Literature Review: Differential Privacy for Big Data Security
VerifiedAdded on 2021/04/24
|25
|4078
|68
Literature Review
AI Summary
This document presents a comprehensive literature review on differential privacy mechanisms in the context of big data applications. It analyzes three research papers, each exploring different aspects of privacy-preserving techniques. The first paper, "Differential Privacy of Big Data: An Overview," examines various differential privacy mechanisms, including the Matrix mechanism and MWEM algorithm, and their application in securing statistical databases and data mining. It highlights the importance of differential privacy in addressing the vulnerabilities of current security approaches. The second paper, "Privacy-preserving utility verification of the data published by non-interactive differentially private mechanisms," focuses on the challenges of collaborative data publishing and utility verification. It proposes methods to ensure data privacy through encryption and verification mechanisms. The third paper, "Improving the utility in differential private histogram publishing: Theoretical study and practice," explores techniques to enhance the utility of differentially private histogram publishing. The review critically assesses each paper, evaluating the methods, analyses, and conclusions, and identifies potential areas for improvement and further research. It emphasizes the importance of differential privacy in safeguarding sensitive data and ensuring its secure utilization in various applications.
Literature Review (Secondary Research) Template
Student Name &
CSU ID
Project Topic Title
NOTE: Please you need to use YOUR OWN WORDS in writing this template.
Your Literature Review Should be in Scope and MUST Address all Your Project's Questions
You should ONLY use CSU library, or other University Library, and Google search is NOT allowed. The papers
you select should be in last 3 years. If you are in 2018, then you need to collect 2018, 2017, and 2016.
We encourage you to search for Journal papers rather than conference papers as it will give you more
details.
Check the Journal ranking (Q1, Q2, …etc) of the journal based on uploaded excel sheet in interact.
1
Student Name &
CSU ID
Project Topic Title
NOTE: Please you need to use YOUR OWN WORDS in writing this template.
Your Literature Review Should be in Scope and MUST Address all Your Project's Questions
You should ONLY use CSU library, or other University Library, and Google search is NOT allowed. The papers
you select should be in last 3 years. If you are in 2018, then you need to collect 2018, 2017, and 2016.
