies and the opportunities mainly for the privacy standards. The
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

smarter infrastructures generally include the activities like the energy, deployment and the
operations of the cyber physical system that are controlled by the equipment of the data and the
interaction is mainly to collaborate and work on the exchanging of data under the different
schemes which include the different levels of maturity as well. For this, the usage is depending
upon the software controlled devices with the check on how the risks and the economy is
collaborated with the data controlled equipment (Pearson et al., 2010). There are different
schemes which are based on handling the software controlled devices with proper interaction that
includes the physical world. The trends of the critical infrastructures include the smart
infrastructure with deploying the IoT. ENISA works on the development of the secured smart
infrastructures that comes from the cyber threats and by properly highlighting any of the security
practices and the recommendations.
operations of the cyber physical system that are controlled by the equipment of the data and the
interaction is mainly to collaborate and work on the exchanging of data under the different
schemes which include the different levels of maturity as well. For this, the usage is depending
upon the software controlled devices with the check on how the risks and the economy is
collaborated with the data controlled equipment (Pearson et al., 2010). There are different
schemes which are based on handling the software controlled devices with proper interaction that
includes the physical world. The trends of the critical infrastructures include the smart
infrastructure with deploying the IoT. ENISA works on the development of the secured smart
infrastructures that comes from the cyber threats and by properly highlighting any of the security
practices and the recommendations.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Question 2:
2) Out of the ‘’Top threats’’ which threat would you regard to be the most significant and
why?
The web threats are the WWW threats which are mainly set to facilitate the cybercrime. It
includes the use of the different types of the malware and the fraud that is to handle the HTTP
and HTTPs protocols which includes the employing of the other protocols and the components.
There are broad range of the risks which include the financial risks which includes the loss of
information as well. The web based attacks mainly hamper the security and the integrity of the
system, wherein it is important to handle the information based on the identity theft. There are
different targets which need to be handled with the unprotected and the unencrypted uses. The
application vulnerabilities are based on the malicious end users to handle the system breach with
the protection mechanism which is based on gaining access to the private information. The
information is mainly from the different areas through the unprotected and the unencrypted
forms which could be used to damage the organisation and its valued assets. The customers need
to focus on the spoofing methods with mimicking the other users or the processes to perform the
tasks based on retrieving the information (Popovic et al., 2010). The specific actions are for the
single user and how the applications like the web access, authentication and the different
transaction logs of the database are handled. The online web applications work with the users
and how one can easily claim the changes with the information disclosures as well. The
authorisation controls are reliable with the requisites that are based on the system and the
applications which include all the important and the sensitive information (Pearson, 2013). For
ENISA, it is important to focus on the level of risks which are different for the different
2) Out of the ‘’Top threats’’ which threat would you regard to be the most significant and
why?
The web threats are the WWW threats which are mainly set to facilitate the cybercrime. It
includes the use of the different types of the malware and the fraud that is to handle the HTTP
and HTTPs protocols which includes the employing of the other protocols and the components.
There are broad range of the risks which include the financial risks which includes the loss of
information as well. The web based attacks mainly hamper the security and the integrity of the
system, wherein it is important to handle the information based on the identity theft. There are
different targets which need to be handled with the unprotected and the unencrypted uses. The
application vulnerabilities are based on the malicious end users to handle the system breach with
the protection mechanism which is based on gaining access to the private information. The
information is mainly from the different areas through the unprotected and the unencrypted
forms which could be used to damage the organisation and its valued assets. The customers need
to focus on the spoofing methods with mimicking the other users or the processes to perform the
tasks based on retrieving the information (Popovic et al., 2010). The specific actions are for the
single user and how the applications like the web access, authentication and the different
transaction logs of the database are handled. The online web applications work with the users
and how one can easily claim the changes with the information disclosures as well. The
authorisation controls are reliable with the requisites that are based on the system and the
applications which include all the important and the sensitive information (Pearson, 2013). For
ENISA, it is important to focus on the level of risks which are different for the different
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

organisations. There are different threat levels which are set for intellectual property and how the
intellects work on the information that has been stored by the organisation. The success of the
companies and the reputation is mainly depending upon the patents and the research,
development which includes the standardised approach for the vulnerability prevention and work
on the framework which starts with the developers. The software architecture includes the
building of the physical structures and the planning is mainly to adhere to the fundamental
software development methodologies. The software attacks and the other sorts of exploitation
detection is mainly to provide a better level of error check (Gonzalez et al., 2010). The attack
detection and prevention is mainly for the deployment set with the demilitarised zones of the
corporate network where the applications are depending upon the network traffic which works
on the intrusion detection systems upon the detection of the attack, where one can drop the
packets and then sent TCP packets to the malicious servers (Mahmood, 2011).
