NIT6130 - Introduction to Research: Experiment Design and Analysis
VerifiedAdded on 2023/06/04
|16
|1975
|236
Project
AI Summary
This project report details the process of designing and implementing experiments related to bio-inspired communications and IoT. The assignment begins with data collection from various sources including online journals, books, articles, government databases, and private companies. The collected data is stored and organized, followed by data pre-computing, feature selection, and experiment design using a hybrid methodology including qualitative and quantitative approaches. The implementation involves the use of software tools to analyze data, and the report presents experiment results through tables and charts. The analysis focuses on result estimation and summarization, providing insights into employee satisfaction with IoT implementation, and the application of bio-inspired secure IPv6 communication protocols. The research concludes with a research outline and bibliography.

NIT 6130- Introduction to Research
Bio-inspired Communications and IoT
Submitted by: Submitted to:
Student ID:
Bio-inspired Communications and IoT
Submitted by: Submitted to:
Student ID:
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Table of Contents
Objective..........................................................................................................................................3
1. Data Collection.........................................................................................................................3
1.1 Identification of data sources............................................................................................3
1.2 Gathering of information.......................................................................................................4
1.3 Data Storage......................................................................................................................5
2. Design and Implementation......................................................................................................6
2.1 Data pre-computing...........................................................................................................6
2.2 Feature section or dimension reduction............................................................................6
2.3 Experiment Designing.......................................................................................................7
2.4 Implementation..........................................................................................................................8
2.4.1 Software tool used..............................................................................................................8
2.4.2 Experiment results............................................................................................................11
3. Result analysis...........................................................................................................................12
3.1 Result Estimation.................................................................................................................12
3.2 Result Summary...................................................................................................................13
4. Research Outline........................................................................................................................14
Objective..........................................................................................................................................3
1. Data Collection.........................................................................................................................3
1.1 Identification of data sources............................................................................................3
1.2 Gathering of information.......................................................................................................4
1.3 Data Storage......................................................................................................................5
2. Design and Implementation......................................................................................................6
2.1 Data pre-computing...........................................................................................................6
2.2 Feature section or dimension reduction............................................................................6
2.3 Experiment Designing.......................................................................................................7
2.4 Implementation..........................................................................................................................8
2.4.1 Software tool used..............................................................................................................8
2.4.2 Experiment results............................................................................................................11
3. Result analysis...........................................................................................................................12
3.1 Result Estimation.................................................................................................................12
3.2 Result Summary...................................................................................................................13
4. Research Outline........................................................................................................................14

Objective
The purpose of assignment has been analyzing data and informtion collected from various
sources. Experiment design and result analysis have been done in the assignment. There have
been various data and information collected from both primary and secondary data sources.
Therefore, analysis of data and information will be done in this assignment.
1. Data Collection
Data Collection has been an important part of research. The two types of data collection process
have been primary and secondary methods. This research has followed hybrid approach that
includes both primary and secondary method of data collection. Different sources have been used
from collecting data regarding bio inspired communication and IoT. Various organizations have
been approached for collecting data related to the IoT. All data has been put into a table for
creating records in proper manner.
1.1 Identification of data sources
Following data sources have been used in this research:
Online Journals
Books
Articles
Government databases
Private Companies
The purpose of assignment has been analyzing data and informtion collected from various
sources. Experiment design and result analysis have been done in the assignment. There have
been various data and information collected from both primary and secondary data sources.
Therefore, analysis of data and information will be done in this assignment.
1. Data Collection
Data Collection has been an important part of research. The two types of data collection process
have been primary and secondary methods. This research has followed hybrid approach that
includes both primary and secondary method of data collection. Different sources have been used
from collecting data regarding bio inspired communication and IoT. Various organizations have
been approached for collecting data related to the IoT. All data has been put into a table for
creating records in proper manner.