We encourage you to search for Journal papers rather than conference papers as it will give you more
details.
Check the Journal ranking (Q1, Q2, …etc) of the journal based on uploaded excel sheet in interact.
1
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Example (How to work on each section in template below):
2
2

3
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
Version 1.0 _ Week 1
1
Reference in APA format
URL of the Reference Authors Names and Emails
and Level of Journal (Q1, Q2, …
Qn)
Keywords in this Reference
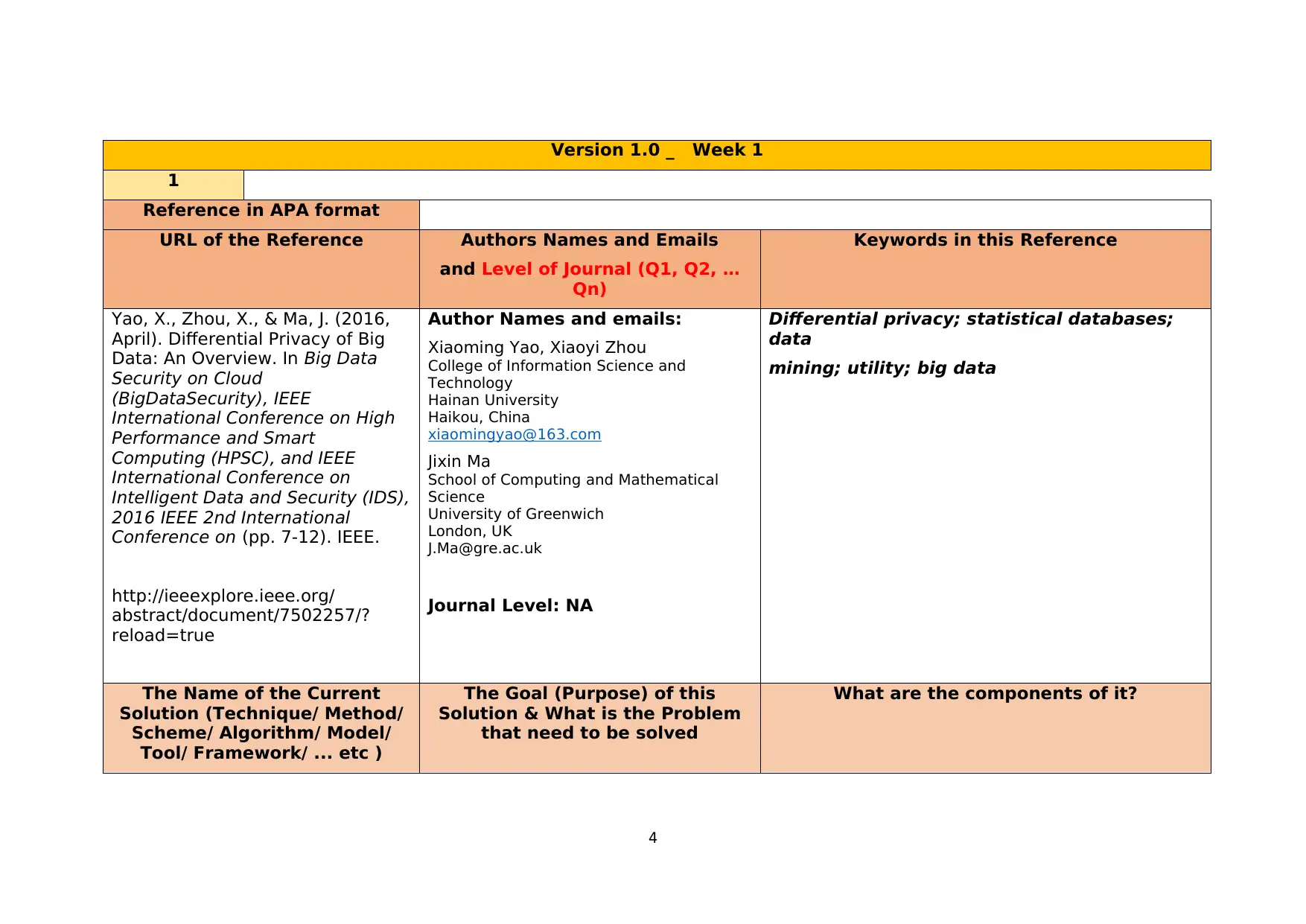
Yao, X., Zhou, X., & Ma, J. (2016,
April). Differential Privacy of Big
Data: An Overview. In Big Data
Security on Cloud
(BigDataSecurity), IEEE
International Conference on High
Performance and Smart
Computing (HPSC), and IEEE
International Conference on
Intelligent Data and Security (IDS),
2016 IEEE 2nd International
Conference on (pp. 7-12). IEEE.
http://ieeexplore.ieee.org/
abstract/document/7502257/?
reload=true
Author Names and emails:
Xiaoming Yao, Xiaoyi Zhou
College of Information Science and
Technology
Hainan University
Haikou, China
xiaomingyao@163.com
Jixin Ma
School of Computing and Mathematical
Science
University of Greenwich
London, UK
J.Ma@gre.ac.uk
Journal Level: NA
Differential privacy; statistical databases;
data
mining; utility; big data
The Name of the Current
Solution (Technique/ Method/
Scheme/ Algorithm/ Model/
Tool/ Framework/ ... etc )
The Goal (Purpose) of this
Solution & What is the Problem
that need to be solved
What are the components of it?
4
1
Reference in APA format
URL of the Reference Authors Names and Emails
and Level of Journal (Q1, Q2, …
Qn)
Keywords in this Reference
Yao, X., Zhou, X., & Ma, J. (2016,
April). Differential Privacy of Big
Data: An Overview. In Big Data
Security on Cloud
(BigDataSecurity), IEEE
International Conference on High
Performance and Smart
Computing (HPSC), and IEEE
International Conference on
Intelligent Data and Security (IDS),
2016 IEEE 2nd International
Conference on (pp. 7-12). IEEE.
http://ieeexplore.ieee.org/
abstract/document/7502257/?
reload=true
Author Names and emails:
Xiaoming Yao, Xiaoyi Zhou
College of Information Science and
Technology
Hainan University
Haikou, China
xiaomingyao@163.com
Jixin Ma
School of Computing and Mathematical
Science
University of Greenwich
London, UK
J.Ma@gre.ac.uk
Journal Level: NA
Differential privacy; statistical databases;
data
mining; utility; big data
The Name of the Current
Solution (Technique/ Method/
Scheme/ Algorithm/ Model/
Tool/ Framework/ ... etc )
The Goal (Purpose) of this
Solution & What is the Problem
that need to be solved
What are the components of it?