intellects work on the information that has been stored by the organisation. The success of the
companies and the reputation is mainly depending upon the patents and the research,
development which includes the standardised approach for the vulnerability prevention and work
on the framework which starts with the developers. The software architecture includes the
building of the physical structures and the planning is mainly to adhere to the fundamental
software development methodologies. The software attacks and the other sorts of exploitation
detection is mainly to provide a better level of error check (Gonzalez et al., 2010). The attack
detection and prevention is mainly for the deployment set with the demilitarised zones of the
corporate network where the applications are depending upon the network traffic which works
on the intrusion detection systems upon the detection of the attack, where one can drop the
packets and then sent TCP packets to the malicious servers (Mahmood, 2011).
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Question 3:
3) Identify and discuss the key Threat Agents. What could be done to minimize their
impact on the system? Based on the data provided, discuss the trends in threat probability.
The threat agents are based on the roles which include the deployment where there are:
a. The cyber criminals who are able to handle the illicit actions with the different agent
groups to make the profit in the cyberspace. The major motivation is for the actions and
how the monetisation and intelligence is directed. The roles involve the programmers and
the distributors for the IT experts who are able to develop requirements with the proper
use of the cybercriminal organisations (Lombardi et al., 2011). The security threats
include the malicious codes, web based attacks, botnets and the denial of service,
spamming, phishing and the other insider threats.
b. The cyber fighters are also related to the national motivation of the citizens which
includes and cause a damage to the different sabotages. The publishing of the video
messages and the breached data is mainly to get the attention of public. There are
increased cases which have been mainly evolved with the use of the sophisticated
technology to gain the sensitivity of the data.
c. The cyber terrorists also include how they are motivated for the groups which includes
the threats mainly to the national security that targets the large-scale areas. The
discrimination of the different groups is based on positioning the violence related videos
which leads to the disruptions mainly in between the religious groups for the gain of the
personal agendas. The evolvement of the group of agents include the web based attacks,
denial of service, spam and the phishing modules (Khajeh et al., 2010).
3) Identify and discuss the key Threat Agents. What could be done to minimize their
impact on the system? Based on the data provided, discuss the trends in threat probability.
The threat agents are based on the roles which include the deployment where there are:
a. The cyber criminals who are able to handle the illicit actions with the different agent
groups to make the profit in the cyberspace. The major motivation is for the actions and
how the monetisation and intelligence is directed. The roles involve the programmers and
the distributors for the IT experts who are able to develop requirements with the proper
use of the cybercriminal organisations (Lombardi et al., 2011). The security threats
include the malicious codes, web based attacks, botnets and the denial of service,
spamming, phishing and the other insider threats.
b. The cyber fighters are also related to the national motivation of the citizens which
includes and cause a damage to the different sabotages. The publishing of the video
messages and the breached data is mainly to get the attention of public. There are
increased cases which have been mainly evolved with the use of the sophisticated
technology to gain the sensitivity of the data.
c. The cyber terrorists also include how they are motivated for the groups which includes
the threats mainly to the national security that targets the large-scale areas. The
discrimination of the different groups is based on positioning the violence related videos
which leads to the disruptions mainly in between the religious groups for the gain of the
personal agendas. The evolvement of the group of agents include the web based attacks,
denial of service, spam and the phishing modules (Khajeh et al., 2010).