1.1 Identification of data sources
Following data sources have been used in this research:
Online Journals
Books
Articles
Government databases
Private Companies
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
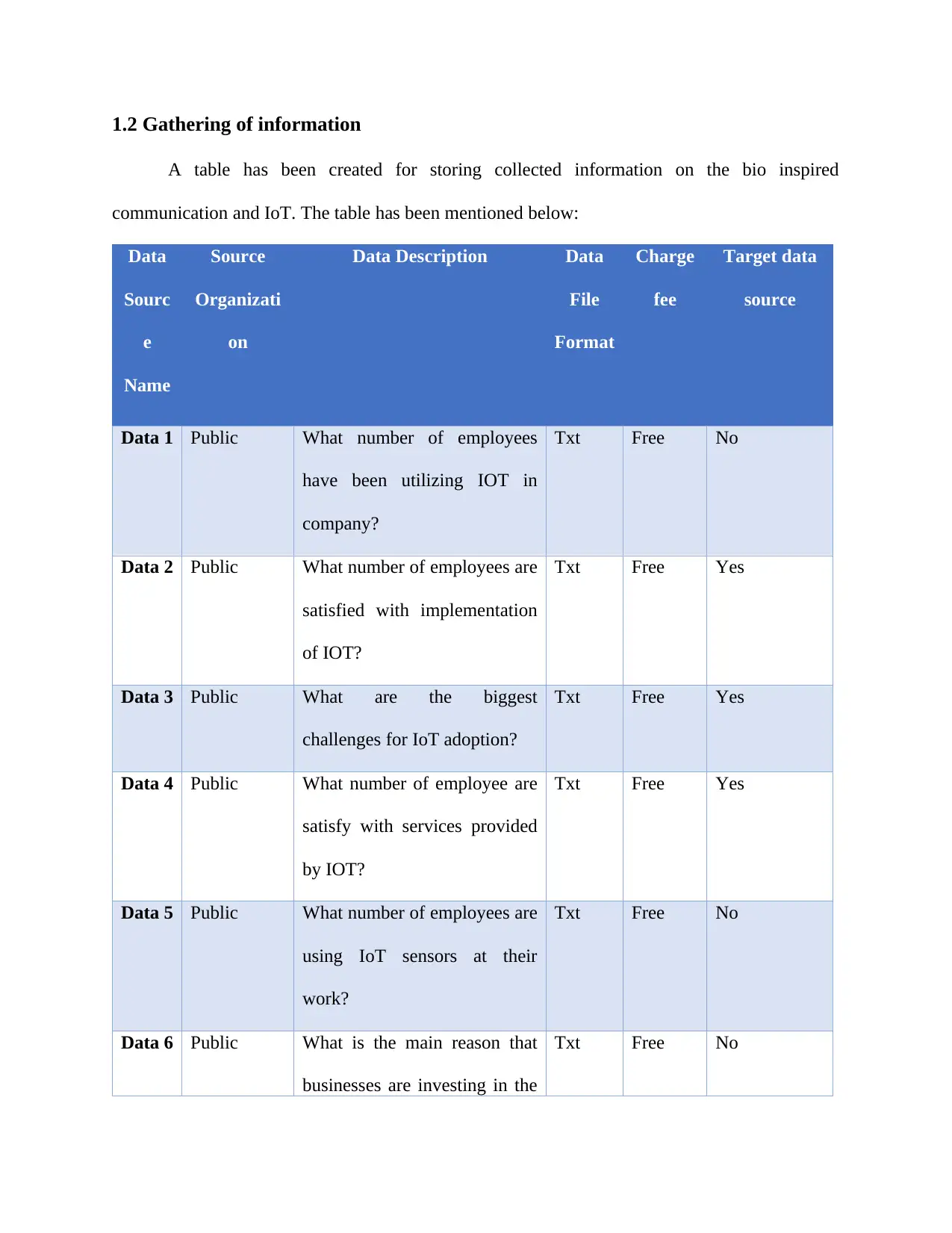
1.2 Gathering of information
A table has been created for storing collected information on the bio inspired
communication and IoT. The table has been mentioned below:
Data
Sourc
e
Name
Source
Organizati
on
Data Description Data
File
Format
Charge
fee
Target data
source
Data 1 Public What number of employees
have been utilizing IOT in
company?
Txt Free No
Data 2 Public What number of employees are
satisfied with implementation
of IOT?
Txt Free Yes
Data 3 Public What are the biggest
challenges for IoT adoption?
Txt Free Yes
Data 4 Public What number of employee are
satisfy with services provided
by IOT?
Txt Free Yes
Data 5 Public What number of employees are
using IoT sensors at their
work?
Txt Free No
Data 6 Public What is the main reason that
businesses are investing in the
Txt Free No
A table has been created for storing collected information on the bio inspired
communication and IoT. The table has been mentioned below:
Data
Sourc
e
Name
Source
Organizati
on
Data Description Data
File
Format
Charge
fee
Target data
source
Data 1 Public What number of employees
have been utilizing IOT in
company?
Txt Free No
Data 2 Public What number of employees are
satisfied with implementation
of IOT?
Txt Free Yes
Data 3 Public What are the biggest
challenges for IoT adoption?
Txt Free Yes
Data 4 Public What number of employee are
satisfy with services provided
by IOT?
Txt Free Yes
Data 5 Public What number of employees are
using IoT sensors at their
work?