4
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
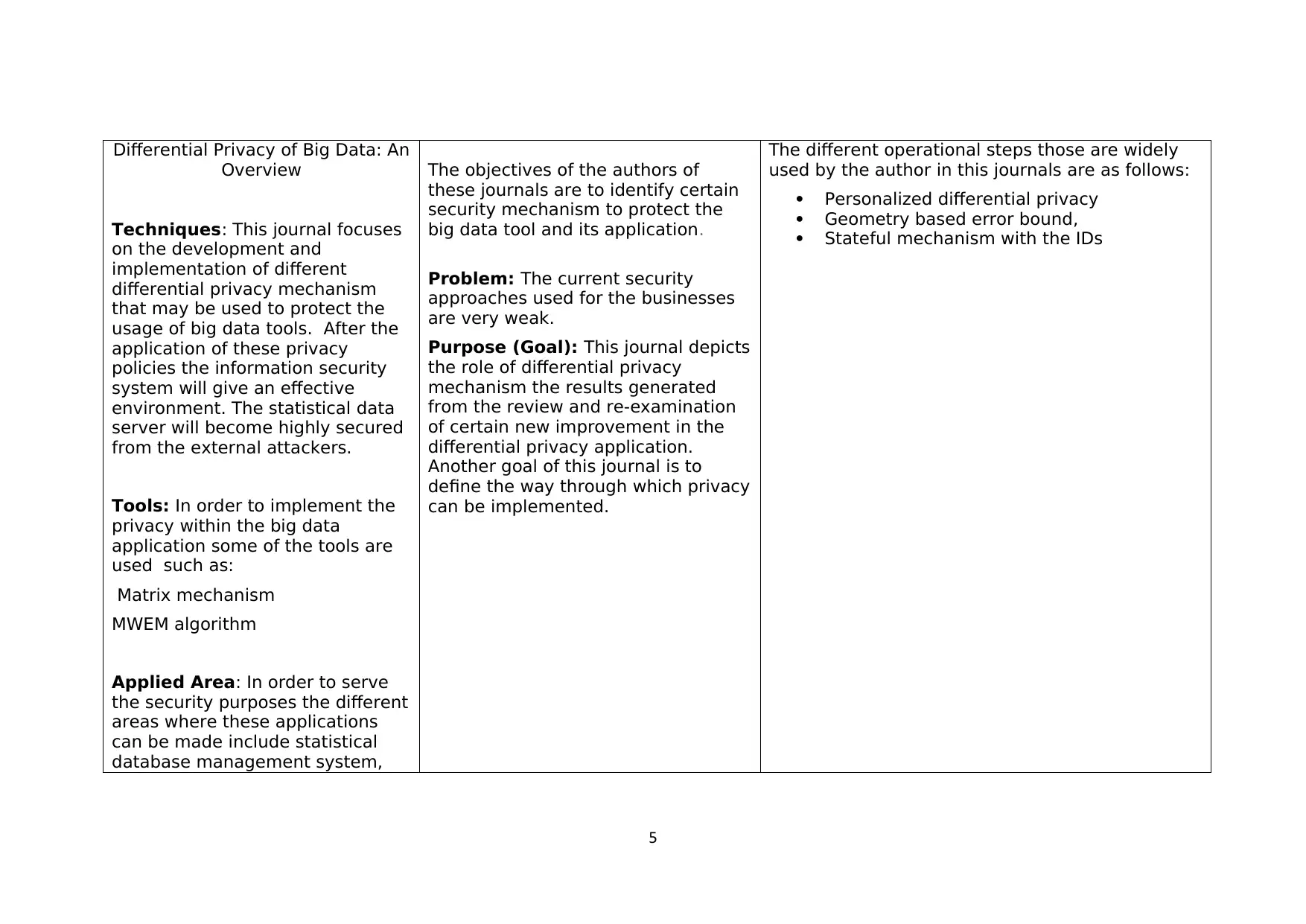
Differential Privacy of Big Data: An
Overview
Techniques: This journal focuses
on the development and
implementation of different
differential privacy mechanism
that may be used to protect the
usage of big data tools. After the
application of these privacy
policies the information security
system will give an effective
environment. The statistical data
server will become highly secured
from the external attackers.
Tools: In order to implement the
privacy within the big data
application some of the tools are
used such as:
Matrix mechanism
MWEM algorithm
Applied Area: In order to serve
the security purposes the different
areas where these applications
can be made include statistical
database management system,
The objectives of the authors of
these journals are to identify certain
security mechanism to protect the
big data tool and its application.
Problem: The current security
approaches used for the businesses
are very weak.
Purpose (Goal): This journal depicts
the role of differential privacy
mechanism the results generated
from the review and re-examination
of certain new improvement in the
differential privacy application.
Another goal of this journal is to
define the way through which privacy
can be implemented.