There are different preventive measures which include the structuring and handling the measures
related to the cloud computing, mobile computing and the big data. hence, there is a need to
handle and update the firewalls. This will help in making sure that the data kept is set in a proper
manner. With this, the setting of the stronger passwords with the updation of the token
passwords is also needed. The updates of the firmware and the higher security layered structures
are for the anti-virus protection. The frequent monitoring processes with the anti-virus protection
is important for handling the network traffics as well as the employee logging data. The creation
of the standardised security policies with the increased employee awareness is based on the
security and the safety actions. The increased employee awareness is mainly based on the
security and the safety actions as well. The threats are monitored with the processing and
examining based on the potential to impact the organisation (Hashizume et al, 2013). The frame
works on the addressing of the different challenges where the organisation assets and the
vulnerabilities are evaluated based on the processing of the work with the diversified
backgrounds. Here, the residual risks are for the threats and how the associated vulnerabilities
lead to the creation of preliminary lists of different controlled ideas.
related to the cloud computing, mobile computing and the big data. hence, there is a need to
handle and update the firewalls. This will help in making sure that the data kept is set in a proper
manner. With this, the setting of the stronger passwords with the updation of the token
passwords is also needed. The updates of the firmware and the higher security layered structures
are for the anti-virus protection. The frequent monitoring processes with the anti-virus protection
is important for handling the network traffics as well as the employee logging data. The creation
of the standardised security policies with the increased employee awareness is based on the
security and the safety actions. The increased employee awareness is mainly based on the
security and the safety actions as well. The threats are monitored with the processing and
examining based on the potential to impact the organisation (Hashizume et al, 2013). The frame
works on the addressing of the different challenges where the organisation assets and the
vulnerabilities are evaluated based on the processing of the work with the diversified
backgrounds. Here, the residual risks are for the threats and how the associated vulnerabilities
lead to the creation of preliminary lists of different controlled ideas.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

Question 4:
4) How could the ETL process be improved? Discuss.
The ENISA Threat Landscape processes could be improved through the major focus on the
increased sophistication of the attacks and the tools. It includes that there are different cyber
activities which includes the development of the capabilities and the measurements that are set
for the attacking patterns. Here, there are different digital battlefields which have been set for the
big data and the Internet of Things. ENISA need to work on the improvement of the network and
the information security standards where the groups are set to develop and advice for all the
important information security practices. This works on balancing and handling the development
depending upon the improved network and the information security standards. ETL is mainly
subjected to process and work on the different applications which includes how the lessons are
evaluated with the threat processes (Kuo, 2011). The evaluation is based on working over the
current state of play with the balance manly in between the practicality and the quality, cost and
effort. The project includes the forces where ENISA need to handle the leveraging on synergies
with the use of the open source approaches, tools and the data. this will help in implementing the
improvement options along with handling the data which is existing. For achieving this, there are
different contracts which works on the optimisation and the improvement options. ETL works on
the sharing of the information and should be improved based on the organisation adopting all the
important countermeasures. The report is about handling the targets with the internet
infrastructure, organisations and the security experts with the strong policy makers. The study is
about allowing the assets with the reports that include the improvement of the security
architecture and the tools which are expose on the internet (Almorsy et al., 2016). The categories
4) How could the ETL process be improved? Discuss.
The ENISA Threat Landscape processes could be improved through the major focus on the
increased sophistication of the attacks and the tools. It includes that there are different cyber
activities which includes the development of the capabilities and the measurements that are set
for the attacking patterns. Here, there are different digital battlefields which have been set for the
big data and the Internet of Things. ENISA need to work on the improvement of the network and
the information security standards where the groups are set to develop and advice for all the
important information security practices. This works on balancing and handling the development
depending upon the improved network and the information security standards. ETL is mainly
subjected to process and work on the different applications which includes how the lessons are
evaluated with the threat processes (Kuo, 2011). The evaluation is based on working over the
current state of play with the balance manly in between the practicality and the quality, cost and
effort. The project includes the forces where ENISA need to handle the leveraging on synergies
with the use of the open source approaches, tools and the data. this will help in implementing the
improvement options along with handling the data which is existing. For achieving this, there are
different contracts which works on the optimisation and the improvement options. ETL works on
the sharing of the information and should be improved based on the organisation adopting all the
important countermeasures. The report is about handling the targets with the internet
infrastructure, organisations and the security experts with the strong policy makers. The study is
about allowing the assets with the reports that include the improvement of the security
architecture and the tools which are expose on the internet (Almorsy et al., 2016). The categories
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

are related to the physical attacks that depend on the disasters including the natural disasters and
the other environmental disasters. The failure or the malfunctioning also need to be improved
with recommendations that are for properly evaluating the current level of security. The
understanding is also about the security measures with the focus on the internet infrastructure
owners and to cooperate with the community to work with the exchange in threats and promoting
better applications of the good practices with mitigating measures. The organisation need to
handle the infrastructure with proper use of the assessment methods that works on evaluating the
protecting actions. The communication technology is for the security awareness and the training
programs with the current stay on the different updates. ENISA need to work on the handling of
the firewall security with the check on the different security threats and the DDos attacks which
leads to the reduction of infected servers (Chen et al., 2010). The threat trends are of the threats
which include the varying evolution with the botnets and ransomware. This is attributed mainly
to the enforcement which includes the infrastructure criminal crew use with the consideration
about the exploring of various threat modelling approaches.