Txt Free No
Data 6 Public What is the main reason that
businesses are investing in the
Txt Free No
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
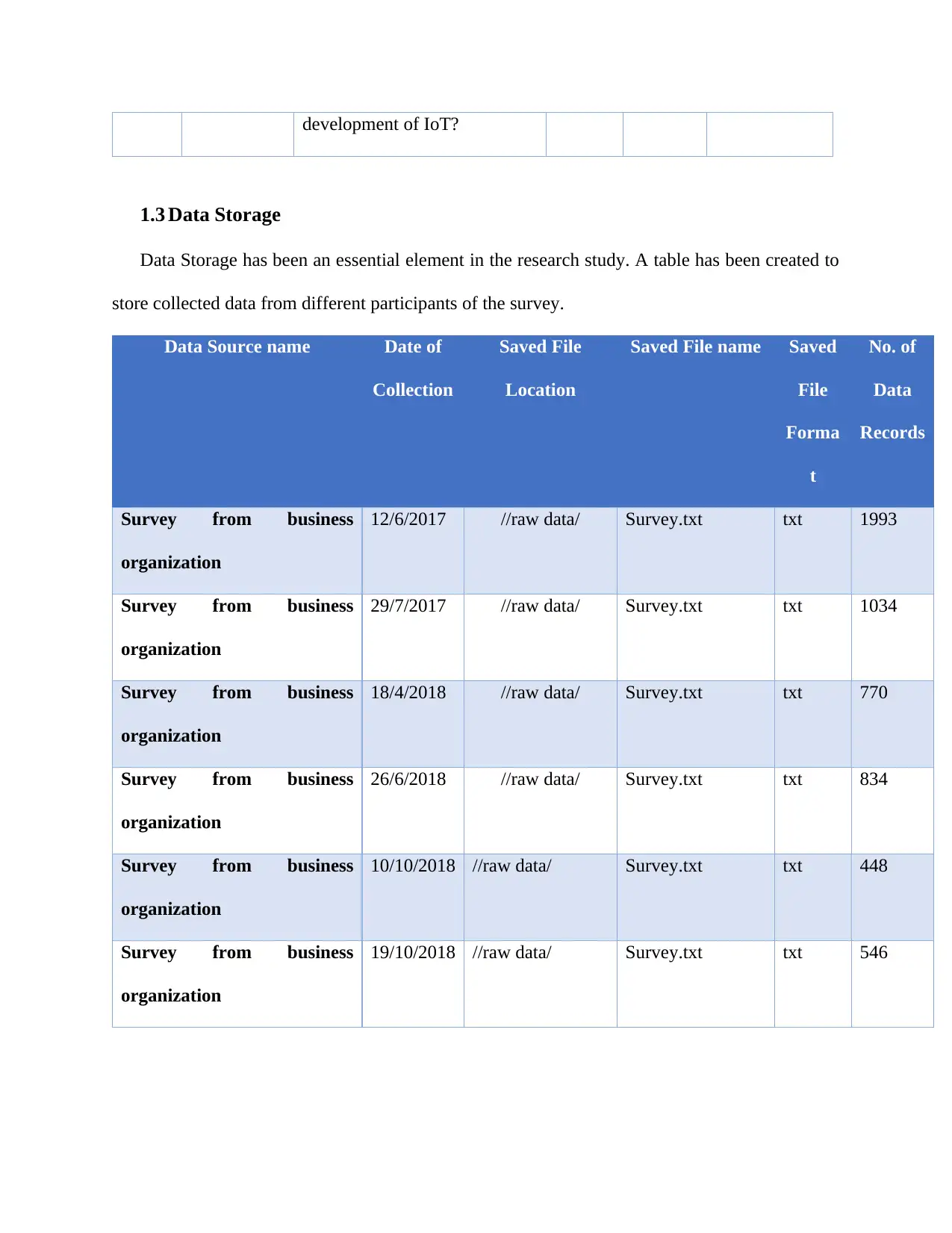
development of IoT?
1.3 Data Storage
Data Storage has been an essential element in the research study. A table has been created to
store collected data from different participants of the survey.
Data Source name Date of
Collection
Saved File
Location
Saved File name Saved
File
Forma
t
No. of
Data
Records
Survey from business
organization
12/6/2017 //raw data/ Survey.txt txt 1993
Survey from business
organization
29/7/2017 //raw data/ Survey.txt txt 1034
Survey from business
organization
18/4/2018 //raw data/ Survey.txt txt 770
Survey from business
organization
26/6/2018 //raw data/ Survey.txt txt 834
Survey from business
organization
10/10/2018 //raw data/ Survey.txt txt 448
Survey from business
organization
19/10/2018 //raw data/ Survey.txt txt 546
1.3 Data Storage
Data Storage has been an essential element in the research study. A table has been created to
store collected data from different participants of the survey.
Data Source name Date of
Collection
Saved File
Location
Saved File name Saved
File
Forma
t
No. of
Data
Records
Survey from business
organization
12/6/2017 //raw data/ Survey.txt txt 1993
Survey from business
organization
29/7/2017 //raw data/ Survey.txt txt 1034
Survey from business
organization
18/4/2018 //raw data/ Survey.txt txt 770
Survey from business
organization
26/6/2018 //raw data/ Survey.txt txt 834
Survey from business
organization
10/10/2018 //raw data/ Survey.txt txt 448
Survey from business
organization
19/10/2018 //raw data/ Survey.txt txt 546
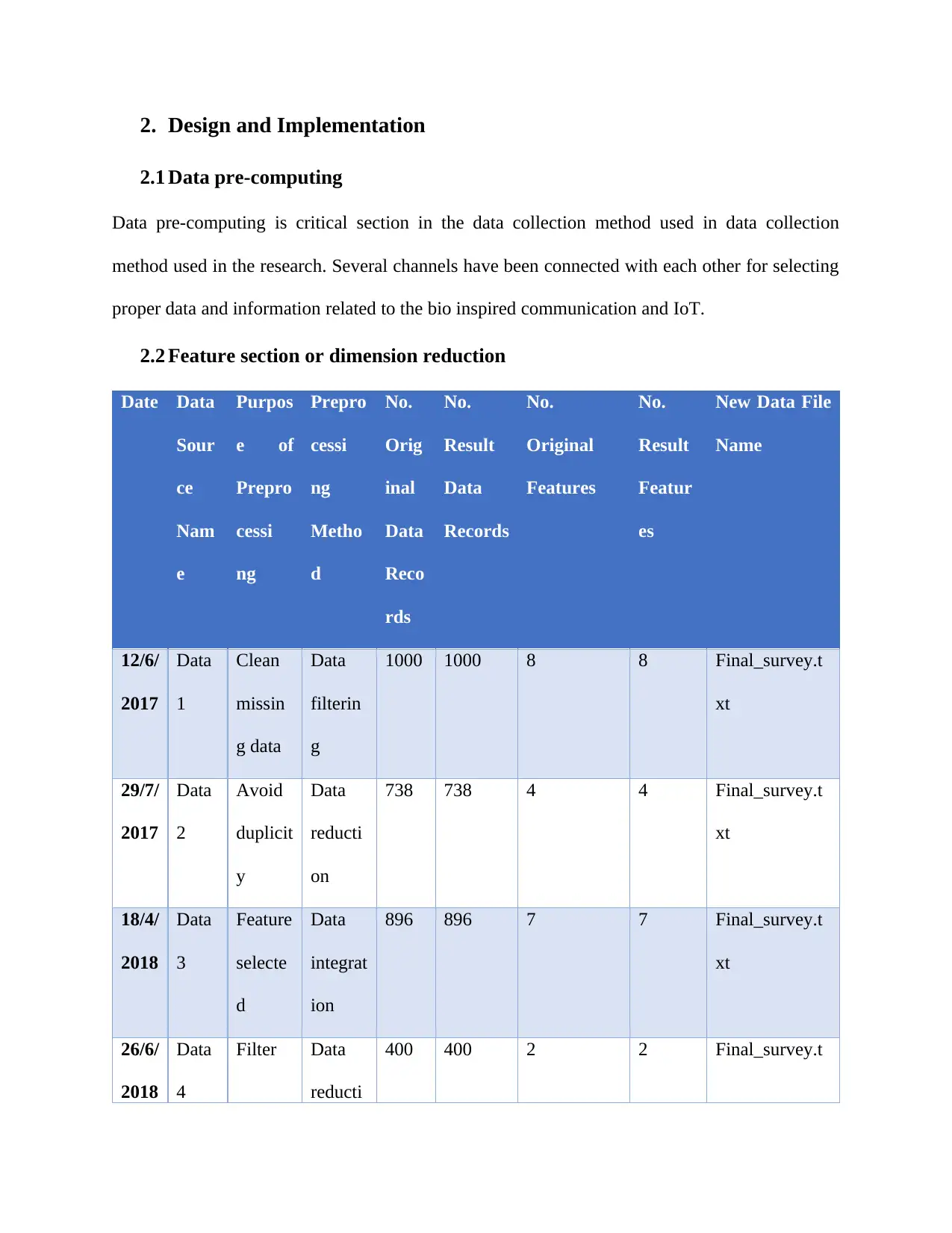
2. Design and Implementation
2.1 Data pre-computing
Data pre-computing is critical section in the data collection method used in data collection