The different operational steps those are widely
used by the author in this journals are as follows:
Personalized differential privacy
Geometry based error bound,
Stateful mechanism with the IDs
5
Overview
Techniques: This journal focuses
on the development and
implementation of different
differential privacy mechanism
that may be used to protect the
usage of big data tools. After the
application of these privacy
policies the information security
system will give an effective
environment. The statistical data
server will become highly secured
from the external attackers.
Tools: In order to implement the
privacy within the big data
application some of the tools are
used such as:
Matrix mechanism
MWEM algorithm
Applied Area: In order to serve
the security purposes the different
areas where these applications
can be made include statistical
database management system,
The objectives of the authors of
these journals are to identify certain
security mechanism to protect the
big data tool and its application.
Problem: The current security
approaches used for the businesses
are very weak.
Purpose (Goal): This journal depicts
the role of differential privacy
mechanism the results generated
from the review and re-examination
of certain new improvement in the
differential privacy application.
Another goal of this journal is to
define the way through which privacy
can be implemented.
The different operational steps those are widely
used by the author in this journals are as follows:
Personalized differential privacy
Geometry based error bound,
Stateful mechanism with the IDs
5
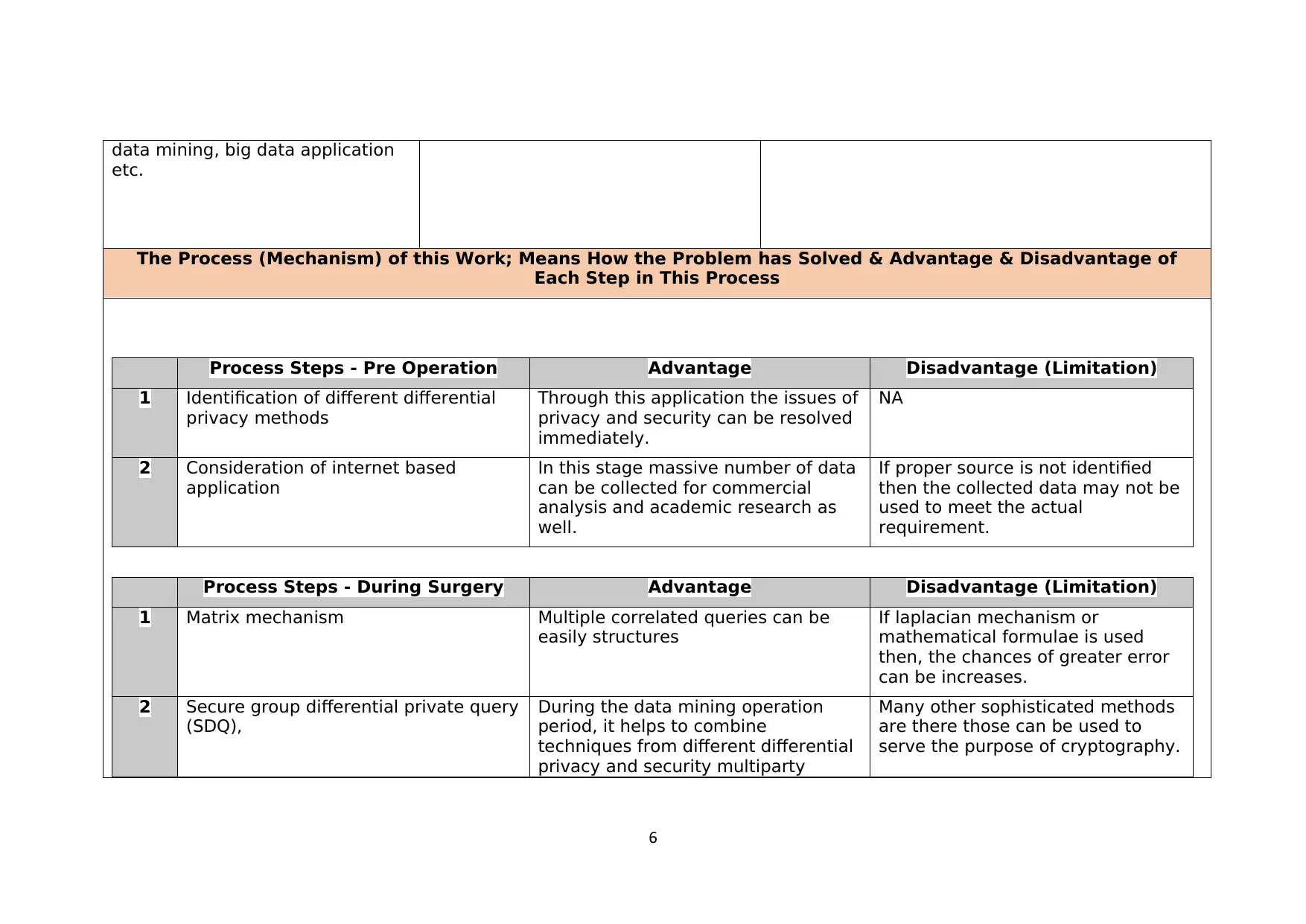
data mining, big data application
etc.