the other environmental disasters. The failure or the malfunctioning also need to be improved
with recommendations that are for properly evaluating the current level of security. The
understanding is also about the security measures with the focus on the internet infrastructure
owners and to cooperate with the community to work with the exchange in threats and promoting
better applications of the good practices with mitigating measures. The organisation need to
handle the infrastructure with proper use of the assessment methods that works on evaluating the
protecting actions. The communication technology is for the security awareness and the training
programs with the current stay on the different updates. ENISA need to work on the handling of
the firewall security with the check on the different security threats and the DDos attacks which
leads to the reduction of infected servers (Chen et al., 2010). The threat trends are of the threats
which include the varying evolution with the botnets and ransomware. This is attributed mainly
to the enforcement which includes the infrastructure criminal crew use with the consideration
about the exploring of various threat modelling approaches.

Question 5:
5) To sum up, should ENISA be satisfied with its current state of IT Security? Why? Or
Why not?
As per my opinion, ENISA should focus on not only satisfying the needs with the current state of
the IT security but also focus on improvising the stronger engineering capabilities. The focus is
on the competitive standards with the attackers through the cyber security. Hence, to overcome
and handle the issues, there is a need to handle the threat governments which are adapting the
technological developments. With this, there is a proper storage of the information with the
precautions that are based on handling the easy access to the system. The protection is mainly
through the firewall and how the blocking of any unauthorised users could be handled. ENISA
need to focus on prompting the opposition powers with the points that include the assorted
qualities which have different suggestions of security (Sultan, 2011). With this, there are other
forms which include how EU Commission will be able to guarantee and work on the
presentation of different purposes.
ENISA need to focus on the promotional risks and the assessment with the risks management
which will be mainly dealing with the network and the other security measures. The promotional
risks assessment and the management is mainly to invest in the efforts of promoting the methods,
tools and the practices for continuity management. The business processes are related to the
increased links that are set for the communication technology. It includes the technical systems
with the identification of managing the reduced likelihood or the impacts. The continuity is set
with the series of management processes and the integrated plans that leads to maintaining the
continuity with the processes of the organisation. ICT systems need to focus on the electronic
5) To sum up, should ENISA be satisfied with its current state of IT Security? Why? Or
Why not?
As per my opinion, ENISA should focus on not only satisfying the needs with the current state of
the IT security but also focus on improvising the stronger engineering capabilities. The focus is
on the competitive standards with the attackers through the cyber security. Hence, to overcome
and handle the issues, there is a need to handle the threat governments which are adapting the
technological developments. With this, there is a proper storage of the information with the
precautions that are based on handling the easy access to the system. The protection is mainly
through the firewall and how the blocking of any unauthorised users could be handled. ENISA
need to focus on prompting the opposition powers with the points that include the assorted
qualities which have different suggestions of security (Sultan, 2011). With this, there are other
forms which include how EU Commission will be able to guarantee and work on the
presentation of different purposes.
ENISA need to focus on the promotional risks and the assessment with the risks management
which will be mainly dealing with the network and the other security measures. The promotional
risks assessment and the management is mainly to invest in the efforts of promoting the methods,
tools and the practices for continuity management. The business processes are related to the
increased links that are set for the communication technology. It includes the technical systems
with the identification of managing the reduced likelihood or the impacts. The continuity is set
with the series of management processes and the integrated plans that leads to maintaining the
continuity with the processes of the organisation. ICT systems need to focus on the electronic
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 15
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