method used in the research. Several channels have been connected with each other for selecting
proper data and information related to the bio inspired communication and IoT.
2.2 Feature section or dimension reduction
Date Data
Sour
ce
Nam
e
Purpos
e of
Prepro
cessi
ng
Prepro
cessi
ng
Metho
d
No.
Orig
inal
Data
Reco
rds
No.
Result
Data
Records
No.
Original
Features
No.
Result
Featur
es
New Data File
Name
12/6/
2017
Data
1
Clean
missin
g data
Data
filterin
g
1000 1000 8 8 Final_survey.t
xt
29/7/
2017
Data
2
Avoid
duplicit
y
Data
reducti
on
738 738 4 4 Final_survey.t
xt
18/4/
2018
Data
3
Feature
selecte
d
Data
integrat
ion
896 896 7 7 Final_survey.t
xt
26/6/
2018
Data
4
Filter Data
reducti
400 400 2 2 Final_survey.t
2.1 Data pre-computing
Data pre-computing is critical section in the data collection method used in data collection
method used in the research. Several channels have been connected with each other for selecting
proper data and information related to the bio inspired communication and IoT.
2.2 Feature section or dimension reduction
Date Data
Sour
ce
Nam
e
Purpos
e of
Prepro
cessi
ng
Prepro
cessi
ng
Metho
d
No.
Orig
inal
Data
Reco
rds
No.
Result
Data
Records
No.
Original
Features
No.
Result
Featur
es
New Data File
Name
12/6/
2017
Data
1
Clean
missin
g data
Data
filterin
g
1000 1000 8 8 Final_survey.t
xt
29/7/
2017
Data
2
Avoid
duplicit
y
Data
reducti
on
738 738 4 4 Final_survey.t
xt
18/4/
2018
Data
3
Feature
selecte
d
Data
integrat
ion
896 896 7 7 Final_survey.t
xt
26/6/
2018
Data
4
Filter Data
reducti
400 400 2 2 Final_survey.t
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

the
data
on xt
2.3 Experiment Designing
Analysis has been depended on the approach selected for the research. I have selected hybrid
methodology including qualitative and quantitative approach. I have included 6 questionnaires in
survey.