The Process (Mechanism) of this Work; Means How the Problem has Solved & Advantage & Disadvantage of
Each Step in This Process
Process Steps - Pre Operation Advantage Disadvantage (Limitation)
1 Identification of different differential
privacy methods
Through this application the issues of
privacy and security can be resolved
immediately.
NA
2 Consideration of internet based
application
In this stage massive number of data
can be collected for commercial
analysis and academic research as
well.
If proper source is not identified
then the collected data may not be
used to meet the actual
requirement.
Process Steps - During Surgery Advantage Disadvantage (Limitation)
1 Matrix mechanism Multiple correlated queries can be
easily structures
If laplacian mechanism or
mathematical formulae is used
then, the chances of greater error
can be increases.
2 Secure group differential private query
(SDQ),
During the data mining operation
period, it helps to combine
techniques from different differential
privacy and security multiparty
Many other sophisticated methods
are there those can be used to
serve the purpose of cryptography.
6
etc.
The Process (Mechanism) of this Work; Means How the Problem has Solved & Advantage & Disadvantage of
Each Step in This Process
Process Steps - Pre Operation Advantage Disadvantage (Limitation)
1 Identification of different differential
privacy methods
Through this application the issues of
privacy and security can be resolved
immediately.
NA
2 Consideration of internet based
application
In this stage massive number of data
can be collected for commercial
analysis and academic research as
well.
If proper source is not identified
then the collected data may not be
used to meet the actual
requirement.
Process Steps - During Surgery Advantage Disadvantage (Limitation)
1 Matrix mechanism Multiple correlated queries can be
easily structures
If laplacian mechanism or
mathematical formulae is used
then, the chances of greater error
can be increases.
2 Secure group differential private query
(SDQ),
During the data mining operation
period, it helps to combine
techniques from different differential
privacy and security multiparty
Many other sophisticated methods
are there those can be used to
serve the purpose of cryptography.
6
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
computation. The intermediate data
will become completely protected
during the data mining operation.
3 Process optimization It helps to restrict all the errors The workloads of the queries are
supposed to known as quite
advanced.
4 Linear query mechanism It also helps to reduce the rate of
error
These linear queries can be carried
out many times but each time their
sensitivity also differs a lot.
Major Impact Factors in this Work
Dependent Variable Independent Variable
Big data tool and its application in the organization.
Big data tool is the dependent variable here because
it cannot be used securely without the application of
proper differential privacy mechanism.
Differential privacy mechanisms such as Laplacian
mechanism, MWEM algorithm, Matrix algorithm are the
dependent variable.
Input and Output Feature of This Solution Contribution & The Value of This Work
Input - Pre
Operation
Output - Pre
Operation
I think that this particular journal is
very much valuable for both the
business and information security
perspectives. It shows different
differential security mechanism and its
The authors have applied different
mathematical derivation to make the big
data privacy solution effective for the users.
Not only will this but also with the help of
the mathematical application the statistical
7
will become completely protected
during the data mining operation.
3 Process optimization It helps to restrict all the errors The workloads of the queries are
supposed to known as quite
advanced.
4 Linear query mechanism It also helps to reduce the rate of
error
These linear queries can be carried
out many times but each time their
sensitivity also differs a lot.
Major Impact Factors in this Work
Dependent Variable Independent Variable
Big data tool and its application in the organization.
Big data tool is the dependent variable here because
it cannot be used securely without the application of
proper differential privacy mechanism.
Differential privacy mechanisms such as Laplacian
mechanism, MWEM algorithm, Matrix algorithm are the
dependent variable.
Input and Output Feature of This Solution Contribution & The Value of This Work
Input - Pre
Operation
Output - Pre
Operation
I think that this particular journal is
very much valuable for both the
business and information security
perspectives. It shows different
differential security mechanism and its
The authors have applied different
mathematical derivation to make the big
data privacy solution effective for the users.
Not only will this but also with the help of
the mathematical application the statistical
7
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
Input - During
Surgery
Output - During
Surgery
During the
application
mechanism of
MWEM algorithm
it has been found
that, the inputs
during the
application are
dataset, value of
the data and
privacy budget.
Proper privacy to
the bi data tool
an its application
application as well. These security
mechanisms can be used by the
information security officers to protect
their data set from the external
assaults.
database become much secure and
technically strong.
1. what in the method could have
been better?
2. what in the author analyses
were missed?
3. was there a technique that could
have been used, or a question that
could have been asked, that the
researchers did not use or ask?
Cryptograph is the only combination or
mechanism which required further
improvement. Other no such kinds of
method are mentioned in this journal
that requires further improvement. It
already provides a better trade off
between the privacy and the datasets
utility.
Some kids of challenges are found with the
cryptography combination and the authors
have failed to identify those areas of analysis.
Another question is there that can be asked to the
author to gain further result from the analysis.
4. Were the conclusion justified
and How?
Analyse This Work By Critical
Thinking
The Tools That Assessed this Work
Yes, the conclusion is completely 1. Different advanced mathematical The practical applications those are used
8
Surgery
Output - During
Surgery
During the
application
mechanism of
MWEM algorithm
it has been found
that, the inputs
during the
application are
dataset, value of
the data and
privacy budget.
Proper privacy to
the bi data tool
an its application
application as well. These security
mechanisms can be used by the
information security officers to protect
their data set from the external
assaults.
database become much secure and
technically strong.
1. what in the method could have
been better?
2. what in the author analyses
were missed?
3. was there a technique that could
have been used, or a question that
could have been asked, that the
researchers did not use or ask?
Cryptograph is the only combination or
mechanism which required further
improvement. Other no such kinds of
method are mentioned in this journal
that requires further improvement. It
already provides a better trade off
between the privacy and the datasets
utility.
Some kids of challenges are found with the
cryptography combination and the authors
have failed to identify those areas of analysis.
Another question is there that can be asked to the
author to gain further result from the analysis.
4. Were the conclusion justified
and How?
Analyse This Work By Critical
Thinking
The Tools That Assessed this Work
Yes, the conclusion is completely 1. Different advanced mathematical The practical applications those are used
8
justified because these differential
privacy mechanisms can preserve the
privacy of the datasets and all other
correlated processes.
approaches are used for further
success of protecting datasets from
external assaults.
2. The author fails to identify the all
the cryptographic concept those are
necessary for securing information
stored in the data server. Due to lack
of security approaches, information
may get hijacked by the external
attackers.
identified and applied in this journal include
Matrix mechanism and MWEM algorithm.
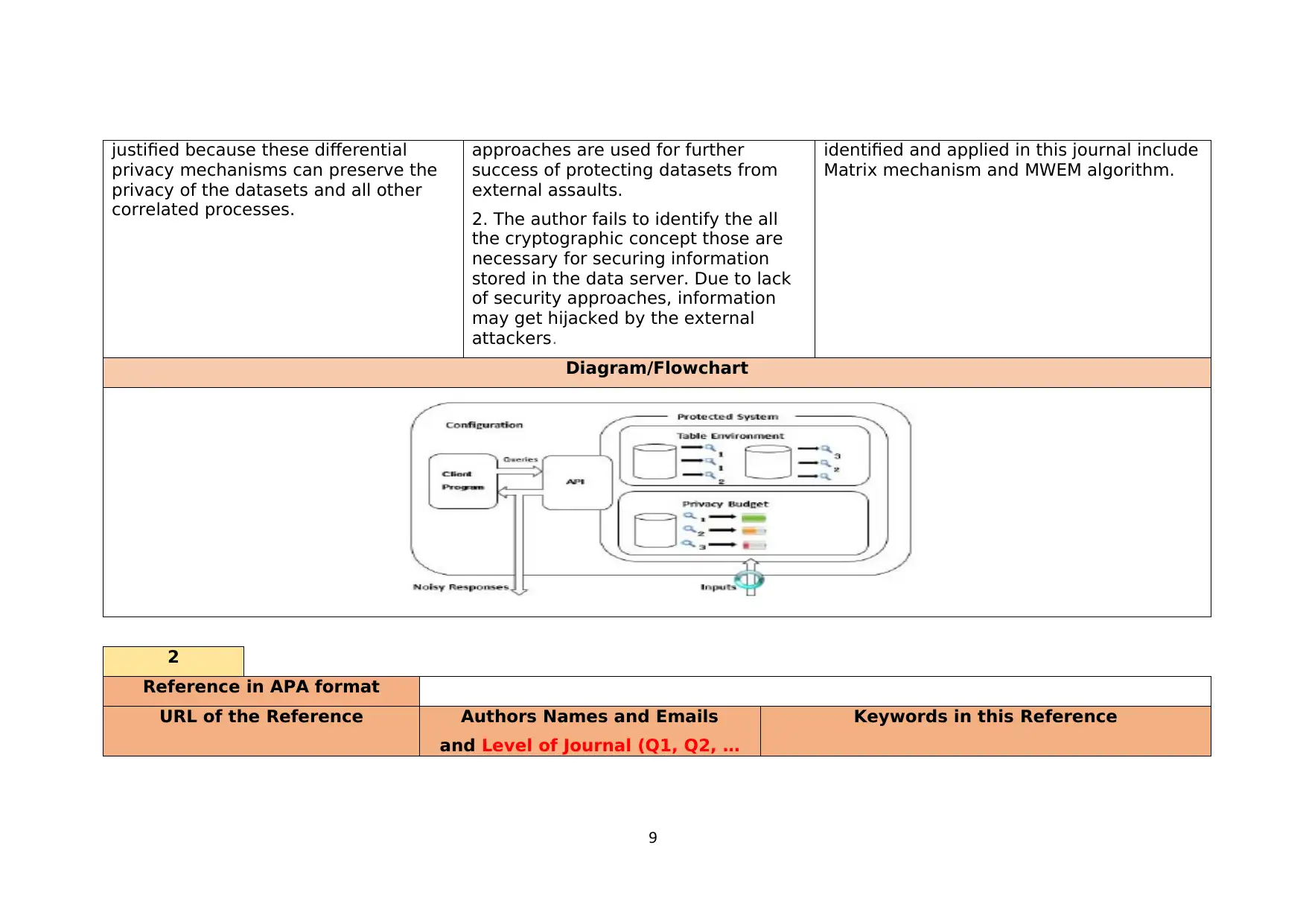
Diagram/Flowchart
2
Reference in APA format
URL of the Reference Authors Names and Emails
and Level of Journal (Q1, Q2, …
Keywords in this Reference
9