Sex Male
Female
Age range 18-25 years
26-35 years
36-45 years
45-50 years
Over 50 years
Education High school
College Diploma
Commerce
Graduation
Masters
Background Manager
IT officer
Accountant
Employee
data
on xt
2.3 Experiment Designing
Analysis has been depended on the approach selected for the research. I have selected hybrid
methodology including qualitative and quantitative approach. I have included 6 questionnaires in
survey.
Sex Male
Female
Age range 18-25 years
26-35 years
36-45 years
45-50 years
Over 50 years
Education High school
College Diploma
Commerce
Graduation
Masters
Background Manager
IT officer
Accountant
Employee
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
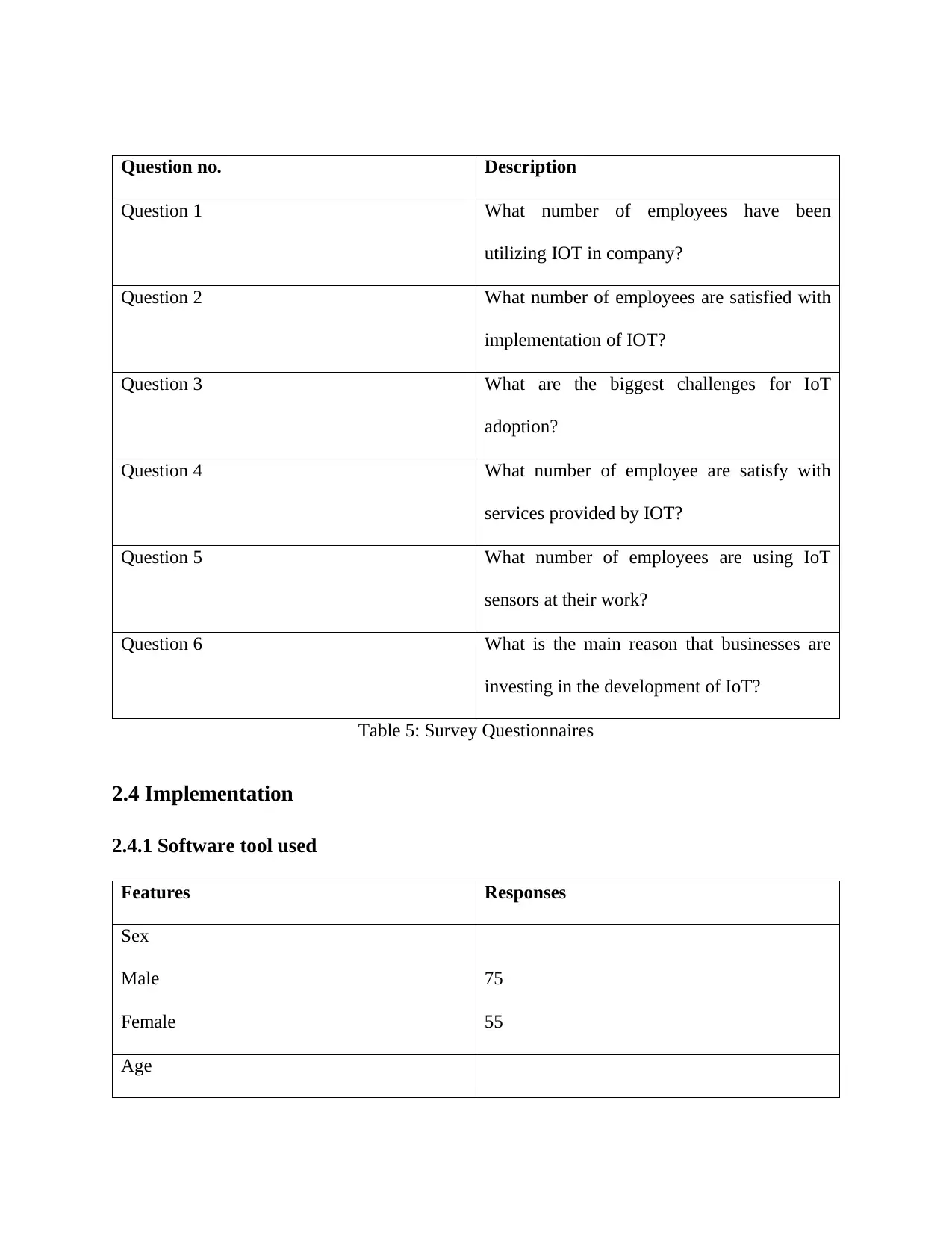
Question no. Description
Question 1 What number of employees have been
utilizing IOT in company?
Question 2 What number of employees are satisfied with
implementation of IOT?
Question 3 What are the biggest challenges for IoT
adoption?
Question 4 What number of employee are satisfy with
services provided by IOT?
Question 5 What number of employees are using IoT
sensors at their work?
Question 6 What is the main reason that businesses are
investing in the development of IoT?