privacy mechanisms can preserve the
privacy of the datasets and all other
correlated processes.
approaches are used for further
success of protecting datasets from
external assaults.
2. The author fails to identify the all
the cryptographic concept those are
necessary for securing information
stored in the data server. Due to lack
of security approaches, information
may get hijacked by the external
attackers.
identified and applied in this journal include
Matrix mechanism and MWEM algorithm.
Diagram/Flowchart
2
Reference in APA format
URL of the Reference Authors Names and Emails
and Level of Journal (Q1, Q2, …
Keywords in this Reference
9
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
Qn)
Hua, J., Tang, A., Fang, Y., Shen, Z., &
Zhong, S. (2016). Privacy-preserving utility
verification of the data published by non-
interactive differentially private
mechanisms. IEEE Transactions on
Information Forensics and Security, 11(10),
2298-2311.
http://ieeexplore.ieee.org/
abstract/document/7416007/
Author Names and emails:
Jingyu Hua, An Tang, Yixin Fang,
Zhenyu Shen, and Sheng Zhong
Email: NA
Journal Level: NA
Collaborative data publishing, utility
verification, differential privacy.
The Name of the Current
Solution (Technique/ Method/
Scheme/ Algorithm/ Model/
Tool/ Framework/ ... etc )
The Goal (Purpose) of this
Solution & What is the Problem
that need to be solved
What are the components of it?
Techniques: Collaboration data
publishing, utility verification and
differential privacy
Tools: Encryption is the only tool
or method mentioned in this
journal.
Applied Area: Application of this
mechanism is possible only on the
published datasets.
Problem: The main problem
identified in this journal is lack of
usage of privacy mechanism for
protecting data from the external
attackers.
Purpose (Goal): To identify the way
on how the central data publishers
are responsible to aggregate
sensitive data.
The goal of the article is to identify
the privacy preserving utility
verification of all those data
published in the non interactive
Pre-Operation:
Data identification
Data collection
Data collaboration
During Surgery:
Differentially publishing private data
10
Hua, J., Tang, A., Fang, Y., Shen, Z., &
Zhong, S. (2016). Privacy-preserving utility
verification of the data published by non-
interactive differentially private
mechanisms. IEEE Transactions on
Information Forensics and Security, 11(10),
2298-2311.
http://ieeexplore.ieee.org/
abstract/document/7416007/
Author Names and emails:
Jingyu Hua, An Tang, Yixin Fang,
Zhenyu Shen, and Sheng Zhong
Email: NA
Journal Level: NA
Collaborative data publishing, utility
verification, differential privacy.
The Name of the Current
Solution (Technique/ Method/
Scheme/ Algorithm/ Model/
Tool/ Framework/ ... etc )
The Goal (Purpose) of this
Solution & What is the Problem
that need to be solved
What are the components of it?
Techniques: Collaboration data
publishing, utility verification and
differential privacy
Tools: Encryption is the only tool
or method mentioned in this
journal.