Table 5: Survey Questionnaires
2.4 Implementation
2.4.1 Software tool used
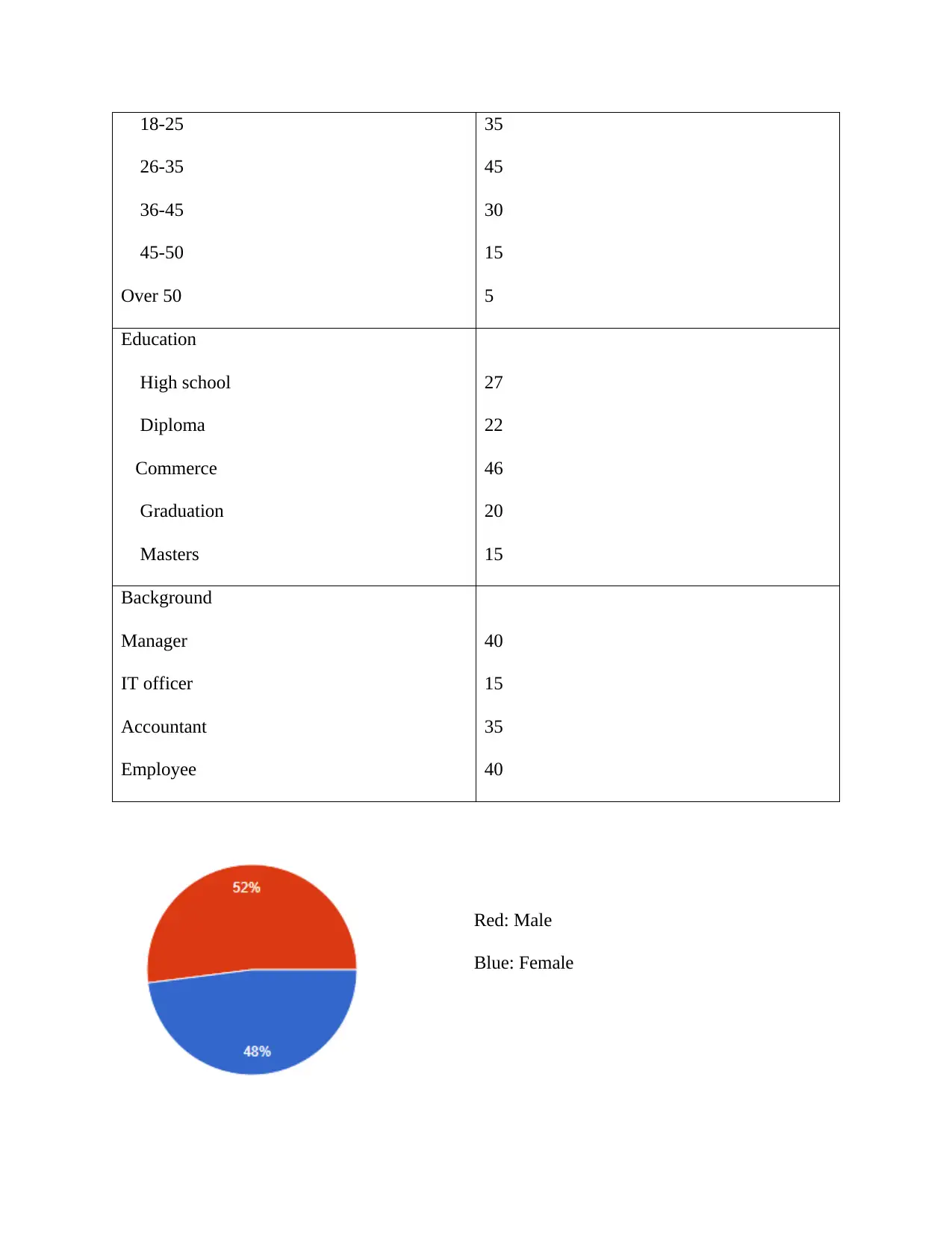
Features Responses
Sex
Male
Female
75
55
Age
Question 1 What number of employees have been
utilizing IOT in company?
Question 2 What number of employees are satisfied with
implementation of IOT?
Question 3 What are the biggest challenges for IoT
adoption?
Question 4 What number of employee are satisfy with
services provided by IOT?
Question 5 What number of employees are using IoT
sensors at their work?
Question 6 What is the main reason that businesses are
investing in the development of IoT?
Table 5: Survey Questionnaires
2.4 Implementation
2.4.1 Software tool used
Features Responses
Sex
Male
Female
75
55
Age
18-25
26-35
36-45
45-50
Over 50
35
45
30
15
5
Education
High school
Diploma
Commerce
Graduation
Masters
27
22
46
20
15
Background
Manager
IT officer
Accountant
Employee
40
15
35
40
Red: Male
Blue: Female
26-35
36-45
45-50
Over 50
35
45
30
15
5
Education
High school
Diploma
Commerce
Graduation
Masters
27
22
46
20
15
Background
Manager
IT officer
Accountant
Employee
40
15
35
40
Red: Male
Blue: Female
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
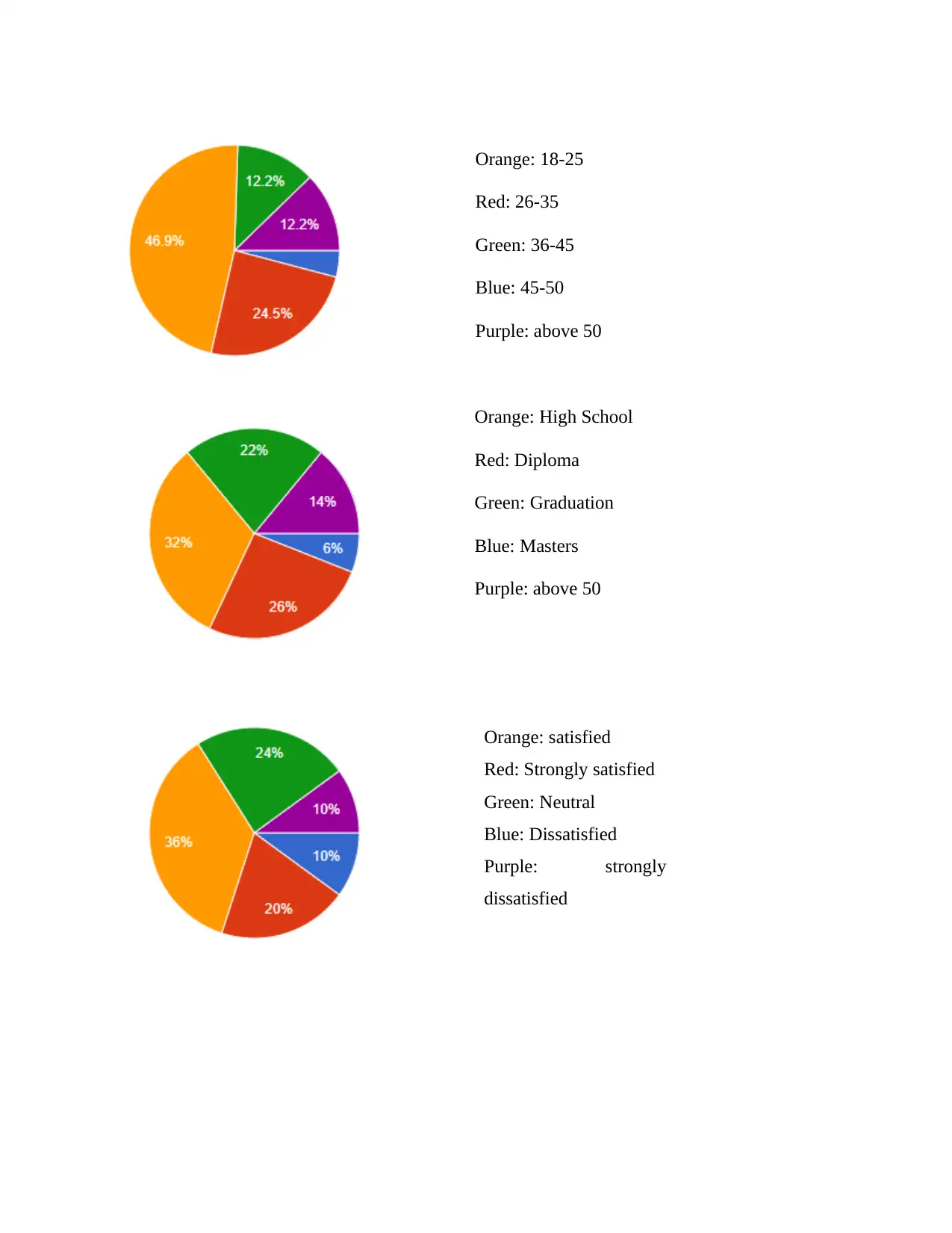
Orange: 18-25
Red: 26-35
Green: 36-45
Blue: 45-50
Purple: above 50
Orange: High School
Red: Diploma
Green: Graduation
Blue: Masters
Purple: above 50
Orange: satisfied
Red: Strongly satisfied
Green: Neutral
Blue: Dissatisfied
Purple: strongly
dissatisfied
Red: 26-35
Green: 36-45
Blue: 45-50
Purple: above 50
Orange: High School
Red: Diploma
Green: Graduation
Blue: Masters
Purple: above 50
Orange: satisfied
Red: Strongly satisfied
Green: Neutral
Blue: Dissatisfied
Purple: strongly
dissatisfied
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
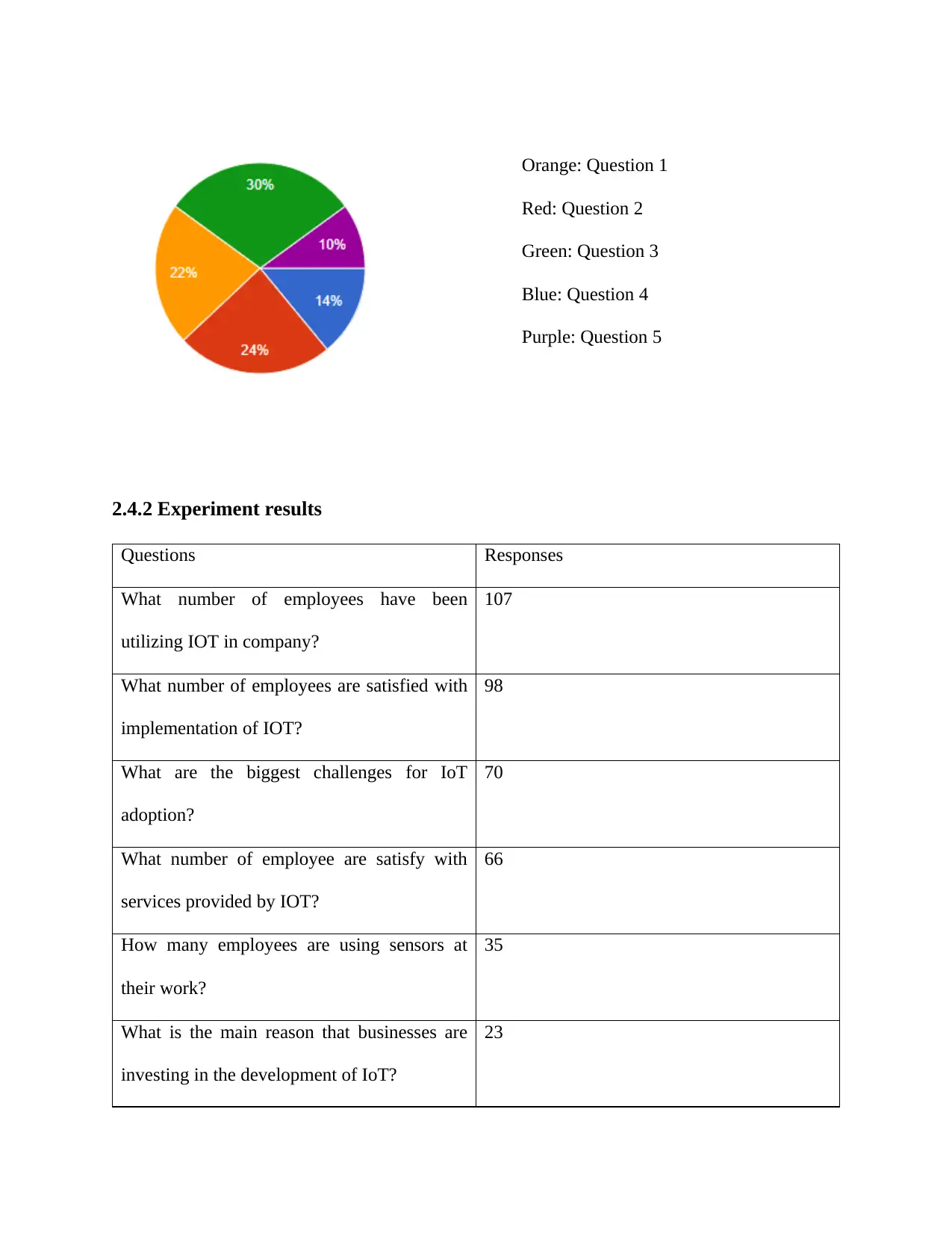
2.4.2 Experiment results
Questions Responses
What number of employees have been
utilizing IOT in company?
107
What number of employees are satisfied with
implementation of IOT?
98
What are the biggest challenges for IoT
adoption?
70
What number of employee are satisfy with
services provided by IOT?
66
How many employees are using sensors at
their work?
35
What is the main reason that businesses are
investing in the development of IoT?
23
Orange: Question 1
Red: Question 2
Green: Question 3
Blue: Question 4
Purple: Question 5
Questions Responses
What number of employees have been
utilizing IOT in company?
107
What number of employees are satisfied with
implementation of IOT?
98
What are the biggest challenges for IoT
adoption?
70
What number of employee are satisfy with
services provided by IOT?
66
How many employees are using sensors at
their work?
35
What is the main reason that businesses are
investing in the development of IoT?
23
Orange: Question 1
Red: Question 2
Green: Question 3
Blue: Question 4
Purple: Question 5

Figure 5: Pie chart of % responses
3. Result analysis
3.1 Result Estimation