Applied Area: Application of this
mechanism is possible only on the
published datasets.
Problem: The main problem
identified in this journal is lack of
usage of privacy mechanism for
protecting data from the external
attackers.
Purpose (Goal): To identify the way
on how the central data publishers
are responsible to aggregate
sensitive data.
The goal of the article is to identify
the privacy preserving utility
verification of all those data
published in the non interactive
Pre-Operation:
Data identification
Data collection
Data collaboration
During Surgery:
Differentially publishing private data
10
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
differentially private mechanism.
Another goal is to identify the
mechanism through which the
private data can be encrypted.
Utility verification
Differential privacy
The Process (Mechanism) of this Work; Means How the Problem has Solved & Advantage & Disadvantage of
Each Step in This Process
Process Steps - Pre Operation Advantage Disadvantage (Limitation)
1 Data identification Through this component service
providers can collect huge amount of
data from the required sources.
If proper data are not collected
then it will lead to major loss.
2 Data collection Data collection can be widely used
and outsourced as well whenever
needed.
NA
3 Data collaboration Collected data can be used to serve
different purposes.
NA
Process Steps - During Surgery Advantage Disadvantage (Limitation)
1 Differentially publishing private data This data can be accessed much
easily than the others.
NA
2 Utility verification Data verification helps to identify and
understand the feature of the data
and also the areas where the
information can be used widely.
NA
3 Differential privacy With proper privacy none of the
unauthorized user will be able to
NA
11
Another goal is to identify the
mechanism through which the
private data can be encrypted.
Utility verification
Differential privacy
The Process (Mechanism) of this Work; Means How the Problem has Solved & Advantage & Disadvantage of
Each Step in This Process
Process Steps - Pre Operation Advantage Disadvantage (Limitation)
1 Data identification Through this component service
providers can collect huge amount of
data from the required sources.
If proper data are not collected
then it will lead to major loss.
2 Data collection Data collection can be widely used
and outsourced as well whenever
needed.
NA
3 Data collaboration Collected data can be used to serve
different purposes.
NA
Process Steps - During Surgery Advantage Disadvantage (Limitation)
1 Differentially publishing private data This data can be accessed much
easily than the others.
NA
2 Utility verification Data verification helps to identify and
understand the feature of the data
and also the areas where the
information can be used widely.
NA
3 Differential privacy With proper privacy none of the
unauthorized user will be able to
NA
11
access the data from the published
dataset.
Major Impact Factors in this Work
Dependent Variable Independent Variable
Sensitive data Central data publisher
Input and Output Feature of This Solution Contribution & The Value of This Work
Input: Generalization operation is the
input of the article.
Output: Successful privacy and security
operation through which the
collaborated information can be
secured from the external attackers.
The solution highlighted the issues of
privacy preservation and published
collaborative data. How the utility can
be measured are also demonstrated
by the author, In addition to this, a
privacy preserving verification
mechanism is proposed and also the
security and efficiency of the proposed
mechanism are also provided in this
solution.
The authors highlighted the data privacy
issues and also mentioned both the DiffPart
and DiffGen to set valued data. This
mechanism can be used in real world and it
is expected that it will give major success.
1. What in the method could have
been better?
2. what in the author analyses
were missed?
3. was there a technique that could
have been used, or a question that
could have been asked, that the
researchers did not use or ask?
The methods that requires betterment
include cryptography algorithm
The authors have analysed all the relevant tools
and techniques and even how the techniques
In a horizontal distribution context how the
mechanism actually works can be another question to
12
dataset.
Major Impact Factors in this Work
Dependent Variable Independent Variable
Sensitive data Central data publisher
Input and Output Feature of This Solution Contribution & The Value of This Work
Input: Generalization operation is the
input of the article.
Output: Successful privacy and security
operation through which the
collaborated information can be
secured from the external attackers.
The solution highlighted the issues of
privacy preservation and published
collaborative data. How the utility can
be measured are also demonstrated
by the author, In addition to this, a
privacy preserving verification
mechanism is proposed and also the
security and efficiency of the proposed
mechanism are also provided in this
solution.
The authors highlighted the data privacy
issues and also mentioned both the DiffPart
and DiffGen to set valued data. This
mechanism can be used in real world and it
is expected that it will give major success.
1. What in the method could have
been better?
2. what in the author analyses
were missed?
3. was there a technique that could
have been used, or a question that
could have been asked, that the
researchers did not use or ask?
The methods that requires betterment
include cryptography algorithm
The authors have analysed all the relevant tools
and techniques and even how the techniques
In a horizontal distribution context how the
mechanism actually works can be another question to
12
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 25
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