According to the pie charts, there have been 34.7% male and 65.3% female involved in
the survey. These data shows that female employees have been using IoT devices in the business
organization. 33% employees are satisfied with the use of the IoT in the business organization.
IoT have been helping in maintaining several duties in the organization. The Bio-inspired Secure
IPv6 Communication Protocol have been flexible in function which helps in delivering high
security over the IPv6 based communication. However, for ensuring security resource
constrained heterogeneous IPv6 communication systems have been injected with AIS code.
Artificial Immune System has been able to enhance recognized pouting protocol for providing
low power and lossy networks or facilitating intelligent security in BsCoP. The correlation
function identifies about different malicious node for misbehaving in the thresholds under AIS.
Routing protocols have been providing improved performance by the integration of AIS code
Orange: Question 1
Red: Question 2
Green: Question 3
Blue: Question 4
Purple: Question 5
3. Result analysis
3.1 Result Estimation
According to the pie charts, there have been 34.7% male and 65.3% female involved in
the survey. These data shows that female employees have been using IoT devices in the business
organization. 33% employees are satisfied with the use of the IoT in the business organization.
IoT have been helping in maintaining several duties in the organization. The Bio-inspired Secure
IPv6 Communication Protocol have been flexible in function which helps in delivering high
security over the IPv6 based communication. However, for ensuring security resource
constrained heterogeneous IPv6 communication systems have been injected with AIS code.
Artificial Immune System has been able to enhance recognized pouting protocol for providing
low power and lossy networks or facilitating intelligent security in BsCoP. The correlation
function identifies about different malicious node for misbehaving in the thresholds under AIS.
Routing protocols have been providing improved performance by the integration of AIS code
Orange: Question 1
Red: Question 2
Green: Question 3
Blue: Question 4
Purple: Question 5
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 16
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





